Enhancing Two-Step Random Access in LEO Satellite Internet an Attack-Aware Adaptive Backoff Indicator (AA-BI)
Abstract
1. Introduction
- Threat-Aware Backoff Indicator Design: We propose a composite threat intensity metric (denoted as Peff) that incorporates not only traditional collision probability (Pc), but also quantifies DoS attack intensity (Pdos) and replay attack intensity (Prep). This enables accurate real-time network state assessment under malicious conditions.
- Sigmoid-Based Adaptive Window Mapping: A lightweight Sigmoid mapping function is designed to translate Peff into appropriate backoff window sizes, ensuring low latency under benign conditions and rapid attack suppression under high threats.
- Low-Complexity Offline Optimization: Critical parameters including the sensitivity coefficient k and the trigger threshold x0 of the mapping function are optimized via offline grid search, ensuring robust performance across diverse attack scenarios without introducing significant online computation.
2. Materials and Methods
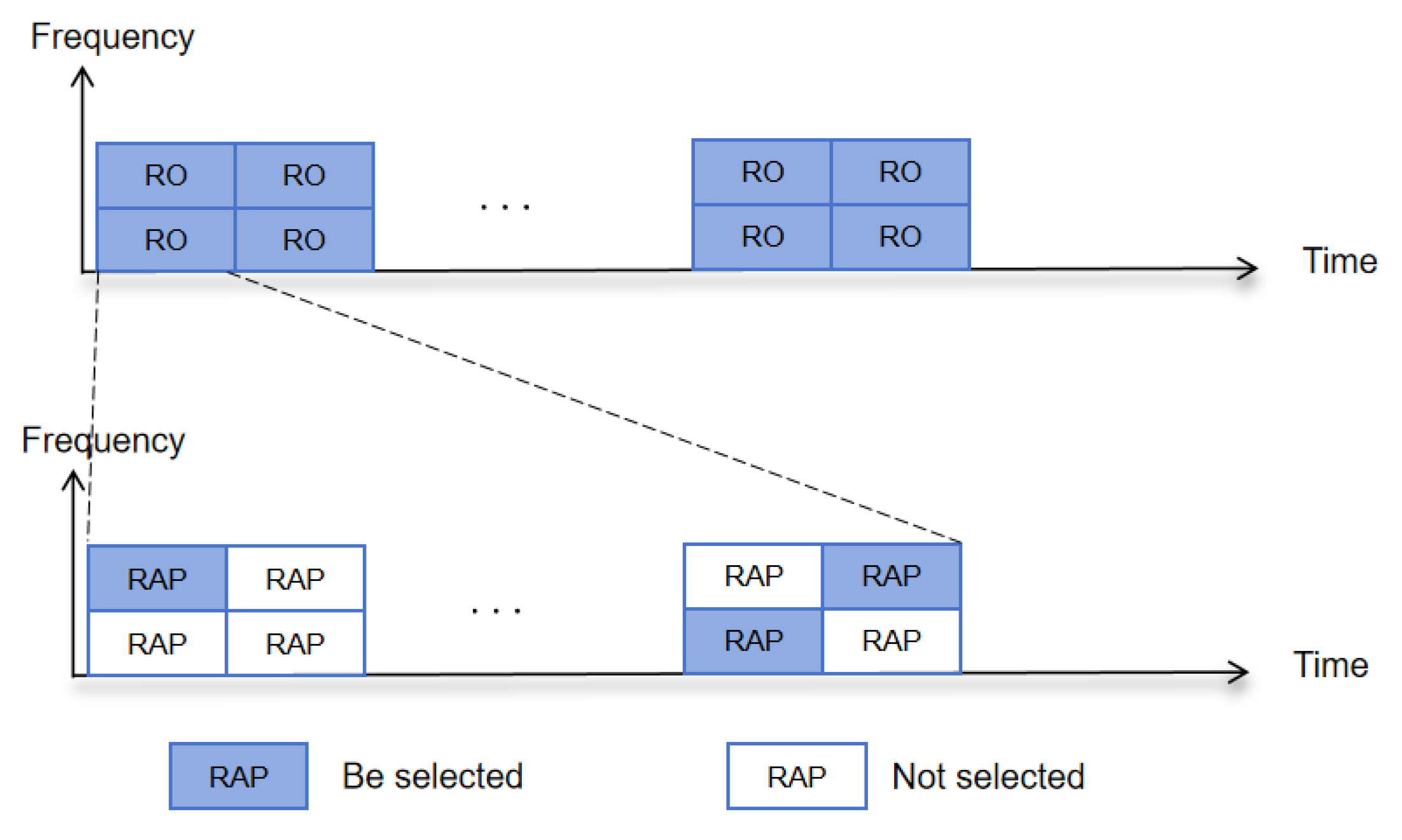
2.1. Random Access Procedure
2.2. DoS and Replay Attacks
- DoS Attack: Due to the limited computational power and bandwidth resources on satellites, DoS attacks can cause more severe damage—or even complete paralysis—to LEO satellite internet systems [18]. In this attack model, one or more malicious nodes (attackers) continuously transmit a large number of forged random access preambles over the PRACH. These preambles may be completely random or may mimic legitimate UE. The primary goal is to exhaust the limited resources of the PRACH, causing access requests from legitimate UE to fail due to either resource unavailability or collisions. In our model, the intensity of the DoS attack is quantified by Pdos, defined as the proportion of access requests sent by attackers within the total PRACH load. This attack significantly increases the collision probability on the channel, misleading conventional BI mechanisms into misjudging the network as experiencing high load, thereby inappropriately increasing the backoff window for all UEs.
- Replay Attack: The replay attack is a more stealthy form of assault. The attacker first intercepts legitimate MsgA transmissions from UE through eavesdropping or other means. At a later time, the attacker retransmits these intercepted legitimate messages into the PRACH. Since the MsgA itself is valid, this type of attack is more difficult to detect using traditional signature-based detection methods. The objective of the replay attack is to create artificial contention and collisions, disrupt the gNodeB’s assessment of channel status, and cause legitimate UE to fail during the contention resolution phase—thereby also increasing the channel collision rate. In our model, the intensity of the replay attack is quantified by Prep, defined as the ratio of replayed access requests to the total PRACH load.
3. Attack-Aware Adaptive Backoff Indicator (AA-BI)
| Algorithm 1: Attack-Aware Adaptive Backoff Indicator (AA-BI) |
| Input: Collision probability Pc, DoS attack intensity Pdos, Replay attack intensity Prep, sensitivity coefficient k, activation threshold x0, minimum backoff window Wmin, maximum backoff window Wmax |
| Output: Backoff window W for each UE |
| //gNodeB side: 1. Monitor the random access channel and 2. Estimate Pc, Pdos, Prep. 3. Compute the composite threat intensity Peff = Pc + Pdos + Prep. 4. Broadcast Peff to all User Equipments (UEs) within the coverage area. |
| //UE side: 5. Upon receiving Peff from gNodeB: 6. Calculate the Sigmoid mapping factor: f(Peff) = 1/(1 + exp(−k ∗ (Peff − x0))) 7. Determine the backoff window: W = Wmin + (Wmax − Wmin) ∗ f(Peff) 8. Select a random backoff time uniformly from [0, W] 9. Wait for the backoff time before initiating a new access attempt. |
4. Performance Evaluation and Simulation Analysis
4.1. Simulation Environment and Parameter Design
4.2. Evaluation Metrics
4.3. Compared Algorithms
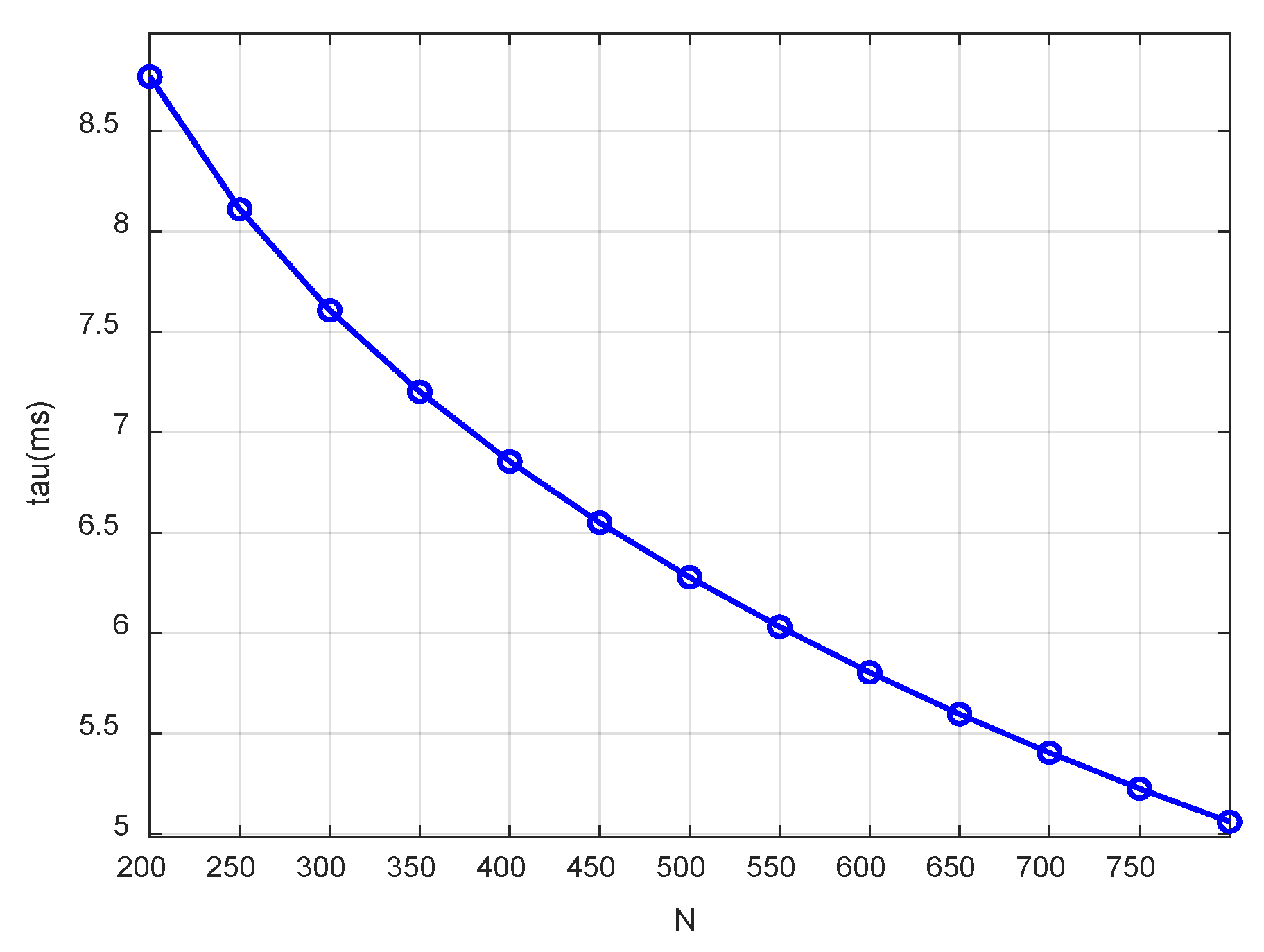
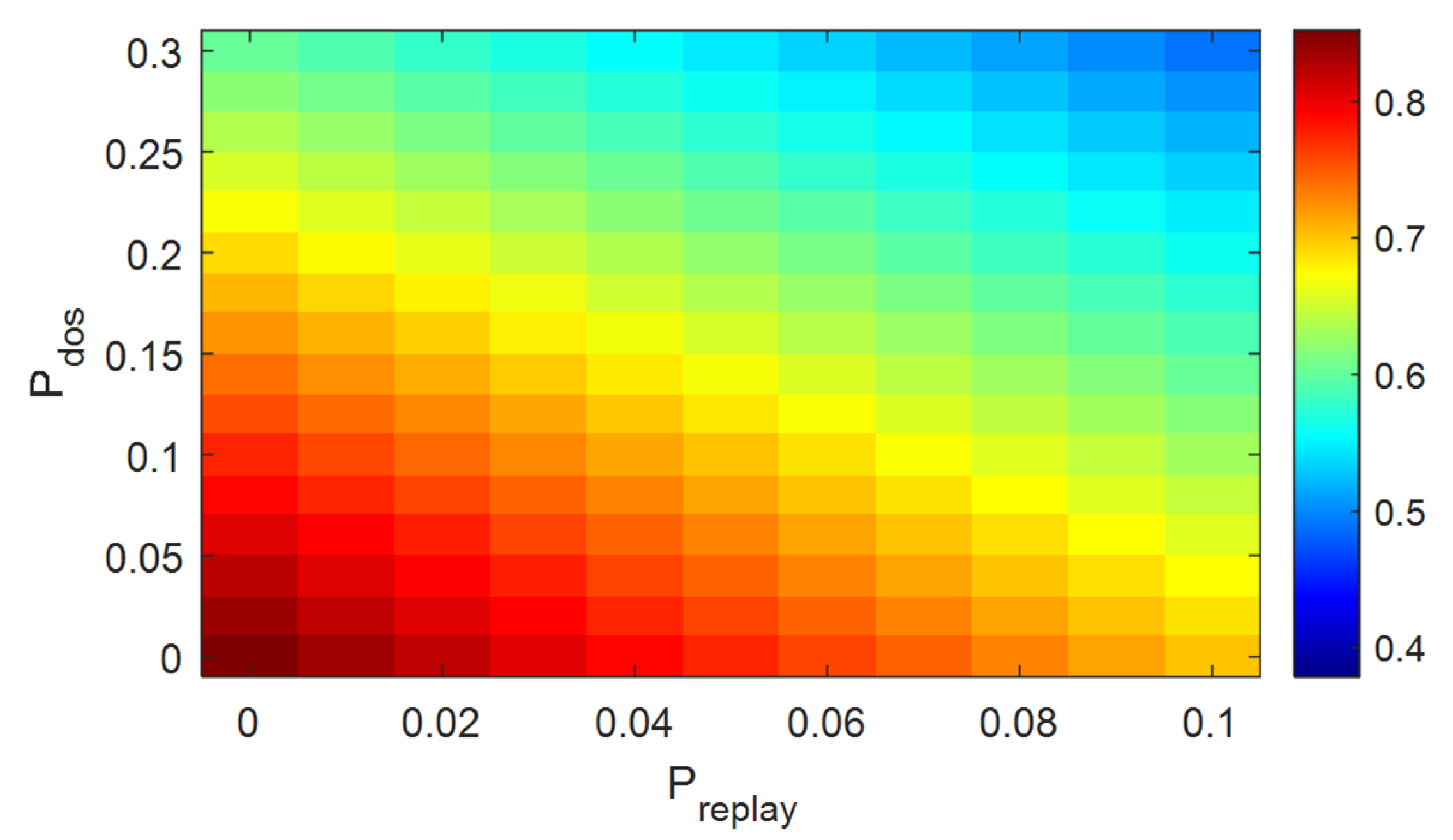
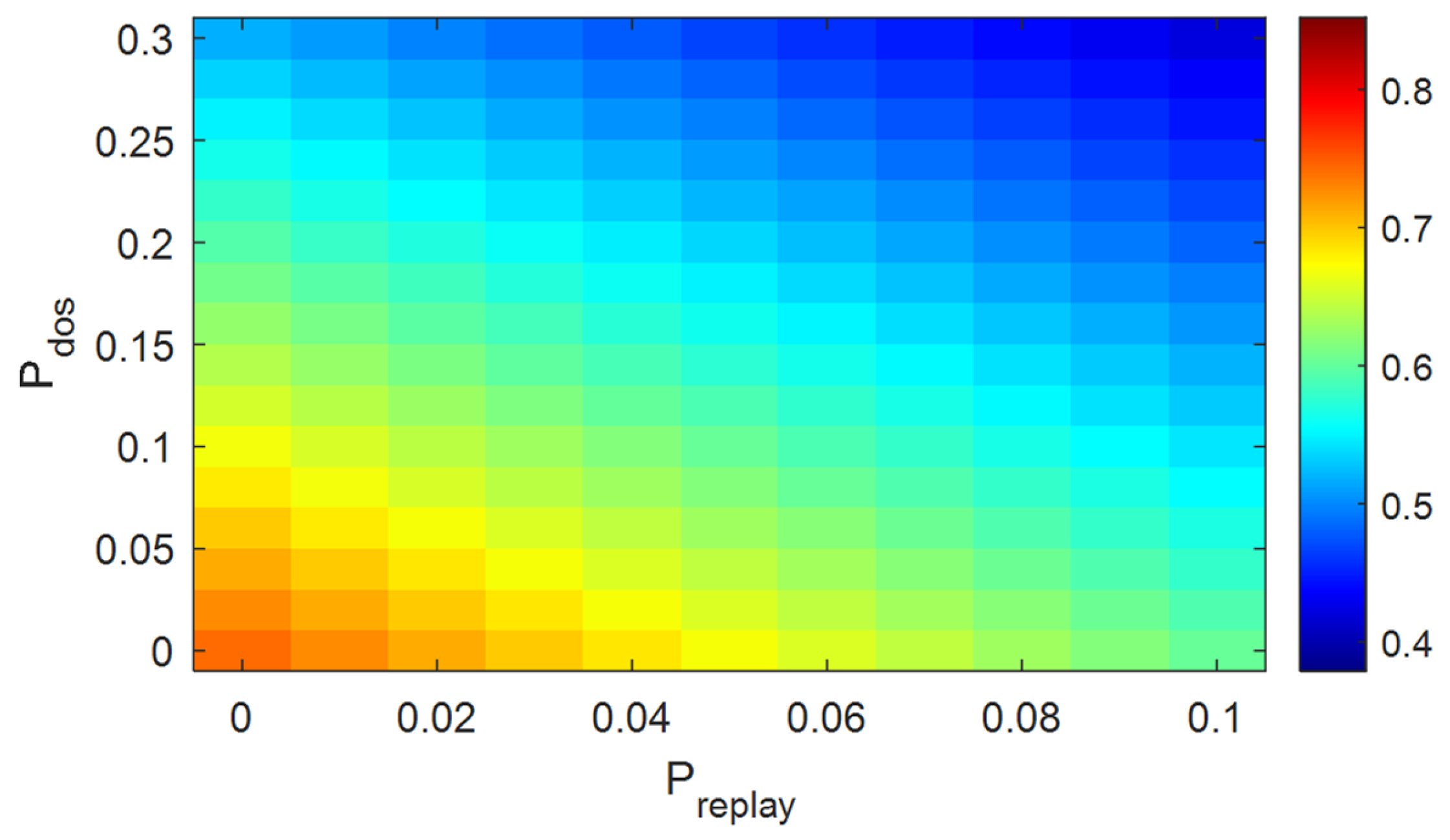
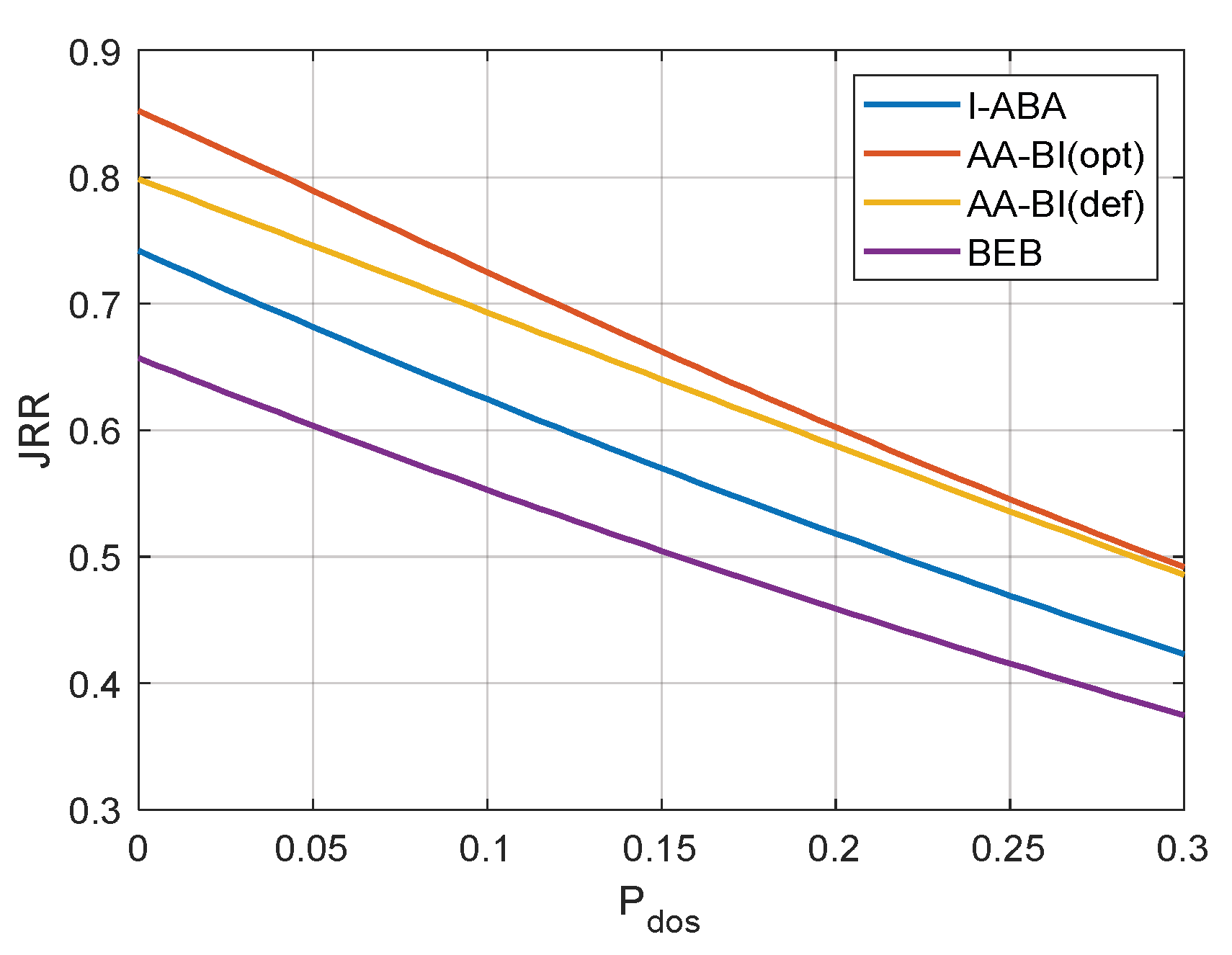
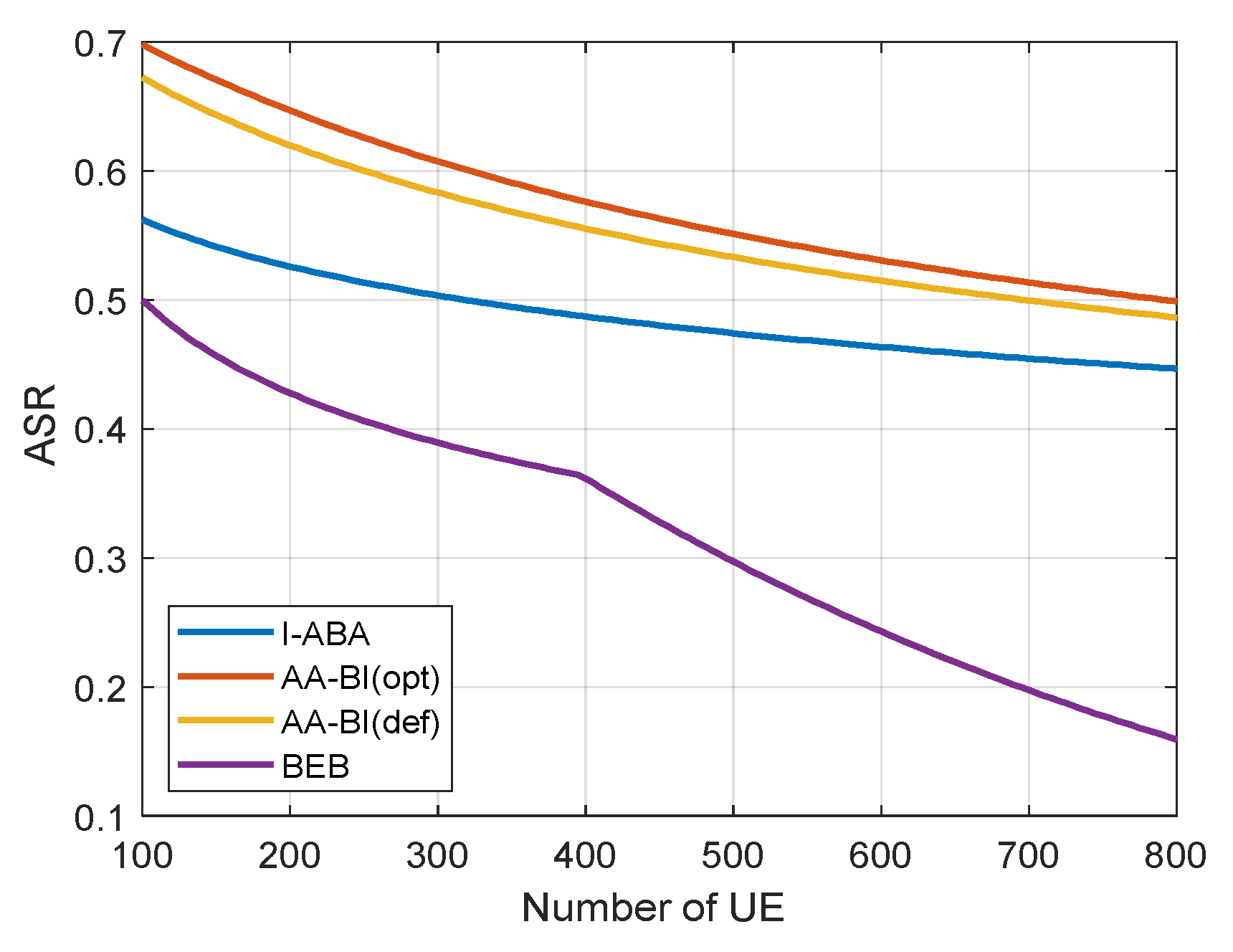
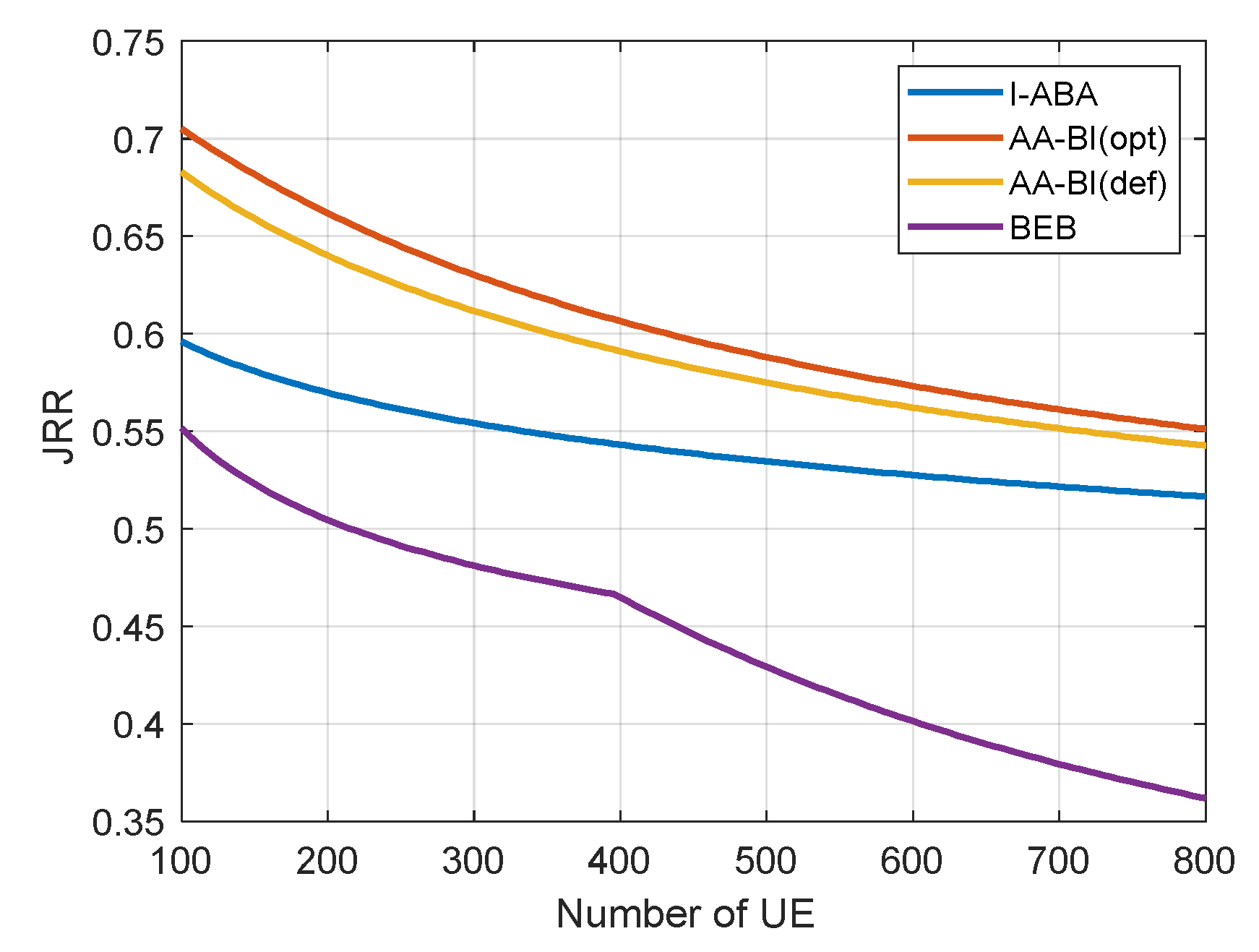
4.4. Analysis of Simulation Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhou, Y.; Chen, H.; Dou, Z. MOLM: Alleviating Congestion through Multi-Objective Simulated Annealing-Based Load Balancing Routing in LEO Satellite Networks. Future Internet 2024, 16, 109. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Iglesias-Sanuy, P.; López-Ardao, J.C.; Rodríguez-Pérez, M.; Herrería-Alonso, S.; Suárez-González, A.; Rodríguez-Rubio, R.F. An Efficient Location-Based Forwarding Strategy for Named Data Networking and LEO Satellite Communications. Future Internet 2022, 14, 285. [Google Scholar] [CrossRef]
- Althumali, H.D.; Othman, M.; Noordin, N.K.; Hanapi, Z.M. Dynamic Backoff Collision Resolution for Massive M2M Random Access in Cellular IoT Networks. IEEE Access 2020, 8, 201345–201359. [Google Scholar] [CrossRef]
- Non-Terrestrial Networks (NTN). Available online: https://www.3gpp.org/technologies/ntn-overview (accessed on 24 August 2025).
- 3GPP. Solutions for NR to Support Non-Terrestrial Networks (NTN), TR 38.821, Version 19.0.0; 3GPP: Sophia Antipolis, France, 2019.
- Guidotti, A.; Cioni, S.; Colavolpe, G.; Conti, M.; Foggi, T.; Mengali, A.; Montorsi, G.; Piemontese, A.; Vanelli-Coralli, A. Architectures, Standardisation, and Procedures for 5G Satellite Communications: A Survey. Comput. Netw. 2020, 183, 107588. [Google Scholar] [CrossRef]
- IEEE 802.15.4-2020; IEEE Standard for Low-Rate Wireless Networks. IEEE: Manhattan, NY, USA, 2020.
- Khanafer, M.; Guennoun, M.; El-Abd, M. Improved Adaptive Backoff Algorithm for Optimal Channel Utilization in Large-Scale IEEE 802.15.4-Based Wireless Body Area Networks. Future Internet 2024, 16, 313. [Google Scholar] [CrossRef]
- Halloush, R.D. Transmission Early-Stopping Scheme for Anti-Jamming Over Delay-Sensitive IoT Applications. IEEE Internet Things J. 2019, 6, 7891–7906. [Google Scholar] [CrossRef]
- Yan, P.; Chu, F.; Jia, L.; Qi, N. A Cross-Layer Anti-Jamming Method in Satellite Internet. IET Commun. 2023, 17, 121–133. [Google Scholar] [CrossRef]
- Mostafa, A.; Kousar, M.; Tu, W.; Bag-Mohammadi, M. Physical-layer Jammer Detection in Multi-hop IoT Networks. IEEE Internet Things J. 2023, 10, 1. [Google Scholar]
- Liu, J.; Zhao, X.; Wang, Y.; Liu, H.; Zhang, Y.; Wang, X.; Gan, J.; Li, D. A Resource Optimization for Two-Step Random Access in 5G New Radio. J. Phys. Conf. Ser. 2023, 2625, 012063. [Google Scholar] [CrossRef]
- Krummacker, D.; Veith, B.; Lindenschmitt, D.; Schotten, H.D. Radio Resource Sharing in 6G Private Networks: Trustworthy Spectrum Allocation for Coexistence through DLT as Core Function. In Proceedings of the 1st International Conference on 6G Networking (6GNet 2022), Paris, France, 6–8 July 2022. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.H.; Debbah, M. A Tutorial on UAVs for Wireless Networks: Applications, Challenges, and Open Problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef]
- Kim, T.; Chae, S.H.; Bang, I. Two-Step Random Access With Message Replication for Low-Earth Orbit Satellite Networks. IEEE Wirel. Commun. Lett. 2025, 14, 1. [Google Scholar] [CrossRef]
- Dawy, Z.; Saad, W.; Ghosh, A.; Andrews, J.G.; Yaacoub, E. Toward Massive Machine Type Cellular Communications. IEEE Wirel. Commun. 2017, 24, 120–128. [Google Scholar] [CrossRef]
- Guo, W.; Xu, J.; Pei, Y.; Yin, L.; Jiang, C.; Ge, N. A Distributed Collaborative Entrance Defense Framework Against DDoS Attacks on Satellite Internet. IEEE Internet Things J. 2022, 9, 15497–15510. [Google Scholar] [CrossRef]





| Parameter | Description | Value |
|---|---|---|
| N | Total number of units of UE in the network | 200–800 |
| BE | Backoff Exponent | 3–11 |
| Wmin | Minimum backoff window | 8 |
| Wmax | Maximum backoff window | 2048 |
| k | Sensitivity coefficient | 0–20 |
| x0 | Activation threshold | 0–0.05 |
| Pdos | DoS attack intensity | 0–0.3 |
| Prep | replay attack intensity | 0–0.1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, J.; Wang, Y.; Zhao, Q.; Ma, R.; Yang, J. Enhancing Two-Step Random Access in LEO Satellite Internet an Attack-Aware Adaptive Backoff Indicator (AA-BI). Future Internet 2025, 17, 454. https://doi.org/10.3390/fi17100454
Dong J, Wang Y, Zhao Q, Ma R, Yang J. Enhancing Two-Step Random Access in LEO Satellite Internet an Attack-Aware Adaptive Backoff Indicator (AA-BI). Future Internet. 2025; 17(10):454. https://doi.org/10.3390/fi17100454
Chicago/Turabian StyleDong, Jiajie, Yong Wang, Qingsong Zhao, Ruiqian Ma, and Jiaxiong Yang. 2025. "Enhancing Two-Step Random Access in LEO Satellite Internet an Attack-Aware Adaptive Backoff Indicator (AA-BI)" Future Internet 17, no. 10: 454. https://doi.org/10.3390/fi17100454
APA StyleDong, J., Wang, Y., Zhao, Q., Ma, R., & Yang, J. (2025). Enhancing Two-Step Random Access in LEO Satellite Internet an Attack-Aware Adaptive Backoff Indicator (AA-BI). Future Internet, 17(10), 454. https://doi.org/10.3390/fi17100454






