A Network Intrusion Detection Method Incorporating Bayesian Attack Graph and Incremental Learning Part
Abstract
1. Introduction
2. Related Works
3. A Network Intrusion Detection Method Incorporating a Bayesian Attack Graph and IL
3.1. The Generation of Bayesian Attack Graphs
3.2. IL Intrusion Detection Method Based on XGBoost
4. Performance Analysis of Network Intrusion Detection Methods Incorporating Bayesian Attack Graph and IL
4.1. Path Prediction Experiments with Bayesian Attack Graphs
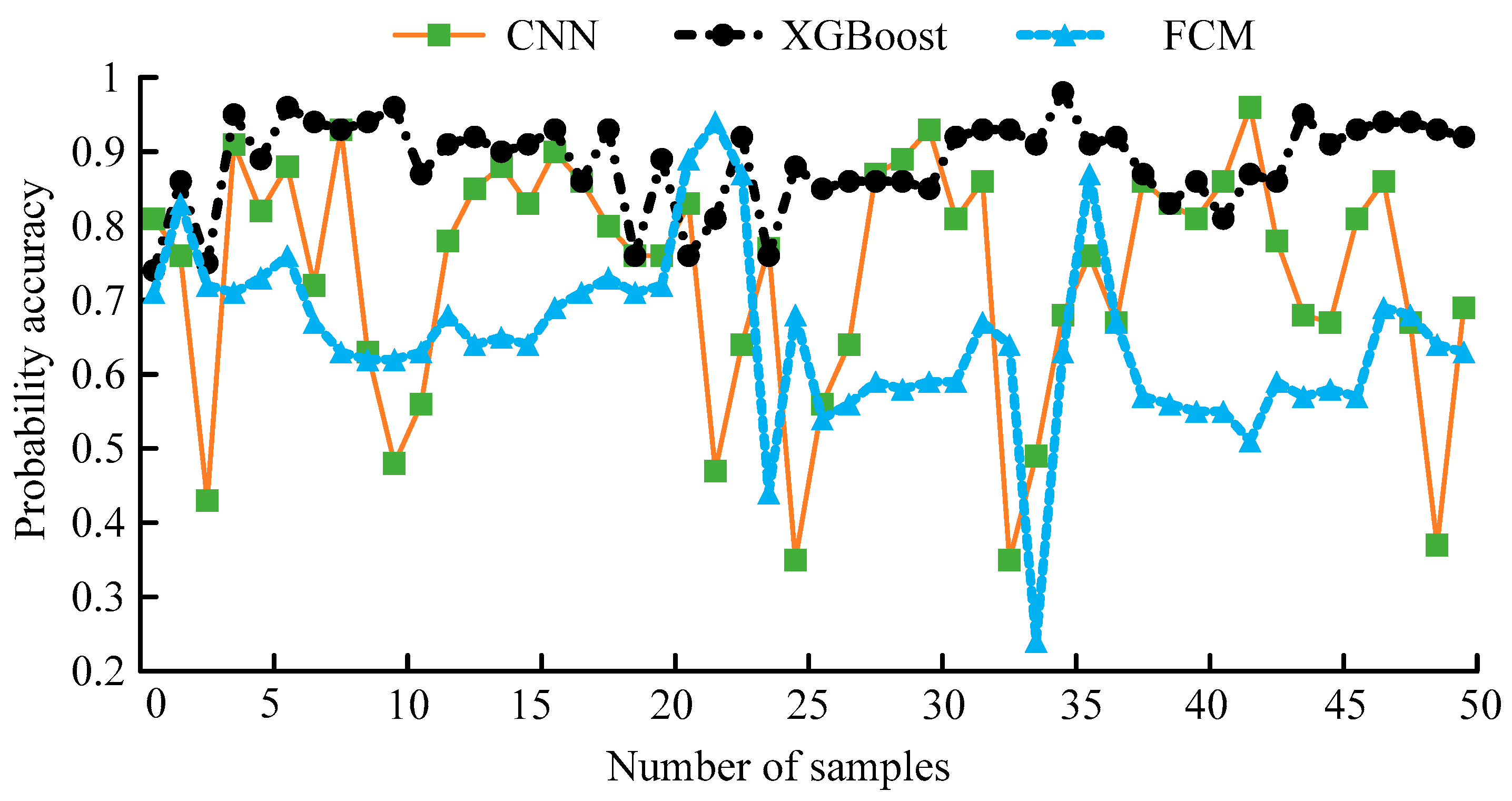
4.2. IL for Intrusion Detection Performance Verification Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mishra, P.; Varadharajan, V.; Tupakula, U.S.; Pilli, E. A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE Commun. Surv. Tutor. 2018, 21, 686–728. [Google Scholar] [CrossRef]
- Shone, N.; Ngoc, T.N.; Phai, V.D.; Shi, Q. A deep learning approach to network intrusion detection. IEEE Trans. Emerg. Top. Comput. Intell. 2018, 2, 41–50. [Google Scholar] [CrossRef]
- Gao, X.; Shan, C.; Hu, C.; Niu, Z.; Liu, Z. An adaptive ensemble machine learning model for intrusion detection. IEEE Access 2019, 7, 82512–82521. [Google Scholar] [CrossRef]
- Ramos, M.D.; Foster, A.D.; Felici, S.; Fos, V.G.; Solano, J.J.P. Gatherer: An environmental monitoring application based on IPv6 using wireless sensor networks. Int. J. Ad Hoc Ubiquitous Comput. 2013, 13, 209–217. [Google Scholar] [CrossRef]
- Segura-Garcia, J.; Calero, J.M.A.; Pastor-Aparicio, A.; Marco-Alaez, R.; Felici-Castell, S.; Wang, Q. 5G IoT system for real-time psycho-acoustic soundscape monitoring in smart cities with dynamic computational offloading to the edge. IEEE Internet Things J. 2021, 8, 12467–12475. [Google Scholar] [CrossRef]
- Kim, M. ML/CGAN: Network attack analysis using CGAN as meta-learning. IEEE Commun. Lett. 2020, 25, 499–502. [Google Scholar] [CrossRef]
- Públio, M.L.; Marcos Vinícius, S.A.; Lilian, K.C.; Marcos, V.M. Security against communication network attacks of cyber-physical systems. J. Control Autom. Electr. Syst. 2019, 30, 125–135. [Google Scholar]
- Wu, H.; Gu, Y.; Cheng, G.; Zhou, Y. Effectiveness evaluation method for cyber deception based on dynamic bayesian attack graph. In Proceedings of the 2020 3rd International Conference on Computer Science and Software Engineering, Beijing, China, 22–24 May 2020; pp. 1–9. [Google Scholar]
- Kaynar, K.; Sivrikaya, F. Distributed attack graph generation. IEEE Trans. Dependable Secur. Comput. 2015, 13, 519–532. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y.; Cao, Y. Searching forward complete attack graph generation algorithm based on hypergraph partitioning. Procedia Comput. Sci. 2017, 107, 27–38. [Google Scholar] [CrossRef]
- Al Ghazo, A.T.; Ibrahim, M.; Ren, H. A2G2V: Automatic attack graph generation and visualization and its applications to computer and SCADA networks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 50, 3488–3498. [Google Scholar] [CrossRef]
- Garcia-Pineda, M.; Segura-Garcia, J.; Felici-Castell, S. A holistic modeling for QoE estimation in live video streaming applications over LTE Advanced technologies with Full and Non Reference approaches. Comput. Commun. 2018, 117, 13–23. [Google Scholar] [CrossRef]
- Chapaneri, R.; Shah, S. Multi-level Gaussian mixture modeling for detection of malicious network traffic. J. Supercomput. 2021, 77, 4618–4638. [Google Scholar] [CrossRef]
- Wang, H.; Gu, J.; Wang, S. An effective intrusion detection framework based on SVM with feature augmentation. Knowl. Based Syst. 2017, 136, 130–139. [Google Scholar] [CrossRef]
- Gu, J.; Lu, S. An effective intrusion detection approach using SVM with naïve Bayes feature embedding. Comput. Secur. 2021, 103, 102158. [Google Scholar] [CrossRef]
- Hakim, L.; Fatma, R. Influence analysis of feature selection to network intrusion detection system performance using nsl-kdd dataset. In Proceedings of the 2019 International Conference on Computer Science, Information Technology, and Electrical Engineering (ICOMITEE), Jember, Indonesia, 16–17 October 2019; pp. 217–220. [Google Scholar]
- Laghrissi, F.E.; Douzi, S.; Douzi, K.; Hssina, B. Intrusion detection systems using long short-term memory (LSTM). J. Big Data 2021, 8, 65. [Google Scholar] [CrossRef]
- Alsughayyir, B.; Qamar, A.M.; Khan, R. Developing a network attack detection system using deep learning. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS), Aljouf, Saudi Arabia, 3–4 April 2019; pp. 1–5. [Google Scholar]
- Belouch, M.; El Hadaj, S.; Idhammad, M. Performance evaluation of intrusion detection based on machine learning using apache spark. Procedia Comput. Sci. 2018, 127, 1–6. [Google Scholar] [CrossRef]
- Poolsappasit, N.; Dewri, R.; Ray, I. Dynamic Security Risk Management Using Bayesian Attack Graphs. IEEE Trans. Dependable Secur. Comput. 2012, 9, 61–74. [Google Scholar] [CrossRef]
- Polatidis, N.; Pimenidis, E.; Pavlidis, M.; Papastergiou, S.; Mouratidis, H. From product recommendation to cyber-attack prediction: Generating attack graphs and predicting future attacks. Evol. Syst. 2020, 11, 479–490. [Google Scholar] [CrossRef]
- Yazdi, M.; Kabir, S.; Walker, M. Uncertainty handling in fault tree based risk assessment: State of the art and future perspectives. Process Saf. Environ. Prot. 2019, 131, 89–104. [Google Scholar] [CrossRef]



| Literature Field | Literature Number | Sketch |
|---|---|---|
| Introduction to Network Attack | [1,2,3] | Network intrusion security literature introduced in the background |
| Wireless sensor networks | [4,5] | Modern English for Wireless Sensor Networks Introduced as a Background |
| DL | [6,7] | Application of DL in Network Technology |
| Network Intrusion Attack Graph Technology | [7,8,9,10,11,20] | Optimization results of attack graph technology by domestic and foreign scholars |
| Other network security information technology | [12,13,14,15,16,17] | Domestic and foreign scholars’ detection methods for network intrusion |
| Internet of Things and Computer Communication | [17,18,19,21] | Research on new application of network security technology and information transmission |
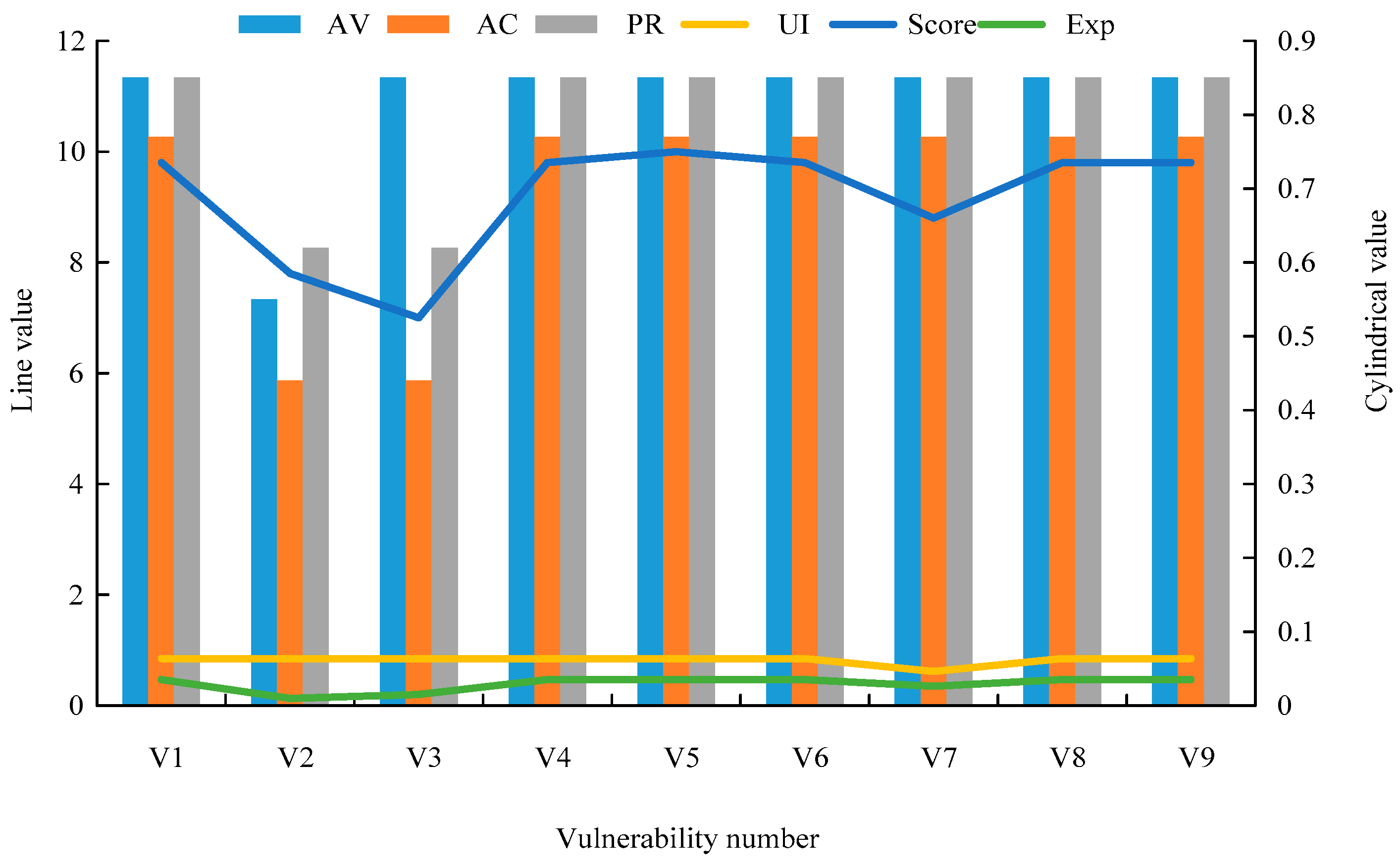
| Host Name | Function Description | Host Number | Vulnerability Name | Vulnerability Number |
|---|---|---|---|---|
| Apache server | Provide Web Server services | H1 | CVE-2020-13942 | V1 |
| CVE-2020-15778 | V2 | |||
| Mail server | Be responsible for email sending and receiving management | H2 | CVE-2018-19518 | V3 |
| CVE-2018-6789 | V4 | |||
| DNS server | Domain name resolves to IP address | H3 | CVE-2020-1350 | V5 |
| PC | Personal office machine | H4 | CVE-2019-0708 | V6 |
| CVE-2021-1675 | V7 | |||
| FTP server | Provide file storage and access services | H5 | CVE-2019-12815 | V8 |
| MySQL server | Provide database services | H6 | CVE-2016-6662 | V9 |
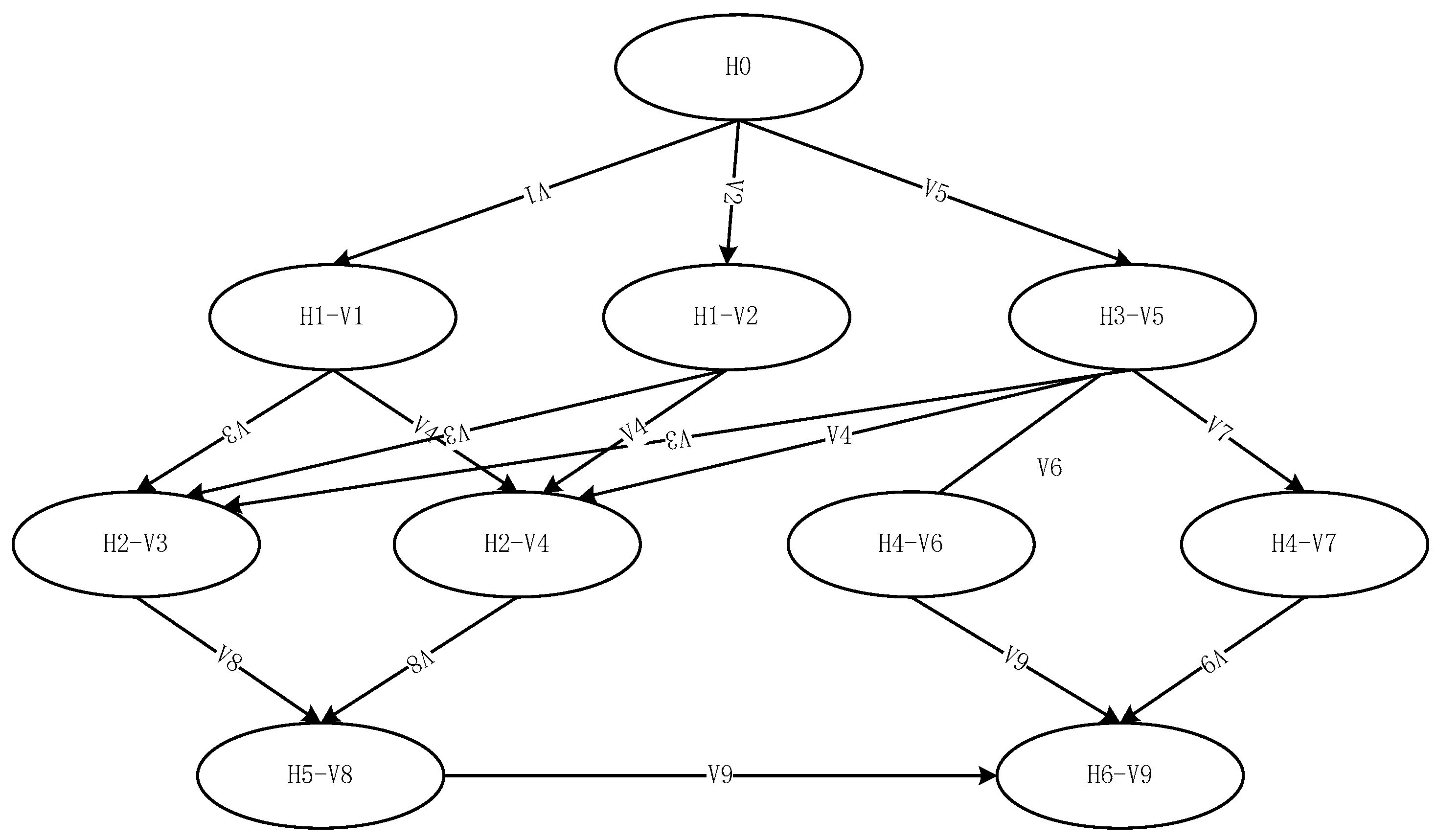
| Node | Node Reachability Probability | Path Number | Route | Path Reachability Probability |
|---|---|---|---|---|
| H1-V1 | 0.46 | Path-A | H0→H1-V1→H2-V3→H5-V8→H6-V9 | 0.0036 |
| H1-V2 | 0.1 | Path-B | H0→H1-V1→H2-V4→H5-V8→H6-V9 | 0.0116 |
| H2-V3 | 0.13 | Path-C | H0→H1-V2→H2-V3→H5-V8→H6-V9 | 0.0008 |
| H2-V4 | 0.41 | Path-D | H0→H1-V2→H2-V4→H5-V8→H6-V9 | 0.0032 |
| H3-V5 | 0.47 | Path-E | H0→H3-V5→H2-V3→H5-V8→H6-V9 | 0.0037 |
| H4-V6 | 0.22 | Path-F | H0→H3-V5→H2-V4→H5-V8→H6-V9 | 0.0116 |
| H4-V7 | 0.14 | Path-G | H0→H3-V5→H4-V6→H6-V9 | 0.0259 |
| H5-V8 | 0.24 | Path-H | H0→H3-V5→H4-V7→H6-V9 | 0.0165 |
| H6-V9 | 0.25 | / | / | / |
| Date | Number of Samples | Date | Number of Samples |
|---|---|---|---|
| 14 February 2018 | 392,909 | 22 February 2018 | 443,070 |
| 15 February 2018 | 426,094 | 23 February 2018 | 445,761 |
| 16 February 2018 | 470,336 | 28 February 2018 | 470,336 |
| 20 February 2018 | 3,447,677 | 1 March 2018 | 128,073 |
| 21 February 2018 | 522,559 | 2 March 2018 | 517,200 |
| / | Acc | Prec | Re | f1-Score | AUC |
|---|---|---|---|---|---|
| Base model | 0.734 | 0.602 | 0.001 | 0.002 | 0.500 |
| IL | 0.951 | 0.999 | 0.815 | 0.898 | 0.907 |
| Full training | 0.949 | 0.999 | 0.807 | 0.893 | 0.904 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, K.; Qu, H.; Huang, C. A Network Intrusion Detection Method Incorporating Bayesian Attack Graph and Incremental Learning Part. Future Internet 2023, 15, 128. https://doi.org/10.3390/fi15040128
Wu K, Qu H, Huang C. A Network Intrusion Detection Method Incorporating Bayesian Attack Graph and Incremental Learning Part. Future Internet. 2023; 15(4):128. https://doi.org/10.3390/fi15040128
Chicago/Turabian StyleWu, Kongpei, Huiqin Qu, and Conggui Huang. 2023. "A Network Intrusion Detection Method Incorporating Bayesian Attack Graph and Incremental Learning Part" Future Internet 15, no. 4: 128. https://doi.org/10.3390/fi15040128
APA StyleWu, K., Qu, H., & Huang, C. (2023). A Network Intrusion Detection Method Incorporating Bayesian Attack Graph and Incremental Learning Part. Future Internet, 15(4), 128. https://doi.org/10.3390/fi15040128





