Determining the Role of Social Identity Attributes to the Protection of Users’ Privacy in Social Media
Abstract
:1. Introduction
2. Digital Identity and Privacy Implications on Social Media
2.1. Digital Identity and Social Aspects
2.2. Privacy Implications and the Privacy Paradox
3. The Role of Self-Determination and Self-Disclosure in Users’ Privacy
3.1. Privacy and Self-Determination
3.2. Privacy and Self-Disclosure
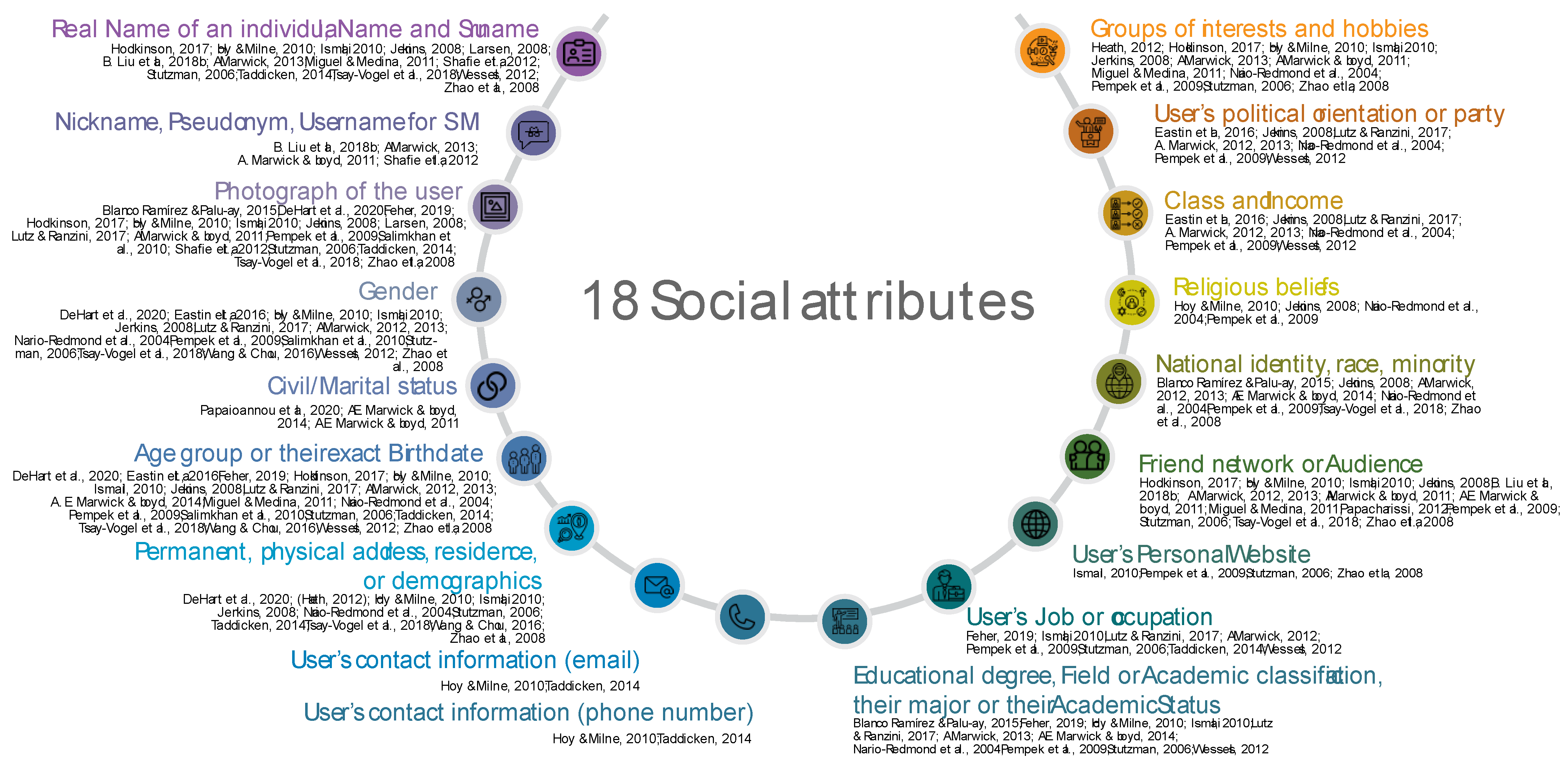
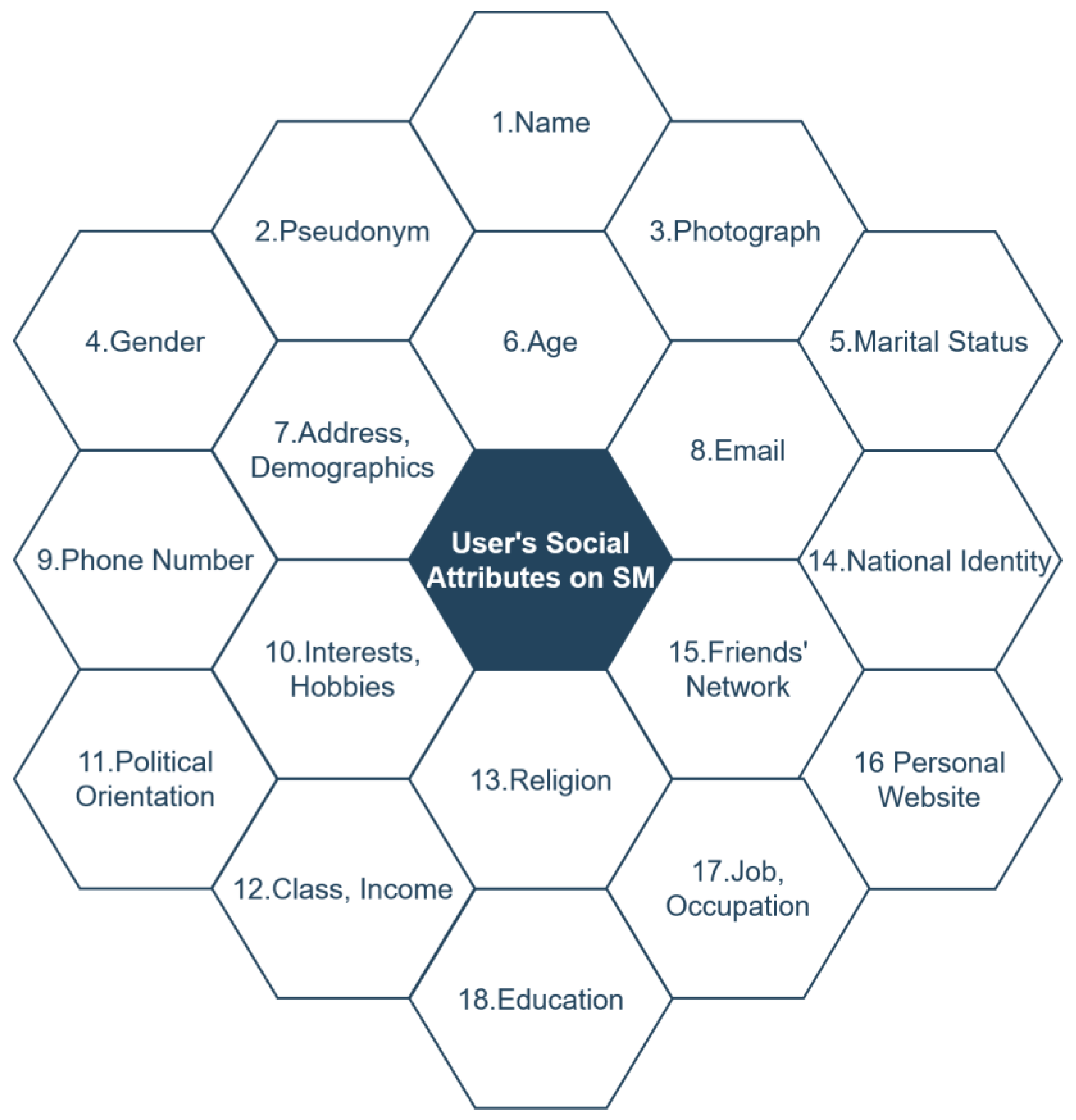
4. Revealing Social Attributes: A Review
5. Discussion
5.1. Domains, Attributes, and Variables
5.2. Users’ SI Domains of Social Attributes on SM
6. Conclusions
6.1. General Remarks
6.2. Limitations and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Almudawi, N.A. Cloud Computing Privacy Concerns in Social Networks. Int. J. Comput. 2016, 22, 29–36. [Google Scholar]
- Kiranmayee, T.S. A Survey on the Role of Cloud Computing in Social Networking Sites. Int. J. Comput. Sci. Inf. Technol. 2015, 6, 1509–1512. [Google Scholar]
- DeHart, J.; Stell, M.; Grant, C. Social Media and the Scourge of Visual Privacy. Information 2020, 11, 57. [Google Scholar] [CrossRef] [Green Version]
- Lenberg, P.; Feldt, R.; Wallgren, L.G. Behavioral Software Engineering: A Definition and Systematic Literature Review. J. Syst. Softw. 2015, 107, 15–37. [Google Scholar] [CrossRef]
- Kalloniatis, C.; Kavakli, E.; Gritzalis, S. Addressing Privacy Requirements in System Design: The PriS Method. Requir. Eng. 2008, 13, 241–255. [Google Scholar] [CrossRef]
- Margulis, S.T. On the Status and Contribution of Westin’s and Altman’s Theories of Privacy. J. Soc. Issues 2003, 59, 411–429. [Google Scholar] [CrossRef]
- Begel, A.; Deline, R.; Zimmermann, T. Social Media for Software Engineering. In Proceedings of the FSE/SDP Workshop on Future of Software Engineering Research, Santa Fe, NM, USA, 7–11 November 2010; pp. 33–38. [Google Scholar]
- Schwartz, R.; Halegoua, G.R. The Spatial Self: Location-Based Identity Performance on Social Media. New Media Soc. 2015, 17, 1643–1660. [Google Scholar] [CrossRef] [Green Version]
- Fusco, S.J.; Michael, K.; Michael, M.G. Using a Social Informatics Framework to Study the Effects of Location-Based Social Networking on Relationships between People: A Review of Literature. In Proceedings of the 2010 IEEE International Symposium on Technology and Society, Wollongong, Australia, 7–9 June 2010; pp. 157–171. [Google Scholar]
- Liu, B.; Zhou, W.; Zhu, T.; Gao, L.; Xiang, Y. Location Privacy and Its Applications: A Systematic Study. IEEE Access 2018, 6, 17606–17624. [Google Scholar] [CrossRef]
- Gurses, F.S. Multilateral Privacy Requirements Analysis in Online Social Network Services; KU Leuven: Heverlee, Belgium, 2010. [Google Scholar]
- Joinson, A.N.; Paine, C.B. Self-Disclosure, Privacy and the Internet; Joinson, A.N., McKenna, K.Y.A., Postmes, T., Reips, U.-D., Eds.; Oxford University Press: Oxford, UK, 2012; Volume 1. [Google Scholar]
- Marwick, A. Online Identity in Companion to New Media Dynamics; Wiley: Hoboken, NJ, USA, 2013; pp. 355–364. [Google Scholar]
- Zhou, B.; Pei, J.; Luk, W. A Brief Survey on Anonymization Techniques for Privacy Preserving Publishing of Social Network Data. SIGKDD Explor. Newsl. 2008, 10, 12–22. [Google Scholar] [CrossRef]
- Hogan, B. Pseudonyms and the Rise of the Real-Name Web. In A Companion to New Media Dynamics; Hartley, J., Burgess, J., Bruns, A., Eds.; Wiley-Blackwell: Oxford, UK, 2013; pp. 290–307. ISBN 978-1-118-32160-7. [Google Scholar]
- Taddicken, M. The ‘Privacy Paradox’ in the Social Web: The Impact of Privacy Concerns, Individual Characteristics, and the Perceived Social Relevance on Different Forms of Self-Disclosure. J. Comput.-Mediat. Comm. 2014, 19, 248–273. [Google Scholar] [CrossRef]
- Rodotà, S. Privacy, Freedom, and Dignity. 2004. Available online: https://www.garanteprivacy.it/home/docweb/-/docweb-display/docweb/1049293 (accessed on 19 August 2022).
- Blanco Ramírez, G.; Palu-ay, L. “You Don’t Look like Your Profile Picture”: The Ethical Implications of Researching Online Identities in Higher Education. Educ. Res. Eval. 2015, 21, 139–153. [Google Scholar] [CrossRef]
- Jenkins, R. Social Identity, 3rd ed.; Routledge: London, UK; New York, NY, USA, 2008; ISBN 978-0-415-44848-2. [Google Scholar]
- Myles, G.; Friday, A.; Davies, N. Preserving Privacy in Environments with Location-Based Applications. IEEE Pervasive Comput. 2003, 2, 56–64. [Google Scholar] [CrossRef] [Green Version]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C.; Kavroudakis, D. Do Identity and Location Data Interrelate? New Affiliations and Privacy Concerns in Social-Driven Sharing. In Trust, Privacy and Security in Digital Business; Gritzalis, S., Weippl, E.R., Katsikas, S.K., Anderst-Kotsis, G., Tjoa, A.M., Khalil, I., Eds.; Springer International Publishing: Cham, Switzerland, 2019; Volume 11711, pp. 3–16. ISBN 978-3-030-27812-0. [Google Scholar]
- Vgena, K.; Mavroeidi, A.-G.; Kitsiou, A.; Kalloniatis, C. Can Social Gamification and Privacy Co-Exist? Identifying the Major Concerns. In Proceedings of the 25th Pan-Hellenic Conference on Informatics, Volos, Greece, 26–28 November 2021. [Google Scholar]
- Austin, L.M. Re-Reading Westin. Theor. Inq. Law 2019, 20, 53–81. [Google Scholar] [CrossRef]
- Beldad, A.; Kusumadewi, M.C. Here’s My Location, for Your Information: The Impact of Trust, Benefits, and Social Influence on Location Sharing Application Use among Indonesian University Students. Available online: https://reader.elsevier.com/reader/sd/pii/S0747563215001685?token=8EA609560A5E713BFE0E4583698789CAF5058ED85DE538327F28BDB6D5F2461EF46A4B750582D43395CD418D29D3D257 (accessed on 29 July 2020).
- Michael, G.E.K.; Michael, M.G. The Social and Behavioural Implications of Location-Based Services. J. Locat. Based Serv. 2011, 5, 121–137. [Google Scholar] [CrossRef] [Green Version]
- Lahlou, S. Identity, Social Status, Privacy and Face-Keeping in Digital Society. Soc. Sci. Inf. 2008, 47, 299–330. [Google Scholar] [CrossRef]
- Curzon, J.; Almehmadi, A.; El-Khatib, K. A Survey of Privacy Enhancing Technologies for Smart Cities. Pervasive Mob. Comput. 2019, 55, 76–95. [Google Scholar] [CrossRef]
- Wachter, S. Normative Challenges of Identification in the Internet of Things: Privacy, Profiling, Discrimination, and the GDPR. Comput. Law Secur. Rev. 2018, 34, 436–449. [Google Scholar] [CrossRef]
- Maple, C. Security and Privacy in the Internet of Things. J. Cyber Policy 2017, 2, 155–184. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, Privacy and Trust in Internet of Things: The Road Ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Talbot, C.V.; Talbot, A.; Roe, D.J.; Briggs, P. The Management of LGBTQ+ Identities on Social Media: A Student Perspective. New Media Soc. 2022, 24, 1729–1750. [Google Scholar] [CrossRef]
- Emanuel, L.; Stanton Fraser, D. Exploring Physical and Digital Identity with a Teenage Cohort. In Proceedings of the 2014 Conference on Interaction Design and Children, Aarhus, Denmark, 17–20 June 2014; ACM: New York, NY, USA, 2014; pp. 67–76. [Google Scholar]
- Satchell, C.; Shanks, G.; Howard, S.; Murphy, J. Identity Crisis: User Perspectives on Multiplicity and Control in Federated Identity Management. Behav. Inf. Technol. 2011, 30, 51–62. [Google Scholar] [CrossRef] [Green Version]
- Papaioannou, T.; Tsohou, A.; Karyda, M. Shaping Digital Identities in Social Networks: Data Elements and the Role of Privacy Concerns; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Wessels, B. Identification and the Practices of Identity and Privacy in Everyday Digital Communication. New Media Soc. 2012, 14, 1251–1268. [Google Scholar] [CrossRef]
- Miguel, C.; Medina, P. The Transformation of Identity and Privacy through Online Social Networks (The CouchSurfing Case). 2011. Available online: https://eprints.leedsbeckett.ac.uk/id/eprint/2159/1/The%20Transforma (accessed on 19 August 2022).
- Bria, F.; Primosig, F. Internet as a Common or Capture of Collective Intelligence. Available online: https://dcentproject.eu/wp-content/uploads/2015/06/D3.3-Annex-Internet-Identity-Seminar_annex.pdf (accessed on 19 August 2022).
- Yuan, M.; Chen, L.; Yu, P.S.; Yu, T. Protecting Sensitive Labels in Social Network Data Anonymization. IEEE Trans. Knowl. Data Eng. 2013, 25, 633–647. [Google Scholar] [CrossRef]
- Papacharissi, Z. A Networked Self Identity Performance and Sociability on Social Network Sites; Routledge: London, UK, 2012. [Google Scholar]
- Tsay-Vogel, M.; Shanahan, J.; Signorielli, N. Social Media Cultivating Perceptions of Privacy: A 5-Year Analysis of Privacy Attitudes and Self-Disclosure Behaviors among Facebook Users. New Media Soc. 2018, 20, 141–161. [Google Scholar] [CrossRef]
- Fei Wu, P. The Privacy Paradox in the Context of Online Social Networking: A Self-Identity Perspective. Available online: https://www.researchgate.net/publication/329039895_The_privacy_paradox_in_the_context_of_online_social_networking_A_self-identity_perspective_JOURNAL_OF_THE_ASSOCIATION_FOR_INFORMATION_SCIENCE_AND_TECHNOLOGY (accessed on 21 September 2019).
- Kokolakis, S. Privacy Attitudes and Privacy Behaviour: A Review of Current Research on the Privacy Paradox Phenomenon. Comput. Secur. 2017, 64, 122–134. [Google Scholar] [CrossRef]
- Acquisti, A.; Gross, R. Imagined Communities: Awareness, Information Sharing, and Privacy on the Facebook. In Proceedings of the Privacy Enhancing Technologies; Danezis, G., Golle, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 36–58. [Google Scholar]
- Gross, R.; Acquisti, A. Information Revelation and Privacy in Online Social Networks (The Facebook Case). In Proceedings of the 2005 ACM Workshop on Privacy in the Electronic Society, Alexandria, VA, USA, 7 November 2005. [Google Scholar]
- Hoy, M.G.; Milne, G. Gender Differences in Privacy-Related Measures for Young Adult Facebook Users. J. Interact. Advert. 2010, 10, 28–45. [Google Scholar] [CrossRef]
- Shafie, L.A.; Nayan, S.; Osman, N. Constructing Identity through Facebook Profiles: Online Identity and Visual Impression Management of University Students in Malaysia. Procedia Soc. Behav. Sci. 2012, 65, 134–140. [Google Scholar] [CrossRef] [Green Version]
- van Dijck, J. ‘You Have One Identity’: Performing the Self on Facebook and LinkedIn. Media Cult. Soc. 2013, 35, 199–215. [Google Scholar] [CrossRef] [Green Version]
- Zhao, S.; Grasmuck, S.; Martin, J. Identity Construction on Facebook: Digital Empowerment in Anchored Relationships. Comput. Hum. Behav. 2008, 24, 1816–1836. [Google Scholar] [CrossRef] [Green Version]
- Kalloniatis, C. Increasing Internet Users Trust in the Cloud Computing Era: The Role of Privacy. J. Mass Commun. Journal. 2016, 6, 2–5. [Google Scholar] [CrossRef]
- Kalloniatis, C. Incorporating Privacy in the Design of Cloud-Based Systems: A Conceptual Meta-Model. Inf. Comput. Secur. 2017, 25, 614–633. [Google Scholar] [CrossRef]
- Marwick, A.; Boyd, D. To See and Be Seen: Celebrity Practice on Twitter. Convergence 2011, 17, 139–158. [Google Scholar] [CrossRef] [Green Version]
- Albrechtslund, A. New Media and Changing Perceptions of Surveillance. In A Companion to New Media Dynamics; Hartley, J., Burgess, J., Bruns, A., Eds.; Wiley-Blackwell: Oxford, UK, 2013; pp. 309–321. ISBN 978-1-118-32160-7. [Google Scholar]
- Bazarova, N.N.; Choi, Y.H. Self-Disclosure in Social Media: Extending the Functional Approach to Disclosure Motivations and Characteristics on Social Network Sites. J. Commun. 2014, 64, 635–657. [Google Scholar] [CrossRef]
- Powell, L.M.; Wimmer, H.; Rebman, C. Learner security & privacy risks: How usage of online social media outside a learning management system affects learners’ digital identity. Issues Inf. Syst. 2019, 20, 1–7. [Google Scholar]
- Arthur, P.L. Data Portraits: Identity, Privacy, and Surveillance. Auto/Biogr. Stud. 2017, 32, 371–373. [Google Scholar] [CrossRef]
- Beam, M.A.; Child, J.T.; Hutchens, M.J.; Hmielowski, J.D. Context Collapse and Privacy Management: Diversity in Facebook Friends Increases Online News Reading and Sharing. New Media Soc. 2018, 20, 2296–2314. [Google Scholar] [CrossRef]
- Brandtzaeg, P.B.; Lüders, M. Time Collapse in Social Media: Extending the Context Collapse. Soc. Media Soc. 2018, 4, 205630511876334. [Google Scholar] [CrossRef]
- Marwick, A.E.; Boyd, D. I Tweet Honestly, I Tweet Passionately: Twitter Users, Context Collapse, and the Imagined Audience. New Media Soc. 2011, 13, 114–133. [Google Scholar] [CrossRef]
- Marwick, A.E.; Boyd, D. Networked Privacy: How Teenagers Negotiate Context in Social Media. New Media Soc. 2014, 16, 1051–1067. [Google Scholar] [CrossRef]
- Hodkinson, P. Bedrooms and beyond: Youth, Identity and Privacy on Social Network Sites. New Media Soc. 2017, 19, 272–288. [Google Scholar] [CrossRef] [Green Version]
- Westin, A.F. Social and Political Dimensions of Privacy. J. Soc. Issues 2003, 59, 431–453. [Google Scholar] [CrossRef]
- Debatin, B. Privacy Online; Trepte, S., Reinecke, L., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; ISBN 978-3-642-21520-9. [Google Scholar]
- Yuan, M.; Chen, L.; Yu, P.S. Personalized Privacy Protection in Social Networks. Proc. VLDB Endow. 2010, 4, 141–150. [Google Scholar] [CrossRef] [Green Version]
- The PRISMA 2020 Statement: An Updated Guideline for Reporting Systematic Reviews|The BMJ. Available online: https://www.bmj.com/content/372/bmj.n71 (accessed on 29 July 2022).
- Lutz, C.; Ranzini, G. Where Dating Meets Data: Investigating Social and Institutional Privacy Concerns on Tinder. Soc. Media 2017, 3, 2056305117697735. [Google Scholar]
- Eastin, M.S.; Brinson, N.H.; Doorey, A.; Wilcox, G. Living in a Big Data World: Predicting Mobile Commerce Activity through Privacy Concerns. Comput. Hum. Behav. 2016, 58, 214–220. [Google Scholar] [CrossRef]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C. Understanding the Role of Users’ Socio-Location Attributes and Their Privacy Implications on Social Media. Inf. Comput. Secur. 2022; ahead-of-print. [Google Scholar] [CrossRef]
- Cover, R.; Doak, S. Identity Offline and Online. In International Encyclopedia of the Social & Behavioral Sciences; Elsevier: Amsterdam, The Netherlands, 2015; pp. 547–553. ISBN 978-0-08-097087-5. [Google Scholar]
- Ismail, S. An Evaluation of Students’ Identity-Sharing Behaviour in Social Network Communities as Preparation for Knowledge Sharing. Ismail, Shahrinaz. An evaluation of students’ identity-sharing behavior in social network communities as preparation for knowledge sharing. Int. J. Adv. Sci. Arts 2010, 1, 14–21. [Google Scholar]
- Papacharissi, Z. A Networked Self: Identity, Community, and Culture on Social Network Sites; Routledge: London, UK, 2010; ISBN 978-1-135-96616-4. [Google Scholar]
- Tufekci, Z. Can You See Me Now? Audience and Disclosure Regulation in Online Social Network Sites. Bull. Sci. Technol. Soc. 2008, 28, 20–36. [Google Scholar] [CrossRef]
- Feher, K. Digital Identity and the Online Self: Footprint Strategies—An Exploratory and Comparative Research Study. J. Inf. Sci. 2021, 47, 192–205. [Google Scholar] [CrossRef]
- Birnholtz, J.; Fitzpatrick, C.; Handel, M.; Brubaker, J.R. Identity, Identification and Identifiability: The Language of Self-Presentation on a Location-Based Mobile Dating App. In Proceedings of the 16th International Conference on Human-Computer Interaction with Mobile Devices & Services, Toronto, ON, Canada, 23–26 September 2014; ACM: New York, NY, USA; pp. 3–12. [Google Scholar]
- Pempek, T.A.; Yermolayeva, Y.A.; Calvert, S.L. College Students’ Social Networking Experiences on Facebook. J. Appl. Dev. Psychol. 2009, 30, 227–238. [Google Scholar] [CrossRef]
- Stutzman, F. An Evaluation of Identity-Sharing Behavior in Social Network Communities. J. Int. Digit. Media Arts Assoc. 2006, 3, 10–18. [Google Scholar]
- Marwick, A. The Public Domain: Surveillance in Everyday Life. Available online: https://www.researchgate.net/publication/279673507_The_Public_Domain_Surveillance_in_Everyday_Life (accessed on 2 March 2019).
- Papacharissi, Z.; Easton, E. In the Habitus of the New. In A Companion to New Media Dynamics; John and Wiley and Sons: Hoboken, NJ, USA, 2013; pp. 167–184. ISBN 978-1-118-32160-7. [Google Scholar]
- Li, S.; Li, J.Z. Web and Social Media Dynamics, and Evolutionary and Adaptive Branding: Theories and a Hybrid Intelligent Model. In Proceedings of the 13th international conference on artificial intelligence, knowledge engineering and data bases, Gdansk, Poland, 15–17 May 2014. [Google Scholar]
- Nario-Redmond, M.R.; Biernat, M.; Eidelman, S.; Palenske, D.J. The Social and Personal Identities Scale: A Measure of the Differential Importance Ascribed to Social and Personal Self-Categorizations. Self Identity 2004, 3, 143–175. [Google Scholar] [CrossRef] [PubMed]
- Kounadi, O.; Resch, B.; Petutschnig, A. Privacy Threats and Protection Recommendations for the Use of Geosocial Network Data in Research. Soc. Sci. 2018, 7, 191. [Google Scholar] [CrossRef] [Green Version]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C.; Kavroudakis, D.; Gritzalis, S. Toward Addressing Location Privacy Issues: New Affiliations with Social and Location Attributes. Future Internet 2019, 11, 234. [Google Scholar] [CrossRef] [Green Version]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C.; Kavroudakis, D. Disclosing Social and Location Attributes on Social Media: The Impact on Users’ Privacy; Springer LNCS Lecture Notes in Computer Science: Darmstadt, Germany, 2021; Volume 12501. [Google Scholar]
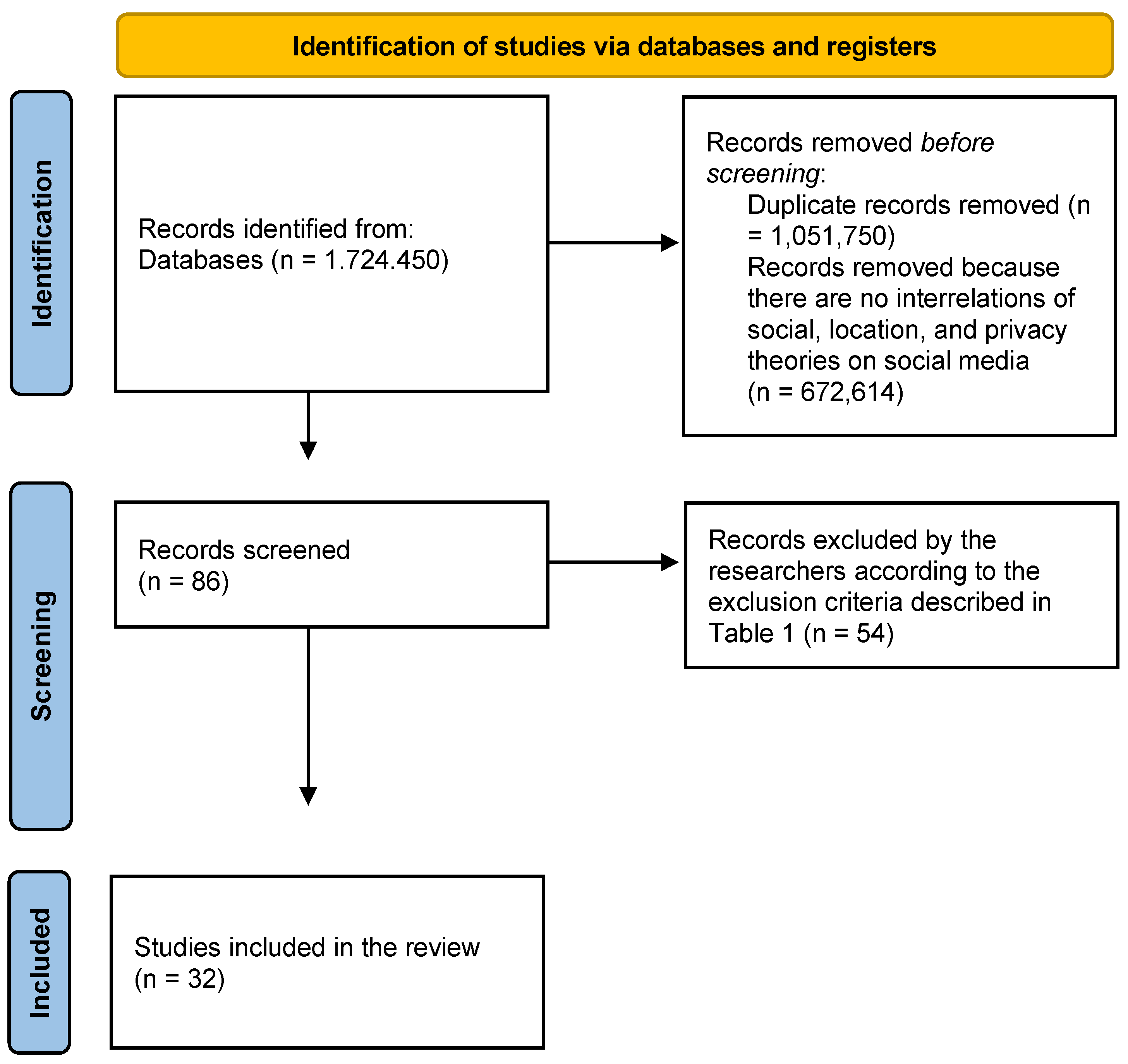

| Exclusion Criteria |
|---|
|
|
|
|
|
|
|
|
| SI Domains | SA on SM |
|---|---|
| Face | 1–6, 8–18 |
| Frame | 3, 7–11, 13–14, 17–18 |
| Time | 3, 10–11, 12, 18 |
| Stage | 3, 7–14, 18 |
| Activity or Performance | 2–3, 10–18 |
| Social Identity Domains | Social Attributes on SM | Variables | Identified Disclosures |
|---|---|---|---|
| Face | user’s name, nickname, profile picture, gender, age, address or residence, education, affiliations, job, personal website, friends’ network, national or religious identity, class or income, groups of interests and hobbies | Name, Gender, Nationality, Membership, Education, Sexual orientation | actual name (John), gender (M/F), a photograph of the user, membership in a specific group |
| Frame | user’s photograph, address or residence, contact information (email and phone number), affiliations, job, friends’ network, national identity, group of interests | Neighborhood, City, Municipality | exact spatial information (x, y), landmark, hashtags, use of a photograph of the place |
| Time | photographs, education, affiliations, job, user’s website, groups of interests | Hours, Minutes, Day, Week, Month | exact temporal information (hh:mm:ss), use of hashtags, use of a photograph with light depiction |
| Stage | user’s photograph, address or residence, contact information (email and phone number), Education, affiliations, job, friends’ network, national identity, user’s website, group of interests | Combination of both the Frame and the Time Social Attributes | combination of both the Frame and the Time Expected Ways of Disclosure on SM |
| Activity or Performance | nickname, photographs, education, affiliations, job, user’s personal website, friends’ network, national or religious identity, class, income, or political orientation, groups of interest and hobbies | Activity, Occupation | exact activity, use of hashtag, exact occupation, use of a photograph doing an activity |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vgena, K.; Kitsiou, A.; Kalloniatis, C.; Gritzalis, S. Determining the Role of Social Identity Attributes to the Protection of Users’ Privacy in Social Media. Future Internet 2022, 14, 249. https://doi.org/10.3390/fi14090249
Vgena K, Kitsiou A, Kalloniatis C, Gritzalis S. Determining the Role of Social Identity Attributes to the Protection of Users’ Privacy in Social Media. Future Internet. 2022; 14(9):249. https://doi.org/10.3390/fi14090249
Chicago/Turabian StyleVgena, Katerina, Angeliki Kitsiou, Christos Kalloniatis, and Stefanos Gritzalis. 2022. "Determining the Role of Social Identity Attributes to the Protection of Users’ Privacy in Social Media" Future Internet 14, no. 9: 249. https://doi.org/10.3390/fi14090249
APA StyleVgena, K., Kitsiou, A., Kalloniatis, C., & Gritzalis, S. (2022). Determining the Role of Social Identity Attributes to the Protection of Users’ Privacy in Social Media. Future Internet, 14(9), 249. https://doi.org/10.3390/fi14090249









