1. Introduction
Computer network systems have been implemented to enable device communication and perform crucial business functions. However, this creates a higher reliance on an entity’s connection systems’ primary functions. Due to their extensive and critical reliance on computer networks, key sectors including banking, healthcare organizations, and service providers are subject to instability threats [
1,
2,
3,
4]. Due to this dependence, maintaining ideal networks is necessary to maintain accessibility, efficiency, and safety. A security breach can significantly impact network performance, leading to instability and eventual network incompatibility.
Moreover, cyberattacks may result in blackouts, issues in weapon systems, and confidential information releases. They might cause the loss of priceless sensitive data, such as hospital files, military records, etc. Furthermore, they can disable phone and computer networks, making data unavailable or rendering systems unusable [
5,
6,
7]. Banking and government networks are particularly vulnerable because of the tremendous value of the data they contain. The hackers steal the information (especially other people’s banking details) and profit from that information.
Over the past decade, there have been instances of different kinds of hybrid network attacks, causing severe system anomalies. Such attacks have been more prevalent over the past ten years, posing a severe threat to the stability of networks due to the modification of numerous services [
8,
9,
10]. Denial of service (DoS) attacks fall into mainly two categories: service outages and service flooding.
The internet-of-things network has experienced severe losses due to DDoS attacks. Therefore, IoT users consequently have paid great attention to the vulnerabilities. Numerous devices or systems work together to attack a single target, making it challenging to locate and disable the attacking devices [
11,
12,
13,
14,
15]. Cyberattackers frequently use a botnet to interfere with internet infrastructure. DDoS attacks are difficult to identify and prevent in real time, yet this approach has enormous utility because attacks can have significant effects.
Many intrusion detection systems (IDSs) have been developed in the past to identify these assaults, utilizing a variety of techniques involving mathematical modeling, and data mining techniques such as machine learning techniques, etc. Due to their difficulties in processing high-dimensional network information, these analytical and conventional machine learning models perform poorly [
16,
17,
18,
19,
20]. Therefore, deep learning-based techniques are essential to handle these issues.
Recently, deep learning has attracted much interest in attack detection due to its efficient feature extraction and learning abilities, specifically in settings with massive datasets. Without contextual information, deep learning techniques eventually capture significant characteristics from the input data using numerous layers [
21,
22,
23,
24]. Therefore, in this paper, Densenet-based deep learning was implemented to perform multi-class classification on DoS and DDoS attacks. To solve the imbalanced data issue, a self-organized generative adversarial network (SOMGAN) was implemented to perform data augmentation. Afterwards, the feature extraction and selection are performed using a pyramid atrous attention network and artificial bee colony optimization algorithm (ABC). Finally, the attacks were detected and classified using a convolution block attention classifier.
The primary contributions of this paper include the following:
- −
A self-organizing map generative adversarial network (SOMGAN)-based data augmentation technique was utilized to address the challenge of the imbalanced dataset and enhance the effectiveness of the proposed network;
- −
Departing from traditional feature extraction methods, the paper adopts a deep learning approach incorporating the pyramid atrous attention module to extract crucial attributes from raw network traffic data;
- −
The development of a feature selection and classification system based on the artificial bee colony optimization algorithm (ABC) and convolutional dense-attention module to identify various types of attacks;
- −
The investigation results demonstrate that the proposed approach outperforms previous techniques in terms of attack detection on ot-IoT, CIC-IDS2017, and UNSW_NB15 datasets.
The study is subdivided into the following sections. The study’s concept introduction is presented in
Section 1, and a literature review is briefly described in
Section 2. The methodology, experimental results, and discussion follow in
Section 2,
Section 3 and
Section 4, respectively. Finally, the conclusions are delivered.
2. Literature Review
DoS and DDoS assaults are a severe threat to many organizations because of their tremendous ability to bring down unprotected servers in a short period. Therefore, the prevention of DoS and DDoS attacks has been the subject of many research proposals. Current studies suggest some robust defensive frameworks from network breach attacks, which are briefly explained below.
Detection and classification of DDoS attacks was studied by Wei et al. [
25], who incorporated two deep learning-based techniques using an auto encoder (AE) multi-layer perceptron (MLP). To perform feature extraction without human assistance, AE was implemented by the authors. Using the extracted features, various kinds of DDoS attacks were classified by MLP network. To assess the effectiveness of the suggested approach, large DDoS attack samples from CICDDoS2017 were extracted to access the accuracy metrics.
Shroff et al. [
26] studied a generative adversarial network (GAN)-based reliable detector for identifying cyberattacks. In this system, two distinct GAN-based models were implemented. The first generator produced benign instances that closely resembled benign samples from the dataset and the second generator was capable of producing DDoS cases that closely resembled those from the dataset. Moreover, the creation of a DNN classifier-based framework facilitated distinguishing between huge samples of DDoS and benign classes over structural similarity metrics. GANs are a powerful deep generative model trained with an adversarial procedure. GANs have undergone several modifications since they were first proposed to solve several different problems in different domains [
27].
Azzaoui et al. [
28] implemented a deep neural network (DNN)-based intrusion detection model to effectively classify dynamic network traffic outside the sandbox. The kernel consisted of a four-layer network, and each layer contained 136 neurons. To analyze the effectiveness of the suggested approach, numerous experiments were carried out with various hyperparameter combinations, and the results were compared with those of other shallow and deep ANN models. They used CICIDS2017 and NSL-KDD datasets with standard performance metrics for this assessment. They then created and tested 36 alternative DNN model combinations, each producing different outcomes.
To identify unknown DDoS attacks, Shieh et al. [
29] created a method that employed reconstruction error and distributed hidden layer features. The deep hierarchical reconstruction nets (DHRNet) structure was used in this research to recompile it with a 1D interconnected neural network using a spatial location constraint prototype loss function. A random gradient descent approximation-based one-class SVM (support vector machine) was implemented to identify the unidentified patterns in the following stage. The performance of this approach was assessed using the CICIDS2017 Friday Open Dataset.
Alduailij et al. [
30] developed a system for detecting DDoS attacks by employing various machine learning and feature selection algorithms. The initial step involved selecting the most relevant attributes from the network-IoT datasets using dual machine learning (ML) approaches, namely correlative and mutual information random forest. Subsequently, the attack detection was carried out using an ensemble-weighted voting method and then scored with random forest (RF) algorithms. The performance of the system was assessed using evaluation metrics and coefficient metrics confirmed the higher true positives of the target class.
Smith et al. [
31] utilized the UNSW-NB15 dataset to evaluate the effectiveness of machine learning algorithms for network intrusion detection. They compared the performance of various classifiers, including random forest, support vector machines, and neural networks, using a range of features extracted from the dataset. The results demonstrated that the random forest classifier outperformed other algorithms, achieving an accuracy of 95% and a low false-positive rate. The study highlighted the significance of leveraging the UNSW-NB15 dataset as a benchmark for assessing the efficacy of intrusion detection systems and emphasized the potential of machine learning techniques in enhancing network security.
DenseNet [
32] is a deep learning architecture that achieves efficient information flow across levels by directly connecting all of its layers. Each layer passes its feature maps to all succeeding layers and receives extra input from all earlier layers. Concatenation is used to merge the output feature maps from the previous layer with those from the current layer. Each layer of the network is connected to all of the successive levels, and together they are known as DenseNets. Comparatively speaking, this model needs fewer parameters than conventional CNNs. It also reduces the overfitting problem that occurs with smaller malware training sets [
33,
34,
35].
3. Proposed Methodology
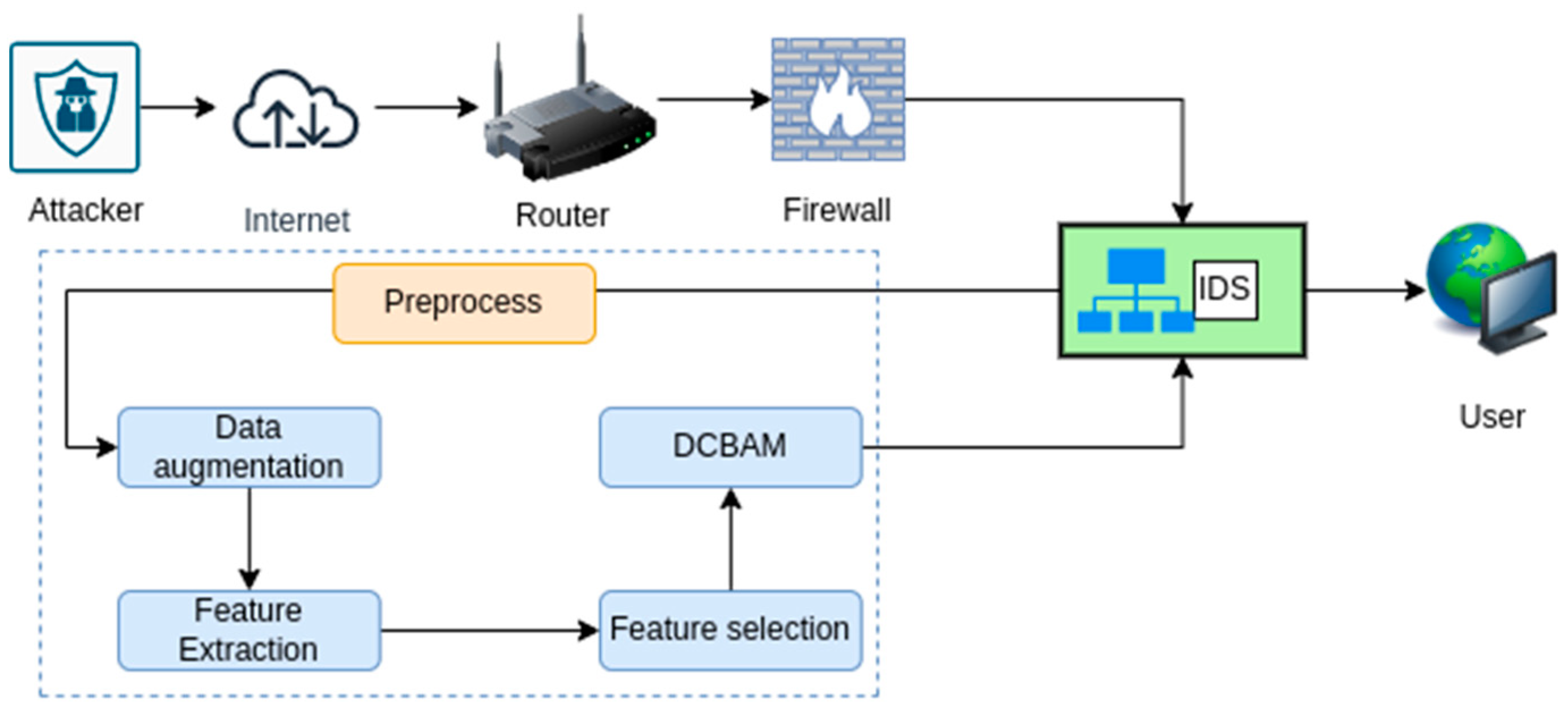
This section introduces a novel intrusion detection method based on deep learning, which aims to classify various forms of DoS and DDoS attacks. The proposed method’s high-level architecture is depicted in
Figure 1, consisting of four key phases. These phases include preprocessing and data augmentation, feature extraction, feature selection, and classification using a Densenet convolutional block attention module (DCBAM). It mainly uses the improved convolutional block attention (CBA) DenseNet algorithm to enhance beneficial features to better integrate the attention module into DenseNet without increasing too many parameters and wasting computing resources. Initially, the raw data undergoes a series of preprocessing steps to remove unwanted information. To address the issue of imbalanced data, a data augmentation technique based on a conditional generative adversarial network (SOMGAN) is applied, resulting in improved performance of the classifier. Subsequently, the augmented data are subjected to feature extraction using the pyramid atrous attention-based deep learning technique. The artificial bee colony optimization algorithm (ABC) is then employed to identify significant features from the extracted set. Lastly, a classifier based on Densenet architecture analyzes these features and accurately classifies the detected cyberattacks. DenseNet [
36] uses a dense connection layer, in which each layer can obtain the connected feature map of the previous layer. Model redundancy is reduced by feature reuse at each level of the network [
37].
3.1. Preprocessing
The data preprocessing stage is crucial to the overall kernel learning phase and training process, as it becomes more robust and yields a more precise model. Consequently, undesired characteristics such as “infinity” or “NaN” values in “flow packets/s” are eliminated during this phase. Additionally, redundant rows, including Fwd Avg Bytes, Bwd Avg Bulk, Fwd Avg Bulk, are removed.
The main objective of the approach is to perform multi-class categorization of DDoS attacks, which necessitates encoding. To achieve this, the study employed a one-hot encoder (OHE). This involved adding a new column for each label and assigning a value of 1 or 0 which denoted an attack or benign class.
After the labels were encoded, the next step involved data normalization using L2 normalization, and consequent columns were processed to its standard. The attributes of the label datasets are categorized by the equation below, where x represents each instance of a record.
The process of normalizing the dataset records generally leads to significantly faster training. By ensuring that the dataset attributes are within a consistent range, this normalization step contributes to the generation of a more accurate model.
3.2. Data Augmentation Using a Self-Organizing Map Generative Adversarial Network
While using a SOMGAN, self-organizing maps (SOM) can be used for feature extraction. A SOM is a type of unsupervised neural network that is used for dimensionality reduction and clustering of input data. It works by mapping high-dimensional data onto a low-dimensional grid and preserving the topological properties of the input space. The resulting map can be used to identify clusters in the data and reduce the dimensionality of the input space. The generator is then used to generate new samples that are similar to the input data but also diverse. Using a self-organizing map generative adversarial network (SOMGAN) for data augmentation in the context of identifying cyberattacks can offer several benefits, primarily related to improving the robustness and generalization of the cyberattack detection model. Here is why SOMGAN techniques might be used for data augmentation:
Limited real data: In many cybersecurity applications, obtaining a diverse and extensive dataset of real-world cyberattacks can be challenging due to their infrequent occurrence or limited availability. Data augmentation techniques, like SOMGAN, can artificially expand the dataset, making the model more robust by exposing it to a wider range of possible attack scenarios.
Class imbalance: Cyberattack datasets often suffer from class imbalance, where certain attack types are rare compared to normal instances. This can lead to biased models that perform well on the majority class but poorly on the minority class (attacks). By generating synthetic attack instances, a SOMGAN can balance the class distribution and help the model better understand the characteristics of various attack types.
Generalization: Data augmentation helps the model generalize better. By exposing the model to a more diverse set of attack patterns, it learns to differentiate between normal and attack instances more effectively, even when faced with previously unseen or slightly different attack variations.
Anomaly detection: Many cyberattacks are “anomalies” compared to normal network behavior. Data augmentation techniques like SOMGAN can help the model learn to identify subtle anomalies that may not be well-represented in the original dataset.
Zero-day attacks: Data augmentation can aid in preparing the model for detecting zero-day attacks, which are previously unseen attack types. The model’s exposure to a wider range of attack patterns through synthetic data can enhance its ability to identify novel attacks.
Improved feature learning: A SOMGAN can help the model learn more robust and relevant features from the data. This is particularly useful for complex and high-dimensional data like network traffic or system logs, where manual feature engineering can be challenging.
Reducing overfitting: By augmenting the dataset with synthetic data, the model is less likely to overfit to the limited real data. This is especially important when building deep learning models for cybersecurity, as overfitting can lead to poor generalization and a high false-positive/negative rate.
In summary, SOM can be used as an alternative to other dense generative algorithms for data augmentation in a SOMGAN [
38,
39,
40,
41,
42,
43]. A SOMGAN is sufficiently employed in a number of applications for data augmentation with unbalanced distributions in fault diagnosis, anomaly detection, and DoS attack detection.
3.3. Feature Extraction by Pyramid Atrous Attention Module
The attention network plays a crucial role in extracting effective features from the preprocessed data. This sort of network is built upon encoder and decoder structures, consisting of five stages. The initial three stages employ 1 × 1 convolution layers for the convolution process, while the subsequent two stages utilize atrous convolution with 3 × 3 convolution layers. A ReLU layer is introduced between the two convolution layers to generate nonlinear representations, capturing low-level specific features.
To upscale the high-level feature maps within all residual blocks, the deconvolution technique is employed. Ensuring uniform feature map sizes is necessary for conducting feature fusion operations. Subsequently, the convolutional block attention module (CBAM) [
5] is incorporated into the lateral connections to fine-tune the feature maps layer by layer. This integration aids in reducing false detections and enhancing feature extraction accuracy.
The CBAM module holds the capability to enhance network feature learning and can be seamlessly integrated into any network architecture. In our approach, we incorporated a CBAM module after each dense block to refine the features and bolster the network’s ability to represent features effectively. Please refer to
Figure 2 and
Figure 3 for a visual representation of this process.
Overall, the attention network leverages encoder and decoder structures, employing convolution and atrous convolution layers to extract features. The deconvolution technique is used to upscale feature maps, and the CBAM module is added to adjust feature maps and improve feature representation accuracy. This comprehensive approach enhances the network’s capability to learn and represent features accurately.
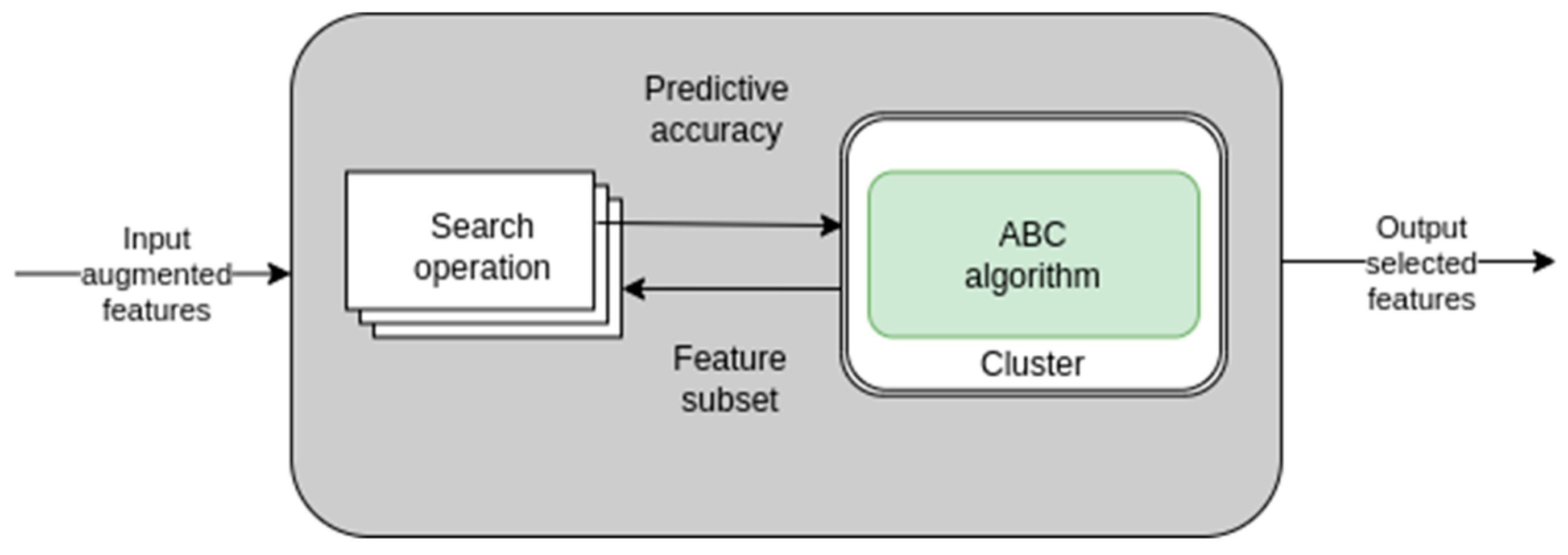
3.4. Feature Selection Using Artificial Bee Colony (ABC) Algorithm
An artificial bee colony (ABC) algorithm is a population-based stochastic optimization technique, which replicates the intelligent foraging behavior of honeybee swarms. It can be used for classification, clustering, and optimization studies. The food supply position—which represents the solution to the optimization problem—and the amount of nectar in the food source depends on the quality of the associated solution. This value is calculated in formula below:
SN in the algorithm indicates the size of the population. Each
zi solution is a
D-dimensional vector for
i = 1, 2, 3, …, SN. Here,
D is the numbers of cluster products and input size for each dataset. The probability value (
pi) is calculated in (3):
where SN is the number of food sources, which is equal to the number of employed bees and the goodness of the fit
i solution given in (1).
zij represents comparison of two food sources to a bee.
So a greedy selection mechanism is used to make selections among the old source and one of the candidates.
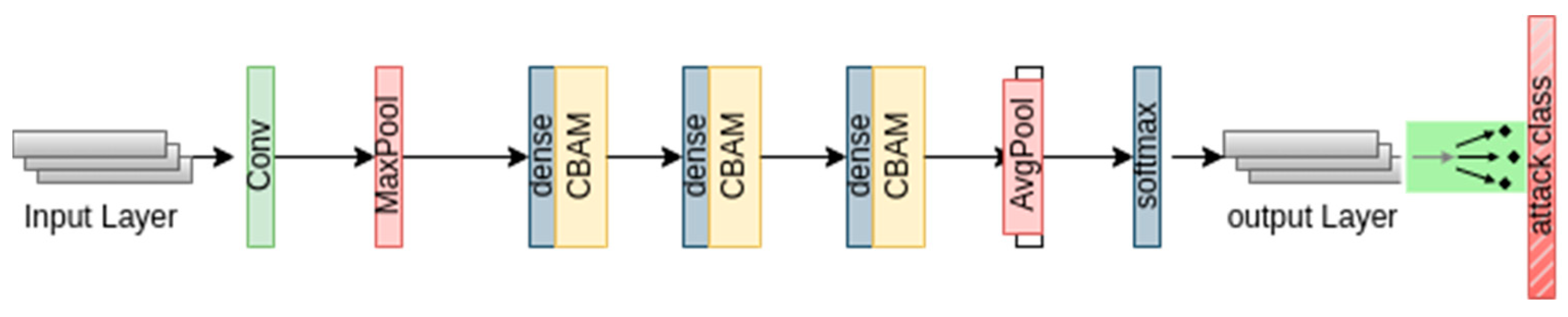
3.5. Intrusion Detection Using DCBAM Architecture
This section provides a comprehensive overview of the implementation process for an attack detection and classification system utilizing DenseNet201, a deep learning model with 201 layers. The framework leverages the unique characteristics of DenseNet201, which establishes direct connections between layers possessing the same feature map size. This design enables the reuse of extracted features across layers, resulting in a more precise and compact model. The DenseNet201 model is structured with four dense blocks interconnected by three transition layers responsible for downsampling. These blocks and layers are crucial for feature extraction. The final deep layers in DenseNet201 incorporate the information from all preceding layers, as denoted by Equation (4). This equation represents the composite function involving batch normalization, ReLu activation, and a 3 × 3 convolution layer. Furthermore, specific convolution layers with varying filter sizes and kernel shapes are appended after the fourth dense block to capture more detailed information. The features extracted from previous aggregated layers are subsequently passed to the classification head of the model. The classification layer comprises two dense layers, a batch normalization layer, and a convolution layer, with a Softmax. These components play a vital role in the final classification of attacks based on the extracted features. In summary, the implementation of the attack detection and classification system utilizes DenseNet201 as the underlying model, incorporating direct connections, dense blocks, transition layers, and specific convolution layers. The system effectively captures and reuses features, leading to a more precise and compact model for accurate classification of attacks.
To extract important features while removing redundant information, the attention mechanism is employed. The convolutional block attention module (CBAM) proposed by Woo et al. [
4] effectively extracts meaningful features in the channel and spatial dimensions, respectively, allowing for adaptive feature refinement. The module is shown in
Figure 3. Using deep learning-based techniques, such as DenseNet, for cyberattack detection has become increasingly popular due to several advantages over other available techniques. Here are some reasons why DenseNet and similar deep learning approaches are favored [
44,
45,
46,
47,
48,
49,
50,
51,
52]:
- −
Feature learning: Deep learning models like DenseNet automatically learn relevant features from the data, making them highly effective at capturing intricate patterns in complex data like network traffic or system logs. This adaptability is crucial in detecting new and evolving cyberattacks.
- −
End-to-end learning: Deep learning models are designed to learn from raw input data to make predictions directly. This end-to-end learning can help simplify the detection pipeline, reducing the need for manual feature engineering and potentially improving accuracy.
- −
Complex relationships: Cyberattacks can exhibit intricate relationships across multiple dimensions of data. Traditional techniques may struggle to capture these relationships effectively, whereas deep learning models can handle complex, nonlinear interactions in the data.
- −
Scalability: Deep learning models can handle large-scale datasets, making them suitable for real-time or near-real-time detection in high-speed network environments, which is essential for modern cybersecurity needs.
- −
Adaptability: Deep learning models can adapt to new attack patterns with minimal human intervention. This adaptability is crucial as cyberattacks constantly evolve, making it challenging to maintain rule-based or signature-based detection systems.
- −
Representation learning: Deep learning models can learn useful representations of the data, which can aid in identifying both known and novel attack types. This feature is particularly valuable in zero-day attack detection.
- −
Performance: In many cases, deep learning techniques like DenseNet can achieve state-of-the-art performance on benchmark datasets, demonstrating their effectiveness in cyberattack detection compared to other techniques.
4. Experimental Results
In this section, exploratory analysis is performed to expunge redundancies in the data and state the potency of the intrusion detection (ID) model. The results of the analysis are discussed in the following sections. The experiments were conducted on the system mentioned in the
Table 1. These parameters were carefully selected to optimize the training process and achieve the best possible performance of the intrusion detection model. The Adam optimizer is known for its effectiveness in training deep learning models, while the ReLU activation function helps introduce nonlinearity, enhancing the model’s representational power. The batch size and momentum values contribute to efficient gradient updates during training, and the dropout regularization technique aids in preventing overfitting. By conducting experiments with these specified settings, obtained evaluation metrics clearly denote the robustness of our proposed architecture over SOTA models.
4.1. Dataset Description
4.1.1. Bot-IoT Dataset
This dataset is the most recent in the industry. The dataset was released by Koroniotis et al. in 2018 [
53]. It has a variety of synthetic and real-world scenarios and includes more than 72 million recordings. There are four different assault types, while DoS and DDoS-type packets make up the majority of the dataset. Similar to the UNSW-NB15 data collection, this set is imbalanced.
4.1.2. CICIDS2017 Dataset
The Canadian Institute of Cybersecurity has just produced an open-source dataset for intrusion detection called CICIDS-2017 [
54]. Labeling the CICIDS-2017 dataset is based on the date, destination, source IP addresses, attacks, protocols, destination, and source ports. It contains the characteristics of actual, realistic internet traffic. With 80 network traffic features and 2,830,743 records, this dataset was collected over five days. The dataset is a compilation of eight traffic surveillance periods and a CSV file with both regular and intruder traffic. DDoS, DoS, SSH, brute force, FTP, botnet, infiltration, heartbleed, and web attacks are the different types in this dataset.
4.1.3. UNSW-NB15 Dataset
UNSW-NB15 dataset has a hybrid of the real modern normal and the contemporary synthesized attack activities of the network traffic [
55]. Smith et al. (2021) utilized the UNSW-NB15 dataset to evaluate the effectiveness of machine learning algorithms for network intrusion detection. They compared the performance of various classifiers, including random forest, support vector machines, and neural networks, using a range of features extracted from the dataset. The results demonstrated that the random forest classifier outperformed other algorithms, achieving an accuracy of 95% and a low false-positive rate. The study highlighted the significance of leveraging the UNSW-NB15 dataset as a benchmark for assessing the efficacy of intrusion detection systems and emphasized the potential of machine learning techniques in enhancing network security.
4.2. Discussion
In this section, the proposed framework is tested on the test datasets (Bot-IoT, CICIDS2017, and UNSW_NB15) over numerous evaluation metrics, and the detailed ablation is conducted to compare with other SOTA methods. To evaluate and analyze the effectiveness of attack detection cases, we compared the proposed approach with recently published attack detection methods. To perform this task, we employed widely used estimation metrics (precision, recall, and F1), as detailed in these publications [
56,
57,
58,
59,
60]. To classify the results obtained, the following cases were distinguished:
True positives (TP): attack present and correct classification;
True negatives (TN): attack not present and correct classification;
False positives (FP): attack not present and incorrect classification;
False negatives (FN): attack present and incorrect classification.
A confusion matrix is a table used to estimate a classifier’s goodness. There are the events considered in the rows, while in the columns, their classification is present. The data on the main diagonal represent correct classifications. From this table are also derived three merit factors that contribute to the analysis of a classifier’s performance: the precision (P) (6) merit factor takes into account the number of correct attack identifications concerning the total number of detections. It is obtained with the following formula:
The recall (R) (7) factor of merit takes into account the number of correct attack identifications compared to the total number of attacks made:
Finally, the F1-score factor (F1) (8) is given by the harmonic average of precision and recall and measures the accuracy of the classification of events:
4.2.1. Performance Evaluation on Bot-IoT Dataset
Our proposed strategy’s multi-class classification is shown in
Table 2. The table illustrates that the performance of our proposed method across all classes was superior. The Bot-IoT dataset achieved 99.87% and 99.68% accuracy in the DDoS and DoS classifications, respectively. The performance on theft and reconnaissance classes was marginally worse than that on other classes. Only 99% (theft) and 98.67% (reconnaissance) accuracy were achieved in those classes using our suggested approach. The behavior on reconnaissance assaults was similar to the DDoS/DoS attack behavior mirrored in the current feature set. This activity makes it more challenging using the model to identify the difference between those two attacks.
Figure 4 displays a visual depiction of
Table 2. From the figure, it is observed that the F1 (99.89%), recall (99.96%), precision (99.93%), and accuracy (99.87%) value of the DDoS class was higher than that for all other classes. Overall, the results were positive for all types of attacks. However, the reconnaissance class received the lowest grade because it resembled regular data. Moreover, theft-exfiltration also attained the least values because a few instances in the dataset were mistakenly classified as belonging to a different class.
After the multi-class classification, the proposed approach’s results were compared with the existing intrusion detection techniques evaluated on the Bot-IoT dataset, as shown in
Table 3. The table shows that the proposed approach’s precision, accuracy, F1, and recall were more significant than those of other existing techniques, which means that the proposed framework dramatically reduced the false positives in most classes. Compared to all other techniques, the support vector machine (SVM)’s performance could have been better and more accurate because it incorrectly divided all theft assaults into various classes. Additionally, many attacks were misidentified as regular packets, demonstrating the inability of SVM in intrusion detection.
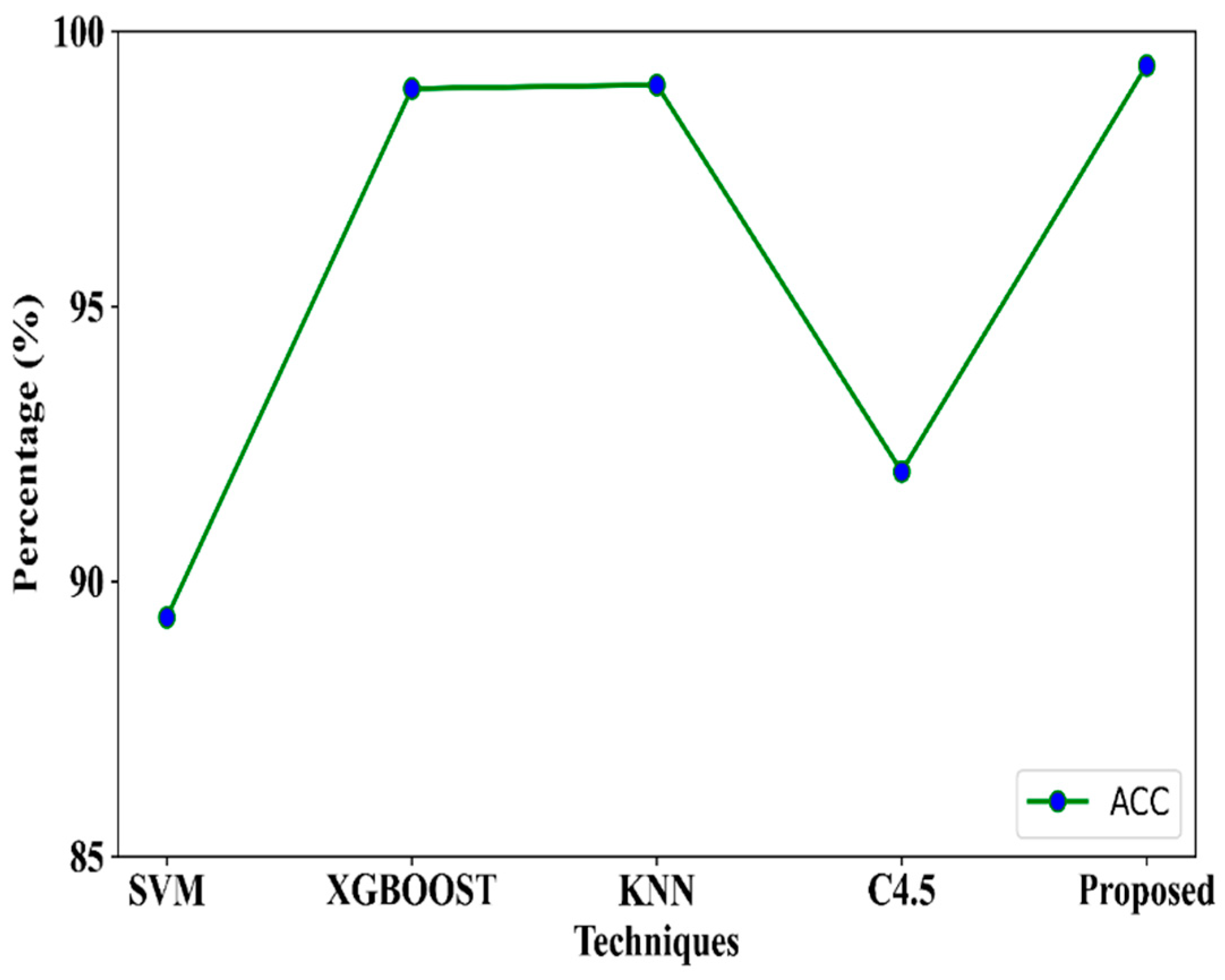
Compared to all other approaches, the overall performance of XGBoost was superior. However, the accuracy of k-nearest neighbor (KNN) (99.03%) was higher than that of XGBoost (98.96%) because it easily handled multi-class cases and achieved better accuracy than SVM. The performance of C4.5 was also better than that of SVM. Nevertheless, merely one metric (accuracy) (
Figure 5) does not adequately capture how effective the technique was at classifying intrusions. Last but not least, the results of the suggested strategy acquired using the Bot-IoT dataset show that our technique produced more practical outcomes when compared to other techniques.
4.2.2. Performance Evaluation on the CIC-IDS2017 Dataset
Table 4 displays the suggested model’s performance in multi-class classification on the CICIDS2017 dataset according to ACC, PRE, REC, and F1. The proposed method performed the best at detecting “benign” traffic (detection ACC of 99.97%) and the worst at detecting “SQL injection” traffic (detection ACC of 97.98%). The “SQL injection” data were scarce in the whole dataset, which caused the performance of the classifier to be poor. Moreover, the behavior pattern of a “bot” attack is similar to that of regular network traffic, making it harder for the proposed approach to recognize the attacks accurately, thus leading to average performance. Compared with heartbleed and SQL injection attacks, the brute force attack was more accurately predicted.
Figure 6 displays a visual depiction of
Table 4.
Regarding other performance scores, brute force and DDoS Hulk achieved similar PRE (99.67%), REC (99.65%), and F1 (99.67%) results. This demonstrated that the proposed classifier still displayed asymmetric behavior with regard to traffic classifications in this arrangement. Furthermore, ACC and REC rates are critical for assessing the classifier’s performance for every attack. According to the statistics, a class with low accuracy has a lot of false positives, which implies that ‘benign’ classes are unnecessarily marked as assaults.
Additionally, a model with low recall may ignore actual intrusion. Therefore, to ensure that the model performs optimally, ACC and REC values must be high enough. As stated in
Figure 6, the proposed model achieved superior values for all the parameters that describe the method’s efficiency for multi-class categorization.
To show the effectiveness of the proposed approach,
Table 5 compares the proposed approach’s results with those of existing techniques on the CICIDS2017 dataset. Our suggested methodology produced better performance when compared to existing techniques. In terms of F1, the deep neural network (DNN) and recurrent neural network (RNN) achieved similar values. Compared to all other techniques, Adaboost’s performance in terms of DDoS attack classification was substandard. However, the REC (100%) value of this technique was higher than that of all other approaches, which means this technique provided only a few false negatives.
On the other hand, the recurrent neural network (RNN) (98% ACC) and 1D-CNN (98.96% ACC) approaches outperformed comparable techniques and produced minimal misclassification errors. However, they did not match the performance of the proposed approach (99.26% ACC). This indicates that the proposed approach is more appropriate for DDoS attack categorization and detection.
4.2.3. Performance Evaluation on the UNSW-NB15 Dataset
Table 6 displays the outcomes of the proposed method’s multi-class categorization using the UNSW_NB15 dataset. The multi-class categorization performance of the suggested method was outstanding and produced the best results for each attack class, as seen from the table. For every class, ACC rates were greater than 99%. The benign, DDoS, and DSproto classes achieved exceptional performance, with ACC rates of 99.94%, 99.83%, and 99.81%, respectively. The categorization performance on other assault categories also delivered the most significant result.
Figure 7 shows a graphic depiction of
Table 6.
According to the figure, the proposed classification model performed less optimally on the “sLoss” and “sWin” classes compared to other label types. Through testing, we discovered that the properties of “sLoss” and “sWin” shared many of the same features. Therefore, to correctly classify the traffic data of these classes, the classifiers need more significant features, because our model combines the efficient ABC algorithm to select significant features. However, the overall model accuracy in distinguishing target classes was quite high for “sLoss” and “sWin” target labels, at 99.00% and 99.28%, respectively. This will lead to improving the overall accuracy of the classifier.
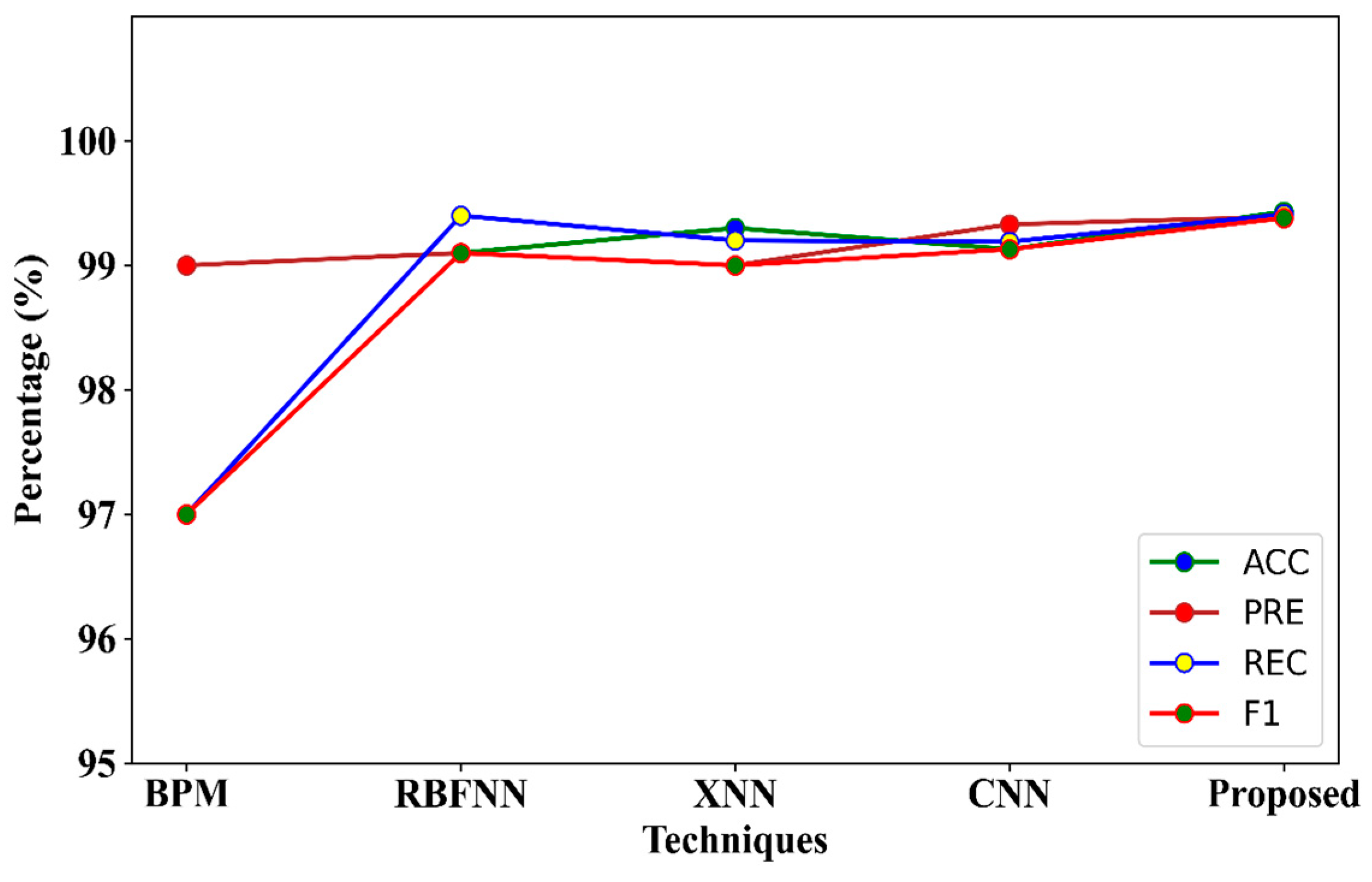
The suggested technique’s comparison to various existing intrusion detection algorithms is shown in
Table 7 and
Figure 8. The existing techniques, such as radial basis function neural network (RBFNN), Bayes point machine (BPM), explainable neural network (XNN), and convolutional neural network (CNN) were used. From the table, it is observed that the proposed strategy attained 99.58% accuracy compared to all the other state-of-the-art methods on the UNSW_NB15 dataset; also, it is observed that the overall accuracy was improved with CNN more than other methods. This might be due to the fact that the correlation between target features is better learned by a convolution kernel than other shallow networks. However, in terms of precision, all the techniques achieved better results.
4.2.4. Impact of Feature Selection Approach
By selecting the most pertinent aspects from the collected features, a binary POA method is applied to improve the suggested intrusion detection methodology. On the Bot-IoT, CICIDS2017, and UNSW_NB15 datasets, the ABC-based technique minimized the number of features and presented more information.
Table 8 provides the proposed model performance feature selection criterion.
Table 8 shows that using an efficient ABC-based feature selection approach enhanced the performance of the suggested strategy. Without the feature selection process, it achieved only 99.29%, 99.17%, and 99.32% accuracy for Bot-IoT, CICIDS2017, and UNSW_NB15 datasets, respectively. After the feature selection process, the classifier’s performance was increased with the optimal set of features and achieved the best results without the feature selection technique. Finally, we hope that the proposed system will be effective in various real-world applications, particularly in bolstering cybersecurity measures against DoS and DDoS attacks. The integration of advanced deep learning techniques, such as the pyramid atrous attention module and the convolutional block attention module, enhances the accuracy and efficiency of intrusion detection systems. We plan to develop a small model with reliable cyberattack detection performance using YOLOv, dilated CNNs and weighted non-negative matrix factorization (WNMF) in IoT environments [
73,
74,
75,
76,
77].
5. Conclusions
The demand for using more precise and effective IDS has grown more critical due to the quick increase in network traffic and the development of intrusions. Therefore, a deep learning-based network intrusion detection was implemented in this research. The outcomes demonstrated the performance of the proposed approach in terms of recognizing and categorizing cyber-security threats. Different performance metrics, including accuracy, F-score, recall (sensitivity), and precision (detection rate) were used in the evaluation process to analyze the usefulness of the suggested models on the three benchmark datasets. In contrast to previous attack detection techniques, the proposed framework achieved superior results with 99.38%, 99.26%, and 99.43% accuracy for Bot-IoT, CICIDS2017, and UNSW_NB15 datasets, respectively. This outcome was attained by the ABC-based feature selection method, which improved the data quality. Based on the findings of this study, it is determined that the recommended model will help create a successful intrusion detection system with a high detection rate. In the forthcoming endeavors, there will be a focus on refining the suggested IDS to detect different categories of attacks. Furthermore, the suggested approach has the potential to be adapted and utilized in a robust security application.