1. Introduction
In recent years, advances in communication technology and artificial intelligence have driven a smart revolution in the automotive industry, transforming vehicles into intelligent, interconnected systems. The integration of on-board computers, sensors, and control systems has significantly improved vehicle performance and safety [
1]. With the widespread adoption of wireless communication, in-vehicle technologies ,such as remote control and speed limit systems, have become increasingly prevalent [
2]. This evolution has accelerated the development of the Internet of Vehicles (IoV), fostering the growth of driver assistance systems that offer safer and more intelligent driving experiences [
3]. The emergence of 5G further boosts the IoV, enabling high-speed, low-latency communication between vehicles. In vehicular ad hoc networks (VANETs), 5G allows for real-time sharing of traffic updates, road conditions, and event alerts, improving the responsiveness and efficiency of transportation systems [
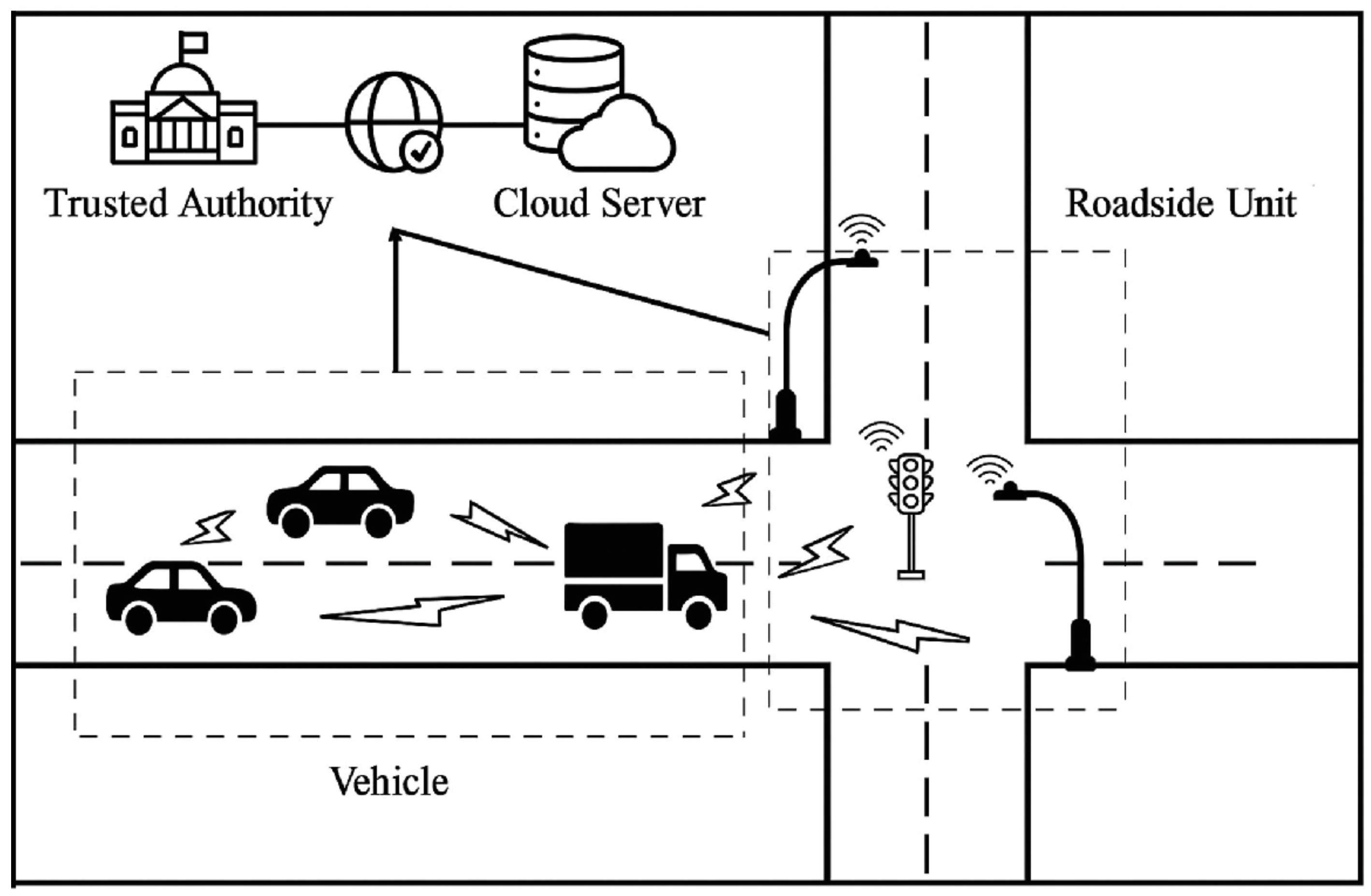
4]. As illustrated in
Figure 1, VANETs consist of three core components: Trusted Authority (TA), vehicles, and Roadside Units (RSUs), all supported by cloud servers and network infrastructure. In VANETs, the TA serves as a reliable third party with strong computational capabilities. Each vehicle is equipped with an On-Board Unit (OBU) that enables communication with nearby vehicles and RSUs. RSUs, typically installed along roadways, function as wireless devices that interact with passing vehicles and relay messages to the TA.
With the rapid advancement of Intelligent Transportation Systems (ITSs), VANETs have become an integral component of modern traffic management and service delivery. The primary goal of VANETs is to improve traffic safety and improve the efficiency of traffic flow through the sharing of information on the roads. Using vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) wireless communications, VANETs enable the real-time exchange of traffic data and support a wide range of applications, including traffic updates, emergency warnings, road condition monitoring, etc. These capabilities not only help vehicles make timely decisions about driving routes, but also contribute to the optimization of traffic signal control, thereby enhancing traffic fluidity and overall system performance. However, the widespread deployment of VANETs introduces significant challenges related to security and privacy. Key concerns include ensuring the confidentiality and integrity of communications, maintaining the quality of communication services, and securing key management mechanisms. Confidentiality is essential to prevent unauthorized access to sensitive information, while integrity ensures that traffic data remain anti-tamper and trustworthy, especially critical in preventing threats such as man-in-the-middle attacks. The reliability of communication services is also crucial, as real-time data delivery is necessary for maintaining system responsiveness and avoiding denial-of-service (DoS) attacks. Moreover, robust key management is vital for secure communications, necessitating lightweight storage solutions and efficient key generation methods—issues that remain central to the continued development of secure VANET infrastructures.
To mitigate potential cybersecurity threats, it is essential to establish a secure communication protocol for identity verification. However, most protocols proposed in the existing literature are based on traditional cryptographic techniques. These include ECC-based conditional privacy-preserving identity verification protocols [
5], signature-based authentication methods [
6], and group-signature-based identity verification schemes [
7]. With the rapid advancement of quantum computing, these conventional protocols face significant challenges, as quantum algorithms, such as Shor’s algorithm [
8], can compromise the security of widely used cryptographic primitives. In response to the emerging threat posed by quantum computing, post-quantum cryptography has garnered increasing attention as a promising solution. The primary approaches are generally classified into five categories: hash-based cryptography [
9], code-based cryptography [
10], multivariate cryptography [
11], supersingular isogeny-based cryptography [
12], and lattice-based cryptography [
13], which is adopted in this paper. Unlike traditional cryptographic methods, these approaches do not rely on number-theoretic problems, allowing them to remain secure even in the presence of quantum-computing capabilities.
In this paper, we focus on lattice-based cryptography and present a security analysis of the identity authentication protocol proposed by Li et al. [
14]. To address the security vulnerabilities identified in their method, we propose an enhanced authentication protocol. In particular, to mitigate the risk of master private key disclosure, we redesign the key generation mechanism to eliminate the weaknesses present in Li et al.’s original approach. A well-designed secure authentication protocol must satisfy a range of security requirements, including confidentiality, integrity, and non-repudiation. These requirements are essential to ensure that the protocol remains secure and reliable under various attack scenarios, with detailed descriptions of these security requirements as follows:
Integrity: The RSU must be able to verify the validity of received messages and ensure that they have not been tampered with during transmission.
Anonymity: The true identity of the vehicle must remain hidden from all entities, except the trusted third-party authentication authority.
Traceability: When necessary, the trusted third-party authority must be able to reveal the real identity of the vehicle or the RSU from the transmitted message.
Unlinkability: It must be computationally infeasible for RSUs or malicious attackers to correlate two different messages as originating from the same vehicle.
Attack resistance: The protocol must be resilient against various common attacks in VANETs, including man-in-the-middle attacks, replay attacks, verification table stealing attacks, and forgery attacks. Crucially, the protocol should also be secure against quantum-based attacks.
The remainder of this paper is organized as follows:
Section 2 reviews related works and identifies the limitations of existing lattice-based authentication schemes.
Section 3 presents the proposed lattice-based identity authentication protocol with a detailed design and workflow.
Section 4 provides the performance evaluation and experimental results.
Section 5 analyzes the computational complexity and security properties. Finally,
Section 6 concludes the paper and outlines future research directions.
2. Review of Li et al.’s Proposed Protocol
We review the privacy-preserving authentication protocol proposed by Li et al. [
14]. The roles of each entity are described below:
Trusted Authority (TA): In vehicular ad hoc networks (VANETs), the TA serves as a trusted third party with substantial computational resources.
Vehicle: Each vehicle is equipped with an On-Board Unit (OBU) capable of communicating with nearby vehicles and RSUs.
RSUs: Typically installed along roadways, RSUs are wireless communication devices that interact with vehicles and relay messages to the TA.
The protocol comprises three main phases: the system initialization phase, the message signing phase, and the message verification phase. Additionally, key notations are defined as follows:
2.1. System Initialization Phase
During the system initialization phase, the TA performs the following steps to generate the necessary system parameters. After the vehicle completes registration, the TA stores the corresponding vehicle information in the OBU. Detailed descriptions are as follows:
System Parameter Generation: The TA generates the system parameters
Trapdoor Generation: The TA executes the probabilistic polynomial time
TrapGen algorithm [
15] to generate the master public key
and a the master private key
.
Hash Function Initialization: The TA initializes four cryptographic hash functions, and , which are defined as follows: .
OBU Key Generation: The TA computes
and selects a real number
. Then, the TA uses the
SampleD algorithm [
16] to generate the OBU’s private key
based on
, such that
.
System Parameter Publication: TA publishes the system parameters .
Vehicle Registration: After the vehicle registers with the TA, the TA stores the vehicle’s real identity (RID), password (PWD), and transmits the corresponding OBU private key to the OBU.
2.2. Message Signing Phase
The vehicle transmits and to the OBU. The OBU verifies whether and . If either parameter does not match, all requests are rejected.
The OBU generates
according to a Gaussian distribution [
17].
The OBU computes , and , and forms the anonymous identity of the vehicle as .
The OBU calculates .
The OBU generates the private key and transmits to the vehicle.
The vehicle generates a random matrix and computes .
The vehicle calculates .
The vehicle signs the message as and transmits to other vehicles or RSU.
2.3. Message Verification Phase
Upon receiving the message, the verifier performs the following steps:
Verify the validity of the timestamp. If the timestamp is invalid, subsequent verification is aborted.
Verify whether . If this condition is satisfied, the verification is considered successful.
2.4. Analysis
According to the verification equation , the verifier requires the hashing value of the vehicle’s identity . However, to maintain privacy, the verifier does not have access to the actual identity, and the corresponding hashing value is not transmitted during communication. Consequently, this verification approach is impractical. Furthermore, if a vehicle transmits false information, this protocol cannot determine the true identity of the vehicle from transmitted data or public key information. Without , the TA cannot run the algorithm SampleD to get the secret key and further recover from .
Although Li et al. defined as the public key, the verifier still cannot obtain the correct value without prior transmission or registration linkage. Even if is transmitted, the original scheme still lacks a complete tracing mechanism, as the Trusted Authority (TA) cannot reconstruct the mapping between and the real identity without additional encrypted binding. Our proposed method addresses this by introducing pseudo-identities , which allow the TA to perform decryption and recover the real identity when misbehavior occurs.
3. Our Methods
In this section, we present the design and operational details of the proposed identity authentication protocol, which is built on lattice-based cryptography to ensure postquantum security and conditional privacy in vehicular networks. To address the concern about accountability, our protocol introduces a tracking mechanism. Although Road Side Units (RSUs) and other vehicles only receive pseudo-IDs that cannot reveal the real identity, the Trusted Authority (TA) holds the master secret and can map a pseudo-ID back to the corresponding real ID. If a vehicle transmits false or malicious information, the TA can decrypt the pseudo-ID to recover the true identity and enforce penalties. This design ensures that the scheme maintains privacy during normal operations while still preserving traceability and accountability in the event of misbehavior.
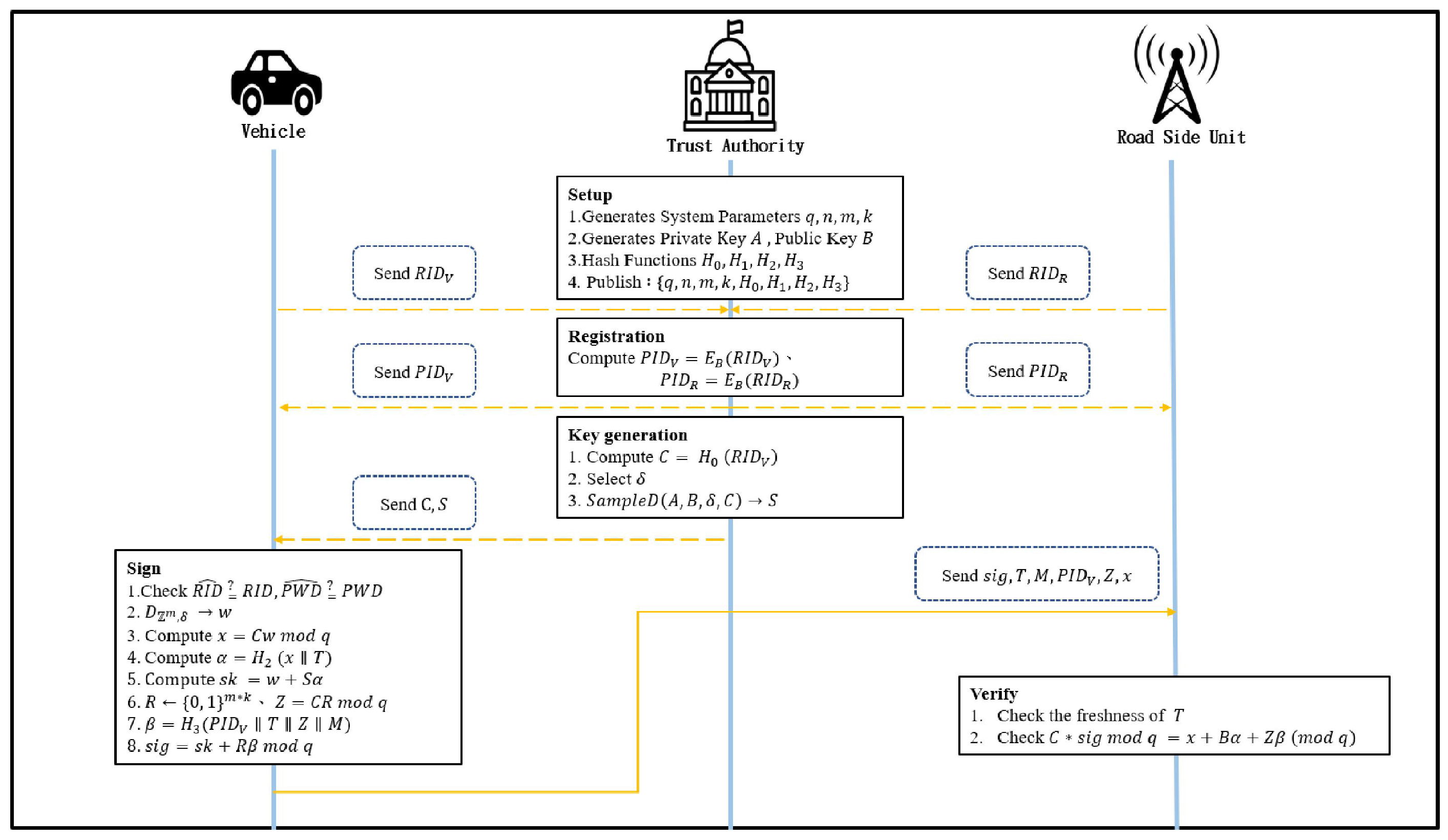
The protocol is structured into six distinct phases: system initialization, registration, key generation, message signing, message verification, and dispute settlement. Each phase is carefully designed to avoid the exposure of master private keys, thereby overcoming the key leakage vulnerability observed in previous works, such as the scheme by Li et al. [
14]. The system consists of three core entities: the TA, Vehicles, and RSUs. The TA is assumed to be fully trusted, computationally powerful, and safe to operate. It is responsible for generating the cryptographic parameters in the system and managing the registration of entities. Vehicles are mobile nodes equipped with On-Board Units (OBUs) and participate in message broadcasting. RSUs are fixed infrastructure nodes that receive, verify, and relay vehicle messages to the TA or other vehicles. Communication occurs over a vehicular ad hoc network (VANET), with cloud-based support for TA connectivity and certificate storage.
We assume that the initial key distribution between the TA and both Vehicles and RSUs occurs over a secure and authenticated channel. After registration, all entities are expected to follow the protocol honestly. The adversary is considered to be passive (eavesdropping) or active (message forging or replay), but not capable of compromising the TA. The security of the protocol relies on the computational hardness of the Short Integer Solution (SIS) and Inhomogeneous Short Integer Solution (ISIS) problems, which are widely regarded as being resistant to quantum attacks. Specifically, SIS is used in the construction of hash-based commitments and pseudonymous identities, while ISIS forms the basis for the signature generation and verification process. The protocol employs the
TrapGen algorithm to generate a public matrix
and a corresponding trapdoor
, which allows for the TA to sample short lattice vectors using the
SampleD algorithm. The hash functions, denoted as
and
, are used in the protocol. We set the parameters as follows:
, and modulus
, which provides approximately 128-bit post-quantum security. The discrete Gaussian distribution used in key sampling has a standard deviation
, and a tail-cutoff of
is enforced for negligible rejection rates. The symbols used in our proposed protocol are the same as those defined in
Table 1.
Detailed descriptions of each phase are provided below.
3.1. Initialization Phase
The TA generates all system security parameters, along with the system’s public and private keys, initializes four hash functions, and finally publishes the system information. The detailed steps are as follows:
Parameter Generation: The TA generates the security parameter n, a prime number , and two positive integers k and m, where .
Key Generation: The TA runs to generate the system master public key and the system master private key , such that and .
Hash Function Definition: TA defines four hash functions and , as follows: , , , and .
Publication: The TA publicly releases all the security parameters and hash functions of the system: .
3.2. Registration Phase
The vehicle and the RSU each register with the TA using their real identities. The TA then uses its system master public key to encrypt these identities and generate the corresponding anonymous identities. The detailed steps are as follows:
The RSU sends its real identity to the TA for registration.
The vehicle sends its real identity and the corresponding password to the TA for registration.
The TA encrypts and using the system master public key B, obtaining and , and returns the encrypted identities to the vehicle and the RSU, respectively. We refer to this encrypted identity as a pseudo-identity.
3.3. Key Generation Phase
The TA uses the pseudo-identity of the vehicle to generate the public key and the private key of the vehicle. The key generation process for the RSU is identical; therefore, we will describe only the vehicle’s key generation process:
Compute .
Select a real number .
Execute the algorithm to generate , ensuring .
Transmit and to the vehicle.
3.4. Message Signing Phase
In this phase, the driver is responsible for logging into the system using the registered real identity () and password (). Upon receiving these credentials, the vehicle’s On-Board Unit (OBU) verifies whether the input and match the records stored during registration. The vehicle combines the current timestamp with a Gaussian distribution to generate a key to verify the signature and uses this key to sign the message. The detailed signing steps are as follows:
Receive inputs and , and verify whether and . If either parameter does not match, the request is rejected.
Samples w from the Gaussian distribution .
Compute .
Concatenate with the current timestamp , apply the hash function , and compute .
The vehicle calculates , obtaining the key for signature generation.
Generate a random matrix and compute .
Compute for the message , where .
Generate the signature and transmit , the current timestamp , the message , the anonymous identity , , and to the RSU or other vehicle.
3.5. Message Verification Phase
After receiving the message, the RSU or other vehicle uses the current timestamp and a relational expression to verify the validity of the signature. The detailed verification steps are as follows:
Therefore, the verification equation holds, and the signature is valid. By successfully verifying the signature in this manner, the RSU or other vehicle can confirm both the integrity of the message and the authenticity of the sender while preserving the anonymity of the vehicle. The RSU or other vehicle can then proceed to process the verified message and, if applicable, forward it to other vehicles or the central authority for further action.
3.6. Dispute Settlement
If a vehicle transmits a false message, its real identity can be retrieved by TA through the following steps:
Verify whether the following equation holds: If the equation holds, it confirms that the message is indeed transmitted by the vehicle.
Use its private key to decrypt and reveal the real identity .
The complete method flow is depicted in the
Figure 2 below.
4. Results
To ensure the reproducibility of this research, the configuration parameters used in the evaluation are described as follows: The lattice dimension is set to , the modulus to , and the Gaussian standard deviation to . The message size is configured as 256 bytes, and the hash function adopts SHA-3. These parameters are selected according to standard recommendations in lattice-based cryptography, striking a balance between post-quantum security and computational efficiency in VANET environments.
4.1. Security Analysis
We analyze the security of the proposed method based on two fundamental hard problems in lattice-based cryptography: the Short Integer Solution (SIS) problem [
18] and the Inhomogeneous Short Integer Solution (ISIS) problem [
18]. Both problems are known to be computationally hard, even in the presence of quantum adversaries, and form the basis for the security of many post-quantum cryptographic schemes.
Definition 1. SIS problem: Given integers , a random matrix , and a real number β, the goal is to find a non-zero vector v, such that and .
The hardness of the SIS problem underpins the unforgeability of signatures in our protocol. Without knowledge of the secret key, an attacker would need to solve an SIS instance in order to generate a valid signature that satisfies the required verification equation.
Definition 2. ISIS problem: Given integers , a random matrix , a target vector , and a real number β, the goal is to find a non-zero vector v, such that and .
The ISIS problem is directly related to the generation of valid signatures within our scheme. Each signature produced by a legitimate vehicle corresponds to solving an instance of the ISIS problem, with the secret key enabling efficient sampling of the solution vector vvv. Without access to the secret key, an adversary cannot efficiently generate such a vector, ensuring the robustness of the signature mechanism. Since both SIS and ISIS are believed to be hard even for quantum computers, our protocol inherits strong post-quantum security guarantees. This makes it well-suited for deployment in future VANETs, where long-term security and resilience against emerging quantum threats are critical.
We outline a reduction from breaking the proposed protocol to solving the SIS/ISIS problems. If an adversary
can forge a valid authentication or derive the real identity with non-negligible probability, then a challenger
can construct an algorithm that uses
’s advantage to solve the underlying SIS/ISIS instance. This implies that the security of our protocol is tightly based on the hardness of SIS/ISIS problems, thus ensuring resistance against quantum attacks. Our improved protocol satisfies both the original security goals of Li et al.’s protocol [
14] and offers enhanced protection in the following areas:
Message Integrity: Upon receiving , the verifier confirms message integrity by verifying: . Thus, the message integrity is guaranteed. The security of our protocol is based on the hardness of the ISIS problem, making it infeasible for attackers to forge valid signatures within polynomial time.
Identity Privacy: Vehicles communicate only through anonymous identities . Without access to the master private key B, it is computationally infeasible to recover the real identity . Therefore, the protocol protects the privacy of the identity of the vehicle.
Traceability: Although vehicles use anonymous identities during communication, in emergencies, the Trusted Authority (TA) can recover the real identity by decrypting with the master private key B. Hence, the system maintains traceability.
Unlinkability Due to the randomness of and in the calculations and , signatures and messages from the same vehicle cannot be linked. The protocol thus ensures unlinkability.
Attack Resistance: Our protocol is designed to resist a variety of attacks:
Man-in-the-Middle Attacks: Based on the hardness of the ISIS problem, signatures are unforgeable. Message integrity checks between vehicles and RSUs prevent tampering.
Replay Attacks: Each signature includes a timestamp . The verifier checks its validity before accepting the message, defending against replay attacks.
Forgery Attacks: Signature verification using the equation ensures any forged or modified message is detected.
Verification Table Stealing: The protocol does not store verification tables. That is, only the private keys to TA and the vehicles are kept. Thereby, our protocol prevents from verification table theft.
Quantum Attacks: The cryptographic primitives in this protocol are lattice-based (ISIS/SIS), making them resilient against quantum attacks due to their proven post-quantum security.
4.2. Comparative Security Evaluation
Our improved protocol was evaluated against key security metrics, including message integrity, identity privacy, traceability, unlinkability, and resistance to various attacks.
Table 2 compares the proposed scheme with that of Li et al. [
14].
According to
Table 2, Li et al.’s protocol [
14] cannot achieve message integrity and traceablity. In the message verification, the verifier requires the hashing value of the vehicle’s identity
. However, to preserve privacy, the verifier does not have access to the real identity
, and the corresponding hashing value is not transmitted during communication. Therefore, this verification method is not feasible in practice. Furthermore, if the TA attempts to trace the vehicle’s real identity, the TA cannot execute the
SampleD algorithm to generate the secret key
and therefore cannot recover the real identity
from
.
In addition to Li et al. [
14], several recent studies have explored lattice-based authentication in VANETs. Prajapat et al. [
13] proposed a lattice-based aggregate signature scheme to enhance message aggregation efficiency, while Huang et al. [
12] introduced an isogeny-based signature with lower key sizes. Compared to these approaches, our method not only preserves quantum resistance but also introduces a practical tracing mechanism to recover the real identity in case of disputes, which is not addressed in the aforementioned schemes. Furthermore, our protocol achieves both anonymity and accountability simultaneously, balancing privacy and traceability more effectively than prior works.
5. Discussion
The proposed lattice-based identity authentication protocol introduces significant enhancements over traditional cryptographic approaches in vehicular ad hoc networks (VANETs), particularly in terms of security, privacy, and future resilience against quantum adversaries. In this section, we reflect on the broader implications of the design, assess trade-offs between security and efficiency, and discuss potential challenges and directions for future development.
5.1. Theoretical Performance Analysis
We also analyzed the computational cost and communication overhead of the protocol in terms of standard lattice parameters. The signature generation and verification procedures primarily involve matrix–vector multiplications, hash function evaluations, and discrete Gaussian sampling. For carrying out the proposed scheme, we set the lattice dimension to , modulus , Gaussian parameter , and a message size of 256 bytes. These parameters were chosen to provide a balance between post-quantum security and computational efficiency, ensuring that the reported results reflect practical feasibility in VANET environments. Signing involves the following operations:
Sampling a short vector w from a discrete Gaussian.
Generating the signature as .
Appending timestamp and pseudonym data.
The verification process requires the following:
Multiplying matrix A with signature vector .
Reconstructing and checking the equation with values .
Although lattice-based operations are heavier than ECC-based schemes, recent advancements in hardware acceleration and optimized Gaussian samplers make this computationally tractable even for embedded vehicular devices.
5.2. Trade-Offs in Efficiency and Security
A central trade-off in adopting lattice-based cryptography is the increased computational and communication overhead compared to conventional schemes based on elliptic curve cryptography (ECC) or RSA. Lattice operations, such as discrete Gaussian sampling and matrix-vector multiplication, are more computationally intensive and often result in larger key and signature sizes. However, this increase in cost is justified by the robustness of the protocol against quantum attacks. Unlike ECC or RSA, whose security depends on problems solvable by quantum algorithms (e.g., Shor’s algorithm), lattice-based schemes like ours rely on the hardness of SIS and ISIS, which are currently resistant even to quantum computation. This positions the protocol as a forward-looking solution that anticipates the post-quantum era. To mitigate the performance cost, various optimization techniques can be applied. For instance, Ring-LWE or Module-LWE variants can reduce key and signature sizes while preserving security. Moreover, modern vehicular ECUs increasingly support parallel and hardware-accelerated computation, which can significantly reduce the latency of signing and verification operations.
A notable challenge of lattice-based schemes is their relatively larger key, signature, and message sizes, as well as higher computational and memory demands compared with classical RSA or ECC. In VANETs, strict latency, bandwidth, and resource constraints must be considered. To address these challenges, our scheme adopts three optimization strategies:
Pseudo-ID compression to minimize the transmitted size.
Batching of authentication requests to reduce signaling overhead.
Careful selection of optimized lattice parameters that balance security and efficiency.
In addition, we note that modern OBUs are increasingly equipped with multicore processors and hardware acceleration, and the dominant operations in our proposed method (polynomial multiplications and hash functions) are highly parallelizable. Hence, our method confirms that even under dense network conditions, the average authentication latency remains within acceptable limits for real-time VANET applications, demonstrating that the scheme is efficient and practical despite the inherent overhead of lattice-based cryptography.
5.3. Scalability and System Integration
The modular design of our five-phase protocol allows for straightforward integration into existing VANET infrastructures. Each phase, initialization, registration, key generation, signing, and verification, is self-contained and can be implemented as part of a distributed identity management system. The use of pseudonyms and the ability to trace real identities only through the Trusted Authority (TA) ensure compliance with privacy laws while still allowing for accountability. To evaluate scalability, we analyzed the impact of increasing network size and frequent communication. As the number of vehicles grows, the communication overhead increases linearly due to more authentication requests and pseudo-ID exchanges. However, our scheme supports batching of authentication messages and pseudo-ID compression, which reduces redundant transmission costs. Moreover, computational complexity at the RSU remains manageable since verification operations are based on lightweight hash evaluations and lattice sampling. Therefore, the scheme scales efficiently in dense VANET environments, maintaining acceptable latency for real-time deployment.
5.4. Privacy and Traceability
One of the most compelling features of the proposed scheme is its support for conditional privacy. In regular operation, vehicle identities remain hidden behind pseudonyms derived from lattice-based encryption. This protects users against tracking, profiling, and location-based inference attacks. However, in cases of malicious behavior—such as the broadcasting of false information or attempts to manipulate traffic—the TA can trace the real identity using stored mappings. This traceability is achieved without relying on a central database that Roadside Units (RSUs) or other vehicles can access, ensuring that privacy is only lifted under appropriate authority and conditions. This design strikes a balance between civil privacy rights and public accountability, which is crucial in transportation networks where safety and trust are paramount.
5.5. Complexity Analysis
This section analyzes the computational, communication, and storage complexity of the proposed protocol in detail.
Computational Complexity: The dominant operations include lattice-based sampling, polynomial multiplication, and hash evaluations. Sampling and polynomial operations require time, while hashing is . Although lattice schemes incur higher costs than RSA or ECC, these operations are well suited for parallel execution and can be efficiently supported by modern vehicular processors.
Communication Complexity: Each authentication involves transmitting a pseudo-ID, a signature, and auxiliary parameters. The overall communication overhead increases linearly with the number of vehicles in the network. To mitigate this, our design incorporates pseudo-ID compression and batching of authentication requests, significantly reducing redundant data exchange and ensuring scalability in dense VANET deployments.
Storage Complexity: Vehicles store their private keys, generated pseudo-IDs, and a small number of session parameters. The TA and RSUs maintain mapping tables between pseudo-IDs and real identities for traceability. The storage overhead is moderate and remains within the memory capacity of current vehicular on-board units.
While lattice-based cryptography imposes a higher overhead compared to classical approaches, the combination of compression, batching, and parallelization ensures that the proposed scheme remains efficient and practical for real-time VANET applications.