Minimal Overhead Modelling of Slow DoS Attack Detection for Resource-Constrained IoT Networks
Abstract
1. Introduction
- A lightweight resource-efficient slow DoS detection model.
- Minimal processing overheads compared to alternative models that require large datasets and bi-directional packet capture.
- Model efficiency utilising a computationally lightweight decision tree classifier.
- A robust evaluation environment using non-default attack parameters.
- Critical impact analysis of the role of genuine SN in detection performance.
- Resource cost modelling to balance accuracy and efficiency.
2. Related Work
2.1. Detection and Mitigation Approaches
2.2. Data Capture Strategies and Resource Lightweight Solutions
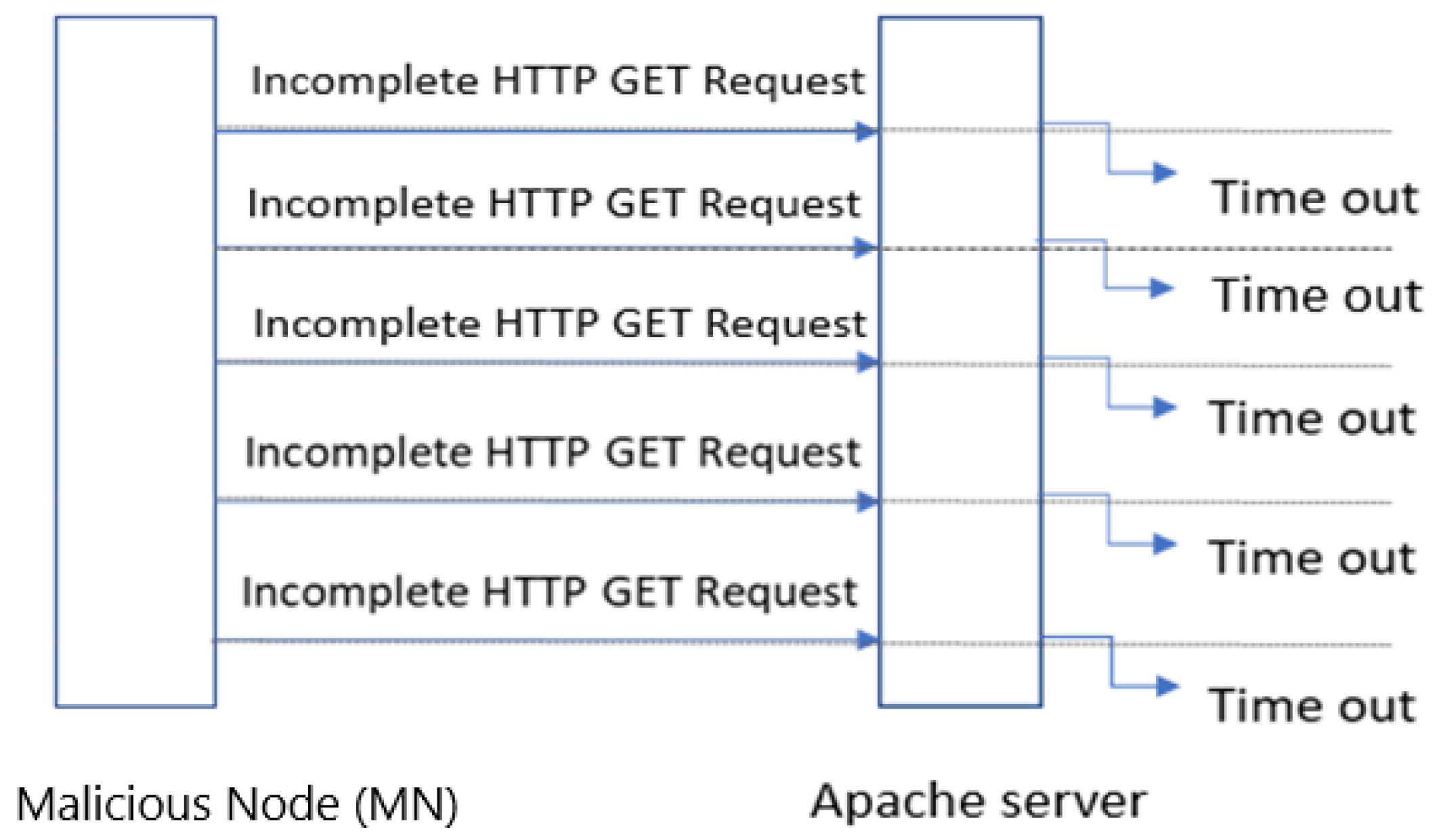
3. The Three Slow DoS Variants
3.1. Slow GET (SG)
3.2. Slow Read (SR)
3.3. Slow POST (SP) (aka R.U.Dead.Yet)
3.4. Slow DoS Detection Issues
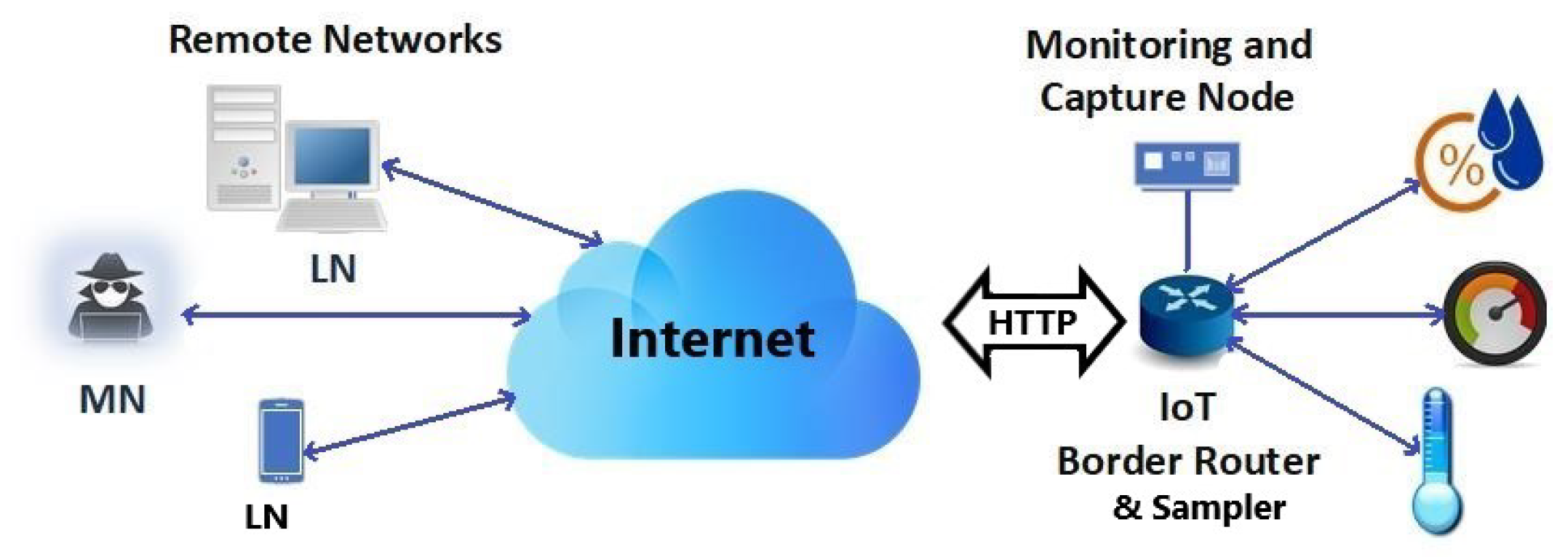
4. Research Methods
4.1. Comparison of Datasets
4.2. Stealthy Slow DoS and Slow Nodes
5. Critical Results Evaluation
5.1. Observations
Summary
6. Modelling Accuracy and Processing Cost
- = Accuracy as a function of the packet count .
- = Initial accuracy at packet count
- = Final accuracy (maximum achievable)
- = Initial packet count (where growth begins)
- = Growth rate parameter for accuracy increase
6.1. Application Cost Modelling
6.2. Modelling Performance
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| FPC | Full Packet Capture |
| LPC | Limited Packet Capture |
| SN | slow Legitimate Node |
| SG | slow GET |
| SR | slow Read |
| SP | slow POST |
| LN | Legitimate Node |
| MN | Malicious Node |
| TP | Traffic Profile |
| TCP/IP Packet Length | |
| Packet Delta Time |
References
- Rizzardi, A.; Zachos, G.; Mantas, G.; Porfyrakis, K.; Rodriguez, J. Implementing Anomaly-Based Intrusion Detection for Resource-Constrained Devices in IoMT Networks. Sensors 2025, 25, 1216. [Google Scholar] [CrossRef]
- Wakili, A.; Bakkali, S. Privacy-Preserving Security of IoT Networks: A Comparative Analysis of Methods and Applications. Cyber Secur. Appl. 2025, 25, 100084. [Google Scholar] [CrossRef]
- Cao, Z.; Zhao, Z.; Shang, W.; Ai, S.; Shen, S. Using the ToN-IoT dataset to develop a new intrusion detection system for industrial IoT devices. Multimed. Tools Appl. 2024, 84, 16425–16453. [Google Scholar] [CrossRef]
- Sinha, S. Number of Connected IoT Devices Growing 13% to 18.8 Billion. 2024. Available online: https://iot-analytics.com/number-connected-iot-device (accessed on 2 January 2025).
- Saied, M.; Guirguis, S.; Madbouly, M. Review of filtering based feature selection for Botnet detection in the Internet of Things. Artif. Intell. Rev. 2025, 58, 114. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.S.; Kouadri, S. A Reliable Real-Time slow DoS Detection Framework for Resource-Constrained IoT Networks. In Proceedings of the 2021 IEEE Global Communications Conference: IoT and Sensor Networks (Globecom2021 IoTSN), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Kampourakis, V.; Makrakis, G.M.; Kolias, C. From Seek-and-Destroy to Split-and-Destroy: Connection Partitioning as an Effective Tool against Low-Rate DoS Attacks. Future Internet 2024, 16, 137. [Google Scholar] [CrossRef]
- Tripathi, N. Delays Have Dangerous Ends: Slow HTTP/2 DoS Attacks Into the Wild and Their Real-Time Detection Using Event Sequence Analysis. IEEE Trans. Dependable Secur. Comput. 2024, 21, 1244–1256. [Google Scholar] [CrossRef]
- Mohammed, M.; Shailendra, S.; Jong, R.; Park, H. Distributed denial of service attacks and its defenses in IoT: A survey. J. Supercomput. 2020, 76, 5320–5363. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.S.; Kouadri, S.M. The Guardian Node slow DoS Detection Model for Real-Time Application in IoT Networks. Sensors 2024, 24, 5581. [Google Scholar] [CrossRef]
- Coscia, A.; Dentamaro, V.; Galantucci, S.; Maci, A.; Pirlo, G. Automatic decision tree-based NIDPS ruleset generation for DoS/DDoS attacks. J. Inf. Secur. Appl. 2024, 82, 103736. [Google Scholar] [CrossRef]
- Logeswari, G.; Thangaramya, K.; Selvi, M.; Deepika Roselind, J. An improved synergistic dual-layer feature selection algorithm with two type classifier for efficient intrusion detection in IoT environment. Sci. Rep. 2025, 15, 8050. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Samarakoon, S.; Porambage, P.; Liyanage, M.; Chang, S.Y.; Kim, J.; Kim, J.; Ylianttila, M. Descriptor: 5G Wireless Network Intrusion Detection Dataset (5G-NIDD). IEEE Data Descr. 2025, 1–12. [Google Scholar] [CrossRef]
- Makina, H.; Letaifa, A.B.; Rachedi, A. Survey on security and privacy in Internet of Things -based eHealth applications: Challenges, architectures, and future directions. Secur. Priv. 2024, 7, e346. [Google Scholar] [CrossRef]
- Hasan, M.K.; Ghazal, T.M.; Saeed, R.A.; Pandey, B.; Gohel, H.; Eshmawi, A.A.; Abdel-Khalek, S.; Alkhassawneh, H.M. A review on security threats, vulnerabilities, and counter measures of 5G enabled Internet-of-Medical-Things. IET Commun. 2022, 16, 421–432. [Google Scholar] [CrossRef]
- Mendon, S. slow DOS Attack: Why It Is Dangerous and How to Detect Using a SIEM. 2016. Available online: https://www.paladion.net/blogs/how-to-detect-slow-dos-attack-using-siem (accessed on 4 January 2017).
- Dhanapal, A.; Nithyanandam, P. The slow http distributed denial of service attack detection in cloud. Scalable Comput. 2019, 20, 285–298. [Google Scholar] [CrossRef]
- NetScout. Slow Read Attacks. 2024. Available online: https://www.netscout.com/what-is-ddos/slow-post-attacks (accessed on 19 May 2024).
- Inchara, S.; Keerthana, D.; Babu, K.N.M.; Mabel, J.P. Detection and mitigation of slow DoS attacks using machine learning. In AIP Conference Proceedings; American Institute of Physics Inc.: College Park, MD, UDA, 2023; pp. 1–10. [Google Scholar] [CrossRef]
- Ilango, H.S.; Ma, M.; Su, R. A FeedForward–Convolutional Neural Network to Detect Low-Rate DoS in IoT. Eng. Appl. Artif. Intell. 2022, 114, 105059. [Google Scholar] [CrossRef]
- Haddadi, M.; Khiat, A.; Bouaoud, H.; Djehiche, H. SPGDAD: Slow HTTP-Get denial of service attack detection using ontology. Inf. Secur. J. Glob. Perspect. 2024, 34, 79–87. [Google Scholar] [CrossRef]
- UNB. CIC-IDS2017. 2017. Available online: http://www.unb.ca/cic/datasets/ids-2017.html (accessed on 21 April 2022).
- Muraleedharan, N.; Janet, B. Scaffy: A slow denial-of-service attack classification model using flow data. Int. J. Inf. Secur. Priv. 2021, 15, 106–128. [Google Scholar] [CrossRef]
- Lukaseder, T. 2017-SUEE-Data-Set. 2017. Available online: https://github.com/vs-uulm/2017-SUEE-data-set/tree/master (accessed on 17 September 2025).
- Garcia, N.; Alcaniz, T.; González-Vidal, A.; Bernabe, J.B.; Rivera, D.; Skarmeta, A. Distributed real-time slowDoS attacks detection over encrypted traffic using Artificial Intelligence. J. Netw. Comput. Appl. 2021, 173, 1084–8045. [Google Scholar] [CrossRef]
- Jablaoui, R.; Cheikhrouhou, O.; Hamdi, M.; Liouane, N. Deep learning enabled intrusion detection system for IoT security. EURASIP J. Wirel. Commun. Netw. 2025, 2025, 66. [Google Scholar] [CrossRef]
- Gogoi, B.; Ahmed, T. HTTP Low and slow DoS Attack Detection using LSTM based deep learning. In Proceedings of the 2022 IEEE 19th India Council International Conference (INDICON), Kochi, India, 24–26 November 2022; pp. 1–6. [Google Scholar]
- Kemp, C.; Calvert, C.; Khoshgoftaar, T.M.; Leevy, J.L. An approach to application-layer DoS detection. J. Big Data 2023, 10, 22. [Google Scholar] [CrossRef]
- Chen, J.; Wu, H.; Wang, X.; Wang, S.; Cheng, G.; Hu, X. IEA-DMS: An Interpretable feature-driven, Efficient and Accurate Detection Method for slow HTTP DoS in high-speed networks. Comput. Secur. 2025, 150, 104291. [Google Scholar] [CrossRef]
- Chen, J.; Wu, H.; Wang, S.; Cheng, G.; Hu, X. An Accurate and Real-Time Detection Method for Concealed slow HTTP DoS in Backbone Network. In ICT Systems Security and Privacy Protection, Proceedings of the 38th IFIP TC 11 International Conference, SEC 2023, Poznan, Poland, 14–16 June 2023; Springer: Cham, Switzerland, 2024; Volume 679, pp. 207–221. [Google Scholar] [CrossRef]
- Kemp, C.; Calvert, C.; Khoshgoftaar, T.M. Detection Methods of slow Read DoS Using Full Packet Capture Data. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science, IRI 2020, Las Vegas, NV, USA, 11–13 August 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020; pp. 9–16. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.S.; Mostefaoui, S.K. Packet Filtering and Sampling for Efficient slow Denial of Service Detection in Resource Scarce IoT Networks. In Proceedings of the 2023 International Symposium on Networks, Computers and Communications (ISNCC) 2023, Doha, Qatar, 23–26 October 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Sikora, M.; Fujdiak, R.; Kuchar, K.; Holasova, E.; Misurec, J. Generator of slow Denial-of-Service Cyber Attacks. Sensors 2021, 21, 5473. [Google Scholar] [CrossRef]
- Prakash, K.J.; Saumya, B.; Tapaswi, S. mFCBF based lightweight intrusion detection system for IoT networks. Clust. Comput. 2025, 28, 416. [Google Scholar] [CrossRef]
- Memon, S.Q. Prevention Mechanism For RUDY Attack And Its Comparison. Univ. Sindh J. Inf. Commun. Technol. 2020, 4, 45–51. [Google Scholar]
- Fu, Y.; Duan, X.; Wang, K.; Li, B. Low-rate Denial of Service attack detection method based on time-frequency characteristics. J. Cloud Comput. 2022, 11, 1–19. [Google Scholar] [CrossRef]
- Sood, S.; Hubballi, N. slowTrack: Detecting slow rate Denial of Service attacks against HTTP with behavioral parameters. J. Supercomput. 2024, 80, 1788–1817. [Google Scholar] [CrossRef]
- Dung, D.A.; Nakamura, Y. Verification of State Based slow HTTP DDoS Prevention Method. In Proceedings of the 12th IEEE International Conference on Control, Automation and Information Sciences, ICCAIS 2023, Hanoi, Vietnam, 27–29 November 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 686–691. [Google Scholar] [CrossRef]
- Tang, D.; Wang, S.; Zhang, S.; Qin, Z.; Liang, W.; Xiao, S. Real-Time Monitoring and Mitigation of SDoS Attacks Using the SDN and New Metrics. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 1721–1733. [Google Scholar] [CrossRef]
- Kapourchali, R.F.; Mohammadi, R.; Nassiri, M. P4httpGuard: Detection and prevention of slow-rate DDoS attacks using machine learning techniques in P4 switch. Clust. Comput. 2024, 27, 8047–8064. [Google Scholar] [CrossRef]
- Rios, V.; Inacio, P.; Magoni, D.; Freire, M. Detection of slowloris Attacks using Machine Learning Algorithms. In Proceedings of the 39th ACM/SIGAPP Symposium on Applied Computing, Avila Spain, 8–12 April 2024; pp. 1321–1330. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.; Kouadri, S. SA-IDS: A single attribute intrusion detection system for slow DoS attacks in IoT networks. Internet Things 2025, 30, 101512. [Google Scholar] [CrossRef]
- Tripathi, N.; Hubballi, N.; Singh, Y. How Secure are Web Servers? An empirical study of slow HTTP DoS attacks and detection. In Proceedings of the =2016 11th International Conference on Availability, Reliability and Security, ARES 2016, Salzburg, Austria, 31 August 2016–2 September 2016; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2016; pp. 454–463. [Google Scholar] [CrossRef]
- Benzaid, C.; Boukhalfa, M.; Taleb, T. Robust Self-Protection Against Application-Layer (D)DoS Attacks in SDN Environment. In Proceedings of the IEEE Wireless Communications and Networking Conference, WCNC, Seoul, Republic of Korea, 25–28 May 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020; Volume 2020-May, pp. 1–6. [Google Scholar] [CrossRef]
- Cambiaso, E. On the Use of Low Cost IoT Devices to Perpetrate slow DoS Attacks. In Proceedings of the Eighth International Congress on Information and Communication Technology; Lecture Notes in Networks and Systems; Springer Science and Business Media Deutschland GmbH: Singapore, 2024; Volume 695, pp. 859–875. [Google Scholar] [CrossRef]
- Herzalla, D.; Lunardi, W.T.; Andreoni, M. TII-SSRC-23 Dataset: Typological Exploration of Diverse Traffic Patterns for Intrusion Detection. IEEE Access 2023, 11, 118577–118594. [Google Scholar] [CrossRef]
- Karmous, N.; Aoueileyine, M.O.E.; Abdelkader, M.; Romdhani, L.; Youssef, N. Software-Defined-Networking-Based One-versus-Rest Strategy for Detecting and Mitigating Distributed Denial-of-Service Attacks in Smart Home Internet of Things Devices. Sensors 2024, 24, 5022. [Google Scholar] [CrossRef]
- Reed, A. HTTP DoS IoT Dataset. 2021. Available online: https://ordo.open.ac.uk/search?q=Reed (accessed on 20 June 2021).
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef] [PubMed]
- Catillo, M.; Del Vecchio, A.; Pecchia, A.; Villano, U. A Critique on the Use of Machine Learning on Public Datasets for Intrusion Detection. In Quality of Information and Communications Technology, Proceedings of the 14th International Conference, QUATIC 2021, Algarve, Portugal, 8–11 September 2021; Springer: Cham, Switzerland, 2021; Volume 1439, pp. 253–266. [Google Scholar] [CrossRef]
- Shukla, P.; Krishna, C.R.; Patil, N.V. SDDA-IoT: Storm-based distributed detection approach for IoT network traffic-based DDoS attacks. Clust. Comput. 2024, 27, 6397–6424. [Google Scholar] [CrossRef]
- Swe, Y.M.; Aung, P.P.; Hlaing, A.S. A slow ddos attack detection mechanism using feature weighing and ranking. In Proceedings of the International Conference on Industrial Engineering and Operations Management, Rome, Italy, 2–5 August 2021; pp. 4500–4509. [Google Scholar] [CrossRef]
- Abisoye, O.A.; Shadrach Akanji, O.; Abisoye, B.O.; Awotunde, J. slow Hypertext Transfer Protocol Mitigation Model in Software Defined Networks. In Proceedings of the 2020 International Conference on Data Analytics for Business and Industry: Way Towards a Sustainable Economy, ICDABI 2020, Sakheer, Bahrain, 26–27 October 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Fuladi, R.; Baykas, T.; Anarim, E. The Use of Statistical Features for Low-Rate Denial of Service Attack Detection. In Proceedings of the International Conference on 6G Networking, 6GNet 2023, Paris, France, 18–20 October 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Alsolami, T.; Alsharif, B.; Ilyas, M. Enhancing Cybersecurity in Healthcare: Evaluating Ensemble Learning Models for Intrusion Detection in the Internet of Medical Things. Sensors 2024, 24, 5937. [Google Scholar] [CrossRef] [PubMed]




| Citation | Resources | Environment | IoT | SN | Slow DoS Variants |
|---|---|---|---|---|---|
| [6] | Yes | Live | Yes | Yes | 1/3 |
| [23] | - | Live | - | - | 2/3 |
| [25] | - | Live | - | - | 3/3 |
| [20] | - | Live | Yes | - | 2/3 |
| [36] | - | Live | - | - | 2/3 |
| [27] | - | Hybrid | - | - | 3/3 |
| [37] | - | Simulated | - | - | 1/3 |
| [38] | - | Live | - | - | 3/3 |
| [19] | - | Live | - | - | 2/3 |
| [39] | - | Simulated | - | - | Custom |
| [30] | Yes | Live | - | - | 3/3 |
| [7] | - | Simulated | Yes | - | Not defined |
| [21] | - | Live | - | - | 1/3 |
| [40] | - | Simulated | - | - | Not defined |
| [41] | - | Hybrid | - | - | 1/3 |
| [10] | Yes | Live | Yes | Yes | 3/3 |
| [42] | Yes | Live | Yes | Yes | 3/3 |
| Node | DH22 | TME | 2TH | Disruption of Access to Server (s) |
|---|---|---|---|---|
| Slow POST | ✓ | ✓ | ✓ | 120 |
| Slow GET | ✓ | ✓ | ✓ | 235 |
| Slow Read | ✓ | ✓ | ✓ | 240 |
| Sensor | CPU | RAM | Flash | Protocols |
|---|---|---|---|---|
| 2TH | 20 MHz | 18 KB | 256 KB | HTTP, MQTT, Telnet |
| TME | 20 MHz | 18 KB | 256 KB | HTTP, MQTT, Telnet |
| DHT22 | 1.2 GHz | 1 GB | 8 GB | HTTP, Telnet |
| Web Server | CPU | RAM | Flash | Model |
| Raspberry Pi | 1.5 GHz | 4 GB | 16 GB | 4 B |
| Default | Stealthy Attack | Duration | |
|---|---|---|---|
| Slow GET (cnx/rpc) | 1000/200 | 500/50 | 240 |
| Slow Read (cnx/rpc) | 1000/200 | 500/50 | 240 |
| Slow POST (cnx/rpc) | 1000/200 | 500/50 | 240 |
| Node Class | LN | SN | SG | SR | SP |
|---|---|---|---|---|---|
| Packets # | 1279 | 714 | 838 | 634 | 1440 |
| Total Count | 4905 | ||||
| Total Megabytes | 0.52 | ||||
| Node Class | LN | SN | SG | SR | SP |
|---|---|---|---|---|---|
| Packets # | 331,974 | 63,122 | 128,450 | 28,778 | 68,354 |
| Total Count | 620,678 | ||||
| Total Megabytes | 396.05 | ||||
| Observed | LN | MN | % Correct |
|---|---|---|---|
| LN | 1232 | 47 | 96.3% |
| MN | 114 | 2798 | 96.1% |
| Overall | 32.1% | 67.9% | 96.2% |
| Precision | 91.5% | 98.3% |
| Observed | LN | MN | % Correct |
|---|---|---|---|
| LN | 1905 | 88 | 95.6% |
| MN | 114 | 2798 | 96.1% |
| Overall | 41.2% | 58.8% | 95.9% |
| Precision | 94.3% | 97.0% |
| FPC | Inbound-Only | LPC | |
|---|---|---|---|
| 0.32 | 0.42 | 0.70 | |
| 36.30 | 30.50 | 10.10 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Reed, A.; Dooley, L.S.; Kouadri Mostefaoui, S. Minimal Overhead Modelling of Slow DoS Attack Detection for Resource-Constrained IoT Networks. Future Internet 2025, 17, 432. https://doi.org/10.3390/fi17100432
Reed A, Dooley LS, Kouadri Mostefaoui S. Minimal Overhead Modelling of Slow DoS Attack Detection for Resource-Constrained IoT Networks. Future Internet. 2025; 17(10):432. https://doi.org/10.3390/fi17100432
Chicago/Turabian StyleReed, Andy, Laurence S. Dooley, and Soraya Kouadri Mostefaoui. 2025. "Minimal Overhead Modelling of Slow DoS Attack Detection for Resource-Constrained IoT Networks" Future Internet 17, no. 10: 432. https://doi.org/10.3390/fi17100432
APA StyleReed, A., Dooley, L. S., & Kouadri Mostefaoui, S. (2025). Minimal Overhead Modelling of Slow DoS Attack Detection for Resource-Constrained IoT Networks. Future Internet, 17(10), 432. https://doi.org/10.3390/fi17100432






