Abstract
This study focuses on trust within water-treatment IoT plants, examining the collaboration between IoT devices, control systems, and skilled personnel. The main aim is to assess the levels of trust between these different critical elements based on specific criteria and to emphasize that trust is neither bidirectional nor transitive. To this end, we have developed a synthetic database representing the critical elements in the system, taking into account characteristics such as accuracy, reliability, and experience. Using a mathematical model based on the (AHP), we calculated levels of trust between these critical elements, taking into account temporal dynamics and the non-bidirectional nature of trust. Our experiments included anomalous scenarios, such as sudden fluctuations in IoT device reliability and significant variations in staff experience. These variations were incorporated to assess the robustness of our approach. The trust levels obtained provide a detailed insight into the relationships between critical elements, enhancing our understanding of trust in the context of water-treatment plants.
1. Introduction
In the context of wastewater treatment plants, trust plays an essential role in guaranteeing the safety of the water supply, which is a fundamental priority. Failures or errors within these infrastructures have significant implications, going beyond mere technical malfunctions, as they can have serious consequences for both water quality and the availability of this vital resource [1].
In a collaborative environment within water-treatment plants, mutual trust between IoT devices, control systems (i.e., electronic and electromechanical components), and skilled personnel becomes pivotal to the operational chain. Maintaining a high level of trust between infrastructure components facilitates smooth coordination, helps to reduce the likelihood of mistakes, and enables rapid and effective response to incidents [2].
Measuring and understanding trust is of strategic importance and extends beyond mere technical performance monitoring. It involves quantifying and analyzing the reliability of human and automated interactions within the system. In this context, trust encompasses predictability, reliability of actions, transparency of communication, and the ability to anticipate the responses of various critical elements in exceptional circumstances.
Furthermore, it is imperative for IoT devices and control systems to also demonstrate their trust in human entities (i.e., qualified personnel). This can be achieved by ensuring transparent data communication, providing accurate insights into their operation, and allowing some form of interaction and control from qualified personnel to ensure effective decision-making and proper system management in complex situations. These devices can also be designed to alert qualified personnel of potential issues, therefore indicating trust in the personnel’s ability to intervene and resolve issues appropriately. Additionally, control systems can incorporate features enabling human operators to access detailed information about the status of IoT devices and electromechanical components, thus enhancing transparency and collaboration between human entities and automated systems.
By building trust within the operational ecosystem, water-treatment plants can mitigate the risk of human or technological failure. High levels of trust foster a culture of safety, where each element of the infrastructure depends on the others to function optimally. This translates into reduced risk of error and downtime, as well as a greater ability to anticipate and mitigate potential problems. Given their role as essential pillars of water safety, water-treatment plants demand unwavering operational integrity, where trust is a critical factor. Failures or errors in this context can have serious repercussions on the safety of the water supply.
This study aims to address the imperative need to measure, evaluate, and reinforce trust between various critical elements within water-treatment facilities. While previous research has explored the security of IoT systems in various sectors, one aspect of understanding trust within these facilities has often been overlooked. The limited research that has examined trust has primarily focused on security in the broadest sense, without specifically delving into the collaboration between IoT devices, control systems, and skilled personnel within water-treatment plants [3].
Furthermore, given the rapid evolution of IoT technology and the increasing demands on water management, there is an urgent need to investigate how trust can be maintained and assessed in dynamic environments. The complex interplay between critical elements within this kind of infrastructure requires in-depth examination to understand the emergence and evolution of trust over time [4], which our article aims to address, which our article aims to address by focusing on the key objective of measuring, evaluating, and enhancing trust within water-treatment facilities. By making explicit the dynamics of trust in these critical environments, we aim to provide valuable insights for improving operational integrity and mitigating water supply security risks.
This paper focuses on the critical role of trust in water-treatment plants, exploring how it can be measured, assessed, and enhanced to improve operational integrity and mitigate water supply security risks. The following sections of this paper are devoted to a comprehensive analysis of existing trust measurement frameworks, the identification of key factors influencing trust in water-treatment plants, and the objective method for calculating trust in such critical environments. Specifically, Section 2 provides an overview of related work in the field, highlighting existing research on trust measurement frameworks and their application in similar contexts. In Section 3, we outline our methodology and proposed approach for measuring and assessing trust within water-treatment facilities. Section 4 presents the results of our study and offers a discussion of key findings, including insights into the factors influencing trust dynamics in these environments. Finally, in Section 5, we conclude our analysis and propose recommendations for enhancing trust in water-treatment plants, emphasizing the importance of our findings for improving operational integrity and safeguarding water supply security.
2. Related Work
Understanding previous research and relevant developments provides crucial insights into the advancements, persistent challenges, and innovative solutions shaping the field of secure IoT systems for drinking-water distribution. This exploration forms the bedrock for our contextual understanding, guiding the formulation of new approaches and the resolution of outstanding issues. In this section, we delve into past research milestones, illuminating the groundwork for our contributions and emphasizing the significance of our proposed approach.
In the nascent stages of applying the Internet of Things (IoT) to water management, the emphasis was predominantly on establishing connectivity and facilitating data collection. Early implementations focused on creating networks capable of gathering information about various aspects of water resources. However, security considerations often took a backseat during this period, with primary attention directed towards functional system establishment rather than safeguarding against potential threats [5,6,7].
The escalating sophistication of cyber-attacks has catalyzed a paradigm shift in the architecture of IoT systems, particularly regarding security. Evolving security protocols now address the unique demands of industrial applications, including the management of drinking water. Protocols such as TLS/SSL have emerged as indispensable tools for securing communications across diverse IoT network components, therefore bolstering secure communication channels and ensuring data integrity [8,9].
Incidents targeting critical infrastructures, such as water-treatment facilities, have underscored the imperative to enhance security measures. Heightened awareness of potential threats to water quality and resource availability has spurred research efforts and the development of more resilient security mechanisms [10,11,12].
The establishment of standards and regulations tailored to IoT system security, particularly within critical sectors like water management, has played a pivotal role in shaping trust management frameworks. These standards, often formulated in response to identified vulnerabilities, offer guidelines for implementing standardized security practices [13,14].
In recent times, attention has shifted towards leveraging artificial intelligence (AI) to enhance IoT system security. Ongoing research explores AI’s potential to detect anomalies in data, preempt attacks, and bolster the resilience of water management systems. The integration of AI represents a strategic leap towards proactive security, empowering systems to respond effectively to emerging threats [15,16,17].
Moreover, recent advancements in utilizing artificial intelligence (AI) have shown promising outcomes in preventing malfunctions and failures in critical industrial equipment. For instance, research demonstrates the application of machine learning algorithms, including Support Vector Machine (SVM) and Multilayer Perceptron (MLP), for fault prediction in centrifugal pumps within the oil and gas industry [18].
Similarly, innovative approaches leveraging deep transfer learning techniques have been proposed for enhanced fault diagnosis of monoblock centrifugal pumps (MCP) [19].
Converting vibration signals into spectrogram images and utilizing pre-trained neural networks such as AlexNet offer efficient and precise solutions for fault detection and diagnosis in MCPs, therefore enhancing reliability and maintenance practices across various industrial settings. Furthermore, in water pump bearings, novel feature extraction and fault detection techniques utilizing extreme gradient boosting (XGB) classifiers have achieved notable success in reliably detecting and classifying minor bearing faults with high accuracy [20].
This signifies a significant advancement in the field, addressing the ongoing challenge of cost-effective fault detection in centrifugal water pumps and underlining the potential of AI-driven solutions in industrial equipment maintenance. These studies underscore the growing significance of AI-driven approaches in mitigating equipment malfunctions and failures, ultimately contributing to improved operational efficiency and reduced downtime in industrial and water management systems.
With mounting concerns about IoT system security, the integration of trust management mechanisms has become indispensable. However, it is disconcerting that certain critical industrial sectors, such as drinking-water management, have been overlooked in this endeavor [21].
In the examined previous works, a significant gap has been identified regarding the application of IoT system security principles to drinking-water management. This omission is particularly concerning given the unique characteristics of this domain and the critical stakes associated with the security of water distribution infrastructure.
Drinking-water management stands out for its direct impact on public health and safety, necessitating a specific approach to IoT system security. Unlike other industrial sectors, vulnerabilities in drinking-water distribution systems can have immediate and potentially disastrous consequences on the health and well-being of served populations. Therefore, safeguarding these systems must be an absolute priority, underscoring the importance of targeted research focused on IoT system security in this domain.
Furthermore, the complexity of drinking-water distribution networks, coupled with the sensitivity of the data and processes involved, requires tailored security approaches. IoT systems in this context must not only protect digital data but also ensure the reliability and integrity of the physical processes associated with water distribution. This dual requirement makes security challenges in this domain particularly intricate and deserving of specific attention from the research community.
The previous works have inadequately addressed the specificities of drinking-water management in the context of IoT system security. This gap underscores the urgent need for targeted research aimed at developing adapted and effective security approaches to protect critical water distribution infrastructure against cyber threats and security breaches.
To address this gap, we propose an innovative approach. By meticulously evaluating trust among critical elements, we aim to establish robust trust relationships, fostering secure collaboration between IoT devices, control systems, and qualified personnel. Our approach endeavors to mitigate risks by identifying trust levels, therefore providing a solid foundation for proactive threat management in IoT-based water-treatment plants. Through this endeavor, we aspire to fortify the security posture of critical infrastructure and enhance the resilience of water management systems.
In reviewing previous works, several trust modeling approaches for the Internet of Things (IoT) have been studied. The approach described in “A model-driven approach to ensure trust in the IoT” primarily focuses on trust modeling within the system development lifecycle (SDLC), which may limit its ability to effectively capture and mitigate real-time security risks, particularly in critical environments such as IoT-based water-treatment plants [22].
Similarly, other models, such as the one presented in “A conceptual trust model for the Internet of Things interactions,” suffer from limitations related to their generality and abstraction, making it difficult to adapt to the specific needs and security requirements of critical infrastructures like water-treatment plants [23].
Furthermore, approaches like the one described in “A dynamic trust model in the Internet of Things” may be limited by their reliance on historical data to predict trust, which can be ineffective in unforeseen situations or against sophisticated attacks [24].
Additionally, models such as the one presented in “Modeling trust dynamics in the Internet of Things” may lack consideration for the specific requirements and dynamics of critical infrastructures such as water-treatment plants, requiring deeper customization and integration to ensure adequate protection against potential threats [25].
As for the CTRUST approach, its limitations lie in its lack of precise modeling of trust degradation and weighted recommendations, as well as its rigidity in defining trust parameters. In comparison, our trust modeling approach for an IoT water-treatment plant acknowledges the dynamic and non-transitive nature of trust, offering a more suitable perspective by recognizing the specific complexity of trust relationships among critical infrastructure elements [26].
In the end, our approach addresses the limitations of existing trust modeling methods for IoT by introducing a dynamic model tailored for water-treatment plants. Unlike previous approaches, ours adapts in real time to evolving threats, leveraging machine learning for accurate risk assessment. By recognizing the nuanced nature of trust relationships, our model offers precise security allocation, enhancing resilience against cyber threats. Our proactive and context-aware approach ensures robust security for critical infrastructure.
3. Methods and Proposed Approach
In this section, we will explain how we establish effective trust management for IoT installations designed for drinking-water management. We will aim to answer the following important questions: Who trusts whom or what, and how can we measure levels of trust in this specific context? The next section will focus on presenting and discussing the results.
3.1. Data Collection
This subsection focuses on the crucial first step of our methodology: data collection. To establish effective trust management in IoT plants dedicated to drinking-water management, it is imperative to gather relevant information. We will explore the characteristics of the existing IoT system, identify the involved critical elements, and examine the history of past incidents. By bringing together these data, we will establish a solid foundation for modeling trust relationships and creating a robust trust management system. This step is essential for understanding the dynamics of the system and directing our efforts toward critical points that require specific monitoring.
3.1.1. Characteristics of the IoT System for Drinking-Water Treatment
To understand the implications of trust in drinking-water management environments, let us examine the water life cycle in a drinking-water production facility using the example of the Sherbrooke Drinking-Water Treatment Plant. This plant has received accolades for its water quality, winning the first prize in Quebec in 2017 and the second prize in North America [27]. The process of producing drinking-water comprises four essential steps:
- Pumping Stage: The pumping station is located at the edges of Lake Memphremagog, extracting water 150 m offshore and 15 m deep. Water is pumped to Sherbrooke through a 90 cm diameter pipeline over a distance of 27 km. Upon arrival, the water passes through five pumping wells equipped with five raw water pumps.
- Primary Micro-Screening Stage: Five small micro-screens eliminate particles of 300 microns (sand grains, small pieces of wood or plastic, etc.) to prevent them from reaching the subsequent treatment stages.
- Membrane Filtration Stage: This crucial step in the treatment process uses nine membrane trains to achieve a processing capacity of at least 96,000 m²/day. Each membrane train contains thousands of tubes, each with 7000 small tubules with a porosity of 0.02 microns, allowing water passage while excluding bacteria and viruses.
- Ozonation Stage: Ozone gas is produced from pure oxygen using ozonizers. This gas is injected into the filtered water basins to react with the water, producing oxygenated water. Ozonation improves water quality, destroys organic micro-pollutants, and neutralizes the odor, taste, and color of the water.
- Chlorination Stage: Although the water may be entirely potable at this stage, chlorine is added as a disinfectant at a concentration of at least 0.3 PPM to prevent potential bacterial growth in the aqueduct network.This complex process is managed by PLCs and monitored by IoT sensors throughout the treatment cycle. These devices contribute to the collection of essential data to ensure the quality of drinking water and are key components of the IoT system deployed in this plant. Trust in these devices and the overall system is crucial to guarantee the supply of safe and high-quality drinking water to the population of Sherbrooke [28].
3.1.2. Critical Elements and Trust Relationships
We will identify the critical elements involved in the system, thus defining the necessary trust relationships.
3.1.3. Critical Elements and Trust Relationships: Sources and Derivation
The critical elements and trust relationships outlined in Table 1 have been derived from a comprehensive analysis of the components and operations within the water-treatment plant. These results are based on a combination of industry standards, best practices, and expert knowledge in water-treatment systems.

Table 1.
Critical Elements and Trust Relationships in the Water-Treatment Plant.
Each critical element listed in the table, including the management team, human operators, IoT sensors, PLCs, technology suppliers, and regulatory authorities, plays a vital role in ensuring the functionality, safety, and regulatory compliance of the water-treatment plant.
The responsibilities attributed to each critical element have been determined through an assessment of their functions and roles within the system. For instance, the management team is responsible for overseeing the entire water-treatment process, while human operators are tasked with monitoring operations, intervening in emergencies, and conducting maintenance activities.
Similarly, the trust relationships associated with each critical element have been established based on their interdependencies and reliance on one another. For example, human operators trust the data provided by IoT sensors to make informed decisions and rely on the reliability of PLCs to control automated processes effectively.
Furthermore, the table reflects the trust that technology suppliers must inspire by providing reliable and secure equipment, as well as the need for regulatory authorities to maintain ongoing compliance with standards and regulations to ensure the safety and trustworthiness of the water-treatment process.
Table 1 serves as a concise summary of the critical elements involved in the water-treatment plant and the trust relationships that bind them together. It highlights the interconnectedness of various critical elements and emphasizes the importance of mutual trust in ensuring the efficient and safe operation of the facility.
By clearly delineating the responsibilities and trust relationships of each critical element, the table provides a valuable reference for critical elements involved in the management and operation of the water-treatment plant. It underscores the significance of transparency, reliability, and compliance in fostering trust among all parties involved.
Moreover, the inclusion of technology suppliers and regulatory authorities in the table acknowledges their crucial roles in supporting the functioning and oversight of the water-treatment plant. Their involvement underscores the broader context within which the plant operates and the need for collaboration among critical elements to achieve common goals.
Establishing relationships of trust between these critical elements is essential to ensure the safety and efficiency of the water-treatment process. This implies not only the reliability of the technologies deployed but also the transparency of processes and communications between the players in the system. Mutual trust helps ensure the continued supply of high-quality drinking water to the people. In this Figure 1, we can see a visual representation of the critical elements of the IoT drinking-water treatment plant. Each essential element, such as IoT sensors, PLCs, maintenance personnel, human operators, etc., is represented graphically, providing a clear overview of the plant structure and its key components.
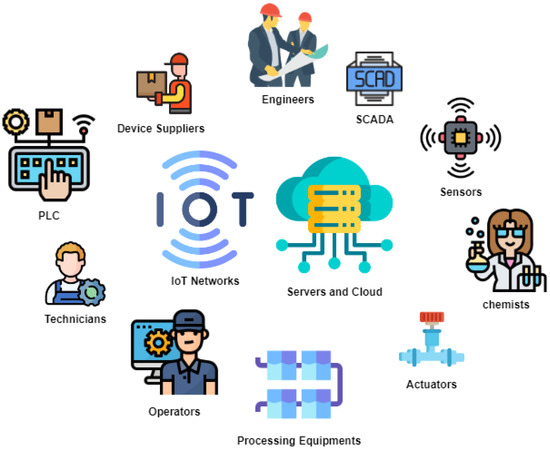
Figure 1.
Critical elements of the IoT drinking-water treatment plan.
3.1.4. Incident History and Responses
To assess the implications of trust in drinking-water treatment plants, it is essential to analyze the history of past incidents and the responses to them. This analysis will enable us to better understand critical situations, identify weak points in the system, and implement preventive measures. Table 2 shows examples of potential incidents that can happen in a water-treatment system and an expected response to the incident.

Table 2.
Examples of Incidents and Responses.
The selection of incidents showcased in Table 2 aims to offer a comprehensive representation of the various challenges that may arise in a water-treatment facility. These incidents span diverse categories of potential issues, encompassing hardware malfunctions, cyber threats, and concerns regarding water quality.
Each incident is meticulously described, outlining the specific nature of the problem alongside recommended response strategies. This comprehensive approach enables us to grasp effective methods for anticipating and addressing such scenarios, ultimately bolstering the reliability and safety of the entire water-treatment system.
By analyzing the history of incidents, we will assess previous responses to critical situations. This will help us to understand the aspects that influence trust and to identify elements that require special monitoring.
3.2. Proposed Approach
Our proposed approach begins by modeling trust relationships within the drinking-water management IoT system. We will define a conceptual framework describing the interactions between the various critical elements in the system, highlighting the elements that influence trust.
3.2.1. Trust Relationship Modeling
Modeling trust relationships in a water-treatment plant like Sherbrooke’s requires a mathematical approach to calculating trust levels. This approach takes into account the dynamic nature of trust, reflecting changes over time. In addition, it recognizes the non-bi-directional aspect, where trust can vary depending on the direction of the interaction, and the non-transitive aspect, acknowledging that trust is not necessarily transitive between all parties involved. This mathematical modeling thus offers a realistic and flexible representation of trust relationships in a drinking-water management environment.
Let us define some notations to formalize our model:
- Let N be the set of critical elements in the water-treatment station, including sensors, PLCs, operators, etc.
- Let be the trust variable between critical element i and critical element j, where represents the trust level of i in j.To calculate trust levels, we have employed an approach based on dynamic weights. The weights are used to model factors influencing trust.
- Each weight reflects the influence of a specific factor on the trust relationship between i and j.
3.2.2. Formalization of Trust Calculation
- m is the number of factors considered.
- is the value of factor k for the relationship between i and j. This factor is a specific characteristic influencing trust between these critical elements, chosen according to ISO 8000-61 standard to ensure an objective selection [29].
- is the weight associated with factor k for the relationship between i and j, calculated using the (AHP) method. AHP is a method that decomposes a complex problem into a hierarchy of criteria and sub-criteria and then evaluates and compares these elements quantitatively. We will describe it clearly in the next section. The goal is to assign values to different factors to enhance the objectivity of our approach [30]:
- Calculation of Weights: Let n be the number of criteria. We will compare each criterion with every other in terms of their relative importance. Comparisons are made on a scale, typically from 1 to 9, where 1 means “equivalent” and 9 means “extremely more important”. This matrix is symmetric.where is the measure of the relative importance between criteria i and j.
- Calculation of Relative Weights: Calculate the relative weights for each criterion by averaging the columns of the comparison matrix.where is the relative weight for factor i.
- Normalization of Relative Weights: Normalize the relative weights to obtain normalized weights. This ensures that the sum of all weights is equal to 1 (normalizing weights to 1 in AHP is a common practice to make results more consistent, interpretable, and comparable, facilitating the decision-making process).where is the normalized weight for criterion i.
- Calculation of Aggregated Weights: Aggregated weights are calculated by multiplying the normalized weights of the lower levels by the relative weights of the higher levels and summing these products for each criterion.where is the aggregated weight for criterion i.
This model provides flexibility in considering various factors influencing trust, and the weights allow for the adjustment of the impact of each factor. It is a general and objective representation that is adaptable to specific conditions of water-treatment stations, such as Sherbrooke’s, by integrating the unique characteristics of each critical element and relationship. The following subsection presents a formalization of trust calculation within the context of water-treatment plant management. This formalization relies on specifically chosen functions to address the unique needs of this crucial domain. Let us explore why these functions were selected and how they align with the dedicated purpose of water-treatment management.
First, the trust calculation equation was crafted with careful consideration given to its ability to integrate multiple factors influencing trust between critical elements within a water-treatment plant. This approach allows for a holistic and comprehensive analysis, taking into account various dimensions of the relationship between these elements.
As for the factors , their selection based on ISO 8000-61 ensures an objective foundation. This standard establishes rigorous criteria for choosing specific characteristics that influence trust. Thus, by adhering to this standard, the trust calculation model ensures adequate consideration of essential aspects of the relationship between critical elements.
Similarly, the weights associated with these factors are calculated using the Analytic Hierarchy Process (AHP) method. AHP was preferred for its ability to decompose a complex problem into a hierarchy of criteria and sub-criteria, therefore offering a systematic and structured approach to quantitatively evaluate and compare these elements. By employing AHP, we were able to assign weights to different factors rationally, taking into account their relative importance within the specific context of water-treatment management.
Furthermore, the normalization of weights ensures fair and consistent weighting, thus enhancing the objectivity and reliability of the model.
It is crucial to note that this model was specifically tailored to the unique conditions and requirements of water-treatment plants, such as those in Sherbrooke. By incorporating the special characteristics of each critical element and relationship, this model provides an accurate and personalized representation of trust within this critical context.
The choices of functions, methods, and particularly the integration of AHP, made for trust calculation, were carefully considered to ensure a robust, objective, and tailored approach to the specific needs of water-treatment management.
3.2.3. Monitoring Trust
Detecting trust levels in a drinking-water treatment plant involving IoT sensors, PLCs (programmable logic controllers), and personnel plays a crucial role in ensuring the plant’s safety and smooth operation. By monitoring the trust placed in each component, anomalies and potential risks can be quickly identified.
This detection ensures the reliability of the IoT sensors that measure various water parameters, the PLCs that control automated processes, and the personnel who interact with the systems. In the event of fluctuations or unusual behavior, the system can react in real time to minimize the risk of failure or compromise.
The impact of this confidence level detection can be seen in the prevention of critical failures, human error, and security breaches. By identifying early warning signals, the plant can take corrective action before an incident occurs. This helps to guarantee the quality of treated water and maintain continuity of operations.
On the security front, this approach enhances protection against cyber-attacks by monitoring unusual sensor and PLC behavior, helping to prevent intrusions. In addition, monitoring staff confidence levels can help identify potentially malicious or negligent actions.
4. Results and Discussion
In this section, we present the results of our experiments evaluating the effectiveness of the proposed approach for modeling trust relationships within the IoT system for drinking-water management.
4.1. Experiment
Experiments were carried out by simulating system operation over a given period, taking into account temporal variations in confidence levels and introducing generated scenarios such as sensor errors, PLC failures, and manual interventions by operators.
We generated a synthetic database with specific characteristics for each critical element, dynamic weights, and trust factors based on ISO standards. Using our mathematical model based on the (AHP), we calculated trust levels between critical elements [29].
The experiments also included abnormal scenarios to test the robustness of the approach, such as sudden fluctuations in PLC reliability and significant variations in operator experience.
4.1.1. Generation of Synthetic Database
In this section, we created a synthetic database representing critical elements in the IoT system for drinking-water management. Each critical element is characterized by several attributes, such as accuracy, reliability, and experience, influencing trust within the system. Here is an example of some entries from the generated database:
Each row in this Table 3 represents a critical element in the system, and the values in the columns describe specific characteristics of each critical element. Accuracy, reliability, and experience are measures that can vary from one critical element to another.

Table 3.
Performance Evaluation of System Components.
The “accuracy” of a critical element, such as a sensor or a PLC, can be defined as measuring the correctness of its measurements concerning a reference value. Let us imagine that each critical element is evaluated on its ability to provide accurate data. “Accuracy” can be calculated as the correlation between measured and actual values, with a higher score indicating greater precision.
The “reliability” of a critical element can be assessed in terms of its stability and consistency in transmitting data over time. For sensors or PLCs, this may involve the frequency of measurement errors or failures. Higher “reliability” means more stable and consistent performance.
An operator’s “experience” can be quantified by considering his or her work history, years of experience, and success in handling similar situations. An operator with more years of experience or who has successfully managed similar incidents may be awarded a higher experience score.
4.1.2. Calculation of Trust Levels
To assess trust levels between critical elements, we used a mathematical model based on the (AHP).
The (AHP) is a method used for multi-criteria decision-making that involves breaking down a complex decision problem into a hierarchical structure and assessing the relative importance of different criteria. In the context of trust level calculation, the AHP method is used to evaluate the trustworthiness of different critical elements based on factors such as accuracy, reliability, and experience. Here is a brief explanation of how the trust levels might be calculated using the AHP model:
- Step 1: Define the Hierarchy
We define the hierarchy of factors and sub-factors. In this example, the main factors are accuracy, reliability, and experience.
Level 1: Trust Evaluation factors
Level 2: Accuracy
Level 2: Reliability
Level 2: Experience
- Step 2: Pairwise Comparisons
We create pairwise comparison matrices for each level 2 factor. For example, for accuracy, reliability, and experience, see Table 4:

Table 4.
Pairwise Comparison Matrix for Accuracy (example values).
These values represent the relative importance of each factor compared to the others. The values are assigned based on expert judgment.
- Step 3: Calculate Weighted Sum
We calculate the weighted sum for each level 1 factor by multiplying the values in the comparison matrix by their respective weights.
Weighted Sum for Accuracy:
- Step 4: Normalize the Weights
We normalize the weighted sums to obtain the relative weights for each level 1 factor.
- Step 5: Calculate Trust Levels
Using the normalized weights, we calculate the trust levels for each critical element.
Example Calculation for Trust Level (Sensor1):
where:
represents the trust level of Sensor 1. NWA is the Normalized Weight for Accuracy. NWR is the Normalized Weight for Reliability. NWE is the Normalized Weight for Experience.
We repeat similar calculations for the other critical elements.
4.2. Discussion
In this section, we compare our proposed approach for modeling trust relationships in the IoT system for drinking-water management with existing works in the literature.
4.2.1. Flexibility of the Model
Our AHP-based model offers remarkable flexibility. By assigning dynamic weights to trust-influencing factors, we can adjust the impact of each characteristic according to the specific needs of the system. This flexibility allows easy adaptation to different conditions of water-treatment plants, reinforcing the relevance of our approach.
4.2.2. Consideration of Temporal Dynamics
The dynamic nature of trust, reflected by our model through the temporal variation of trust levels, is an innovative feature. Sudden fluctuations in PLC reliability and changes in operator experience introduced in our experiments demonstrate the model’s ability to capture the complex temporal aspects of trust relationships.
4.2.3. ISO-Objective Approach
The integration of ISO standards in the choice of trust factors gives our approach an objective character. Using criteria in line with ISO standards, we ensure an impartial evaluation of trust relationships, enhancing the credibility of our model [29].
We elaborated our criteria based on ISO 9001 [31], ISO 27001 [32], ISO 14001 [33], ISO 24511 [34], ISO 24512 [35], ISO 24521 [36], ISO 24516 [37], ISO 24517 [38], ISO 24523 [39], and ISO 24526 [40] standards, which are recognized references for quality, information security, environmental management systems, and water-treatment machines. These standards provide guidelines and specific requirements to ensure the quality, security, sustainability, and performance of systems and equipment.
Building on these standards, we identified relevant criteria to assess the quality of sensors, IoT devices, and drinking-water treatment machines. These criteria encompass aspects such as accuracy, reliability, information security, environmental impact, component performance, corrosion resistance, output pressure, and other essential characteristics.
The objectivity of our approach stems from these criteria being aligned with internationally recognized standards, establishing a transparent evaluation framework in line with universally accepted quality standards. This approach instills confidence in the evaluation process, providing users with assurance regarding the robustness and reliability of the results generated by our model.
It is important to note that our approach remains adaptable to changes in ISO standards and advances in specific fields. We are committed to keeping our methodology up-to-date by incorporating the latest standards and best practices, ensuring the ongoing relevance of our ISO-objective approach.
Table 5, Table 6, Table 7, Table 8 and Table 9 provide a succinct summary of criteria aligned with ISO standards across different domains. For Quality (ISO 9001), criteria cover measurement precision, reliability, and adherence to specifications for sensors and IoT devices. In Information Security (ISO 27001), the focus is on data protection and secure communications. Environmental considerations (ISO 14001) encompass the impact of materials, eco-friendly design, and regulatory compliance. Water-treatment machine criteria (ISO 24511-26) include factors like energy efficiency and maintenance frequency. The Personnel category (ISO 9001, ISO 45001, ISO 14001, ISO 50001) outlines leadership commitment, resource management, and process control criteria. This concise format facilitates a clear understanding of standards-compliant assessment criteria in each area.

Table 5.
Criteria for Quality (ISO 9001) [31].

Table 6.
Criteria for Information Security (ISO 27001) [32].

Table 7.
Criteria for Environment (ISO 14001) [33].

Table 8.
Criteria for Water-Treatment Machines (ISO 24511-26) [34,35,36,37,38,39,40].

Table 9.
Criteria for Personnel (ISO 9001, ISO 45001 [41], ISO 14001, ISO 50001 [42]).
4.2.4. Comparison with Existing Models in the Literature
In reviewing previous works, several trust modeling approaches for the Internet of Things (IoT) have been studied. The approach described in “A model-driven approach to ensure trust in the IoT” primarily focuses on trust modeling within the system development lifecycle (SDLC), which may limit its ability to effectively capture and mitigate real-time security risks, particularly in critical environments such as IoT-based water-treatment plants [25].
Similarly, other models, such as the one presented in “A conceptual trust model for the Internet of Things interactions”, suffer from limitations related to their generality and abstraction, making it difficult to adapt to the specific needs and security requirements of critical infrastructures like water-treatment plants [23].
Furthermore, approaches like the one described in “A dynamic trust model in the Internet of Things” may be limited by their reliance on historical data to predict trust, which can be ineffective in unforeseen situations or against sophisticated attacks [24].
Additionally, models such as the one presented in “Modeling trust dynamics in the Internet of Things” may lack consideration for the specific requirements and dynamics of critical infrastructures such as water-treatment plants, requiring deeper customization and integration to ensure adequate protection against potential threats [25].
As for the CTRUST approach, its limitations lie in its lack of precise modeling of trust degradation and weighted recommendations, as well as its rigidity in defining trust parameters. In comparison, our trust modeling approach for an IoT water-treatment plant acknowledges the dynamic and non-transitive nature of trust, offering a more suitable perspective by recognizing the specific complexity of trust relationships among critical infrastructure elements [28].
Our comparison between existing models and our approach revolves around four key aspects. First, flexibility holds paramount importance in the domain of drinking-water treatment, where conditions within treatment plants can vary significantly. The ability to adapt is crucial for dynamically adjusting trust factors and weights to suit the diverse conditions encountered. Similarly, temporal dynamics play a pivotal role as trust relationships undergo evolution over time due to various factors. Incorporating these temporal variations facilitates improved adaptation and more effective management of water-treatment systems. See Table 10.

Table 10.
Comparison with Existing Models.
Additionally, adherence to ISO standards is imperative to ensure objectivity and transparency in the evaluation of trust models. In the water-treatment field, where quality and safety are top priorities, aligning models with recognized standards helps alleviate potential biases and establishes consistent and dependable evaluation criteria.
Finally, model robustness is indispensable in an environment where unexpected scenarios and abrupt changes can arise. Water-treatment plants must maintain operation even in abnormal situations. Therefore, the model’s capacity to withstand such exceptional conditions ensures its reliability and practicality in real-world applications. In summary, these four aspects—flexibility, temporal dynamics, alignment with ISO standards, and robustness—constitute essential pillars for tackling the complex challenges of water-treatment management, validating their central role in the proposed approach.
In the end, our approach addresses the limitations of existing trust modeling methods for IoT by introducing a dynamic model tailored for water-treatment plants. Unlike previous approaches, ours adapts in real time to evolving threats, leveraging machine learning for accurate risk assessment. By recognizing the nuanced nature of trust relationships, our model offers precise security allocation, enhancing resilience against cyber threats. Overall, our approach provides a proactive and context-aware solution, ensuring robust security for critical infrastructure.
4.3. Limitations and Future Works
Despite the successes of our approach, certain limitations must be acknowledged. First, the modeling of trust relationships relies on dynamic weights determined by the (AHP). While this method is robust, the accuracy of the results depends on the relevance of the comparisons made when defining the weight matrices. Second, our model assumes a non-transitive trust relationship among all involved parties. In some situations, transitive trust relationships might be observed, requiring adaptation of our model to reflect this variability.
Future work could be considered to address these limitations. Improving the accuracy of the model might involve exploring alternative methods for determining weights while maintaining the objectivity of the approach. Machine learning techniques could be integrated to dynamically adjust weights based on system evolutions over time. Furthermore, exploring more complex scenarios and validating the model on real-world data would contribute to consolidating its robustness and practical applicability. Finally, a potential extension of this research would be the integration of additional security mechanisms, such as real-time anomaly detection and secure communication protocols, to enhance the system’s resilience against potential threats.
5. Conclusions
In the context of IoT facilities dedicated to drinking-water management, trust equates to the assurance of reliability, availability, and integrity of systems and data. This trust is crucial to ensure the uninterrupted operation of processes, guarantee the quality of distributed water, and maintain the security of sensitive data.
However, establishing this trust in critical infrastructures poses specific challenges. These include the need to prevent potential cyber threats targeting IoT systems, manage data integrity from multiple sensors, and ensure continuous system availability to avoid any impact on water distribution. Trust in these environments, therefore, demands a proactive approach to address these unique challenges and ensure the security, performance, and compliance with stringent standards of these essential facilities.
In conclusion, our work has resulted in an innovative approach to model trust relationships within IoT systems for drinking-water management. By implementing a mathematical model based on the (AHP), we successfully captured the dynamic complexity of trust, considering factors such as precision, reliability, and the experience of system critical elements.
The experiments carried out, based on the scenarios generated, demonstrated the effectiveness of our approach while also revealing certain limitations. The results highlighted the model’s ability to respond to abnormal situations and maintain adaptive confidence levels.
Author Contributions
Conceptualization, A.A.; Methodology, A.A.; Software, A.A.; Writing—original draft, A.A.; Supervision, P.-M.T. and M.E. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available due to privacy or ethical restrictions.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| AHP | Analytic Hierarchy Process |
| ISO | International Standards Organization |
| PLC | Programmable Logic Controller |
| PPM | Parts per million |
| TLS | Transport Layer Security |
| SSL | Secure Sockets Layer |
References
- Brouwer, S.; Hofman-Caris, R.; Van Aalderen, N. Trust in drinking water quality: Understanding the role of risk perception and transparency. Water 2020, 12, 2608. [Google Scholar] [CrossRef]
- Zhen, N.; Barnett, J.; Webber, M. Is Trust Always a Precondition for Effective Water Resource Management? Water Resour. Manag. 2020, 34, 1423–1436. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- Corritore, C.L.; Kracher, B.; Wiedenbeck, S. On-line trust: Concepts, evolving themes, a model. Int. J. Hum.-Comput. Stud. 2003, 58, 737–758. [Google Scholar] [CrossRef]
- Xiaocong, M.; Jiao, Q.X.; Shaohong, S. An IoT-based system for water resources monitoring and management. In Proceedings of the 2015 7th International Conference on Intelligent Human-Machine Systems and Cybernetics, Hangzhou, China, 26–27 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 365–368. [Google Scholar]
- Liu, H. Agricultural water management based on the Internet of Things and data analysis. Acta Agric. Scand. Sect. B—Soil Plant Sci. 2022, 72, 300–311. [Google Scholar]
- Hawari, H.F.B.; Mokhtar, M.N.S.B.; Sarang, S. Development of Real-Time Internet of Things (IoT) Based Water Quality Monitoring System. In Proceedings of the International Conference on Artificial Intelligence for Smart Community, AISC 2020, Universiti Teknologi Petronas, Seri Iskandar, Malaysia, 17–18 December 2020; Springer Nature: Singapore, 2022; pp. 443–454. [Google Scholar]
- Jaloudi, S. Communication protocols of an industrial internet of things environment: A comparative study. Future Internet 2019, 11, 66. [Google Scholar] [CrossRef]
- Wang, C.; Daneshmand, M.; Dohler, M.; Mao, X.; Hu, R.Q.; Wang, H. Guest Editorial-Special issue on internet of things (IoT): Architecture, protocols and services. IEEE Sens. J. 2013, 13, 3505–3510. [Google Scholar] [CrossRef]
- Jiang, X.; Lora, M.; Chattopadhyay, S. An experimental analysis of security vulnerabilities in industrial IoT devices. ACM Trans. Internet Technol. TOIT 2020, 20, 1–24. [Google Scholar] [CrossRef]
- Antrobus, R.; Green, B.; Frey, S.; Rashid, A. The Forgotten I in IIoT: A Vulnerability Scanner for Industrial Internet of Things. In Proceedings of the Living in the Internet of Things (IoT 2019), London, UK, 1–2 May 2019. [Google Scholar]
- Mourtzis, D.; Angelopoulos, K.; Zogopoulos, V. Mapping vulnerabilities in the industrial internet of things landscape. Procedia CIRP 2019, 84, 265–270. [Google Scholar] [CrossRef]
- Karie, N.M.; Sahri, N.M.; Yang, W.; Valli, C.; Kebande, V.R. A review of security standards and frameworks for IoT-based smart environments. IEEE Access 2021, 9, 121975–121995. [Google Scholar] [CrossRef]
- Lee, E.; Seo, Y.-D.; Oh, S.-R.; Kim, Y.G. A Survey on Standards for Interoperability and Security in the Internet of Things. IEEE Commun. Surv. Tuts. 2021, 23, 1020–1047. [Google Scholar] [CrossRef]
- Selvarajan, S.; Srivastava, G.; Khadidos, A.O.; Baza, M.; Alshehri, A.; Lin, J.C.W. An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J. Cloud Comput. 2023, 12, 38. [Google Scholar] [CrossRef] [PubMed]
- Karimipour, H.; Derakhshan, F. Artificial Intelligence for Threat Detection and Analysis in Industrial IoT: Applications and Challenges. In AI-Enabled Threat Detection and Security Analysis for Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 1–6. [Google Scholar]
- Kim, J.; Park, J.; Lee, J.-H. Analysis of Recent IIoT Security Technology Trends in a Smart Factory Environment. In Proceedings of the 2023 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Bali, Indonesia, 20–23 February 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 840–845. [Google Scholar]
- Orrù, P.F.; Zoccheddu, A.; Sassu, L.; Mattia, C.; Cozza, R.; Arena, S. Machine learning approach using MLP and SVM algorithms for the fault prediction of a centrifugal pump in the oil and gas industry. Sustainability 2020, 12, 4776. [Google Scholar] [CrossRef]
- Irfan, M.; Alwadie, A.S.; Glowacz, A.; Awais, M.; Rahman, S.; Khan, M.K.A.; Jalalah, M.; Alshorman, O.; Caesarendra, W. A novel feature extraction and fault detection technique for the intelligent fault identification of water pump bearings. Sensors 2021, 21, 4225. [Google Scholar] [CrossRef] [PubMed]
- Chennai Viswanathan, P.; Venkatesh, S.N.; Dhanasekaran, S.; Mahanta, T.K.; Sugumaran, V.; Lakshmaiya, N.; Paramasivam, P.; Nanjagoundenpalayam Ramasamy, S. Deep learning for enhanced fault diagnosis of monoblock centrifugal pumps: Spectrogram-based analysis. Machines 2023, 11, 874. [Google Scholar] [CrossRef]
- Boudagdigue, C.; Benslimane, A.; Kobbane, A.; Liu, J. Trust management in industrial Internet of Things. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3667–3682. [Google Scholar] [CrossRef]
- Ferraris, D.; Fernandez-Gago, C.; Lopez, J. A Model-Driven Approach to Ensure Trust in the IoT. Hum. Cent. Comput. Inf. Sci. 2020, 10, 50. [Google Scholar] [CrossRef]
- Arabsorkhi, A.; Sayad Haghighi, M.; Ghorbanloo, R. A Conceptual Trust Model for the Internet of Things Interactions. In Proceedings of the 8th International Symposium on Telecommunications (IST), Tehran, Iran, 27–28 September 2016; pp. 89–93. [Google Scholar] [CrossRef]
- Wang, E.K.; Chen, C.M.; Zhao, D.; Ip, W.H.; Yung, K.L. A Dynamic Trust Model in Internet of Things. Soft Comput. 2020, 24, 5773–5782. [Google Scholar] [CrossRef]
- Fernandez-Gago, C.; Moyano, F.; Lopez, J. Modelling Trust Dynamics in the Internet of Things. Inf. Sci. 2017, 396, 72–82. [Google Scholar] [CrossRef]
- Adewuyi, A.A.; Cheng, H.; Shi, Q.; Cao, J.; MacDermott, Á.; Wang, X. CTRUST: A Dynamic Trust Model for Collaborative Applications in the Internet of Things. IEEE Internet Things J. 2019, 6, 5432–5445. [Google Scholar] [CrossRef]
- Bourgouin, F. Mot du CA. Available online: https://lavalnews.ca/laval-wins-the-jurys-prize-for-the-best-water-in-quebec-and-renews-its-5-stars/ (accessed on 17 March 2024).
- Gauthier, Y. L’adaptation aux Changements Climatiques au Niveau Municipal: Des Inspirations Internationales aux Aspirations Québécoises. Master’s Thesis, Université de Sherbrooke, Sherbrooke, QC, Canada, 2016. [Google Scholar]
- Perez-Castillo, R.; Carretero, A.G.; Caballero, I.; Rodriguez, M.; Piattini, M.; Mate, A.; Kim, S.; Lee, D. DAQUA-MASS: An ISO 8000-61 based data quality management methodology for sensor data. Sensors 2018, 18, 3105. [Google Scholar] [CrossRef] [PubMed]
- de FSM Russo, R.; Camanho, R. Criteria in AHP: A systematic review of literature. Procedia Comput. Sci. 2015, 55, 1123–1132. [Google Scholar] [CrossRef]
- ISO 9001:2010; What Does it Mean in the Supply Chain? International Organization for Standardization: Geneva, Switzerland, 2010. Available online: https://www.iso.org/files/live/sites/isoorg/files/store/en/PUB100304.pdf (accessed on 17 March 2024).
- ISO/IEC 27001:2013; Information Technology—Security Techniques—Information Security Management Systems—Requirements. International Organization for Standardization: Geneva, Switzerland, 2013. Available online: https://www.iso.org/standard/27001 (accessed on 17 March 2024).
- ISO 14001:2015; Introduction to ISO 14001: Understanding the Environmental Management System Standard. International Organization for Standardization: Geneva, Switzerland, 2015. Available online: https://www.iso.org/files/live/sites/isoorg/files/archive/pdf/fr/introduction_to_iso_14001_fr_ld.pdf (accessed on 17 March 2024).
- ISO 24511:2007; Activities Relating to Drinking Water and Wastewater Services—Guidelines for the Management of Wastewater Utilities and for the Assessment of Wastewater Services. 2007. Available online: https://cdn.standards.iteh.ai/samples/37247/6fb47acbde0248b4aa4f81b1bc79eb3e/ISO-24511-2007.pdf (accessed on 17 March 2024).
- ISO 24512:2024; Activities Relating to Drinking Water and Wastewater Services—Guidelines for the Management of Drinking Water Utilities and for the Assessment of Drinking Water Service. 2024. Available online: https://cdn.standards.iteh.ai/samples/82490/766edc7f032d40079d78ada799ad7294/ISO-24512-2024.pdf (accessed on 17 March 2024).
- ISO 24521:2016; Activities Relating to Drinking Water and Wastewater Services—Guidelines for the Management of Basic on-Site Domestic Wastewater Services. 2016. Available online: https://www.iso.org/standard/64679.html (accessed on 17 March 2024).
- ISO 24516:2016; Guidelines for the Management of Assets of Water Supply and Wastewater Systems. 2016. Available online: https://www.iso.org/standard/64117.html (accessed on 17 March 2024).
- ISO 24517:2008; Document Management—Engineering Document Format Using PDF. 2008. Available online: https://www.iso.org/standard/42274.html (accessed on 17 March 2024).
- ISO 24523:2008; Service Activities Relating to Drinking Water Supply Systems and Wastewater Systems—Guidelines for Benchmarking of Water Utilities. 2017. Available online: https://www.iso.org/standard/59814.html (accessed on 17 March 2024).
- ISO 24523:2018; Water Efficiency Management Systems—Requirements with Guidance for Use. 2018. Available online: https://www.iso.org/obp/ui#iso:std:iso:24526:dis:ed-1:v1:en (accessed on 17 March 2024).
- ISO 45001:2018; Occupational Health and Safety Management Systems—Requirements with Guidance for Use. 2018. Available online: https://www.iso.org/standard/63787.html (accessed on 17 March 2024).
- ISO 50001:2018; Energy Management. 2018. Available online: https://www.iso.org/iso-50001-energy-management.html (accessed on 17 March 2024).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).