Software-Defined Named Data Networking in Literature: A Review
Abstract
1. Introduction
2. Related Work
3. Overview and Background
3.1. Named Data Networking
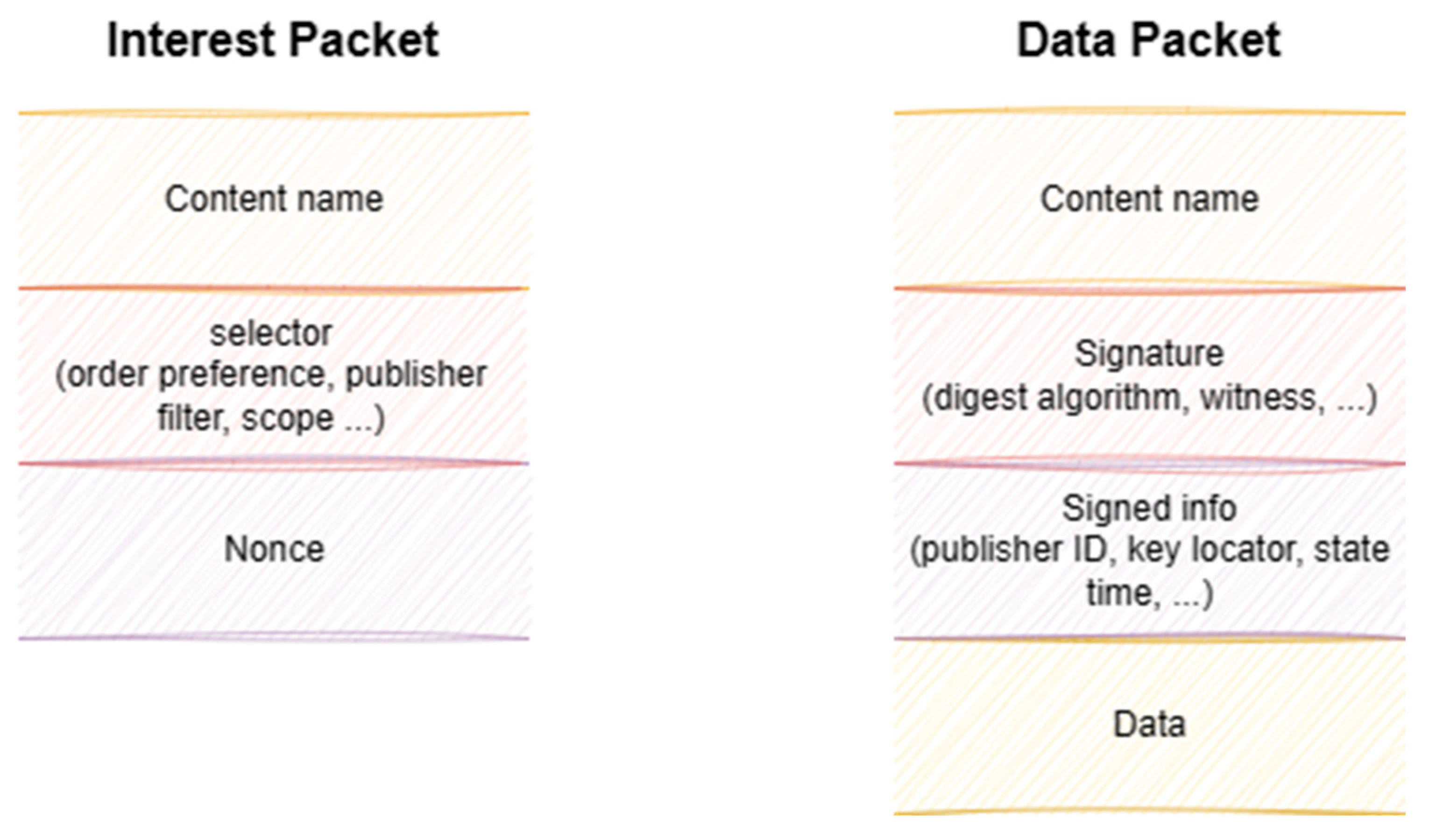
- Packet: A packet refers to a named data object (NDO) that exceeds the network’s maximum transmission unit (MTU) in size. When an NDO is broken down at the data link layer, these smaller pieces are known as frames. NDN typically processes two kinds of packets: interest and data (Figure 2).
- o
- An interest packet signifies a request for specific data. When a consumer requires certain information, it dispatches an interest packet into the network to find the desired content.
- o
- In contrast, a data packet carries the actual content being transmitted. It answers the requests initiated by interest packets, delivering the requested data to consumers.
- Consumer: A consumer is an entity capable of generating names and requesting data through interest packets.
- Producer: A producer is an entity that produces data packets to meet consumer requests.
- NDN node: An NDN node can function as a consumer, producer, or forwarder of cached content.
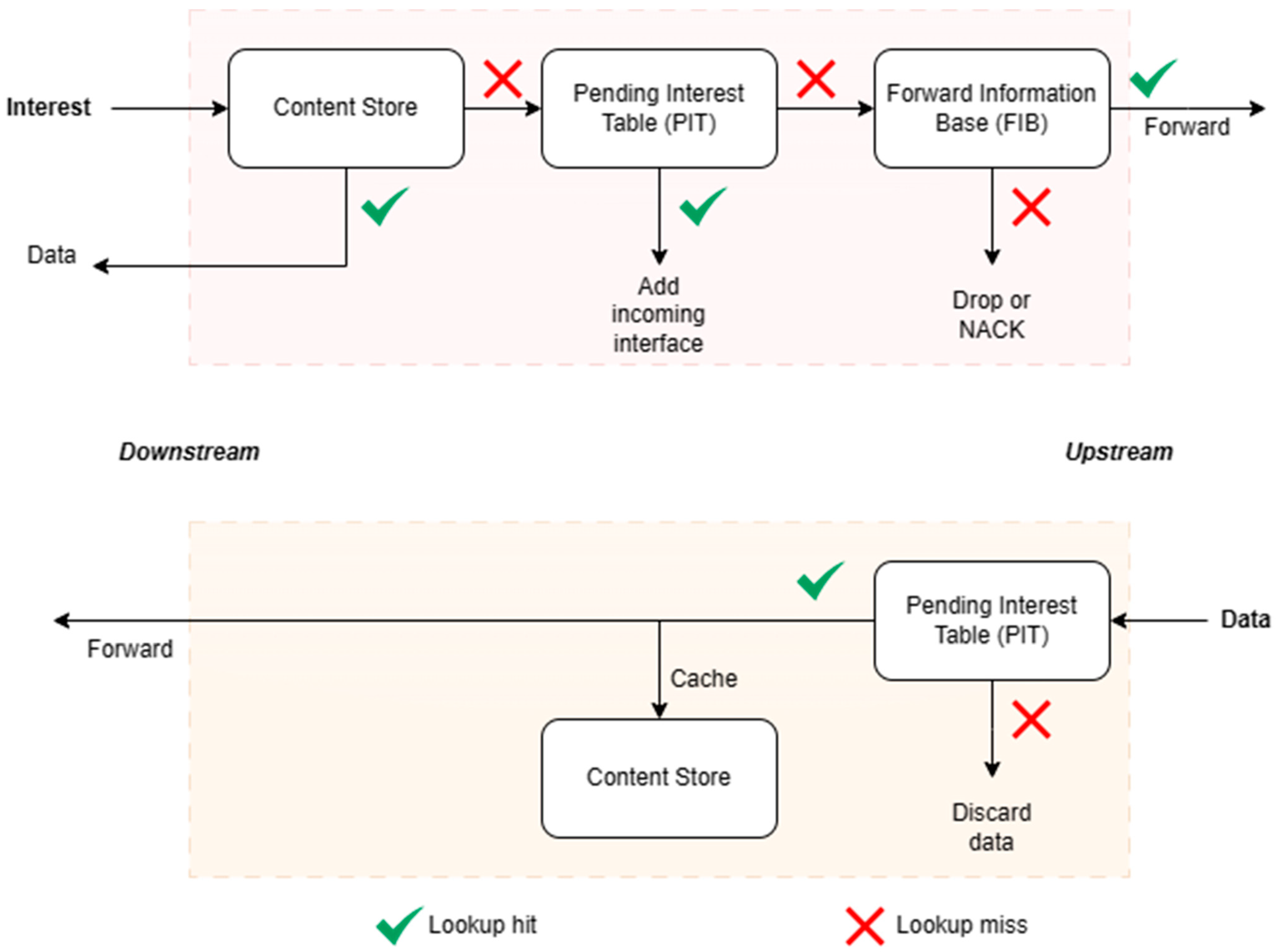
- Forwarding plane: The forwarding plane of NDN is composed of three data structures: CS, PIT, and FIB. The forwarding plane utilizes these structures to forward data using specific forwarding strategies as shown in Figure 3.
- NDN routers: NDN routers are devices that perform fundamental routing and forwarding operations. They contain CS, PIT, and FIB. They can cache content in their CS to fulfill future requests for the same content. Additionally, they forward data according to their forwarding tables. However, they are not to be mistaken for content providers.
- Routing plane: The routing plane refers to a collection of NDN protocols used to share information about the accessibility of a namespace. Whereas the routing plane calculates and decides globally on routes’ availability, the forwarding plane makes per-node decisions about the preference and use of these routes based on their performance and status. In other words, the routing plane finds and calculates the costs of routes toward the requested content and provides them to the forwarding plane.
- Data/content names: Data/content names are unique, human-readable strings usually generated by applications and act as identifiers for NDOs.
3.1.1. NDN Naming
3.1.2. NDN Routing
3.1.3. NLSR
- Routers periodically send out a root advise interest that contains the hash value of its LSDB to their neighbors to check if their databases match. The neighboring routers reply only when they detect any differences.
- When Router A’s NLSR creates a new LSA, it writes the LSA in the CCNx repository (REPO), which changes Router A’s LSDB hash value.
- Router A then detects the difference from Router B’s LSDB hash value and replays the root advise interest sent in Step 1.
- The routers continue exchanging hash values at the next tree level until they find the exact data causing the mismatch. After that, Router B sends a content interest packet to retrieve the data.
- Router A then sends the requested data (LSA) to Router B.
- Once Router B’s REPO receives the data (LSA), it sends a notification to its local NLSR with the data name.
- Following that, Router B’s NLSR requests the LSA from the REPO.
- Subsequently, Router B’s REPO replies with the LSA.
- Lastly, Router B’s NLSR updates its LSDB with the new LSA.
3.1.4. NDN Forwarding
- Forwarding strategies: Select the appropriate interface to forward interest packets. An example of such a strategy is the NDN basic forwarding strategy, which forwards the interest packet to all matching context prefix interfaces (except the interest incoming interface). Different forwarding strategies can be found in [21,22,23,24,25].
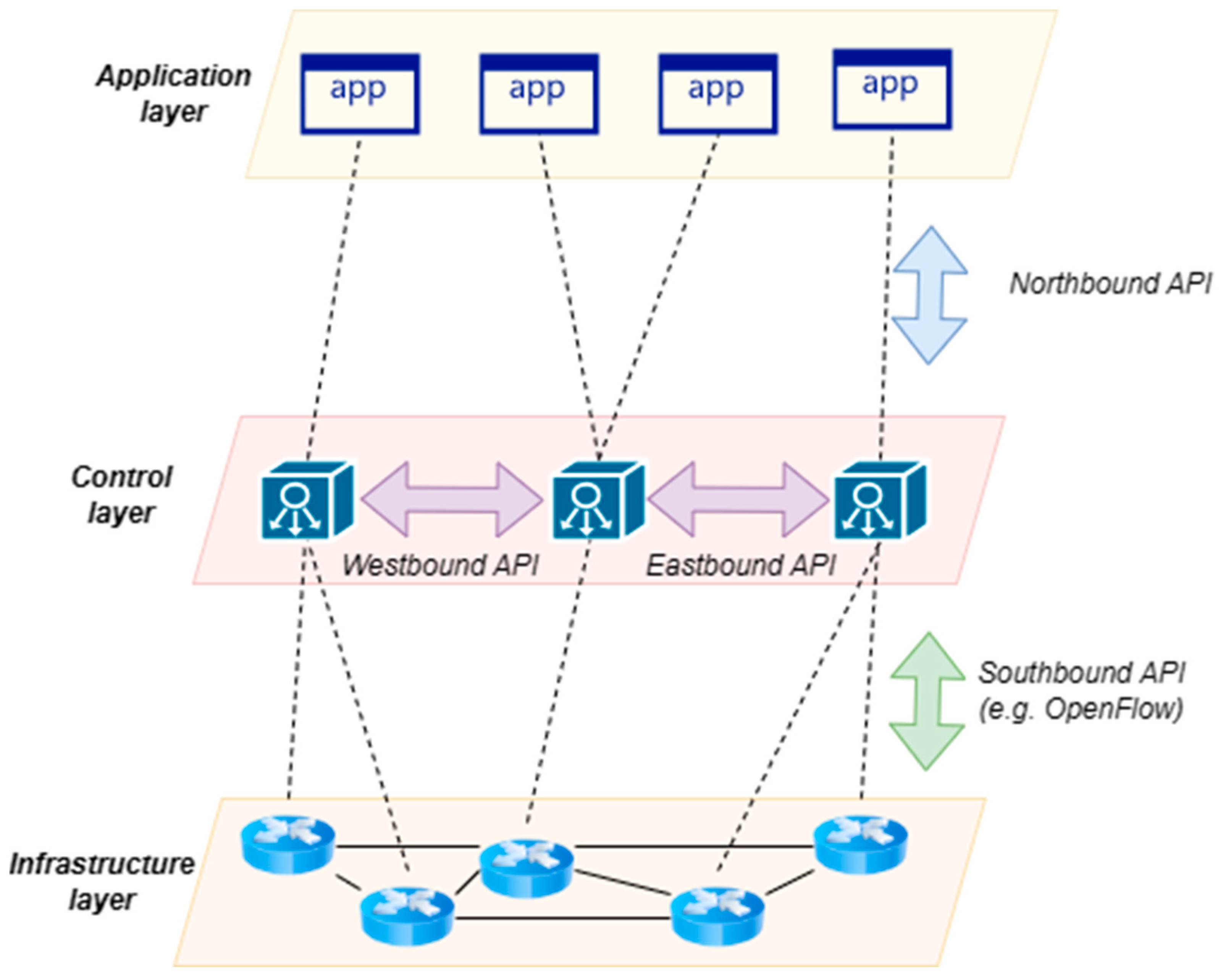
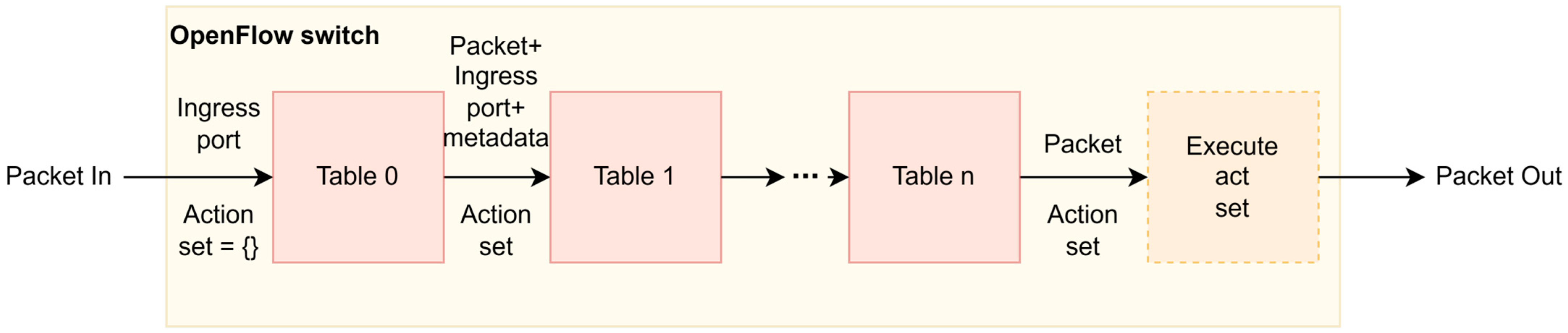
3.2. Software-Defined Networking
4. Literature Review
5. Discussion
- Existing SDN controllers and southbound APIs are not compatible with the NDN framework. As a result, most of the models in Table 2 had to have their own SDN-like controller software developed, and these may lack some features that known SDN controllers possess.
- Alternatively, if existing SDN controllers, such as Floodlight, are to be used, one must consider the fundamental differences in the protocol stacks between SDN and NDN. SDN uses the IP stack to carry packets, while NDN eliminates the IP stack and relies solely on content names. Implementing a model that integrates both NDN and SDN requires modifications to either the SDN or NDN protocol stack. Two examples of changes that can merge existing SDN controllers with NDN include the following:
- o
- Encapsulating SDN packets in NDN packets or vice versa, and
- o
- Adding an additional layer to the SDN or NDN protocol stacks.
- In [46], the authors encapsulated NDN packets in SDN packets by employing OpenFlow switches. These switches acted as a proxy between the SDN controller and NDN nodes, transforming NDN packets into SDN packets that could be processed by an SDN controller.
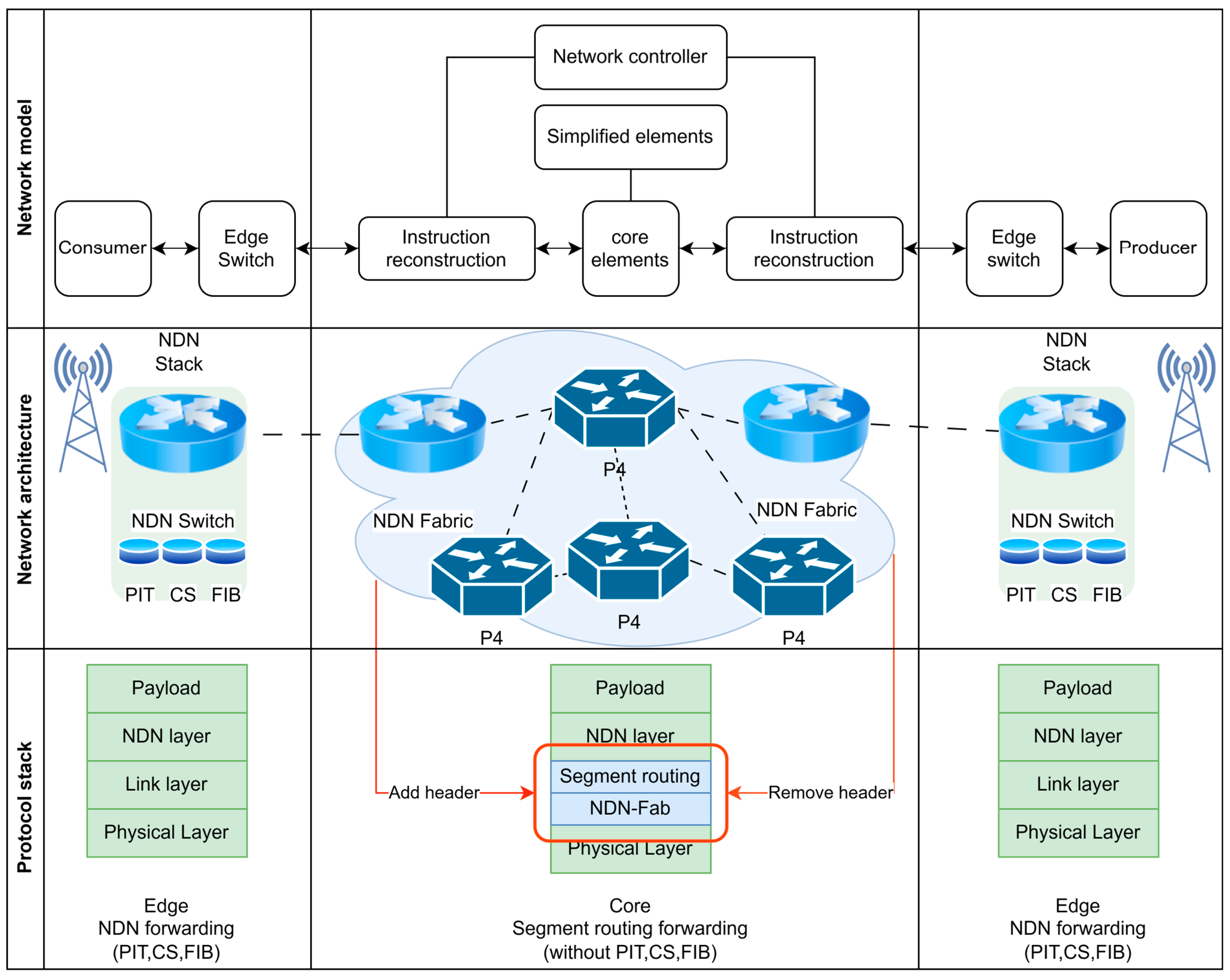
- In contrast, reference [54] aimed to preserve the characteristics of both SDN and NDN. This was accomplished by adding additional layers to the NDN stack for use by SDN controllers, as illustrated in Figure 8. This allowed SDN controllers and switches to communicate with each other using the IP stack, while NDN nodes communicated using the NDN stack.
- When designing an SD-NDN model, one should consider the memory overhead of storing global data prefix tables in SDN controllers, as this consumes storage and increases table lookup time, leading to increased data retrieval times.
- Similar to the above point, controller scalability should be considered when designing an SD-NDN model, as controllers have limitations in the number of inquiries they can handle. A critical consideration is determining how many requests and routers a single controller can effectively manage. In [21], an approach was taken to prevent overwhelming the controller by allowing routers to drop interest packets not found in their FIB, rather than forwarding every unmatched interest to the controller. Additionally, in [24] and [17], an interest is sent to the controller only once, and the controller responds with the end-to-end forwarding path. This path is then forwarded, along with the interest, to the next hop by the router nodes. This contrasts with [27], where the controller is responsible for sending forwarding updates to all routers in the route of interest.
- A viable solution should be adaptable to dynamic topologies, especially in the context of mobility. In [28], controller discovery involved a node flooding the network to find a controller, accommodating node mobility. Conversely, [24] employed a strategy in which a controller floods the network to announce its presence, allowing nodes to bind with the controller. The former supports node mobility, while the latter supports controller mobility. However, it seems more practical to prioritize support for node mobility over controller mobility, given that controllers are less likely to change their locations.
- One of the factors that affect the performance of SD-NDN models is the request processing time and route discovery algorithms of the SDN controller. Most of the aforementioned solutions rely on the Dijkstra algorithm. However, it is important to evaluate the processing time and efficiency of different route discovery algorithms and to choose the best one for SD–NDN models. In addition, one may consider using AI algorithms and machine learning to improve performance.
- NDN routers periodically send root advise interest that contains the hash tree values of their LSDB to their corresponding controller. The controller will reply only when it detects differences between the hash value it has and the received hash value, indicating that there is an update on the network state.
- Once a deference between the hash values is detected by controller A, the controller sends a root advise reply that contains a hash value of data at the next tree level to router A. The router and controller then keep exchanging hash values at the next tree level until they find the data that are causing the mismatch.
- After detecting the data (LSA) that are causing the mismatch, controller A sends an interest packet to request the data (LSA).
- Router A replies with a data packet containing the LSA.
- Controllers periodically exchange root advise interest that contains the hash tree values of their LSDB. A reply to this interest will be sent only when controllers detect a mismatch between the hash values, indicating that there has been an update on the network state.
- Similar to Step 2, once a mismatch is detected between the controllers’ hash values, the controllers keep exchanging a root advise reply that contains a hash value of data at the next tree level until they find the data that are causing the problem.
- After detecting the data (LSA), controller B sends an interest packet requesting the LSA.
- Controller A replies with a data packet containing the requested LSA.
- Controller B then sends a synchronization notification to all its connected routers.
- Router B sends a data interest to request the LSA.
- Controller B replies with the data.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sinha, S. Number of Connected IoT Devices Growing 16% to 16.7 Billion Globally. IoT Analytics. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 17 May 2024).
- Al-Karaki, J.N.; Kamal, A.E. Routing techniques in wireless sensor networks: A survey. IEEE Wirel. Commun. 2004, 11, 6–28. [Google Scholar] [CrossRef]
- Ahlgren, B.; Dannewitz, C.; Imbrenda, C.; Kutscher, D.; Ohlman, B. A survey of information-centric networking. IEEE Commun. Mag. 2012, 50, 26–36. [Google Scholar] [CrossRef]
- Singh, V.P.; Ujjwal, R.L. A walkthrough of name data networking: Architecture, functionalities, operations and open issues. Sustain. Comput. Inform. Syst. 2020, 28, 100419. [Google Scholar] [CrossRef]
- Aboodi, A.; Wan, T.C.; Sodhy, G.C. Survey on the Incorporation of NDN/CCN in IoT. IEEE Access 2019, 7, 71827–71858. [Google Scholar] [CrossRef]
- Rafique, W.; Hafid, A.S.; Cherkaoui, S. Complementing IoT Services Using Software-Defined Information Centric Networks: A Comprehensive Survey. IEEE Internet Things J. 2022, 9, 23545–23569. [Google Scholar] [CrossRef]
- Aldaoud, M.; Al-Abri, D.; Awadalla, M.; Kausar, F. Leveraging ICN and SDN for Future Internet Architecture: A Survey. Electronics 2023, 12, 1723. [Google Scholar] [CrossRef]
- Rowshanrad, S.; Parsaei, M.R.; Keshtgari, M. Implementing NDN using SDN: A review of methods and applications. IUM Eng. J. 2016, 17, 11–20. [Google Scholar] [CrossRef]
- Bannour, F.; Souihi, S.; Mellouk, A. Distributed SDN Control: Survey, Taxonomy, and Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 333–354. [Google Scholar] [CrossRef]
- Majed, A.; Wang, X.; Yi, B. Name Lookup in Named Data Networking: A Review. Information 2019, 10, 85. [Google Scholar] [CrossRef]
- Tariq, A.; Rehman, R.A.; Kim, B.-S. Forwarding Strategies in NDN-Based Wireless Networks: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 68–95. [Google Scholar] [CrossRef]
- Nurhayati, A.; Mayasari, R.; Ahdan, S.; Negara, R.M.; Nurkahfi, G.N.; Syambas, N.R. Naming Scheme on Named Data Networking: A Survey. In Proceedings of the 2022 8th International Conference on Wireless and Telematics (ICWT), Yogyakarta, Indonesia, 21–22 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–5. [Google Scholar] [CrossRef]
- da Silva, E.T.; Costa, A.L.D.; de Macedo, J.M.H. On the realization of VANET using named data networking: On improvement of VANET using NDN-based routing, caching, and security. Int. J. Commun. Syst. 2022, 35, e5348. [Google Scholar] [CrossRef]
- FIA-NP: Collaborative Research: Named Data Networking Next Phase (NDN-NP). 2014. Available online: https://api.semanticscholar.org/CorpusID:5454097 (accessed on 13 June 2024).
- Hoque, A.K.M.M.; Amin, S.O.; Alyyan, A.; Zhang, B.; Zhang, L.; Wang, L. NLSR. In Proceedings of the 3rd ACM SIGCOMM Workshop on Information-Centric Networking, Hong Kong, China, 12 August 2013; ACM: New York, NY, USA, 2013; pp. 15–20. [Google Scholar] [CrossRef]
- Wang, L.; Lehman, V.; Hoque, A.K.M.M.; Zhang, B.; Yu, Y.; Zhang, L. A Secure Link State Routing Protocol for NDN. IEEE Access 2018, 6, 10470–10482. [Google Scholar] [CrossRef]
- Yi, C.; Abraham, J.; Afanasyev, A.; Wang, L.; Zhang, B.; Zhang, L. On the Role of Routing in Named Data Networking. 2013. [Online]. Available online: http://named-data.net/techreports.html (accessed on 12 June 2024).
- Zhang, Y.; Xia, Z.; Afanasyev, A.; Zhang, L. A Note on Routing Scalability in Named Data Networking. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Ariefianto, W.T.; Syambas, N.R. Routing in NDN network: A survey and future perspectives. In Proceedings of the 2017 11th International Conference on Telecommunication Systems Services and Applications (TSSA), Lombok, Indonesia, 26–27 October 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, k.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named data networking. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Chowdhury, M.; Khan, J.A.; Wang, L. Leveraging Content Connectivity and Location Awareness for Adaptive Forwarding in NDN-based Mobile Ad Hoc Networks. In Proceedings of the 7th ACM Conference on Information-Centric Networking, Virtual, 29 September–1 October 2020; ACM: New York, NY, USA, 2020; pp. 59–69. [Google Scholar] [CrossRef]
- Yi, C.; Afanasyev, A.; Wang, L.; Zhang, B.; Zhang, L. Adaptive forwarding in named data networking. ACM SIGCOMM Comput. Commun. Rev. 2012, 42, 62–67. [Google Scholar] [CrossRef]
- Alkwai, L.; Belghith, A.; Gazdar, A.; Al-Ahmadi, S. Comparative Analysis of Producer Mobility Management Approaches in Named Data Networking. Appl. Sci. 2022, 12, 12581. [Google Scholar] [CrossRef]
- Alkwai, L.; Belghith, A.; Gazdar, A.; AlAhmadi, S. Awareness of user mobility in Named Data Networking for IoT traffic under the push communication mode. J. Netw. Comput. Appl. 2023, 213, 103598. [Google Scholar] [CrossRef]
- Alkwai, L.; Belghith, A.; Gazdar, A.; AlAhmadi, S. Transparent consumer mobility management in named data networking under the push communication mode. Comput. Netw. 2023, 235, 109953. [Google Scholar] [CrossRef]
- Zhang, Z.; Lung, C.-H.; Lambadaris, I.; St-Hilaire, M. IoT Data Lifetime-Based Cooperative Caching Scheme for ICN-IoT Networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Ruggeri, G.; Molinaro, A. Beyond Edge Caching: Freshness and Popularity Aware IoT Data Caching via NDN at Internet-Scale. IEEE Trans. Green Commun. Netw. 2022, 6, 352–364. [Google Scholar] [CrossRef]
- Alahmri, B.; Al-Ahmadi, S.; Belghith, A. Efficient Pooling and Collaborative Cache Management for NDN/IoT Networks. IEEE Access 2021, 9, 43228–43240. [Google Scholar] [CrossRef]
- Meddeb, M.; Dhraief, A.; Belghith, A.; Monteil, T.; Drira, K.; AlAhmadi, S. Cache Freshness in Named Data Networking for the Internet of Things. Comput. J. 2018, 61, 1496–1511. [Google Scholar] [CrossRef]
- Putra, M.A.P.; Kim, D.-S.; Lee, J.-M. Adaptive LRFU replacement policy for named data network in industrial IoT. ICT Express 2022, 8, 258–263. [Google Scholar] [CrossRef]
- Wei, Y.; Shi, K.; Li, J. A cache replacement strategy based on content features in named data networking. In Proceedings of the 2021 5th International Conference on Electronic Information Technology and Computer Engineering, Xiamen, China, 22–24 October 2021; ACM: New York, NY, USA, 2021; pp. 1577–1581. [Google Scholar] [CrossRef]
- Kalghoum, A.; Gammar, S.M.; Saidane, L.A. Towards a novel cache replacement strategy for Named Data Networking based on Software Defined Networking. Comput. Electr. Eng. 2018, 66, 98–113. [Google Scholar] [CrossRef]
- Al-Turjman, F.M.; Al-Fagih, A.E.; Hassanein, H.S. A value-based cache replacement approach for Information-Centric Networks. In Proceedings of the 38th Annual IEEE Conference on Local Computer Networks—Workshops, Sydney, NSW, Australia, 21–24 October 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 874–881. [Google Scholar] [CrossRef]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Foster, N.; Guha, A.; Reitblatt, M.; Story, A.; Freedman, M.J.; Katta, N.P.; Monsanto, C.; Reich, J.; Rexford, J.; Schlesinger, C.; et al. Languages for software-defined networks. IEEE Commun. Mag. 2013, 51, 128–134. [Google Scholar] [CrossRef]
- Rawat, D.B.; Reddy, S.R. Software Defined Networking Architecture, Security and Energy Efficiency: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 325–346. [Google Scholar] [CrossRef]
- Gong, Y.; Huang, W.; Wang, W.; Lei, Y. A survey on software defined networking and its applications. Front. Comput. Sci. 2015, 9, 827–845. [Google Scholar] [CrossRef]
- OpenFlow Switch Specification Version 1.5.1 (Protocol Version 0x06) for Information on Specification Licensing through Membership Agreements. 2015. [Online]. Available online: http://www.opennetworking.org (accessed on 12 June 2024).
- Prabha, C.; Goel, A.; Singh, J. A Survey on SDN Controller Evolution: A Brief Review. In Proceedings of the 7th International Conference on Communication and Electronics Systems, ICCES 2022—Proceedings, Coimbatore, India, 22–24 June 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022; pp. 569–575. [Google Scholar] [CrossRef]
- Zhu, L.; Karim, M.M.; Sharif, K.; Li, F.; Du, X.; Guizani, M. SDN Controllers: Benchmarking & Performance Evaluation. arXiv 2019, arXiv:1902.04491. [Google Scholar]
- Adnan, M.; Ali, J.; Ayadi, M.; Elmannai, H.; Almuqren, L.; Amin, R. Leveraging Software-Defined Networking for a QoS-Aware Mobility Architecture for Named Data Networking. Electronics 2023, 12, 1914. [Google Scholar] [CrossRef]
- Sharif, S.; Moghaddam, M.H.Y.; Seno, S.A.H. Adaptive cache content placement for software-defined Internet of Things. Future Gener. Comput. Syst. 2022, 136, 34–48. [Google Scholar] [CrossRef]
- Guesmi, T.; Kalghoum, A.; Alshammari, B.M.; Alsaif, H.; Alzamil, A. Leveraging Software-Defined Networking Approach for Future Information-Centric Networking Enhancement. Symmetry 2021, 13, 441. [Google Scholar] [CrossRef]
- Tariq, A.; Rehman, R.A.; Kim, B.S. Epf—An efficient forwarding mechanism in sdn controller enabled named data iots. Appl. Sci. 2020, 10, 7675. [Google Scholar] [CrossRef]
- Alhowaidi, M.; Nadig, D.; Ramamurthy, B.; Bockelman, B.; Swanson, D. Multipath Forwarding Strategies and SDN Control for Named Data Networking. In Proceedings of the International Symposium on Advanced Networks and Telecommunication Systems, ANTS, Indore, India, 16–19 December 2018; IEEE Computer Society: Washington, DC, USA, 2018. [Google Scholar] [CrossRef]
- Siracusano, G.; Salsano, S.; Ventre, P.L.; Detti, A.; Rashed, O.; Blefari-Melazzi, N. A framework for experimenting ICN over SDN solutions using physical and virtual testbeds. Comput. Netw. 2018, 134, 245–259. [Google Scholar] [CrossRef]
- Torres, J.V.; Alvarenga, I.D.; Boutaba, R.; Duarte, O.C.M.B. An autonomous and efficient controller-based routing scheme for networking Named-Data mobility. Comput. Commun. 2017, 103, 94–103. [Google Scholar] [CrossRef]
- Kalghoum, A.; Gammar, S.M. Towards new Information Centric Networking strategy based on software defined networking. In Proceedings of the IEEE Wireless Communications and Networking Conference, WCNC, San Francisco, CA, USA, 19–22 March 2017; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2017. [Google Scholar] [CrossRef]
- Xiulei, W.; Ming, C.; Chao, H.; Xi, W.; Changyou, X. SDICN: A software defined deployable framework of information centric networking. China Commun. 2016, 13, 53–65. [Google Scholar] [CrossRef]
- Jeeva, R. OpenFlow-Based Control Plane for Information-Centric Networking. 2016. Available online: https://publications.scss.tcd.ie/theses/diss/2016/TCD-SCSS-DISSERTATION-2016-058.pdf (accessed on 13 June 2024).
- Aubry, E.; Silverston, T.; Chrisment, I. SRSC: SDN-based routing scheme for CCN. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Berman, M.; Chase, J.S.; Landweber, L.; Nakao, A.; Ott, M.; Raychaudhuri, D.; Ricci, R.; Seskar, I. GENI: A federated testbed for innovative network experiments. Comput. Netw. 2014, 61, 5–23. [Google Scholar] [CrossRef]
- Salsano, S.; Blefari-Melazzi, N.; Detti, A.; Morabito, G.; Veltri, L. Information centric networking over SDN and OpenFlow: Architectural aspects and experiments on the OFELIA testbed. Comput. Netw. 2013, 57, 3207–3221. [Google Scholar] [CrossRef]
- Madureira, A.L.R.; Araujo, F.R.C.; Araújo, G.B.; Sampaio, L.N. NDN Fabric: Where the Software-Defined Networking Meets the Content-Centric Model. IEEE Trans. Netw. Serv. Manag. 2021, 18, 374–387. [Google Scholar] [CrossRef]




| Ref. | Year | SDN | NDN | Examples of SD-NDN | Compare between the SD-NDN Examples | Notes |
|---|---|---|---|---|---|---|
| [8] | 2016 | Yes | Yes | Yes | No | Explores methods of implementing NDN over SDN. |
| [9] | 2018 | Yes | No | No | No | Compares between different SDN controllers. |
| [10] | 2019 | No | Yes | No | No | Surveys different name lookup schemes in NDN. |
| [7] | 2022 | Yes | Yes | Relevant to IOT services | Yes | Focuses on leveraging SD-NDN to improve IOT services. |
| [11] | 2022 | No | Yes | No | No | Explore different NDN forwarding strategy implementations. |
| [12] | 2022 | No | Yes | No | No | Surveys different NDN naming schemes. |
| [6] | 2023 | Yes | Yes | Includes examples of NDN over SDN | Yes | Explores the implementation of NDN over SDN and vice versa. |
| This paper | 2024 | Yes | Yes | Yes | Yes | Focuses on leveraging SD-NDN to improve NDN routing, forwarding, and caching. |
| Model Ref. | Date | SDN | Enhanced Mechanism | Simulation Tool | Evaluation Matrices | Model Limitations |
|---|---|---|---|---|---|---|
| SDPCACM [41] | 2023 | ODL controller | Consumer mobility | Mininet | CPU usage, Jitter, Throughput, and Packet loss ratio | Not suitable for networks with high mobility |
| [42] | 2022 | SDN-like (SDCC) | Caching | MATLAB | Energy consumption, and Cache hit ratio | Centralized model = single point of failure, and Not scalable |
| [43] | 2021 | SDN-like | Routing and forwarding | NDNSim | Bandwidth, Delay, Cache hit ratio, and Memory overhead | Not scalable, Memory overhead, and Efficacy issues due to large prefix tables lookups |
| EPF [44] | 2020 | SDN-like | Forwarding | NDNSim | Number of interests, Content retrieval time, Network lifetime, Number of high-priority interests, Retransmissions, and Average energy consumption | Not scalable, Memory overhead, and Efficacy issues due to large prefix tables lookups |
| S-MP [45] | 2018 | - | Routing | GENI testbeds [52] | Delay | Not scalable |
| ICNoSDN V2 [46] | 2018 | Floodlight controller | Routing and caching | OFELIA project testbeds [53] and Mininet | Crossing traffic of cache servers and data servers, and Number of cached items | Not scalable |
| CRoS-NDN [47] | 2017 | SDN-like | Routing | NDNSim | Content delivery delay, and Signaling efficiency | Not scalable |
| NDNS [48] | 2017 | SDN-like | Routing and caching | NDNSim | Bandwidth, Delay, Cache hit ratio, and Bootstrap (setup) time | Memory overhead, and Efficacy issues due to large prefix tables lookups |
| SDICN [49] | 2016 | NOX controller | Routing and caching | Testbeds | Storage overhead, Request hit ratio, Content download time, and Control computation time cost | Not scalable |
| OF-ICN [50] | 2016 | POX controller | Routing | - | Round trip time | Not scalable |
| SRSC [51] | 2015 | SDN-like | Routing | NDNSim | Bootstrap (setup) time, Cache hit ratio, and Number of data and interest messages | Not scalable |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alhawas, A.; Belghith, A. Software-Defined Named Data Networking in Literature: A Review. Future Internet 2024, 16, 258. https://doi.org/10.3390/fi16080258
Alhawas A, Belghith A. Software-Defined Named Data Networking in Literature: A Review. Future Internet. 2024; 16(8):258. https://doi.org/10.3390/fi16080258
Chicago/Turabian StyleAlhawas, Albatool, and Abdelfettah Belghith. 2024. "Software-Defined Named Data Networking in Literature: A Review" Future Internet 16, no. 8: 258. https://doi.org/10.3390/fi16080258
APA StyleAlhawas, A., & Belghith, A. (2024). Software-Defined Named Data Networking in Literature: A Review. Future Internet, 16(8), 258. https://doi.org/10.3390/fi16080258







