A Systematic Literature Review on Authentication and Threat Challenges on RFID Based NFC Applications
Abstract
1. Introduction
2. Research Methodology
2.1. Elementary Exploration
- Keyword 1 = “Mifare” “Threats”
- Keyword 2 = “Mifare” (“Security” OR “Authentication”).
2.2. Extraction Criteria and Primary Results
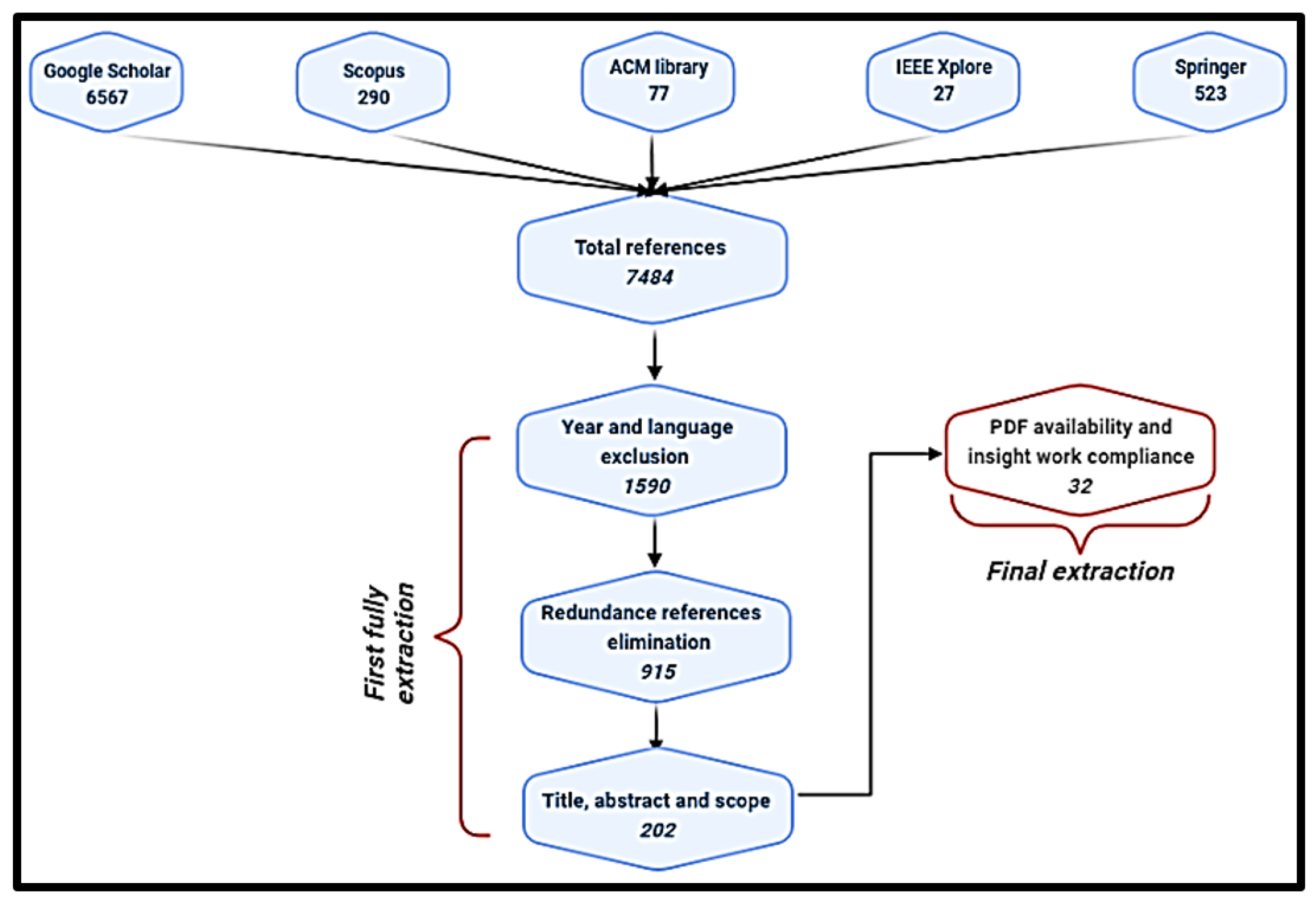
- Another metric was taken into consideration, which was the language utilized by the authors. Thus, only results written in English were included. Due to this metric, the number of explored studies decreased from 2138 to 1590, which represents 74.36% of the results we obtained after the first extraction.
- Checking for duplicates in the 1590 studies included in the SLR should be performed to avoid a study being double-analyzed or -checked. As a result, the number of studies decreased from 1590 to 915 (57.54%).
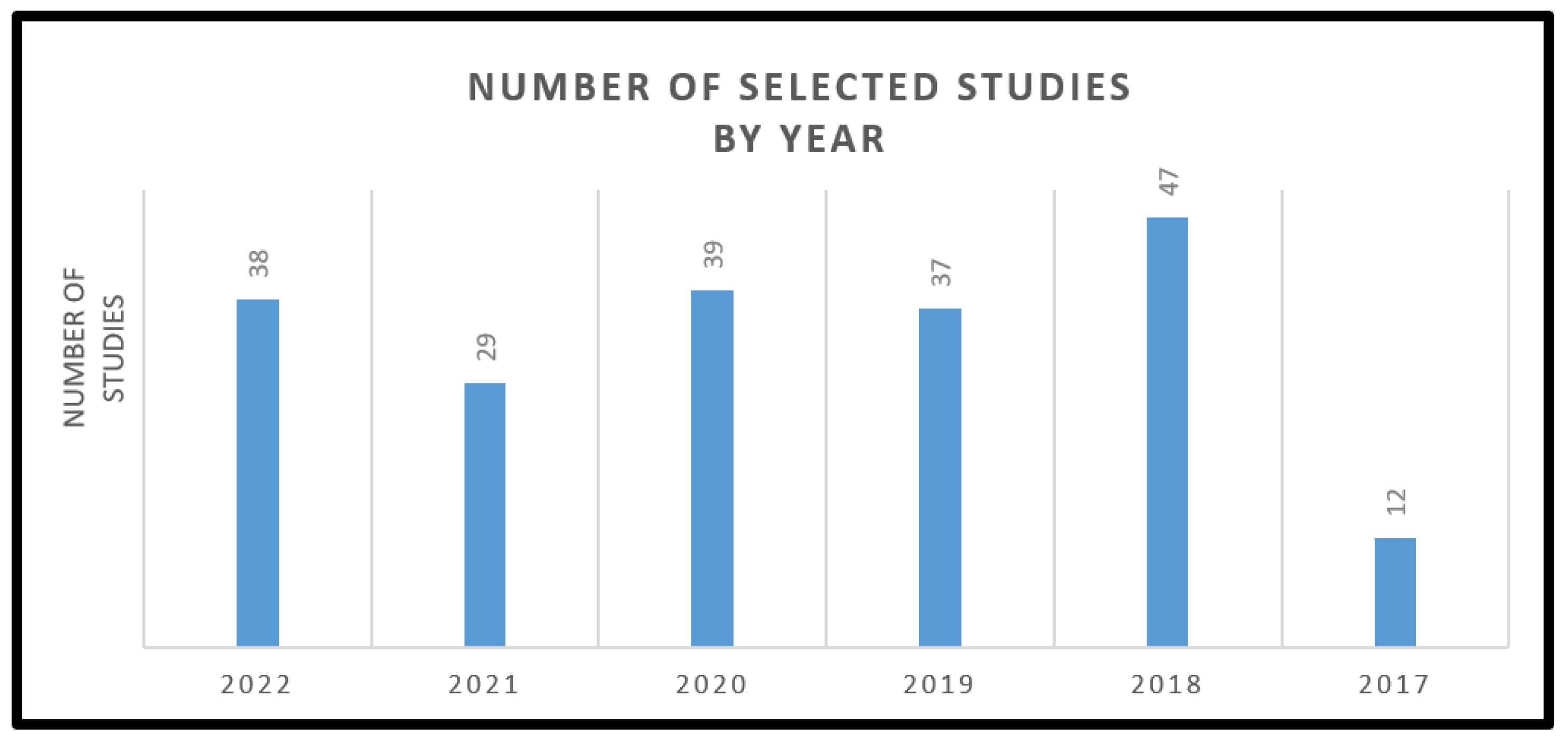
- Last, but not least, an extraction built on the title, abstract, and scope of research was deemed for the sake of organizing the work. Further, to further scrutinize the existent implementations that had a quite similar vision as ours, 202 out of the 915 (22.07%) were selected to be utilized to accomplish the intended SLR (first full extraction). The distribution of these studies by year is shown in Figure 1 and Table 4.
- Another criterion that was borne in mind was the article’s availability and its perceived compliance. At this stage, we determined whether the realized study had a strong link with our principal insight. Only 32 out of the 202 studies were selected to go through the realization process (final extraction); see Figure 2.
3. RFID Security and Threats
3.1. RFID Challenges
- Code division multi-access: This is built by multiplying the tag ID by a pseudo-random sequence before the data transmission. This method offers security to the communication between the reader and the tag; however, it has some high demands such as computation, along with enhancing the complexity.
- Frequency division multi-access: This refers to the utilization of frequency ranges for the sake of recognizing tags. At such a level, each tag must belong to a specific frequency. FDMA seems expensive to implement and it is not designed for general employment.
- Space division multi-access: Its main concern is to split the channel into distinct areas to enhance the channel’s connection capability. Unfortunately, SDMA is extremely costly and requires some complex designs for the antennas.
- Time division multi-access: This approach is widely used and covers many anti-collision algorithms. TDMA divides the transmission channel between tags to ensure the reader’s identification ability at separate times to overcome interference. This method is not costly and reduces the number of tag interrogations after each successful response (broadcast message response).
3.2. RFID Security Threats
- Tracking: This is known as the act of reading RFID tags without the proper authorization by the use of a considerable number of RFID readers to gather their identifiers, and these identifiers can be personal credit card numbers [10].
- Counterfeiting: This attack manipulates the tag, where a smaller amount of information is needed. Here, circumventing the security mechanisms utilized is the main objective of the counterfeiting threat [10].
- Eavesdropping: This attack is based on saving the read intercepted communication with the intention to be re-used for analysis and as a baseline for another type of attack such as tag cloning attacks [7].
- Tags cloning: Its major purpose is to duplicate a reliable tag as a copy to be used for unauthorized access to the reader’s information with the intention of extracting data to be stored in another tag. Tag cloning leads to several damages such as the manufacturer’s reputation and some serious financial losses [7].
- Physical attacks: Its main concern is to tamper with the tag physically by damaging one of its components or disrupting its normal performance by glitching the tag’s clock or changing the transmitted radio frequencies, and we can mention side channel and timing attacks [10].
- DoS attack: The is a denial of service, where the intruder tries to take the tag out of service. Consequently, no information will be leaked or occupied. However, it reduces the RFID system’s efficiency and faithfulness. The concept of realizing a DoS attack is to interfere with the signals of the channels used for the tags’ radio frequency communications [10].
4. RFID Security Solutions
5. Discussion
- Healthcare applications: Due to the real-time demand of data, low-cost cryptosystems are preferred, and we can mention the Tiny Encryption Algorithm (TEA) and Mickey ciphers. However, some critical changes must be made at the core of both algorithms because of the low resistance of to a manifold of types of attacks such as side channel attacks and the weak avalanche abilities, which reduce the cryptosystem’s trustworthiness. For this reason, advanced or improved versions of both algorithms are suggested.
- E-payment: Because of the high sensitivity of the exchanged data between smart cards, readers, and connected databases that are related to banks, the higher the security, the more confident the system becomes. Therefore, it is suggested to employ the public key infrastructure concept within digital signatures to provide authenticity and confidentiality to users.
- E-voting: A card can be issued to every eligible citizen to vote in his/her country’s elections. This can be a one-time utilization card, where robust cryptosystems are implemented to avoid vote corruption. Homomorphic cryptography along with other algorithms such as AES can be combined to offer the utmost possible security.
- Other applications: The cost, performance, and security trade-off must always be kept in mind by developers. Security requires computational abilities that obviously decrease the application’s performance, a fact that directly enhances the cost and vice versa.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| BAN | Burrows–Abadi–Needham |
| CDMA | Code Division Multi-Access |
| CRC | Cyclic Redundancy Check |
| DSA | Digital Signature Algorithm |
| ECC | Elliptic Curve Cryptography |
| FDMA | Frequency Division Multi-Access |
| MD5 | Message Digest 5 |
| MFA | Multi-Factor Authentication |
| NFC | Near-Field Communications |
| PBE | Password-Based Encryption |
| PKI | Public Key Infrastructure |
| PRNG | Pseudo-Random Number Generation |
| RC | Rivest Code |
| RFID | Radio Frequency Identification |
| VGG | Visual Geometry Group |
| RESNET | Residual Neural Network |
| SHA | Secure Hash Algorithm |
| SDMA | Space Division Multi-Access |
| TDMA | Time Division Multi-Access |
| TEA | Tiny Encryption Algorithm |
References
- El Gaabouri, I.; Senhadji, M.; Belkasmi, M. A Survey on Lightweight Cryptography Approach for IoT Devices Security. In Proceedings of the 2022 5th International Conference on Networking, Information Systems and Security: Envisage Intelligent Systems in 5g//6G-based Interconnected Digital Worlds (NISS), Bandung, Indonesia, 30–31 March 2022; pp. 1–8. [Google Scholar]
- El Mouaatamid, O.; Lahmer, M.; Belkasmi, M. Internet of Things Security: Layered classification of attacks and possible Countermeasures. Electron. J. Inf. Technol. 2016, 9, 66–80. [Google Scholar]
- Baashirah, R.; Abuzneid, A. Survey on prominent RFID authentication protocols for passive tags. Sensors 2018, 18, 3584. [Google Scholar] [CrossRef] [PubMed]
- Maarof, A.; Senhadji, M.; Labbi, Z.; Belkasmi, M. Security analysis of low cost RFID systems. In Proceedings of the 2014 5th Workshop on Codes, Cryptography and Communication Systems (WCCCS), El Jadida, Morocco, 27–28 November 2014; pp. 11–16. [Google Scholar]
- Costa, F.; Genovesi, S.; Borgese, M.; Michel, A.; Dicandia, F.A.; Manara, G. A review of RFID sensors, the new frontier of internet of things. Sensors 2021, 21, 3138. [Google Scholar] [CrossRef]
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946. [Google Scholar] [CrossRef]
- Kumar, A.; Jain, A.K.; Dua, M. A comprehensive taxonomy of security and privacy issues in RFID. Complex Intell. Syst. 2021, 7, 1327–1347. [Google Scholar] [CrossRef]
- Landaluce, H.; Arjona, L.; Perallos, A.; Falcone, F.; Angulo, I.; Muralter, F. A review of IoT sensing applications and challenges using RFID and wireless sensor networks. Sensors 2020, 20, 2495. [Google Scholar] [CrossRef]
- Cmiljanic, N.; Landaluce, H.; Perallos, A. A comparison of RFID anti-collision protocols for tag identification. Appl. Sci. 2018, 8, 1282. [Google Scholar] [CrossRef]
- Damghani, H.; Hosseinian, H.; Damghani, L. Investigating attacks to improve security and privacy in RFID systems using the security bit method. In Proceedings of the 2019 5th Conference on Knowledge Based Engineering and Innovation (KBEI), Tehran, Iran, 28 February–1 March 2019; pp. 833–838. [Google Scholar]
- Adeniji, O.D.; Akinola, O.E.; Adesina, A.O.; Afolabi, O. Text Encryption with Advanced Encryption Standard (AES) for Near Field Communication (NFC) Using Huffman Compression. In Proceedings of the Applied Informatics: 5th International Conference, ICAI 2022, Arequipa, Peru, 27–29 October 2022; pp. 158–170. [Google Scholar]
- Olaniyi, O.; Dogo, E.; Nuhu, B.; Treiblmaier, H.; Abdulsalam, Y.; Folawiyo, Z. A Secure Electronic Voting System Using Multifactor Authentication and Blockchain Technologies. In Blockchain Applications in the Smart Era; Springer: Berlin/Heidelberg, Germany, 2022; pp. 41–63. [Google Scholar]
- Vivek Raj, K.; Navya, N.; Madhushree, P.; Anjali, K.; Soundarya, B. RFID-Based Secure Multipurpose Smart Card Using Arduino Module. In Proceedings of the Third International Conference on Intelligent Computing, Information and Control Systems: ICICCS 2021, Secunderabad, India, 14–17 July 2022; pp. 403–415. [Google Scholar]
- Arslan, A.; Çolak, S.A.; Ertürk, S. A secure and privacy friendly ECC based RFID authentication protocol for practical applications. Wirel. Pers. Commun. 2021, 120, 2653–2691. [Google Scholar] [CrossRef]
- Dreyer, J.; Fischer, M.; Tönjes, R. NFC Key Exchange-A light-weight approach to authentic Public Key Exchange for IoT devices. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), Yokohama, Japan, 26 October–11 November 2021; pp. 374–379. [Google Scholar]
- Noprianto, N.; Wijayaningrum, V.N. Smart card security mechanism with dynamic key. J. Infotel 2021, 13, 197–204. [Google Scholar] [CrossRef]
- Benamara, N.K.; Keche, M.; Wellington, M.; Munyaradzi, Z. Securing E-payment Systems by RFID and Deep Facial Biometry. In Proceedings of the 2021 1st International Conference on Artificial Intelligence and Data Analytics (CAIDA), Riyadh, Saudi Arabia, 6–7 April 2021; pp. 151–157. [Google Scholar]
- Basjaruddin, N.C.; Ramadhan, S.; Asyikin, M.B.Z.; Indrianty, Y. Baggage Tracing and Passenger Management System in Airport Based on NFC Using Homomorphic Cryptography. In Proceedings of the International Seminar of Science and Applied Technology (ISSAT 2020), Online, 24–25 November 2020; pp. 296–301. [Google Scholar]
- Suyitno, D.; Aladhirus, B.R.; Wardhani, R.W. Design and Implementation of Smart Card based Secure Key Storage The Blockchain E-voting Application. In Proceedings of the 2020 1st International Conference on Information Technology, Advanced Mechanical and Electrical Engineering (ICITAMEE), Yogyakarta, Indonesia, 13–14 October 2020; pp. 259–264. [Google Scholar]
- Chikouche, N.; Cherif, F. EAP-SRES: An Enhanced Authentication Protocol for Secure Remote Education Systems Using NFC Technology. Int. J. Comput. Digit. Syst. 2020, 9, 3. [Google Scholar]
- Alamer, A.; Soh, B.; Alahmadi, A.H.; Brumbaugh, D.E. Prototype device with lightweight protocol for secure RFID communication without reliable connectivity. IEEE Access 2019, 7, 168337–168356. [Google Scholar] [CrossRef]
- Arulmozhi, P.; Rayappan, J.; Raj, P. A lightweight memory-based protocol authentication using radio frequency identification (rfid). In Advances in Big Data and Cloud Computing: Proceedings of ICBDCC18; Springer: Berlin/Heidelberg, Germany, 2019; pp. 163–172. [Google Scholar]
- Zhang, Y.; Guin, U. End-to-end traceability of ICs in component supply chain for fighting against recycling. IEEE Trans. Inf. Forensics Secur. 2019, 15, 767–775. [Google Scholar] [CrossRef]
- Kang, J. Lightweight mutual authentication RFID protocol for secure multi-tag simultaneous authentication in ubiquitous environments. J. Supercomput. 2019, 75, 4529–4542. [Google Scholar] [CrossRef]
- Putra, I.G.S.E.; Labasariyani, N.L.P. Design and Development of Login Security System Using Radio Frequency Identification. Logic J. Ranc. Bangun Dan Teknol. 2019, 19, 41–46. [Google Scholar] [CrossRef]
- Soe, N.; Aung, T.H. Implementation of Secure Electronic Payment System Using RFID and ECC Digital Signature. Int. J. Sci. Eng. Technol. Res. 2019, 8, 6. [Google Scholar]
- Rzouga Haddada, L.; Essoukri Ben Amara, N. Double watermarking-based biometric access control for radio frequency identification card. Int. J. Microw. Comput. Aided Eng. 2019, 29, e21905. [Google Scholar] [CrossRef]
- Insan, I.M.; Sukarno, P.; Yasirandi, R. Multi-factor authentication using a smart card and fingerprint (case study: Parking gate). Indones. J. Comput. 2019, 4, 55–66. [Google Scholar]
- Abdulsalam, Y.S.; Olaniyi, O.M.; Ahmed, A. Enhanced tiny encryption algorithm for secure electronic health authentication system. Int. J. Inf. Privacy Secur. Integr. 2018, 3, 230–252. [Google Scholar] [CrossRef]
- Cetinkaya, M.; Dede, J.; Förster, A. An RFID Based Secure Key and Configuration Distribution for Contiki. In Proceedings of the EWSN, Madrid, Spain, 14–16 February 2018; pp. 189–190. [Google Scholar]
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A lightweight RFID mutual authentication protocol based on physical unclonable function. Sensors 2018, 8, 760. [Google Scholar] [CrossRef]
- Villanueva, E.B.; Gerardo, B.D.; Medina, R.P. Implementation of the Enhanced RC5 (ERC5) Algorithm in an RFID-based Payment Scheme. In Proceedings of the 2nd International Conference on Business and Information Management, Barcelona, Spain, 20–22 September 2018; pp. 6–10. [Google Scholar]
- Malina, L.; Dzurenda, P.; Hajny, J.; Martinasek, Z. Secure and efficient two-factor zero-knowledge authentication solution for access control systems. Comput. Secur. 2018, 77, 500–513. [Google Scholar] [CrossRef]
- Liu, B.; Yang, B.; Su, X. An improved two-way security authentication protocol for RFID system. Information 2018, 9, 86. [Google Scholar] [CrossRef]
- Nurdiyanto, H.; Rahim, R.; Hidayat, R.; Harliana, P.; Gunawan, G.; Adam, H.; Sonatha, Y.; Azmi, M. Authentication Security in Radio Frequency Identification with IDEA Algorithm. In Proceedings of the IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2018; Volume 384, p. 012042. [Google Scholar]
- Álvarez-Dίaz, N.; Caballero-Gil, P.; Burmester, M. A luggage control system based on NFC and homomorphic cryptography. Mob. Inf. Syst. J. 2017, 2017, 2095161. [Google Scholar]
- Younis, M.I.; Abdulkareem, M.H. ITPMAP: An improved three-pass mutual authentication protocol for secure RFID systems. Wirel. Pers. Commun. J. 2017, 96, 65–101. [Google Scholar] [CrossRef]
- Olaniyi, O.M.; Arulogun, O.T.; Omotosho, A.; Onuh, V.O. Securing clinic tele-diagnostic system using enhanced tiny encrypted radio frequency identification and image steganographic technique. Int. J. Telemed. Clin. Pract. 2017, 2, 242–266. [Google Scholar] [CrossRef]
- Chien, H.Y. Elliptic curve cryptography-based RFID authentication resisting active tracking. Wirel. Pers. Commun. 2017, 94, 2925–2936. [Google Scholar] [CrossRef]
- Chien, H.Y. Efficient authentication scheme with tag-identity protection for EPC Class 2 Generation 2 version 2 standards. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717697321. [Google Scholar] [CrossRef][Green Version]
- Ratnadewi, R.; Adhie, R.; Hutama, Y.; Christian, J.; Wijaya, D. Implementation and performance analysis of AES-128 cryptography method in an NFC-based communication system. World Trans. Eng. Technol. Educ. 2017, 15, 178–183. [Google Scholar]
- Naija, Y.; Beroulle, V.; Machhout, M. Low cost countermeasure at authentication protocol level against electromagnetic side channel attacks on RFID tags. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 11. [Google Scholar] [CrossRef]
| Exclusion Criteria | Inclusion Criteria |
|---|---|
| Publications came from predatory journals or conferences. | Journals’ and conferences’ credibility. |
| Published before 2012. | Published after 2012. |
| Studies not written in English. | Studies written in English. |
| The studies did not address smart card RFID security. | The studies directly addressed smart card RFID security. |
| Database | All References | After 2012 | After 2017 | English Only and after 2017 |
|---|---|---|---|---|
| Google Scholar | 877 | 556 | 217 | 186 |
| Scopus | 52 | 31 | 13 | 13 |
| ACM library | 18 | 14 | 6 | 6 |
| IEEE Xplore | 1 | 1 | 1 | 1 |
| SpringerLink | 147 | 99 | 52 | 52 |
| Total | 1095 | 701 | 289 | 258 |
| Database | All References | After 2012 | After 2017 | English Only and after 2017 |
|---|---|---|---|---|
| Google Scholar | 5690 | 3640 | 1660 | 1150 |
| Scopus | 238 | 92 | 42 | 42 |
| ACM library | 59 | 34 | 14 | 14 |
| IEEE Xplore | 26 | 20 | 11 | 11 |
| SpringerLink | 376 | 250 | 122 | 115 |
| Total | 6389 | 4036 | 1849 | 1332 |
| Year of study | 2017 | 2018 | 2019 | 2020 | 2021 | 2022 | All |
| Total of number of studies | 38 | 29 | 39 | 37 | 47 | 12 | 202 |
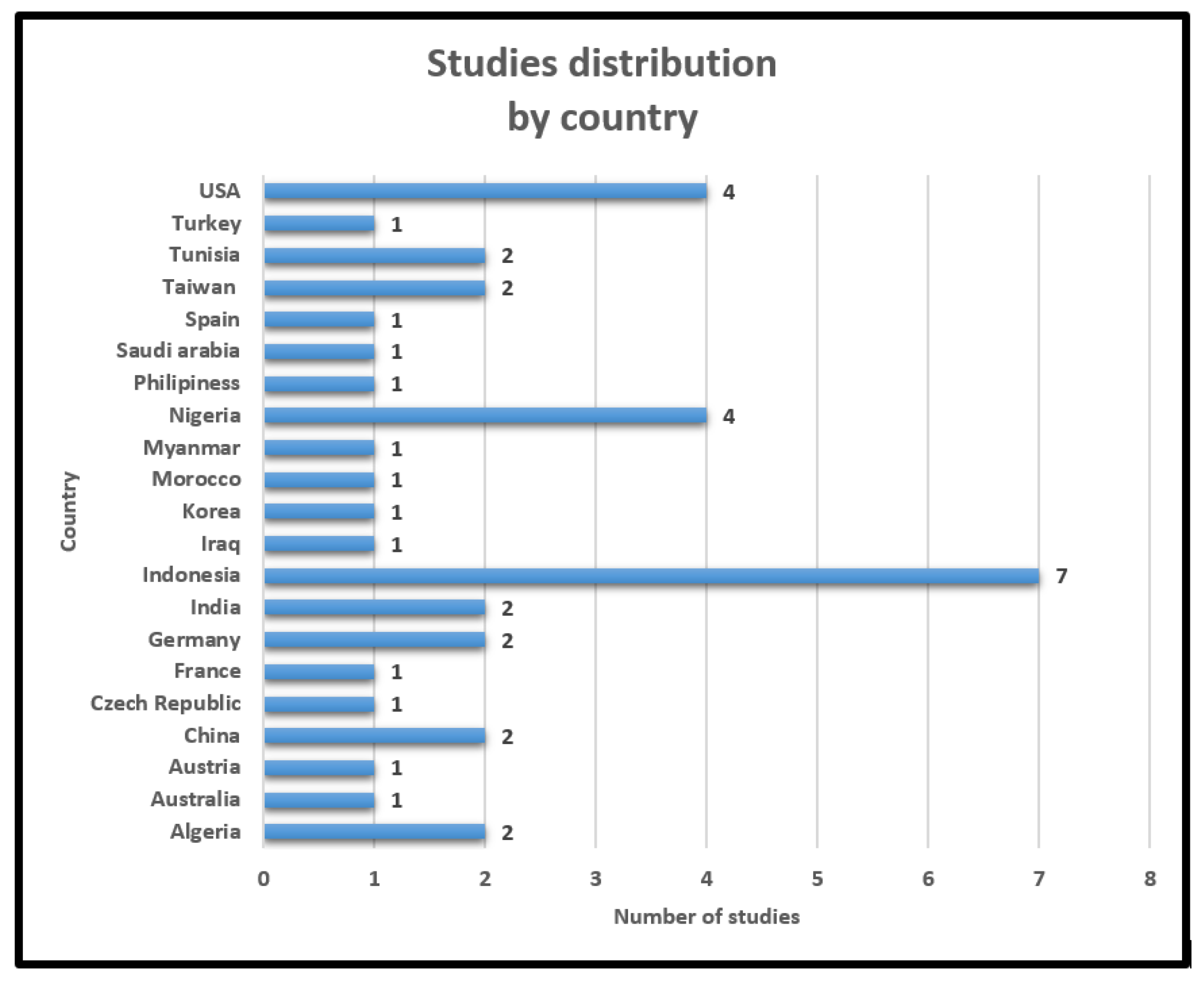
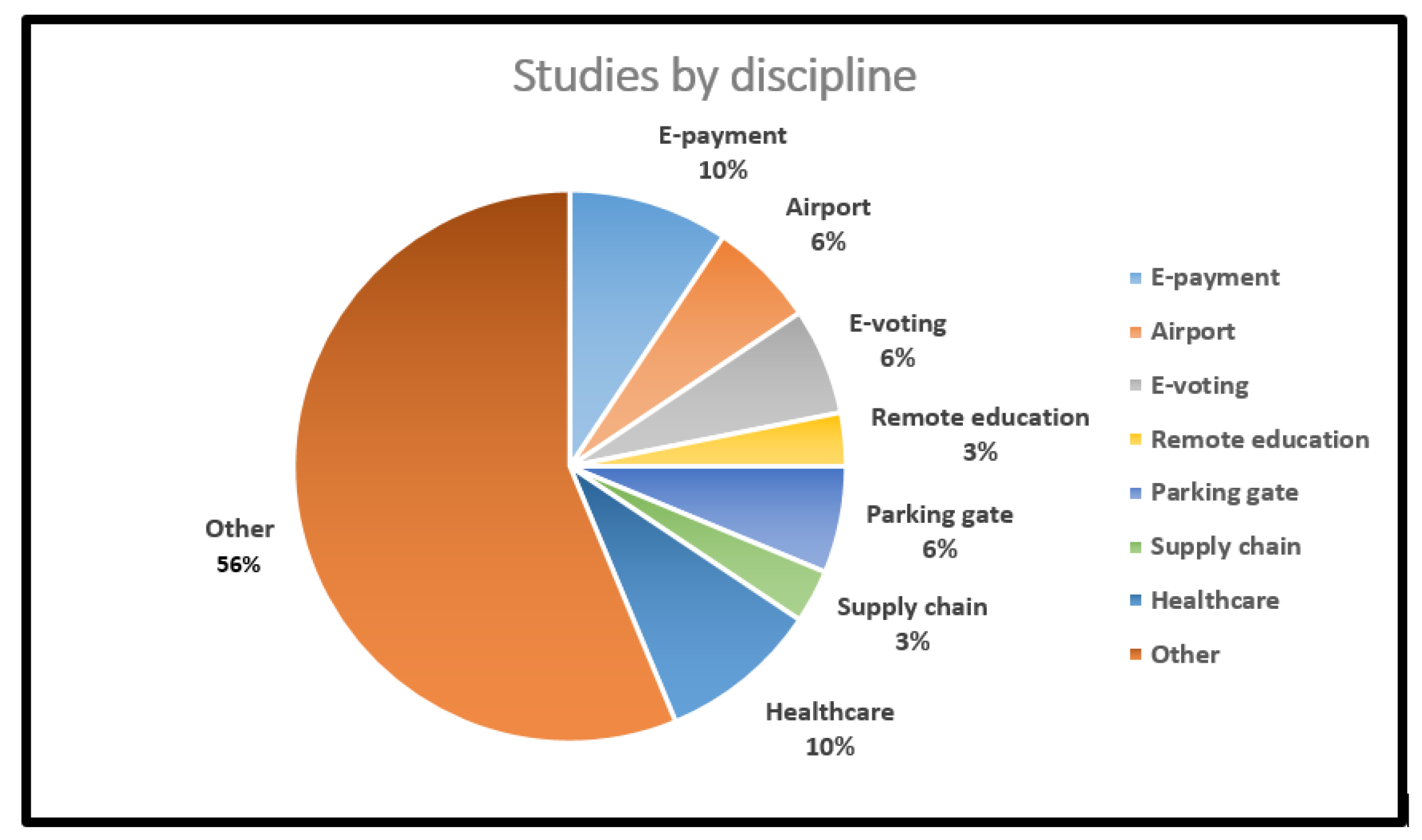
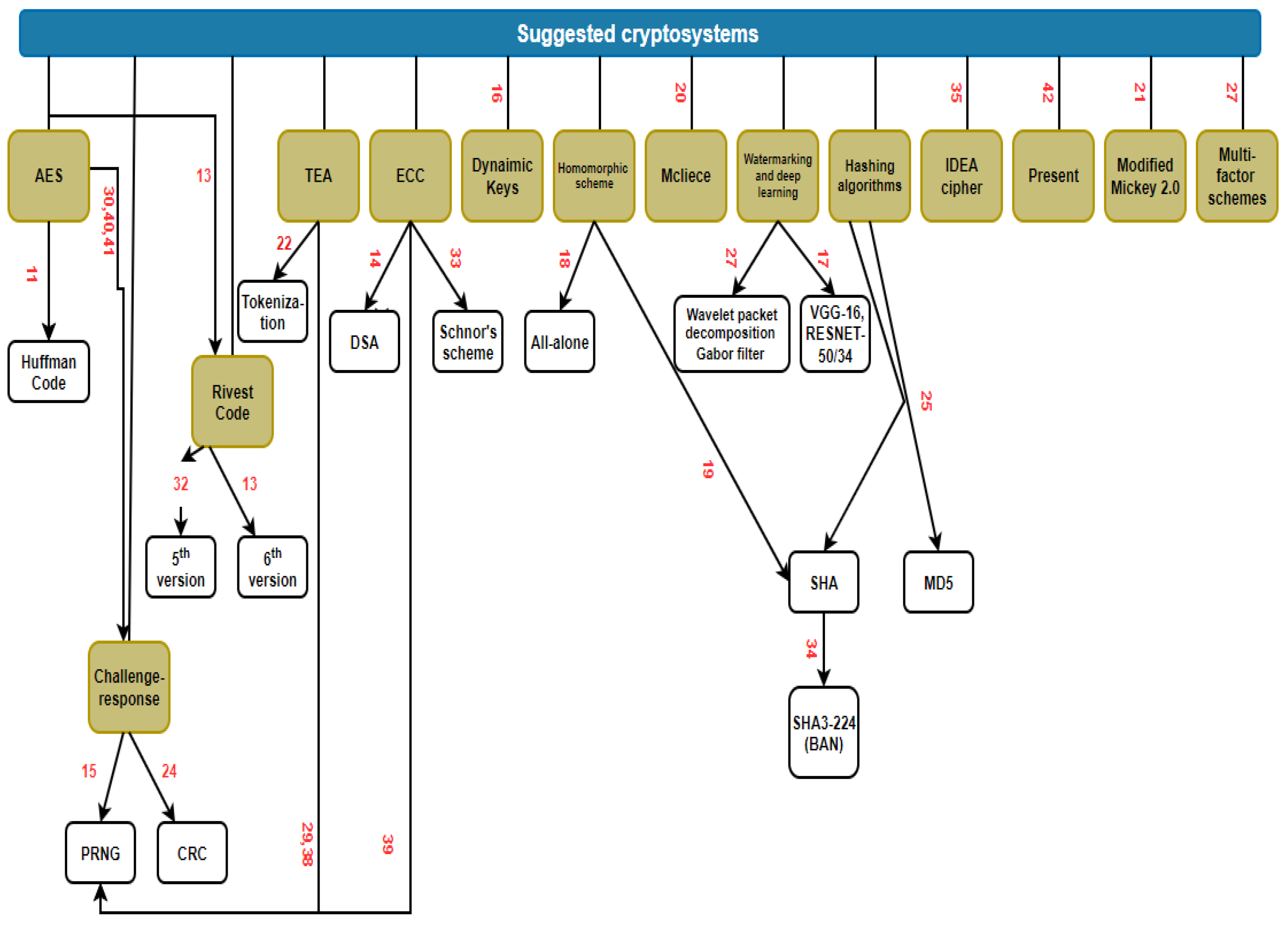
| Authors and | Main Objective | Year | Country | Method Utilized | Discipline |
|---|---|---|---|---|---|
| Adeniji, O.D. et al. [11] | Guaranteeing multi-level security for NFC smart cards by combining Huffman code and AES. | 2022 | Nigeria | Huffman code and AES | Multi-discipline |
| Olaniyi, O.M et al. [12] | The proposal of a secure NFC e-voting-based application to enhance the digitization of democratic decision-making trustworthiness. | 2022 | Nigeria Austria Morocco | Multi-Factor and Authentication (MFA) | e-voting |
| Raj, K.V et al. [13] | Increasing the use ofa multipurpose smart card by applying a proficient crypto algorithm. | 2022 | India | RC6 over AES and Blowfish SHA-256 for authentication | Multi-discipline |
| Arslan, A et al. [14] | Enhancing the ID17 scheme to overcome the mentioned protocol weaknesses. | 2021 | Turkey | ECC, brainpoolP160r1, and Digital Signature (DSA) | Multi-discipline |
| Dreyer, J et al. [15] | A novel approach to exchange public keys authentically via NFC (no third-party smuggling.) | 2021 | Germany | Challenge–response scheme | Multi-discipline |
| Noprianto et al. [16] | Introduced a data security technique built on keys’ and access conditions’ dynamic altering. | 2021 | Indonesia | Dynamic key utilization | Multi-discipline |
| Benamara N.K et al. [17] | Proposed a face authentication system based on deep learning facial biometry and RFID cards. | 2021 | Algeria | VGG-16, RESNET-50 RESNET-34 models | e-payment |
| Basjaruddin N.C et al. [18] | Applying homomorphic encryption NFC system security. | 2020 | Indonesia | Homomorphic cryptography (Paillier cryptosystem) | Airport baggage tracing |
| Damayani, S et al. [19] | Suggested the usage of AES-256 for key storage and SHA-256 for authentication, with the intention to provide robust data protection. | 2020 | Indonesia | Homomorphic cryptography (Paillier cryptosystem) SHA-256 and AES | e-voting |
| Chikouche, N. et al. [20] | Suggested an efficient protocol built on a post-quantum cryptosystem to secure RFID and NFC wireless communications. | 2020 | Indonesia | McEliece cryptosystem | |
| Alamer, A. et al. [21] | Proposed a modified approach (4 IVs and key pairs) to enhance Mickey cryptosystem Version 2.0 security providence. | 2019 | Australia Saudi-Arabia USA | Mickey 2.0 stream cipher | Healthcare |
| Arulmozhi, P. et al. [22] | Suggested a lightweight three-pass authentication scheme to verify the token. | 2019 | India USA Australia | Three-pass authentication tokenization TEA/RF-TEA | Multi-discipline |
| Zhang, Y. et al. [23] | The major intention was to provide full supply chain traceability by integrating several security features such as cryptography and blockchain (no consensus needed needed due to end entities’ trust). | 2019 | USA | ECDSA SHA-256 10 BytesCRC (integrity) | Supply chain |
| Kang, J. et al. [24] | Presented a secure RFID-suitable data-transmission protocol that offers protection against several attacks. | 2019 | Korea | Challenge–response process (PRNG + CRC) | Multi-discipline |
| Eka Putra, I.G.S et al. [25] | Suggested a logging-based application, where the MD5 algorithm was utilized against several attacks to offer smart card data privacy. | 2019 | Indonesia | MD5 | Multi-discipline |
| Nilar Soe et al. [26] | Offered a secure access control system based on the utilization of the ECDSA algorithm to overcome inaccurate payment issues. | 2019 | Myanmar | PKI infrastructure based on ECDSA | Electronic payment |
| Lamia Rzouga et al. [27] | Fulfillment of a secure biometric built-in application for access control by integrating watermarking techniques. | 2019 | Tunisia | Wavelet packet decomposition and Gabor filter extractor | Multi-discipline |
| Isa Mulia Insan et al. [28] | The application of the MFA scheme with usage of fingerprints and smart cards as security factors. | 2019 | Indonesia | Multi-Factor Authentication scheme (MFA) | Parking gate |
| Abdulsalam, Y.S. et al. [29] | Proposed an enhanced TEA ciphering algorithm to secure RFID-based healthcare application factors. | 2018 | Nigeria | TEA algorithm and Yarrow PRNG | Healthcare |
| Mine Cetinkaya et al. [30] | The intention was to allow RFID tags to be configured and to gather keys in a secure way, without the necessity of a direct computer connection to the sensor. | 2018 | Germany | AES-128 | Multi-discipline |
| He Xu et al. [31] | A mutual verification-based protocol with the integration of PUF and Kulseng’s verification to offer efficient security against desynchronized attacks. | 2018 | China | Mutual verification (physical unclonable function + Kulseng verification) | Multi-discipline |
| Excel B. et al. [32] | Enhanced the RC5’s slow encryption speed by a generated random number for keys’ generation (speed up key expansion process). | 2018 | Philippines | Enhanced RC5 | Electronic payment |
| Lukas Malina et al. [33] | A zero-knowledge-based cryptography scheme was suggested, where Schnorr’s identification scheme was used to provide the proof of knowledge and ECC for data size moderation. | 2018 | Czech Republic | Schnorr’s scheme ECC | Multi-discipline |
| Baolong Liu et al. [34] | The utilization of a hash-based scheme to identify the reader and tag, each part being identified by half of the generated hash. BAN was implemented for protocol correctness. | 2018 | China | SHA3-224 Burrows–Abadi–Needham (BAN) | Multi-discipline |
| H Nurdiyanto et al. [35] | The usage of the IDEA cipher for an RFID-based parking application to identify, verify, and authenticate tags with the intention to improve the entire system’s security. | 2018 | Indonesia Republic | IDEA cipher Burrows–Abadi–Needham (BAN) | Parking gate |
| Néstor Álvarez-Díaz et al. [36] | The usage of the IDEA cipher for an RFID-based parking application to identify, verify, and authenticate tags with the intention to improve the entire system’s security. | 2017 | Spain USA | Homomorphic cryptography (the Paillier cryptosystem | Airport luggage control |
| Mohammed Issam Younis et al. [37] | A mutual authentication scheme to secure RFID system communications involves signing, issuing, and charging for verification. | 2017 | Iraq | PRNG (tag side) ECDSA + PBE (backend database) | Multi-discipline |
| Olayemi M et Olaniyi et al. [38] | Applying the enhanced-TEA cipher to secure clinical telediagnostic information and tags from being cloned or falsified. | 2017 | Nigeria | Pseudo-random TEA | Healthcare |
| Hung-Yu Chien [39] | Suggested a new ECC-based authentication scheme to secure RFID against active tracking attacks. | 2017 | Taiwan | ECC | Multi-discipline |
| Hung-Yu Chien [40] | A radio-frequency authentication scheme based on the usage of a challenge–response approach and AES cipher to protect tags from unauthorized identification and non-legitimate tracing. | 2017 | Taiwan | AES | Multi-discipline |
| Ratnadewi et al. [41] | They tried to implement the AES-128 algorithm to ensure data transmission privacy. | 2017 | Indonesia | AES-128 Burrows–Abadi | Multi-discipline |
| Yassine Naija et al. [42] | Proposed a low-cost mutual authentication that was built in. | 2017 | Tunisia France | PRESENT | Parking gate |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
El Gaabouri, I.; Senhadji, M.; Belkasmi, M.; El Bhiri, B. A Systematic Literature Review on Authentication and Threat Challenges on RFID Based NFC Applications. Future Internet 2023, 15, 354. https://doi.org/10.3390/fi15110354
El Gaabouri I, Senhadji M, Belkasmi M, El Bhiri B. A Systematic Literature Review on Authentication and Threat Challenges on RFID Based NFC Applications. Future Internet. 2023; 15(11):354. https://doi.org/10.3390/fi15110354
Chicago/Turabian StyleEl Gaabouri, Ismail, Mohamed Senhadji, Mostafa Belkasmi, and Brahim El Bhiri. 2023. "A Systematic Literature Review on Authentication and Threat Challenges on RFID Based NFC Applications" Future Internet 15, no. 11: 354. https://doi.org/10.3390/fi15110354
APA StyleEl Gaabouri, I., Senhadji, M., Belkasmi, M., & El Bhiri, B. (2023). A Systematic Literature Review on Authentication and Threat Challenges on RFID Based NFC Applications. Future Internet, 15(11), 354. https://doi.org/10.3390/fi15110354






