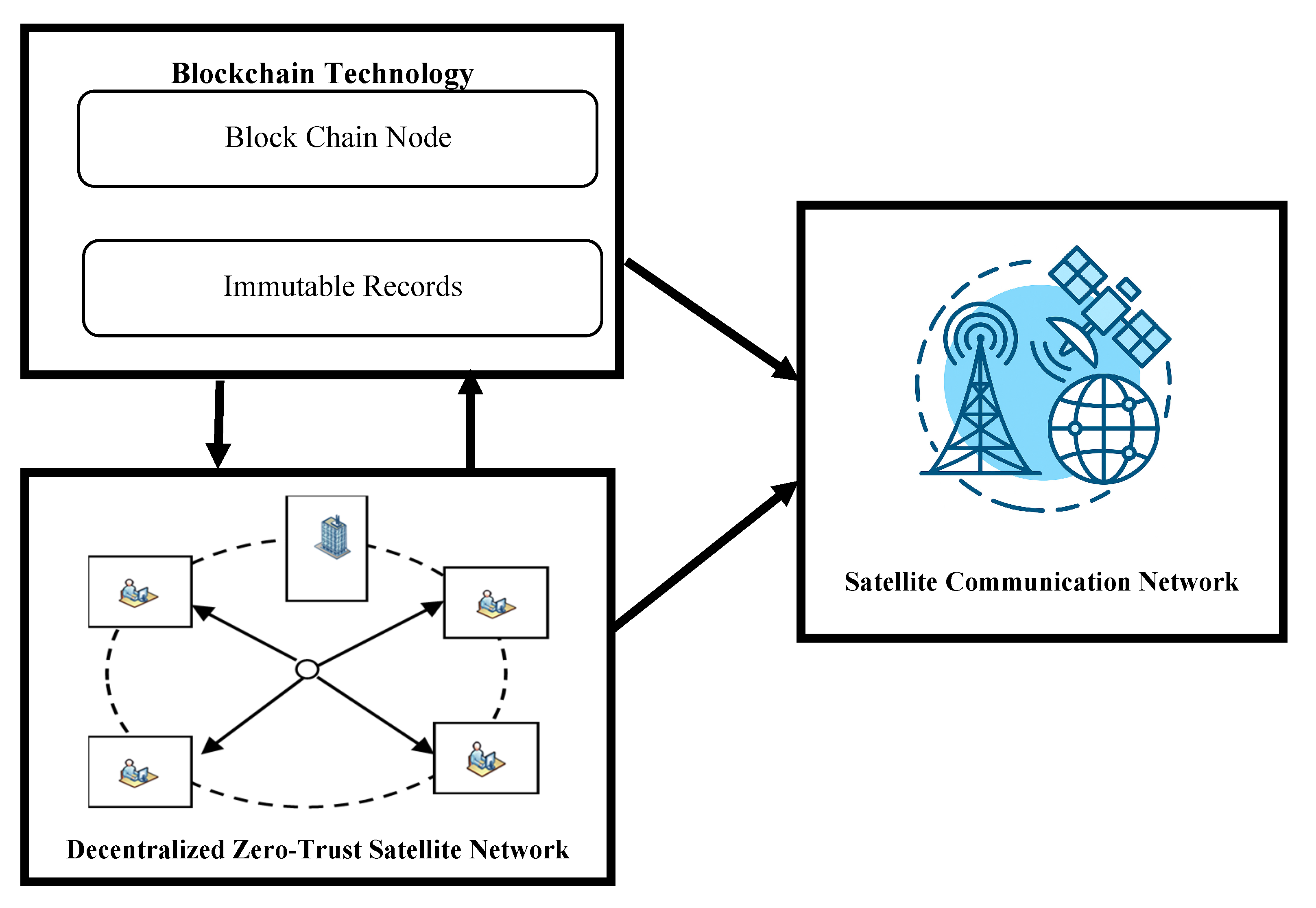
1. Introduction
A satellite network is a communication system that uses artificial satellites to relay signals between different points on Earth. These networks are especially useful for covering large or remote areas where traditional infrastructure like cables or towers might be impractical. A decentralized zero-trust architecture in satellite networks is an advanced approach to securing space-based communication systems. The conventional security models designed for satellite networks do not achieve higher security. Therefore, there is a requirement for novel security models to improve the robustness and intelligence of a decentralized zero-trust architecture for anomaly detection in satellite networks.
An existing blockchain-enabled federated learning (BFL) framework was implemented in [
1] for anomaly detection in a robust zero-trust architecture. However, secure communications against quantum attacks have remained an open issue. Variance-based genetic ensemble of neural networks was designed in [
2] for increasing the efficiency of satellite anomaly detection, but the false-positive rate was higher. A deep learning-based anomaly detection framework was designed in [
3] for satellite telemetry with false anomalies. However, the existing framework included a high computational cost, over-fitting, and data privacy and security concerns.
Long Short-Term Memory (LSTM) Networks were introduced in [
4], aiming at achieving better anomaly detection accuracy in satellite communications systems, but there were more computational costs, training time, and memory consumption. A security method, created to notice malicious events, that depended on the examination of blockchain network traffic statistics, was presented in [
5]. However, handling a greater number of transactions was not efficient in this work, which increased delays and costs. Zero-trust authentication concepts were utilized in [
6] to secure communications with the application of hyperelliptic curve cryptography (HECC). But authentication accuracy was poor when considering a larger number of satellite users.
Convolution neural networks (CNNs) and zero-trust security policies were developed in [
7] for the reliable and accurate identification of false data injection attacks. However, the transmission delay was higher. An orbital zero-trust architecture (oZTA) was implemented in [
8] for securing the LEO satellite networks. However, different types of anomalies were not detected. A multi-factor authentication method was presented in [
9] using the zero-trust network concept for LEO satellite communication systems. However, a higher level of security was not achieved.
An access authentication procedure was utilized in [
10] with the goal of reducing the communication delay and signaling cost. However, data integrity was not considered. An identity-based quantum signature scheme was intended in [
11] to boost security. However, authentication performance was insufficient. Zero-trust and edge intelligence (ZTEI)-empowered continuous authentication was performed in [
12] to achieve improved accuracy for user authentication. However, the robustness of the zero-trust model still needed to be improved.
The dual-branch reconstruction model was implemented in [
13] for satellite anomaly detection, but the time complexity during the anomaly identification process was higher. Two-stage anomaly detection was performed in [
14] for the LEO satellite network. However, continuous authentication was not considered. A federated learning (FL) framework and conditional generative adversarial network (CGAN) representation were utilized in [
15] for threat identification in satellite–terrestrial integrated networks. However, communication overhead and data privacy issues were not solved.
Recent studies emphasize the growing role of FL in enabling privacy-preserving and distributed intelligence across heterogeneous communication environments. For instance, the hierarchical SFL (HSFL) framework was presented in [
16] for secure edge networks. Similarly, federated learning based on model repair (FedMR)was implemented in [
17] to demonstrate the use of hierarchical FL to improve anomaly detection accuracy while preserving data privacy. A backdoor data-poisoning attack method was introduced in [
18] to highlight FL’s potential in supporting decentralized trust management for 6G and space–air–ground networks. Additionally, a unified multi-domain face normalization network (UMFN) was utilized in [
19] to provide robust FL-based security models resistant to adversarial manipulation. These recent advancements underline the suitability of federated learning as a foundation for intelligent, privacy-preserving anomaly detection in satellite networks, motivating its integration with blockchain and post-quantum cryptography in the proposed BEDZTM-PQC framework.
A deep learning-based smart framework was developed in [
16] for cyber-physical and satellite system security risk identification. However, it was more computationally complex. A deep learning-based hybrid intrusion detection system was designed in [
17] to safeguard satellite networks. But the ratio of the number of satellite users that was mistakenly detected as normal or the anomaly was higher. A literature review of different machine learning and deep learning-based satellite communication technologies and their applications, open challenges, and future research solutions was presented in [
18].
A study of various machine learning algorithms developed for anomaly detection in satellite networks, with their merits and demerits, was analyzed in [
19,
20]. A PQC technique was designed in [
21,
22] to defend satellite communications against quantum computing threats. Single-user security [
23,
24] and robust zero-trust architecture [
25]. But zero-trust models and blockchain technology were not utilized. In order to overcome the above issues, BEDZTM-PQC [
23] is introduced in this paper. Zero trust [
24] means “never trust, always verify.” Every device, user, or satellite must prove its identity and authorization before gaining access; there is no assumption, not even within the network. Traditional satellite networks often rely on centralized control, which can be a single point of failure [
25]. A decentralized ZTA distributes trust decisions across multiple nodes (satellites, ground stations, etc.), improving resilience and reducing vulnerability to attacks or outages. Combining decentralized ZTA with blockchain technology in satellite networks creates a powerful framework for secure, resilient, and autonomous space communication systems. The integration of a decentralized ZTA and blockchain in satellite networks provides strong security, but scalability was unsatisfactory, i.e., as satellite constellations grew, maintaining a synchronized blockchain ledger across hundreds of fast-moving nodes becomes increasingly complex. Another problem is resource constraints, where satellites have limited processing power, memory, and energy. Running blockchain nodes or continuous ZTA authentication can strain these resources.
In addition to that, blockchain operations (like consensus and smart contract execution) can establish delays. In space, where communication already suffers from latency and limited bandwidth, this can be a serious bottleneck. Also, implementing strong cryptographic protocols and continuous verification (as required by ZTA) can slow down mission-critical operations if not optimized properly. Integrating blockchain and ZTA across satellites from different vendors or nations requires standardized protocols. In order to overcome the previously mentioned problems, a novel BEDZTM-PQC is proposed in this paper by combining decentralized ZTA, blockchain technology, post-quantum cryptography, and FL algorithms in a satellite network for reliable data communication.
The key contributions of BEDZTM-PQC are described as follows:
- (1)
Decentralized Group-Based Zero-trust Security: Proposes an innovative zero-trust framework that performs authentication and access control at the group level, thereby mitigating risks associated with single points of failure in satellite communication networks.
- (2)
Integration of PQC: Employs quantum-resistant cryptographic primitives to secure communication and identity management, ensuring long-term resilience against quantum computing threats in space-based systems. To ensure a higher level of security when combining decentralized ZTA and blockchain technology in satellite networks and to reduce the latency and resource usage, the PQC concept is introduced in this paper. Thus, the proposed BEDZTM-PQC increases the authentication performance as the blockchain enforces continuous verification, ensuring that only authenticated entities can interact with satellite networks.
- (3)
Hierarchical FL for Anomaly Detection: Introduces a multi-layer FL strategy that facilitates collaborative anomaly detection across satellite clusters while preserving local data privacy and minimizing power consumption. By applying FL, the proposed BEDZTM-PQC protects privacy and reduces overhead communication in satellite networks.
- (4)
Blockchain-Enabled Trust and Access Management: Utilizes blockchain technology and smart contracts to maintain immutable transaction records, dynamically manage trust scores, and implement decentralized anomaly validation and access control decisions. To improve the security and intelligence of the designed blockchain-enabled decentralized zero-trust satellite network, FL is utilized in this work. With this concept, the proposed BEDZTM-PQC boosts the anomaly detection performance by collecting behavioral data and trust scores of users in a satellite network. Here, behavioral data represents authentication success/failure rates, communication delays or drops, smart contract violations, and resource usage anomalies recorded on the blockchain.
- (5)
Blockchain provides decentralized authentication and immutable transaction records, ensuring tamper-proof security for inter-satellite communications.
- (6)
Post-quantum cryptography (PQC) guarantees forward security and resistance against emerging quantum attacks, safeguarding key exchange and encryption processes.
- (7)
Federated learning (FL) enables distributed anomaly detection and adaptive trust management without requiring raw data sharing, thereby preserving privacy and reducing communication overhead.
The residual paper is formulated as follows:
Section 2 shows the problem formulation,
Section 3 describes the architecture of BEDZTM-PQC for the secured LEO satellite network model,
Section 4 provides the detailed processes of the developed FL-based anomaly detection,
Section 5 illustrates the experimental results and compares them with conventional methods, and
Section 6 concludes the paper.
2. Problem Formulation
In modern satellite networks, the increasing number of interconnected nodes (satellites and ground stations) introduces critical security vulnerabilities, especially in environments relying on centralized control or node-specific authentication. Existing anomaly detection and security models often fail to scale securely and reliably when protecting groups of satellite nodes or agents, leading to single points of failure (SPOF), delayed threat response, and vulnerability to quantum-era cyber attacks. To overcome these challenges, we designed a decentralized, quantum-resilient, and privacy-preserving security architecture for satellite networks that enables group-level protection, dynamic trust management, and accurate anomaly detection. Here, the objective is to maximize security trust and anomaly detection accuracy, while minimizing communication overhead and trust decay, which is mathematically described as follows:
In Equation (1),
describes the accuracy of model ‘
’,
defines the communication cost of the groups,
refers tradeoff weight parameter, and
represents each group’s dynamic trust score, whereas ‘
’ describes the set of satellite groups. The conventional system model for BEDZTSN is shown in
Figure 1.
With the motivation of strengthening the security level of the blockchain-assisted decentralized zero-trust satellite network while decreasing the latency and resource utilization, post-quantum cryptography is utilized in this paper. In addition to that, FL is utilized in this study to accurately identify the threats in this network with better complexity.
Motivation and Novelty of the Proposed BEDZTM-PQC Framework:
Traditional satellite communication systems rely on centralized trust models that are vulnerable to single points of failure and evolving cyber threats. The proposed BEDZTM-PQC introduces a novel fusion of blockchain, PQC, and FL to overcome these challenges. The blockchain provides decentralized trust management through immutable smart contracts, ensuring transparent authentication and secure coordination among satellites. PQC guarantees resistance against quantum-based attacks, making the communication framework future-proof. FL enables distributed anomaly detection by allowing satellites to collaboratively train models without sharing raw data, thus preserving privacy and reducing communication overhead.
This integrated approach establishes a multi-layered, self-adaptive, and intelligence-driven zero-trust architecture. Unlike conventional systems, BEDZTM-PQC simultaneously achieves decentralized trust, quantum-resilient encryption, and privacy-preserving anomaly detection, offering a unique and comprehensive cybersecurity solution for next-generation satellite networks.
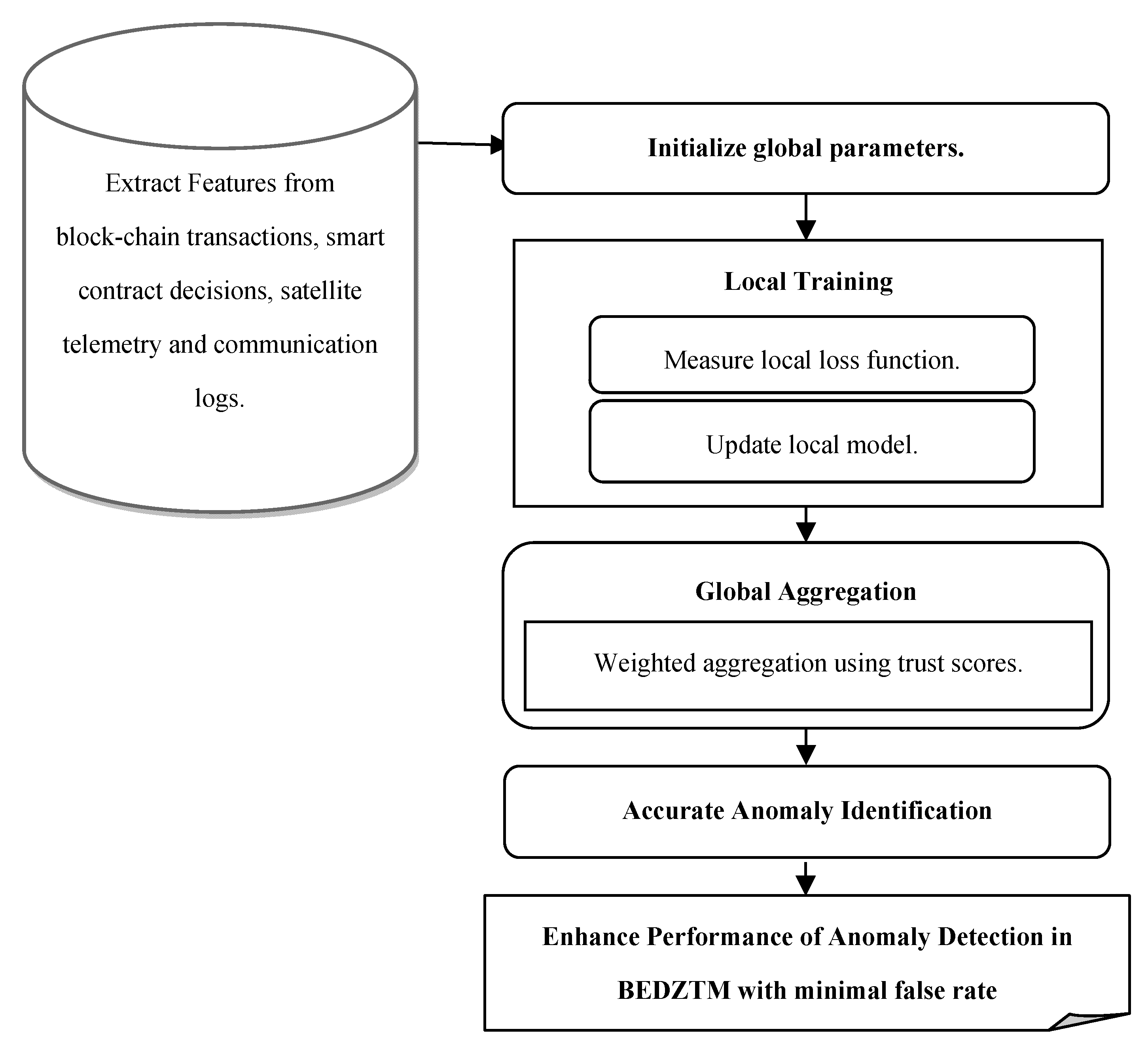
4. FL-Based Anomaly Detection
In this paper, FL is used to efficiently identify the normal and anomalous behavior node based on encrypted satellite traffic data, node behavior, and smart contract interaction logs. The processing diagram of FL for threat identification in BEDZTSN is demonstrated in
Figure 3.
The training phase of federated learning for anomaly detection is described mathematically as follows:
Here, represents FL and indicates the training dataset where includes extracted features from blockchain transactions, smart contract decisions and satellite telemetry, communication logs, and .
FL is a machine learning concept where multiple decentralized clients (e.g., satellites, ground stations) collaboratively train a shared global model without sending their local data to a central server. Each node trains a local anomaly detection model (e.g., autoencoder), and the global model is updated in rounds.
Step-by-Step FL Process:
Step 1: Initialization: First, the global model parameters are initialized and shared with all participating satellites (clients).
Step 2: Local Training: Each client ‘
’ uses its local behavioral dataset
to train the model and compute an updated model
at round
t. Here, the local loss function (i.e., mean squared error for auto encoder) is mathematically obtained as follows:
In Equation (10),
describes model output (e.g., reconstructed input), whereas
represents the input vector of behavioral features. In the FL concept, the autoencoder is considered as a local model for anomaly detection. Consequently, each node determines updated model using the following:
The above Equation notations are shown in
Table 3.
Step 3: Model Update Sharing (on-chain)
Each satellite determines its local update using the following:
The hash of
and a proof of correctness (optional for privacy) are stored on the blockchain for verifiability using the following:
Step 4: Global Aggregation
The aggregator determines the Federated Averaging using the following:
Then, weighted aggregation using trust scores (e.g., based on node behavior history) is formulated as follows:
The updated model is sent to all clients for the next training round or for inference use.
Step 5: Anomaly Detection: After training, each satellite uses the global model to detect behavioral anomalies in real-time using the following:
From that, FL efficiently detects unusual patterns or behaviors in network data that may point out security threats or system faults with higher accuracy. Here, 0 represents a normal behavior satellite node, whereas 1 describes an anomaly satellite node, according to the detected output; then, ZTDE in BEDZTM-PQC makes policy enforcement, i.e., allows, restricts, or re-authenticates. If the anomaly node is detected, then BEDZTM-PQC logs the event in the blockchain ledger and triggers the smart contract policy (e.g., deny access, re-authenticate). If the normal behavior node is detected, then BEDZTM-PQC logs the event in the blockchain ledger and grants full access.
Step 6: Continuous Verification (zero-trust Loop):
The identity of each satellite user or node is continuously re-verified with the help of a PQ signature and using dynamic behavioral data. Here, suspicious activity (i.e., invalid PQ signature anomaly in message timing) triggers policy enforcement via the smart contract.
The algorithmic process of the proposed BEDZTM-PQC is described in Algorithm 1.
| Algorithm 1: Blockchain-Enabled Decentralized Zero-trust Model based Post-Quantum Cryptography and Federated Learning |
| 1: Input: Number of satellite ’; Behavior logs, access pattern, trust score |
|
2: Output: Enhance security and Intelligence of satellite network
|
|
3: Begin
|
|
4: Consider number of satellite users ’ in BEDZTSN
|
|
5: Define problem formulation |
|
6: For each satellite user ‘’
|
|
//Satellite Behavior Continuous Monitoring//
|
|
7: Continuously monitors their behaviors in dynamic satellite network
|
|
8: Stores Behavioral data of each user in blockchain ledger
|
|
9: end for
|
|
10: // Satellite Key Generation//
|
|
11: For each satellite user ‘’ generate post-quantum public and private key pair
|
|
12: Sample Secret and error vectors are represented as , indicate discrete Gaussian or centered binomial distribution
|
|
13: public matrix is formulated as |
|
14: compute . Then, public key (PK) is generated as, |
|
15: secret key (SK) is generated as, |
|
16: end for
|
|
// Mutual Authentication via ZTDE Decision Logic//
|
|
17: for each new access request from satellite node or user ‘’
|
|
18: if (PQ Signature Valid) & (Policy Match), Then
|
|
19: if (QRVM Trust Score < Threshold) Then Grant Access
|
|
20: else
|
|
21: Deny Access + Log Event
|
|
22: end if
|
|
23: else
|
|
24: Re-Authenticate or Block
|
|
25: end if
|
|
26: end for
|
|
// BlockChain Ledger//
|
|
27: For each transaction data in blockchain
|
|
28: Hash function maps transaction data of any size to fixed-size output
|
|
|
29: Blockchain ledger securely stores hashes of transaction data
|
|
30: Verifies data integrity
|
|
31: end for
|
|
// Quantum Safe Key Exchange for Secure Channel//
|
|
32: For each transaction in blockchain
|
|
33: Encrypt transaction with public key of receiver satellite node
|
|
|
34: Perform Post-quantum Decryption with secret key of receiver node
|
|
|
35: End For
|
|
// FL for Anomaly Detection//
|
|
36: For each satellite user ‘’ with input behavior data features ‘’
|
|
37: Initialization global parameters ‘’anddistribute to all clients
|
|
38: for each round t = 1 to T
|
|
39: Local Training phase |
|
40: Local loss function |
|
41: Update model at round t using |
|
42: Each satellite determines its local update using |
|
43: Each node records a hashed proof of update on blockchain for audit
|
|
|
44: Global Aggregation |
|
45: Weighted aggregation using trust scores using Where |
|
46: Anomaly Detection |
|
47: end if
|
|
48: end for
|
|
49: end for
|
|
// Continuous Verification (Zero Trust Loop)//
|
| 50: Each satellite user or node is continuously re-verified |
| 51: Triggers policy enforcement via smart contract |
| 52: end |
5. Simulation
The proposed BEDZTM-PQC and conventional blockchain-enabled federated learning (BFL) framework [
1] are implemented in MATLAB. To conduct the experimental process, the varying numbers of satellite users in a range of 50, 100, 150, 250, 500, 750, and 1000 are assumed as input. The simulations and model evaluations were performed on a standalone desktop system with the following conditions are shown in
Table 4,
Table 5 and
Table 6 respectively.
The following table shows five users’ session evaluations.
In the above
Table 7, User_1 and User_5 had low trust scores due to higher local loss, and, therefore, BEDZTM-PQC found User_1 and User_5 as an anomaly.
The simulation results of BEDZTM-PQC are compared against the state-of-the-art BFL framework [
1] using the following metrics:
5.1. Performance Measure of Accuracy
The accuracy is calculated based on the ratio of the number of satellite users that are correctly identified as an anomaly or normal to the total number of satellite users considered as an input, using the following equation:
In Equation (17), ‘’ represents the number of satellite users exactly authenticated as an anomaly or normal, whereas ‘’ defines the total users considered as an input for simulation work. The authentication accuracy is observed in terms of percentage (%).
Table 8 and
Figure 4 demonstrate that the simulation results of BEDZTM-PQC consistently outperform conventional BFL [
1] across all tested satellite constellation sizes (from 50 to 1000 nodes). This improvement validates the effectiveness of combining trust-aware federated learning, zero-trust authentication, and post-quantum secure communication mechanisms. The BEDZTM-PQC model achieves near 96.14% accuracy at 1000 nodes, demonstrating excellent scalability, security, and learning stability. The performance gap between BFL [
1] and BEDZTM-PQC increases with network size, which is critical for future large-scale LEO satellite constellations. The experimental results demonstrate that the BEDZTM-PQC framework significantly enhances authentication accuracy over conventional BFL [
1] across all network sizes. The combination of blockchain, zero-trust evaluation, and PQC not only improves authentication accuracy but also ensures resilience against adaptive threats and scalability to 1000 nodes. Thus, the proposed BEDZTM-PQC achieves 96.14% accuracy while considering 1000 users as input for experimental evaluation, whereas state-of-the-art BFL [
1] obtained 91.31%.
5.2. Performance Measure of Latency
Latency is calculated based on the time required to efficiently deliver the data packets between the genuine users in the satellite network. Accordingly, the latency is obtained as follows:
In Equation (18), ‘’ represents a data packet and ‘’ describes the time used by a satellite user to effectively broadcast the single data packets in the network, whereas ‘’ represents the total data packets considered as input. The latency is observed in terms of milliseconds (ms).
In
Table 9 and
Figure 5, the proposed BEDZTM-PQC model consistently outperforms traditional BFL across all scalability points. In addition, the proposed BEDZTM-PQC offers stronger authentication security, better resistance to adaptive attacks, and higher robustness in FL environments. The performance gap increases with scale, demonstrating that the proposed BEDZTM-PQC is better suited for large satellite constellations. This is because of the use of trust-aware federated learning, zero-trust authentication, and the post-quantum secure communication concept in our research work. Hence, the proposed BEDZTM-PQC model boosts the rate of reliable data transmission in a satellite environment. For that reason, the proposed BEDZTM-PQC attained 98.12% security while taking 250 data packets as input for experimental evaluation, whereas the state-of-the-art BFL [
1] achieves 93.48%.
5.3. Performance Measure of Security
The security level (µ) is calculated depending on the ratio of the number of data packets that are accessed only by authoritative users to the total data packets considered as input. Thus, the security level (µ) is obtained using the following:
In Equation (14), ‘’ describes the number of data packets accessed only by genuine users in a satellite network environment, whereas ‘’ points out the total data packets taken as input. The security rate is observed in terms of percentage (%).
In
Table 10 and
Figure 6, the proposed BEDZTM-PQC model consistently outperforms traditional BFL across all scalability points. In addition, the proposed BEDZTM-PQC offers stronger authentication security, better resistance to adaptive attacks, and higher robustness in FL environments. The performance gap increases with scale, demonstrating that the proposed BEDZTM-PQC is better suited for large satellite constellations. This is because of the use of trust-aware federated learning, zero-trust authentication, and the post-quantum secure communication concept in our research work. Hence, the proposed BEDZTM-PQC model boosts the rate of reliable data transmission in satellite environments. For that reason, the proposed BEDZTM-PQC attained 98.12% security while taking 250 data packets as input for experimental evaluation, whereas state-of-the-art BFL [
1] achieves 93.48%, respectively.
5.4. Scalability to Large Satellite Constellations (e.g., 1000+ Nodes)
In
Table 11 [
24], accuracy decreases gradually as the number of satellite nodes increases due to higher behavioral diversity, increased chance of data heterogeneity, and more potential for adversarial behavior.
Table 11 [
24] illustrates the performance of the proposed BEDZTM-PQC under varying numbers of satellite nodes (250–1500). The results demonstrate a clear trade-off between authentication accuracy, latency, memory consumption, and blockchain overhead as network scale increases. The authentication accuracy decreases slightly from 96.3% at 250 satellites to 88.6% at 1500 satellites. Theoretically, this degradation occurs because as the network expands, the number of inter-satellite communication links and concurrent authentication requests grows exponentially, increasing the probability of transient mismatches and synchronization delays. However, the model maintains high accuracy due to the FL mechanism, which continuously updates local models using decentralized anomaly feedback while preserving data privacy. Latency increases from 1.48 ms to 3.42 ms as the number of satellites grows. This trend aligns with the expected communication overhead in decentralized blockchain-based systems. The latency growth is primarily due to block propagation delay and consensus validation time within the blockchain ledger. Despite this increase, the observed latency remains within acceptable real-time communication thresholds for inter-satellite links, demonstrating that the ZTA with smart contract enforcement does not critically impact operational responsiveness. The peak memory per node rises gradually from 4.8 MB to 8.9 MB. This increment is theoretically justified by the increase in stored local ledger data, authentication logs, and FL model parameters. The hierarchical federated learning structure minimizes this impact by distributing training tasks across groups, thus avoiding excessive memory overload on individual satellites. Blockchain overhead increases from 190 ms to 398 ms with network size, reflecting the additional time required for consensus verification and block synchronization among larger satellite clusters. This overhead is partly mitigated by the model’s group-based blockchain partitioning, where smaller clusters maintain localized chains before synchronizing globally, reducing delay propagation effects. The PQC key size remains constant at 3.2 kB, which indicates that the post-quantum cryptographic scheme (likely lattice-based or hash-based) maintains consistent key lengths regardless of network size. This stability ensures predictable storage and transmission overhead, making the cryptographic layer scalable for large constellations. The theoretical analysis confirms that BEDZTM-PQC achieves a balanced trade-off between security strength and computational efficiency. Despite a moderate increase in latency and overhead with scaling, the system maintains high authentication accuracy, manageable resource utilization, and quantum-resistant protection, validating its feasibility for next-generation decentralized satellite security architectures.
5.5. Energy/Resource Consumption per Authentication Cycle
Table 12 shows ultra-low energy footprint per cycle (~68.4 mJ), which fits well within LEO nano satellite power budgets; real-time authentication is achieved in ~19.2 ms and communication overhead is under 1 KB, including PQC keys and blockchain logs.
Table 12 presents the computational and communication performance of the BEDZTM-PQC model during different action phases within each authentication and anomaly detection cycle. The metrics analyzed include average CPU time, energy consumption, and communication overhead, which together quantify the system’s operational efficiency and resource cost. Trust score calculation phase consumes an average of 3.8 ms CPU time and 13.2 mJ of energy, with a communication overhead of 250 bytes per session. The moderate resource usage stems from the multi-factor trust evaluation, where each satellite computes a trust score based on behavioral, cryptographic, and consensus parameters. The computational demand here is largely due to the Bayesian trust aggregation and blockchain state verification used to cross-validate node integrity within the cluster. The PQC decryption phase requires 2.2 ms and 8.1 mJ, with an additional 128 bytes for key exchange and handshake communication. The relatively low overhead demonstrates the efficiency of the selected lattice-based post-quantum cryptographic scheme, which provides quantum-resistant encryption while maintaining practical computational requirements. This phase ensures message confidentiality and forward security without significantly impacting energy budgets, which is crucial for power-constrained satellites. The blockchain transaction stage exhibits a CPU time of 3.6 ms and energy consumption of 11.7 mJ, with a communication payload of approximately 300 bytes per anomaly or transaction record. The overhead arises from smart contract execution and block validation, which require consensus among group members. The theoretical advantage here lies in distributed verification, where logging security events on-chain guarantees immutability and accountability, thereby reinforcing the ZTA principles. The detection and action phase is responsible for alert generation or access authorization, consuming 1.3 ms and 4.2 mJ with 150 bytes of signaling data. Its minimal cost reflects the optimized federated anomaly classifier, which leverages locally trained models for rapid decision-making. The lightweight signaling ensures prompt response for threat mitigation with minimal delay propagation across the satellite cluster. The total computational cost per full cycle is 19.2 ms and 68.4 mJ, with an approximate communication footprint of 828 bytes. Theoretically, this represents a highly efficient operational profile, balancing cryptographic security, blockchain verification, and learning-based detection. Such results validate the feasibility of deploying BEDZTM-PQC in real-time inter-satellite communication environments, where both low latency and high energy efficiency are mission-critical. The integrated evaluation of cryptographic, blockchain, and federated processes shows that the model maintains strong security guarantees with lightweight computational and communication overhead. This confirms that the multi-layered zero-trust mechanism is suitable for distributed satellite networks without compromising operational efficiency.
5.6. Robustness to Adaptive Attacks
In
Table 13, the BEDZTM-PQC maintains strong robustness for baseline random attack, replay attack, and slight vulnerability to mimicry attackers, and insider trusted node hijack due to static behavior inputs.
Table 14 and
Figure 7 show the proposed BEDZTM-PQC consistently outperforms BFL, HECC-based authentication, and oZTA across all critical metrics. Its integration of the blockchain, federated learning, and PQC provides not only immediate improvements in accuracy and latency but also ensures long-term quantum resilience and robustness against adaptive threats.
6. Conclusions
In this paper, BEDZTM-PQC is presented for anomaly detection in satellite communication networks by integrating PQC mechanisms with the FL concept. The designed BEDZTM-PQC eliminates implicit trust among satellite nodes and ground stations by enforcing continuous verification, decentralized access control, and tamper-proof auditability via a blockchain. By incorporating lattice-based post-quantum cryptographic primitives, the BEDZTM-PQC ensures long-term resilience against quantum-era attacks, which are especially relevant to mission-critical space systems. To detect anomalous behaviors in real time, BEDZTM-PQC employed the FL concept, where autoencoder-based detectors are considered as local models. These models can adapt to evolving traffic patterns without requiring labeled training data, making them ideal for dynamic, high-latency satellite environments. This research presents an advanced security framework tailored for the emerging needs of satellite networks, where traditional centralized models and individual node protections are no longer sufficient. The proposed group-protected decentralized zero-trust architecture, reinforced by the blockchain, PQC, and FL provides a robust and scalable solution to modern cyber threats, particularly in the context of space-based communication systems. By introducing group-level authentication, trust scoring, and threshold cryptographic mechanisms, the model effectively mitigates single point of failure (SPOF) risks at both node and team levels. Blockchain technology underpins the system’s trust and accountability by maintaining immutable records of all interactions and decisions. The proposed architecture demonstrates significant improvements in security robustness, anomaly detection accuracy, fault tolerance, and system scalability. These enhancements make the solution particularly suitable for critical applications in defense, remote sensing, environmental monitoring, and global satellite communications.