Toward Generative AI-Based Intrusion Detection Systems for the Internet of Vehicles (IoV)
Abstract
1. Introduction
1.1. Existing Reviews and Our Contributions
1.2. Survey Methodology
1.2.1. Inclusion Criteria
- Research applying IDS to vehicular networks, including in-vehicle (IVN) and external communication (V2X) settings.
- Studies involving Machine Learning, Deep Learning, or Generative AI methods such as GANs, Transformers, and LLMs.
- Papers providing sufficient technical detail, including the threat model, dataset, and evaluation metrics.
1.2.2. Exclusion Criteria
- Papers focused on general IoT or cloud environments without specific application to vehicular networks.
- Studies lacking experimental validation or performance metrics.
- Non-English articles or those with limited accessibility or academic rigor.
1.3. Survey Organization
2. Background
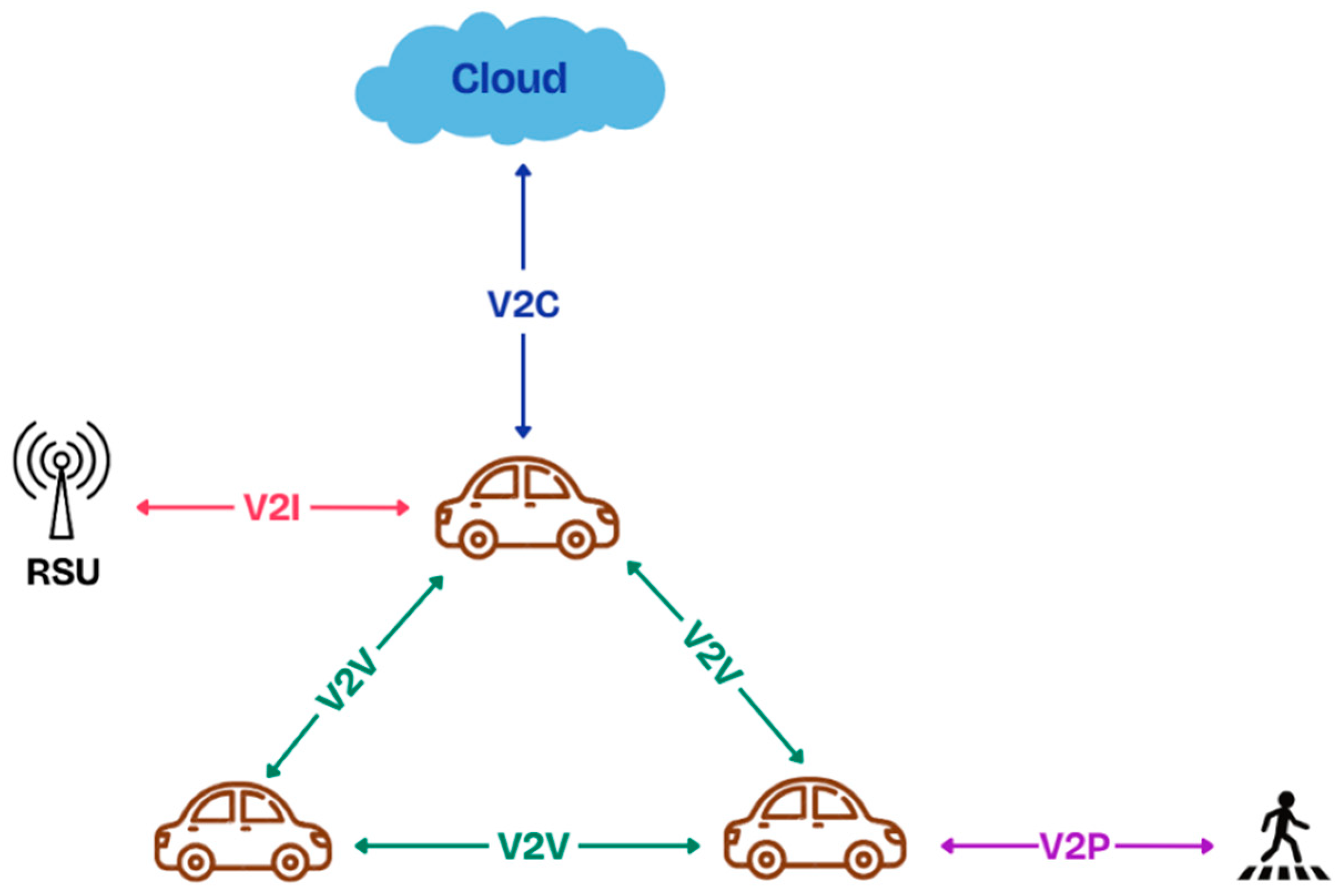
2.1. IoV Communication Types
2.2. IoV Communication Architecture
2.3. Possible Attacks in IoV
2.4. Emerging AI-Driven Threats in IoT and Implications for IoV Security
2.5. Review of Existing ML and DL Security Approaches in IoV
2.5.1. Machine Learning-Based IDS
2.5.2. Deep Learning-Based IDS
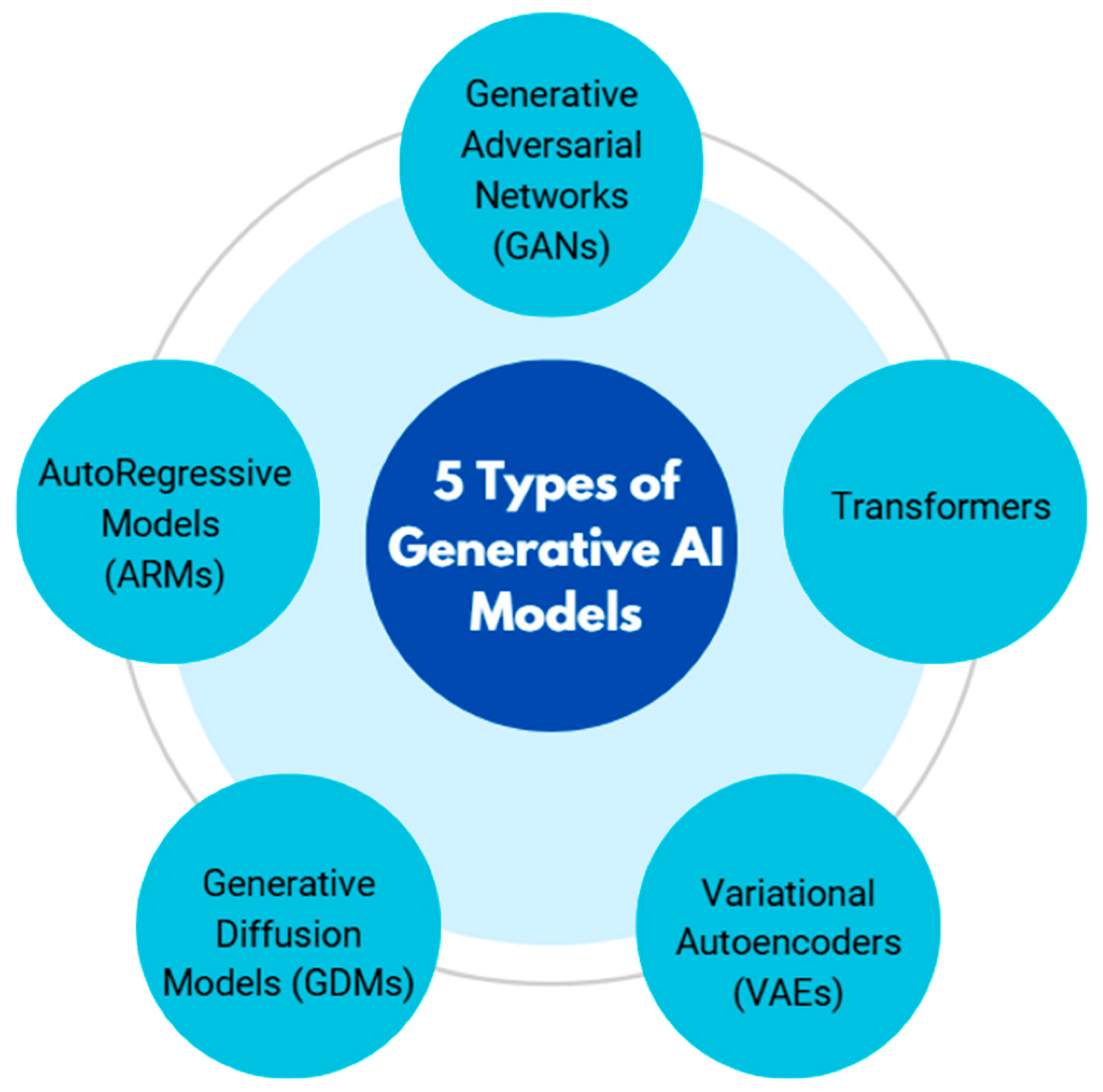
3. Generative AI for Threat Detection
3.1. Generative Adversarial Networks (GANs)
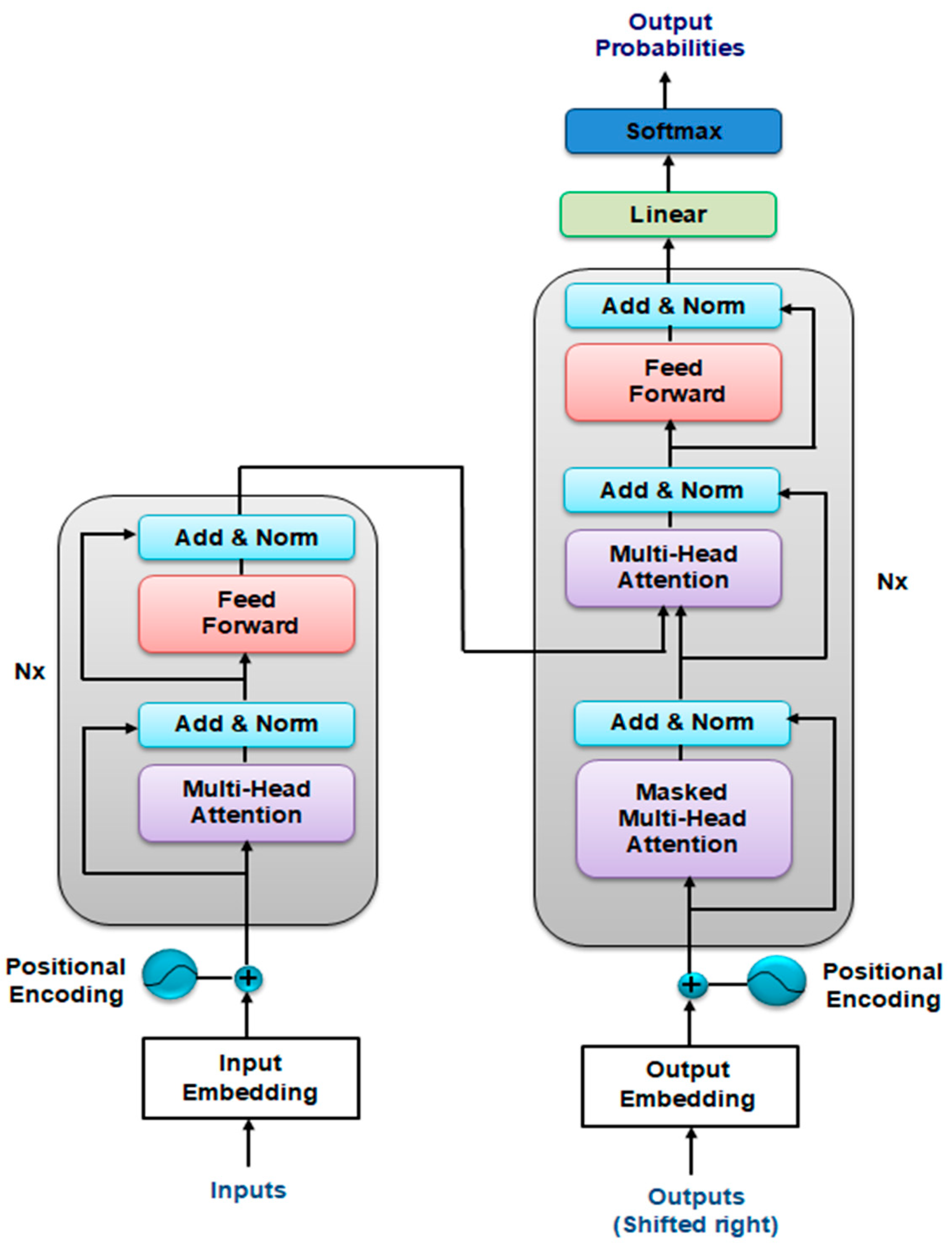
3.2. Transformers
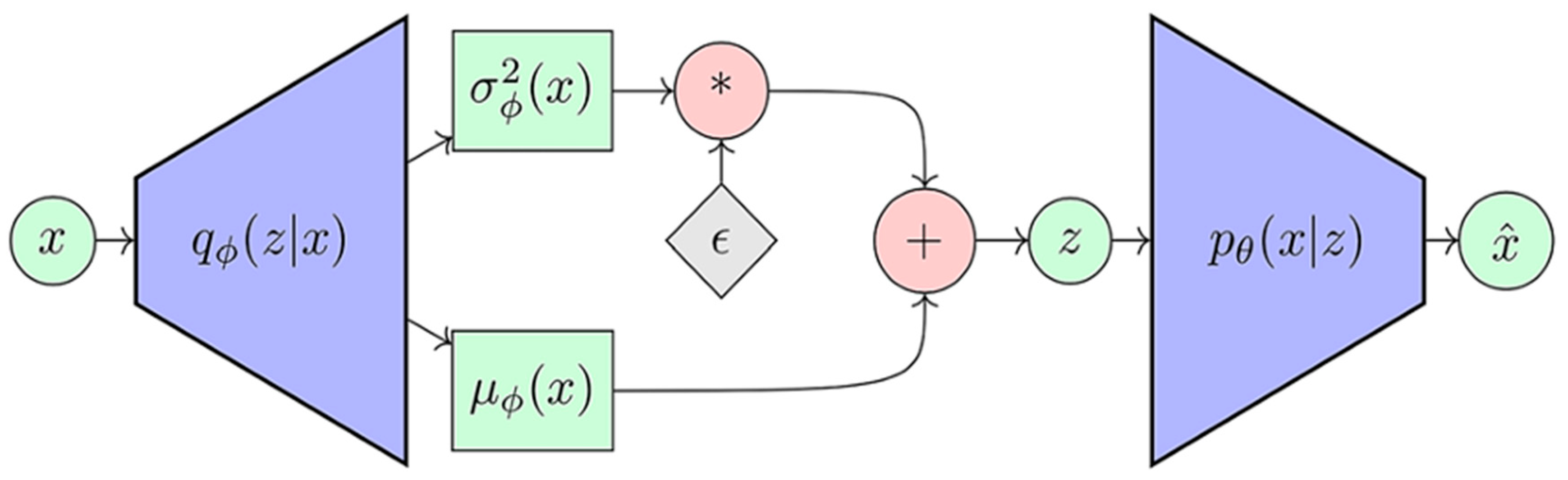
3.3. Variational Autoencoders (VAEs)
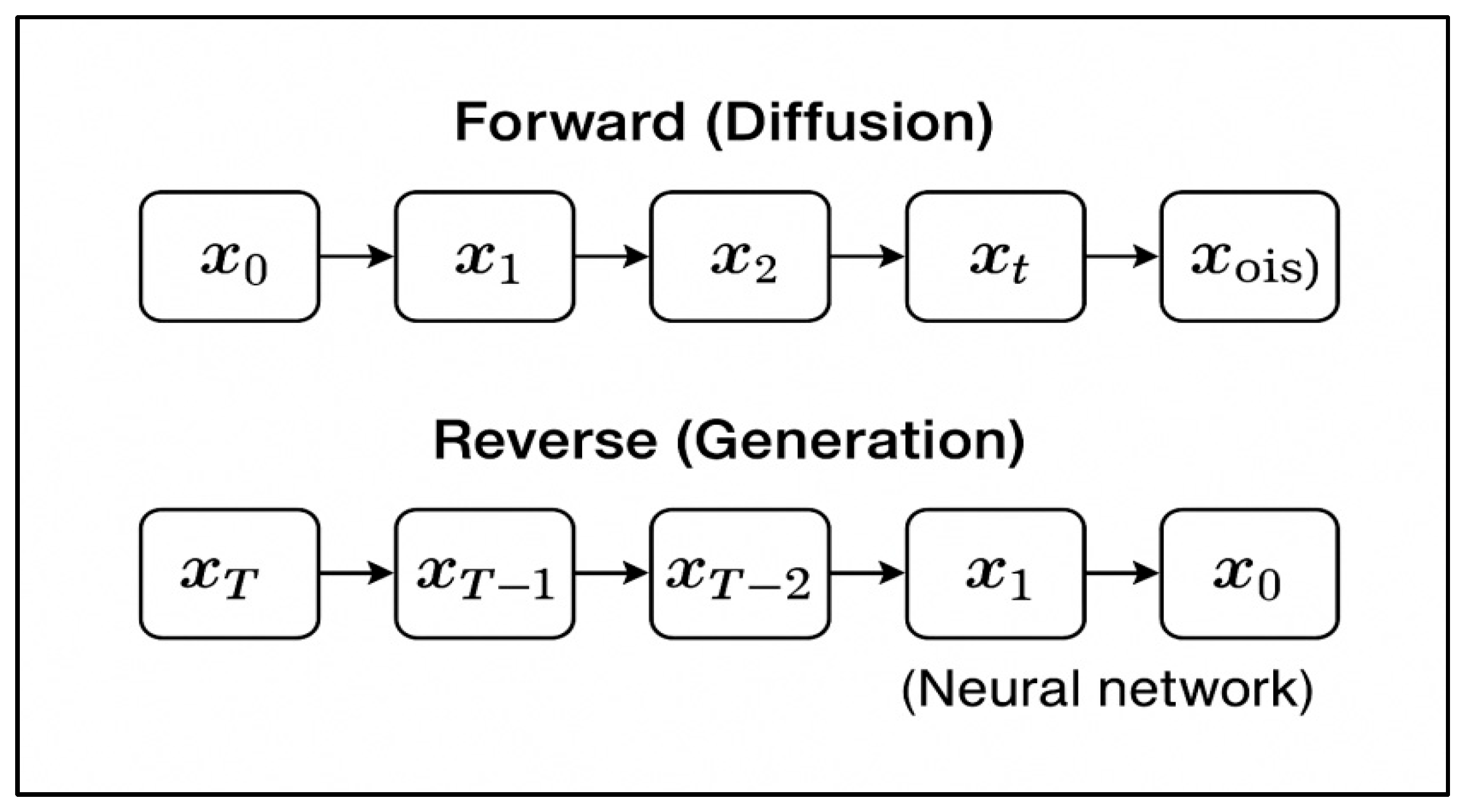
3.4. Generative Diffusion Models (GDMs)
3.5. AutoRegressive Models (ARMs)
4. Generative AI-Based IDS for IoV
4.1. Standardized Evaluation and Benchmarking Challenges
4.2. Comparative Analysis: Generative AI’s Role in Addressing Traditional ML/DL Limitations
4.3. Contextual Suitability of Generative Models
5. Challenges and Future Research Directions
5.1. Challenges
5.2. Adversarial Threats to Generative Models
5.3. Ethical and Privacy Considerations
5.4. Future Research Directions
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| IDS | Intrusion Detection System |
| IoV | Internet of Vehicles |
| GAI | Generative Artificial Intelligence |
| GAN | Generative Adversarial Network |
| VAE | Variational Autoencoder |
| GDM | Generative Diffusion Model |
| ARM | AutoRegressive Model |
| ML | Machine Learning |
| DL | Deep Learning |
| IVN | In-Vehicle Network |
| CAN | Controller Area Network |
| VANET | Vehicular Ad Hoc Network |
| IoT | Internet of Things |
| V2X | Vehicle-to-Everything |
| V2V | Vehicle-to-Vehicle |
| V2I | Vehicle-to-Infrastructure |
| V2P | Vehicle-to-Pedestrian |
| V2C | Vehicle-to-Cloud |
| Inter-V | Inter-Vehicle |
| OBU | On-Board Unit |
| RSU | Road-Side Unit |
| DoS | Denial of Service |
| DDoS | Distributed Denial of Service |
| KNN | K-Nearest Neighbor |
| SVM | Support Vector Machine |
| RF | Random Forest |
| DT | Decision Tree |
| ET | Extra Trees |
| XGBoost | Extreme Gradient Boosting |
| LightGBM | Light Gradient-Boosting Machine |
| AdaBoost | Adaptive Boosting |
| LDA | Linear Discriminant Analysis |
| OCSVM | One-Class Support Vector Machine |
| FPR | False Positive Rate |
| FNR | False Negative Rate |
| ANN | Artificial Neural Network |
| MLP | Multi-Layer Perceptron |
| DNN | Deep Neural Network |
| DBN | Deep Belief Network |
| CNN | Convolutional Neural Network |
| DCNN | Deep Convolutional Neural Network |
| LSTM | Long Short-Term Memory |
| Bi-LSTM | Bidirectional LSTM |
| BiGAN | Bidirectional Generative Adversarial Network |
| ACGAN | Auxiliary Classifier GAN |
| AE | Autoencoder |
| CVAE | Conditional Variational Autoencoder |
| A-VAE | Attention-based Variational Autoencoder |
| Conv-AE | Convolutional Autoencoder |
| SA | Self-Attention |
| FL | Federated Learning |
| EC | Edge Computing |
| MDS | Misbehavior Detection System |
| LLM | Large Language Model |
| BSM | Basic Safety Message |
References
- Man, D.; Zeng, F.; Lv, J.; Xuan, S.; Yang, W.; Guizani, M. AI-Based Intrusion Detection for Intelligence Internet of Vehicles. IEEE Consum. Electron. Mag. 2021, 12, 109–116. [Google Scholar] [CrossRef]
- Almehdhar, M.; Albaseer, A.; Khan, M.A.; Abdallah, M.; Menouar, H.; Al-Kuwari, S.; Al-Fuqaha, A. Deep Learning in the Fast Lane: A Survey on Advanced Intrusion Detection Systems for Intelligent Vehicle Networks. IEEE Open J. Veh. Technol. 2024, 5, 869–906. [Google Scholar] [CrossRef]
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Petrovski, A.; Madzudzo, G.; Cheah, M. AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey. ACM Comput. Surv. 2023, 55, 237. [Google Scholar] [CrossRef]
- Karim, S.M.; Habbal, A.; Chaudhry, S.A.; Irshad, A. Architecture, Protocols, and Security in IoV: Taxonomy, Analysis, Challenges, and Solutions. Secur. Commun. Netw. 2022, 2022, 1131479. [Google Scholar] [CrossRef]
- Liu, N. Internet of Vehicles: Your Next Connection. WinWin Mag. 2011, 11, 23–28. [Google Scholar]
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.T.; Liu, X. Internet of Vehicles: Motivation, Layered Architecture, Network Model, Challenges, and Future Aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of Vehicles: Architecture, Protocols, and Security. IEEE Internet Things J. 2017, 5, 3701–3709. [Google Scholar] [CrossRef]
- Liu, K.; Xu, X.; Chen, M.; Liu, B.; Wu, L.; Lee, V.C. A Hierarchical Architecture for the Future Internet of Vehicles. IEEE Commun. Mag. 2019, 57, 41–47. [Google Scholar] [CrossRef]
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the Internet of Vehicles: Network Architectures and Applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Gao, L.; Wu, C.; Du, Z.; Yoshinaga, T.; Zhong, L.; Liu, F.; Ji, Y. Toward Efficient Blockchain for the Internet of Vehicles with Hierarchical Blockchain Resource Scheduling. Electronics 2022, 11, 832. [Google Scholar] [CrossRef]
- Wang, Y.; Ning, W.; Zhang, S.; Yu, H.; Cen, H.; Wang, S. Architecture and Key Terminal Technologies of 5G-Based Internet of Vehicles. Comput. Electr. Eng. 2021, 95, 107430. [Google Scholar] [CrossRef]
- Samad, A.; Alam, S.; Mohammed, S.; Bhukhari, M. Internet of Vehicles (IoV) Requirements, Attacks and Countermeasures. In Proceedings of the 12th INDIACom—5th International Conference on Computing for Sustainable Global Development, New Delhi, India, 14–16 March 2018; pp. 1–4. [Google Scholar]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.P.C.; Park, Y. Authentication Protocols in Internet of Vehicles: Taxonomy, Analysis, and Challenges. IEEE Access 2020, 8, 54314–54344. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANET Security Challenges and Solutions: A Survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Francillon, A.; Danev, B.; Capkun, S. Relay Attacks on Passive Keyless Entry and Start Systems in Modern Cars. In Proceedings of the 18th Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 6–9 February 2011. [Google Scholar]
- Bariah, L.; Shehada, D.; Salahat, E.; Yeun, C.Y. Recent Advances in VANET Security: A Survey. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference (VTC2015-Fall), Boston, MA, USA, 6–9 September 2015; pp. 1–7. [Google Scholar]
- Haddaji, A.; Ayed, S.; Chaari Fourati, L. IoV Security and Privacy Survey: Issues, Countermeasures, and Challenges. J. Supercomput. 2024, 80, 23018–23082. [Google Scholar] [CrossRef]
- Sun, Y.; Wu, L.; Wu, S.; Li, S.; Zhang, T.; Zhang, L.; Cui, X. Attacks and Countermeasures in the Internet of Vehicles. Ann. Telecommun. 2017, 72, 283–295. [Google Scholar] [CrossRef]
- Cao, H.; Xu, G.; He, Z.; Shi, S.; Xu, S.; Wu, C.; Ning, J. Unveiling the superiority of unsupervised learning on GPU cryptojacking detection: Practice on magnetic side channel-based mechanism. IEEE Trans. Inf. Forensics Secur. 2025, 20, 4874–4889. [Google Scholar] [CrossRef]
- Cao, H.; Liu, D.; Jiang, H.; Luo, J. MagSign: Harnessing dynamic magnetism for user authentication on IoT devices. IEEE Trans. Mob. Comput. 2022, 23, 597–611. [Google Scholar] [CrossRef]
- Ni, T.; Zhang, X.; Zuo, C.; Li, J.; Yan, Z.; Wang, W.; Xu, W.; Luo, X.; Zhao, Q. Uncovering user interactions on smartphones via contactless wireless charging side channels. In Proceedings of the 2023 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–24 May 2023; pp. 3399–3415. [Google Scholar] [CrossRef]
- Ni, T.; Lan, G.; Wang, J.; Zhao, Q.; Xu, W. Eavesdropping mobile app activity via radio-frequency energy harvesting. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 3511–3528. [Google Scholar]
- Ni, T.; Zhang, X.; Zhao, Q. Recovering fingerprints from in-display fingerprint sensors via electromagnetic side channel. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 26–30 November 2023; pp. 253–267. [Google Scholar]
- Hu, P.; Zhuang, H.; Santhalingam, P.S.; Spolaor, R.; Pathak, P.; Zhang, G.; Cheng, X. Accear: Accelerometer acoustic eavesdropping with unconstrained vocabulary. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), Francisco, CA, USA, 23–25 May 2022; pp. 1757–1773. [Google Scholar]
- Duan, D.; Sun, Z.; Ni, T.; Li, S.; Jia, X.; Xu, W.; Li, T. F2key: Dynamically converting your face into a private key based on COTS headphones for reliable voice interaction. In Proceedings of the 22nd Annual International Conference on Mobile Systems, Applications and Services, New York, NY, USA, 3–7 June 2024; pp. 127–140. [Google Scholar]
- Zhou, Y.; Ni, T.; Lee, W.-B.; Zhao, Q. A survey on backdoor threats in large language models (LLMs): Attacks, defenses, and evaluation methods. Trans. Artif. Intell. 2025, 3, 3. [Google Scholar] [CrossRef]
- Wang, J.; Ni, T.; Lee, W.-B.; Zhao, Q. A contemporary survey of large language model assisted program analysis. arXiv 2025, arXiv:2502.18474. [Google Scholar] [CrossRef]
- Alshammari, A.; Zohdy, M.A.; Debnath, D.; Corser, G. Classification Approach for Intrusion Detection in Vehicle Systems. Wirel. Eng. Technol. 2018, 9, 79–94. [Google Scholar] [CrossRef]
- Yang, L.; Moubayed, A.; Hamieh, I.; Shami, A. Tree-Based Intelligent Intrusion Detection System in Internet of Vehicles. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Vuong, T.P.; Loukas, G.; Gan, D. Performance Evaluation of Cyber-Physical Intrusion Detection on a Robotic Vehicle. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; pp. 2106–2113. [Google Scholar]
- Albishi, O.A.; Abdullah, M. DDoS Attacks Detection in IoV Using ML-Based Models with an Enhanced Feature Selection Technique. Int. J. Adv. Comput. Sci. Appl. 2024, 15, 814. [Google Scholar] [CrossRef]
- Sumathi, S.; Rajesh, R.; Karthikeyan, N. DDoS Attack Detection Using Hybrid Machine Learning-Based IDS Models. J. Sci. Ind. Res. 2022, 81, 276–286. [Google Scholar] [CrossRef]
- Halladay, J.; Cullen, D.; Briner, N.; Warren, J.; Fye, K.; Basnet, R.; Doleck, T. Detection and Characterization of DDoS Attacks Using Time-Based Features. IEEE Access 2022, 10, 49794–49807. [Google Scholar] [CrossRef]
- Minawi, O.; Whelan, J.; Almehmadi, A.; El-Khatib, K. Machine Learning-Based Intrusion Detection System for Controller Area Networks. In Proceedings of the 10th ACM Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications, Miami, FL, USA, 16–20 November 2020; pp. 41–47. [Google Scholar]
- Goncalves, F.; Macedo, J.; Santos, A. Intelligent Hierarchical Intrusion Detection System for VANETs. In Proceedings of the 2021 13th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Brno, Czech Republic, 25–27 October 2021; pp. 50–59. [Google Scholar]
- Kosmanos, D.; Pappas, A.; Aparicio-Navarro, F.J.; Maglaras, L.; Janicke, H.; Boiten, E.; Argyriou, A. Intrusion Detection System for Platooning Connected Autonomous Vehicles. In Proceedings of the 2019 4th South-East Europe Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM), Piraeus, Greece, 20–22 September 2019; pp. 1–9. [Google Scholar]
- Sousa, B.; Magaia, N.; Silva, S. An Intelligent Intrusion Detection System for 5G-Enabled Internet of Vehicles. Electronics 2023, 12, 1757. [Google Scholar] [CrossRef]
- Sharma, A.; Jaekel, A. Machine Learning Based Misbehaviour Detection in VANET Using Consecutive BSM Approach. IEEE Open J. Veh. Technol. 2021, 3, 1–14. [Google Scholar] [CrossRef]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion Detection System Based on the Analysis of Time Intervals of CAN Messages for In-Vehicle Network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar] [CrossRef]
- Marchetti, M.; Stabili, D. Anomaly Detection of CAN Bus Messages through Analysis of ID Sequences. In Proceedings of the 2017 IEEE Intelligent Vehicles Symposium (IV), Redondo Beach, CA, USA, 11–14 June 2017; pp. 1577–1583. [Google Scholar] [CrossRef]
- Stabili, D.; Marchetti, M.; Colajanni, M. Detecting Attacks to Internal Vehicle Networks through Hamming Distance. In Proceedings of the 2017 AEIT International Annual Conference, Cagliari, Italy, 20–22 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Narayanan, S.N.; Mittal, S.; Joshi, A. Using Data Analytics to Detect Anomalous States in Vehicles. arXiv 2015, arXiv:1512.08048. [Google Scholar] [CrossRef]
- Avatefipour, O. Physical-Fingerprinting of Electronic Control Unit (ECU) Based on Machine Learning Algorithm for In-Vehicle Network Communication Protocol “CAN-BUS”. Master’s Thesis, University of Michigan-Dearborn, Dearborn, MI, USA, 2017. Available online: https://hdl.handle.net/2027.42/140731 (accessed on 14 April 2025).
- Anzer, A.; Elhadef, M. A Multilayer Perceptron-Based Distributed Intrusion Detection System for Internet of Vehicles. In Proceedings of the 2018 IEEE 4th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 18–20 October 2018; pp. 438–445. [Google Scholar]
- Kang, M.J.; Kang, J.W. Intrusion Detection System Using Deep Neural Network for In-Vehicle Network Security. PLoS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef] [PubMed]
- Xun, Y.; Zhao, Y.; Liu, J. VehicleEIDS: A Novel External Intrusion Detection System Based on Vehicle Voltage Signals. IEEE Internet Things J. 2021, 9, 2124–2133. [Google Scholar] [CrossRef]
- Zhang, L.; Shi, L.; Kaja, N.; Ma, D. A two-stage deep learning approach for CAN intrusion detection. In Proceedings of the Ground Vehicle Systems Engineering and Technology Symposium (GVSETS), Novi, MI, USA, 7–9 August 2018; pp. 1–11. [Google Scholar]
- Vitalkar, R.S.; Thorat, S.S. A Review on Intrusion Detection System in Vehicular Ad Hoc Network Using Deep Learning Method. Int. J. Res. Appl. Sci. Eng. Technol. 2020, 8, 1591–1595. [Google Scholar] [CrossRef]
- Peng, R.; Li, W.; Yang, T.; Huafeng, K. An Internet of Vehicles Intrusion Detection System Based on a Convolutional Neural Network. In Proceedings of the 2019 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Xiamen, China, 16–18 December 2019; pp. 1595–1599. [Google Scholar]
- Desta, A.K.; Ohira, S.; Arai, I.; Fujikawa, K. Rec-CNN: In-Vehicle Networks Intrusion Detection Using Convolutional Neural Networks Trained on Recurrence Plots. Veh. Commun. 2022, 35, 100470. [Google Scholar] [CrossRef]
- Nie, L.; Ning, Z.; Wang, X.; Hu, X.; Cheng, J.; Li, Y. Data-Driven Intrusion Detection for Intelligent Internet of Vehicles: A Deep Convolutional Neural Network-Based Method. IEEE Trans. Netw. Sci. Eng. 2020, 7, 2219–2230. [Google Scholar] [CrossRef]
- Ashraf, J.; Bakhshi, A.D.; Moustafa, N.; Khurshid, H.; Javed, A.; Beheshti, A. Novel Deep Learning-Enabled LSTM Autoencoder Architecture for Discovering Anomalous Events from Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4507–4518. [Google Scholar] [CrossRef]
- Agrawal, K.; Alladi, T.; Agrawal, A.; Chamola, V.; Benslimane, A. NovelADS: A Novel Anomaly Detection System for Intra-Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 22596–22606. [Google Scholar] [CrossRef]
- Khan, I.A.; Moustafa, N.; Pi, D.; Haider, W.; Li, B.; Jolfaei, A. An Enhanced Multi-Stage Deep Learning Framework for Detecting Malicious Activities from Autonomous Vehicles. IEEE Trans. Intell. Transp. Syst. 2022, 23, 25469–25478. [Google Scholar] [CrossRef]
- Zeng, Y.; Qiu, M.; Zhu, D.; Xue, Z.; Xiong, J.; Liu, M. DeepVCM: A Deep Learning Based Intrusion Detection Method in VANET. In Proceedings of the 2019 IEEE 5th Intl Conference on Big Data Security on Cloud (BigDataSecurity), High Performance and Smart Computing (HPSC), and Intelligent Data and Security (IDS), Washington, DC, USA, 27–29 May 2019; pp. 288–293. [Google Scholar]
- Alladi, T.; Kohli, V.; Chamola, V.; Yu, F.R.; Guizani, M. Artificial Intelligence (AI)-Empowered Intrusion Detection Architecture for the Internet of Vehicles. IEEE Wirel. Commun. 2021, 28, 144–149. [Google Scholar] [CrossRef]
- Wang, C.; Zhao, Z.; Gong, L.; Zhu, L.; Liu, Z.; Cheng, X. A distributed anomaly detection system for in-vehicle network using HTM. IEEE Access 2018, 6, 9091–9098. [Google Scholar] [CrossRef]
- Loukas, G.; Vuong, T.; Heartfield, R.; Sakellari, G.; Yoon, Y.; Gan, D. Cloud-based cyber-physical intrusion detection for vehicles using deep learning. IEEE Access 2017, 6, 3491–3508. [Google Scholar] [CrossRef]
- Banh, L.; Strobel, G. Generative Artificial Intelligence. Electron. Mark. 2023, 33, 63. [Google Scholar] [CrossRef]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative Adversarial Nets. Adv. Neural Inf. Process. Syst. 2014, 27, 1–9. [Google Scholar]
- Salehi, P.; Chalechale, A.; Taghizadeh, M. Generative Adversarial Networks (GANs): An Overview of Theoretical Model, Evaluation Metrics, and Recent Developments. arXiv 2020, arXiv:2005.13178. [Google Scholar] [CrossRef]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, L.U.; Polosukhin, I. Attention Is All You Need. In Advances in Neural Information Processing Systems; Guyon, I., Luxburg, U.V., Bengio, S., Wallach, H., Fergus, R., Vishwanathan, S., Garnett, R., Eds.; Curran Associates, Inc.: Red Hook, NY, USA, 2017; Volume 30. [Google Scholar]
- Kingma, D.P.; Welling, M. Auto-Encoding Variational Bayes. arXiv 2013, arXiv:1312.6114. [Google Scholar]
- Asperti, A.; Evangelista, D.; Loli Piccolomini, E. A Survey on Variational Autoencoders from a Green AI Perspective. SN Comput. Sci. 2021, 2, 301. [Google Scholar] [CrossRef]
- Sohl-Dickstein, J.; Weiss, E.; Maheswaranathan, N.; Ganguli, S. Deep Unsupervised Learning Using Nonequilibrium Thermodynamics. In Proceedings of the International Conference on Machine Learning (ICML), Lille, France, 7–9 July 2015; pp. 2256–2265. [Google Scholar]
- Xie, Y.; Yu, J.; Ranneby, B. A General Autoregressive Model with Markov Switching: Estimation and Consistency. Math. Methods Stat. 2008, 17, 228–240. [Google Scholar] [CrossRef]
- Khalil, A.; Farman, H.; Nasralla, M.M.; Jan, B.; Ahmad, J. Artificial Intelligence-Based Intrusion Detection System for V2V Communication in Vehicular Adhoc Networks. Ain Shams Eng. J. 2024, 15, 102616. [Google Scholar] [CrossRef]
- Poongodi, M.; Hamdi, M. Intrusion Detection System Using Distributed Multilevel Discriminator in GAN for IoT System. Trans. Emerg. Telecommun. Technol. 2023, 34, e4815. [Google Scholar] [CrossRef]
- Shu, J.; Zhou, L.; Zhang, W.; Du, X.; Guizani, M. Collaborative Intrusion Detection for VANETs: A Deep Learning-Based Distributed SDN Approach. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4519–4530. [Google Scholar] [CrossRef]
- Chen, X.; Xiao, K.; Luo, L.; Li, Y.; Chen, L. GAN-IVDS: An Intrusion Detection System for Intelligent Connected Vehicles Based on Generative Adversarial Networks. In Proceedings of the 2023 8th International Conference on Data Science in Cyberspace (DSC), Hefei, China, 18–20 August 2023; pp. 237–244. [Google Scholar]
- Qiu, Y.; Misu, T.; Busso, C. Unsupervised Scalable Multimodal Driving Anomaly Detection. IEEE Trans. Intell. Veh. 2022, 8, 3154–3165. [Google Scholar] [CrossRef]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN Based Intrusion Detection System for In-Vehicle Network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Wang, X.; Xu, Y.; Xu, Y.; Wang, Z.; Wu, Y. Intrusion Detection System for In-Vehicle CAN-FD Bus ID Based on GAN Model. IEEE Access 2024, 12, 82402–82412. [Google Scholar] [CrossRef]
- Xie, G.; Yang, L.T.; Yang, Y.; Luo, H.; Li, R.; Alazab, M. Threat Analysis for Automotive CAN Networks: A GAN Model-Based Intrusion Detection Technique. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4467–4477. [Google Scholar] [CrossRef]
- Zhao, Q.; Chen, M.; Gu, Z.; Luan, S.; Zeng, H.; Chakrabory, S. CAN Bus Intrusion Detection Based on Auxiliary Classifier GAN and Out-of-Distribution Detection. ACM Trans. Embed. Comput. Syst. 2022, 21, 45. [Google Scholar] [CrossRef]
- Nguyen, T.P.; Nam, H.; Kim, D. Transformer-Based Attention Network for In-Vehicle Intrusion Detection. IEEE Access 2023, 11, 55389–55403. [Google Scholar] [CrossRef]
- Li, M.; Han, D.; Li, D.; Liu, H.; Chang, C.C. MFVT: An Anomaly Traffic Detection Method Merging Feature Fusion Network and Vision Transformer Architecture. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 39. [Google Scholar] [CrossRef]
- Cobilean, V.; Mavikumbure, H.S.; Wickramasinghe, C.S.; Varghese, B.J.; Pennington, T.; Manic, M. Anomaly Detection for In-Vehicle Communication Using Transformers. In Proceedings of the IECON 2023—49th Annual Conference of the IEEE Industrial Electronics Society, Singapore, 16–19 October 2023; pp. 1–6. [Google Scholar]
- Lai, Q.; Xiong, C.; Chen, J.; Wang, W.; Chen, J.; Gadekallu, T.R.; Hu, X. Improved Transformer-Based Privacy-Preserving Architecture for Intrusion Detection in Secure V2X Communications. IEEE Trans. Consum. Electron. 2023, 70, 1810–1820. [Google Scholar] [CrossRef]
- Liu, Z.; Xu, H.; Kuang, Y.; Li, F. SVMDFormer: A Semi-Supervised Vehicular Misbehavior Detection Framework Based on Transformer in IoV. In Proceedings of the 2023 IEEE 43rd International Conference on Distributed Computing Systems (ICDCS), Hong Kong, China, 18–21 July 2023; pp. 887–897. [Google Scholar]
- Hamhoum, W.; Cherkaoui, S. MistralBSM: Leveraging Mistral-7B for Vehicular Networks Misbehavior Detection. arXiv 2024, arXiv:2407.18462. [Google Scholar] [CrossRef]
- Li, X.; Fu, H. SecureBERT and LLAMA 2 Empowered Control Area Network Intrusion Detection and Classification. arXiv 2023, arXiv:2311.12074. [Google Scholar] [CrossRef]
- Nwafor, E.; Olufowobi, H. CanBERT: A Language-Based Intrusion Detection Model for In-Vehicle Networks. In Proceedings of the 2022 21st IEEE International Conference on Machine Learning and Applications (ICMLA), Nassau, Bahamas, 12–14 December 2022; pp. 294–299. [Google Scholar]
- Aldossary, S.M. Smart Vehicles Networks: BERT Self-Attention Mechanisms for Cyber-Physical System Security. Int. J. Syst. Assur. Eng. Manag. 2023, 1–9. [Google Scholar] [CrossRef]
- Tang, W.; Li, D.; Fan, W.; Liu, T.; Chen, M.; Dib, O. An Intrusion Detection System Empowered by Deep Learning Algorithms. In Proceedings of the 2023 IEEE International Conference on Dependable, Autonomic and Secure Computing, Pervasive Intelligence and Computing, Cloud and Big Data Computing, Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Abu Dhabi, United Arab Emirates, 14–17 November 2023; pp. 1137–1142. [Google Scholar]
- Alkhatib, N.; Mushtaq, M.; Ghauch, H.; Danger, J.L. CAN-BERT Do It? Controller Area Network Intrusion Detection System Based on BERT Language Model. In Proceedings of the 2022 IEEE/ACS 19th International Conference on Computer Systems and Applications (AICCSA), Abu Dhabi, United Arab Emirates, 5–8 December 2022; pp. 1–8. [Google Scholar]
- Monshizadeh, M.; Khatri, V.; Gamdou, M.; Kantola, R.; Yan, Z. Improving Data Generalization with Variational Autoencoders for Network Traffic Anomaly Detection. IEEE Access 2021, 9, 56893–56907. [Google Scholar] [CrossRef]
- Aslam, N.; Kolekar, M.H. A-VAE: Attention-Based Variational Autoencoder for Traffic Video Anomaly Detection. In Proceedings of the 2023 IEEE 8th International Conference for Convergence in Technology (I2CT), Lonavla, India, 7–9 April 2023; pp. 1–7. [Google Scholar]
- Wei, Y.; Jang-Jaccard, J.; Sabrina, F.; Singh, A.; Xu, W.; Camtepe, S. AE-MLP: A Hybrid Deep Learning Approach for DDoS Detection and Classification. IEEE Access 2021, 9, 146810–146821. [Google Scholar] [CrossRef]
- Kim, T.; Kim, J.; You, I. An Anomaly Detection Method Based on Multiple LSTM-Autoencoder Models for In-Vehicle Network. Electronics 2023, 12, 3543. [Google Scholar] [CrossRef]
- Hoang, T.N.; Kim, D. Detecting In-Vehicle Intrusion via Semi-Supervised Learning-Based Convolutional Adversarial Autoencoders. Veh. Commun. 2022, 38, 100520. [Google Scholar] [CrossRef]
- Wei, P.; Wang, B.; Dai, X.; Li, L.; He, F. A Novel Intrusion Detection Model for the CAN Bus Packet of In-Vehicle Network Based on Attention Mechanism and Autoencoder. Digit. Commun. Netw. 2023, 9, 14–21. [Google Scholar] [CrossRef]
- ISO/SAE 21434:2021; Road vehicles—Cybersecurity engineering. International Organization for Standardization: Geneva, Switzerland, 2020.



| Survey | Time Span | ML-Based IDS | DL-Based IDS | Generative AI-Based IDS | Network Focus | ||
|---|---|---|---|---|---|---|---|
| GANs-IDS | Transformer-IDS | VAEs-IDS | |||||
| Man et al. [1] | --- | ✓ | Limited | x | x | x | IVNs + V2X |
| Almehdhar et al. [2] | 2017–2024 | ✓ | ✓ | x | x | x | IVNs |
| Rajapaksha et al. [3] | 2016–2022 | ✓ | ✓ | x | x | x | IVNs |
| This Survey | 2015–2024 | ✓ | ✓ | ✓ | ✓ | ✓ | IVNs + V2X |
| Existing Architectures | Layers | Layers Name |
|---|---|---|
| 2011—Liu Nanjie [5] | Three | 1—Client, 2—Connection, 3—Cloud |
| 2016—Kaiwartya et al. [6] | Five | 1—Perception, 2—Coordination, 3—Artificial intelligence, 4—Application, 5—Business |
| 2017—Contreras-Castillo et al. [7] | Seven | 1—User interaction layer, 2—Data acquisition layer, 3—Data filtering and preprocessing layer, 4—Communication layer, 5—Control and management layer, 6—Business layer, 7—Security layer |
| 2019—KaiLiu et al. [8] | Four | 1—Cloud computing, 2—SDN control, 3—Fog computing, 4—Infrastructure |
| 2020—Ji et al. [9] | Four | 1—Cloud platform, 2—Edge, 3—Data acquisition, 4—Security authentication |
| 2022—Gao et al. [10] | Three | 1—Clients, 2—Endorsement and commitment peers, 3—Ordering services |
| 2023—Wang et al. [11] | Four | 1—Terminal, 2—Network, 3—Platform, 4—Service |
| Attack | Attack Type | Affected Security Component |
|---|---|---|
| Sybil attack | Active | Authentication, Availability |
| Masquerading attack | Active | Authentication, Confidentiality |
| Man-in-the-Middle attack | Active, Passive | Availability, Confidentiality |
| Replay attack | Passive | Availability |
| Cookie Theft attack | Active | Authentication, Confidentiality |
| Message Injection attack | Active | Availability |
| Message Manipulation attack | Active | Availability |
| Channel Interference attack | Active, Passive | Availability |
| Denial of Service (DoS) attack | Active | Availability |
| Distributed DoS attack | Active | Availability |
| Eavesdropping attack | Passive | Confidentiality |
| Message Holding attack | Active | Availability |
| False Information Flow attack | Active | Availability |
| Channel Hindrance attack | Active | Availability |
| Malware attack | Active | Availability |
| Physical Vehicle damage | Active | Availability |
| Fuzzy attack | Active | Availability |
| Guessing attacks | Active | Authentication |
| Session Linking attack | Active | Authentication, Confidentiality |
| Black-hole attack | Active | Availability |
| Forgery attack | Active | Authentication |
| Wormhole attack | Active | Availability |
| GPS Deception attack | Active | Confidentiality, Availability |
| Reference | ML Model | Detection Target | Strengths and Limitations |
|---|---|---|---|
| [28] | KNN, SVM | Classification of intrusion events | ✓Fast, effective for structured data ✗Limited by static datasets |
| [29] | RF, DT, ET, XGBoost | Multiple attack types | ✓High accuracy ✗High computational time |
| [30] | Decision Tree | Network attack detection for vehicles | ✓Integration of network and physical features ✗Scalability and flexibility limitations |
| [31] | DT, RF, KNN | DDoS attacks (UDP-Lag, SYN Flood) | ✓High accuracy, effective feature selection ✗Scalability and robustness concerns |
| [32] | SVM, KNN, C4.5 | DDoS attacks | ✓Combines multiple classifiers ✗Limited by high computational overhead |
| [33] | RF, KNN, LightGBM, XGBoost, AdaBoost, SVM, LDA | DDoS attacks | ✓High accuracy ✗Dataset-dependent, real-time constraints |
| [34] | Multiple ML algorithms | Injection attacks on CAN bus | ✓Good accuracy and low false alarm rate ✗Missing false negative metrics, high external deployment cost |
| [35] | Various ML methods (hierarchical) | General vehicular attacks | ✓Flexible multi-level detection ✗Lack of performance metrics |
| [36] | RF, KNN, OCSVM | Spoofing and Jamming attacks | ✓Precise attack detection ✗Lacks FPR/FNR and latency metrics |
| [37] | DT, RF | Flooding attacks in 5G vehicular networks | ✓Excellent performance (F1 Score of 1) ✗Narrow attack scope |
| [38] | KNN, RF, DT, Naïve Bayes | Position falsification in VANETs | ✓High accuracy, RSU-based detection ✗Needs dense RSU coverage |
| [39] | Timing anomaly detection | Injection attacks | ✓0% FPR, lightweight ✗Not robust to slow attacks |
| [40] | Sequence-based anomaly detection | Malicious CAN message injections | ✓Low memory and computational footprint, high detection accuracy ✗Limited replay attack detection |
| [41] | Hamming distance on payloads | Fuzzing, Replay attacks | ✓Lightweight, good Fuzzing detection ✗Low detection rate for replay attacks |
| [42] | Hidden Markov Model (HMM) | Anomalous vehicle states | ✓Real deployment. ✗Threshold-dependent |
| [43] | ML-based physical-layer fingerprinting | ECU and channel identification | ✓High accuracy using real signal data ✗Depends on hardware-level variations |
| DL Model | Reference | Detection Target | Strengths and Limitations |
|---|---|---|---|
| MLP | [44] | DoS attack, U2R attack, R2L attack, Probe attack | ✓High accuracy with simple design ✗Needs deep architecture for better performance |
| DNN | [45] | General malicious packet injection attacks | ✓High accuracy and real-time detection ✗Time-consuming training |
| [46] | CAN bus signal anomalies | ✓High detection accuracy, robust to external intrusion attacks ✗Cannot detect attacks originating from internal ECUs | |
| [47] | CAN malicious attacks | ✓Tested on real data from 3 vehicles ✗Complexity in embedded setups | |
| DBN | [48] | VANET intrusions | ✓Good for classification, mitigates overfitting ✗Rarely used independently, slower |
| CNN | [49] | Real-time intrusion detection at vehicle terminals | ✓Lightweight, real-time detection ✗Limited handling of temporal data |
| [50] | CAN bus intrusion | ✓Effective online/offline detection ✗Requires external CAN devices | |
| DCNN | [51] | DDoS attack | ✓High accuracy, good for RSU traffic ✗Latency not addressed |
| LSTM | [52] | Fuzzy, RPM, DOS, GEAR attacks | ✓Good for sequential data, multiple intrusion types ✗Resource-intensive |
| [53] | CAN bus attacks | ✓High accuracy ✗High latency (128 ms), large overhead | |
| Bi-LSTM + DNN + Bloom Filter | [54] | Internal and external IoV attacks | ✓Short training, low detection latency ✗Lacks FPR and FNR metrics |
| CNN, LSTM | [55] | Wormhole, Sybil, DoS, Infiltrating Transfer, DDoS, Black-hole, Brute Force attacks | ✓Efficient, high detection performance ✗Model complexity |
| CNN-LSTM, MLP, LSTM, CNN | [56] | Disruptive, Replay, DoS, Sybil, Hybrid | ✓High accuracy, low latency, MEC-friendly ✗Struggles with similar attack types |
| HTM | [57] | CAN anomaly detection | ✓Outperforms RNN and HMM in precision and recall ✗Relies on synthetic attack data |
| RNN-LSTM with cloud offloading | [58] | Cyberattacks | ✓Outperforms traditional classifiers in accuracy ✗Limited to robotic testbed |
| Generative Model | Core Mechanism | Key Strengths |
|---|---|---|
| GANs | Involves adversarial training between two networks: a generator (produces synthetic data) and a discriminator (evaluates authenticity). | —High-quality data synthesis —Learns complex data distributions |
| Transformers | Utilizes self-attention mechanisms to process all elements of an input sequence in parallel, capturing long-range dependencies efficiently. | —Handles long-range dependencies —Scalable and parallelizable —Pretrained on large data |
| VAEs | Learns a probabilistic latent representation by encoding and decoding input data, optimizing a balance between reconstruction and generalization. | —Probabilistic reasoning —Low reconstruction error alerts —Good latent representations |
| GDMs | Learns to reverse a structured noise process by progressively denoising the corrupted input, based on diffusion and generative modeling. | —High sample quality —Robust to noise —Good uncertainty estimation |
| ARMs | Predicts future values in a sequence based on past observations; can be extended with regime-switching mechanisms. | —Effective in time series —Adapts to changes over time —Interpretable |
| GAI Technique | Ref | Main Approach | Detection Target | Network Focus | Performance Summary | Strengths and Limitations |
|---|---|---|---|---|---|---|
| GANs | [67] | BiGAN (Encoder–Discriminator) | Known and unknown attacks | V2V | Acc: 92.15% F1: 0.961 Latency: 83.71 s FPR: 7.3 FNR: 0.6 | ✓Robust and strong performance ✗High computational resources |
| [68] | Distributed GANs + Federated Learning | Malicious traffic behavior | V2X | Acc: 98.92% F1: 0.77 | ✓Scalable and decentralized ✗Communication and synchronization complexity | |
| [69] | Collaborative Multi-Discriminator GAN (SDN) | Intrusion detection | V2X | --- | ✓Collaborative framework, validated on datasets ✗No numerical evaluation results | |
| [70] | GAN-based Anomaly Detection | Traffic anomalies | V2X | Acc: 94.9% | ✓Addresses traffic imbalance ✗Trained only on normal data | |
| [71] | Multi-modal GANs | Driving anomaly detection | V2X | --- | ✓High detection accuracy ✗Poor scalability for new modalities | |
| [72] | GAN-based IDS | CAN messages | IVN | Acc: 98% Latency: 0.18 s | ✓High accuracy ✗Limited to known CAN formats and lacks generalization | |
| [73] | Dual-discriminator GAN with ID encoding | CAN-FD bus | IVN | Acc: 99.93% Latency: 0.15 ms per message | ✓High accuracy (99.93%) ✗Specialized for ID-based detection only | |
| [74] | Combining CAN communication matrix with image-based GANs | Tampering detection | IVN | --- | ✓High precision and accuracy ✗Requires complex preprocessing | |
| [75] | ACGAN with two-stage classification | Attacks classification | IVN | F1: 99.23 Latency: 0.203 ms (multicore) 0.538 ms (single-core) FPR: 0.36 FNR: 0.96 | ✓High accuracy and low computational cost ✗Design complexity | |
| Transformers | [76] | Transformer-based attention network + transfer learning | Multi-class attack detection | IVN | Acc: 1-ER = 99.94% F1: 1.00 (single-message input) Latency: 11.6 ms/batch | ✓Good classification, adaptable ✗CAN-specific, scalability limits |
| [77] | MFVT | Anomaly traffic detection | V2X | Acc: 99.96% (IDS 2012) 99.99% (IDS 2017) F1: 0.9995 (IDS 2012) 1.00 (IDS 2017) FPR: 0.000175 (IDS 2012) | ✓Captures diverse input aspects ✗Limited in long-range dependencies | |
| [78] | CAN-Former (self-supervised) | Anomalies detection | IVN | Acc: 99.75% (Kia Soul), 99.48% (Chevrolet Spark), 98.35% (Sonata) F1: 0.9873 (Kia Soul), 0.9892 (Chevrolet Spark), 0.9702 (Sonata) | ✓No handcrafted features ✗Evaluation limited to specific datasets | |
| [79] | FL-EC with FSFormer | Intrusion detection | V2X | --- | ✓High accuracy, improves privacy ✗Computational edge overhead | |
| [80] | Fine-tuned encoder- based Transformer | Misbehavior via BSM sequences | V2X | Acc: 99.66% F1: 99.66% FPR: 0.34 | ✓Good detection, adaptable ✗Computational challenges | |
| [81] | LLM (Mistral-7B) | Misbehavior detection | V2X | Acc: 98% F1: 0.98 | ✓High detection accuracy and efficient use of resources ✗Resources constraints, privacy issues | |
| [82] | SecureBERT, BERT, LLAMA-2 | CAN intrusion detection | IVN | Acc: 99.99% F1: 0.999993 Latency: 14 messages/s FAR: 3.1 × 10−6 | ✓Effective, better with large models ✗High computational cost | |
| [83] | CANBERT | Multiple CAN attacks | IVN | Acc: 100% F1: 1.00 | ✓High precision and accuracy ✗High computational requirements | |
| [84] | BERT with self-attention | Harmful texts detection | V2X | Acc: 96.65%. | ✓High accuracy (96.65%) ✗Text-only focus, needs labeled data, and high resource demands | |
| [85] | IoV-BERT-IDS | Network intrusion detection | IVN + V2X | --- | ✓Improved detection accuracy ✗Requires heavy fine-tuning | |
| [86] | BERT + masked training | CAN message injection attacks | IVN | F1: 0.81 to 0.99 Latency: 0.8 to 3.8 ms Model size: 20–70 MB ParametersL: ~2.9 M–3.2 M | ✓Outperforms PCA/AEs ✗Focused on CAN-ID sequences | |
| VAEs | [87] | CVAE + RF | Traffic anomaly detection | Network Traffic | F1: 0.85 to 0.99 Latency: 82.72 s (MAWILab-2018) 46.37 s (ISCX-2012) | ✓Improved feature learning, good accuracy ✗Varies across datasets and attack types |
| [88] | A-VAE + CNN + Bi-LSTM + Attention | Traffic video anomaly detection | V2X | EER: 27% (Crossroad1), 31% (Pedestrian) Latency: 0.0149 sec/frame on Crossroad 0.0192 sec/frame on Pedestrian | ✓High real-time accuracy, unsupervised learning ✗Needs diverse training data | |
| AEs | [89] | AE + MLP | DDoS attacks | V2X | Acc: 98.34% F1: 98.18% | ✓High accuracy and F1 score ✗Limited to DDoS |
| [90] | Multiple LSTM-AEs | CAN bus anomalies | IVN | Acc: 97% F1: 0.98 Latency: 0.5 ms FPR: 0.01 | ✓Good accuracy with dynamic data ✗Limited to CAN protocol | |
| [91] | Conv-AE + GAN (semi-supervised) | General intrusions | IVN | F1: 99.84% Latency: 0.63 ms (GPU), 0.69 ms (CPU) | ✓Strong detection accuracy ✗High training complexity | |
| [92] | Denoising AE + Attention Mechanism | Real-time anomalies | IVN | --- | ✓Robust and generalizable ✗Compared only to traditional ML methods |
| Criteria | GANs | Transformers | VAEs |
|---|---|---|---|
| Real-Time Latency | ✗ Poor (slow training and inference) | ✓ Good (fast inference with attention) | ✓ Good (fast reconstruction-based scoring) |
| Robustness Under Network Variability | ✗ Sensitive to noise and imbalance | ✓ High (context-aware sequence modeling) | ✓ Moderate (probabilistic generalization) |
| Hardware Compatibility | ✗ Low (GPU required) | △ Moderate (requires optimization) | ✓ High (lightweight and deployable) |
| Memory and Computation Constraints | ✗ High (dual models, unstable training) | △ Moderate–High (manageable with pruning) | ✓ Low (suitable for edge devices) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mahmoudi, I.; Boubiche, D.E.; Athmani, S.; Toral-Cruz, H.; Chan-Puc, F.I. Toward Generative AI-Based Intrusion Detection Systems for the Internet of Vehicles (IoV). Future Internet 2025, 17, 310. https://doi.org/10.3390/fi17070310
Mahmoudi I, Boubiche DE, Athmani S, Toral-Cruz H, Chan-Puc FI. Toward Generative AI-Based Intrusion Detection Systems for the Internet of Vehicles (IoV). Future Internet. 2025; 17(7):310. https://doi.org/10.3390/fi17070310
Chicago/Turabian StyleMahmoudi, Isra, Djallel Eddine Boubiche, Samir Athmani, Homero Toral-Cruz, and Freddy I. Chan-Puc. 2025. "Toward Generative AI-Based Intrusion Detection Systems for the Internet of Vehicles (IoV)" Future Internet 17, no. 7: 310. https://doi.org/10.3390/fi17070310
APA StyleMahmoudi, I., Boubiche, D. E., Athmani, S., Toral-Cruz, H., & Chan-Puc, F. I. (2025). Toward Generative AI-Based Intrusion Detection Systems for the Internet of Vehicles (IoV). Future Internet, 17(7), 310. https://doi.org/10.3390/fi17070310






