A Survey of 5G Core Network User Identity Protections, Concerns, and Proposed Enhancements for Future 6G Technologies
Abstract
1. Introduction
1.1. Technological Privacy in the Modern Day
1.2. Focus of This Paper
2. Concerns Related to User Identity and Privacy in 5G Core Networks
2.1. Fifth-Generation Service-Based Architecture and Personally Identifiable Information
2.2. Newly Adopted Technologies
| Identifiers in 5G Communications | ||
|---|---|---|
| Identifier | Applicable Standards | Description |
| Subscription Permanent Identifier (SUPI) | TS 33.501 [21], TS 23.003 [22], TS 22.261 [23], TS 23.316 [24] | A globally unique SUPI is allocated to each subscriber and provisioned in the UDM (Unified Data Management)/UDR (Unified Data Repository). The SUPI may contain an IMSI (International Mobile Subscriber Identity), a network-specific identifier, or other identifiers for specific use cases. It is concealed for privacy and supports roaming and interoperability with (Long-Term Evolution) networks. |
| Subscription Concealed Identifier (SUCI) | TS 33.501, TS 23.316 | The SUCI is a privacy-preserving identifier containing the concealed SUPI. It is used for secure identification in the 5G system. The usage of SUCI for non-3GPP network access is also specified within TS 23.316. |
| Permanent Equipment Identifier (PEI) | TS 23.003, TS 23.316 | The PEI identifies the UE in the 5G system. In 3GPP access modes, the PEI must be either the IMEI (International Mobile Equipment Identity) or IMEISV (International Mobile Equipment Identity Software Version). For non-3GPP access scenarios, the UE sends the IEEE Extended Unique Identifier EUI-64 [25]. |
| 5G-GUTI | TS 33.501, TS 23.003, TS 38.304 [26], TS 36.304 [27], TS 38.331 [28], TS 36.331 [29] | The 5G-GUTI is a temporary identifier assigned by the AMF to the UE. It is structured as [<GUAMI> <5G-TMSI>] (Globally Unique AMF ID) and supports both 3GPP and non-3GPP access. The AMF ensures the uniqueness of the 5G-TMSI within the GUAMI. |
| AMF Name | TS 23.003 | The AMF is identified by a globally unique Fully Qualified Domain Name (FQDN). Each AMF can be associated with one or more GUAMI(s). |
| Data Network Name (DNN) | TS 23.003, TS 23.502 [30] | The DNN is equivalent to an APN (Access Point Name) and is used to select SMF (Session Management Function), UPF (User Plane Function), and N6 (5G Internet Connectivity Interface) interfaces for a PDU Session. |
| Internal-Group Identifier | TS 23.502 | The Internal-Group Identifier associates a UE with groups in the subscription data. It is used for applying group-specific policies in the SMF and AMF. |
| Generic Public Subscription Identifier (GPSI) | TS 23.003 | The GPSI is a public identifier (Phone Number or External Identifier) used to address a 3GPP subscription outside the 3GPP system. It is stored in the subscription data and associated with the SUPI. |
| AMF UE NGAP (Next-Generation Application Protocol) ID | TS 38.413 | The AMF UE NGAP ID is used to identify the UE on the N2 reference point. It is unique per AMF set and may be updated without changing the AMF. |
| UE Radio Capability ID | TS 23.003 | The UE Radio Capability ID uniquely identifies a set of UE radio capabilities. It can be assigned by the UE manufacturer or the serving PLMN. The PLMN-assigned ID includes a Version ID to ensure its validity. |
2.3. Linkability
3. Privacy Enhancement Proposals for 5G Core Networks
Lawful Interception
4. A Look Toward Privacy in 6G Core Networks
- Network Anomaly Detection: With the anticipated massive number of connected devices in 6G networks, there will a significant rise in the need for sophisticated network monitoring. A big contender for addressing this challenge is the use of FL for real-time, automated anomaly detection. However, evaluating and ensuring the accuracy, precision, and recall of these automated threat detection systems are important research questions.
- Regulatory Compliance: Sixth-Generation networks will be connected across geographical borders. This brings with it the need to address differing approaches, laws, and viewpoints regarding privacy and data handling between different countries.
- Security and Privacy in Edge Computing: With the diversity of 6G technology’s targeted use cases, there will be an inherent risk from edge computing to privacy and security. Since edge nodes may serve numerous devices at once, using shared resources, isolation of tasks will be vital for user privacy.
- Risk Assessment Frameworks for 6G Technology: A formal risk assessment framework must be created for 6G technology, as previous models may not fully capture the expansiveness and novel network capabilities of 6G technology. This model must also serve to explain privacy threats and their impact, as well as potential mitigation strategies.
- Privacy Concerns in Smart City and Health Services: Sixth-Generation networks will be handling a variety of potentially sensitive data, across domains such as healthcare, public services, self-driving cars, distributed energy resources, etc. Thus, in order to maintain privacy, there is a critical need for standards on data de-identification.
- Secure IoT Protocols and Energy Efficiency: Sixth-Generation technology aims to become even more efficient in terms of energy use compared to 5G technology and also improve cryptographic security. IoT devices are considered to be resource constrained, however, which means these devices need the ability to be energy efficient without jeopardizing their security by using less secure cryptographic schemes to save power.
4.1. Sixth-Generation Identity Protections
4.2. Implications of AI for Identity Protections in 6G Technology
- P1—Privacy attacks on AI models and private data
- P2—IoT (Internet of Things) edge network and edge AI privacy attacks
- P3—Privacy limitations in cloud computing and storage environments
- P4—Cost of privacy enhancements
- P5—Privacy differences based on location
- P6—Difficulty in defining levels and indicators for privacy
- N1—Difficulty determining the border between personal and non-personal data
- N2—Mixing personal data with non-personal data
- N3—Utility vs. privacy of anonymized data
- N4—Privacy attacks on anonymized and synthetic data
- N5—Data Localization Laws vs. free flow of data.
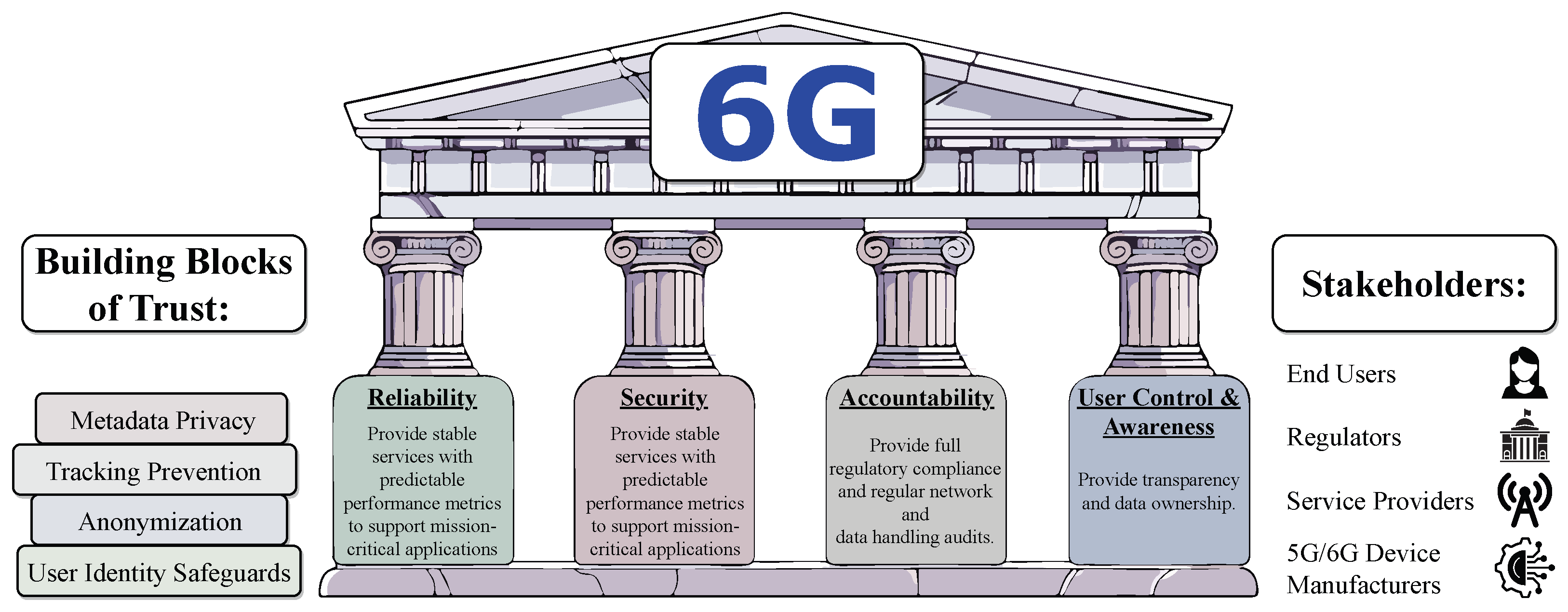
4.3. Trustworthiness in 6G Networks
- Non-Repudiation;
- Immutability;
- Transparency;
- Programmability;
- Modularity;
- Integration.
5. Conclusions
- There exists a strong need to reduce the prevalence and reliance on personal identifiers such as the SUPI (Subscription Permanent Identifier) within 5G/6G Core operations to help better protect user identity. This has the potential to be achieved by replacing the widespread usage of the SUPI between VNFs with decentralized ephemeral identifiers, thereby maintaining 3GPP standard operations, billing and fraud prevention capabilities, and customer service expectations. This would add a layer of identity abstraction for the user on the network to better protect the SUPI and other identifiers from eavesdroppers and unauthorized behavioral tracking and metadata collection.
- Systems can also be designed to leverage the powerful nature of AI to bring enhanced services, experiences, and threat deterrence for users. User datasets must be de-identified to prevent privacy leaks. Continual training methods such as FL preserve user identity protections, as PII is not transmitted to central servers. Concerns may arise from metadata exposure, which may facilitate linkage attacks.
- The creation of a standardized trust architecture between users, providers, and third-party vendors would provide visibility and transparency to 5G/6G operations with regard to the data shared or collected by different network elements. Furthermore, adherence to a strict privacy-by-design rationale for newly developed specifications would help to alleviate issues resulting from untrusted third-party vendors or cloud providers.
- The incorporation of HSMs into 5G/6G infrastructure to enhance the physical-layer security of cryptographic secrets and to enable end-to-end encryption is a further recommendation for enhancing the privacy and data protection capabilities of these systems.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| VNF | Virtual Network Function |
| SBA | Service-Based Architecture |
| CN | Core Network |
| NF | Network Function |
| SA | Standalone |
| SSN | Social Security Number |
| 5G-GUTI | Globally Unique Temporary ID |
| NAS | Non-Access Stratum |
| RNTI | Radio Network Temporary Identifier |
| MAC | Medium Access Control |
| HN | Home Network |
| AKMA | Authentication and Key Management |
| TSN | Time-Sensitive Network |
| AMF | Access and Mobility Function |
| RESTful | Representational State Transfer Application Programming Interfaces |
| PII | Personally Identifiable Information |
| UE | User Equipment |
| SUPI | Subscription Permanent Identifier |
| QoS | Quality of Service |
| PDU | Protocol Data Unit |
| UDM | Unified Data Management |
| UDR | Unified Data Repository |
| IMSI | International Mobile Subscriber Identity |
| LTE | Long-Term Evolution |
| SUCI | Subscriber Concealed Identity |
| PEI | Personal Equipment Identifier |
| IMEI | International Mobile Equipment Identity |
| IMEISV | International Mobile Equipment Identity Software Version |
| 5G-GUAMI | Globally Unique AMF ID |
| FQDN | Fully Qualified Domain Name |
| DNN | Data Network Name |
| APN | Access Point Name |
| SMF | Session Management Function |
| UPF | User Plane Function |
| GPSI | Generic Public Subscription Identifier |
| NGAP | Next-Generation Application Protocol |
| RAN | Radio Access Network |
| SDN | Software-Defined Networking |
| NIST | National Institute of Science and Technology |
| NSA | Non-Standalone |
| PEFMA | Privacy Enhanced Fast Mutual Authentication |
| 5G-AKA | Authentication and Key Agreement |
| HMAC | Hash-Based Message Authentication Code |
| LI | Lawful Interception |
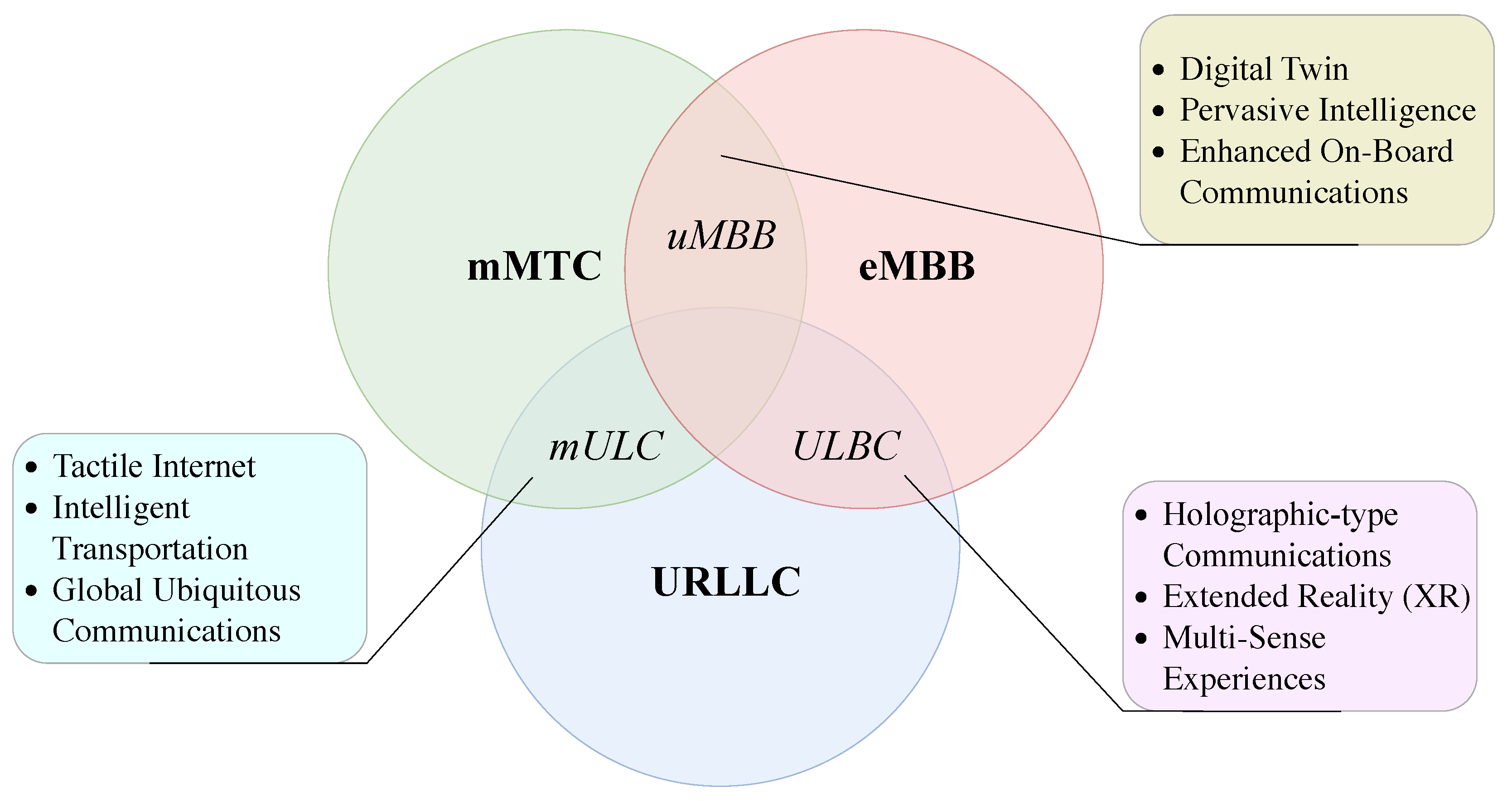
| URLLC | Ultra-Reliable Low-Latency Communications |
| eMBB | Enhanced Mobile Broadband |
| mMTC | Massive Machine Type Communications |
| mULC | Massive Ultra-Reliable Low-Latency Communication |
| ULBC | Ultra-Reliable Low-Latency Broadband Communication |
| uMBB | Ubiquitous Mobile Broadband |
| KPI | Key Performance Indicators |
| HSM | Hardware Security Module |
| FL | Federated Learning |
| ZTA | Zero-Trust Architectures |
| AI | Artificial Intelligence |
| ML | Machine Learning |
| IoT | Internet of Things |
| LLM | Large Language Model |
| XAI | Explainable AI |
| ToSC | Task-Oriented Semantic Communication |
| DL | Deep Learning |
| SPCTM | Sensing Policy, Consent, and Transparency Management |
References
- The Tor Project. The Tor Project | Privacy & Freedom Online—torproject.org. Available online: https://www.torproject.org (accessed on 21 January 2025).
- Jardine, E. Tor, what is it good for? Political repression and the use of online anonymity-granting technologies. New Media Soc. 2018, 20, 435–452. [Google Scholar]
- Cao, J.; Ma, M.; Li, H.; Ma, R.; Sun, Y.; Yu, P.; Xiong, L. A survey on security aspects for 3GPP 5G networks. IEEE Commun. Surv. Tutor. 2019, 22, 170–195. [Google Scholar] [CrossRef]
- Zhang, S.; Wang, Y.; Zhou, W. Towards secure 5G networks: A Survey. Comput. Netw. 2019, 162, 106871. [Google Scholar] [CrossRef]
- Park, J.H.; Rathore, S.; Singh, S.K.; Salim, M.M.; Azzaoui, A.; Kim, T.W.; Pan, Y.; Park, J.H. A comprehensive survey on core technologies and services for 5G security: Taxonomies, issues, and solutions. Hum.-Centric Comput. Inf. Sci. 2021, 11, 1–22. [Google Scholar] [CrossRef]
- Ziani, A.; Medouri, A. A survey of security and privacy for 5G networks. In Emerging Trends in ICT for Sustainable Development: The Proceedings of NICE2020 International Conference; Springer: New York, NY, USA, 2021; pp. 201–208. [Google Scholar] [CrossRef]
- Madi, T.; Alameddine, H.A.; Pourzandi, M.; Boukhtouta, A. NFV security survey in 5G networks: A three-dimensional threat taxonomy. Comput. Netw. 2021, 197, 108288. [Google Scholar] [CrossRef]
- Tang, Q.; Ermis, O.; Nguyen, C.D.; De Oliveira, A.; Hirtzig, A. A systematic analysis of 5g networks with a focus on 5g core security. IEEE Access 2022, 10, 18298–18319. [Google Scholar] [CrossRef]
- Yue, K.; Zhang, Y.; Chen, Y.; Li, Y.; Zhao, L.; Rong, C.; Chen, L. A survey of decentralizing applications via blockchain: The 5G and beyond perspective. IEEE Commun. Surv. Tutor. 2021, 23, 2191–2217. [Google Scholar] [CrossRef]
- Scalise, P.; Boeding, M.; Hempel, M.; Sharif, H.; Delloiacovo, J.; Reed, J. A systematic survey on 5G and 6G security considerations, challenges, trends, and research areas. Future Internet 2024, 16, 67. [Google Scholar] [CrossRef]
- Mjolsnes, S.F.; Olimid, R.F. Private Identification of Subscribers in Mobile Networks: Status and Challenges. IEEE Commun. Mag. 2019, 57, 138–144. [Google Scholar] [CrossRef]
- US Cybersecurity and Infrastructure Security Agency. Joint Statement by FBI and CISA on PRC Activity Targeting Telecommunications. 2024. Available online: https://www.cisa.gov/news-events/news/joint-statement-fbi-and-cisa-prc-activity-targeting-telecommunications (accessed on 27 February 2025).
- US Cybersecurity and Infrastructure Security Agency. AT&T Discloses Breach of Customer Data. 2024. Available online: https://www.cisa.gov/news-events/alerts/2024/07/12/att-discloses-breach-customer-data (accessed on 27 February 2025).
- Office of the Maine Attorney General. Data Breach Notifications. 2024. Available online: https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/3778e1fc-2ed5-461d-9cc5-df15c07f687c.shtml (accessed on 27 February 2025).
- Office of the Maine Attorney General. Data Breach Notifications. 2024. Available online: https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/65b9290a-b22e-4ae7-93e7-5acb84357297.shtml (accessed on 27 February 2025).
- Sicari, S.; Rizzardi, A.; Coen-Porisini, A. 5G In the internet of things era: An overview on security and privacy challenges. Comput. Netw. 2020, 179, 107345. [Google Scholar] [CrossRef]
- 3GPP. 5G System; Technical Realization of Service Based Architecture; Stage 3. Technical Specification (TS) 29.500, 3rd Generation Partnership Project (3GPP). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3338 (accessed on 21 January 2025).
- 3GPP. 5G System; Principles and Guidelines for Services Definition; Stage 3. Technical Specification (TS) 29.501, 3rd Generation Partnership Project (3GPP). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3341 (accessed on 21 January 2025).
- Bartock, M.; Cichonski, J.; Souppaya, M.; Scarfone, K.; Grayeli, P.; Sharma, S. Reallocation of Temporary Identities: Applying 5G Cybersecurity and Privacy Capabilities (Draft); Technical Report; US Department of Commerce: Washington, DC, USA, 2024. [CrossRef]
- Gorrepati, U.; Zavarsky, P.; Ruhl, R. Privacy Protection in LTE and 5G Networks. In Proceedings of the 2021 2nd International Conference on Secure Cyber Computing and Communications (ICSCCC), Jalandhar, India, 21–23 May 2021; pp. 382–387. [Google Scholar] [CrossRef]
- 3GPP. Security Architecture and Procedures for 5G System. Technical Specification (TS) 33.501, 3rd Generation Partnership Project (3GPP). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3169 (accessed on 21 January 2025).
- 3GPP. Numbering, Addressing and Identification. Technical Specification (TS) 23.003, 3rd Generation Partnership Project (3GPP). 2019. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=729 (accessed on 22 January 2025).
- 3GPP. Service Requirements for the 5G System. Technical Specification (TS) 22.261, 3rd Generation Partnership Project (3GPP). 2017. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3107 (accessed on 22 January 2025).
- 3GPP. Wireless and Wireline Convergence Access Support for the 5G System (5GS). Technical Specification (TS) 23.316, 3rd Generation Partnership Project (3GPP). 2019. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3576 (accessed on 22 January 2025).
- Institute of Electrical and Electronics Engineers. Guidelines for Use of Extended Unique Identifier (EUI), Organizationally Unique Identifier (OUI), and Company ID (CID)—standards-support.ieee.org. 2023. Available online: https://standards-support.ieee.org/hc/en-us/articles/4888705676564-Guidelines-for-Use-of-Extended-Unique-Identifier-EUI-Organizationally-Unique-Identifier-OUI-and-Company-ID-CID (accessed on 27 February 2025).
- 3GPP. NR; User Equipment (UE) Procedures in Idle Mode and in RRC Inactive State. Technical Specification (TS) 38.304, 3rd Generation Partnership Project (3GPP). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3192 (accessed on 22 January 2025).
- 3GPP. Evolved Universal Terrestrial Radio Access (E-UTRA); User Equipment (UE) Procedures in Idle Mode. Technical Specification (TS) 36.304, 3rd Generation Partnership Project (3GPP). 2016. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=2432 (accessed on 22 January 2025).
- 3GPP. NR; Radio Resource Control (RRC); Protocol Specification. Technical Specification (TS) 38.331, 3rd Generation Partnership Project (3GPP). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3197 (accessed on 22 January 2025).
- 3GPP. Evolved Universal Terrestrial Radio Access (E-UTRA); Radio Resource Control (RRC); Protocol Specification. Technical Specification (TS) 36.331, 3rd Generation Partnership Project (3GPP). 2017. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=2440 (accessed on 22 January 2025).
- 3GPP. Procedures for the 5G System (5GS). Technical Specification (TS) 23.502, 3rd Generation Partnership Project (3GPP). 2017. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3145 (accessed on 22 January 2025).
- Yao, J.; Han, Z.; Sohail, M.; Wang, L. A Robust Security Architecture for SDN-Based 5G Networks. Future Internet 2019, 11, 85. [Google Scholar] [CrossRef]
- Humayun, M.; Hamid, B.; Jhanjhi, N.; Suseendran, G.; Talib, M. 5G network security issues, challenges, opportunities and future directions: A survey. J. Phys. Conf. Ser. 2021, 1979, 012037. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. Linkable Information. Available online: https://csrc.nist.gov/glossary/term/linkable_information (accessed on 22 January 2025).
- Guo, L.; Zhang, C.; Sun, J.; Fang, Y. A Privacy-Preserving Attribute-Based Authentication System for Mobile Health Networks. IEEE Trans. Mob. Comput. 2013, 13, 1927–1941. [Google Scholar] [CrossRef]
- Liyanage, M.; Salo, J.; Braeken, A.; Kumar, T.; Seneviratne, S.; Ylianttila, M. 5G Privacy: Scenarios and Solutions. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Santa Clara, CA, USA, 9–11 July 2018; pp. 197–203. [Google Scholar] [CrossRef]
- Liyanage, M.; Ahmad, I.; Abro, A.B.; Gurtov, A.; Ylianttila, M. User Privacy, Identity and Trust in 5G. In A Comprehensive Guide to 5G Security; Wiley: New York, NY, USA, 2017; pp. 267–279. [Google Scholar] [CrossRef]
- Eleftherakis, S.; Otim, T.; Santaromita, G.; Zayas, A.D.; Giustiniano, D.; Kourtellis, N. Demystifying Privacy in 5G Stand Alone Networks. In Proceedings of the 30th Annual International Conference on Mobile Computing and Networking, ACM MobiCom ’24, Washington, DC, USA, 18–22 November 2024; pp. 1330–1345. [Google Scholar] [CrossRef]
- Khan, M.; Niemi, V. Privacy Enhanced Fast Mutual Authentication in 5G Network Using Identity Based Encryption. J. ICT Stand. 2017, 5, 69–90. [Google Scholar] [CrossRef]
- Ginzboorg, P.; Niemi, V. Privacy of the long-term identities in cellular networks. In Proceedings of the 9th EAI International Conference on Mobile Multimedia Communications, Xi’an, China, 18–19 June 2016; pp. 167–175. [Google Scholar] [CrossRef]
- Khan, M.S.A.; Mitchell, C.J. Improving Air Interface User Privacy in Mobile Telephony. In Security Standardisation Research: Proceedings of the Security Standardisation Research: Second International Conference, SSR 2015, Tokyo, Japan, 15–16 December 2015; Proceedings 2; Springer: New York, NY, USA, 2015; pp. 165–184. [Google Scholar] [CrossRef]
- Norrman, K.; Näslund, M.; Dubrova, E. Protecting IMSI and User Privacy in 5G Network. In Proceedings of the 9th EAI International Conference on Mobile Multimedia Communications, MobiMedia ’16, Xi’an, China, 18–19 June 2016; pp. 159–166. [Google Scholar]
- Van Den Broek, F.; Verdult, R.; De Ruiter, J. Defeating IMSI Catchers. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 340–351. [Google Scholar] [CrossRef]
- Eiza, M.H.; Ni, Q.; Shi, Q. Secure and Privacy-Aware Cloud-Assisted Video Reporting Service in 5G-Enabled Vehicular Networks. IEEE Trans. Veh. Technol. 2016, 65, 7868–7881. [Google Scholar] [CrossRef]
- Saeed, M.M.; Kamrul Hasan, M.; Hassan, R.; Mokhtar, R.; Saeed, R.A.; Saeid, E.; Gupta, M. Preserving Privacy of User Identity Based on Pseudonym Variable in 5G. Comput. Mater. Contin. 2022, 70, 5551–5568. [Google Scholar] [CrossRef]
- Liu, F.; Su, L.; Yang, B.; Du, H.; Qi, M.; He, S. Security Enhancements to Subscriber Privacy Protection Scheme in 5G Systems. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Harbin, China, 28 June–2 July 2021; pp. 451–456. [Google Scholar] [CrossRef]
- Saeed, M.M.; Hasan, M.K.; Obaid, A.J.; Saeed, R.A.; Mokhtar, R.A.; Ali, E.S.; Akhtaruzzaman, M.; Amanlou, S.; Hossain, A.Z. A comprehensive review on the users’ identity privacy for 5G networks. IET Commun. 2022, 16, 384–399. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and Privacy for Cloud-Based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- 3GPP. 3G Security; Lawful Interception Requirements. Technical Specification (TS) 33.106, 3rd Generation Partnership Project (3GPP). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=2265 (accessed on 20 January 2025).
- Lange, S.; Gringoli, F.; Hollick, M.; Classen, J. Wherever I May Roam: Stealthy Interception and Injection Attacks Through Roaming Agreements. In Proceedings of the European Symposium on Research in Computer Security, Bydgoszcz, Poland, 16–20 September 2024; pp. 208–228. [Google Scholar] [CrossRef]
- open5gs.org. 2025. Available online: https://open5gs.org (accessed on 21 January 2025).
- Jiang, W.; Han, B.; Habibi, M.A.; Schotten, H.D. The Road Towards 6G: A Comprehensive Survey. IEEE Open J. Commun. Soc. 2021, 2, 334–366. [Google Scholar] [CrossRef]
- Shahraki, A.; Abbasi, M.; Piran, M.J.; Taherkordi, A. A Comprehensive Survey on 6G Networks:Applications, Core Services, Enabling Technologies, and Future Challenges. arXiv 2021, arXiv:2101.12475. [Google Scholar] [CrossRef]
- Yang, M.; Qu, Y.; Ranbaduge, T.; Thapa, C.; Sultan, N.; Ding, M.; Suzuki, H.; Ni, W.; Abuadbba, S.; Smith, D.; et al. From 5G to 6G: A Survey on Security, Privacy, and Standardization Pathways. arXiv 2024, arXiv:2410.21986. [Google Scholar] [CrossRef]
- Gkonis, P.K.; Nomikos, N.; Trakadas, P.; Sarakis, L.; Xylouris, G.; Masip-Bruin, X.; Martrat, J. Leveraging Network Data Analytics Function and Machine Learning for Data Collection, Resource Optimization, Security and Privacy in 6G Networks. IEEE Access 2024, 12, 21320–21336. [Google Scholar] [CrossRef]
- Abdel Hakeem, S.A.; Hussein, H.H.; Kim, H. Security Requirements and Challenges of 6G Technologies and Applications. Sensors 2022, 22, 1969. [Google Scholar] [CrossRef] [PubMed]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Mahmoud, H.H.H.; Amer, A.A.; Ismail, T. 6G: A comprehensive survey on technologies, applications, challenges, and research problems. Trans. Emerg. Telecommun. Technol. 2021, 32, e4233. [Google Scholar] [CrossRef]
- Pujolle, G.; Urien, P. A New Generation of Security for the 6G. In Proceedings of the 2024 8th Cyber Security in Networking Conference (CSNet), Paris, France, 4–6 December 2024; pp. 161–164. [Google Scholar] [CrossRef]
- Sun, Y.; Liu, J.; Wang, J.; Cao, Y.; Kato, N. When Machine Learning Meets Privacy in 6G: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2694–2724. [Google Scholar] [CrossRef]
- Nguyen, V.L.; Lin, P.C.; Cheng, B.C.; Hwang, R.H.; Lin, Y.D. Security and Privacy for 6G: A Survey on Prospective Technologies and Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- Sandeepa, C.; Siniarski, B.; Kourtellis, N.; Wang, S.; Liyanage, M. A Survey on Privacy of Personal and Non-Personal Data in B5G/6G Networks. ACM Comput. Surv. 2024, 56, 1–37. [Google Scholar] [CrossRef]
- Wang, X.; Lyu, J.; Peter, J.D.; Kim, B.G. Privacy-Preserving AI Framework for 6G-enabled Consumer Electronics. IEEE Trans. Consum. Electron. 2024, 70, 3940–3950. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Ylianttila, M. AI and 6G Security: Opportunities and Challenges. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 616–621. [Google Scholar] [CrossRef]
- Navaie, K. Personal Data Protection in AI-Native 6G Systems. arXiv 2024, arXiv:2411.03368. [Google Scholar] [CrossRef]
- Ismail, L.; Buyya, R. Artificial Intelligence Applications and Self-Learning 6G Networks for Smart Cities Digital Ecosystems: Taxonomy, Challenges, and Future Directions. Sensors 2022, 22, 5750. [Google Scholar] [CrossRef] [PubMed]
- Li, S.; Lin, X.; Liu, Y.; Li, J. Trustworthy AI-Generative Content in Intelligent 6G Network: Adversarial, Privacy, and Fairness. arXiv 2024, arXiv:2405.05930. [Google Scholar] [CrossRef]
- Uwaoma, C. On Security Strategies for Addressing Potential Vulnerabilities in 6G Technologies Deployable in Healthcare. arXiv 2023, arXiv:2309.16714. [Google Scholar] [CrossRef]
- Xu, M.; Niyato, D.; Kang, J.; Xiong, Z.; Mao, S.; Han, Z.; Kim, D.I.; Letaief, K.B. When Large Language Model Agents Meet 6G Networks: Perception, Grounding, and Alignment. IEEE Wirel. Commun. 2024, 31, 63–71. [Google Scholar] [CrossRef]
- Wang, S.; Qureshi, M.A.; Miralles-Pechuán, L.; Huynh-The, T.; Gadekallu, T.R.; Liyanage, M. Explainable AI for 6G Use Cases: Technical Aspects and Research Challenges. IEEE Open J. Commun. Soc. 2024, 5, 2490–2540. [Google Scholar] [CrossRef]
- Ylianttila, M.; Kantola, R.; Gurtov, A.; Mucchi, L.; Oppermann, I.; Yan, Z.; Nguyen, T.H.; Liu, F.; Hewa, T.; Liyanage, M.; et al. 6G White paper: Research challenges for Trust, Security and Privacy. arXiv 2020, arXiv:2004.11665. [Google Scholar] [CrossRef]
- Drampalou, S.F.; Uzunidis, D.; Vetsos, A.; Miridakis, N.I.; Karkazis, P. A User-Centric Perspective of 6G Networks: A Survey. IEEE Access 2024, 12, 190255–190294. [Google Scholar] [CrossRef]
- Guo, S.; Zhang, A.; Wang, Y.; Feng, C.; Quek, T.Q. Trustworthy Semantic-Enabled 6G Communication: A Task-oriented and Privacy-preserving Perspective. arXiv 2024, arXiv:2408.04188. [Google Scholar] [CrossRef]
- Dass, P.; Ujjwal, S.; Novotny, J.; Zolotavkin, Y.; Laaroussi, Z.; Köpsell, S. Addressing Privacy Concerns in Joint Communication and Sensing for 6G Networks: Challenges and Prospects. In Proceedings of the Annual Privacy Forum, Karlstad, Sweden, 4–5 September 2024; pp. 87–111. [Google Scholar] [CrossRef]
- Veith, B.; Krummacker, D.; Schotten, H.D. The Road to Trustworthy 6G: A survey on Trust Anchor Technologies. IEEE Open J. Commun. Soc. 2023, 4, 581–595. [Google Scholar] [CrossRef]
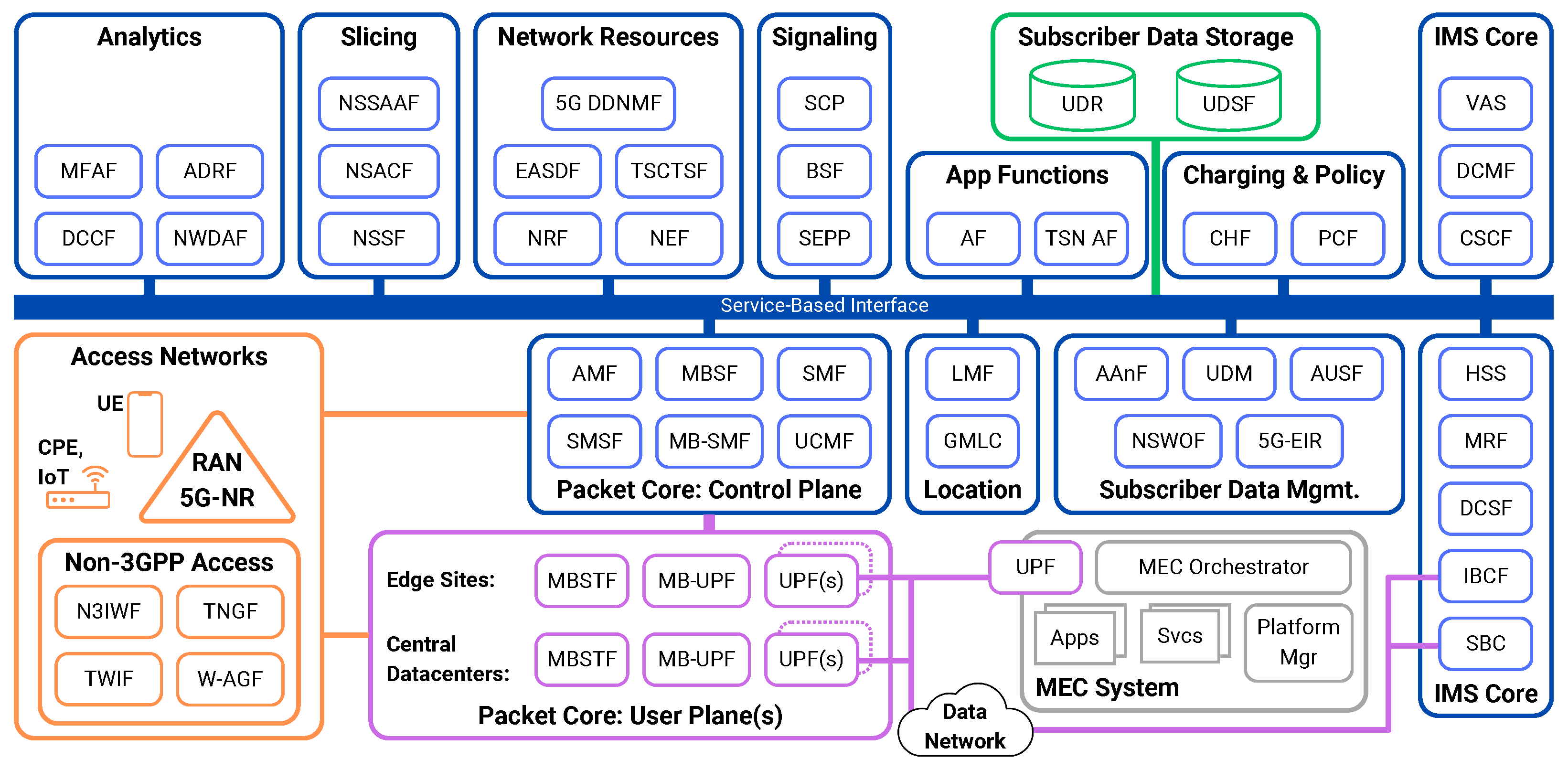
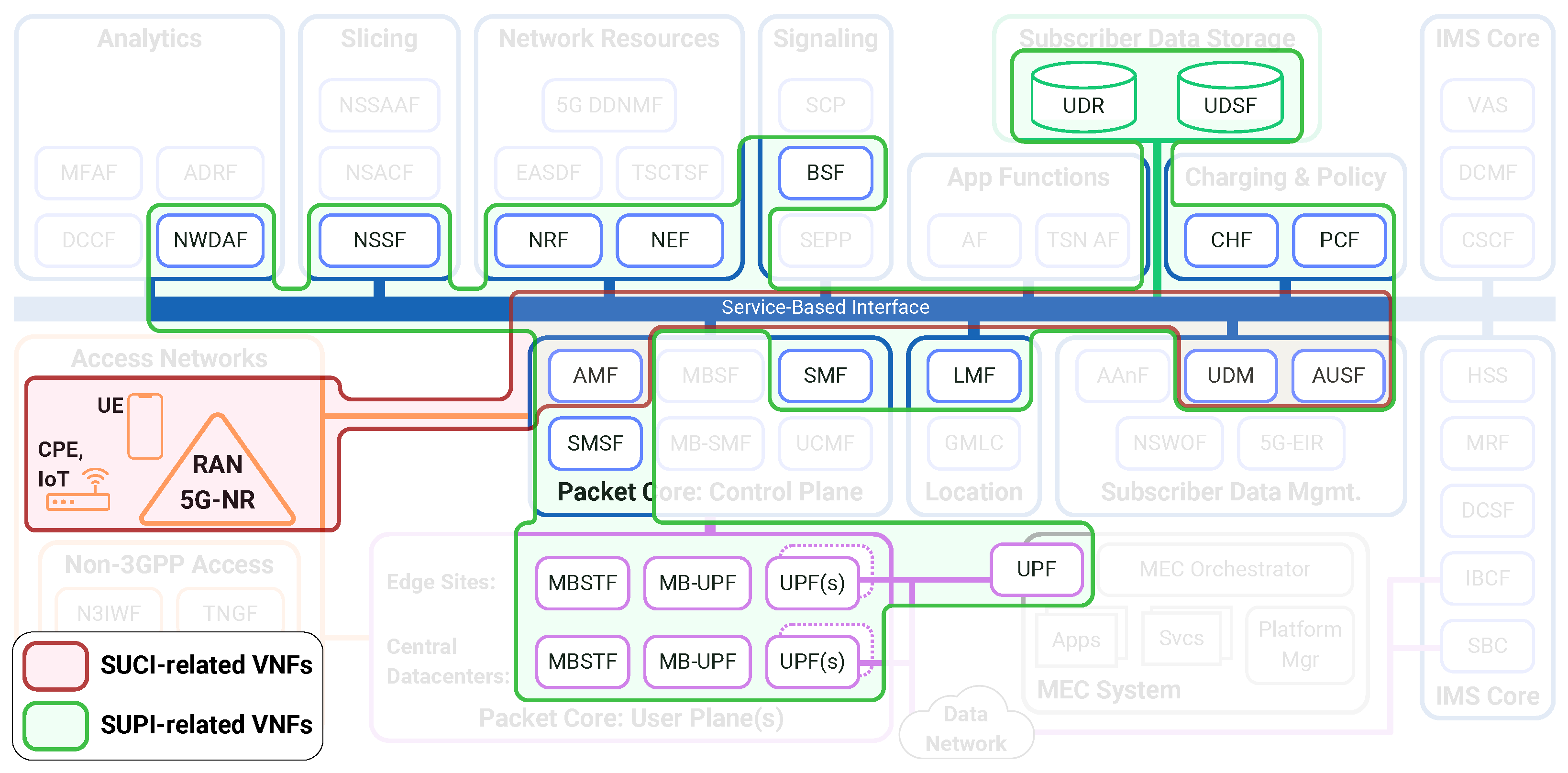

| VNF Abbreviation Resolutions | |||
|---|---|---|---|
| 5G DDNMF | Direct Discovery Name Management Function | NEF | Network Exposure Function |
| 5G-EIR | Equipment Identity Register | NRF | Network Repository Function |
| AAnF | Authentication and Key Management for Applications (AKMA) Anchor Function | NSACF | Network Slice Admission Control Function |
| ADRF | Analytics Data Repository Function | NSSAAF | Network Slice Specific Authentication and Authorization Function |
| AF | Application Function | NSSF | Network Slice Selection Function |
| AMF | Access and Mobility Management Function | NSWOF | Non-Seamless WLAN Offload Function |
| AUSF | Authentication Server Function | NWDAF | Network Data Analytics Function |
| BSF | Binding Support Function | PCF | Policy Control Function |
| CHF | Charging Function | SBC | Session Border Controller |
| CSCF | Call Session Control Function | SCP | Service Communication Proxy |
| DCCF | Data Collection Configuration Function | SEPP | Security Edge Protection Proxy |
| DCMF | Distributed Control and Management Framework | SMF | Session Management Function |
| DCSF | Data Channel Signaling Function | SMSF | Short Message Service Function |
| EASDF | Edge Application Server Discovery Function | TNGF | Trusted Non-3GPP Gateway Function |
| GMLC | Gateway Mobile Location Centre | TSCTSF | Time-Sensitive Communication Time Synchronization Function |
| HSS | Home Subscriber Server | TSN AF | Time-Sensitive Network (TSN) Application Function |
| IBCF | Interconnection Border Control Function | TWIF | Trusted WLAN Interworking Function |
| LMF | Location Management Function | UCMF | User Equipment (UE) Capability Management Function |
| MB-SMF | Multicast/Broadcast Session Management Function | UDM | Unified Data Management |
| MB-UPF | Multicast/Broadcast User Plane Function | UDR | Unified Data Repository |
| MBSF | Multicast/Broadcast Service Function | UDSF | Unstructured Data Storage Function |
| MBSTF | Multicast/Broadcast Service Transport Function | UPF | User Plane Function |
| MFAF | Messaging Framework Adapter Function | VAS | Value-Added Services |
| MRF | Multimedia Resource Function | W-AGF | Wireline Access Gateway Function |
| N3IWF | Non-3GPP Interworking Function | ||
| New Adopted Technologies in 5G and Potential Threats They Pose to User Identity Protections [20] | |
|---|---|
| Technology | Summarized Description |
| Cross-Border Data Flows | As nations’ data networks are interconnected, data must be transmitted and shared securely while also maintaining user privacy. Different countries around the world may have different standards for protecting user privacy. |
| Virtualization and Cloudification | The use of Software-Defined Networking (SDN) and VNFs allow for virtual connections between cloud services, compared to previous generations where all interfaces and network connections were closely coupled physically. If these cloud services or resources are shared, there is a possibility for unauthorized user data access. |
| SDN | SDN is a vital enabler of 5G networks, enhancing flexibility and performance by separating the control, data, and application layers through standard interfaces. The control layer, managed by the SDN controller, oversees data flow, while the application layer supports functions like load balancing and quality assurance. Despite its advantages, SDN introduces privacy risks, such as attacks on the controller or application layer that can lead to unauthorized access and manipulation of data flows [31]. To mitigate these risks, robust authentication, together with authorization mechanisms and privacy impact assessments, is essential in SDN-based 5G deployments. |
| Insider Threats | It is vital that a user of a network can afford a high degree of trust towards the operators. The complexity of a 5G environment increases the opportunity for intentional or unintentional user privacy compromises. Similarly, it is possible for insiders to misuse critical network elements, resulting in a lack of integrity of the user’s privacy [32]. As this was a threat in previous generations of cellular networks, the threat model has only grown and become more complex due to the deployment of the extensible technologies listed earlier. The increased dependence on cloud services and Software-Defined Networking has provided more areas for misuse. The additions to 5G infrastructure thus require strict access and monitoring procedures. |
| Privacy Solution | P1 | P2 | P3 | P4 | P5 | P6 | N1 | N2 | N3 | N4 | N5 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Non-centralized ML | ✓ | ✓ | ✓ | ✓ | ✓ | X | X | ✓ | ✓ | ✓ | ✓ |
| Differential privacy and data perturbation | ✓ | ✓ | ✓ | X | ✓ | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| Homomorphic encryption | ✓ | ✓ | ✓ | X | ✓ | X | X | ✓ | ✓ | ✓ | ✓ |
| Lightweight cryptography for IoT and edge | ✓ | ✓ | X | ✓ | ✓ | X | X | X | ✓ | ✓ | ✓ |
| Fog computing privacy preservation | ✓ | X | ✓ | ✓ | ✓ | X | X | X | ✓ | ✓ | ✓ |
| Blockchain-based consensus and storage | ✓ | ✓ | ✓ | ✓ | ✓ | X | X | ✓ | ✓ | ✓ | ✓ |
| Privacy level definitions and quantification | X | X | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | X | ✓ |
| Current 6G AI Privacy Literature | ||
|---|---|---|
| Paper Title and Citation | Focus | Description |
| ‘Privacy-Preserving AI Framework for 6G-Enabled Consumer Electronics’ [62] | Differential privacy, federated learning | Covers user data privacy concerns in 6G technology and presents a differential privacy and federated learning (FL) framework, offering a solution to safeguard sensitive user data during transmission. Blockchain is utilized to support the FL model in a decentralized manner, reducing vulnerabilities. |
| ‘AI and 6G Security: Opportunities and Challenges’ [63] | Intelligent security privacy provisions | Discusses the use of AI to catch and deter threats in 6G networks. Mentions the use of AI as a double-edged sword, and the importance of maintaining user privacy given the huge influx of data consumed or produced by models. Underscores the importance of the “Ethics by Design” of AI systems. |
| ‘Personal Data Protection in AI-Native 6G Systems’ [64] | AI privacy compliance, privacy by design | Identifies privacy risks with AI-enabled 6G systems, such as privacy breaches, data misuse, lack of transparency, and bias. Solutions to these issues include regulatory compliance, bias audits, and explainable AI-deployed systems. |
| ‘Artificial Intelligence Applications and Self-Learning 6G Networks for Smart Cities Digital Ecosystems: Taxonomy, Challenges, and Future Directions’ [65] | Cellular network evolution, self-learning AI systems | Details how 6G technology can be used to create smart cities with interconnected services and applications. Stresses the importance of data privacy in the use of self-learning edge AI systems and data caching. |
| ‘Trustworthy AI-Generative Content in Intelligent 6G Network: Adversarial, Privacy, and Fairness’ [66] | Safe, fair, and private AI | An operational framework is presented named TrustGAIN, which aims to protect against AI poising or prompt attacks, ensuring fair and unbiased output and maintaining user privacy with encryption. The authors also share how differential privacy can be used to limit privacy leaks but note that it cannot eliminate them. Homomorphic encryption on user datasets is also mentioned, adding identity protections and processing encrypted data without the need for decryption. |
| ‘On Security Strategies for Addressing Potential Vulnerabilities in 6G Technologies Deployable in Healthcare’ [67] | Healthcare privacy | Reviews current and past privacy and security concerns in cellular networks, such as unauthorized access and data breaches. Proposes Zero-Trust Architectures (ZTA) with the use of AI to enforce strict privacy measures for medical data. |
| ‘When large language model agents meet 6G networks: Perception, grounding, and alignment’ [68] | Large Language Models (LLM), Agentic AI, edge computing | The authors cover the expected aspects of agentic LLMs in 6G networks with a split approach for on-device capabilities and the use of edge computing. User privacy is discussed as a split approach with associated pros and cons: high anonymity when using on-device model inference with concerns arising from the reliance on edge computing for complex tasks. The authors note that privacy in edge computing poses a risk in the case of malicious edge nodes. |
| ‘Explainable AI for 6G use cases: Technical aspects and research challenges’ [69] | Explainable AI (XAI) in 6G technology | This research covers an exhaustive list of XAI use cases in 6G technology, ranging from self-driving vehicles to medicine. Important privacy focuses include leveraging XAI to catch user privacy ‘leakages’, understand re-identification attacks on user datasets, and retain user expectations in terms of service capabilities and performance. It is prominent that XAI is still a bleeding-edge field with open research questions, notably, Can privacy threats be posed by the increased transparency of AI decision-making? |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Scalise, P.; Hempel, M.; Sharif, H. A Survey of 5G Core Network User Identity Protections, Concerns, and Proposed Enhancements for Future 6G Technologies. Future Internet 2025, 17, 142. https://doi.org/10.3390/fi17040142
Scalise P, Hempel M, Sharif H. A Survey of 5G Core Network User Identity Protections, Concerns, and Proposed Enhancements for Future 6G Technologies. Future Internet. 2025; 17(4):142. https://doi.org/10.3390/fi17040142
Chicago/Turabian StyleScalise, Paul, Michael Hempel, and Hamid Sharif. 2025. "A Survey of 5G Core Network User Identity Protections, Concerns, and Proposed Enhancements for Future 6G Technologies" Future Internet 17, no. 4: 142. https://doi.org/10.3390/fi17040142
APA StyleScalise, P., Hempel, M., & Sharif, H. (2025). A Survey of 5G Core Network User Identity Protections, Concerns, and Proposed Enhancements for Future 6G Technologies. Future Internet, 17(4), 142. https://doi.org/10.3390/fi17040142







