Establishing a Model for the User Acceptance of Cybersecurity Training
Abstract
1. Introduction
2. Components and Evolution of the TAM and Its Extensions
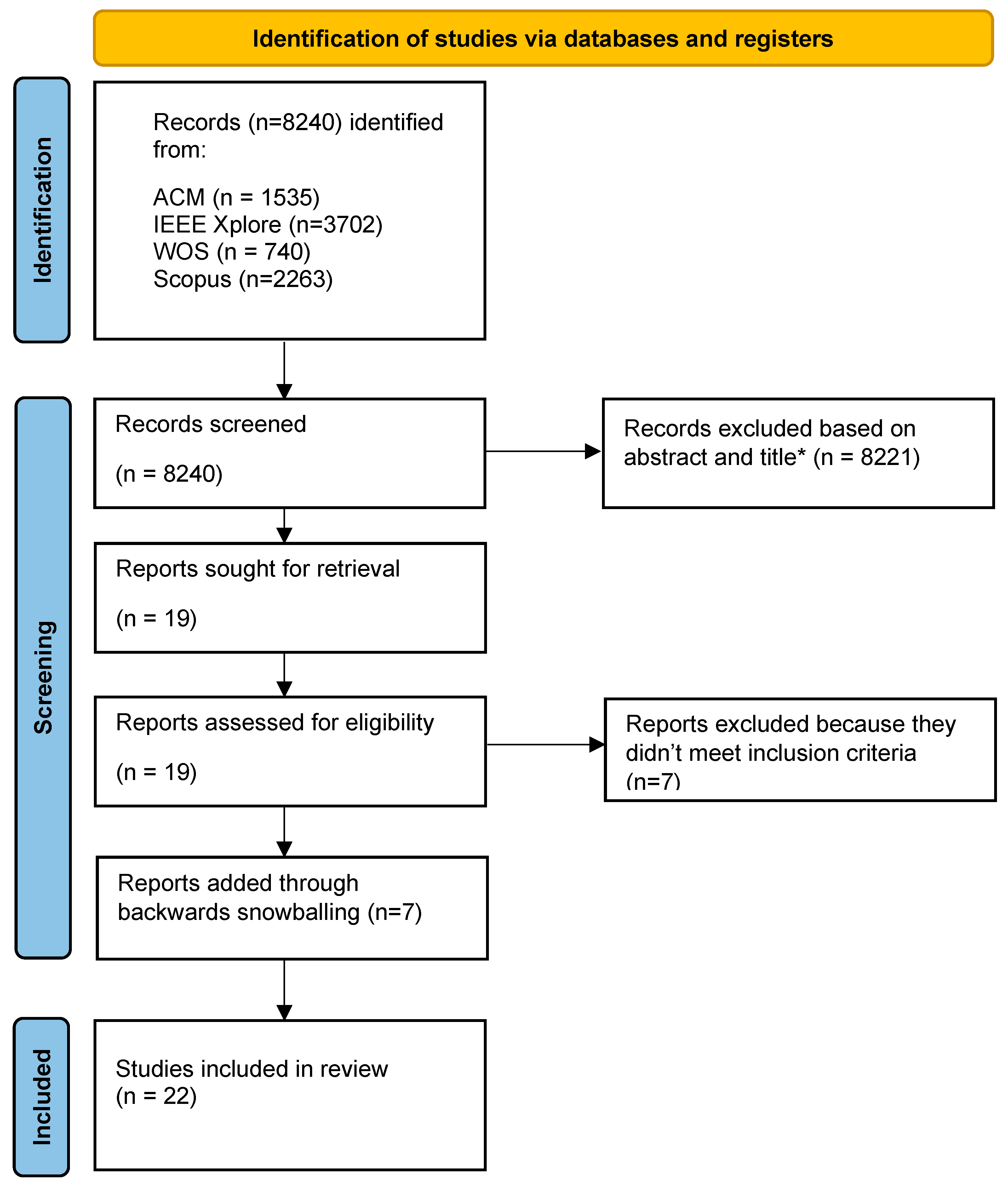
3. Literature Assessment Methodology
- The hits from each search were screened based on titles and abstracts. The result of this step was a list of candidate papers. This step was completed by two researchers individually.
- The lists of the two researchers were compared, and all papers included by one or both researchers were included for the next step.
- The full body of the candidate papers was screened again by two researchers individually. The result was a refined list of candidate papers.
- The lists of the two researchers were compared. Disagreements were solved by discussing each paper, where the researcher made different decisions until a consensus was reached. The output of this step was reviewed by a third researcher.
- Backwards snowballing was applied by considering all papers referenced by the set of papers from (4). Steps 1–4 were repeated for those papers, resulting in a final set of included publications.
4. Results
5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Davis, F.D. A Technology Acceptance Model for Empirically Testing New End-User Information Systems: Theory and Results; Massachusetts Institute of Technology: Cambridge, MA, USA, 1985. [Google Scholar]
- Lee, Y.; Kozar, K.A.; Larsen, K.R. The technology acceptance model: Past, present, and future. Commun. Assoc. Inf. Syst. 2003, 12, 50. [Google Scholar] [CrossRef]
- Venkatesh, V.; Davis, F.D. A theoretical extension of the technology acceptance model: Four longitudinal field studies. Manag. Sci. 2000, 46, 186–204. [Google Scholar] [CrossRef]
- Venkatesh, V.; Bala, H. Technology acceptance model 3 and a research agenda on interventions. Decis. Sci. 2008, 39, 273–315. [Google Scholar] [CrossRef]
- Paré, G.; Kitsiou, S. Methods for literature reviews. In Handbook of Ehealth Evaluation: An Evidence-Based Approach [Internet]; University of Victoria: Victoria, BC, Canada, 2017. [Google Scholar]
- Meline, T. Selecting studies for systemic review: Inclusion and exclusion criteria. Contemp. Issues Commun. Sci. Disord. 2006, 33, 21–27. [Google Scholar] [CrossRef]
- Jesson, J.; Lacey, F.M.; Matheson, L. Doing Your Literature Review: Traditional and Systematic Techniques; Sage: Thousand Oaks, CA, USA, 2011. [Google Scholar]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The prisma 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, 71. [Google Scholar] [CrossRef] [PubMed]
- Sarkis-Onofre, R.; Catalá-López, F.; Aromataris, E.; Lockwood, C. How to properly use the prisma statement. Syst. Rev. 2021, 10, 117. [Google Scholar] [CrossRef] [PubMed]
- Shukla, S.S.; Tiwari, M.; Lokhande, A.C.; Tiwari, T.; Singh, R.; Beri, A. A comparative study of cyber security awareness, competence and behavior. In Proceedings of the 2022 5th International Conference on Contemporary Computing and Informatics (IC3I), Uttar Pradesh, India, 14–16 December 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1704–1709. [Google Scholar]
- Abawajy, J. User preference of cyber security awareness delivery methods. Behav. Inf. Technol. 2014, 33, 237–248. [Google Scholar] [CrossRef]
- Mokwetli, M.; Zuva, T. Adoption of the ict security culture in smme’s in the gauteng province, south africa. In Proceedings of the 2018 International Conference on Advances in Big Data, Computing and Data Communication Systems (icABCD), Durban, South Africa, 6–7 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–7. [Google Scholar]
- Dang-Pham, D.; Pittayachawan, S.; Bruno, V. Why employees share information security advice? Exploring the contributing factors and structural patterns of security advice sharing in the workplace. Comput. Hum. Behav. 2017, 67, 196–206. [Google Scholar] [CrossRef]
- Alhalafi, N.; Veeraraghavan, P. Exploring the challenges and issues in adopting cybersecurity in saudi smart cities: Conceptualization of the cybersecurity-based utaut model. Smart Cities 2023, 6, 1523–1544. [Google Scholar] [CrossRef]
- Lui, S.M.; Hui, W. The effects of knowledge on security technology adoption: Results from a quasi-experiment. In Proceedings of the 5th International Conference on New Trends in Information Science and Service Science, Macao, China, 24–26 October 2011; IEEE: Piscataway, NJ, USA, 2011; Volume 2, pp. 328–333. [Google Scholar]
- Bryan Foltz, C.; Schwager, P.H.; Anderson, J.E. Why users (fail to) read computer usage policies. Ind. Manag. Data Syst. 2008, 108, 701–712. [Google Scholar] [CrossRef]
- Gadzama, W.A.; Katuka, J.I.; Gambo, Y.; Abali, A.M.; Usman, M.J. Evaluation of employees awareness and usage of information security policy in organizations of developing countrties: A study of federal inland revenue service, nigeria. J. Theor. Appl. Inf. Technol. 2014, 67, 443–460. [Google Scholar]
- Hart, S.; Margheri, A.; Paci, F.; Sassone, V. Riskio: A serious game for cyber security awareness and education. Comput. Secur. 2020, 95, 101827. [Google Scholar] [CrossRef]
- Ma, S.; Zhang, S.; Li, G.; Wu, Y. Exploring information security education on social media use: Perspective of uses and gratifications theory. Aslib J. Inf. Manag. 2019, 71, 618–636. [Google Scholar] [CrossRef]
- Rhee, H.-S.; Kim, C.; Ryu, Y.U. Self-efficacy in information security: Its influence on end users’ information security practice behavior. Comput. Secur. 2009, 28, 816–826. [Google Scholar] [CrossRef]
- Potgieter, M.; Marais, C.; Gerber, M. Fostering content relevant information security awareness through browser extensions. In Proceedings of the Information Assurance and Security Education and Training: 8th IFIP WG 11.8 World Conference on Information Security Education, WISE 8, Auckland, New Zealand, 8–10 July 2013, Proceedings, WISE 7, Lucerne Switzerland, 9–10 June 2011, and WISE 6, Bento Gonçalves, RS, Brazil, 27–31 July 2009; Revised Selected Papers 8. Springer: Berlin/Heidelberg, Germany, 2013; pp. 58–67. [Google Scholar]
- Reeves, A.; Calic, D.; Delfabbro, P. Get a red-hot poker and open up my eyes, it’s so boring” 1: Employee perceptions of cybersecurity training. Comput. Secur. 2021, 106, 102281. [Google Scholar] [CrossRef]
- Kävrestad, J.; Gellerstedt, M.; Nohlberg, M.; Rambusch, J. Survey of users’ willingness to adopt and pay for cybersecurity training. In Proceedings of the International Symposium on Human Aspects of Information Security and Assurance, Lesbos, Greece, 6–8 July 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 14–23. [Google Scholar]
- Shillair, R. Talking about online safety: A qualitative study exploring the cybersecurity learning process of online labor market workers. In Proceedings of the 34th ACM International Conference on the Design of Communication, Silver Spring, MD, USA, 23–24 September 2016; pp. 1–9. [Google Scholar]
- Shen, L.W.; Mammi, H.K.; Din, M.M. Cyber security awareness game (csag) for secondary school students. In Proceedings of the 2021 International Conference on Data Science and Its Applications (ICoDSA), Porto, Portugal, 6–9 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 48–53. [Google Scholar]
- Jin, G.; Tu, M.; Kim, T.-H.; Heffron, J.; White, J. Game based cybersecurity training for high school students. In Proceedings of the 49th ACM Technical Symposium on Computer Science Education, Baltimore, MD, USA, 21–24 February 2018; pp. 68–73. [Google Scholar]
- CJ, G.; Pandit, S.; Vaddepalli, S.; Tupsamudre, H.; Banahatti, V.; Lodha, S. Phishy-a serious game to train enterprise users on phishing awareness. In Proceedings of the 2018 Annual Symposium on Computer-Human Interaction in Play Companion Extended Abstracts, Melbourne, VIC, Australia, 28–31 October 2018; pp. 169–181. [Google Scholar]
- Talib, S.; Clarke, N.L.; Furnell, S.M. An analysis of information security awareness within home and work environments. In Proceedings of the 2010 International Conference on Availability, Reliability and Security, Krakow, Poland, 15–18 February 2010; IEEE: Piscataway, NJ, USA, 2021; pp. 196–203. [Google Scholar]
- Kajzer, M.; D’Arcy, J.; Crowell, C.R.; Striegel, A.; Van Bruggen, D. An exploratory investigation of message-person congruence in information security awareness campaigns. Comput. Secur. 2014, 43, 64–76. [Google Scholar] [CrossRef]
- Yasin, A.; Liu, L.; Li, T.; Fatima, R.; Jianmin, W. Improving software security awareness using a serious game. IET Softw. 2019, 13, 159–169. [Google Scholar] [CrossRef]
- Aladawy, D.; KBeckers; Pape, S. Persuaded: Fighting social engineering attacks with a serious game. In Proceedings of the Trust, Privacy and Security in Digital Business: 15th International Conference, TrustBus 2018, Regensburg, Germany, 5–6 September 2018; Proceedings 15. Springer: Berlin/Heidelberg, Germany, 2018; pp. 103–118. [Google Scholar]
- Bada, M.; Sasse, A.M.; Nurse, J.R. Cyber security awareness campaigns: Why do they fail to change behaviour? arXiv 2019, arXiv:1901.02672. [Google Scholar]

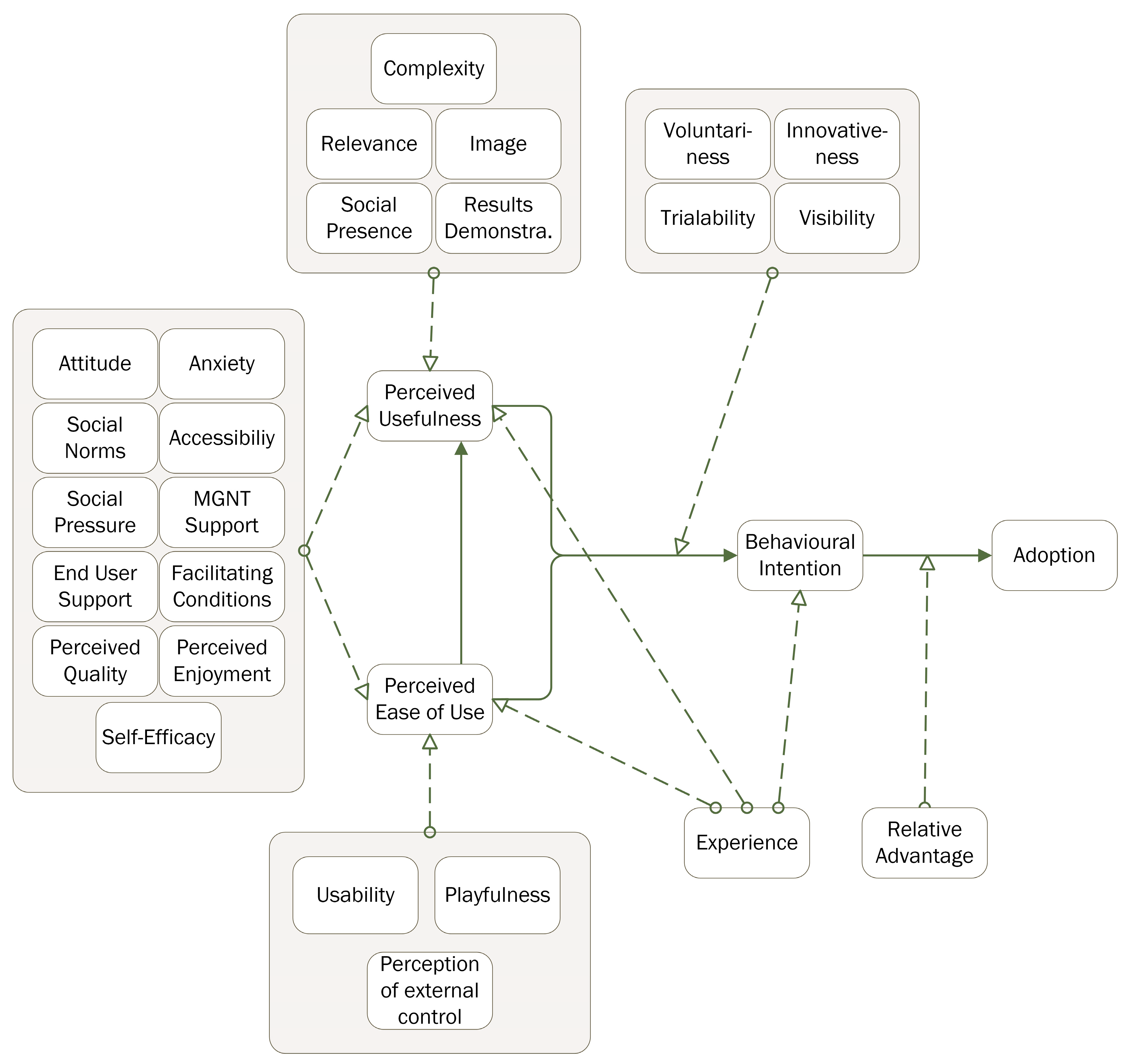
| Factor | Description |
|---|---|
| Attitude | A person’s general attitude towards a technology or group of technologies will impact their adoption of it |
| Anxiety | Users who are anxious about using computers are less prone to adopt new technology |
| Social Norms | The perception of whether others think that it is good to adopt a technology |
| Accessibility | User access to hardware and the ability to retrieve desired information impacts user acceptance |
| Social Pressure | Pressure from others to adopt a technology or not |
| Management support | The degree to which management supports the use of a technology by providing resources and acting as a change agent |
| End User Support | A technology is more likely to be adopted if support for users and IT staff is available |
| Facilitating Conditions | User acceptance is impacted by a user’s perception of how well the use of a technology is supported by resource factors such as time, money, and systems support |
| Perceived Quality | How well a system is perceived to perform, with regard to job goals, impacts user acceptance |
| Perceived Enjoyment | A technology which is perceived as enjoyable to use is more likely to be adopted by users |
| Self-Efficacy | A user’s perception of their own ability to use a system will impact their acceptance of that system |
| Complexity | A technology which is perceived as difficult to use is less likely to be adopted |
| Relevance | Users are more likely to adopt technology they perceive as beneficial for their job performance |
| Image | Users are more likely to adopt technology which is perceived to improve their social status |
| Social Presence | A technology that allows users to experience the presence of others in a digital environment is more likely to be adopted |
| Result Demonstrability | If the impact of using a technology can be communicated to others and is observable, the user is more likely to adopt it |
| Voluntariness | Users are more positive towards a technology which is perceived as being voluntary and/or free to use |
| Innovativeness | Innovativeness increases a person’s willingness to test new technology |
| Trialability | The possibility of testing a technology increases the likelihood of it becoming adopted |
| Visibility | A technology which is more visible in the organisation is more likely to be adopted |
| Usability | A technology which can be objectively shown to be usable is more likely to be adopted |
| Playfulness | A technology which is perceived as fun to use is more likely to be adopted by users |
| Perception of External Control | A user’s perception of how well the organisation will support the use of a technology impacts the user’s acceptance of that technology |
| Experience | Prior experience of a technology or similar technologies will impact users’ acceptance |
| Relative Advantage | A technology which is perceived as better than similar technologies is more likely to be adopted |
| Paper | Directly Researched Factors | Indirectly Researched Factors |
|---|---|---|
| Shukla et al. [10] | Relevance, Experience, Management Support, Facilitating Conditions | |
| Abawajy [11] | Innovativeness | Usability |
| Mokwetli and Zuva [12] | Management Support, Relevance, Regulatory control | |
| Dang-Pham et al. [13] | Trust, Social Presence | |
| Alhalafi and Veeraraghavan [14] | Perceived Quality, Usability, Social Norms and Pressure, Facilitating Conditions, Accessibility | |
| Lui and Hui [15] | Self-efficacy | |
| Bryan Foltz et al. [16] | Attitude, Apathy, Social Norms | Complexity |
| Gadzama et al. [17] | Management Support | |
| Hart et al. [18] | Perceived Enjoyment, Relevance | |
| Ma et al. [19] | Perceived Quality, Social Norms, Perceived Enjoyment | |
| Rhee et al. [20] | Self-efficacy | |
| Potgeiter et al. [21] | Usability, Relevance | |
| Reeves et al. [22] | Experience, Perceived Quality, Social Norms, Perception of External Control | |
| Kävrestad et al. [23] | Facilitating Conditions, Relative Advantage, Worry | |
| Shillair [24] | Innovativeness, Relevance, Result Demonstrability | |
| Shen et al. [25] | Perceived Enjoyment | |
| Jin et al. [26] | Perceived Enjoyment | |
| Gokul et al. [27] | Perceived Enjoyment | |
| Talib et al. [28] | Perception of External Control | |
| Kajzer et al. [29] | Image, Social Presence, Attitude, Self-Efficacy | |
| Yasin et al. [30] | Perceived Enjoyment | |
| Aladawy et al. [31] | Perceived Enjoyment |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fallatah, W.; Kävrestad, J.; Furnell, S. Establishing a Model for the User Acceptance of Cybersecurity Training. Future Internet 2024, 16, 294. https://doi.org/10.3390/fi16080294
Fallatah W, Kävrestad J, Furnell S. Establishing a Model for the User Acceptance of Cybersecurity Training. Future Internet. 2024; 16(8):294. https://doi.org/10.3390/fi16080294
Chicago/Turabian StyleFallatah, Wesam, Joakim Kävrestad, and Steven Furnell. 2024. "Establishing a Model for the User Acceptance of Cybersecurity Training" Future Internet 16, no. 8: 294. https://doi.org/10.3390/fi16080294
APA StyleFallatah, W., Kävrestad, J., & Furnell, S. (2024). Establishing a Model for the User Acceptance of Cybersecurity Training. Future Internet, 16(8), 294. https://doi.org/10.3390/fi16080294