Abstract
Smart home devices and home automation systems, which control features such as lights, blinds, heaters, door locks, cameras, and speakers, have become increasingly popular and can be found in homes worldwide. Central to these systems are smart home hubs, which serve as the primary control units, allowing users to manage connected devices from anywhere in the world. While this feature is convenient, it also makes smart home hubs attractive targets for cyberattacks. Unfortunately, the average user lacks substantial cybersecurity knowledge, making the security of these systems crucial. This is particularly important as smart home systems are expected to safeguard users’ privacy and security within their homes. This paper synthesizes eight prevalent cybersecurity challenges associated with smart home hubs through a systematic literature review. The review process involved identifying relevant keywords, searching, and screening 713 papers in multiple rounds to arrive at a final selection of 16 papers, which were then summarized and synthesized. This process included research from Scopus published between January 2019 and November 2024 and excluded papers on prototypes or individual features. The study is limited by scarce academic sources on open-source smart home hubs, strict selection criteria, rapid technological changes, and some subjectivity in study inclusion. The security of extensible smart home hubs is a complex and evolving issue. This review provides a foundation for understanding the key challenges and potential solutions, which is useful for future research and development to secure this increasingly important part of our everyday homes.
1. Introduction
The smart home is defined by Corno and Mannella as “a home equipped with lighting, heating and electronic devices that can be controlled remotely by smartphone or computer” [1]. Smart home devices, like light bulbs, plugs, blinds, cameras, robot vacuums, door locks, heaters, and speakers, have been popular for a long time and are continuously growing in popularity. Statista [2] has observed an increase in the number of smart home users for nine consecutive years and has predicted that the number of smart home users will more than double between 2023 and 2028, reaching an estimated peak of almost 800 million users worldwide in 2028. Furthermore, a market report from 2025 [3] estimates that the global smart home market will be at USD 199.4 billion this year, with a compound annual growth rate of 8.5% until 2034.
Smart home hubs are central to the smart home because they are the “central control unit of a smart home system” [4]. The smart home hubs act as a single entry point, usually allowing the user to control any connected smart home device anywhere in the world. While this offers great convenience to the user, it also makes smart home hubs a lucrative target for cyberattacks. This means that the security of these systems is essential, especially considering that smart home systems protect the user’s privacy and security in one of the few places where most people expect to have both, in their own homes. Smart home hubs and home automation systems are typically used by tech enthusiasts, homeowners, renters, families, elderly and disabled individuals, and environmentally conscious users to enhance home security, convenience, energy efficiency, and manage household tasks. As Andrade et al. [5] pointed out, the cybersecurity architecture in smart homes does not have the same levels of security as in organizations. This implies that they tend to be even more exposed to attacks like phishing, malware, and fake apps. Even more so, smart homes share much of the same attack surface as common IoT systems, where Lazzaro et al. [6] have shown that replay attacks, dictionary attacks, and TLS interceptions thrive against consumer devices.
Due to the rapid expansion of the smart home market, standardization efforts have been unable to keep up with innovation. This has led to a heterogeneous smart home market, with fragmented ecosystems that do not interoperate well. While there are multiple popular communication standards, like Zigbee, Z-Wave, Wi-Fi/Ethernet, and Bluetooth Low Energy, these have not ensured interoperability and feature uniformity, sometimes even among devices that use the same communication standard. Matter and Thread, two promising new standards, could solve many of these problems; however, the development and adoption of these have been slow. This lack of interoperability has led to the development of several other solutions. One of these is extensible smart home hubs, which provide a uniform platform for the user while supporting each device ecosystem through first- or third-party extensions. This model is used by commercial solutions, like Samsung SmartThings [7] and Athom Homey [8], and open-source solutions, like Home Assistant [9], MagicMirror2 [10], and openHAB [11]. While improving interoperability, the extensible nature of these hubs also changes their security landscape.
The purpose of this study is to provide an overview of the security challenges associated with smart home devices and home automation systems, as well as the general concepts useful for solving these challenges. Our approach has been to investigate the recent academic literature through a systematic literature review and synthesize the results from the most central peer-reviewed publications. Our work has been driven by the following research question: What are the prevalent cybersecurity challenges in extensible smart home hubs as indicated by the academic literature?
2. Materials and Methods
This section outlines the methodology employed in conducting our literature review. According to Aromataris and Pearson [12], such a systematic review, also known as research synthesis, aims to provide a comprehensive, unbiased synthesis of many relevant studies. The primary objective of this review is to synthesize existing research findings, identify prevailing trends, and highlight gaps in the current body of knowledge related to the security of smart home hubs. By systematically analyzing peer-reviewed articles, conference papers, and other scholarly sources, this review aimed to provide a robust foundation for understanding the topic under investigation and identify key security challenges. The review was conducted in accordance with the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) 2020 guidelines [13,14]. The review process adhered to the updated 27-item PRISMA checklist to ensure transparency, rigor, and reproducibility in reporting.
Figure 1 gives an overview of the authors’ literature search and selection process. The search was performed using the Scopus literature database [15]. It was chosen because it is the world’s largest, most comprehensive, and trusted academic database, and provides good search functionality. During the search process, relevant keywords were extracted according to the process depicted in the “Search” section of Figure 1. The first search was constructed using keywords identified by the authors. The result of this initial search was processed to find representative papers on which to perform further keyword extraction. This process was repeated and refined to ensure that the final search parameters covered an acceptable portion of the relevant research.
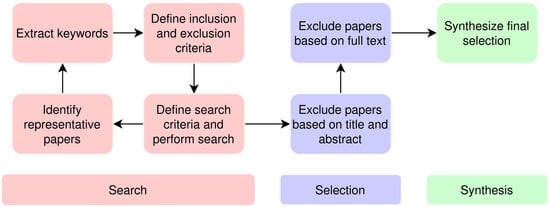
Figure 1.
Research process flow chart.
The keywords used during the search process were divided into primary keywords (Table 1) and secondary keywords (Table 2). The primary keywords include 4 synonyms for “smart home” and 3 synonyms for “hub”, and cover all 12 combinations used to describe extensible smart home hubs and similar systems in research. General keywords were used to ensure that every relevant paper was included, even though this increased the number of search results. In Table 1, the 12 names are grouped by the first and last half of the names, e.g., “smart home …” includes results for “smart home system”, “smart home gateway”, and “smart home”. The secondary keywords narrowed the search to 4 specific research topics related to these systems. Table 2 shows the number of results for each keyword when combined with the primary search.

Table 1.
Primary keywords.

Table 2.
Secondary keywords.
The literature inclusion criteria were defined to include recent works ( year ) written in English. Table 3 documents how the search queries were combined and the number of results for each query refinement. The search combines the inclusion criteria, primary keywords, and secondary keywords. The last query in the search log’s result was the basis of the literature “selection” process depicted in Figure 1. The final round of queries was run in November 2024.

Table 3.
Search queries and results.
The exclusion criteria in Table 4 defined the literature selection strategy. Due to the high number of results (713), the authors performed exclusions in multiple rounds. Ensuring objectivity and minimizing bias in a systematic review can be challenging [16]. Our strategy to maintain rigor and reduce subjectivity was to initially perform a pilot test on a small sample to refine and clarify the inclusion and exclusion criteria. This step involved both the primary and secondary researchers and helped identify ambiguities and biases early on. The agreed-upon criteria were documented in an internal report that the primary researcher used during the overall selection process, meaning no separate review protocol was developed. During the selection rounds, a log was kept to record all decisions made during the review process. During full-text screening, reasons for including and excluding studies were also documented. The secondary researcher reviewed this log and provided an external perspective to the selection. Cases of uncertainty were resolved through discussions.

Table 4.
Exclusion criteria.
The first round excluded studies based on the title alone (leaving 85), the second round excluded studies based on the title and abstract (leaving 33), and the third round excluded studies based on the title, abstract, and full-text. During the third round of screening, articles were removed when they were primarily off-topic (e.g., [17]) or demonstrated a prototype (e.g., [18,19]). The final selection of studies resulted in 16 articles. The flow diagram shown in Figure 2 illustrates the study selection process, including the number of records identified, screened, excluded, and included, along with reasons for exclusions.
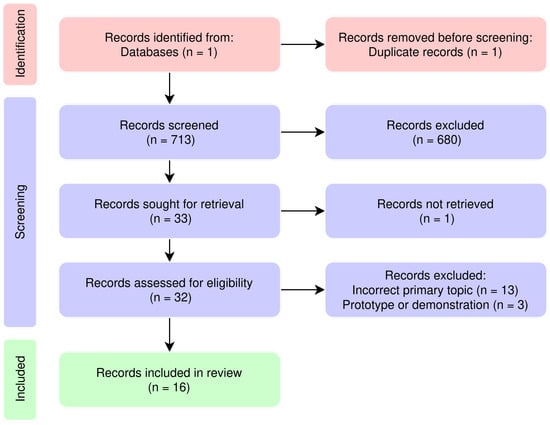
Figure 2.
PRISMA flow diagram.
3. Results
This section presents the study’s findings, derived from the comprehensive literature review. The selected studies are analyzed and summarized to highlight key trends, patterns, and insights. The papers are presented chronologically in the following subsection. The trailing subsection focuses on synthesizing and discussing the key challenges from the literature. These challenges are critical for understanding the current state of research and for guiding future investigations.
3.1. Summary of the Literature
In their 2019 paper [20], Parocha and Macabebe explore the concept of extensible smart home hubs, with a focus on the openHAB smart home system. They begin by explaining the overall architecture of these hubs and the abstraction of specific devices into generic “things”. The paper then describes a reference smart home system setup, which includes a local network of devices, a microcomputer hub, and cloud services integrated through the hub. The authors share their experiences with the added and missing functionalities of openHAB compared to native apps. They also compare the open-source openHAB solution to one of the leading commercial solutions at the time, SmartThings, which Samsung acquired in 2014. Regarding cybersecurity, the paper cites two studies indicating that researchers could manipulate smart home devices controlled by the SmartThings system. At the same time, the open-source openHAB solution only revealed minor API errors. This suggests that openHAB is a safer alternative, although it has a more complicated setup process.
In the same year (2019), Yahyazadeh et al. [21] presented an approach to enforce user expectation policies in appified smart home systems that utilize Trigger-Action Programming. This approach ensures that automations act according to user expectations regarding what can and cannot happen in their smart home environment. The need for this approach arises from the paradigm of unvetted third-party apps running as part of smart home systems, which the authors address through their malicious app-based threat model. Instead of validating actions using static analysis, the authors’ approach inspects requested actions at runtime and either allows or disallows them based on user-provided invariants, such as “I expect the front door to unlock only when vacation mode is off”. They present an openHAB-based implementation of their approach and test it with previously studied problematic automation rules.
In 2020, Yang et al. [22] introduced a blockchain-based perspective on smart home system security, specifically utilizing the advantages of blockchain technology for authentication and permission control. The authors break down the architecture of centralized systems into user, permission, data, and message subsystems, highlighting the disadvantages of a centralized system: account security, admin abuse, and a single point of failure. A system is proposed where accounts are replaced with a blockchain encryption method that avoids account management pitfalls. Further, the system is decentralized without a single device to control the rest, ensuring that the remaining system stays up even when parts of it fail. The authors show how blockchain technology can be used to implement short-term permissions, multi-user permissions, and a control hierarchy.
In 2021, Kanchi and Karlapalem [23] introduced a model for a multi-device and multi-user access control scheme for smart home systems. They highlight the lack of a fine-grained permissions structure in popular smart home systems or the lack of restraint in the default assignments of permissions where fine-grained permissions do exist. The authors categorize common user groups, such as home adults, home children, and guest adults, and discuss their specific needs. They explain the challenge of balancing over-privileging and under-privileging different users. Their proposed solution involves different default levels of privilege, which can be temporarily overridden. For example, a child could be allowed to use the stove for an hour with parental permission. Future work on this model includes implementing and testing it in a smart home system.
Mahadewa et al. [24] scrutinized smart home systems from an integration perspective in 2021, utilizing an approach that extracts application-layer protocols and behaviors from integration implementations to derive a unified abstraction for analysis. They categorize security issues in smart home systems into malicious entity behavior and network-based attacks, where entities can be control points, hubs, or devices. Using their approach, the authors highlight vulnerabilities in the Philips Hue smart lighting system, including discovery request abuse, flawed authentication, lack of authorization, and replay attacks.
In 2021, Mohammad et al. [25] surveyed mechanisms for access control and authorization in smart home systems, presenting an overview and guidelines for future work and open challenges to consider when developing frameworks. The authors introduce different models for access control and the requirements for access control in smart homes: scalability, heterogeneity, reliability, and lightweight. The survey emphasizes how the most common access control and authorization models are ineffective for smart home uses due to their static nature, indicating the need for more advanced models like Attribute-based Access Control (ABAC). Finally, it is argued that the ideal access control framework is centralized and policy-based, making dynamic access decisions. Future challenges for this model include multi-user management and the dynamic nature of smart home systems, where devices are continuously added and removed.
Also in 2021, Setz et al. [26] argued that free open-source home automation systems are good solutions to vendor lock-in in the smart home space and explained the requirements for the systems to succeed: secure APIs, protocol interoperability, constrained device support, and consolidated management of heterogeneous devices. The authors provide an overview of 20 free open-source home automation systems and a deeper analysis of the four most promising ones: Home Assistant, openHAB, ioBroker, and Domoticz, based on challenges identified by related works. Among these are biometric authentication, multi-user authentication, authorization management, and quality control for third-party extensions. Finally, the authors point to the lack of role-based access control as an open issue for future work.
Amraoui and Zouari [27] cover the approaches currently being used to secure smart home systems in their paper from 2022. Some security threats highlighted include direct remote operation, compromised user accounts, user impersonation, and permission abuse in malicious third-party extensions. Conventional security approaches include Intrusion Detection Systems (IDSs), user authentication, access control models, and anomaly detection. The authors conclude that conventional methods are insufficient to secure the operation of smart home systems, and further work is needed on securing app-based and multi-user smart home systems.
Corno and Mannella [1] introduced in 2022 a threat model tailored to extensible smart home hubs designed to be extended using third-party extensions. The purpose of the model is to provide a tool for extension developers. The threat model focuses on how extensions might interfere with confidentiality, integrity, availability, and non-repudiation by accessing and/or changing device states and information not within their scope. The authors validate the threat model by creating sample integrations for the Home Assistant open-source extensible smart home hub that access data outside their scope, including sometimes even data belonging to another integration. The sample integrations were able to demonstrate all but three of the threats in the threat model. The article concludes that there is a need for more detailed examples of each threat and that an improved security architecture is required in the Home Assistant platform API for integrations.
In 2022, Wang et al. [28] analyzed device integration bugs in the Home Assistant home automation platform and applied the lessons to the systems that allow third-party extensions to add device support. These systems have three main concepts: device integration through third-party extensions, a unified automation and monitoring interface, and a device mapping system. The analysis was performed by analyzing roughly 2500 GitHub issues submitted between the release of versions 2020.5 (May 2020) and 2020.12 (December 2020). The impacts of the integration bugs are somewhat similar to the effects of security vulnerabilities, mainly on availability and integrity. The authors summarize their findings into concrete lessons for device integration developers and smart home system designers, highlighting the need for authentication, data validation, and standardization. While the main topic of their paper is feature-oriented, the authors argue that the outcomes are somewhat related to cybersecurity.
Also in 2022, Wang et al. [29] surveyed different styles of smart home systems, including IFTTT, Google Home, Apple HomeKit, Samsung SmartThings, Home Assistant, and openHAB. The survey explains the general architecture of smart home systems and gives examples of security architectures. Further, it covers common attack categories divided into perception layer, communication layer, and application layer attacks. Among the application layer attacks are third-party app backdoors, over-privileged third-party apps, vulnerable automation rules, and fragile cross-platform interactions. Finally, it introduces the security requirements of smart home systems and indicates open research questions for attacks and defenses. These questions include exploiting devices, permissions, authentication, and automation, mitigating data security risks of third-party apps, and ensuring the security of cross-platform data sharing.
In another survey from 2022, Yang and Sun [30] presented the general security of smart home systems seen through the lens of the Internet of Things. The authors introduce a broad new definition of smart home systems and provide background on general challenges in the industry: scale, diversity, fragmentation, resource restrictions, cyber–physical coupling, and complex temporality. Typical attack technologies and models are introduced, as well as typical defense approaches and common architecture types of smart home systems. The authors also stress the importance of soft security (human factors that impact security) in achieving overall security of smart home systems. The focus of this survey is broader than several of the others combined, and it, therefore, also focuses on the general application of software-defined networks, blockchain, and other technologies in smart home systems. Because of this focus, future work suggested includes creating a general secure architecture, finding security solutions that work on low-performance devices, and exploring techniques for overcoming smart home fragmentation issues.
The following year, 2023, Corno and Mannella [4] proposed adjusting and implementing the IETF Manufacturer Usage Description standard on extendable smart home gateways to accelerate the technology adoption and improve the security of smart home gateways. This work uses the threat model published in 2022 by the same authors [1]. IETF MUD is a standardized description provided by manufacturers to indicate the expected uses of the device, allowing other requests to be blocked on the network level. The architecture proposed by the authors uses access requirement information from Home Assistant add-ons to construct a gateway-level MUD file to enforce network traffic rules utilizing a firewall. This work is one of several that use extensible smart home gateways to retrofit smart home devices with new security features.
Also in 2023, Olabode et al. [31] reviewed the harms of the smart home from an interdisciplinary perspective, among which the perspectives of information security, human–computer interaction, social sciences, and law were included. From the information security perspective, the authors write that harms, vulnerabilities, and risks are formalized by standards like CVE, CWE, OWASP IoT TOP 10, STRIDE, and CAPEC. Furthermore, the security analysis of smart homes is divided into three levels: smart home devices, smart home networks, and security protocols. The reviewers also find that the most common limitation in the existing security research is the lack of “real life experiments”. From the human–computer interaction perspective, the most important risks are users being unaware of the cybersecurity and privacy risks of using smart home systems and the lack of authentication in voice-based smart personal assistant systems.
Yuan et al. [32] reviewed in 2023 the security of smart home hubs by identifying and categorizing threats and potential solutions described in recent research. The threats were classified in two ways. One uses their target component, which is divided into platforms, smart devices, and communication channels. The other uses the nature of the security threat, which is divided into programming security, linkage security, authentication, authorization, voice assistant security, and privacy protection. The authors suggest that the root causes of security flaws are heterogeneous components, customized protocols, and a lack of clear responsibility boundaries. Finally, further research into automated vulnerability discovery, security checks, and analysis is recommended to ensure a more powerful security guarantee from smart home systems.
In 2024, Yu et al. [33] proposed a solution for automatically detecting and repairing vulnerabilities in automation frameworks based on Trigger-Action Programming (TAP). Due to its user-friendly nature, TAP automation is used in home automation systems like SmartThings, IFTTT, and Home Assistant. According to the authors, TAP vulnerabilities are introduced because using a simplified programming interface to make automations for complex physical spaces leaves the door open for user error. The TAP vulnerabilities are categorized into Trigger-Inference, Condition-Inference, and Action-Inference and are detected using model-checking and repaired using negated-property reasoning.
3.2. Synthesis of Key Security Challenges
The following key security challenges have been defined based on their prominence in the included literature. Figure 3 provides a visual summary of the challenges in the form of a Euler diagram. The relative size of each bubble indicates how often each challenge appears in the reviewed papers. However, the size does not indicate priority or potential impact. It can also be seen that many challenges are not mutually exclusive, either overlapping or completely encompassing others. We have also tried to show through relative closeness how the challenges are related to a typical smart home user and a smart home developer in terms of responsibility. For instance, the smart home user will have more to do with configuring the local instance, while the smart home developer manages the core hub software or extensions/integrations. As can also be seen, insufficient access control overlaps to some extent with all other challenges. The challenges are described in more detail below. While the challenge descriptions include relevant findings and suggested solutions, their feasibility, performance, and drawbacks are not compared due to a lack of coverage in the included papers.
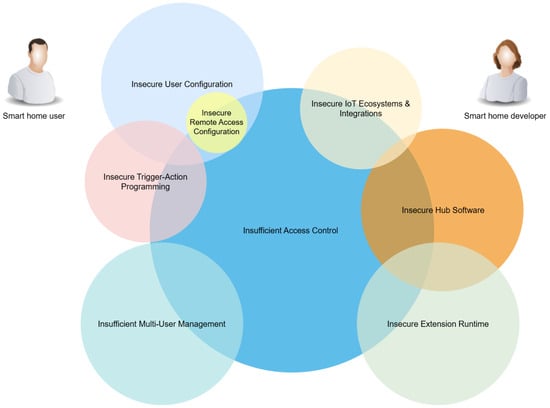
Figure 3.
Euler diagram of the key security challenges.
3.2.1. Insecure Hub Software
It is safe to assume that all software has security vulnerabilities. Although there are many unique security considerations in extensible smart home hubs, it is important to consider that the hubs might also have vulnerabilities associated with software engineering. There are regular headlines on breaches in smart home systems. Parocha and Macabebe [20] refer to studies in which security researchers found small and large vulnerabilities in openHAB and SmartThings, respectively. In addition, multiple other papers [29,30,32] describe problems with software security and design in hubs as a major threat to smart home systems due to a lack of secure coding practices and security mechanisms in the fast-growing APIs designed to accommodate interactions with other systems.
Multiple papers [22,27,30] suggest eliminating the central hub in favor of a decentralized blockchain-based solution. Others [29,30,32] focus on improved secure coding practices without further specification. The improvement of secure coding practices in this context is closely related to mitigating risks included in the categories of OWASP Top 10:2021 [34], which are summarized in Table 5. OWASP Top 10:2021 contains the most common risk groups in web applications and recommendations for mitigating them, and, given its overlap with highlighted issues in extensible smart home hubs, it is reasonable to assume it could also be well applied to smart home hubs.

Table 5.
OWASP Top 10:2021.
3.2.2. Insecure IoT Ecosystems and Integrations
Extensible smart home hubs have a comparatively large attack surface given their support for multiple device ecosystems. All systems, standards, and protocols have underlying weaknesses. One concern is that the underlying weaknesses in the integrated components could have cascading effects on the attack surface of the hub. The potential underlying weaknesses of smart home devices are well described by the risk categories in OWASP IoT Top 10:2018 [35], an IoT-specific version of OWASP Top 10 [34]. The risk categories from OWASP IoT Top 10:2018 are shown in Table 6. Many of the included papers [29,30,32] describe vulnerable devices and underlying protocols as a potential security threat to hubs. Suggested solutions to this challenge include compartmentalizing components [1,20,29,30], enforcing internal access control [23,25,27], analyzing firmware at runtime [30], or using anomaly detection technology to detect and prevent suspicious activity related to device integrations [32].

Table 6.
OWASP IoT Top 10:2018.
Another important concern extends beyond vulnerabilities inherited from underlying protocols, instead focusing on integration bugs with security implications. This is especially relevant considering the added complexity of supporting multiple heterogeneous ecosystems. Mahadewa et al. [24] and Wang et al. [28] explain how assumptions about interfaces, APIs, and trust boundaries can cause invalid or insecure interactions between components. In addition, Corno and Mannella [1] highlight the lack of proper guidelines for hub integration developers, which might add to this challenge. To solve this problem, Mahadewa et al. [24] demonstrated an approach that identifies integration bugs through interface specification extraction in the SmartThings hub.
3.2.3. Insecure User Configuration
One major advantage of extensible smart home hubs, especially open-source ones, is that they allow for extensive customization. This freedom allows the hubs to be customized to fit almost every need, but also allows the user to misconfigure them. Inexperienced users could potentially compromise hub security through poor configuration of passwords, login methods, permissions, network settings, or other settings, some of which are included in OWASP IoT Top 10:2018 [35] as shown in Table 6. Amraoui and Zouari [27] highlight how poor user configuration could lead to malicious or unexpected operations being performed, and Parocha and Macabebe [20] point out the need for openHAB to be configured by computer-savvy users, given its steep learning curve. Additionally, Yang and Sun [30] and Olabode et al. [31] highlight the user’s role, experienced or not, in ensuring security, and how security awareness is lacking in a lot of users.
A common solution to the user configuration problem is restricting the user’s freedom, or hiding critical configuration options behind “Advanced settings”, which can be perceived as bothersome and is not guaranteed to prevent insecure configuration. Other, more complex solutions include detecting insecure configuration through anomaly detection as suggested by Amraoui and Zouari [27] and Wang et al. [29], and educating users on cybersecurity awareness (for instance, through the UI) as explained by Yang and Sun [30] and Olabode et al. [31].
3.2.4. Insecure Remote Access Configuration
Insecure remote access is closely related to insecure user configuration, as problems often emerge when users configure their own remote access method. However, remote access configuration has a massive impact on the hub security and is therefore included as a separate challenge. Yang and Sun [30] describe direct communication with devices as insecure and recommend connecting to devices through a hub for access.
There are many things to consider when exposing a smart home hub to the Internet. Cloud connector services are, therefore, a popular way to enable secure remote access. Most commercial and some open-source actors provide this service. Yang and Sun [30] explain that while cloud connectors (IFTTT, Home Assistant Cloud, openHAB Cloud Connector) provide secure remote access, these options require reliance on a third-party cloud service, which sometimes requires users to pay a subscription fee. Amraoui and Zouari [27] explain how existing Intrusion Detection Systems (IDSs) and authentication methods can be used on the hub level to ensure remote access security.
3.2.5. Insecure Trigger-Action Programming
Insecure Trigger-Action Programming is another challenge closely connected to insecure user configuration. This challenge is specified separately due to the number of references to it in the included literature. Automations, actions, or similar programs based on the TAP paradigm are popular ways to add new functionality to smart home hubs. These programs can have bugs or malicious logic that cause unexpected outcomes. Yahyazadeh et al. [21] highlight how the popular TAP paradigm can lead to conflicting automations and unpredictable results due to its simple user interface and subtle interplay. Amraoui and Zouari [27] and Wang et al. [29] highlight that malicious TAP programs have the potential to threaten hub security through trigger manipulation or malicious actions, due to their stealthy run-in-the-background nature.
One suggested solution to this challenge is a system proposed by Wang et al. [29] for verifying the consistency and security of automation rules and triggers to avoid manipulation. Another potential solution was demonstrated in 2024 by Yu et al. [33], and consists of performing automatic detection and repair of home automation vulnerabilities through negated-property reasoning. Similarly to the user configuration challenge, this challenge could be solved through increased user security awareness.
3.2.6. Insufficient Multi-User Management
Most homes have more than one inhabitant, meaning that smart home hubs must support multiple users. Kanchi and Karlapalem [23] and Mohammad et al. [25] both describe the need for a multi-user, multi-device system that supports users with different access needs to devices. This feature is important to eliminate over- and under-privileging and to ensure users only have the necessary access. In addition to multi-user support, user accounts need to be secure. However, when Setz et al. [26] compared several open-source hubs, they found that only the most popular system had support for account security features like 2FA and WebAuthn. Yang and Sun write that multi-factor mechanisms are widely used in smart home systems [30], which might indicate that commercial solutions offer better login security.
Solutions to this challenge involve creating a user management system utilizing fine-grained access control, where access depends on the user and device as suggested by Kanchi and Karlapalem [23], or where access is determined by evaluating dynamic user and device attributes as proposed by Mohammad et al. [25].
3.2.7. Insecure Extension Runtime
The unique feature of the extensible smart home hub is that it provides an extension runtime. This feature makes the hub infinitely versatile but also significantly impacts hub security requirements. A clear trust boundary between the hub core and its extensions is needed to ensure hub security. Several included papers [21,29,32] highlight the extension runtime as one of the main attack vectors in extensible smart home hubs through either malicious or vulnerable extensions. Yahyazadeh et al. [21] note that this is especially true when extensions are made by third parties, often with less quality control and maintenance. Corno and Mannella [1] specifically found that Home Assistant, the most popular open-source hub, has no firm extension isolation, compromising the confidentiality and integrity of other extensions running on the hub. Furthermore, extensions are free to perform actions without being authenticated, reducing the ability to audit logs and locate malicious extensions.
Some solutions to this challenge already exist in select systems. Wang et al. [29] include Apple Homekit as an example of a smart home system using sandboxing technology to isolate extension runtimes, an approach also suggested by Corno and Mannella [1]. Other suggested improvements to extension runtime security include those by Corno and Mannella [4], proposing to use a modified version of IETF’s MUD standard to label extensions with intended use cases; Yahyazadeh et al. [21], demonstrating a user expectation-based extension manager; Yuan et al. [32], suggesting a behavior-based approach; and Wang et al. [29], proposing third-party verification of extensions like in smartphone app stores. Finally, multiple papers bring up the need for better access control to ensure that extensions only have required access [1,21,23,25,27].
3.2.8. Insufficient Access Control
Access control is essential to protect devices and data in a centralized hub. Yang et al. [22] found that all centralized smart home hubs have fundamental authentication and access control issues. As seen in the section on extensions, many authors [1,21,25,29] highlight that insufficient access control allows extensions in extensible hubs unrestricted access to sensitive information and actions, allowing them to potentially wreak havoc. In addition, Amraoui and Zouari [27], Wang et al. [29], and Yuan et al. [32] describe how an application can abuse coarse-grained access control given to it by the user to read sensitive user data and increase the attack surface of the hub. The solution could be dynamic access control systems since Amraoui and Zouari [27] argue that traditional access control models are ineffective in the smart home setting.
There are multiple approaches to solving this challenge. Regardless of Amraoui and Zouari’s [27] call for non-conventional solutions, Kanchi and Karlapalem [23] and Mohammad et al. [25] propose using the RBAC and ABAC access control models. Among the more specific proposals, Yahyazadeh et al. [21] suggest an extension access control system where predefined user expectations determine data access. Later, Mohammad et al. [25] suggest a fine-grained access control system for data and device control, with the ability to make dynamic automated decisions, followed by Yang and Sun [30], describing a prototype of this context-based access control for the SmartThings hub. Yuan et al. [32] suggest building platforms to have stronger permission structures, which Setz et al. [26] found had already been carried out by one of the less popular open-source smart home hubs when they compared several open-source hubs.
Finally, many authors [22,27,30] have suggested using the inherent security features of blockchain technology to provide decentralized authentication and access control, eliminating most of the need for a centralized hub. This solution, although relevant, is slightly outside the scope of this paper.
4. Discussion
The rapid growth of the smart home market underscores the importance of addressing the security challenges associated with smart home devices and home automation systems. The literature review identified eight prevalent cybersecurity challenges in extensible smart home hubs. This does not exclude other challenges, such as user-friendly interfaces, system heterogeneity and compatibility, performance, and costs, which often have indirect implications on the security of a system.
The identified security challenges have significant implications for the design, implementation, deployment, configuration, and use of smart home systems. Ensuring the security of smart home hubs is crucial for protecting user privacy and maintaining trust in smart home technologies. For each security challenge, we have highlighted recommendations or solutions that end users or developers should take into consideration. However, it is difficult to make a security comparison between open-source and commercial smart home hubs due to the unavailability of studies on the latter. Different homes have different setups and users, with varying interests and competencies. This implies that there is no one-size-fits-all solution, and the risk exposure can vary significantly depending on the means and motivation of the attackers. Our general recommendation is to review all these security challenges and take a risk-based approach to how they can be addressed for individual installations. In many cases, not all of the appliances need to be connected to a hub with remote access capabilities.
4.1. Threats to Validity
One threat to the validity of this research is the limited amount of academic research on open-source smart home gateways and hubs. However, a wealth of information can be found in non-academic sources, such as newspapers, magazines, blogs, forums, and so on. These sources are not peer-reviewed and thus could be less reliable than academic sources, but can still provide a more up-to-date picture of security challenges. During this study, we have investigated such sources as a side activity to keep us informed. However, these sources are not part of the synthesis.
Another challenge is that the inclusion and exclusion criteria were quite strict, due to the limitations of the study resources. Although this meant that more time could be allotted to the most relevant articles, it also meant that less central studies that contain potentially relevant research had a higher chance of being excluded. This could have impacted the accuracy of this literature review and give the research a blind spot.
We also recognize that temporal validity can be a challenge in this study. We have focused on publications from the last five years to increase relevance, but there is rapid technological development in the smart home hub community, which could limit the value of the findings over time.
One final threat to selection validity is subjectivity. Even though the authors have put significant time and effort into ensuring objective inclusion and exclusion of studies, it is impossible to remove all subjectivity from the literature selection process.
4.2. Future Research Directions
This literature review has identified several security challenges, and future research should focus more on how to remedy many of these. For instance, Setz et al. [26] performed a comparison of different open-source smart home hubs, providing a helpful guide for users selecting an open-source extensible smart home hub based on various aspects of the system. Building on this work, a detailed comparison of security features in popular hubs and the effectiveness of attack mitigation strategies could be conducted. This comparison would assist security-aware users in choosing the right system and contribute to the future development of security features for all smart home hubs.
As highlighted in the key security challenges, many security risks in extensible smart home hubs, especially open-source ones, stem from user configuration. Developing a security dashboard that helps users identify and understand security risks in their setup could mitigate these risks. A proof-of-concept implementation of such a dashboard could be created and evaluated to determine its effectiveness in securing the hub and educating users, thereby enhancing their security awareness.
Olabode et al. [31] suggested that a common limitation in security research is the lack of “real life experiments”. To help address the security risks from user configuration, it could be beneficial to study real-world user behavior, UI design, and usability to inform the creation of effective awareness and configuration mechanisms. Additionally, it could be valuable to study and analyze the real-world complexity and effectiveness of security features suggested as solutions to security challenges by the included papers.
Extensible smart home hubs often lack fine-grained access control, which is crucial for multi-user setups and less reputable extensions. Exploring the application of zero-trust principles from network security to develop fine-grained access control could be beneficial. A proof-of-concept implementation for Home Assistant, for instance, could be evaluated based on the threat model introduced by Corno and Mannella [1], providing insight into its applicability and effectiveness.
Corno and Mannella [1] also demonstrated how Home Assistant could be exploited based on their threat model for extensible smart home hubs. Developing specific proofs-of-exploit for each identified threat would further validate this work and provide metrics for future research aimed at mitigating these risks. This approach would improve the understanding of vulnerabilities and contribute to the development of more secure smart home systems. At the same time, ethical considerations must be properly addressed when creating proofs-of-exploits.
This study focused almost exclusively on open-source extensible smart home hubs due to the availability and ease of access to information about them compared to their commercial counterparts. Further, the amount of in-depth research covering commercial hubs is minimal. Comparing the security challenges of open-source and commercial extensible smart home hubs and validating the results of this study with commercial systems could be worthwhile research opportunities.
Behind every challenge that was identified in this review, countless examples of suggested solutions exist. Further research is required into these solutions’ feasibility, performance, advantages, and drawbacks. We believe that the challenges this study identified can be helpful in this research by allowing researchers to use them in their analysis of these factors.
5. Conclusions
This study has conducted a comprehensive literature review of the security challenges associated with smart home devices and home automation systems, particularly focusing on extensible smart home hubs. The rapid growth of the smart home market, coupled with the increasing complexity and integration of various devices, underscores the critical need for robust security measures.
The literature review identified eight prevalent cybersecurity challenges, including insecure hub software, insecure IoT ecosystems and integrations, insecure user configurations, insecure remote access configuration, insecure trigger-action programming, insufficient multi-user management, insecure extension runtime, and insufficient access control. These challenges can cause significant risk exposure for smart home systems, and addressing them is essential to ensure the safety and privacy of smart home users. By implementing the recommended solutions and pursuing the suggested research opportunities, the smart home industry and community can continue to grow while maintaining the trust and confidence of its users.
Author Contributions
Conceptualization, T.R.T. and P.H.M.; methodology, T.R.T. and P.H.M.; validation, T.R.T. and P.H.M.; formal analysis, T.R.T.; investigation, T.R.T.; resources, P.H.M.; data curation, T.R.T.; writing—original draft preparation, T.R.T. and P.H.M.; writing—review and editing, T.R.T. and P.H.M.; visualization, T.R.T.; supervision, P.H.M.; project administration, P.H.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Corno, F.; Mannella, L. A Threat Model for Extensible Smart Home Gateways. In Proceedings of the 2022 7th International Conference on Smart and Sustainable Technologies (SpliTech), Split, Croatia, 5–8 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Statista. Global: Smart Home Number of Users 2019–2028. 2025. Available online: https://www.statista.com/forecasts/887613/number-of-smart-homes-in-the-smart-home-market-in-the-world (accessed on 24 March 2025).
- GMI. Smart Home Market Size—By Type, by Connectivity, by Price, by Application, by Distribution Channel, Forecast 2025-20349. 2025. Available online: https://www.gminsights.com/industry-analysis/smart-home-market (accessed on 12 May 2025).
- Corno, F.; Mannella, L. A Gateway-based MUD Architecture to Enhance Smart Home Security. In Proceedings of the 8th International Conference on Smart and Sustainable Technologies (SpliTech), Split, Croatia, 20–23 June 2023. [Google Scholar] [CrossRef]
- Andrade, R.O.; Ortiz-Garcés, I.; Cazares, M. Cybersecurity Attacks on Smart Home During Covid-19 Pandemic. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 398–404. [Google Scholar] [CrossRef]
- Lazzaro, S.; De Angelis, V.; Mandalari, A.M.; Buccafurri, F. A black-box assessment of authentication and reliability in consumer IoT devices. Pervasive Mob. Comput. 2025, 110, 102045. [Google Scholar] [CrossRef]
- Samsung. Connect your home with Samsung SmartThings. Available online: https://www.samsung.com/us/smartthings/ (accessed on 18 November 2024).
- Athom. Homey—A Better Smart Home. Available online: https://homey.app/en-us/ (accessed on 20 September 2024).
- Open Home Foundation. Home Assistant. Available online: https://www.home-assistant.io/ (accessed on 19 September 2024).
- Teeuw, M. MagicMirror2. Available online: https://magicmirror.builders/ (accessed on 19 November 2024).
- openHAB Foundation. openHAB. Available online: https://www.openhab.org/ (accessed on 19 September 2024).
- Aromataris, E.; Pearson, A. The systematic review: An overview. Ajn Am. J. Nurs. 2014, 114, 53–58. [Google Scholar] [CrossRef] [PubMed]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef] [PubMed]
- Page, M.J.; Moher, D.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. PRISMA 2020 explanation and elaboration: Updated guidance and exemplars for reporting systematic reviews. BMJ 2021, 372, n160. [Google Scholar] [CrossRef] [PubMed]
- Elsevier. How do I Search in Scopus? 2024. Available online: https://service.elsevier.com/app/answers/detail/a_id/34325/ (accessed on 10 September 2024).
- Boutron, I.; Page, M.J.; Higgins, J.P.; Altman, D.G.; Lundh, A.; Hróbjartsson, A.; Group, C.B.M. Cochrane Handbook for Systematic Reviews of Interventions Version 6.5; Wiley Online Library. 2024. Chapter Considering Bias and Conflicts of Interest Among the Included Studies [Last Updated August 2022]. Available online: https://training.cochrane.org/handbook (accessed on 17 April 2025).
- Ogundipe, O.; Nwafor, V.; Ajuwon, A.; Uwagboe, E.; Ajisegiri, E.; Adediran, A.; Ikubanni, P.; Onu, P.; Ogunniyi, O.; Adeleke, A. Smart Home Innovations—A Mini Review. In Proceedings of the 2024 International Conference on Science, Engineering and Business for Driving Sustainable Development Goals (SEB4SDG), Omu-Aran, Nigeria, 2–4 April 2024. [Google Scholar] [CrossRef]
- Rak, M.; Salzillo, G.; Granata, D. ESSecA: An automated expert system for threat modelling and penetration testing for IoT ecosystems. Comput. Electr. Eng. 2022, 99, 107721. [Google Scholar] [CrossRef]
- Al-Tahee, M.; Mahdi Hussin, M.; Alsalhy, M.; Diame, H.; Haroon, N.; Bafjaish, S.; Al-Mhiqani, M. A Study on Artificial Intelligence-based Security Techniques for IoT-based Systems. Fusion Pract. Appl. 2023, 13, 147–161. [Google Scholar] [CrossRef]
- Parocha, R.C.; Macabebe, E.Q.B. Implementation of Home Automation System Using OpenHAB Framework for Heterogeneous IoT Devices. In Proceedings of the IEEE International Conference on Internet of Things and Intelligence System (IoTaIS), Bali, Indonesia, 5–7 November 2019; pp. 67–73. [Google Scholar] [CrossRef]
- Yahyazadeh, M.; Podder, P.; Hoque, E.; Chowdhury, O. Expat: Expectation-based policy analysis and enforcement for appified smart-home platforms. In Proceedings of the 24th ACM Symposium on Access Control Models and Technologies, Toronto, ON, Canada, 3–6 June 2019; pp. 61–72. [Google Scholar] [CrossRef]
- Yang, L.; Liu, X.Y.; Gong, W. Secure smart home systems: A blockchain perspective. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops, Toronto, ON, Canada, 6–9 July 2020; pp. 1003–1008. [Google Scholar] [CrossRef]
- Kanchi, S.; Karlapalem, K. A Multi Perspective Access Control in a Smart Home. In Proceedings of the 11th ACM Conference on Data and Application Security and Privacy, New York, NY, USA, 26–28 April 2021; pp. 321–323. [Google Scholar] [CrossRef]
- Mahadewa, K.; Wang, K.; Bai, G.; Shi, L.; Liu, Y.; Dong, J.; Liang, Z. Scrutinizing Implementations of Smart Home Integrations. IEEE Trans. Softw. Eng. 2021, 47, 2667–2683. [Google Scholar] [CrossRef]
- Mohammad, Z.N.; Farha, F.; Abuassba, A.O.M.; Yang, S.; Zhou, F. Access control and authorization in smart homes: A survey. Tsinghua Sci. Technol. 2021, 26, 906–917. [Google Scholar] [CrossRef]
- Setz, B.; Graef, S.; Ivanova, D.; Tiessen, A.; Aiello, M. A Comparison of Open-Source Home Automation Systems. IEEE Access 2021, 9, 167332–167352. [Google Scholar] [CrossRef]
- Amraoui, N.; Zouari, B. Securing the operation of Smart Home Systems: A literature review. J. Reliab. Intell. Environ. 2022, 8, 67–74. [Google Scholar] [CrossRef]
- Wang, T.; Zhang, K.; Chen, W.; Dou, W.; Zhu, J.; Wei, J.; Huang, T. Understanding device integration bugs in smart home system. In Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis, New York, NY, USA, 18 July 2022; pp. 429–441. [Google Scholar] [CrossRef]
- Wang, Z.; Liu, D.; Sun, Y.; Pang, X.; Sun, P.; Lin, F.; Lui, J.C.S.; Ren, K. A Survey on IoT-Enabled Home Automation Systems: Attacks and Defenses. IEEE Commun. Surv. Tutor. 2022, 24, 2292–2328. [Google Scholar] [CrossRef]
- Yang, J.; Sun, L. A Comprehensive Survey of Security Issues of Smart Home System: “Spear” and “Shields,” Theory and Practice. IEEE Access 2022, 10, 124167–124192. [Google Scholar] [CrossRef]
- Olabode, S.; Owens, R.; Zhang, V.; Copilah-Ali, J.; Kolomeets, M.; Wu, H.; Malviya, S.; Markeviciute, K.; Spiliotopoulos, T.; Neesham, C.; et al. Complex online harms and the smart home: A scoping review. Future Gener. Comput. Syst. 2023, 149, 664–678. [Google Scholar] [CrossRef]
- Yuan, B.; Wan, J.; Wu, Y.H.; Zou, D.Q.; Jin, H. On the Security of Smart Home Systems: A Survey. J. Comput. Sci. Technol. 2023, 38, 228–247. [Google Scholar] [CrossRef]
- Yu, Y.; Xu, Y.; Huang, K.; Liu, J. TAPFixer: Automatic Detection and Repair of Home Automation Vulnerabilities based on Negated-property Reasoning. In Proceedings of the USENIX Security, Philadelphia, PA, USA, 14–16 August 2024. [Google Scholar]
- OWASP. OWASP Top 10:2021. 2021. Available online: https://owasp.org/Top10/A00_2021_Introduction/ (accessed on 21 November 2024).
- OWASP. OWASP IoT Top 10:2018. 2018. Available online: https://web.archive.org/web/20200416105630/https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf (accessed on 21 November 2024).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).