Abstract
The increasing deployment of internet of things(IoT) systems across critical domains has broadened the threat landscape, and being the catalyst for a variety of security concerns, including very stealthy slow denial of service (slow DoS) attacks. These exploit the hypertext transfer protocol’s (HTTP) application-layer protocol to either close down service requests or degrade responsiveness while closely mimicking legitimate traffic. Current available datasets fail to capture the more stealthy operational profiles of slow DoS attacks or account for the presence of genuine slow nodes (SN), which are devices experiencing high latency. These can significantly degrade detection accuracy since slow DoS attacks closely emulate SN. This paper addresses these problems by synthesising a realistic HTTP slow DoS dataset derived from a live IoT network, that incorporates both stealth-tuned slow DoS traffic and legitimate SN traffic, with the three main slow DoS variants of slow GET, slow Read, and slow POST being critically evaluated under these network conditions. A limited packet capture (LPC) strategy is adopted which focuses on just two metadata attributes, namely packet length () and packet inter-arrival time (). Using a resource lightweight decision tree classifier, the proposed model achieves over 96% accuracy while incurring minimal computational overheads. Experimental results in a live IoT network reveal the negative classification impact of including SN traffic, thereby underscoring the importance of modelling stealthy attacks and SN latency in any slow DoS detection framework. Finally, a MPerf (Modelling Performance) is presented which quantifies and balances detection accuracy against processing costs to facilitate scalable deployment of low-cost detection models in resource-constrained IoT networks. This represents a practical solution to improving IoT resilience against stealthy slow DoS attacks whilst pragmatically balancing the resource-constraints of IoT nodes. By analysing the impact of SN on detection performance, a robust reliable model has been developed which can both measure and fine tune the accuracy-efficiency nexus.
1. Introduction
The rapid proliferation of the IoT has transformed industries and daily life, providing the potential for new and profitable innovation in commercial, industrial, agricultural, clinical, and recreational domains. As IoT applications increasingly adopt semi and fully autonomous functionalities, they are seen by many to offer new capabilities in personalised e-health care services [1], remote sensing, data processing, and sharing through networks of low-cost, interconnected nodes. This evolving paradigm is seen as the driver of continued growth in smart cities and automation [2], supporting integration of IoT technologies that underpins the next generation of industrial IoT (IIoT) systems [3]. The continued expansion in this domain is highlighted in [4], where the authors predicted that the number of IoT nodes could rise to 40 billion by 2030. This pervasive growth of IoT adoption brings inherent security risks as many of the mass-produced low-resource IoT nodes lack security and protective features, as a result of low production cost and their inherently limited form factor. In [5], these risks to IoT are highlighted in terms of threats to IoT nodes from Botnets, and in particular the distributed denial of service (DDoS) problem. The limited resources of IoT nodes make them vulnerable to physical and cyber threats [2], furthermore, inadequate awareness and education among IoT stakeholders increases the risk of malicious activity targeting the IoT network, the data in transit, and their applications. Recently, slow HTTP DoS attacks, often referred to as low rate or slow denial of service (slow DoS), have received the attention of researchers and, as noted by [6,7], are acutely problematic for current detection methodologies due to their ability to resemble legitimate hypertext transfer protocol (HTTP) and transmission control protocol (TCP) communications. Slow DoS attacks, as discussed in [8], are a stark contrast to high bandwidth, and high traffic volume botnet attacks such as the well documented Mirai attack [9], requiring minimal bandwidth. The slow DoS attack can be executed from a single low-resource device, such as a smartphone, tablet, webcam, or other IoT node. An important characteristic of slow DoS attacks is their apparent ease of operation, as they can be executed by a single malicious node utilising minimal bandwidth or computational resources, yet still capable of significantly hindering or interrupting the functionality of an IoT node [10]. Many modern detection models require a substantial amount of network packets for their analysis, making these methods excessively resource-intensive for IoT nodes and networks. Addressing the slow DoS issue is highly complex and warrants a thorough examination, particularly within the highly resource-constrained IoT network environment. The challenge of accurately identifying slow DoS attacks becomes exacerbated under conditions of significant network latency, leading to delayed transmissions for legitimate nodes. This is a prevalent issue in many modern datasets, which existing detection models often fail to adequately address. Through the examination of legitimate nodes that exhibit slow or suboptimal connectivity in conjunction with sophisticated and highly stealthy slow DoS attack traffic, this study considers the operational cost while providing efficient detection for three of the most significant slow DoS attacks. This is an important motivational aspect of this research, given that contemporary detection models focus on overall accuracy, omitting to measure this in the context of processing overhead placed on the IoT detection node.
The paper also presents a performance model that can be adapted to offer appropriate detection accuracy in highly resource-constrained IoT networks. This differentiation is achieved by implementing a lightweight yet efficient decision tree classification approach [11] focused on only two network attributes, leading to a substantial reduction in the resource requirements of an IoT node, which is achieved by using a lightweight, and efficient approach by limiting the volume of packets for capture and analysis. In [12], the decision tree classifier was found to offer the fastest operating time compared to four other lightweight machine learning (ML) classifiers, while in [13], both efficiency and accuracy were seen as characteristic of this classifier. Hence, the work presented here leverages these findings and uses the decision tree as an efficient and well tested classifier, allowing for a fair comparison to other ML proposals and reproducible analysis.
This research makes several significant original contributions to slow DoS detection in resource-constrained IoT scenarios:
- A lightweight resource-efficient slow DoS detection model.
- Minimal processing overheads compared to alternative models that require large datasets and bi-directional packet capture.
- Model efficiency utilising a computationally lightweight decision tree classifier.
- A robust evaluation environment using non-default attack parameters.
- Critical impact analysis of the role of genuine SN in detection performance.
- Resource cost modelling to balance accuracy and efficiency.
The remainder of this paper is organised as follows. Section 2 defines the problem domain, while in Section 3 the three main slow DoS variants are introduced. In Section 4, the evaluation environment is explained and key terms established. Section 5 presents a critical results analysis and a discussion of the slow DoS detection approach, while Section 6 proposes a cost model that balances intrusion detection accuracy with processing overhead. Section 7 makes some concluding remarks and future work directions.
2. Related Work
Regarding the security concerns of IoT in the e-health domain, [14] noted that threats continue to exist due to the challenges brought about by complex security and privacy requirements, compounded by the resource constraints associated with IoT nodes. In [15], the vulnerabilities to 5G enabled sensor networks that provide services for the internet of medical things (IoMT) are clearly defined, noting that DoS attacks posed a significant threat. Although high volume flooding attacks are still a concern and continue to receive much publicity, there is growing evidence that in terms of the IoT, these are often overshadowing the more subtle slow DoS attack, which are proven to be more challenging to detect. In the contemporary literature, slow DoS attacks have been identified as a particularly serious challenge to IoT security. This is often attributed to the difficulties associated with accurate and reliable detection mainly due to the low bandwidth approach, the nominal network footprint, and the attack’s ability to masquerade as legitimate HTTP service requests and resemble nodes with slow connections, which is still considered an ongoing security concern, as seen in [16,17]. Contemporary research highlights that while IoT networks face a myriad of security and privacy challenges, slow DoS attacks are a particularly serious threat as their low profile makes them harder to detect than conventional flooding attacks, thus demanding new detection and mitigation strategies tailored to IoT constraints.
2.1. Detection and Mitigation Approaches
In terms of mitigating slow DoS attacks, most network security vendors, such as [18], just increase server capacity. This may be appropriate for many high resource internet servers, but is totally impractical in the context of resource-constrained IoT networks. Along with increasing node capacity to handle more connections, vendors also recommend lowering the server timeout value to reduce slow DoS traffic. The caveat here is that this approach can negatively impact the quality of service, especially for legitimate nodes with slow network connections. As such, researchers have sought to develop novel alternative approaches to slow DoS detection and mitigation [19]. In most ML methods, the node’s resource demands for data extraction and processing are typically overlooked. This is shown in [20], where 88,237 traffic instances and 11 of the 80 available characteristics were extracted from the CIC-DoS 2017 dataset to validate their deep ML proposal. This evaluation required ‘all computations’ to be conducted on high performance devices. A significant system issue with this intrusion detection approach and the use of huge multi-feature datasets is the limited interpretability of the model, which is often regarded as a black box. Although detection accuracy is the primary objective, the lack of visibility limits understanding of which attributes of the dataset are crucial to the overall performance of the model. It also limits the ability to understand network variations or fluctuations in attack profiles. Gaining insights into which features or attributes are the most significant in an attack’s network footprint can lead to a more finely tuned and resource efficient detection model.
In [21], an ontological method was explored to identify slow GET attack traffic. The study used the CIC-IDS2017 dataset [22] and highlighted the time a packet spends in transit, and the length of the packet amongst the seven chosen attributes. In this context, the ontology refers to crafting classes and links, such as network characteristics, features, or attributes, in order to understand network behaviour under normal and attack scenarios. This underscores the importance of key network or packet attributes in detecting slow DoS attacks, although the method was restricted to only the slow GET variant.
The study by [23] highlights the challenges slow DoS attacks pose for detection systems designed primarily to identify increased traffic volume or bandwidth usage. Focusing on slow GET, slow Read and slow POST attacks, and the need to reduce the size of the dataset, they employed an ML approach utilising feature selection and classification, favouring packet attributes from uni-directional extraction to evaluate critical flow based parameters. However, resource conservation was not the main objective of their detection proposal, which is evident in their approach to extract uni-directional features from two well known, and very large datasets, CIC-IDS 2017 and SUEE 2019 [24]. In [25], the authors introduced an anomaly detection framework by integrating deep learning with real-time traffic evaluation. This distributed system involves multiple computational layers and generates an extensive dataset from 57 network attributes. The adoption of this and many other proposals discussed is particularly challenging in an IoT context because of the requirement for high specification computing devices and significant processing power to evaluate the large volumes of data. Existing mitigation methods often rely on increasing capacity or adopting ML-driven detection, but these approaches are limited by high computational costs and low interpretability or focus on only a specific slow DoS variant. These drawbacks frame the gap for resource-efficient and generalisable solutions which are better suited to IoT scenarios.
The hybrid deep learning-based intrusion detection framework in [26] has high detection accuracy and demonstrates the effectiveness of combining convolutional and recurrent layers to capture spatial and temporal traffic features. While this study contributes positively by achieving strong classification results and validating the hybrid approach, its applicability to an IoT context is problematic. A key limitation of this approach is the lack of a critical evaluation between detection accuracy and resource efficiency, a pivotal nexus given the resource constraints of IoT nodes. In [27], the authors considered temporal measurements with deep learning as a slow DoS detection model using long short term memory (LSTM), again achieving high accuracy, though, like [26], the comparatively high resource demands mitigate its deployment in real-world IoT environments, especially where lightweight detection models are desired.
2.2. Data Capture Strategies and Resource Lightweight Solutions
Network data capture and preservation are integral to many slow DoS detection model, which is evident in [28] where full packet capture (FPC) and netflow are used to extract key attributes from a reduced dataset of 828,510 instances. The lightweight classifiers achieved good accuracy when the three main slow DoS variants were extracted from a collection of live and synthetic network data. FPC can be considered a highly resource-intensive approach since all packets are extracted in a bi-directional flow for analysis. This approach often requires the use of full or partial datasets, which can require the processing of gigabytes of network data. In [29], slow DoS detection is achieved by extracting both bi-directional and uni-directional traffic from two separate datasets. By observing the impact of high volume packet capture, the authors noted a considerable increase in memory consumption when extracting up to 30 GB of data. While this approach provided encouraging accuracy results for detecting all three slow DoS attack variants, there is neither consideration of genuine SN activity nor using non-default attack profiles.
Some slow DoS models have opted to reduce overhead by only selecting inbound only or uni-directional network traffic [30]. The term limited packet capture (LPC) implies that only a select number of network packet attributes are required for the slow DoS classification, and this approach, while resource efficient, targets only packet attributes that have a proven association with the slow DoS attack pattern. For example, FPC is used in [31] where, including the class labels [attack/benign], 12 attributes were required. Along with the high volume of packets, attributes such as time to live, TCP window size, and TCP window size scaling factor incur extra resource expenditure from deep packet inspection and parsing to extract numerical data. Unlike the LPC approach, where only easily recordable metadata are used, such as the size of each packet or the duration between packets, meaning these can be efficiently extracted and recorded at the ingress point of the network, allowing for a real-time detection solution.
Using a combination of edge AI and federated learning, a scalable approach to protecting IoT networks is proposed that achieves high accuracy and low false positive alerts. However, this requires the use of FPC in the form of a full dataset analysis, and as such a detailed evaluation of the resource implications since there is a considerable load on the IoT edge node. The solution also does not consider adversarial attack profiles, implying that any non-default attack profile will be difficult to adapt to.
To lower the volume of network data for processing, both [30,32] adopted packet sampling and filtering of incoming packets in their respective slow DoS attack detection methodologies. In [30], a sketch-based sample model is used while [32] focusses on a resource-efficient form of systematic sampling. Both approaches limit the number of packets captured for analysis to mitigate the resource constraints imposed on IoT nodes.
The difficulty of identifying the three slow DoS variants within a highly unpredictable network setting has been thoroughly examined in [10,27,33]. The strength of these models lies in their innovative approach to classifying incoming traffic, which greatly limits the packet capture by extracting fewer traffic attributes: TCP packet length and delta time . In addition to introducing legitimate SN, these approaches focused on resource efficiency compared to methods that involve FPC or those that rely on very large datasets. However, the work omitted to fully explore the impact of legitimate high latency nodes on detection accuracies. In this study, FPC represents a complete bi-directional packet capture, including all requests and responses of the client and server nodes. In contrast, LPC defines the approach to extracting and processing a significantly reduced subset of the dataset, so lowering the processing overhead upon the IoT detection node. Recent research, such as [34] has shifted toward lightweight detection strategies such as LPC, acknowledging the benefits of reduced feature datasets and focusing on only attributes of relevance. Although these show promise for resource-scarce IoT networks, there are still major challenges in balancing accuracy, efficiency, and robustness against real-world network variability.
3. The Three Slow DoS Variants
The three key variants of slow DoS have attracted considerable interest from researchers. However, most current studies tend to examine each variant separately, and few adopt an integrated approach to the issue. In this paper, the focus is on a generalised lightweight detection model that targets the following three key slow DoS variants.
3.1. Slow GET (SG)
Slow GET is a variant of slow DoS attack that takes advantage of unfinished HTTP requests to drain server resources. Slowloris is a prominent example of this tactic, focusing on incomplete HTTP headers to maintain open connections. In this mode of attack, the malicious node (MN) transmits partial HTTP GET requests to the server, prolonging open connections. Without receiving a complete request, the server remains in a constant waiting state, occupying resources, resulting in the server’s failure to accept a complete request. The inability to serve additional requests from legitimate nodes (LN), results in a successful DoS. A typical attack profile is illustrated in Figure 1, highlighting the multiple incomplete HTTP GET requests and the subsequent server timeout.
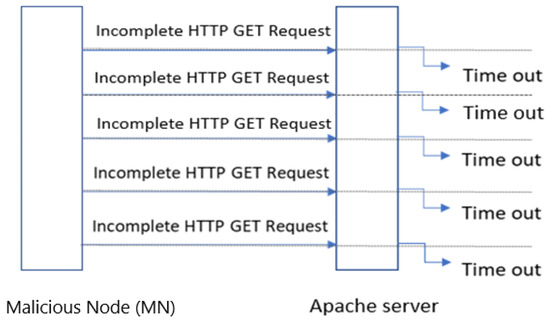
Figure 1.
A slow HTTP GET attack process.
3.2. Slow Read (SR)
The slow Read attack exploits the adjustable TCP window size attribute. This window size, shared by communicating nodes, sets the maximum receive data (in bytes) that can reside in the read buffer in a TCP connection. The size of the TCP window offers a reliable way to regulate the flow of data across the network. An MN may send a valid HTTP request using TCP, and the server accepts the size of the TCP window. The MN can set a large window size, which the server respond to; however, the MN will proceed to read data, slowly, thus holding open the server connection. Sending multiple malicious read requests will use up all available server resources, leading to a DoS.
3.3. Slow POST (SP) (aka R.U.Dead.Yet)
Slow POST represents another form of slow DoS attack, in which the MN initiates server connections with the aim of keeping them active for an extended period by pretending to send data [35]. The MN issues an HTTP POST request, prompting the server to allocate space for the client. The request includes the content length field, which specifies the volume of data to be transferred. This typically large value enables the server to reserve enough memory to handle the anticipated data size. Despite this, the MN sends the POST data in the message body to the server at a very slow pace, possibly one byte per minute, forcing the server to wait until all the expected data arrive or the timeout limit is reached. Note, both slow GET and slow POST are recognised as HTTP operational methods, so are written in capitals, unlike slow Read, which defines the mode of attack.
3.4. Slow DoS Detection Issues
In mission critical IoT networks, such as medical IoT systems that monitor vital patient data or agricultural IoT networks that control automated sensing operations, every millisecond matters. Connectivity issues, such as high latency or intermittent wireless signals can create potentially fatal or costly disruptions.
A critical observation across all three slow DoS attack variants is their ability to convincingly mimic legitimate HTTP over TCP communications. This covert behaviour makes it imperative to measure and compare the traffic patterns of these attack vectors against legitimate nodes, especially those whose slow performance stems from genuine high latency and suboptimal connectivity.
Another aspect that compounds the difficulty of slow DoS detection is that attacks can operate even with an encryption overlay [30]. As such, transport layer encryption mechanisms such as HTTPS (secure HTTP) and the use of transport layer security (TLS) are ineffective because they secure data in transit without inspecting application layer behaviour. This enables malicious clients to establish encrypted connections and execute resource exhausting strategies under the guise of legitimate traffic. Given that end-to-end encryption does not affect the operational parameters of the application layer protocol, it can be cogently argued the underlying network packet attributes and their numeric values remain constant for both HTTP and HTTPS [30]. To validate this judgment, HTTPS was configured for evaluation purposes in the live IoT network, and it was observed that the various network attributes corresponding to the packet metadata retained the same values relative to the packets when using unencrypted HTTP.
To appreciate the operational dynamics of slow DoS attacks, this work realised an experimental setup that went beyond standard practices. Not only were LN incorporated into the live IoT network, but also SN, which are genuine IoT nodes with high latency connections. This novel strategy provided valuable information for discriminating between legitimate and malicious connections in the presence of the three slow DoS variants, by comparing both LN and SN, which are indicative of highly stochastic wireless or cellular networks. Table 1 visualises the work carried out to address the slow DoS problem, highlighting the limitations within this research domain.

Table 1.
Overview and constraints of contemporary slow DoS research.
4. Research Methods
A live IoT network was constructed to simulate an IoT network in which external nodes request sensor data via HTTP.
There are two Cisco 2800 series routers in the network, with the first acting as the IoT gateway or border router, and the second being the internet service router. Each router is equipped with a serial interface connected to the 10.10.10.0/30 subnet, which emulates a WAN (Wide Area Network) link. both routers use the routing information protocol (RIP) to enable packet routing between the networks and their respective nodes. Figure 2, shows the physical topology of the live IoT network, including sensor nodes, LN, SN, and MN along with intermediary network devices.
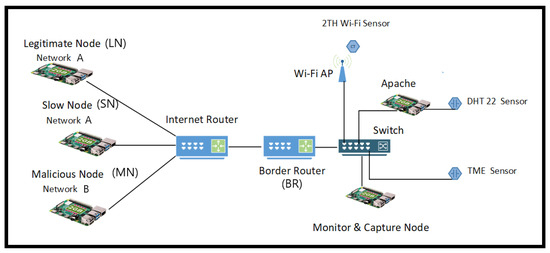
Figure 2.
Physical topology of the IoT network.
To produce a substantial amount of genuine web traffic, the implementation of virtual clients was achieved through the JMeter application. JMeter is an Apache developed tool for monitoring web server load balancing and performance, widely used in both commercial projects and academic investigations [43,44]. The network is configured with differing node latencies and non-default slow DoS attack parameters to create highly stealthy attack profiles. Each node, designated as LN, SN, or MN (responsible for launching the slow DoS attacks), is represented by Raspberry Pi model 4 boards. The test results for the slow DoS attacks are presented in Table 2 which indicates a successful DoS (✓) and the duration of each attack prevents legitimate access to the web services of the target node.

Table 2.
Slow DoS attack results and duration to web service (s).
The Apache web service was configured on a Raspberry Pi Model 4 board to function as the HTTP web interface, utilising standard security settings and operational parameters. Ubuntu Server 20.04.1 LTS is installed on the node serving as a minimalistic operating system on which the Apache 2.4 web server is deployed using standard installation procedures and security configurations. Within this environment, the web server is set to permit a maximum of concurrent connections, a parameter specified by the Apache directive MaxRequestWorkers [45].
Raspberry Pi boards are commonly deployed in IoT networks for analytical purposes, as evidenced in [46,47]. A conceptual illustration of the live IoT network, indicating traffic type and flow is shown in Figure 3.
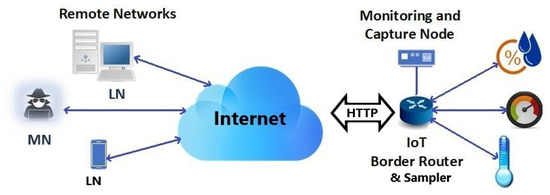
Figure 3.
A conceptual illustration of the live IoT environment.
The live IoT network contained various nodes, including a DHT22 for humidity sensing, a TME probe for critical temperature monitoring with alerts, and a Papago 2TH thermocouple for WiFi based humidity and dew point measurements. These sensors support real-time data retrieval via HTTP GET, with the TME also offering XML data via HTTP POST. Although both the 2TH and the TME sensor nodes have the data transfer functionality of both HTTP and MQTT, HTTP is configured as the default application, thus requiring the network administrator or operator to manually reconfigure each node for MQTT. As HTTP is the default application interface setting, these nodes are particularly vulnerable to slow DoS attacks. The limitations in terms of the resource capacity of the IoT nodes are shown in Table 3, which clearly reflects the restrictions in terms of RAM and flash memory when considering the implementation of the security and intrusion detection mechanisms.

Table 3.
Web server IoT sensor node details.
Dataset creation and subsequent data collection were performed using Wireshark, a widely recognised network packet inspection tool [28]. Wireshark captures and filters packets from each node, facilitating live dataset creation, which consists of Wireshark trace files in the standard .PCAPNG (Packet Capture Next Generation) format, and later converted to a .CSV file. Wireshark was set to listening mode on the monitoring node’s network interface, facilitating the extraction of the necessary packets, focusing on the packet length (), and packet inter-arrival time, or delta time () attribute for analysis. The dataset compiled from the live IoT network is termed the HTTP slow DoS dataset and though commonly referred to as features in ML contexts, this paper uses the term attributes to emphasise their origin as native or derived properties of TCP/IP packets, which is the parlance of users of network packet analysers like Wireshark.
4.1. Comparison of Datasets
To present a fair and balanced evaluation, both the HTTP slow DoS [48], and CIC-IoT dataset 2023 [49] are used to compare attribute values of inbound HTTP traffic from MN and LN, and uniquely in [48] legitimate SN. The introduction of highly stealthy slow DoS traffic was an important inclusion, given no publicly available datasets currently go beyond the default slow DoS attack parameters. This weakness is highlighted in [50] where the authors state in their critique of ML with public datasets that models trained to detect slow DoS may be ineffective against weaker or less overt variations of the same attack.
In this paper the term FPC, and inbound-only refer to bi-directional and uni-directional packet capture respectively, and LPC requires a select number of uni-directional packets. LPC is a considerably more resource efficient as the focus is on a prescribed dataset comprising only the two network attributes and , where is defined by Equation (1).
If and respectively denote the observed arrival and start times of the packet, then Equation (1) represents the lapsed duration between packets in a TCP exchange.
The second attribute extracted for analysis is lp. This also provides an effective method for identifying unusual behaviour at a packet level. The packet header consists of fields crucial to routing IP packets through the network, with its size varying from 20 to 60 bytes. In this paper, denotes the complete length of the IP packet, encompassing headers, options, and application data as defined in Equation (2).
Both and have been proven to be effective indicators of potential slow DoS activity [30,42], where the former uses the information gain feature ranking for selecting attributes based on their ranking scores.
This analysis was performed using the statistical analysis package SPSS. The normalised information gain measures the reduction in entropy of the target variable after observing each attribute and is determined using Equation (3).
where is the entropy of the target variable and is the conditional entropy of the target given the attribute X.
Focusing on eight of the most popularly ranked attributes in publicly accessible datasets, Figure 4, presents the information gain results for these attributes. In particular, the lp attribute scores highest () confirmed its prominence in differentiating node classes within this dataset. Furthermore, the value ( implies its significance in this assessment. Information gain ranking provides demonstrable evidence to justify the inclusion of and in this study of resource-efficient slow DoS detection for IoT nodes. The rational to limited attribute selection was to use the fewest possible, and only those where a clear relationship to the attack profile is evident. In both [10,42], and are proven to produce values intrinsically aligned with the slow DoS attack profiles. This removes redundancy in attribute selection and significantly reduces the processing overhead on the detection node.
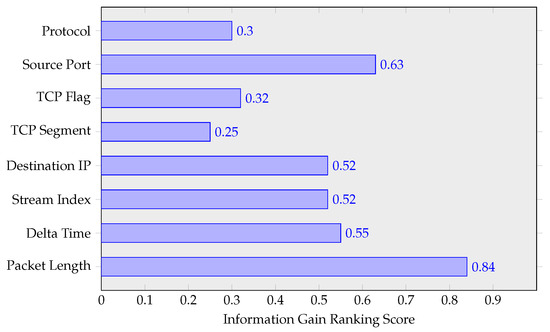
Figure 4.
Attribute validation method.
For classification purposes, it is crucial that the source port and destination IP are considered static or unique attributes specific to individual node identity. Consequently, they are excluded from this study due to their strong association with the nodes themselves. However, as indicated in [51], different ML detection methods within IoT contexts incorporate these node-specific characteristics alongside other specified attributes.
Although attribute filtering is essential for streamlining ML models and reducing testing and training times, these should be considered with caution, as model over generalisation leading to overfitting can arise [5], which is significant in the context of resource-constraint IoT environments.
4.2. Stealthy Slow DoS and Slow Nodes
In order to design highly stealthy slow DoS attacks in the IoT network, each of the three slow DoS variants was manually configured to operate below the standard DoS attack parameters. This is an important inclusion given that publicly available datasets almost exclusively contain slow DoS traffic in their default attack configuration. This implies that highly stealthy slow DoS attacks, where the attack parameters are configured beyond the default, can evade detection, where the training is only on datasets with default attack parameters. To achieve this, the number of concurrent slow DoS connections (CNX) is reduced from 1000 to 500, which represents a notable decrease in attack volume and a substantial lowering of the network footprint and enhancing the stealthiness of the attack to evade detection mechanisms that rely on either high connection counts or traffic volume anomalies. To further mask slow DoS attacks, the attacking MN further adjusts the connection parameters, expressed in requests per connection (RPC). These parameters represent the time between requests which are pre-launch modified. However, in this analysis, these parameters are kept constant once a slow DoS attack has been initiated. The connection parameters set for the three profiles are detailed in Table 4.

Table 4.
Configured connection parameter set for each traffic profile.
During simulations, the SN is subjected to deliberate random latencies ranging from 1500 to 3000 ms. Meanwhile, all other network nodes were left unchanged, functioning at their permitted capacity as dictated by the network infrastructure. The LPC setup that represents the reduced dataset is detailed in Table 5, indicating the instances of each node and the cumulative packet statistics used to evaluate resource overhead.

Table 5.
Reduced dataset packet count per node.
To better contextualise the processing and resource saving from FPC, the packet statistics in Table 5 are compared with the complete bi-directional packet capture for each node in Table 6, where the general reduction in packets equates to a packet processing saving of ≈99.2% which comes from 620,678 to 4905 packets. In addition, if processing decreased from 396.1 MB to 0.52 MB, the overall reduction is ≈99.8%.

Table 6.
Full dataset packet count per node.
For this evaluation, the SG, SR and SP network traffic has been aggregated into a unified MN class. The rationale being to emphasise the holistic accuracy of the model rather than isolating specific types of malicious behaviour. This is a common and prevalent practice, as demonstrated in [13,19,23].
5. Critical Results Evaluation
This section critically evaluates the slow DoS detection classification, accuracy, and precision first by using just LN and MN, before introducing SN. The accuracy is given in Equation (4), while precision, which measures how many of the positive predictions are true positives, is defined in Equation (5).
For this evaluation, five lightweight ML classifiers were considered, these being SVM (Support Vector Machine), K-Nearest Neighbour, Decision Tree, and Logistic Regression. Using the Weka framework as the test platform and using a stock test dataset, the decision tree classifier proved to be the most efficient in terms of speed and processing overhead. This choice of classifier, along with the justification, is documented in [12]. The default parameters of the J48 decision tree in Weka were used for model construction. These defaults include a confidence factor of 0.25 for pruning, a minimum of two instances per leaf. Given the dataset contained only numeric values for and , these settings were appropriate. Pruning ensures the tree does not overfit minor variations, while the minimum leaf size prevents overly specific splits. Since the dataset is discrete, the default parameters provided a balanced approach between model complexity and generalisation.
Given the default parameters, the decision tree classifier was trained and tested on the sample dataset built on the two attributes of and .
In Table 7, the test dataset has been reduced to include only LN and MN, facilitating a binary classification. This means the model is trained on only legitimate traffic patterns where the LN does not experience unusual fluctuations in delay due to high network latency. This narrowing allows examination of the performance of the decision tree classifier in a significantly reduced sample comprising only 4905 instances, where the attributes of and are scrutinised based on their recorded values, where is measured in bytes, and in seconds. The findings from the evaluation underscore the effectiveness of this simplistic decision tree model, revealing its ability to proficiently identify instances even when slow DoS attacks are meticulously designed to be covert. Achieving a high predicted accuracy of 96.2% and mean precision of 94.9% highlights that when LN and MN are present in the network, a lightweight decision tree classifier evaluating only two key attributes, with a reduced dataset leads to comparable results to ML approaches. For example, slow DoS detection is made possible here by testing the model on less than 5000 packets, equating to 526,633 bytes of data. This is in contrast to ML approaches that require large volumes of data, often gigabytes, to produce comparable detection accuracy. For example, [52] required the processing of 10 attributes, including 608,947 instances of legitimate and malicious traffic instances.

Table 7.
Classified LN and MN.
However, like all other publicly available datasets, this approach fails to consider genuine SN with slow connectivity. Given that slow DoS attempts to evade detection by imitating nodes with poor connections, this needed to be factored into the modelling.
By including SN in the reduced dataset, it can be seen in Table 8 the LN accuracy decreases, along with the overall accuracy of the decision tree classifier. It is also apparent the decrease in accuracy is due to the increased misclassifications which collectively supports the hypothesis that incorporating SN within a network significantly impacts the detection performance of a model. This is intensified when persistent slow DoS activity is involved, raising questions about the reliability of classification outcomes that do not consider the impact of legitimate SN in their model. Furthermore, these observations buttress the premise that when SN is included in a dataset and is not accounted for, it can lead to inaccurate classification results. Given this approach analysed only 4905 packets, higher volumes of data packets processed could lead to even greater inaccuracies and misclassifications.

Table 8.
Classified merged LN/SN and MN.
In summarising, evaluating the scenario in which SN traffic is not present, the MN class accuracy is 98.3% while the accuracy for the LN class is 91.5%. With SN present, the corresponding MN class accuracy is 97% while the accuracy for the LN/SN class is 94.3%. The notable difference in misclassification of LN and MN which increases from 47 to 88 instances is significant given the low volume of packets used.
5.1. Observations
Another important observation distilled from Table 8 is a comparison of the slow DoS detection model presented in [19], which achieved an accuracy of 92.6% for the decision tree classifier, along with a comparable average accuracy derived from six ML classifiers of 96.3%. In [37,53], the slow DoS proposals scored slightly higher in terms of overall accuracy, however, these approaches did not consider the resource imposition. For example, [53] required the extraction of 11 attributes, totalling 56,891 tuples, compared to the requirement of two attributes and 4905 packets for the solution presented here. In the work of [23], 18 bi-directional flow features were extracted, based on their observations and evaluation of the CIC-IDS 2017 and SUEE datasets. Their findings showed the decision tree outperformed other ML classifiers and, in doing so, recorded an overall detection accuracy of ≈99.99%.
Summary
While the model presented gives comparable detection accuracy to [19], and towards the top end of [23], the principal advantage is the significantly reduced resource overhead which is an essential design requirement in any IoT-based slow DoS detection model. Although the preceding evaluation demonstrates that a lightweight decision tree classifier operating on a reduced LPC dataset can achieve high classification accuracy with minimal attribute selection, it is important to reflect on the operational constraints imposed by resource-constrained IoT nodes. In IoT environments, the computational overhead associated with packet processing, feature extraction, and classification must be explicitly quantified and optimised. Detection accuracy alone does not capture the practical viability of a real-time model or embedded deployment scenarios, so it is vital to model the critical nexus between classification performance and processing cost to determine optimal operating thresholds. The next section presents a performance cost model that facilitates this balancing process with a systematic method to characterise the diminishing returns of increased packet analysis in constrained IoT networks.
6. Modelling Accuracy and Processing Cost
By focusing the slow DoS detection model only on attributes that are proven to be significant in terms of the attack type, i.e., and it has been shown to significantly lower the processing cost incurred by the detection node. In addition to the resource limitations of the IoT nodes, the aim must be to scale the detection model to an optimal point that balances the nexus of high detection accuracy and low detection processing cost.
Using metrics like accuracy, mean packet length, total packet volume, and the number of extracted features, a predictive model can be developed which scales the classifier’s performance with the number of packets processed. This judgement can be distilled from the decision tree classifier’s results in Table 8, where specifically, the model considers packets with a mean length of bytes. This allows for an estimate of how the accuracy improves as more packets are processed. Taking the decision tree classifier together with the LPC approach in Section 5, and applying this as a known variable, a conceptual model can be constructed that evaluates the processing cost relative to the increased detection accuracy.
Thus, it was possible to model the accuracy of the detection system as an exponential function of the packet count , as shown in Equation (6). This model reflects the system behaviour where the accuracy rapidly improves with increasing packets before levelling off as it approaches the maximum.
- = Accuracy as a function of the packet count .
- = Initial accuracy at packet count
- = Final accuracy (maximum achievable)
- = Initial packet count (where growth begins)
- = Growth rate parameter for accuracy increase
This model can be used to represent the common saturation behaviour in resource-constrained detection systems, showing where early data yield significant gains, and further improvements become marginal with additional data being processed. Figure 5 shows the modelling of (a), the increase in accuracy from 96.2% based on the initial values of Table 7, and the total number of packets from the reduced dataset, to the optimum target values of 99.2% accuracy based on an approximation of similar ML approaches using the decision tree classifier [54,55].
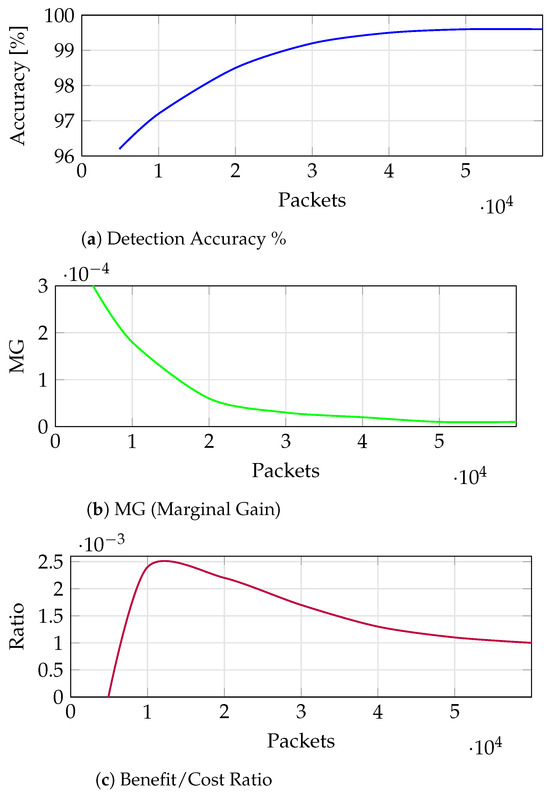
Figure 5.
Modelling accuracy, processing cost and performance gains.
The marginal accuracy gain is depicted in Figure 5b, which predicts the accuracy gained as additional packets are required for processing. This clearly confirms the model’s asymptotic behaviour between 10,000 and 20,000 packets, implying further packet processing is ineffective.
The benefit/cost ratio (R) in Figure 5c is defined as the ratio of accuracy improvement to processing overhead as defined in Equation (8). The corresponding (R) plot shows there is a local maximal point where further packet processing becomes superfluous.
6.1. Application Cost Modelling
The cost model in [10], calculates the processing overhead of an HTTP application, allowing a comparison of resource requirements between the proposed model, FPC and inbound-only packet capture. Equation (9) defines this cost model, based on a packet arrival rate (packets per second), the mean packet length (bytes), and () being the total application runtime.
A linear relationship between the packet processing rate and cost function is assumed to provide a simplified framework for comparative evaluation. The evaluation compares models using four metrics: application cost (), precision or accuracy (A), and processing time (). To ensure an equitable cross metric evaluation, Min-Max normalisation is applied to all values as in [51].
The normalised accuracy is given by:
For those metrics where a lower value is preferable, i.e., , the inverse normalisation is used:
This step enhances interpretability and supports composite evaluation across various units of measurement.
To reflect the relative importance of each metric, a weight is assigned which allows context sensitive emphasis depending on deployment needs. The composite score is then calculated as a weighted sum of normalised values:
Higher values indicate more efficient models while a lower indicates improved efficiency.
For consistency purposes, the values of and should reflect the prevailing operating environment, including network load, network interface card (NIC) capacity, and processing capabilities. These are all critical factors in a resource-constrained IoT network, so the min and max values should be derived from representative run time sampling.
Table 9 compares the LPC, FPC, and inbound-only models using the respective and values of the relevant application.

Table 9.
Comparison of models by normalised composite score.
While Equation (9) assumes linear scalability of the cost with the packet rate and size, this simplifies the analysis though real-world networks may be subject to stochastic effects due to congestion, CPU load, or network interface saturation.
To validate the linear assumption, benchmark tests were performed using two datasets (see Section 4) for packet rates ranging from 12.5 pps [48] to 34.2 pps [49]. A regression analysis of the observed costs yielded = 0.94, indicating a strong linear trend to validate the application of Equation (9) in this comparative evaluation.
Although the application cost model provides a direct means of comparing resource efficiency between detection models such as LPC, FPC, and inbound-only capture, it remains limited in scope by treating cost and accuracy as independent metrics. In realistic IoT deployments, these factors are intrinsically related and optimising one often comes at the expense of another. As such, a more holistic performance evaluation is required that allows the weighting of accuracy versus cost in line with specific deployment priorities, such as energy conservation, real-time responsiveness, or threat sensitivity. To address this, the next section introduces a generalised performance model (MPerf) that enables network security and system designers to calibrate detection strategies to meet the unique operational demands of resource-constrained IoT networks.
6.2. Modelling Performance
This approach to varying the number of packets and/or attributes for analysis can be further extended by adjusting the number of packets extracted (n). This provides a flexible model that can be applied to varying low resource operational requirements. In Equation (13), it is possible to find a preferable by applying a weighted value () to balance the accuracy required (A) with the overhead cost (C) of the model (see Equation (13)) which is a beneficial proposition for resource-constrained IoT nodes.
can be applied to approximate the relationship between A and C as illustrated in Figure 6, where C assumes a linear increase, with A and C being assigned weight values of 0.7 and 0.3 respectively.
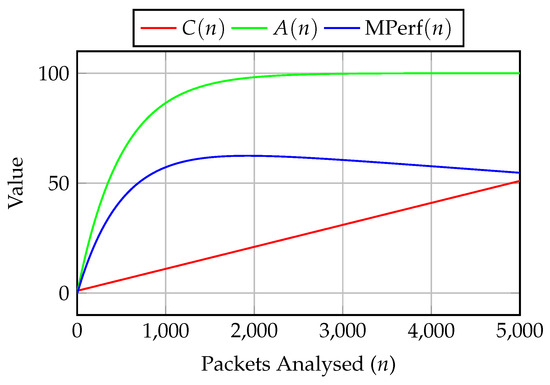
Figure 6.
MPerf approximation.
In Figure 6, the weights and have been chosen to reflect a scenario where detection accuracy is prioritised over computational cost. These values are not empirically derived, but are chosen to demonstrate the flexibility of the model. In practice, these weights can be fine tuned based on the specific constraints or objectives of the target IoT deployment like minimal power consumption or maximising detection accuracy.
By analysing both the accuracy and cost parameters in Figure 6, a compromise can be identified between slow DoS detection performance and resource consumption. In this scenario and based on the results in Table 7 and Table 8, a quasi-optimal performance point can be observed when the packet count n ≈ 2000, gradually decreasing to 3000 packets. Therefore, it can be hypothesised that a detection accuracy of around 98% is achievable with just 2000 packets. This modelling approach is particularly valuable for IoT networks where minimising detection overhead or maximising accuracy depending on operational priorities requires a flexible and scalable performance framework. The MPerf model has been derived from empirical data collected in the live IoT test network (Section 4), so it reflects the typical processing constraints and throughput limitations characteristic of IoT devices. While theoretical, the model is grounded in practical experimentation and offers a basis for future adaptation in intrusion detection methodologies. It can be calibrated to suit alternative hardware platforms, network conditions, or detection objectives, making it a versatile tool for IoT intrusion detection where balancing accuracy and resource expenditure is critical.
7. Conclusions
The growing pervasiveness of IoT deployments in critical domains requires intrusion detection mechanisms that are both accurate, and operationally viable within severe resource constraints. This paper introduces a lightweight and highly efficient slow DoS detection model designed specifically for environments where conventional, resource intensive methods are impractical. By evaluating the three slow DoS attack variants; slow GET, slow Read, and slow POST against legitimate and high latency genuine traffic, the model achieves a detection precision of more than 96% using just the two network attributes of TCP/IP packet length and the TCP delta time.
The core contribution is a novel packet capturing technique that significantly reduces processing overhead by more than 99%, along with the inclusion of genuine slow nodes to simulate real-world latency variations.
This supports a slow DoS detection strategy capable of discriminating benign SN communications from malicious stealthy attacks, a vital nuance overlooked in almost all existing detection schemes. This pragmatic minimal overhead model for slow DoS detection affords flexible IoT deployment options via a measurable and tunable nexus between detection performance and computational cost.
Future work will focus on extending the model’s applicability to time sensitive IoT applications, where minimal detection latency and false positives are paramount requirements. Incorporating adaptive thresholds, online learning, and real-time updates will be key to upholding high detection rates under an ever evolving malicious attack landscape. Moreover, embedding this detection framework into low power embedded systems and benchmarking its resilience against encrypted MN traffic in large scale IoT deployments will further authenticate its practical efficacy.
Author Contributions
Conceptualization, methodology, A.R.; formal analysis, A.R.; Writing—Review and Editing, A.R., L.S.D. and S.K.M.; Supervision, L.S.D. and S.K.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The dataset utilised in this study is available at https://ordo.open.ac.uk/articles/dataset/HTTP_DoS_Dataset_in_PCAP_format_for_Wireshark/17206289 (accessed on 15 February 2025).
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| FPC | Full Packet Capture |
| LPC | Limited Packet Capture |
| SN | slow Legitimate Node |
| SG | slow GET |
| SR | slow Read |
| SP | slow POST |
| LN | Legitimate Node |
| MN | Malicious Node |
| TP | Traffic Profile |
| TCP/IP Packet Length | |
| Packet Delta Time |
References
- Rizzardi, A.; Zachos, G.; Mantas, G.; Porfyrakis, K.; Rodriguez, J. Implementing Anomaly-Based Intrusion Detection for Resource-Constrained Devices in IoMT Networks. Sensors 2025, 25, 1216. [Google Scholar] [CrossRef]
- Wakili, A.; Bakkali, S. Privacy-Preserving Security of IoT Networks: A Comparative Analysis of Methods and Applications. Cyber Secur. Appl. 2025, 25, 100084. [Google Scholar] [CrossRef]
- Cao, Z.; Zhao, Z.; Shang, W.; Ai, S.; Shen, S. Using the ToN-IoT dataset to develop a new intrusion detection system for industrial IoT devices. Multimed. Tools Appl. 2024, 84, 16425–16453. [Google Scholar] [CrossRef]
- Sinha, S. Number of Connected IoT Devices Growing 13% to 18.8 Billion. 2024. Available online: https://iot-analytics.com/number-connected-iot-device (accessed on 2 January 2025).
- Saied, M.; Guirguis, S.; Madbouly, M. Review of filtering based feature selection for Botnet detection in the Internet of Things. Artif. Intell. Rev. 2025, 58, 114. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.S.; Kouadri, S. A Reliable Real-Time slow DoS Detection Framework for Resource-Constrained IoT Networks. In Proceedings of the 2021 IEEE Global Communications Conference: IoT and Sensor Networks (Globecom2021 IoTSN), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Kampourakis, V.; Makrakis, G.M.; Kolias, C. From Seek-and-Destroy to Split-and-Destroy: Connection Partitioning as an Effective Tool against Low-Rate DoS Attacks. Future Internet 2024, 16, 137. [Google Scholar] [CrossRef]
- Tripathi, N. Delays Have Dangerous Ends: Slow HTTP/2 DoS Attacks Into the Wild and Their Real-Time Detection Using Event Sequence Analysis. IEEE Trans. Dependable Secur. Comput. 2024, 21, 1244–1256. [Google Scholar] [CrossRef]
- Mohammed, M.; Shailendra, S.; Jong, R.; Park, H. Distributed denial of service attacks and its defenses in IoT: A survey. J. Supercomput. 2020, 76, 5320–5363. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.S.; Kouadri, S.M. The Guardian Node slow DoS Detection Model for Real-Time Application in IoT Networks. Sensors 2024, 24, 5581. [Google Scholar] [CrossRef]
- Coscia, A.; Dentamaro, V.; Galantucci, S.; Maci, A.; Pirlo, G. Automatic decision tree-based NIDPS ruleset generation for DoS/DDoS attacks. J. Inf. Secur. Appl. 2024, 82, 103736. [Google Scholar] [CrossRef]
- Logeswari, G.; Thangaramya, K.; Selvi, M.; Deepika Roselind, J. An improved synergistic dual-layer feature selection algorithm with two type classifier for efficient intrusion detection in IoT environment. Sci. Rep. 2025, 15, 8050. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Samarakoon, S.; Porambage, P.; Liyanage, M.; Chang, S.Y.; Kim, J.; Kim, J.; Ylianttila, M. Descriptor: 5G Wireless Network Intrusion Detection Dataset (5G-NIDD). IEEE Data Descr. 2025, 1–12. [Google Scholar] [CrossRef]
- Makina, H.; Letaifa, A.B.; Rachedi, A. Survey on security and privacy in Internet of Things -based eHealth applications: Challenges, architectures, and future directions. Secur. Priv. 2024, 7, e346. [Google Scholar] [CrossRef]
- Hasan, M.K.; Ghazal, T.M.; Saeed, R.A.; Pandey, B.; Gohel, H.; Eshmawi, A.A.; Abdel-Khalek, S.; Alkhassawneh, H.M. A review on security threats, vulnerabilities, and counter measures of 5G enabled Internet-of-Medical-Things. IET Commun. 2022, 16, 421–432. [Google Scholar] [CrossRef]
- Mendon, S. slow DOS Attack: Why It Is Dangerous and How to Detect Using a SIEM. 2016. Available online: https://www.paladion.net/blogs/how-to-detect-slow-dos-attack-using-siem (accessed on 4 January 2017).
- Dhanapal, A.; Nithyanandam, P. The slow http distributed denial of service attack detection in cloud. Scalable Comput. 2019, 20, 285–298. [Google Scholar] [CrossRef]
- NetScout. Slow Read Attacks. 2024. Available online: https://www.netscout.com/what-is-ddos/slow-post-attacks (accessed on 19 May 2024).
- Inchara, S.; Keerthana, D.; Babu, K.N.M.; Mabel, J.P. Detection and mitigation of slow DoS attacks using machine learning. In AIP Conference Proceedings; American Institute of Physics Inc.: College Park, MD, UDA, 2023; pp. 1–10. [Google Scholar] [CrossRef]
- Ilango, H.S.; Ma, M.; Su, R. A FeedForward–Convolutional Neural Network to Detect Low-Rate DoS in IoT. Eng. Appl. Artif. Intell. 2022, 114, 105059. [Google Scholar] [CrossRef]
- Haddadi, M.; Khiat, A.; Bouaoud, H.; Djehiche, H. SPGDAD: Slow HTTP-Get denial of service attack detection using ontology. Inf. Secur. J. Glob. Perspect. 2024, 34, 79–87. [Google Scholar] [CrossRef]
- UNB. CIC-IDS2017. 2017. Available online: http://www.unb.ca/cic/datasets/ids-2017.html (accessed on 21 April 2022).
- Muraleedharan, N.; Janet, B. Scaffy: A slow denial-of-service attack classification model using flow data. Int. J. Inf. Secur. Priv. 2021, 15, 106–128. [Google Scholar] [CrossRef]
- Lukaseder, T. 2017-SUEE-Data-Set. 2017. Available online: https://github.com/vs-uulm/2017-SUEE-data-set/tree/master (accessed on 17 September 2025).
- Garcia, N.; Alcaniz, T.; González-Vidal, A.; Bernabe, J.B.; Rivera, D.; Skarmeta, A. Distributed real-time slowDoS attacks detection over encrypted traffic using Artificial Intelligence. J. Netw. Comput. Appl. 2021, 173, 1084–8045. [Google Scholar] [CrossRef]
- Jablaoui, R.; Cheikhrouhou, O.; Hamdi, M.; Liouane, N. Deep learning enabled intrusion detection system for IoT security. EURASIP J. Wirel. Commun. Netw. 2025, 2025, 66. [Google Scholar] [CrossRef]
- Gogoi, B.; Ahmed, T. HTTP Low and slow DoS Attack Detection using LSTM based deep learning. In Proceedings of the 2022 IEEE 19th India Council International Conference (INDICON), Kochi, India, 24–26 November 2022; pp. 1–6. [Google Scholar]
- Kemp, C.; Calvert, C.; Khoshgoftaar, T.M.; Leevy, J.L. An approach to application-layer DoS detection. J. Big Data 2023, 10, 22. [Google Scholar] [CrossRef]
- Chen, J.; Wu, H.; Wang, X.; Wang, S.; Cheng, G.; Hu, X. IEA-DMS: An Interpretable feature-driven, Efficient and Accurate Detection Method for slow HTTP DoS in high-speed networks. Comput. Secur. 2025, 150, 104291. [Google Scholar] [CrossRef]
- Chen, J.; Wu, H.; Wang, S.; Cheng, G.; Hu, X. An Accurate and Real-Time Detection Method for Concealed slow HTTP DoS in Backbone Network. In ICT Systems Security and Privacy Protection, Proceedings of the 38th IFIP TC 11 International Conference, SEC 2023, Poznan, Poland, 14–16 June 2023; Springer: Cham, Switzerland, 2024; Volume 679, pp. 207–221. [Google Scholar] [CrossRef]
- Kemp, C.; Calvert, C.; Khoshgoftaar, T.M. Detection Methods of slow Read DoS Using Full Packet Capture Data. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science, IRI 2020, Las Vegas, NV, USA, 11–13 August 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020; pp. 9–16. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.S.; Mostefaoui, S.K. Packet Filtering and Sampling for Efficient slow Denial of Service Detection in Resource Scarce IoT Networks. In Proceedings of the 2023 International Symposium on Networks, Computers and Communications (ISNCC) 2023, Doha, Qatar, 23–26 October 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Sikora, M.; Fujdiak, R.; Kuchar, K.; Holasova, E.; Misurec, J. Generator of slow Denial-of-Service Cyber Attacks. Sensors 2021, 21, 5473. [Google Scholar] [CrossRef]
- Prakash, K.J.; Saumya, B.; Tapaswi, S. mFCBF based lightweight intrusion detection system for IoT networks. Clust. Comput. 2025, 28, 416. [Google Scholar] [CrossRef]
- Memon, S.Q. Prevention Mechanism For RUDY Attack And Its Comparison. Univ. Sindh J. Inf. Commun. Technol. 2020, 4, 45–51. [Google Scholar]
- Fu, Y.; Duan, X.; Wang, K.; Li, B. Low-rate Denial of Service attack detection method based on time-frequency characteristics. J. Cloud Comput. 2022, 11, 1–19. [Google Scholar] [CrossRef]
- Sood, S.; Hubballi, N. slowTrack: Detecting slow rate Denial of Service attacks against HTTP with behavioral parameters. J. Supercomput. 2024, 80, 1788–1817. [Google Scholar] [CrossRef]
- Dung, D.A.; Nakamura, Y. Verification of State Based slow HTTP DDoS Prevention Method. In Proceedings of the 12th IEEE International Conference on Control, Automation and Information Sciences, ICCAIS 2023, Hanoi, Vietnam, 27–29 November 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 686–691. [Google Scholar] [CrossRef]
- Tang, D.; Wang, S.; Zhang, S.; Qin, Z.; Liang, W.; Xiao, S. Real-Time Monitoring and Mitigation of SDoS Attacks Using the SDN and New Metrics. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 1721–1733. [Google Scholar] [CrossRef]
- Kapourchali, R.F.; Mohammadi, R.; Nassiri, M. P4httpGuard: Detection and prevention of slow-rate DDoS attacks using machine learning techniques in P4 switch. Clust. Comput. 2024, 27, 8047–8064. [Google Scholar] [CrossRef]
- Rios, V.; Inacio, P.; Magoni, D.; Freire, M. Detection of slowloris Attacks using Machine Learning Algorithms. In Proceedings of the 39th ACM/SIGAPP Symposium on Applied Computing, Avila Spain, 8–12 April 2024; pp. 1321–1330. [Google Scholar] [CrossRef]
- Reed, A.; Dooley, L.; Kouadri, S. SA-IDS: A single attribute intrusion detection system for slow DoS attacks in IoT networks. Internet Things 2025, 30, 101512. [Google Scholar] [CrossRef]
- Tripathi, N.; Hubballi, N.; Singh, Y. How Secure are Web Servers? An empirical study of slow HTTP DoS attacks and detection. In Proceedings of the =2016 11th International Conference on Availability, Reliability and Security, ARES 2016, Salzburg, Austria, 31 August 2016–2 September 2016; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2016; pp. 454–463. [Google Scholar] [CrossRef]
- Benzaid, C.; Boukhalfa, M.; Taleb, T. Robust Self-Protection Against Application-Layer (D)DoS Attacks in SDN Environment. In Proceedings of the IEEE Wireless Communications and Networking Conference, WCNC, Seoul, Republic of Korea, 25–28 May 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020; Volume 2020-May, pp. 1–6. [Google Scholar] [CrossRef]
- Cambiaso, E. On the Use of Low Cost IoT Devices to Perpetrate slow DoS Attacks. In Proceedings of the Eighth International Congress on Information and Communication Technology; Lecture Notes in Networks and Systems; Springer Science and Business Media Deutschland GmbH: Singapore, 2024; Volume 695, pp. 859–875. [Google Scholar] [CrossRef]
- Herzalla, D.; Lunardi, W.T.; Andreoni, M. TII-SSRC-23 Dataset: Typological Exploration of Diverse Traffic Patterns for Intrusion Detection. IEEE Access 2023, 11, 118577–118594. [Google Scholar] [CrossRef]
- Karmous, N.; Aoueileyine, M.O.E.; Abdelkader, M.; Romdhani, L.; Youssef, N. Software-Defined-Networking-Based One-versus-Rest Strategy for Detecting and Mitigating Distributed Denial-of-Service Attacks in Smart Home Internet of Things Devices. Sensors 2024, 24, 5022. [Google Scholar] [CrossRef]
- Reed, A. HTTP DoS IoT Dataset. 2021. Available online: https://ordo.open.ac.uk/search?q=Reed (accessed on 20 June 2021).
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef] [PubMed]
- Catillo, M.; Del Vecchio, A.; Pecchia, A.; Villano, U. A Critique on the Use of Machine Learning on Public Datasets for Intrusion Detection. In Quality of Information and Communications Technology, Proceedings of the 14th International Conference, QUATIC 2021, Algarve, Portugal, 8–11 September 2021; Springer: Cham, Switzerland, 2021; Volume 1439, pp. 253–266. [Google Scholar] [CrossRef]
- Shukla, P.; Krishna, C.R.; Patil, N.V. SDDA-IoT: Storm-based distributed detection approach for IoT network traffic-based DDoS attacks. Clust. Comput. 2024, 27, 6397–6424. [Google Scholar] [CrossRef]
- Swe, Y.M.; Aung, P.P.; Hlaing, A.S. A slow ddos attack detection mechanism using feature weighing and ranking. In Proceedings of the International Conference on Industrial Engineering and Operations Management, Rome, Italy, 2–5 August 2021; pp. 4500–4509. [Google Scholar] [CrossRef]
- Abisoye, O.A.; Shadrach Akanji, O.; Abisoye, B.O.; Awotunde, J. slow Hypertext Transfer Protocol Mitigation Model in Software Defined Networks. In Proceedings of the 2020 International Conference on Data Analytics for Business and Industry: Way Towards a Sustainable Economy, ICDABI 2020, Sakheer, Bahrain, 26–27 October 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Fuladi, R.; Baykas, T.; Anarim, E. The Use of Statistical Features for Low-Rate Denial of Service Attack Detection. In Proceedings of the International Conference on 6G Networking, 6GNet 2023, Paris, France, 18–20 October 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Alsolami, T.; Alsharif, B.; Ilyas, M. Enhancing Cybersecurity in Healthcare: Evaluating Ensemble Learning Models for Intrusion Detection in the Internet of Medical Things. Sensors 2024, 24, 5937. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).