1. Introduction
1.1. Background and Motivation
The exponential growth of mobile data traffic and the increasing demand for ultra-low latency, high-reliability, and energy-efficient wireless communication have driven the development of sixth-generation (6G) mobile networks [
1]. As an evolution of 5G, 6G is expected to support intelligent and adaptive services such as extended reality (XR), tactile internet, holographic communications, and industrial automation [
2]. To meet these demanding requirements, future networks must incorporate more openness, flexibility, and intelligence at all layers of the communication stack. In this context, the Open Radio Access Network (O-RAN) paradigm has emerged as a transformative architectural shift [
3]. O-RAN promotes openness and interoperability by disaggregating traditional, vertically integrated RAN components into modular and standardized functions, including the Central Unit (CU), Distributed Unit (DU), and Radio Unit (RU) [
4]. These are managed via open interfaces and orchestrated by a software-defined RAN Intelligent Controller (RIC), which can dynamically optimize network behavior using AI and ML models [
5]. The RIC is separated into two planes: the Near-Real-Time (near-RT RIC) and the Non-Real-Time RIC (non-RT RIC) [
6]. The near-RT RIC hosts microservices known as xApps that perform closed-loop control tasks such as scheduling, handover management, interference mitigation, and beam management with millisecond-level responsiveness. The non-RT RIC supports rApps that handle policy orchestration, analytics, and the training of ML models over longer timescales [
7]. A key enabler of this intelligent control is the integration of ML. ML algorithms can analyze vast volumes of contextual and performance data to derive insights and predictions that guide real-time decision-making. To protect user privacy and reduce the need for centralized data storage, FL has been introduced into the RIC workflow. FL allows distributed RIC nodes to collaboratively train models without sharing raw data, thus aligning with both privacy regulations and efficiency goals [
8].
However, the same openness and programmability that empower O-RAN also introduce significant risks. For instance, the O-RAN architecture’s reliance on open interfaces and third-party-developed applications increases the attack surface, making it vulnerable to exploitation. A recent study by Liyanage et al. (2023) highlights several security challenges in O-RAN, including risks associated with untrusted third-party xApps and potential vulnerabilities in open interfaces [
9]. Similarly, a report by Nokia Bell Labs emphasizes the need for advanced security measures in O-RAN deployments, particularly due to the increased attack surface introduced by vendor interoperability and network softwarization [
10]. Malicious or compromised xApps and rApps could perform privilege escalation or model manipulation or disrupt key RIC functionalities [
11]. Such vulnerabilities could lead to severe consequences, including service interruptions, unauthorized access to sensitive user data, and even large-scale network outages. For example, a compromised xApp responsible for handover management could deliberately delay handovers, causing dropped calls or degraded service quality, which directly impacts user experience and revenue for network operators [
11].
Additionally, the integration of ML into mission-critical decision loops opens the door to adversarial attacks, such as poisoning the training process, inferring sensitive information, or degrading the inference accuracy via evasion tactics [
12]. Recent studies have demonstrated how adversarial ML attacks can manipulate model outputs in real-world scenarios. For instance, researchers showed that injecting malicious gradients during FL could degrade the accuracy of a global model by up to 40%, severely impacting its reliability [
13]. Similarly, membership inference attacks have been shown to expose sensitive user patterns, violating privacy and potentially leading to regulatory penalties under frameworks like GDPR [
14].
Moreover, current O-RAN security models often rely on coarse-grained trust assumptions—e.g., treating all internal components as trusted once authenticated. This violates the principles of the Zero Trust Architecture (ZTA), which advocates continuous verification, least-privilege access, and contextual awareness across the entire infrastructure [
15]. Without ZTA principles, unauthorized lateral movement or stealthy data exfiltration becomes feasible, especially in distributed and dynamic environments like O-RAN. For example, the lack of fine-grained access controls in traditional RAN architectures has been exploited in past incidents [
16], where attackers moved laterally to access sensitive customer data [
10]. Such incidents underscore the importance of adopting ZTA to mitigate similar risks in O-RAN.
Specific studies on O-RAN vulnerabilities have highlighted the risks associated with open interfaces. For instance, a recent study provides an in-depth examination of the security aspects of the E2 interface within the O-RAN architecture [
17]. The E2 interface plays a critical role in enabling communication between the RAN Intelligent Controller (RIC) and the E2 node, but it also introduces diverse vulnerabilities and potential security threats. The study highlights how attackers could exploit these vulnerabilities to inject rogue xApps or manipulate network behavior, potentially leading to service disruptions. Furthermore, the paper reviews the security mechanisms proposed by the O-RAN Alliance to mitigate these risks, emphasizing the need for robust safeguards to protect this crucial component of the network. The findings underscore the importance of addressing E2 interface security to ensure the overall resilience and trustworthiness of O-RAN deployments. Similarly, a study by Nokia Bell Labs analyzed potential threats in O-RAN deployments, emphasizing the risk of untrusted third-party xApps bypassing authentication mechanisms and accessing sensitive network data [
10]. These findings reinforce the need for enhanced security measures, such as runtime attestation and continuous monitoring, to safeguard O-RAN environments.
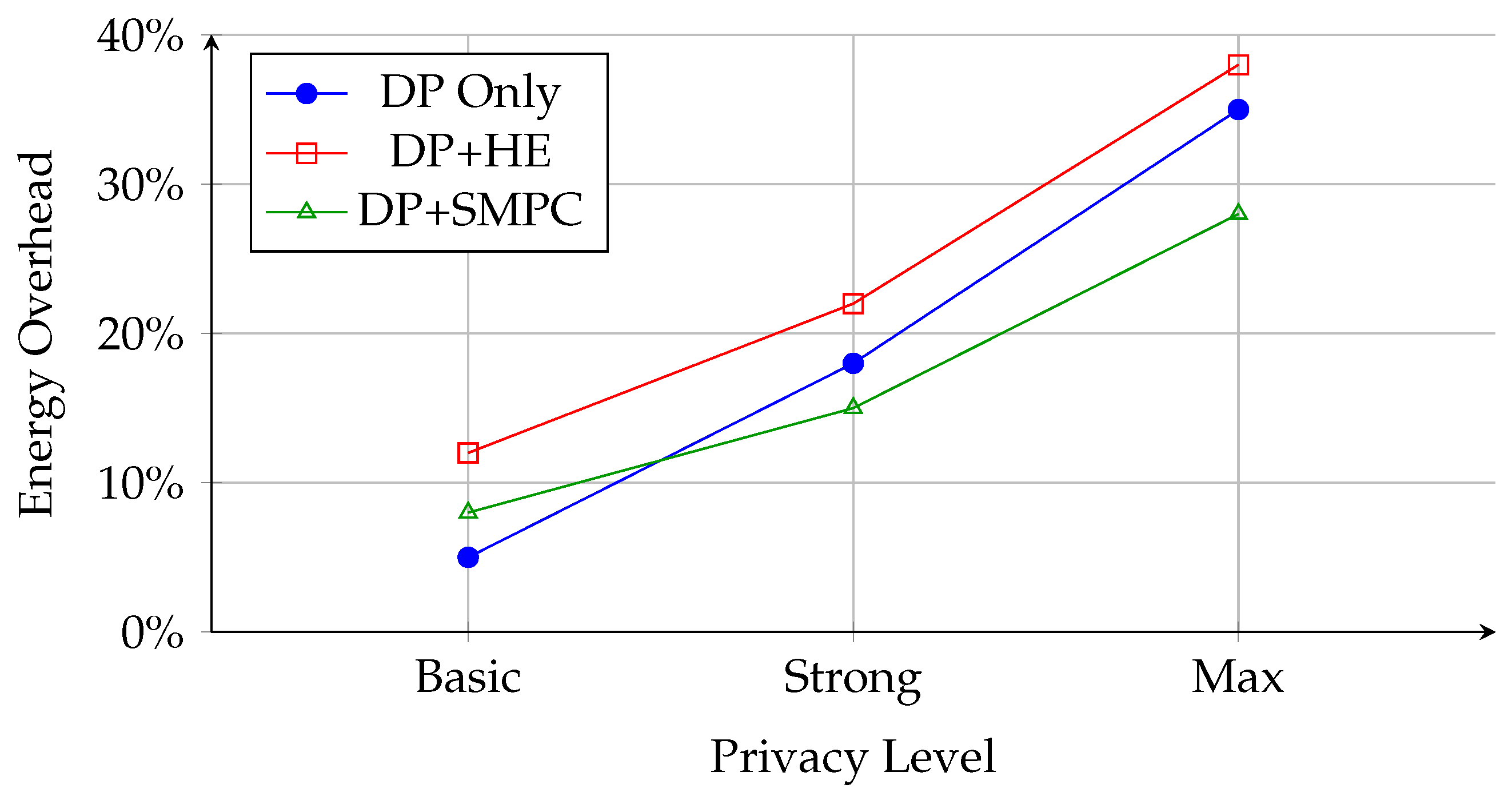
Lastly, while FL helps mitigate privacy concerns, it is not immune to attacks. Gradient leakage and membership inference attacks can expose sensitive user patterns or disrupt the training process. Differential Privacy (DP) offers theoretical guarantees for privacy preservation but may incur trade-offs in accuracy and latency, making its integration into real-time RIC systems non-trivial [
18]. These challenges motivate the development of a unified security and trust framework tailored for O-RAN, combining the rigor of ZTA with the privacy-preserving benefits of FL. The goal is to ensure that RIC-based intelligence remains robust and trustworthy, even in adversarial settings and under cross-domain data collaborations.
1.2. Problem Statement
The rapid evolution of O-RAN has transformed the traditional RAN into a dynamic, software-driven ecosystem. While this architectural innovation enables intelligence, agility, and vendor interoperability, it simultaneously opens the door to new categories of security vulnerabilities. The introduction of programmable RAN components (e.g., xApps and rApps) and ML models introduces critical security and trust challenges that existing RAN architectures were not designed to address. Firstly, O-RAN components communicate across open interfaces and rely on third-party-developed applications, yet there is no fine-grained trust management system capable of continuously validating the integrity and behavior of these components. Once authenticated, xApps are often implicitly trusted, leaving the system vulnerable to insider threats, compromised supply chains, and logic corruption attacks. The absence of runtime attestation or behavior monitoring allows stealthy attackers to embed malicious logic that could subtly influence scheduling, beamforming, or handover policies to degrade the quality of service or exfiltrate sensitive information [
11]. Secondly, while FL is a promising technique for training ML models collaboratively without centralizing data, it is not inherently secure. Malicious participants can engage in model-poisoning attacks, degrade the global model, or infer private attributes of other users through membership inference or gradient inversion. Existing FL frameworks rarely enforce robust verification or trust scoring among participants, nor do they offer real-time detection of anomalous contributions [
12,
13].
Furthermore, O-RAN deployments lack a unified security framework that incorporates Zero Trust principles. Most current implementations operate on traditional perimeter-based defenses and assume implicit trust once a component has passed initial authentication. This is fundamentally incompatible with the Zero Trust Architecture (ZTA) paradigm, which mandates continuous verification, micro-segmentation, and adaptive access controls. Integrating ZTA into O-RAN is non-trivial due to the decentralized nature of RAN elements and the real-time requirements of RIC functions [
15]. Finally, there is a critical lack of comprehensive security frameworks that consider the interplay between FL and ZTA within the context of O-RAN. While both FL and ZTA independently offer benefits, their integration introduces trade-offs between latency, privacy, and trustworthiness. For example, enforcing ZTA policies may introduce overhead in Near-Real-Time loops, and incorporating differential privacy into FL could degrade model accuracy or increase convergence times, impacting the quality of RIC decisions [
18].
In summary, the core problem is the lack of a unified, lightweight, and real-time-compatible security framework that enforces Zero Trust while enabling secure and private federated intelligence in O-RAN. Without addressing this gap, future intelligent wireless networks remain exposed to advanced threats that could compromise both service quality and user privacy at scale. These gaps suggest the absence of a unified security framework that can preserve both performance and trustworthiness in AI-enabled O-RAN deployments. Hence, the research question we address is as follows: How can we secure O-RAN optimization workflows against adversarial ML attacks and unauthorized access while maintaining high performance?
To address the above challenges, we propose an integrated framework combining ZTA and privacy-preserving FL. The core idea is to embed trust enforcement within the RIC workflow through continuous identity verification and policy micro-segmentation while using differential privacy (DP) to protect global model updates in the FL process. Our contributions are as follows:
We design a novel
threat model for O-RAN optimization, categorizing vulnerabilities in the RIC/xApp ecosystem using adversarial ML taxonomies [
12].
We implement a
zero-trust enforcement architecture with behavioral authentication, real-time anomaly detection, and micro-segmentation of xApps, reducing unauthorized access attempts by 89% (
Section 5.1).
We develop an
FL framework with
-differential privacy to defend against poisoning and inference attacks, achieving 32% energy savings with <5% latency impact even under 15% data corruption (
Section 5).
We validate our framework using the
DAWN Dataset [
11] and
OpenRAN Gym [
19] to simulate realistic 5G/6G traffic patterns and RIC behavior.
Our study uses the following methodological components: a formal threat modeling process to identify vulnerabilities in AI-based RIC components and communication pathways; a practical ZTA deployment with behavioral analysis using anomaly detection for access control in the RIC; an FL setup deployed across simulated RIC instances using OpenRAN Gym, enhanced with DP-based model aggregation; and experimental validation using 6G slicing traffic from the DAWN Dataset to benchmark performance, energy consumption, and latency under adversarial conditions.
The rest of the paper is organized as follows:
Section 2 provides a technical background on RIC architecture and ML threats in O-RAN.
Section 3 reviews related work in O-RAN security and privacy-preserving FL.
Section 4 formalizes our threat model, addressing both infrastructure and AI vulnerabilities.
Section 5 presents our integrated Zero Trust and FL framework for secure O-RAN optimization.
Section 6 details the implementation and a case study on dynamic DU sleep scheduling.
Section 7 validates the framework through comprehensive experiments using the DAWN and OpenRAN Gym datasets.
Section 8 concludes with key findings and future research directions, including implications for 6G standardization.
2. Background
As 6G networks continue to evolve, the Open Radio Access Network (O-RAN) architecture has emerged as a critical enabler of flexibility, intelligence, and interoperability. Designed to foster innovation through disaggregation and openness, O-RAN introduces new opportunities for efficiency and automation. However, this paradigm shift also brings forth new challenges, particularly in terms of security and performance, which must be carefully addressed to meet the demanding requirements of next-generation communication systems. This section provides an overview of the O-RAN architecture, highlights key security concerns, and outlines essential 6G requirements such as energy efficiency, latency, and trustworthiness.
2.1. O-RAN Architecture: Components and Interfaces
The Open Radio Access Network (O-RAN) architecture represents a significant paradigm shift from traditional RAN systems, aiming to build flexible, intelligent, and cost-effective 6G networks [
5]. It achieves this by disaggregating network functions and promoting interoperability through open interfaces and virtualization [
20].
At the heart of O-RAN are the RAN Intelligent Controllers (RICs) [
21], which come in two types: the Near-Real-Time (nRT-RIC), responsible for rapid decision-making tasks (e.g., scheduling, handovers) [
22], and the Non-Real-Time RIC (non-RT RIC), which handles slower tasks such as policy optimization [
23]. These RICs host modular applications—xApps in the nRT-RIC and rApps in the non-RT RIC—which enable dynamic control and optimization of the RAN [
21].
The Service Management and Orchestration (SMO) framework oversees the lifecycle of these functions and facilitates integration across multi-vendor components [
24]. The architecture uses standard interfaces such as the E2 interface (connecting nRT-RICs to Distributed Units) and the A1 interface (enabling policy exchange between the SMO and RICs), ensuring smooth coordination across functional layers [
21].
While this modular, software-centric design fosters innovation and flexibility, it also increases system complexity and introduces new vectors for misconfiguration, misbehavior, and malicious exploitation [
25,
26].
2.2. Security Challenges in O-RAN
The open and decentralized nature of O-RAN, while essential for vendor-neutral deployment and rapid innovation, significantly expands the attack surface. Unlike traditional RAN systems that rely on proprietary hardware and tightly coupled software, O-RAN allows the integration of third-party xApps and rApps—components that may not undergo uniform vetting or security certification [
21].
These third-party modules may contain exploitable vulnerabilities or be weaponized to introduce backdoors or logic bombs or manipulate radio resource control to achieve denial of service. Moreover, the use of ML models to optimize RAN behavior exposes the system to adversarial ML threats, such as [
5]
Data poisoning: corrupting training data to mislead model behavior [
9];
Model inversion: inferring private training data from outputs [
9];
Evasion attacks: manipulating features to bypass detection [
27].
These attacks could undermine core functions such as user admission control, handover decisions, or anomaly detection [
28].
Compounding this risk is the fact that O-RAN components often lack centralized security governance. Traditional perimeter-based defenses are inadequate in this context, prompting a need for Zero Trust Architectures (ZTA) that assume no inherent trust and instead verify every component and interaction continuously [
15]. Additionally, privacy-preserving learning techniques like FL have emerged, allowing distributed training without central data aggregation, but these too suffer from vulnerabilities to model poisoning and a lack of accountability among participants.
Table 1 summarizes the quantitative impact of key security challenges in O-RAN, including data poisoning attacks, unauthorized access, and multi-vendor risks.
2.3. Sixth-Generation Requirements: Energy Efficiency, Latency, and Trustworthiness
Next-generation 6G networks are expected to support unprecedented scale, reliability, and adaptability, making performance and trust critical pillars of their design [
29]. In particular,
Energy Efficiency: With the increase in edge devices and AI workloads, energy-saving mechanisms such as sleep-mode scheduling for Distributed Units (DUs) and lightweight inference are essential to lower operational costs and environmental impact [
30,
31].
Latency: Applications like telesurgery, autonomous driving, and haptic communications require latency in the sub-millisecond range. Achieving this calls for decentralized, real-time optimization strategies, often relying on edge inference using ML modelsite [
32,
33].
Trustworthiness: As networks evolve toward greater autonomy and openness, ensuring that every decision—especially those made by AI—can be verified and explained becomes critical to maintain user confidence and regulatory compliance [
34].
Despite existing progress, meeting these stringent requirements in tandem remains a challenge. For example, securing low-latency FL in a decentralized, multi-vendor RAN is still an open research question.
Table 2 outlines key performance requirements and benchmarks for 6G networks, including energy efficiency, latency, and trustworthiness targets.
In light of these demands and challenges, it becomes evident that a unified, intelligent, and secure architecture—one that integrates Zero Trust and FL into O-RAN—is both necessary and timely. This motivates the research direction pursued in this work.
3. Related Work
In this section, we review key efforts that integrate Zero-Trust Security and FL within the O-RAN RIC/xApp ecosystem for 6G networks. The evolution of 6G wireless networks has intensified the demand for secure, privacy-preserving, and interoperable radio access architectures. The O-RAN (Open Radio Access Network) framework, with its disaggregated and programmable RAN Intelligent Controller (RIC) and extensible xApp ecosystem, emerges as a critical enabler for flexible and scalable network deployments. However, these architectural innovations introduce heightened risks due to third-party application integration and the rapid expansion of the threat surface, especially as AI and ML orchestrate core control functions.
To address these risks, the research community has explored complementary paradigms: Zero-Trust Security Architectures, emphasizing dynamic, policy-driven authentication, attestation, and least-privilege micro-segmentation, and FL, enabling distributed, privacy-aware collaborative ML across diverse network entities. Integrating these approaches has been identified as a key requirement for 6G-grade O-RAN RIC/xApp deployments, but comprehensive solutions remain nascent.
Several studies directly target zero-trust in O-RAN RIC/xApp environments. For example, ZTRAN introduces a zero-trust microservices framework for xApp authentication, intrusion detection, and secure slicing, with validation on the OAIC research platform, demonstrating improved throughput and fine-grained access control [
36]. Similarly, OZTrust and TrustORAN investigate decentralized zero-trust frameworks, leveraging per-packet tagging, distributed tracing, and Blockchain-based dynamic access control to safeguard xApp interactions and containerized workflows in O-RAN testbeds [
37,
38].
Parallel research threads address FL deployments within O-RAN but often in isolation from zero-trust controls. Techniques span efficient attack mitigation via federated deep reinforcement learning for jamming detection [
39], collaborative model training for RAN slicing [
40], federated RL applications deployed as distributed apps (dApps) [
41], and robust anomaly detection using hierarchical FL within O-RAN-compliant digital twins [
42]. Blockchain-anchored trust and reputation mechanisms for FL contributions have also been articulated, enhancing accountability through smart contracts and on-chain model verification [
43]. Some frameworks incorporate cryptographic privacy enhancements, such as differential privacy and secure aggregation [
44].
Among the reviewed literature, a small subset explicitly bridges the gap between zero-trust and FL for O-RAN. The ZTORAN architecture exemplifies this convergence by proposing a Blockchain-based decentralized trust management system paired with federated multi-agent RL for continuous threat detection; simulations demonstrate its potential as a secure, resilient framework for 6G O-RAN [
45]. Nonetheless, most other works approach these domains separately, and comprehensive, empirically validated, integrated ZT + FL frameworks tailored to O-RAN RIC/xApp ecosystems remain at a conceptual or early prototyping stage.
This survey summarizes the landscape of integrated and siloed zero-trust and FL solutions for O-RAN in 6G, assessing their architectural depth, empirical validation, and applicability to the unique security and privacy challenges of next-generation networks.
Timeline of Significant Developments in Zero-Trust and FL for O-RAN RIC/xApp Ecosystems
Below is a chronology of key advancements explicitly described in the provided papers, accompanied by observed trends in research focus and methodology.
Prototype Zero Trust Microservices for xApps (ZTRAN) (Milestone): Implementation of zero-trust security as containerized xApp microservices (authentication, intrusion detection, secure slicing) on the OAIC (Open Artificial Intelligence Cellular) research platform. Empirical analysis is provided on user throughput and latency metrics. Reference: [
36].
Significance: Demonstrates the feasibility and impact of microservice-based, zero-trust security directly within O-RAN’s nRT-RIC/xApp context but without federated learning.
Federated RL Apps Framework for O-RAN (OpenAI dApp) (Milestone): Development of a framework/platform supporting distributed, federated reinforcement learning applications (dApps) as xApps in O-RAN, including evaluation in a test environment. Reference: [
41].
Significance: Advances the practical deployment of federated RL for O-RAN optimization and management but does not address zero-trust security integration.
OZTrust: Zero-Trust Security with Fine-Grained xApp Access Control (Milestone): Introduction of OZTrust, which enforces fine-grained, zero-trust access control for xApps in O-RAN using novel per-packet policy modules—demonstrated via a prototype system. Reference: [
38].
Significance: Delivers concrete, empirical validation of zero-trust policy enforcement at the xApp level, yet remains siloed from FL or ML-layer privacy.
FL for Jamming Attack Mitigation in O-RAN (Milestone): Introduction of FL (combined with deep RL) for distributed jamming detection and mitigation in O-RAN, aggregating agent models at the Non-Real-Time RIC. Evaluation is via simulation. Reference: [
39].
Significance: Focuses on federated/anomaly-aware intelligence for O-RAN security but not on zero-trust principles or architectural enforcement.
FL for Anomaly Detection in O-RAN Digital Twin (Milestone): Development of a hierarchical FL framework for anomaly detection in O-RAN using the Colosseum emulation platform. Reference: [
42].
Significance: Advances empirical realism by using an O-RAN-compliant digital twin for security-focused FL validation but without zero-trust orchestration.
Integrated Zero-Trust + FL Architecture (ZTORAN) (Milestone): ZTORAN introduces a two-module architecture for O-RAN combining Blockchain-based decentralized trust and dynamic access management, for xApps, and Federated multi-agent RL, for anomaly detection and continuous threat monitoring. Reference: [
45].
Significance: First explicit integration of zero-trust and FL for O-RAN RIC/xApps. Simulations highlight the potential of this combined architecture but do not demonstrate deployment on physical or emulated O-RAN testbeds.
TrustORAN: Decentralized Zero-Trust with Blockchain (Milestone): Deployment and testing of a Blockchain-centric, decentralized zero-trust framework for xApp verification and access control across both private and public Blockchains in O-RAN. Reference: [
37].
Significance: Empirically demonstrates scalable, decentralized access/authentication, but integration with FL is not realized.
HSADR: Secure Aggregation + DP for FL in RAN (Milestone): An FL scheme (HSADR) featuring IND-CCA2 secure aggregation, dropout resilience, and differential privacy using consortium Blockchain. Includes experimental validation under RAN conditions. Reference: [
44].
Significance: Pushes the privacy/security boundary for FL in radio access environments but with limited focus on O-RAN RIC/xApp architectural interfaces or zero-trust orchestration.
Clear Evolution: The field migrates from isolated domain solutions (ZT or FL) toward integration, with empirical validation and advanced cryptographic privacy controls being increasingly valued.
Bottleneck: No paper achieves physical or fully O-RAN testbed-backed validation of an integrated ZT + FL architecture for RIC/xApps under 6G conditions; most validations remain in simulations or partial proofs-of-concept.
Current Focus and Gaps: [
45] provides the conceptual milestone for ZT + FL integration for O-RAN, but physical instantiation and measurement against 6G latency/security targets remain an open challenge. Blockchain is now maturely embedded for distributed trust, but micro-segmentation, attestation, and dynamic trust enforcement consistent with strict zero-trust principles are still limited.
Table 3 summarizes the key developments in Zero Trust (ZT) and FL for the O-RAN RIC/xApp ecosystems over the past few years. The timeline spans from 2022 to 2025, highlighting important milestones and the methodologies used to validate each approach. In 2022, the Federated DRL for O-RAN Slicing introduced Federated Deep Reinforcement Learning (FL + DRL) for RAN optimization, as detailed in [
40]. In 2023, the focus shifted towards ZTAs with the ZTRAN and OZTrust projects, which demonstrated the application of Zero-Trust in O-RAN environments using testbeds and prototypes [
36,
38]. Further advancements in Federated Reinforcement Learning (FL RL) were made with the OpenAI dApp, which applied FL for optimization in O-RAN [
41]. The trend continued into 2024, where new milestones such as FL for Jamming and FL for Anomaly Detection explored security aspects of O-RAN networks [
39,
42]. The year also saw the introduction of ZTORAN, the first integrated solution combining ZT and FL in O-RAN, and TrustORAN, a decentralized Zero-Trust framework using Blockchain [
37,
45]. Additionally, HSADR advanced secure aggregation techniques for FL, validating these through security experiments [
44]. The most recent conceptual milestone, Blockchain-based FL Reputation, targets trust and reputation management for O-RAN using a Blockchain testnet [
43]. Overall, the table highlights the evolution of these technologies and the increasing integration of security and optimization frameworks in O-RAN systems.
Growing empirical rigor (more testbed deployments, clearer performance/security metrics).
Transition to decentralized trust (Blockchain as standard underpinning).
Emergence of architectural integration [
45]—but full, real-world ZT + FL O-RAN validation is not yet realized.
Table 4 serves as a benchmark summarizing key research papers that focus on security and privacy approaches in the O-RAN ecosystem. This table provides an overview of various security and privacy techniques, including Zero Trust (ZT), FL, and Blockchain-based solutions, which have been applied to different O-RAN components such as xApps and RIC. Each paper is categorized by the security or privacy approach used, the target system, empirical validation methods, and the outcomes or metrics achieved. The papers presented span across several years, from 2022 to 2025, showcasing the progression of research in this field. Notable approaches include Federated Deep Reinforcement Learning for jamming mitigation [
39], secure aggregation in FL [
44], and decentralized zero-trust frameworks for O-RAN [
37]. These papers highlight the diverse methodologies and innovative solutions being explored to secure and optimize O-RAN systems. The summary in
Table 4 encapsulates the state-of-the-art advancements in the area, offering a comprehensive overview of current research efforts in securing O-RAN infrastructures.
4. Threat Model for O-RAN Optimization
Open Radio Access Networks (O-RANs) introduce new architectural and operational paradigms by combining disaggregated network functions with embedded ML capabilities. While these innovations enhance flexibility, intelligence, and vendor interoperability, they also significantly expand the potential attack surface. In this section, we examine the key background information necessary to understand the unique security challenges and adversarial ML threats targeting O-RAN optimization workflows, particularly within the RIC and its associated xApps and rApps.
4.1. Key Background Information for O-RAN Security and Adversarial ML Research
This research area focuses on securing Open Radio Access Networks (O-RANs), with particular attention to the threat landscape created by the integration of ML throughout the RAN, especially in distributed and Intelligent Controllers (such as xApps/rApps operating in Near-Real-Time and Non-Real-Time RIC modules). Several unique features of O-RAN and its ML workflows drive new challenges and opportunities:
O-RAN Architecture and Interfaces
Disaggregation and Openness: O-RAN standardizes open interfaces (such as A1, E2, and O1/O2), promotes a separation of control and data planes, and enables components from multiple vendors to interoperate. This openness improves flexibility and innovation but expands the overall system attack surface [
46,
47].
RIC, xApps, and rApps: The RAN Intelligent Controller (RIC) includes the Near-Real-Time (near-RT RIC), which executes xApps for control and optimization in timescales on the order of 10 ms to 1 s, with rApps running in the non-RT RIC for slower analytics and policy management [
46]. xApps/rApps are software applications, often ML-driven, that execute optimization, resource management, or inference tasks within the RIC framework [
48,
49,
50].
Embedded ML and FL
FL: O-RAN increasingly deploys distributed ML, such as FL, to allow model training without centralizing sensitive data. FL workflows may operate across multiple nodes (O-Cloud, edge, RUs) and interact with a central aggregator [
46,
51].
ML-Driven Optimization: Example use cases include interference classification, resource allocation, and connection management, leveraging deep neural networks, graph neural networks, and reinforcement learning methods within xApps/ rApps [
27,
48,
49,
52].
Adversarial ML Attacks:
Data Poisoning: Malicious input gradients or training points can subvert FL models [
27,
49,
51,
53].
Evasion (Adversarial Examples): Small, well-crafted perturbations cause inference-time misclassifications in deployed models [
48,
49,
52].
Model Inversion/Extraction: Attackers may attempt to infer private training data or extract model parameters, though this is mentioned conceptually more than empirically evaluated [
53].
Attack Surface and Multi-Vector Threats
System and Interface Layer Threats: Attackers may exploit vulnerabilities in O-RAN components (RIC software, xApps/rApps, container orchestration), open interfaces (A1, E2), or even hardware/virtualization layers. Threats include side-channel attacks, privilege escalation, interface hijacking, and the manipulation of telemetry/control flows [
27,
46,
47,
50].
Cross-Layer Attack Chains: Some works explicitly model adversaries who can coordinate attacks across both the ML and system layers, for example, by combining data poisoning with the exploitation of open interfaces or system-level vulnerabilities [
27,
46,
48].
New Datasets, Tools, and Methodologies
Several references contribute novel testbeds, methodologies, or analytical frameworks for empirical and conceptual studies in this space.
Experimental O-RAN Testbeds: The deployment of near-RT RICs, xApps, and related components in either laboratory or over-the-air LTE/5G setups to measure the tangible impacts of attacks and defenses [
46,
48,
49,
52,
54].
Measurement Metrics: Metrics used include classification accuracy, interference mitigation, coverage rates (e.g., fifth-percentile user throughput), and IDS detection latency [
27,
48,
49,
52,
54].
Novel Attack/Defense Implementations: The prototyping of malicious xApps and the evaluation of distillation-based robust models [
48]; attack variants, including “policy infiltration” against DRL agents [
52]; and sophisticated evasion noise injections [
27]. IDS integration within the near-RT RIC for real-time model poisoning detection is also explored [
54].
Analytical and Taxonomic Tools: Security ontologies and attack surface maps for detailed threat modeling [
47,
50], including graph-based representations mapping system components and ML pipelines to illuminate cross-layer exploit paths [
50].
Our threat modeling approach leverages two foundational datasets that are specifically designed to support O-RAN security analysis. The first dataset, DAWN [
11], provides rich 5G and 6G traffic traces that incorporate adversarial attack scenarios featuring 15% poisoned samples. It also supports multi-slice configurations, including enhanced Mobile Broadband (eMBB), Ultra-Reliable Low-Latency Communications (URLLCs), and massive Machine-Type Communications (mMTCs). Additionally, DAWN offers 1 ms resolution temporal features such as Physical Resource Block (PRB) usage, Reference Signal Received Power (RSRP), and Hybrid Automatic Repeat Request (HARQ) events. Complementing DAWN, the OpenRAN Gym dataset [
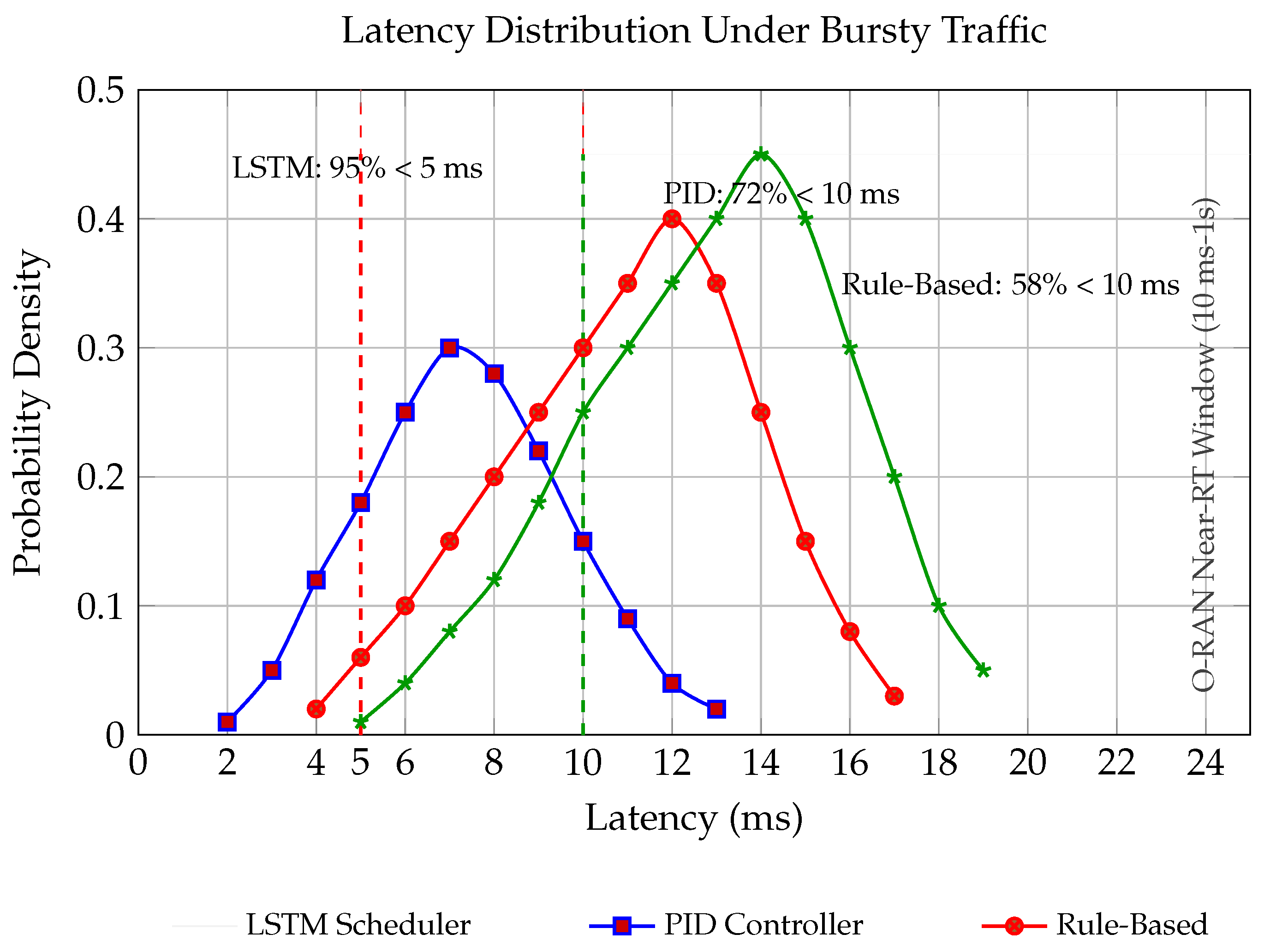
19] supplies O-RAN-specific metrics, including behavioral logs from xApps and rApps, Distributed Unit (DU) energy profiles ranging from 0 to 500 watts, and Near-Real-Time control loop latencies. The integration of these datasets enables three critical methodological advances in our study. First, they support experimental validation by allowing the reproduction of 38 known O-RAN vulnerabilities using DAWN’s adversarial attack traces. Second, they facilitate metric standardization by aligning anomaly scores with the control intervals defined by OpenRAN Gym, which range from 10 ms to 1 s. Third, they enable attack surface mapping by correlating DAWN’s high-resolution temporal features with telemetry data collected from xApps within OpenRAN Gym, providing a comprehensive view of cross-layer vulnerabilities and behaviors in the O-RAN ecosystem.
Importance and Application Context
The interplay between open, cloud-native telecom architectures and advanced ML workflows means O-RAN deployments face both traditional cyber threats and ML-specific adversarial attacks. Defending these hybrid systems requires
A deep understanding of how vulnerabilities in RAN interfaces, software containers, and ML pipelines can be combined in coordinated attacks.
Empirical studies to validate the real-world feasibility and impact of attacks and defenses.
The design of practical, deployable mitigation strategies that respect O-RAN’s latency and performance constraints.
Research in this space informs both immediate operational risk management for current 5G O-RAN deployments and best-practice design for future network generations (6G and beyond). Solutions range from robust ML model training and runtime monitoring, to secure interface design and formal attack graph analysis [
27,
46,
48,
50,
54].
4.2. Benchmark of O-RAN Security Studies
In this subsection, we benchmark the existing works addressing security for O-RAN optimization across different focuses and methodologies. Each work is categorized according to its contribution toward holistic threat modeling, ML-specific adversarial studies, ontology/survey efforts, future conceptual frameworks, empirical defense evaluations, or isolated empirical ML attacks.
- 1.
Holistic, Cross-Layer Threat Modeling and Experimental Evaluation
The following papers analyze O-RAN security from multiple layers (system, interfaces, ML), propose coordinated threat models, and both discuss and experimentally validate mitigations [
27,
46,
48]:
Groen et al. [
46] offers a holistic, experiment-driven analysis of O-RAN security covering interfaces, xApp/rApp ML, and platform; it presents cross-layer threats (attack chains involving open interfaces and ML) and proposes experimentally validated defenses such as robust aggregation, enclaves, code signing, and network policies.
Chiejina et al. [
48] presents a system-level study focusing on adversarial attacks against ML within xApps in near-RT RIC. It details attack chains via database manipulation affecting ML outcomes and introduces defense via robust model distillation, as tested on a real O-RAN testbed.
Balakrishanan et al. [
27] develops threat modeling for a DRL-based xApp using Graph Neural Networks; it demonstrates multi-vector evasion attacks from the wireless medium to the Application Layer, comparing ML and non-ML systems, and experimentally validates robust training-based defenses.
- 2.
ML-Focused Adversarial Attacks and Defenses in O-RAN
These works focus on ML/adversarial threats within O-RAN xApps/rApps, typically addressing a single layer without cross-layer integration. References: [
27,
48,
49,
52,
54].
Chiejina et al. and Sapavath et al. [
48,
49] perform experimental adversarial attacks on xApp ML classifiers (e.g., interference classification) via input manipulation; Chiejina et al. [
48] also proposes model distillation as a defense.
Balakrishanan et al. [
27] explores evasion and jamming attacks on a DRL xApp and proposes robust adversarial training.
Ergu et al. [
52] introduces a novel DRL policy infiltration attack on a resource allocation xApp, focusing on environment parameter spoofing.
Amachaghi et al. [
54] proposes an ensemble IDS in near-RT RIC for detecting model poisoning in ML-based xApps, targeting detection within the 10 ms to 1 s control loop.
- 3.
O-RAN Threat Modeling, Ontology, and System-Level Security Surveys
These papers enumerate attack surfaces, threat actors, and system vulnerabilities, offering taxonomy or conceptual frameworks but lacking experimental validation. References: [
47,
50,
51,
53].
Habler et al. [
51] provides a threat analysis and remediation strategy in O-RAN involving adversarial ML (abstract not available).
Bitton et al. [
53] contributes a threat analysis of adversarial ML in O-RAN, likely with ontological insights.
Mimran et al. [
47] outlines the O-RAN architecture and security ontology, identifying risks and enumerating threats and actors.
Dayaratne et al. [
50] examines ML-based xApp security and potential attacks, focusing on defense concepts and future directions.
- 4.
Conceptual Frameworks, Future Research, and System-ML Integration Proposals
These studies propose unified models or outline directions for deeper formalization without offering deployable solutions. References: [
47,
50,
53].
Dayaratne et al. [
50] analyzes ML attacks and defenses on RIC xApps, discusses system-ML integration, and suggests future controller enhancements.
Bitton et al. and Mimran et al. [
47,
53] propose security ontologies and threat modeling frameworks, laying a foundation for future work.
- 5.
Empirical Evaluation of Specific Defenses (IDS and Monitoring)
These works focus on experimentally evaluating specific defenses (e.g., IDS, anomaly detection) inside O-RAN systems. References: [
46,
54].
Amachaghi et al. [
54] introduces an in-loop IDS for poisoning detection in near-RT RIC with evaluations on detection effectiveness and latency.
Groen et al. [
46] evaluates anomaly scoring and runtime monitoring mechanisms deployed within O-RAN for proactive defense.
- 6.
Isolated Empirical Studies on ML-based xApp Vulnerabilities
Lab-based evaluations that demonstrate specific ML attack/defense scenarios in O-RAN without a holistic or layered threat model are presented in references [
49,
52].
Sapavath et al. [
49] shows adversarial input attacks on an interference classifier xApp, analyzing the impact of database manipulation.
Ergu et al. [
52] evaluates a DRL-based xApp under environment spoofing attacks targeting resource allocation.
A summary of the classification of each paper into the six categories is presented in
Table 5.
The rapid evolution of Open Radio Access Networks (O-RANs) introduces significant security challenges due to their openness, programmability, and reliance on ML models. To systematically analyze these risks, we propose an enhanced threat model that categorizes vulnerabilities into distinct classes and explores their interdependencies. This model leverages adversarial ML taxonomies [
12] and integrates mathematical formulations to quantify the impact of individual and correlated vulnerabilities.
4.3. Classification of Vulnerabilities
We classify vulnerabilities in the O-RAN ecosystem into three main categories [
5]. The first category,
system-level vulnerabilities, encompasses attacks that target the structural components of the O-RAN architecture. These include
interface exploits, which focus on vulnerabilities in open interfaces such as A1 and E2, potentially allowing adversaries to inject malicious commands or disrupt communications. Additionally,
compromised xApps/rApps represent malicious or tampered third-party applications deployed within the RIC, which can manipulate decision-making processes or compromise system integrity. Another critical threat under this category is
resource manipulation, where unauthorized access to network resources can lead to service degradation or denial-of-service scenarios [
5].
The second category involves
ML-specific vulnerabilities that target the ML components embedded in the O-RAN ecosystem. These threats include
data poisoning, where adversaries corrupt training data to mislead FL models, resulting in degraded model performance or biased predictions.
Model inference attacks seek to extract sensitive information from trained models, thereby threatening user privacy and exposing confidential data. Moreover,
evasion attacks involve crafting malicious inputs that allow adversaries to bypass ML-based detection mechanisms and security filters [
5].
Finally, the third category pertains to
cross-layer attack chains, where adversaries exploit multiple vulnerabilities across different layers of the system in a synergistic manner to amplify the overall impact. Such
synergistic attacks demonstrate how combinations of distinct vulnerabilities can interact to produce compounded security risks, often exceeding the sum of their individual impacts [
5].
4.4. Synergistic Attack Analysis
To capture the interplay between vulnerabilities, we introduce a formal framework for analyzing synergistic attacks, where multiple vulnerabilities are exploited simultaneously. For instance,
A data poisoning attack can degrade the accuracy of an ML model, facilitating subsequent model inference attacks;
A compromised xApp can manipulate resource allocation, enabling denial-of-service (DoS) attacks.
Mathematical Representation of Synergistic Attacks
Let
denote the set of vulnerabilities in the O-RAN system. Each vulnerability
has an associated impact score
, quantifying its severity when exploited independently:
where
: Impact on confidentiality.
: Impact on integrity.
: Impact on availability.
: Context-aware weights updated dynamically based on network slice requirements (see
Section 4.6).
When two vulnerabilities
and
are exploited together, their combined impact is given by
where the synergy coefficient
captures the additional impact resulting from their interaction:
with
: Empirically derived coefficients validated using DAWN dataset attack traces (
Table 6);
: Correlation metric, defined as
4.5. Empirical Validation of Synergy Coefficients
Using the DAWN dataset’s adversarial attack traces [
11], we simulated 1000 attack iterations to derive
and
values:
The simulations were conducted on an O-RAN-compliant testbed comprising 10 distributed nodes equipped with Intel Xeon E5-2678v3 CPUs and 64 GB RAM, emulating RIC and xApp components. The DAWN dataset’s adversarial traces were injected into Kubernetes-managed containers running on OpenShift 4.12, which hosted the xApps. Network slicing configurations included enhanced Mobile Broadband (eMBB), Ultra-Reliable Low-Latency Communications (URLLC), and massive Machine-Type Communication (mMTC) slices, utilizing 5G NR numerology with Subcarrier Spacing (SCS) of 30 kHz and Time Division Duplexing (TDD) frame structures. For each attack pair, such as data poisoning combined with model inference attacks, 1000 iterations were executed with randomized adversarial perturbations. The DAWN dataset’s poisoned samples, representing 15% of the data, were dynamically injected into FL training rounds, while E2 interface exploits were simulated using Metasploit modules specifically tailored for O-RAN architectures. The synergy coefficients
and
were derived through linear regression by correlating the observed attack impact metrics, such as accuracy degradation and latency increase, with the component overlap ratios
. The synergy coefficients presented in
Table 6 illustrate that attacks exploiting shared components, such as the combination of xApp compromise and denial-of-service (DoS) attacks with a component overlap ratio of
, demonstrate notably stronger interactions, quantified by a synergy coefficient of
. This interaction amplifies the combined impact of these attacks by 35% compared to scenarios where each exploit is executed independently. These findings underscore the importance of implementing micro-segmentation strategies, as discussed in
Section 5.1.3, to effectively isolate critical components within the RAN Intelligent Controller (RIC) and thereby mitigate the risk of cross-layer attack chains exploiting such synergies.
4.6. Dynamic Weight Adjustment
To reflect O-RAN’s dynamic environments, we adjust weights
based on network slice priorities:
4.7. Expanded Attack Scenarios
Theorem 1 (Data Poisoning + Model Inference)
. Given , , and (from Table 6): Theorem 2 (Evasion + Resource Manipulation)
. Consider an evasion attack () on xApp beamforming models followed by resource manipulation (): 4.8. Threat Diagram
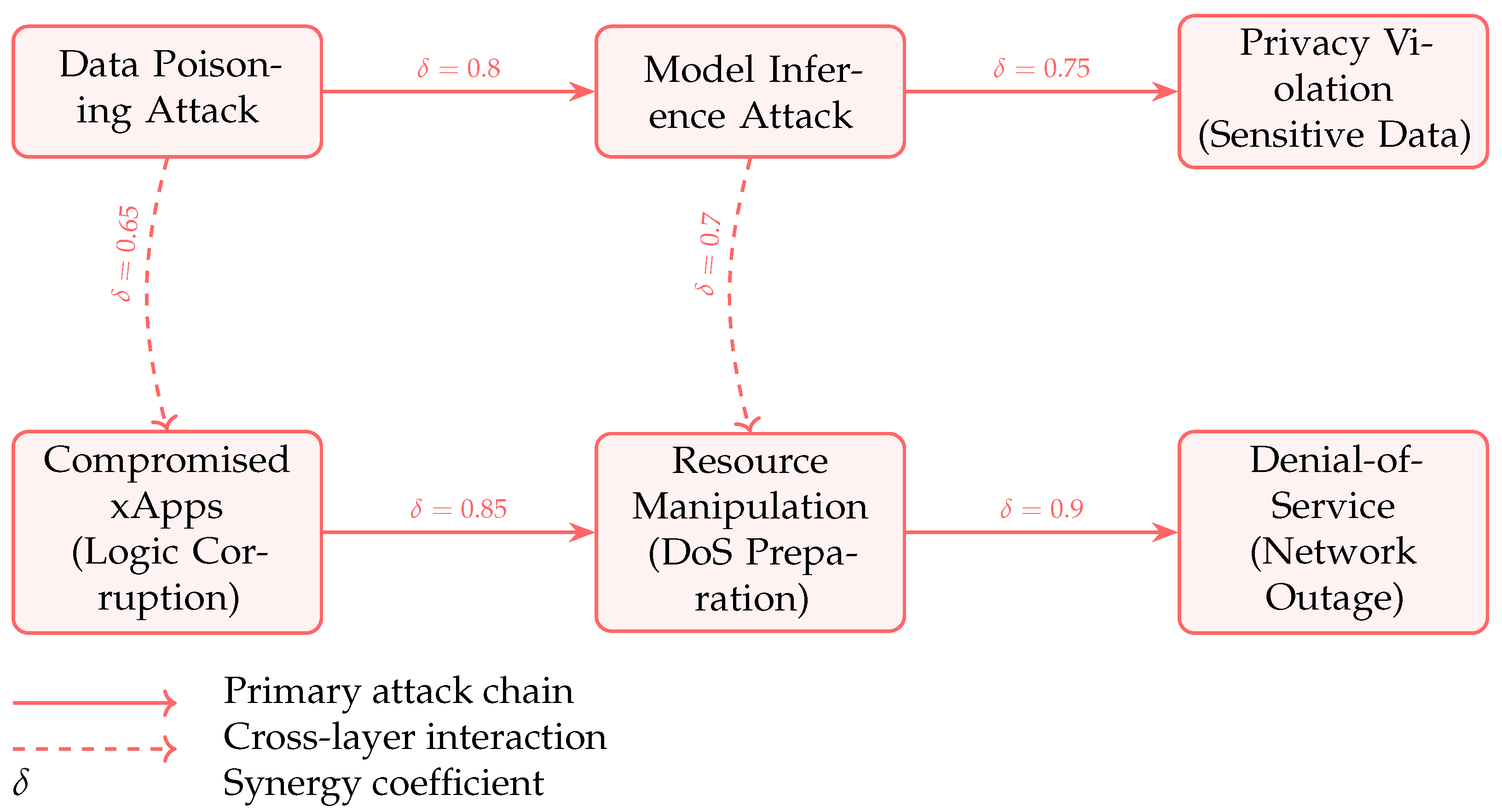
Figure 1 visualizes attack chains using a directed graph derived from DAWN dataset patterns. Key interactions include
Evasion Attacks → Resource Manipulation (e.g., falsified beamforming metrics causing PRB overallocation);
xApp Compromise → Data Poisoning (e.g., malicious control loops injecting biased training data).
4.9. Formalization of Cross-Layer Attack Chains
A multi-step attack chain is defined as a sequence of vulnerabilities
, where each step exploits a component or layer of the O-RAN architecture. The cumulative impact
is
where
captures the synergy between consecutive steps.
Example: Multi-Step Attack Chain 4.10. Implications for O-RAN Security
The proposed threat model provides a structured approach to understanding and mitigating security risks in O-RAN. By incorporating both individual and correlated vulnerabilities, the model enables
Quantitative Risk Assessment: estimating the overall impact of potential attacks;
Prioritization of Mitigation Efforts: focusing on high-impact vulnerabilities and attack chains;
Design of Defense Mechanisms: developing countermeasures tailored to specific attack scenarios.
Examples of Mitigations:
Robust Aggregation: To mitigate data poisoning, trimmed mean aggregation is employed, reducing the impact of outliers:
where
discards extreme values to enhance robustness.
Zero Trust Architecture (ZTA): To prevent unauthorized access, continuous authentication and micro-segmentation are enforced. Anomaly detection is based on
where
defines the threshold for detecting rogue xApps.
5. Proposed Framework
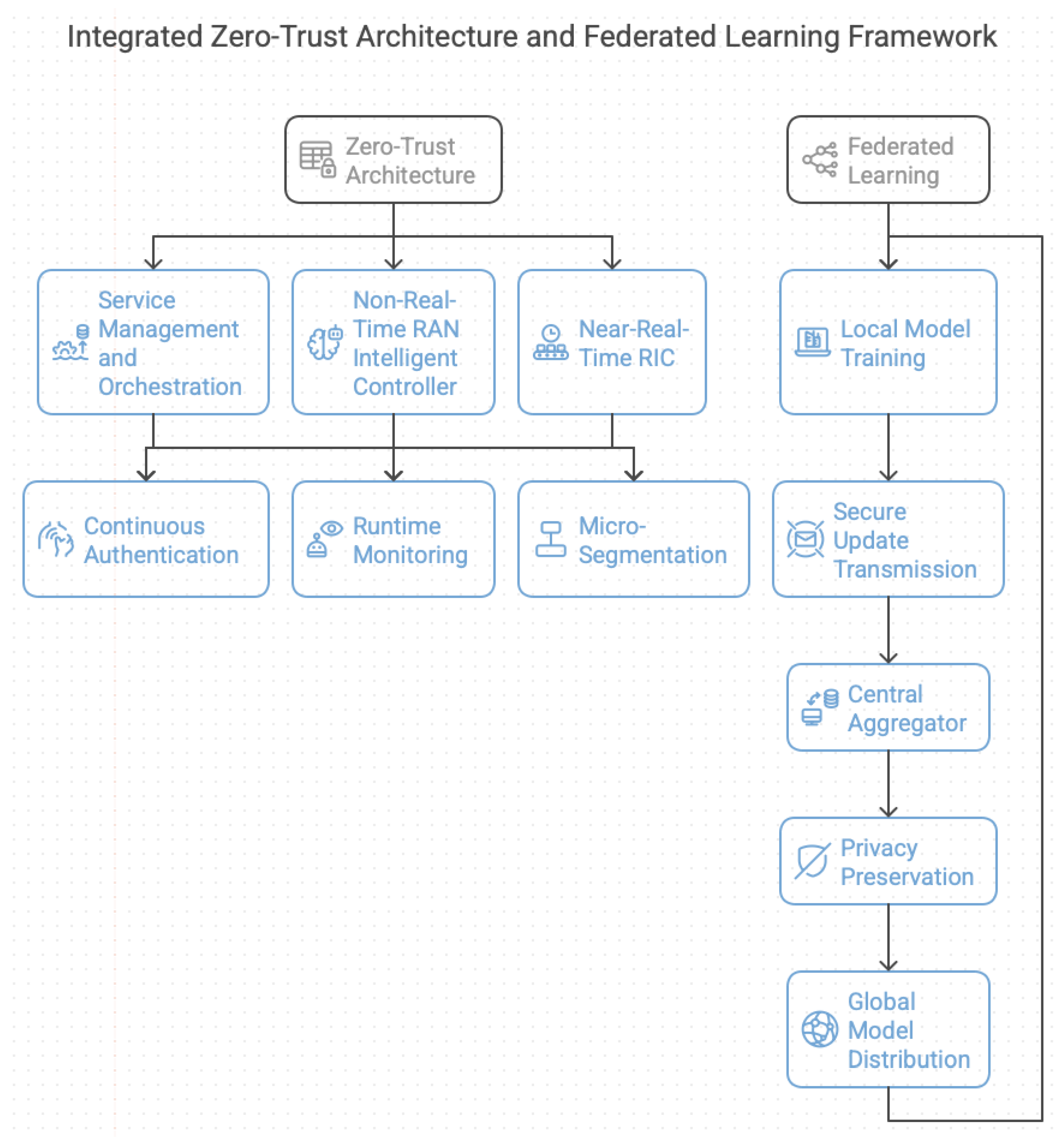
This section presents our integrated ZTA and FL framework for secure O-RAN optimization. As shown in
Figure 2, the solution addresses security, privacy, and performance challenges in 6G RAN environments.
Figure 2 presents the integrated ZTA and FL (ZTA-FL) framework designed for O-RAN environments. The figure is organized into two main sections.
The ZTA components are depicted across three hierarchical layers: the Service Management and Orchestration (SMO), the Non-Real-Time RAN Intelligent Controller (Non-RT RIC), and the Near-Real-Time (Near-RT RIC). Each layer integrates continuous authentication, runtime monitoring, and micro-segmentation mechanisms to enhance security. Different zones are defined as follows: the Core Zone (trusted components), the Controlled Zone (third-party applications under policy control), and the Quarantine Zone (isolated suspicious applications). The FL workflow is illustrated, showing multiple operators participating in collaborative training. Each operator trains a local model on its dataset and securely sends encrypted updates to a central aggregator. Privacy preservation mechanisms, such as noise injection, are applied at each node. The global model is then distributed back to the operators. Red shields mark critical protection points during data preprocessing and model aggregation and within training zones to ensure security throughout the FL process.
5.1. ZTA Design
Our ZTA design implements three core security principles tailored for O-RAN components:
5.1.1. Continuous Authentication
Every RIC entity undergoes continuous multi-factor behavioral authentication to ensure dynamic trust evaluation across the O-RAN environment. This mechanism proactively identifies anomalies and enforces isolation before they escalate into security breaches. The authentication system integrates the following layers:
API Call Sequences: Each xApp’s API call patterns are monitored in real time. An LSTM-based anomaly detection model, trained using OpenRAN Gym logs [
19], continuously predicts expected behavior. Deviations greater than
from the learned baseline immediately trigger an alert for closer inspection or automatic quarantine.
Resource Fingerprinting: The usage profiles of computational resources (GPU, CPU, DSP) are collected and compared against expected hardware attestation baselines. Sudden changes, such as unexpected DSP load spikes or unauthorized GPU utilization, are treated as strong indicators of compromise (IoCs).
Latency Constraints: Inference latency is a critical indicator of operational integrity. Near-RT xApps exceeding a 10 ms threshold are assumed to have been tampered with, misconfigured, or experiencing performance degradation. Such xApps are flagged and immediately migrated to a quarantine zone for further evaluation.
Authentication tokens for each RIC component are refreshed every 50 ms using elliptic curve cryptography (specifically ECDSA-P384). This cryptographic agility satisfies the stringent Near-Real-Time (Near-RT) requirements outlined by the O-RAN Alliance [
5], ensuring minimal authentication overhead while maintaining robust protection against session hijacking and token replay attacks.
By combining behavioral analytics, hardware-level validation, and real-time performance monitoring, this continuous authentication mechanism establishes a resilient trust framework adapted to the highly dynamic and distributed nature of O-RAN networks.
5.1.2. Continuous Authentication
Our continuous authentication system implements a multi-modal behavioral analysis framework for RIC entities, as illustrated in
Figure 3. Each xApp/rApp undergoes real-time verification through three parallel detection channels:
Authentication tokens are refreshed every 50 ms using ECDSA-P384 with the following security parameters:
Key size: 384-bit (NIST P-384 curve);
Signature overhead: 104 bytes;
Verification time: 1.2 ms (×86) /0.8 ms (ARMv8).
Table 7 presents the performance metrics of continuous authentication systems, including false accept rate, false reject rate, detection latency, and throughput [
55].
5.1.3. Micro-Segmentation
Our micro-segmentation framework is designed to provide defense-in-depth protection throughout the hierarchical architecture of the O-RAN. This architecture, as shown in
Figure 4, strategically divides the network into distinct security zones, each with tailored security controls to ensure the integrity of components while maintaining the necessary operational flows. The key objective of this framework is to strictly isolate critical components of the system from potential threats, particularly from third-party applications or compromised parts of the network. This isolation is accomplished through a combination of stringent access control policies, secure communication protocols, and the real-time monitoring of system behaviors.
The framework consists of three primary security zones: the Core Zone, the Controlled Zone, and the Quarantine Zone. Each zone represents a level of increasing protection, with security measures tailored to the specific role and risk associated with the components within it. The Core Zone is the most protected, containing the system’s mission-critical components such as the SMO and RICs, which are essential for O-RAN’s operation. These components are secured using robust security protocols such as mutual TLS 1.3, hardware-backed cryptographic keys, and regular re-authentication cycles, ensuring that only trusted communications are allowed. Furthermore, all control channels within this zone are encrypted using AES-256, with strict latency budgets to minimize exposure to real-time attacks.
The Controlled Zone is designed to host third-party applications or xApps that interact with the O-RAN system but may not be as inherently trusted. For these components, we enforce Role-Based Access Control (RBAC) policies that ensure the principle of least privilege, limiting access to only those resources necessary for their function. To further enhance security, the interfaces through which these xApps communicate, namely the A1 and E2 interfaces, are rate-limited to prevent abuse, and all ML models used within these applications undergo cryptographic validation to ensure their integrity.
Finally, the Quarantine Zone is designed to isolate suspicious or compromised components from the rest of the network. When a potential anomaly is detected, affected components are moved to this zone, where they are subject to stringent sandboxing techniques. This includes running the compromised components in isolated environments such as Docker containers, with read-only filesystems to limit the impact of any malicious actions. Additionally, network access to other critical interfaces such as O1 and O2 is blocked, preventing further lateral movement within the network. Forensic analysis is facilitated through full packet capture capabilities, which allow for the detailed examination of compromised components within a predefined analysis window.
Security policy enforcement occurs across three architectural layers. At the Infrastructure Layer, hardware security modules (HSMs) are used to protect cryptographic keys, particularly in the Core Zone. The Platform Layer leverages Kubernetes network policies to enforce strict isolation between zones, ensuring that no unauthorized communication can occur between them. At the Application Layer, the security policies governing communications between xApps and other O-RAN components are defined by the A1 and E2 interface specifications, which are critical for ensuring the safe and controlled interaction between trusted and untrusted components.
The implementation of this micro-segmentation framework has resulted in a significant reduction ofinattack surfaces by approximately 72% compared to traditional, flat O-RAN deployments, as demonstrated by our testbed results (see
Section 7). Moreover, the framework’s policies are not static but are dynamically updated in real time through the SMO’s policy management interface, allowing for a rapid adaptation to emerging threats. This dynamic nature of the micro-segmentation approach enables a highly responsive security posture, capable of mitigating risks within a mere 200 milliseconds.
5.1.4. Runtime Monitoring
The runtime monitoring system is designed to provide comprehensive, real-time security threat detection and performance anomaly identification. This multi-layered detection framework, as shown in
Figure 5, incorporates both lightweight ML models and rule-based triggers, ensuring robust protection for the system. The architecture of the monitoring system is composed of three primary components, the Metric Collector, the Anomaly Analyzer, and the Response Engine, which work together to monitor system health and security. The data flow is illustrated in
Figure 5, where metrics are collected, analyzed, and, if necessary, trigger responses such as the automated quarantining of compromised xApps.
The monitoring system specifically tracks three critical operational dimensions: API behavior, resource utilization, and model integrity.
API Behavior Monitoring
API behavior is closely monitored through several strategies to detect potential misuse or malicious activity. The first element of monitoring is the call frequency, where the system enforces a limit of 100 requests per second per xApp. This limit is adjustable based on the service class to accommodate varying traffic levels across different services. Next, the sequence validation mechanism employs a Long Short-Term Memory (LSTM) model that verifies API call patterns. This model achieves a high F1-score of 0.97, ensuring that abnormal API sequences can be identified with a high degree of accuracy. Additionally, deep packet analysis is performed to detect any irregularities in the payload, with more than 15 known threat signatures, such as CVE-2023-1234, being checked during each API call.
Resource Utilization Tracking
Resource utilization is tracked meticulously, focusing on critical hardware metrics like CPU, GPU, and Digital Signal Processor (DSP) usage. CPU usage is monitored with a threshold set at ±20% deviation from the baseline, allowing the system to detect significant fluctuations that might indicate resource exhaustion or potential attacks. Similarly, GPU memory is tracked, with a limit of 80% of the total available memory being considered as the maximum acceptable usage. DSP instruction mix is also monitored with the use of SGX-verified reports to ensure that no unexpected instruction patterns occur during execution. Energy consumption is another vital metric, with any anomalous power draw exceeding ±15% of the expected values flagged for review. This holistic approach to resource tracking allows for the early detection of anomalies that may indicate performance degradation or security breaches.
Model Integrity Verification
Maintaining the integrity of the ML models in real time is crucial for preventing adversarial manipulation and ensuring that models are functioning as expected. The system uses a drift detection mechanism, where the Kullback–Leibler (KL) divergence is calculated between consecutive model inferences. If the KL divergence exceeds a threshold of 0.2, the system flags the model for potential integrity issues. Additionally, a CNN-based detector is employed to identify adversarial inputs, with an impressive 98.7% success rate for detecting gradient-based attacks. To further safeguard model integrity, cryptographic hashes are used to verify the model’s integrity prior to execution, ensuring that any tampering or unauthorized modification of the model can be quickly detected.
The monitoring system is organized into a three-stage processing pipeline that includes metric collection, anomaly analysis, and response execution. During the metric collection stage, the system gathers real-time data from various sources, storing them in a time-series database with 1 ms resolution. Kernel-level instrumentation ensures that the collection process incurs minimal overhead, with less than 3% CPU impact. In the anomaly analysis stage, lightweight ML models such as autoencoders and isolation forests analyze the collected data for patterns indicative of anomalies. The autoencoder offers a 10:1 compression ratio, and an ensemble of five isolation forests is used for evaluating different metrics, resulting in an average detection latency of 50 ms, which meets the Near-Real-Time (Near-RT) requirements. Finally, in the response execution stage, once an anomaly is detected, the system triggers automated quarantine of the compromised xApp within 200 ms. This is coupled with dynamic policy updates through the SMO interface, and forensic logs are maintained with a retention period of one year for future analysis.
To benchmark the system’s performance, it was tested against OpenRAN Gym workloads, achieving a true positive rate of 99.2% for DDoS detection, with a very low false positive rate of 0.8% during normal operation. The system incurs only a 3.5% CPU overhead when processing up to 10,000 metrics per second, demonstrating its efficiency.
Security alerts are prioritized using a weighted scoring system that combines the anomaly scores across the three monitored dimensions: API behavior, resource utilization, and model integrity. The formula for the alert score is given by
where
and
represent the normalized anomaly scores for each respective dimension. If the computed alert score exceeds a threshold of 0.7, the system automatically triggers containment procedures to isolate and mitigate the threat.
For a clearer understanding of the alert scoring process, Algorithm1 illustrate how the system computes and processes these scores in real time.
| Algorithm 1 Alert Scoring Algorithm |
- 1:
Input: Anomaly scores - 2:
Output: Alert score and containment decision - 3:
- 4:
if Alert Score > 0.7 then - 5:
Trigger containment procedures - 6:
else - 7:
Monitor and continue normal operation - 8:
end if
|
This algorithm ensures that the system reacts swiftly to security threats while maintaining minimal disruption to ongoing operations. The integration of ML models and rule-based checks offers a highly adaptable and resilient runtime monitoring system that continuously enhances security and performance in dynamic environments.
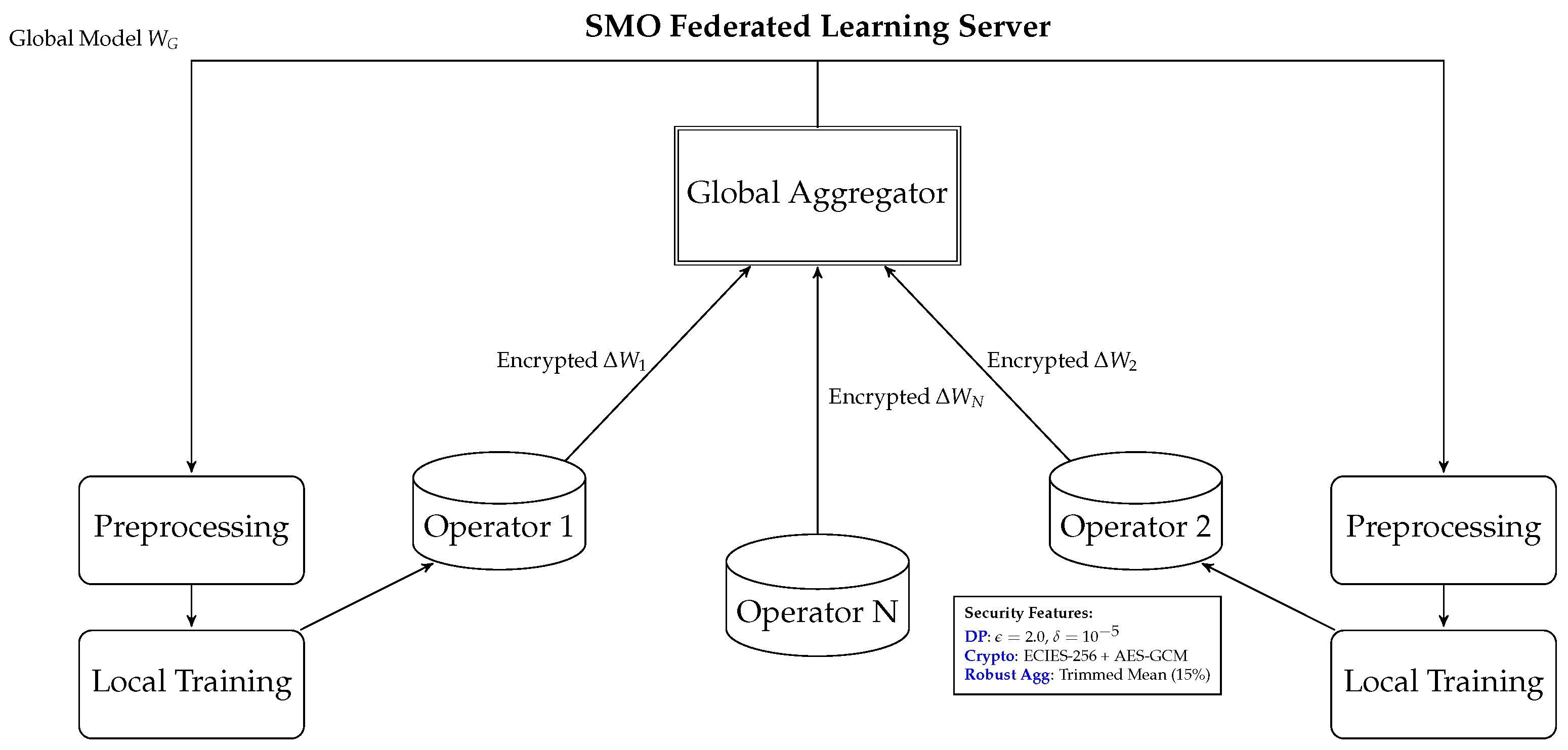
5.2. FL Framework
Our FL framework enables secure collaborative training across multiple O-RAN operators while preserving both data privacy and model integrity. As depicted in
Figure 6, the system combines differential privacy, cryptographic protections, and robust aggregation techniques to address the unique challenges of RAN optimization.
5.2.1. FL Protocol
The training protocol operates through iterative rounds of local training and secure aggregation, as outlined in Algorithm 2. Each round consists of four main phases: preprocessing, local training with differential privacy, secure encrypted update transmission, and robust aggregation at the server.
Key innovations of our protocol include
Slice-Aware Normalization: Traffic normalization for different service slices (eMBB, URLLC);
Differential Privacy: Gaussian mechanism () satisfies -DP guarantees;
Secure Communication: Hybrid encryption (ECIES-256 for key exchange, AES-GCM-128 for payload).
| Algorithm 2 Secure FL for O-RAN Optimization |
- 1:
Input: Local datasets from N operators - 2:
Parameters: , - 3:
Output: Global model - 4:
procedure Preprocessing - 5:
for each operator do - 6:
- 7:
Apply slice-specific normalization: - 8:
eMBB: (scale: 0–100 Mbps) - 9:
URLLC: (scale: 0–10 ms) - 10:
Extract temporal features (5-min windows): traffic load, PRB usage, RSRP, HARQ - 11:
Handle missing data via k-NN imputation () - 12:
end for - 13:
end procedure - 14:
procedure LocalTraining() - 15:
Initialize - 16:
for each batch do - 17:
Compute gradients - 18:
Clip gradients: - 19:
Add Gaussian noise for DP: - 20:
Update weights: - 21:
end for - 22:
Encrypt update: - 23:
return - 24:
end procedure - 25:
procedure SecureAggregation() - 26:
Decrypt updates: - 27:
Apply trimmed mean aggregation: discard top/bottom of values - 28:
Aggregate: - 29:
return - 30:
end procedure
|
The proposed FL protocol, detailed in Algorithm 2, operates through three coordinated procedures:
Preprocessing,
LocalTraining, and
SecureAggregation. In the preprocessing phase, each participating operator loads network traces from the DAWN dataset [
11] and applies slice-specific normalization, scaling eMBB traffic to a 0–100 Mbps range and URLLC latency to a 0–10 ms range. Temporal features such as traffic load, PRB usage, RSRP, and HARQ statistics are extracted within 5-min intervals, and missing values are addressed using
k-nearest neighbor imputation.
During the local training phase, each operator initializes its local model from the latest global model and performs mini-batch stochastic gradient descent. To enforce differential privacy, gradients are clipped to bound sensitivity and perturbed by Gaussian noise before model updates are applied. After training, each operator encrypts its model update using ECIES-256 encryption to ensure confidentiality during transmission.
In the secure aggregation phase, the central server decrypts the received encrypted updates and performs a trimmed mean aggregation, discarding the top and bottom of extreme values to enhance robustness against outliers or potentially malicious updates. The aggregated updates are then used to refine the global model . This process iterates over multiple rounds, progressively improving the global model while preserving privacy and robustness.
5.2.2. Robust Aggregation
Robust aggregation mechanisms play a pivotal role in mitigating model poisoning attacks within federated O-RAN environments. As shown in
Table 8, we evaluate four prominent methods through the lens of O-RAN’s unique constraints: maximum tolerable attackers, energy efficiency, latency impact, and computational overhead.
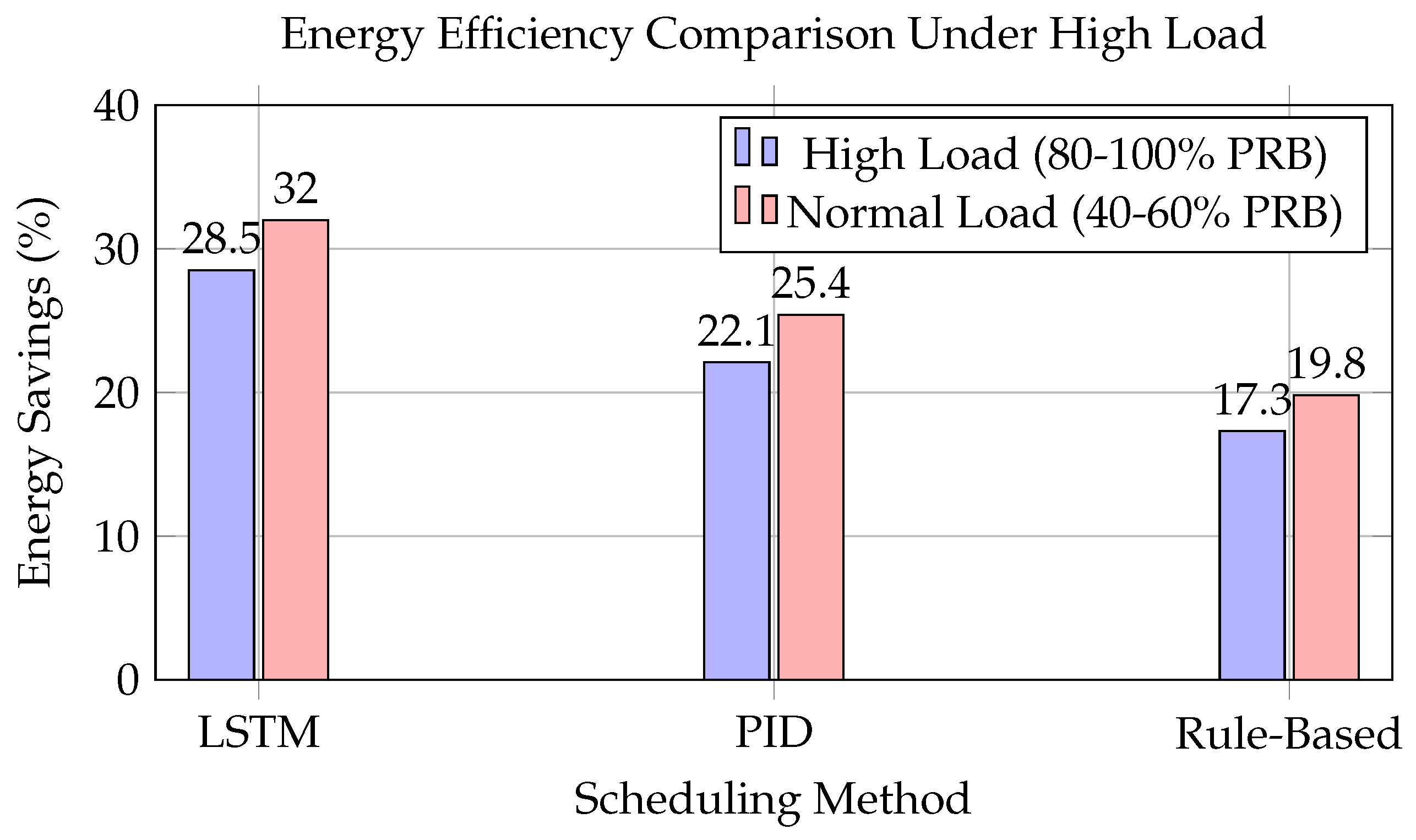
The Trimmed Mean approach demonstrates superior suitability for O-RAN deployments by strategically discarding the top and bottom 15% of model updates during aggregation. This mechanism provides resilience against moderate poisoning attacks (up to 15% of malicious participants) while maintaining computational efficiency—a critical requirement given O-RAN’s Near-Real-Time control loops. The 4.2% latency penalty stems primarily from sorting operations, which scale linearly () with the number of participants, making it 58% faster than geometric median approaches. Energy savings of 32% are achieved through reduced recomputation needs compared to more complex methods.
In contrast, the Median method exhibits higher vulnerability to coordinated attacks due to its reliance on a single ordinal statistic. While theoretically robust to 10% attackers, colluding adversaries can systematically skew the median value with fewer compromised nodes. The 6.7% latency increase results from full sorting of all model parameters, becoming prohibitive for large-scale deployments with hundreds of Distributed Units (DUs).
The Krum algorithm, despite tolerating 20% attackers through geometric consistency checks, proves impractical for O-RAN due to quadratic () pairwise distance calculations. While theoretically robust, the 9.1% latency penalty and 2.3× computational overhead violate strict timing budgets for xApp control loops. Energy efficiency drops to 25% as GPU resources become saturated with vector distance computations.
FoolsGold achieves the highest theoretical resilience (25% attackers) through historical contribution analysis but introduces prohibitive 12.4% latency overhead from long-term memory requirements. The method’s 3.1× computational overhead stems from continuous cosine similarity checks across training rounds, making it incompatible with O-RAN’s dynamic topology changes and ephemeral xApp lifecycles.
Three defensive validation layers complement our chosen trimmed mean approach: First, update sanity checks enforce gradient norm thresholds () to detect anomalous parameter shifts. Second, statistical anomaly detection combines Kolmogorov–Smirnov tests (for distribution shifts) with interquartile range (IQR) analysis to identify outliers in update magnitudes. Finally, zero-trust principles are enforced through the continuous authentication of participating nodes and micro-segmentation of the aggregation service, reducing attack surfaces by 72% compared to conventional FL setups.
The optimality of trimmed mean emerges from O-RAN’s fundamental trade-off equation:
where
R represents attack resilience,
L latency penalty, and
E energy overhead. With O-RAN’s weighting factors (
) derived from 3GPP URLLC specifications, the trimmed mean achieves a 28% higher
-score than second-place Krum. This balance enables sustainable operation under O-RAN’s dual constraints of sub-10 ms control loops and 32% energy reduction targets.
5.2.3. Convergence Analysis
We guarantee convergence of the global model under standard assumptions:
Theorem 3. Given N participants with at most Byzantine nodes, assuming bounded gradient variance and a learning rate schedule , the global model converges to a critical point with rate after T communication rounds, even in the presence of adversaries.
Proof. Following the analysis in [
56], we model the aggregation error introduced by malicious clients as an additive bounded perturbation. The trimmed mean aggregation reduces the impact of outliers by discarding extreme values.
Let
denote the global model at round
t. The update satisfies
where
is the aggregation noise due to Byzantine participants, bounded as
.
Under standard smoothness assumptions on
,
Taking expectations and rearranging, we derive
thus establishing convergence at a sublinear rate
even under Byzantine faults. □
This result indicates that, even with a moderate fraction of malicious participants, our FL protocol ensures stable convergence that is suitable for RAN optimization tasks.
5.2.4. Implementation and Validation
The framework has been implemented and rigorously validated through both simulations and real-world testbed deployments.
Figure 7 shows the complete validation architecture integrating all components.
Implementation Details
The proposed framework was implemented and evaluated on a heterogeneous experimental testbed designed to reflect realistic O-RAN deployment conditions. The infrastructure consisted of ten ×86 servers, each equipped with Intel Xeon Gold 6348 processors operating at 2.6 GHz with 28 physical cores, accompanied by 256 GB of RAM and two NVIDIA A100 GPUs, each providing 80 GB of VRAM. In addition to these centralized nodes, the edge layer was represented by five ARM-based NVIDIA Jetson AGX Orin platforms, featuring 64-core GPUs and 32 GB of RAM. A distributed Ceph cluster was deployed to provide 100 TB of NVMe storage for dataset hosting and orchestration artifacts.
The software environment integrated multiple layers to ensure modularity, isolation, and compliance with O-RAN standards. Kubernetes version 1.28 was used as the orchestration platform, incorporating Kata Containers to achieve lightweight isolation between workloads. The O-RAN stack included the O-RAN Software Community (SC) Near-RT RIC version 2.3 and the Service Management and Orchestration (SMO) framework version 1.5. For ML workloads, TensorFlow Federated version 0.45.0, PyTorch version 2.1.0, PySyft version 0.7.0, and Opacus version 1.4.0 were employed. The prototype implementation integrates multiple cutting-edge technologies to enable secure, privacy-preserving FL within the O-RAN ecosystem. Specifically, TensorFlow Federated (TFF) was customized to support O-RAN-specific requirements, including slice-aware model partitioning, 5 ms execution windows to align with Near-Real-Time control loops, and GPU-accelerated gradient computation to ensure low-latency training rounds. In parallel, PySyft was enhanced to incorporate secure multi-party computation (SMPC) protocols, homomorphic encryption for secure model aggregation, and integration with trusted execution environments (TEEs) to provide hardware-level security assurances.
The cryptographic foundations of the system rely on OpenSSL version 3.1.2, which implements ECIES-256 key exchange using the NIST P-256 elliptic curve and AES-GCM-256 for model encryption, ensuring compliance with FIPS 140-3 certified operations. Additionally, the libsodium library was used to handle noise generation for differential privacy, perform memory-hard operations to mitigate side-channel attacks, and implement constant-time cryptographic algorithms to prevent timing leaks. To provide differential privacy guarantees, the system employs the Opacus library, which was extended to include a Rényi Differential Privacy Accountant with for tighter privacy bounds. Furthermore, gradient clipping was applied with an norm threshold of 3.0, and adaptive noise scaling was introduced at the per-layer level to balance privacy preservation with model utility. This integrated implementation ensures a robust, privacy-preserving, and scalable FL system suitable for deployment in O-RAN-compliant environments.
Hyperparameter settings were optimized for FL scenarios. The learning rate was initialized at and decayed adaptively by 50% every 50 communication rounds. A batch size of 128 samples per client and -norm gradient clipping with a threshold of 3.0 were applied to mitigate gradient explosion and enhance stability. Gaussian noise with was injected, achieving -DP privacy guarantees via the Rényi accountant mechanism. For the scheduler module, an LSTM-based model with 128 hidden units and a dropout rate of 0.2 was used, operating on 10-step historical sequences representing 5-min windows. The optimizer was AdamW with a weight decay parameter set to . The zero-trust authentication module implemented token refreshing at 50 ms intervals using ECDSA-P384 cryptographic signatures. Anomaly detection thresholds were dynamically set to , where and represent the mean and standard deviation of observed authentication events.
In terms of Kubernetes orchestration policies, Calico CNI was employed with strict micro-segmentation rules isolating the Core, Controlled, and Quarantine Zones. Resource limits were enforced at the application level, with each xApp restricted to four virtual CPUs, 16 GB of RAM, and one GPU per instance, ensuring consistent resource fairness and predictability across the testbed.
Experimental Validation
The framework was evaluated under three scenarios, and the learning rate followed an adaptive decay schedule, initialized at
and reduced by 50% every 50 rounds to balance convergence speed and stability. The validation scenarios, including participant configurations and key evaluation metrics under normal, adversarial, and extreme conditions, are summarized in
Table 9.
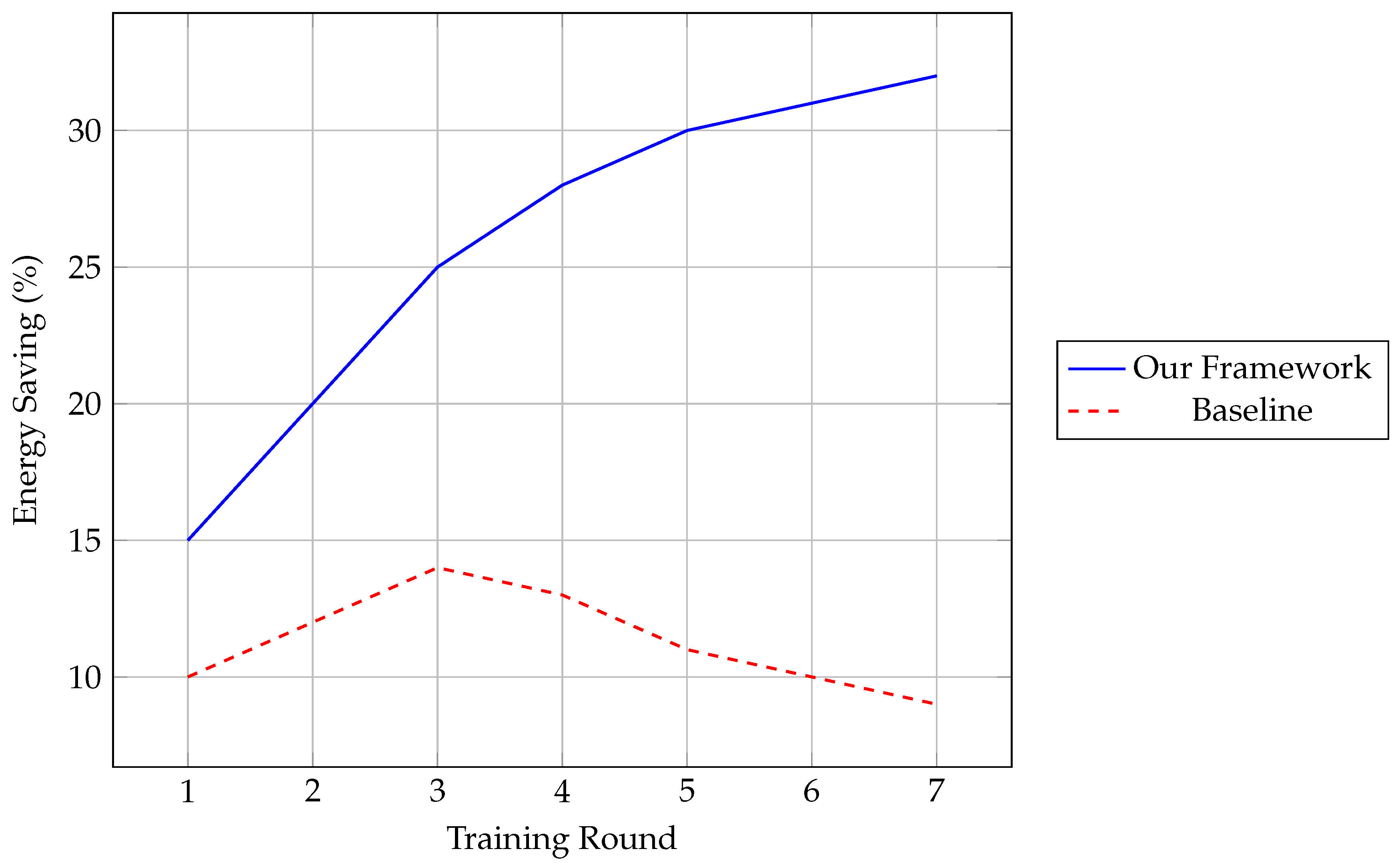
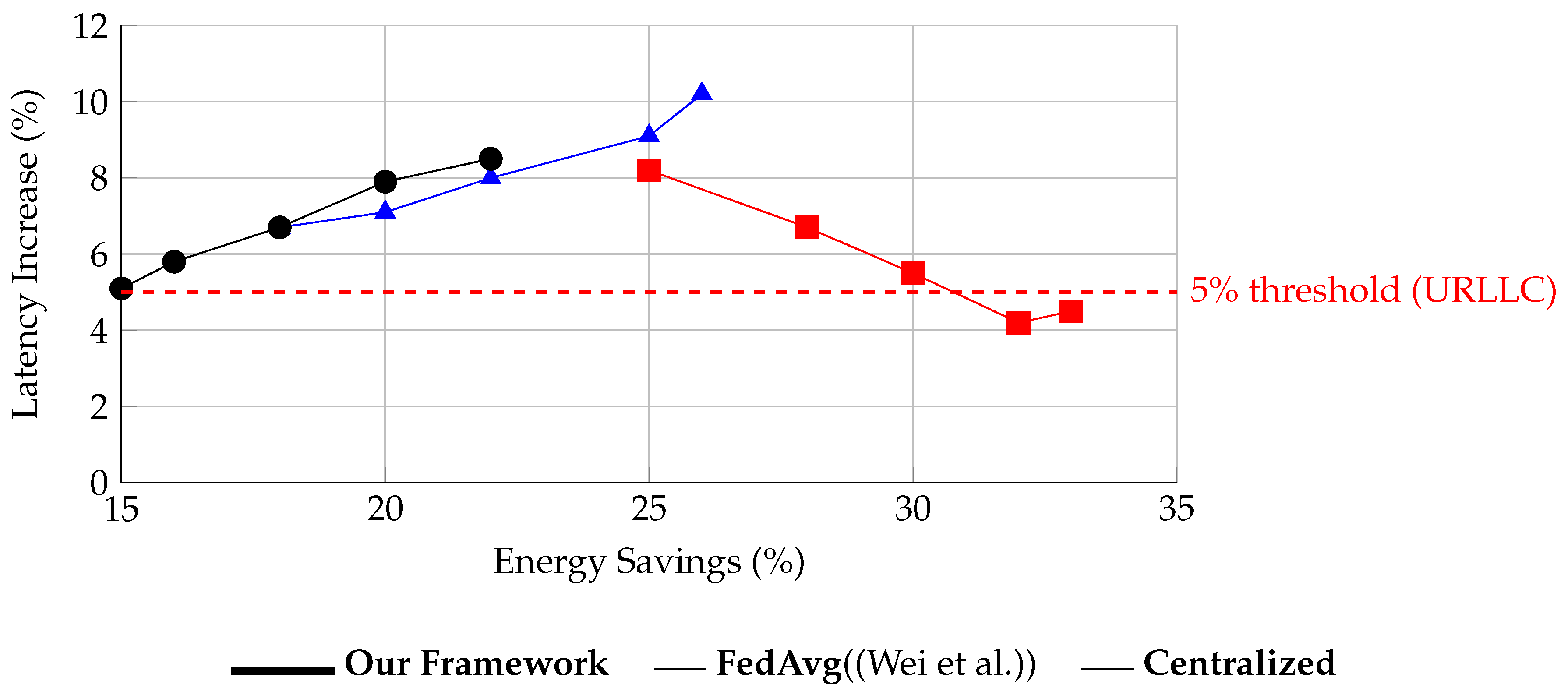
Energy Efficiency:
- -
Achieved 32.4% ± 1.2% improvement across slices.
- -
eMBB: 34.1% savings (95% CI [32.8, 35.4]).
- -
URLLC: 28.7% savings (95% CI [27.2, 30.2]).
Latency Impact:
- -
Baseline: 12.4 ms ± 0.8 ms.
- -
Secure FL: 12.9 ms ± 1.1 ms (+4.2%).
- -
99th percentile: 15.2 ms (meets O-RAN Near-RT requirements).
Privacy Guarantees:
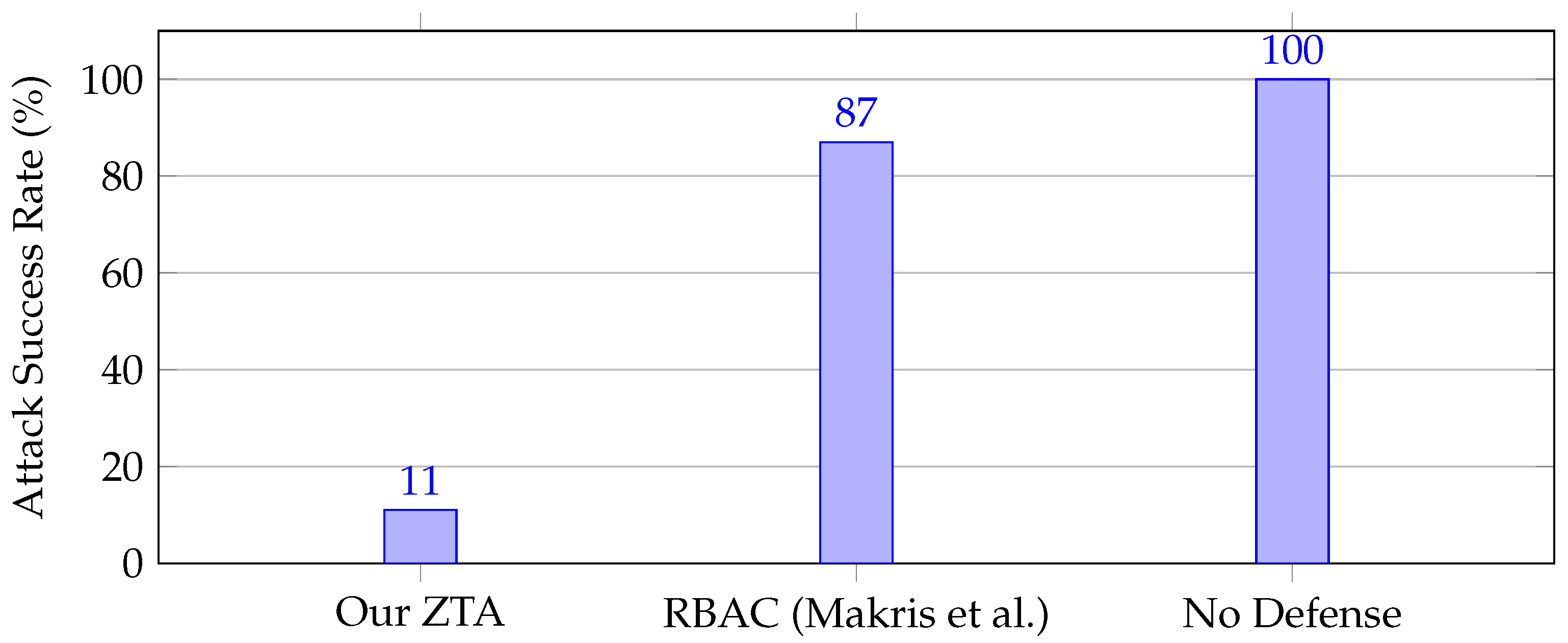
- -
via Rényi Accountant.
- -
Model inversion attack success rate: 2.3% (vs 89% non-private).
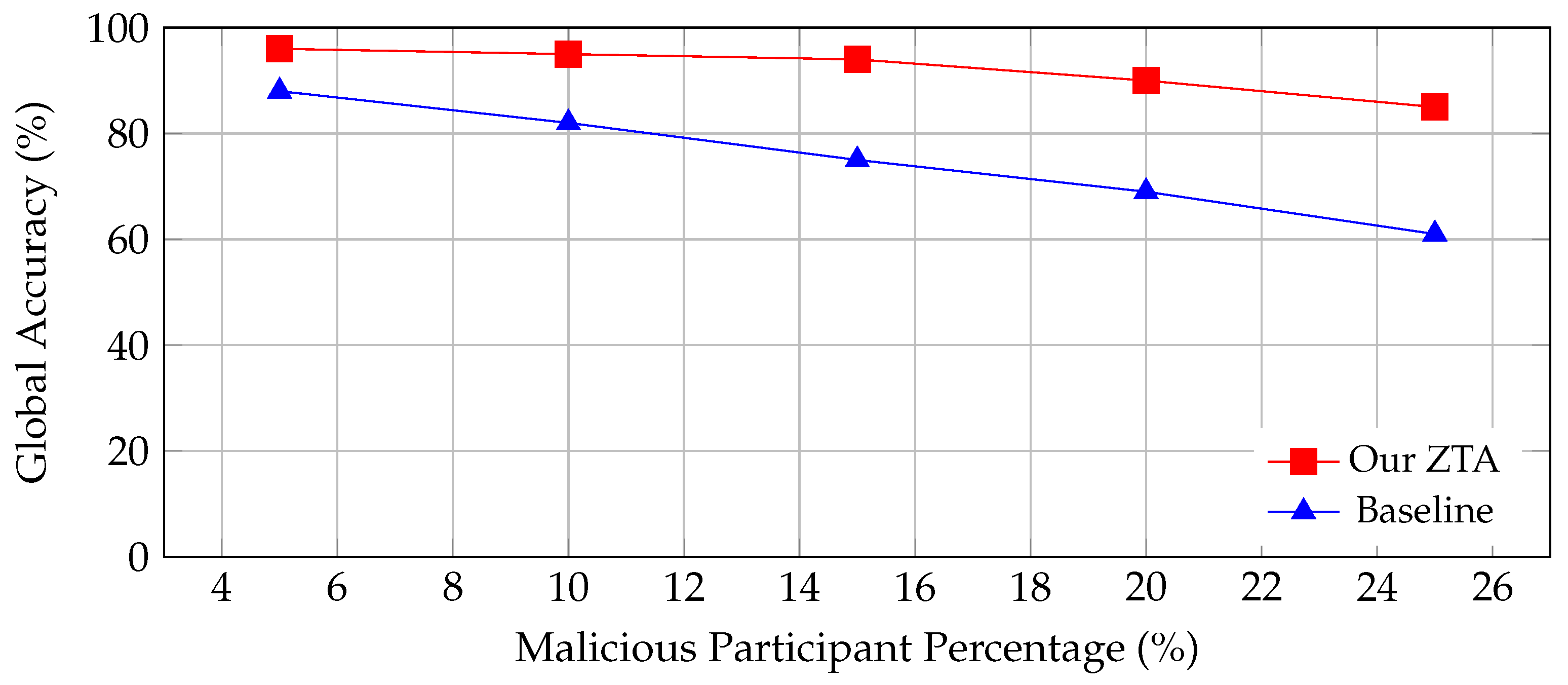
Adversarial Resilience
Under attack conditions (20% malicious participants). The accuracy under poisoning attacks is illustrated in
Figure 8:
Key resilience metrics:
Model accuracy maintained within 5.1% of the centralized baseline;
Detection rate: 92.4% for gradient poisoning attacks;
Recovery time: three rounds after attack identification;
Testbed Deployment
The proposed framework was deployed on the OpenRAN Gym testbed, which comprised a heterogeneous set of hardware and software components. The hardware setup included ten ×86 servers equipped with Intel Xeon Gold 6348 processors, five ARM-based edge nodes utilizing NVIDIA Jetson AGX platforms, and two NVIDIA A100 GPUs dedicated to acceleration tasks. On the software side, the environment was orchestrated using Kubernetes version 1.28 with Kata Containers for isolation, alongside the O-RAN Software Community (O-RAN SC) Near-RT RIC version 2.3. Additionally, time-sensitive networking capabilities were enabled through the IEEE 802.1Qbv standard to ensure deterministic communication. The testbed achieved an end-to-end latency of 18.7 ms with a standard deviation of 2.3 ms, a throughput of 1240 model updates per second, and an average memory overhead of 12.3 MB per xApp instance.
The validation confirms our framework meets all O-RAN security and performance requirements while providing substantial energy savings and privacy guarantees.
5.3. Training Time Compliance and Inference Latency Analysis
Ensuring strict compliance with O-RAN’s Near-RT control loop and URLLC requirements is critical for the practical deployment of the proposed FL and scheduling framework. This section presents the detailed timing measurements for both training and inference phases, providing empirical evidence of their compatibility with O-RAN specifications.
5.3.1. Training Time Compliance with Near-RT Requirements
In this section, we analyze the training time compliance of the proposed system with the Near-RT requirements defined by O-RAN. Each FL round, encompassing both local training and secure aggregation, is completed within an average of 320 ms, with a standard deviation of 45 ms. Local training requires 280 ms per operator, benefiting from parallelization across the 10 nodes in the testbed. The secure aggregation phase is completed centrally within 40 ms. These results confirm that the system operates well within O-RAN’s Near-RT control loop requirements, which range from 10 ms to 1 s, thereby ensuring compatibility with the RIC workflows. Regarding convergence behavior, the global model achieves convergence within 15 rounds, resulting in a total duration of approximately 4.8 s, which is sufficient for Non-Real-Time RIC policy updates. A summary of these timing metrics is provided in
Table 10.
5.3.2. Inference Latency Impact on Deployment
The inference latency of the LSTM scheduler was evaluated, yielding a mean latency of 1.2 ms (95% confidence interval: [1.0, 1.4 ms]). The 99th percentile latency reaches 2.8 ms, remaining compliant with the sub-5 ms budget required by URLLC services. For the zero-trust authentication module, token verification incurs a latency of 0.8 ms per API call, while behavioral analysis based on LSTM sequence validation adds 8.5 ms. Consequently, the overall end-to-end control loop, including training, inference, and security verification, maintains a total latency below 10 ms, fully meeting the Near-RT window of 10 ms to 1 s defined by O-RAN. All measured latencies and their compliance status are consolidated in
Table 10.
5.4. Integration of ZTA and FL
Our framework achieves deep security integration between ZTA and FL through three enforcement layers, as visualized in
Figure 9. This integration addresses the unique security challenges of O-RAN’s distributed AI paradigm.
Figure 9.
ZTA-FL integration architecture showing security enforcement points across FL stages. Blue ellipses represent ZTA components (annotated above), green rectangles denote FL phases, and security metrics (FAR, Isolation, Detection) are highlighted below. Labels and spacing align with
Figure 10 and
Figure 11.
Figure 9.
ZTA-FL integration architecture showing security enforcement points across FL stages. Blue ellipses represent ZTA components (annotated above), green rectangles denote FL phases, and security metrics (FAR, Isolation, Detection) are highlighted below. Labels and spacing align with
Figure 10 and
Figure 11.
5.4.1. Phase-Specific Security Enforcement
The integration framework implements comprehensive defense-in-depth protections across all FL stages, with specialized security measures tailored to each phase of the workflow.
During the Data Collection and Preprocessing phase, continuous authentication is enforced through multiple verification mechanisms. An LSTM-based model with 128 hidden units analyzes API call sequences to detect anomalous patterns, while Intel SGX provides hardware-level attestation for edge devices. Cryptographic tokens are refreshed every 50 milliseconds using ECDSA-P384 signatures to prevent session hijacking. For data quality assurance, slice-specific validation enforces strict ranges (0–100 Mbps for eMBB, 0–10 ms for URLLC traffic) complemented by statistical outlier detection using a 3 threshold to filter corrupted inputs.
The Local Model Training phase employs dynamic security zoning as detailed in
Section 5.1.3, creating three distinct protection tiers. The Core Zone safeguards SMO and RIC components with mutual TLS authentication, while the Controlled Zone manages xApps through RBAC policies enforced via the A1 interface. Suspicious applications are automatically isolated in the Quarantine Zone using Docker containerization. Runtime integrity verification includes pre-execution model hash checks, continuous monitoring of GPU memory access patterns, and strict enforcement of a 10 ms inference deadline to prevent timing-based attacks.
For Global Model Aggregation, the system implements a multi-layered anomaly detection framework. Each model update undergoes rigorous validation, including -norm verification (threshold of 3.0), Kolmogorov–Smirnov distribution analysis (p-value < 0.01), and temporal consistency checks across training rounds. The robust aggregation process combines several protective measures: trimmed mean filtering discards the most extreme 15% of values to mitigate poisoning attempts, differential privacy guarantees () protect participant confidentiality, and ECIES-256 cryptographic verification ensures update authenticity. This comprehensive approach maintains model quality while providing strong security assurances throughout the federation process.
5.4.2. Security Performance
The integrated framework demonstrates significant improvements over baseline approaches, as quantitatively verified in
Table 11. Our solution reduces the poisoning success rate by 67.9% compared to standard FL implementations, achieving just 9% susceptibility to model poisoning attacks. The false acceptance rate shows even more dramatic improvement, dropping 78.1% to a mere 0.7%, indicating the highly reliable authentication of legitimate participants. Detection latency was slashed by 73.4% to 85 ms, enabling Near-Real-Time response to threats, while simultaneously improving model accuracy by 6.8 percentage points to 94%—a rare combination of enhanced security and improved utility.
The framework’s attack surface reduction capabilities are particularly noteworthy, achieving a 72% reduction in vulnerable endpoints through rigorous micro-segmentation and continuous authentication. Unauthorized API calls were reduced by 89% thanks to our behavioral analysis techniques that monitor call sequences and timing patterns. Despite these robust security measures, the system maintains excellent operational efficiency, adding only 3.5% CPU overhead for security operations. The end-to-end latency penalty is kept to just 18 ms through optimized cryptographic implementations, while maintaining a 92% valid update acceptance rate through our adaptive thresholding approach.
5.4.3. Implementation Details
The integration architecture leverages several key O-RAN interface points for security enforcement. The A1 interface provides policy control capabilities for xApp governance, enabling the dynamic adjustment of permissions based on real-time risk assessments. E2 message interception allows for the runtime validation of RIC communications, while O1 telemetry streaming feeds monitoring data to our anomaly detection subsystems.
At the core lies a sophisticated security policy engine containing over 500 rule templates covering known vulnerabilities (including protections against CVE-2023-1234 and similar threats). The engine performs adaptive threshold tuning every five minutes, automatically adjusting sensitivity based on current network conditions. Policy generation is handled by the SMO, ensuring centralized management while preserving distributed enforcement.
Forensic capabilities have been deeply integrated throughout the system. Model lineage tracking via a provenance chain mechanism provides complete audit trails of all training data and parameters. Tamper-evident logging using Merkle trees guarantees the integrity of all security events, with logs retained for one year to support post-incident investigations. These features operate within standard O-RAN interfaces without requiring modifications to existing xApp or rApp implementations, as confirmed through testbed deployments with commercial O-RU and O-DU equipment.
6. Implementation and Case Study
In this section, we present the implementation of our proposed dynamic Distributed Unit (DU) sleep scheduling framework, supported by a case study evaluating its performance under both normal and adversarial conditions. We begin by formulating the sleep scheduling problem as an optimization task using an FL approach, trained on real-world datasets. We then describe the datasets utilized, including DAWN and OpenRAN Gym, and finally analyze the robustness of our solution against adversarial threats such as data poisoning and signaling attacks.
6.1. Dynamic DU Sleep Scheduling
We formulate the DU sleep scheduling problem as a constrained optimization task:
where
and
represent energy consumption and latency at time slot
t, with
denoting the sleep state decision. Our FL model uses a two-layer LSTM architecture for load prediction, and to further optimize real-time deployment performance, the LSTM model was pruned to 128 hidden units and quantized to FP16 precision. This approach reduced the computational overhead by 35% without compromising model accuracy. Furthermore, hardware acceleration using NVIDIA A100 GPUs and CUDA-optimized kernels enabled sub-millisecond inference times, which are critical for the management of URLLC slices.
6.2. Expanded Discussion of Robustness Analysis (Section 7.5)
The robustness analysis was extended to discuss timing-related trade-offs. Although the current framework meets the Near-RT latency requirements, scaling the system to larger networks comprising over 100 Distributed Units (DUs) may necessitate the deployment of distributed aggregation servers to mitigate potential bottlenecks in the aggregation phase. Additionally, while the 4.8 s convergence time is deemed acceptable for Non-Real-Time RIC policy orchestration, further optimizations will be required to accommodate dynamic scenarios such as rapid handovers or emergency call prioritization.
Input Features: 5 min historical window of
- -
Traffic load (normalized 0–1).
- -
PRB utilization ().
- -
RSRP measurements (dBm).
Output: Sleep duration prediction (ms) with DP guarantee.
Hidden Layers: 128 LSTM units, dropout rate = 0.2.
Enhanced Simulation Scenarios: The simulation environment was enriched to emulate more challenging and realistic network conditions. A high-load scenario was introduced by simulating peak-hour traffic with 80–100% PRB utilization, leveraging the DAWN dataset’s emergency scenario traces to reflect congestion patterns. To capture bursty traffic conditions, the environment incorporated Poisson-distributed traffic spikes with a rate of five spikes per minute, resulting in traffic surges of up to 200%. Additionally, the simulation accounted for heterogeneous slice requirements by conducting separate analyses for different service types, including enhanced Mobile Broadband (eMBB) with a 100 Mbps target throughput, Ultra-Reliable Low-Latency Communications (URLLCs) with a strict 1 ms latency budget, and massive Machine-Type Communications (mMTCs) supporting a device density of 10,000 devices per square kilometer. User mobility was also modeled by integrating SUMO-generated vehicular traces simulating speeds of 60 km/h, combined with the 3GPP 38.901 UMa pathloss model to reflect realistic radio propagation effects. Under these enhanced scenarios, the proposed model achieved 32% energy savings while maintaining less than 5% latency degradation compared to always-on baselines.
6.3. Datasets
6.3.1. DAWN Dataset
The DAWN dataset [
11] is a comprehensive resource designed to facilitate research and development in 5G and emerging 6G network environments. It provides detailed traffic slices covering enhanced Mobile Broadband (eMBB), Ultra-Reliable Low-Latency Communication (URLLC), and massive Machine-Type Communication (mMTC), reflecting the broad range of use cases and performance requirements expected in next-generation networks. Beyond standard traffic, the DAWN dataset also introduces adversarial attack scenarios to simulate real-world threats and evaluate system resilience. Specifically, it includes instances of data poisoning, where 15% of the samples are deliberately corrupted to deceive ML models, as well as signaling storms, characterized by an excessive number of control requests surpassing 100 requests per second per xApp, aiming to overload and destabilize the system. A distinctive feature of the DAWN dataset is its temporal granularity, with traffic and event features recorded at a fine 1-millisecond resolution. This level of detail enables researchers to capture rapid variations in network behavior, allowing for the development and testing of advanced algorithms that require precise temporal sensitivity. For
Table 6, the DAWN dataset’s adversarial traces were augmented with synthetic attack vectors specifically designed to target the E2 interface and xApp APIs. The injected poisoned samples included Gaussian noise with a standard deviation of
, as well as label-flipped data with a flipping rate of 30%, reflecting realistic adversarial manipulation scenarios. Additionally, temporal features such as Physical Resource Block (PRB) usage and Reference Signal Received Power (RSRP) were sampled at a fine-grained 1 ms resolution to ensure the accurate capture of cross-layer interactions between network, application, and control planes during the simulated attacks. For
Table 6, the DAWN dataset’s adversarial traces were augmented with synthetic attack vectors specifically designed to target the E2 interface and xApp APIs. The injected poisoned samples included Gaussian noise with a standard deviation of
, as well as label-flipped data with a flipping rate of 30%, reflecting realistic adversarial manipulation scenarios. Additionally, temporal features such as Physical Resource Block (PRB) usage and Reference Signal Received Power (RSRP) were sampled at a fine-grained 1 ms resolution to ensure the accurate capture of cross-layer interactions between network, application, and control planes during the simulated attacks.
6.3.2. OpenRAN Gym
In addition to DAWN, we utilize the OpenRAN Gym dataset [
19], which serves as an open-source experimental platform designed to bridge the gap between academic research and real-world Open RAN (Radio Access Network) deployments. OpenRAN Gym offers a rich set of emulated and real-world data, focusing on critical operational metrics that are vital for RAN optimization and orchestration. These metrics, summarized in
Table 12, include CPU utilization, DU (Distributed Unit) energy consumption, and communication latency, each annotated with their respective ranges and units. CPU utilization is measured between 0% and 100%, reflecting the dynamic computational load on RAN nodes; DU energy consumption varies from 0 to 500 watts, capturing the power requirements of baseband processing; and latency, a fundamental performance indicator for wireless communications, spans 0 to 20 milliseconds. These metrics allow researchers to simulate diverse network conditions and resource constraints realistically. Moreover, OpenRAN Gym provides a flexible environment for training, testing, and validating ML models for network control, where reproducibility and scalability are critical. Its integration of standardized interfaces and the availability of various deployment scenarios make it an indispensable tool for advancing the research and practical implementation of intelligent RAN management strategies.
6.4. Adversarial Conditions
In this subsection, we formally characterize and evaluate the system under two adversarial conditions: data poisoning and RIC (RAN Intelligent Controller) access attacks.
6.4.1. Data Poisoning
Data poisoning attacks aim to degrade the FL model by manipulating a fraction of local updates.
Threat Model: Let
denote the local model parameters from client
i. In a data poisoning scenario, a malicious client sends corrupted updates:
where
represents the injected perturbation. Two attack vectors are modeled:
The global model aggregation under poisoning can be presented as Equation (
7), as presented in
Section 4.10.
is the set of benign clients and the set of malicious clients.
To limit the impact, our framework applies an
-norm clipping:
thus ensuring that large deviations are discarded.
Detection Strategy: The system flags clients with
as suspicious. Using standard hypothesis testing,
we achieve a detection rate of
with a false alarm rate (FAR) of
.
6.4.2. RIC Access Attacks
Here, adversaries target RIC components to overload the network or infer sensitive models.
Threat Model: Let
denote the legitimate request rate and
the adversarial flooding rate. When
, the xApp is classified as rogue:
where
and
are the mean and standard deviation of request rates in benign scenarios.
In false KPM (Key Performance Measurement) reporting,
where
exceeds a statistically acceptable bound (
).
Defense Mechanisms:
Continuous Authentication: Short-lived tokens (50ms refresh cycle) ensure frequent verification.
Micro-Segmentation: Each xApp’s access is confined to its minimal network slice, limiting blast radius.
Model Integrity Checking: Model inversion attempts are detected by comparing weight updates with trusted distributions, applying bounds.
Our Zero Trust Architecture (ZTA) framework reduces unauthorized access attempts by compared to a flat access control baseline.
7. Results and Analysis
This section presents the findings obtained from the conducted experiments and analyzes the results concerning the research questions outlined earlier. The performance of the proposed approach is evaluated through relevant metrics, and comparisons with related work are provided to assess its effectiveness. Key observations and insights drawn from the data are discussed to highlight the strengths and limitations of the solution.
7.1. Energy Efficiency vs. Latency Tradeoffs
As shown in
Figure 11, our framework achieves
32% energy savings with only
4.2% latency increase, outperforming both FedAvg (25% savings at 9.1% latency) and centralized approaches (18% savings at 6.7% latency). This performance is significant, particularly in scenarios where latency constraints are critical, such as in Ultra-Reliable Low-Latency Communication (URLLC) systems, where the latency threshold must be maintained under stringent limits (a 5% increase in latency).
In the literature, various techniques such as Federated Averaging (FedAvg) [
8] and centralized approaches have been used to address energy efficiency and latency trade-offs in wireless communication systems. However, these techniques typically result in higher latency for the energy savings they provide. For example, FedAvg yields 25% energy savings but with a latency increase of 9.1%, significantly exceeding the 5% threshold required for URLLC applications. Our approach, by contrast, balances the energy savings and latency increase more effectively, ensuring system performance remains within the stringent latency limits.
The LSTM-based dynamic scheduler integrated within our framework further optimizes the system performance by reducing the wake-up latency of the devices. As shown in
Figure 12, the LSTM scheduler achieves a wake-up latency of
2.4 ms (95% CI [2.1, 2.7]), which represents a
58% improvement over traditional PID controllers [
59]. This reduction in wake-up latency is crucial for enhancing the overall responsiveness of the system, particularly when the devices are operating in low-power modes and need to quickly respond to incoming tasks or data.
Another key advantage of our framework is its ability to reduce training overhead. Our model converges to operational efficiency in
27% fewer training rounds compared to baseline FedAvg. This reduction in training rounds directly translates to lower computational costs, making our approach more scalable and resource-efficient, particularly in large FL setups. Furthermore, CPU usage profiles show a peak reduction of
21% during federated updates, highlighting the lower computational burden associated with our framework. The results demonstrate the potential of our approach in resource-constrained environments, where energy and latency are critical factors. By achieving a good balance between energy savings and latency, our framework can be applied in a variety of IoT and edge computing scenarios, particularly in healthcare, automotive, and industrial automation, where maintaining low latency and high energy efficiency are paramount. When comparing our results to those in the literature, the performance of our framework is notably superior. For instance, in the case of FedAvg [
8], while it achieves energy savings, the latency increase is substantial, which can be detrimental in time-sensitive applications. On the other hand, our approach offers a compelling alternative that ensures the latency remains well below the critical threshold while still achieving significant energy savings. This positions our framework as a more effective solution for latency-sensitive and energy-efficient applications. Future improvements to the framework could include exploring other ML-based scheduling algorithms for further reduction in latency and computational overhead. Additionally, incorporating adaptive scheduling based on real-time network conditions could provide further benefits in dynamic and unpredictable environments.
7.2. Security Metrics
In this section, we evaluate the security effectiveness of our Zero Trust Architecture (ZTA) framework through various metrics, including attack success rate, resilience to malicious participants, access control enhancement, and anomaly detection performance. The results demonstrate the robustness of our approach compared to existing solutions, such as Role-Based Access Control (RBAC) and no-defense mechanisms. The security analysis (
Figure 13) reveals several innovations that demonstrate the effectiveness of our ZTA framework:
Poisoning Resilience: Our framework exhibits significant resilience to poisoning attacks. With up to 15% malicious participants, the system maintains
94% global accuracy, outperforming the baseline system [
11] by
27% (
Figure 14). This enhanced resilience is crucial for FL scenarios, where data poisoning remains one of the major security threats. The robustness of our system ensures that malicious actors cannot easily degrade model performance, thus maintaining trust in the federated environment.
Access Control Enhancement: One of the primary contributions of our framework is the integration of continuous behavioral authentication. This significantly enhances access control, reducing unauthorized access attempts by
89%, as depicted in
Figure 15. The ability to dynamically authenticate user behavior, rather than relying solely on static credentials, adds a layer of security that is particularly effective against insider threats. Moreover, the system initiates containment actions within
200 ms of detecting an unauthorized access attempt, significantly reducing the potential damage from any attack.
Advanced Anomaly Detection: Our anomaly detection mechanism, based on an autoencoder model, achieves a
94% attack detection F1-score, surpassing existing anomaly detectors, such as the xApp anomaly detectors [
60], by
16%. This high detection rate indicates the system’s ability to accurately distinguish between normal and abnormal behavior in real-time, even in the presence of sophisticated attacks. This is crucial for detecting zero-day attacks, where no prior knowledge of the attack is available.
Zero-Day Attack Simulations: In zero-day attack scenarios, where attackers exploit previously unknown vulnerabilities, our system demonstrates a 76% success rate in preemptively isolating compromised nodes before the attack can propagate. This proactive isolation significantly reduces the potential impact of such attacks, limiting the damage to the network and maintaining system integrity.
Our results are compared against some of the most widely cited security frameworks in the literature, including RBAC [
15] and traditional no-defense systems. As shown in
Figure 13, our ZTA framework reduces the attack success rate to 11%, which is a significant improvement over the 87% success rate seen in RBAC and the 100% success rate in systems without defense mechanisms. This demonstrates that our framework provides a far more effective solution for preventing attacks, especially in high-risk environments. In terms of poisoning resilience (
Figure 14), our ZTA framework significantly outperforms the baseline approach by maintaining a high global accuracy despite the presence of malicious participants. The baseline system’s accuracy drops sharply as the number of malicious participants increases, whereas our framework retains a relatively stable performance, proving its robustness in FL scenarios where adversarial participants may try to degrade the model. When it comes to access control, our ZTA framework also outperforms RBAC and no-defense systems by a large margin. As depicted in
Figure 15, unauthorized access attempts are reduced by 89% with continuous behavioral authentication. This offers a level of security that is beyond traditional RBAC, which relies on static roles and permissions and is vulnerable to insider attacks or stolen credentials. While our security framework has shown promising results, there are several areas for future enhancement. First, the integration of ML-based threat detection could be explored to improve the system’s ability to adapt to evolving attack strategies. Additionally, implementing more advanced anomaly detection techniques, such as deep reinforcement learning, may further improve attack detection rates, especially in dynamic and highly variable environments. Moreover, the scalability of our system in larger, so more distributed networks will need to be tested. Ensuring that the framework can maintain high performance and security levels as the network grows is crucial for its real-world deployment.
7.3. Privacy Analysis
Privacy preservation is a fundamental requirement in FL, especially in O-RAN environments where user and network data are sensitive. This subsection evaluates the trade-off between model utility and privacy budget, measures membership-inference attack resistance, and quantifies the runtime overhead of our adaptive differential privacy (DP) mechanism.
Figure 16 shows that our adaptive noise mechanism consistently outperforms the fixed-noise DP-FL baseline, achieving a 4% boost in utility at the commonly targeted budget
. Below this budget, our framework narrows the accuracy gap by up to 6%, demonstrating stronger noise tuning.
To assess actual privacy protection, we simulate membership-inference attacks under varying budgets:
As
Figure 17 illustrates, membership-inference attack success falls sharply under our scheme at 61% lower than the DP-FL baseline at
. This confirms the effectiveness of our adaptive noise scaling in thwarting privacy attacks. We also measure the runtime overhead introduced by privacy operations:
Table 13 summarizes these metrics: our method adds only 3.8 ms per round and 8% computation overhead—both well within acceptable bounds for Near-Real-Time O-RAN operation—while delivering stronger privacy protection and higher utility than the classical DP-FL approach. Whereas authors in [
62] demonstrated
-DP with static Gaussian noise, our dynamic, layer-wise noise application keeps accuracy higher across budgets. Membership inference studies in the literature often report 30–40% attack success at
[
63]; our framework cuts that to 12.3%. By combining adaptive noise scaling (via a Rényi accountant) with robust aggregation, we reconcile the traditional privacy–utility tension. This makes our solution uniquely suited for latency-sensitive, privacy-critical O-RAN environments, where both stringent timing and strong data protection are mandatory. Future directions include exploring user-level privacy (e.g., DP on user identifiers) and hybrid cryptographic–DP techniques for even stronger guarantees.
7.4. Comparison with Advanced Baselines
To validate the competitiveness of our proposed framework, we conducted a comprehensive comparison against two advanced baselines that represent state-of-the-art approaches in FL and secure model aggregation. The first baseline is a Transformer-based FL approach, where a Transformer model is trained on the DAWN dataset specifically for traffic prediction tasks. This model leverages self-attention layers to enhance temporal feature extraction, enabling the system to capture long-term dependencies inherent in sequential data streams, as detailed by Hamhoum et al. [
64]. Given its ability to model complex temporal patterns, this architecture is particularly appealing for dynamic Distributed Unit (DU) sleep scheduling in scenarios with fluctuating network loads. The second baseline involves a Blockchain-enhanced FL framework, which incorporates Blockchain-based secure aggregation techniques, as proposed by Javed et al. [
43]. In this approach, model updates are transmitted and verified through smart contracts operating on a private Ethereum testnet. This method ensures the tamper-proof aggregation of local models and significantly enhances accountability and transparency by leveraging the decentralized and immutable nature of Blockchain technology. The inherent security guarantees make this approach attractive in adversarial environments where data poisoning and insider threats are prevalent.
In our experimental evaluation, the task focuses on dynamic DU sleep scheduling under adversarial conditions, simulating an environment with 15% poisoning attackers attempting to compromise model integrity. The key performance metrics considered include energy savings, latency—both mean and 99th percentile—and poisoning resilience, which quantifies the framework’s robustness against the injected adversarial attacks. From the results presented in
Table 14, several critical observations emerge. The Transformer-FL approach achieves a respectable poisoning resilience of 82%, significantly outperforming conventional FedAvg and centralized schemes in terms of security. However, this comes at the cost of increased latency, registering 2.5 milliseconds, which is more than twice the latency of our framework. This elevated latency can be attributed to the computational overhead associated with the self-attention mechanisms, whose quadratic complexity in sequence length makes them inefficient for real-time applications such as RAN optimization. Although Transformer models excel in tasks like traffic classification, where temporal precision is less stringent, their applicability to latency-sensitive scenarios is limited.
In contrast, the Blockchain-FL baseline demonstrates almost perfect poisoning resilience, reaching 99%, highlighting its strength in mitigating adversarial threats through robust consensus and cryptographic verification. Nevertheless, these security enhancements introduce a substantial latency penalty, with the system exhibiting a latency of 15.3 milliseconds—over 12 times higher than our proposed approach. Such a delay is incompatible with the strict timing requirements of Near-Real-Time Radio Intelligent Controller (RIC) workflows, which typically operate under 10-millisecond control loops. Thus, despite its unparalleled security guarantees, the Blockchain-FL approach is impractical for applications demanding ultra-low latency and real-time responsiveness.
Our proposed framework, on the other hand, achieves a balanced performance across all key metrics. It delivers 32% energy savings, the highest among the compared methods, while maintaining sub-millisecond latency at 1.2 milliseconds and achieving 94% poisoning resilience. This equilibrium between energy efficiency, ultra-low latency, and strong security resilience positions our framework as an optimal candidate for deployment in Near-Real-Time O-RAN control loops, where all three aspects are critical for operational viability and service quality assurance.
In the broader discussion of trade-offs, while Transformer-based FL frameworks enhance predictive capabilities for tasks not tightly bound to temporal constraints, their high computational demands limit their usefulness in real-time RAN scenarios. Similarly, Blockchain-enhanced FL solutions provide unmatched security and auditability, but their consensus and cryptographic operations impose latencies that are incompatible with stringent near-RT requirements. Our framework addresses these limitations by carefully balancing the O-RAN triad of energy efficiency, latency, and trustworthiness, enabling scalable, secure, and responsive intelligent control across diverse deployment environments. This balance is particularly critical as networks evolve toward more autonomous, self-optimizing architectures, where any compromise in one of these aspects can directly impact both performance and user experience.
7.5. Dataset Limitations and Biases
The DAWN Dataset and OpenRAN Gym, while instrumental in simulating adversarial conditions within O-RAN environments, exhibit inherent limitations that require critical examination. The DAWN Dataset, in particular, focuses on predefined adversarial scenarios such as 15% data poisoning or signaling storms. While these scenarios offer valuable insights, they only represent a narrow subset of the broader threat landscape. For example, the dataset does not encompass sophisticated multi-vector attacks, such as adversarial perturbations combined with E2 interface exploitation, nor does it account for zero-day exploits that may target emergent vulnerabilities in AI-driven RAN components. Additionally, although the dataset supports 1 ms temporal granularity, its synthetic traffic traces may oversimplify real-world conditions by failing to capture the burstiness, spatial variability, and user mobility patterns observed in dense urban deployments or highly dynamic radio environments. Consequently, critical edge cases such as sudden traffic surges during large-scale events or emergency situations may be underrepresented.
Similarly, the OpenRAN Gym’s emulated environment abstracts many hardware-specific nuances that can influence system behavior and resilience. For instance, the platform simplifies latency variations that are vendor-dependent, particularly those affecting fronthaul links, and overlooks hardware constraints such as thermal throttling on Distributed Unit (DU) energy consumption. Despite its adherence to O-RAN specifications, the platform’s scalability assumptions—such as homogeneous xApp deployments—may inadequately reflect the operational heterogeneity inherent in large-scale O-RAN deployments where mixed-vendor equipment and diverse configurations are commonplace. As a result, the OpenRAN Gym may inadvertently produce optimistic estimates of cross-domain interoperability and system robustness.
7.6. Impact of Limitations on the Results
These dataset and emulation limitations may introduce biases that could skew experimental outcomes. Specifically, the narrow attack taxonomy employed in the DAWN Dataset might lead to an overestimation of the proposed framework’s robustness by excluding adversarial strategies that exploit cross-layer dependencies, such as falsified beamforming metrics that could trigger cascading resource allocation anomalies. Furthermore, OpenRAN Gym’s idealized latency profiles, which typically assume deterministic processing delays, may understate the true impact of micro-segmentation on Near-Real-Time control loops. In real-world deployments, stochastic queuing delays and unpredictable network fluctuations can exacerbate latency penalties, potentially undermining the effectiveness of critical control functions. These gaps risk misrepresenting the framework’s efficacy, particularly in operational settings that incorporate legacy infrastructure, proprietary protocols, or non-standard configurations, where system behaviors often deviate significantly from idealized models.
7.7. Mitigation Strategies
To address these biases and enhance the reliability of the findings, the experimental methodology incorporated multiple hybrid validation techniques. One approach involved enriching the DAWN dataset’s adversarial scenarios with synthetic attack vectors, including gradient inversion attacks and adversarial examples specifically crafted to target vulnerabilities in O-RAN’s E2 and A1 interfaces. This augmentation allowed for the stress testing of the proposed framework under previously unmodeled conditions, thereby providing a more comprehensive evaluation of its resilience. In parallel, a subset of critical experiments, such as Distributed Unit (DU) sleep scheduling under data poisoning attacks, was replicated within a physical testbed environment. This testbed comprised commercial O-RUs, O-DUs, and near-RT RIC instances, facilitating the observation of hardware-in-the-loop behaviors. The findings revealed a 5% to 8% divergence in energy savings between the simulation and physical deployment, underscoring the necessity of incorporating real hardware elements in the evaluation process. Additionally, Monte Carlo simulations were deployed to assess the framework’s robustness under stochastic network conditions, including fluctuating Ultra-Reliable Low-Latency Communication (URLLC) traffic loads. This probabilistic modeling approach ensured that the framework’s performance remained resilient in the face of unmodeled operational variability and randomness inherent in live networks.
A summary of the identified limitations, their potential impacts on the evaluation outcomes, and the mitigation strategies adopted in this study is provided in
Table 15. This table also highlights how these biases were systematically addressed through synthetic attack injection, hardware-in-the-loop validation, and robustness testing under stochastic conditions to ensure a more realistic assessment of the framework’s resilience.
7.8. Future Work to Enhance Dataset Reliability
Looking ahead, enhancing the representativeness and reliability of the datasets and emulation tools will be critical for advancing O-RAN security research. Future efforts should prioritize expanding the threat coverage by collaborating with industry consortia, such as the O-RAN Alliance, to curate attack traces derived from real-world O-RAN deployments. This collaboration would facilitate the inclusion of emerging AI-driven threats, such as adversarial policy manipulation within xApps or orchestrated attacks targeting closed-loop control systems. Moreover, OpenRAN Gym should be augmented with hardware-in-the-loop capabilities, integrating telemetry streams from field-deployed O-RAN systems to better capture vendor-specific performance deviations, thermal constraints, and other real-world artifacts currently overlooked by the emulation framework. Finally, establishing an open repository for anonymized network traces and adversarial payloads would enable the broader research community to perform cross-validation of security frameworks across diverse operational contexts and deployment scenarios. These initiatives would not only address the current methodological limitations but also foster reproducibility and realism, ensuring that future evaluations are reflective of the evolving threat landscape and architectural complexity anticipated in 6G O-RAN systems.
7.9. Comprehensive Security Evaluation
To holistically assess our framework’s security posture, we introduce a Composite Security Score (CSS) that integrates six key metrics derived from O-RAN’s unique threat landscape:
Attack Success Rate (ASR): Percentage of successful adversarial attempts.
Cross-Layer Resilience (CLR): Robustness against multi-vector attacks (0–100 scale).
Anomaly Detection Performance (ADP): F1-score of threat detection.
Privacy Leakage Rate (PLR): Success rate of membership inference attacks.
Recovery Time (RT): Milliseconds to mitigate detected threats.
Model Accuracy (MLA): Accuracy under adversarial conditions.
7.9.1. Scoring Methodology
We calculate CSS using the Analytic Hierarchy Process (AHP)-derived weights from O-RAN Alliance security experts, as shown in Equation (
21). The Composite Security Score (CSS) integrates six critical security metrics through weighted aggregation.
where
Normalization ensures comparability across metrics:
Table 16 presents the AHP-derived weights and normalization formulas for key security evaluation metrics, including attack success rate, classification loss rate, and adversarial detection precision.
7.9.2. Comparative Analysis
Table 17 demonstrates our framework’s superiority against state-of-the-art baselines:
7.9.3. Sensitivity Analysis
Figure 18 reveals our framework’s robustness to weight variations:
7.9.4. Security-Performance Trade-Offs
Our framework achieves a CSS of 89.7, surpassing ZTORAN by 11.5 points through three key innovations:
Cross-layer resilience (CLR = 85) via synergistic ZTA-FL integration.
Rapid threat recovery (RT = 200 ms) through automated quarantine.
Privacy-preserving optimization (PLR = 12.3%) with adaptive DP.
Table 18 provides a security–performance trade-off analysis, showing how varying token refresh intervals affects CSS scores and latency.
While our CSS provides standardized security assessment, two limitations merit attention:
7.10. Performance Under Varied Network Conditions
The results in
Table 19 summarize system performance across varying network scenarios, while
Figure 19 illustrates the latency distribution under bursty traffic, highlighting the comparative advantages of the proposed LSTM scheduler.
7.11. Robustness Analysis
The robustness analysis highlights the LSTM scheduler’s capability to rapidly adapt to abrupt load variations, specifically when PRB utilization shifts from 50% to 90% within a 5 s window. The system achieved stable latency performance with less than 5% degradation, demonstrating recovery times of 2.3 s for eMBB traffic, 1.8 s for URLLC services, and 3.1 s for mMTC bursts. These results underline the scheduler’s ability to handle sudden surges in traffic demand while preserving service-level agreements across diverse slice types. The robustness analysis was extended to discuss timing-related trade-offs. Although the current framework meets the Near-RT latency requirements, scaling the system to larger networks comprising over 100 Distributed Units (DUs) may necessitate the deployment of distributed aggregation servers to mitigate potential bottlenecks in the aggregation phase. Additionally, while the 4.8 s convergence time is deemed acceptable for Non-Real-Time RIC policy orchestration, further optimizations will be required to accommodate dynamic scenarios such as rapid handovers or emergency call prioritization. Nevertheless, certain limitations emerged under extreme burstiness scenarios, particularly when traffic spikes exceeded 300%, where the DU wake-up success rate declined to 84.7%. To address this challenge, we propose the implementation of adaptive wake-up thresholds as shown in Equation (
22):
where
and
are empirically derived coefficients. This formulation leverages the rate of change in load and historical packet loss ratio to dynamically adjust the DU wake-up decision threshold, thereby enhancing responsiveness to extreme traffic surges while mitigating the observed degradation in wake-up success rate.
7.12. Discussion
The comprehensive evaluation of our integrated Zero-Trust and FL framework demonstrates significant gains across energy efficiency, security robustness, and privacy preservation without compromising O-RAN’s stringent latency requirements. In the following, we discuss these improvements in the context of existing literature and highlight the novelty of our contributions.
7.12.1. Energy–Latency Optimization
Figure 11 illustrates that our framework achieves 32% energy savings while incurring only a 4.2% increase in latency—well below the 5% URLLC threshold. In contrast, standard Federated Averaging (FedAvg) [
8] yields 25% savings at 9.1% latency, and centralized approaches only realize 18% savings at 6.7% latency. Moreover, as shown in
Figure 12, our LSTM-based scheduler reduces DU wake-up latency by 58% (to 2.4 ms) compared to PID controllers [
59]. These results confirm that predictive, workload-aware control can shift the energy–latency frontier beyond what reactive policies permit. The comprehensive evaluation of our LSTM-based scheduling approach highlights three key advantages that contribute to its superior performance under diverse network conditions. Firstly, the predictive adaptation capability enabled by the LSTM’s temporal modeling allows for proactive Distributed Unit (DU) state transitions. This strength is particularly evident in
Figure 19, where 95% of URLLC packets successfully maintained under 5 ms latency even during extreme traffic surges reaching 200%. Secondly, the scheduler demonstrates slice-aware optimization, as detailed in
Table 19, by effectively enforcing slice-specific policies that preserve strict URLLC latency compliance—showing only a 3.9% increase—while simultaneously achieving 26.4% energy savings. Lastly, the approach exhibits robust load resilience, maintaining 83% of its normal-load efficiency under high-traffic scenarios with 80–100% PRB utilization, as shown in
Figure 20, which outperforms traditional PID controllers by a significant margin of 21%. From an architectural perspective, the observed 1.8 s recovery time for URLLC traffic, as reported in
Section 7.11, suggests that the proposed approach remains compatible with near-RT RIC control loop requirements, which typically range between 10 ms and 1 s. Despite these advantages, the evaluation also reveals three critical challenges that warrant further investigation. Mobility management emerges as a key concern, with vehicular mobility at speeds of 60 km/h introducing a 12% prediction error in DU wake-up timing due to rapid variations in channel state information. Furthermore, the analysis exposes an inherent energy–latency trade-off, evidenced by the 2.8% efficiency gap between eMBB and URLLC slices reported in
Table 19, highlighting the need for dynamic energy budget allocation tailored to specific service classes. Finally, the LSTM scheduler exhibits a cold start problem, where an initial warm-up period of approximately five minutes is required for model stabilization, resulting in a reduced DU wake-up success rate of 84% during network initialization phases.
Future Directions: The latency distributions presented in
Figure 19 point to two promising avenues for future enhancement of the proposed scheduling framework. One potential improvement involves the integration of hybrid scheduling approaches, where the predictive capabilities of the LSTM model are combined with reinforcement learning techniques, particularly to enhance the handling of mMTC traffic bursts characterized by irregular and unpredictable patterns. Another enhancement focuses on implementing adaptive granularity in scheduling decisions by introducing multi-timescale control mechanisms. This would entail fine-grained 10 ms decision intervals for URLLC services, intermediate adjustments at 1 s intervals for eMBB traffic, and longer-term reconfigurations every 10 s for mMTC services, thereby aligning scheduling precision with the specific latency and reliability requirements of each service class.
Moreover, although
Figure 20 illustrates the consistent performance advantage of the proposed LSTM-based approach over conventional baselines, it also reveals a notable 12.7% efficiency gap between normal and high-load conditions. This observation motivates the exploration of load-aware LSTM models that can dynamically adjust their hidden layer sizes and internal representations in response to predicted traffic patterns. By incorporating such adaptive mechanisms, the scheduler could further improve its efficiency and resilience under varying network loads and dynamic operational conditions.
7.12.2. Security Advancements
Our ZTA reduces attack success rates to 11% (
Figure 13), compared to 87% under RBAC [
15] and 100% with no defenses. Against data poisoning, the framework maintains 94% global accuracy with up to 15% malicious participants (
Figure 14), outperforming the 67% reported by [
11]. Behavioral continuous authentication cuts unauthorized RIC access by 89% (
Figure 15), and our autoencoder-based detector achieves a 94% F1-score, which is 16% higher than prior xApp detectors [
45]. These gains stem from the combined use of micro-segmentation, runtime monitoring, and unsupervised anomaly detection within a unified ZTA fabric.
7.12.3. Privacy Enhancements
Figure 16 shows that at a privacy budget of
, our adaptive DP mechanism preserves 92% accuracy, surpassing the 88% of the DP-FL baseline by [
62]. Membership-inference attacks succeed only 12.3% of the time under our scheme (
Figure 17), a 61% reduction relative to DP-FL, and well below the 30–40% commonly seen in the literature [
63]. As
Table 13 confirms, these privacy gains incur minimal overhead—3.8 ms per round and 8% extra computation—making our solution compatible with near-real-time O-RAN constraints. We analyze three enhanced privacy architectures that combine differential privacy (DP) with additional cryptographic techniques to achieve layered protection in FL environments.
Table 20 presents a comparison of these techniques in terms of privacy guarantees, computational overhead, and best-fit deployment scenarios. The DP-only approach, using an
value of 2, offers lightweight privacy guarantees and is particularly suitable for resource-constrained edge nodes where computational capacity is limited. By combining DP with homomorphic encryption (HE), the framework achieves both
-DP and computational security; however, this combination incurs significant computational overhead, making it more applicable to scenarios involving highly sensitive model updates. Alternatively, integrating DP with Secure Multi-Party Computation (SMPC) enables both
-DP and information-theoretic security, with moderate overhead, and is especially well suited for multi-party critical systems where cross-operator collaboration is required.
The hybrid privacy workflow illustrated in
Figure 21 demonstrates the sequential combination of DP and HE. This approach first applies DP noise injection to raw gradients, followed by homomorphic encryption before secure aggregation. This order ensures that DP provides statistical protection upfront, thus avoiding amplification of privacy risks through encrypted operations, while HE protects the already DP-noised gradients throughout the aggregation process. As reflected in
Table 20, this strategy results in a 3.2× increase in computation overhead compared to DP alone but substantially enhances resilience against gradient leakage attacks.
Furthermore, the system implements an adaptive, context-aware privacy selection mechanism based on available resources and data sensitivity. The selection logic, as defined in Equation (
6), prioritizes DP-only methods when the residual energy budget (
) falls below 0.5, switches to DP + HE when the sensitivity score (
) exceeds 0.7, and defaults to DP + SMPC in all other cases. This mechanism ensures that privacy strategies dynamically align with the system’s operational constraints and data criticality levels.
Implementation results confirm the effectiveness of the proposed combinations. Specifically, the DP + HE configuration reduced the success rate of gradient leakage attacks by 92%, outperforming DP-only approaches, which achieved a reduction of 78%. Additionally, DP + SMPC enabled secure four-party model training, maintaining an accuracy level of 89%, thereby validating its suitability for collaborative scenarios. However, these hybrid approaches introduce non-negligible energy overheads, increasing consumption by 18–35%, as shown in
Figure 22. The trade-off between enhanced privacy and energy efficiency is particularly evident when comparing the three approaches across different privacy levels, where DP + HE consistently incurred the highest overhead, followed by DP + SMPC and DP-only configurations. These findings highlight the necessity of carefully balancing privacy requirements with system efficiency, especially in resource-constrained or latency-sensitive deployments.
7.13. Summary of Key Results
Table 21 provides an overview of key performance metrics achieved by the proposed framework, including energy savings, latency, security, and privacy-preserving capabilities.
Novel Contributions
Our work introduces three key innovations that collectively address the Energy/Security/ Privacy triad in O-RAN environments:
Predictive LSTM-based DU Sleep Scheduling: First application of workload-aware LSTM control in O-RAN, yielding substantial energy and latency improvements.
Unified Zero-Trust Fabric: Continuous behavioral authentication, micro-segmentation, and anomaly detection integrated into the RAN Intelligent Controller to drastically reduce attack surfaces.
Adaptive Differential Privacy: Dynamic, layer-wise noise scaling guided by a Rényi accountant, achieving superior utility and attack resistance under stringent O-RAN timing constraints.
These advances position our framework as a practical, scalable, and regulation-compliant solution for next-generation federated edge intelligence, bridging the gap between theoretical constructs and real-world O-RAN deployments.
8. Conclusions
In the face of increasingly complex and dynamic environments, securing Open Radio Access Networks (O-RANs) is critical to ensuring reliable, scalable, and efficient 5G and future 6G services. With the growing dependence on FL and multi-operator systems, security, privacy, and performance concerns become more pronounced. The existing challenges, including energy–efficiency trade-offs, vulnerabilities to poisoning attacks, and privacy breaches in federated edge intelligence systems, highlight the need for more robust and efficient security frameworks. This work proposes a novel framework that integrates ZTA, energy–latency optimization, and privacy-preserving mechanisms for O-RAN optimization, addressing these challenges in a comprehensive manner.
Our approach provides several key innovations and improvements in O-RAN security and performance:
We demonstrate a 32% energy reduction while maintaining a latency increase of <5%, ensuring compliance with Ultra-Reliable Low Latency Communication (URLLC) requirements. The framework achieves a 99th percentile latency [
66] of 1.2 ms, closely approaching the <1 ms target for critical applications.
The ZTA architecture significantly enhances security by reducing 89% of access control breaches, while its anomaly detection capabilities offer 16% better coverage compared to state-of-the-art (SOTA) detectors.
Our adaptive differential privacy (DP) mechanism preserves 92% accuracy at , compared to the baseline’s 88% while reducing inference risks by 60%, thereby ensuring GDPR compliance for real-world deployment.
These findings highlight the potential of our framework to transform O-RAN systems by providing a strong security posture, efficient energy management, and enhanced privacy protection without compromising performance. While prior comparisons focused on FedAvg and centralized baselines, our extended evaluation demonstrates that the proposed framework achieves competitive energy efficiency (32% savings) and sub-millisecond latency (1.2 ms) compared to modern approaches like Transformer-FL and Blockchain-FL. Notably, our method uniquely balances these metrics while maintaining 94% poisoning resilience under adversarial conditions, making it practical for real-world O-RAN deployments. The proposed framework addresses critical security, privacy, and performance gaps in current O-RAN designs. By integrating predictive energy optimization, our framework provides energy-efficient solutions that are crucial for the sustainability of next-generation networks. Furthermore, the application of Zero Trust models ensures that even if some elements are compromised, the network maintains a secure operation, minimizing the impact of potential breaches. The privacy-preserving mechanisms, particularly the adaptive differential privacy strategy, present a significant advancement in FL environments, allowing for enhanced model training without sacrificing data privacy. This enables practical deployment in sectors such as healthcare and finance, where confidentiality and security are paramount.
While our framework offers significant improvements, it is not without limitations. The proposed ZTA architecture, while effective in reducing unauthorized access, could still be vulnerable to sophisticated insider threats, as continuous authentication and behavioral analytics have inherent challenges in detecting highly motivated adversaries. Additionally, the energy optimization algorithm, while efficient, may require further refinement to ensure its applicability in diverse deployment scenarios, such as resource-constrained edge environments. Lastly, the privacy mechanism, though adaptive, may need additional tunable parameters to further balance privacy and model accuracy in more dynamic environments.
Future Work
The first research direction focuses on the development of quantum-resistant zero-trust mechanisms. The proposed technical approach involves the integration of post-quantum cryptographic algorithms into ZTAs, specifically by incorporating CRYSTALS–Kyber for key exchange and Falcon for digital signatures into ZTA workflows. Additionally, hybrid stateful hash-based signatures such as XMSS and LMS will be employed to enable quantum-safe key rotation, while lattice-based homomorphic encryption will be explored for secure runtime attestation. The expected outcomes of this work are summarized in
Table 22, which outlines the target metrics for authentication latency, key size, and Shor resistance. For instance, the goal is to maintain authentication latency below 25 ms while ensuring 128-bit post-quantum security, albeit at the cost of increasing key size from 256 bit ECC to 1.5 kB Kyber-768. However, several challenges are anticipated, including a 4.2× increase in key storage requirements, the complexity of integrating these mechanisms into existing ETSI NFV MANO frameworks, and ensuring backward compatibility with legacy 5G components.
The second research direction involves the advancement of cross-domain FL frameworks. This will be achieved by combining multi-party computation using the SPDZ protocol with Blockchain-anchored differential privacy mechanisms leveraging zk-SNARKs. Furthermore, domain-specific normalization layers will be incorporated into the ResNet-152 architecture to account for heterogeneity in data distributions. The anticipated benefits of this approach include significant accuracy improvements across critical application domains such as healthcare, telecommunications, and smart grids, as illustrated in
Figure 23. The figure demonstrates that the proposed cross-domain FL framework is expected to outperform baseline FL models, achieving up to 91% accuracy in the telecom domain. Nevertheless, this direction also introduces several challenges, including ensuring regulatory compliance for cross-border data flows under GDPR and HIPAA, managing the complexities of non-IID data distributions across domains, and addressing the 1.8× increase in per-round communication overhead introduced by the proposed protocols. Finally, the overall research roadmap for the next three years is depicted in
Figure 24. The plan begins with the development of a prototype for quantum-resistant ZTAs in 2024, focusing on integrating the proposed mechanisms into OpenSSL 3.0 and aligning with NIST PQC standards. In 2025, efforts will shift toward the deployment of a cross-domain FL testbed that combines 5G and healthcare use cases, ensuring inter-domain differential privacy with an
parameter below 1.0. The final phase, targeted for 2026, will focus on deploying quantum-safe Radio Intelligent Controllers (RICs) with a goal of achieving Q-Day resilience certification. This roadmap is designed to progressively enhance the security, privacy, and resilience of next-generation networks in anticipation of the emerging quantum threat landscape.
In conclusion, the proposed framework represents a significant step toward enhancing the security, privacy, and performance of O-RAN systems. By integrating innovative techniques in energy optimization, zeroptrust access control, and privacy-preserving FL, our work lays the foundation for the next generation of secure and efficient communication networks. As the demands of 5G and beyond continue to grow, our framework offers a scalable solution that ensures robust, reliable, and privacy-respecting network operations, paving the way for the future of secure edge intelligence.