Abstract
Anonymous service delivery has attracted the interest of research and the industry for many decades. To obtain effective solutions, anonymity should be guaranteed against the service provider itself. However, if the full anonymity of users is implemented, no accountability mechanism can be provided. This represents a problem, especially when referring to scenarios in which a user, protected by anonymity, may perform illegally when leveraging the anonymous service. In this paper, we propose a blockchain-based solution to the trade-off between anonymity and accountability. In particular, our solution relies on three independent parties (one of which is the service provider itself) such that only the collaboration of all three actors allows for the disclosure of the real identity of the user. In all other cases, anonymity is guaranteed. To show the feasibility of the proposal, we developed a prototype with user-friendly interfaces that minimize the client-side operations. Our solution is then also effective from the point of view of usability.
1. Introduction
Anonymous services are privacy-preserving services offered to users without requiring them to disclose their identities.
We can distinguish two types of services. The first type is represented by one-time services exploited by users just once. Some examples are electronic auctions [1,2], anonymous surveys [3], or e-voting [4]. In the second type of services, users keep an anonymous account and exploit the same service more times. Each user is associated with a pseudonymous username to which their account’s activity is linked. The action of users also includes possible data generated by the user when leveraging the service. A typical example is represented by anonymous social networks [5,6], in which, a pseudonymous username is associated with some data, such as private messages or posts. In this paper, we refer to the second type of services.
A minimal requirement is to provide anonymity to the users with respect to other users leveraging the same service. However, in order to be effective, anonymity should also be guaranteed against the service provider itself.
Even though, for the first type of services, full anonymity may be required, when referring to the second type, it is impractical to pursue user anonymity without taking accountability into consideration. Indeed, without the fear of being identified, held responsible, and punished when abusing the services, users are likely to misbehave due to selfishness or malice, thereby disrupting system operations and harming everyone else [7]. Therefore, a trade-off between anonymity and accountability exists [8].
In this paper, we try to solve this trade-off by proposing a blockchain-based protocol including two further parties, in addition to the user and the service provider. They are: (1) an identity gateway, which interfaces a standard identity provider (knowing the real identity of the user) with the other entities of our proposal, and (2) a linkage agency, acting as a third independent party, which allows for the re-identification of the users if needed (e.g., when required by a court order).
In particular, our solution allows for the identification of the users only when all three parties (i.e., service provider, identity gateway, and linkage agency) collaborate. In all other cases, anonymity is guaranteed. Our paper reaches similar goals of approaches such as [9,10,11], with the relevant difference that, in our solution, the collaboration of just two third parties is not enough to de-anonymize the user.
From the security point of view, in our threat model, we require only a minimum degree of trust in the identity provider, in the sense that it does not perform active attacks such as impersonation. However, we allow it to passively collude with, at most, one of the other entities by disclosing the information that it knows (i.e., the real identity of the users), still preserving unlinkability. No trust is required in the identity gateway, service provider, and linkage agency.
At the basis of our solution, we rely on a challenge–response mechanism (see Section 4) leveraging a smart contract deployed on the Ethereum blockchain. This smart contract also provides an account recovery mechanism in the case where the user loses their access credentials. Indeed, traditional recovery mechanisms based on the telephone number or email address cannot be adopted since they would reveal personal information about users. Finally, another benefit of the blockchain technology is that the re-identification of the user as a consequence of malicious behaviour can be publicly verifiable by anyone.
To show the applicability of our proposal, we provide a user-friendly implementation, including a time-cost analysis. In this implementation, we care about usability by reducing the number of operations performed client-side. This shows that our solution can be easily applied in real-life contexts.
The structure of the paper is the following. In Section 2, we survey the related literature and provide some background notions about the Ethereum blockchain. The entities and the notations used to describe our proposal are introduced in Section 3. In Section 4, we provide the challenge–response mechanism at the basis of our solution. Then, in Section 5, we describe our proposal in detail. Its implementation is discussed in Section 6 and its security is analyzed in Section 7. Finally, in Section 8, we draw our conclusions and discuss future work.
2. Related Work and Background
In the scientific literature, there exist several papers dealing with the general issue of balancing anonymity and accountability in different fields.
Refs. [12,13,14] rely on anonymous credential systems and related schemes. Anonymous credential systems allow users to interact with a service provider in an anonymous yet accountable way [15,16,17]. Ref. [12] is the first paper proposing an anonymous credential system, in which, to prevent the misuse of anonymity, the anonymity property can be revoked for particular transactions. Ref. [13] introduces an approach relying on anonymous credentials that allows access control systems to offer fully anonymous access to resources along with strong accountability guarantees. It is worth noting that the proposed approach relies on a trusted third party to build a mechanism to escrow the identity of the user. Most of the solutions present in the literature assume a client–server architecture in which only the clients care about their privacy. On the contrary, Ref. [18] aims to reach the right balance between privacy and accountability in P2P systems, where both clients and servers are peer users. In [19], the authors deal with the issue of accountability in anonymous publication and storage services where malicious servers can make documents unrecoverable. To discourage this kind of behavior, the authors propose the creation of a “buddy system” that creates an association between pairs of shares from a given document. Therefore, a server holding a given share is responsible for detecting any anomaly regarding its buddy.
Ref. [20] proposes a framework to provide an anonymous mutual authentication protocol in wireless mesh networks. The proposed framework utilizes group signatures, where the private key and the credentials of the users are generated through a secure three-party protocol. User accountability is implemented via a user revocation protocol, whose execution can be carried out by two semi-trusted authorities, one of which is the network operator.
Refs. [21,22] deal with the issue of accountability in anonymous communication networks. Indeed, Ref. [22] highlights that both anonymity and accountability requirements should be satisfied to gain support for the deployment of large-scale anonymity infrastructures. To achieve this, Ref. [21] presents a mechanism that provides practical repudiation for the proxy nodes by tracing back a selected traffic to the predecessor node through a cryptographically verifiable chain.
A proposal that includes some similarities to our work is presented in [23]. Indeed, the authors proposed a solution that leverages the Bitcoin blockchain as a platform to manage and determine ownership of users’ access credentials. The authors design an authentication scheme that is able to provide anonymity and accountability without relying on any trusted third party. Regardless, the proposed solution achieves accountability only in the sense that the service provider can blacklist the misbehaving credentials related to a user. Indeed, as highlighted by [24], accountability can still be obtained by eliminating the reliance on a third trusted party for credentials revocation, but this comes with a cost: the revoked user remains anonymous. Another solution relying on blockchain to support anonymous authentication in VANET is provided in [25].
We conclude this section by discussing some proposals about anonymous social networks [6]. Indeed, these appear as services that might take advantage of adopting our solution.
Anonymous social networks completely shift the traditional social networks paradigm. Indeed, while the latter put the user identity and its social link first, anonymous social networks encourage communication between strangers and allow users to express themselves without fear of bullying or retaliation [5]. Among the most famous anonymous social networks, we found Whisper [5] and Yik Yak [26].
Several studies in the literature focus on the anonymity guarantees offered by popular anonymous social networks [5,26,27]. However, to the best of our knowledge, no paper concerning the accountability problem is available, although several studies suggest that the lack of accountability may encourage users to engage in illegal behavior, potentially harming other users [7].
We conclude this section by providing some background notions about the blockchain technology with a focus on Ethereum. They will be useful for the understanding of some concepts that we recall in our protocol.
Blockchain is a peer-to-peer network that keeps track of the occurrence of events. An entity can generate a transaction towards another entity to exchange a value. This transaction is validated by peers participating in the network, and thus does not require any third-trusted party to validate the transaction. This represents the main advantage offered by this technology. Other features are:
- The transactions have to be validated and cannot be modified after their validation.
- Users cannot repudiate a transaction that they had generated.
- Anyone can access and verify the transactions stored on the blockchain.
- The users generating the transactions should remain anonymous.
Regarding the latter point, for example, Ethereum guarantees pseudonymity, in the sense that the identity of the users is not revealed, but their transactions are linkable.
The above properties are generic of the blockchain technology and apply to almost all of the existing public-permissionless implementations [28,29], even though there exist blockchains supporting full anonymity [30,31].
In order to give a concrete proposal, in this paper, we refer to the Ethereum blockchain.
In Ethereum, there are two types of accounts. The first type is represented by the external owned accounts (EOAs), which are controlled by users through private/public key pairs. Specifically, a user U generates a random string of 32 bytes. It represents the private key of U.
Ethereum leverages the elliptic curve digital signature algorithm (ECDSA) [32] by selecting the curve secp256k1. Then, by applying the ECDSA algorithm to , U obtains a public key of 64 bytes (it represents the coordinates of a point of the elliptic curve). Finally, U applies the hash function Keccak256 [33] to and takes the last 20 bytes to obtain an Ethereum address. This Ethereum address is used to send and receive transactions, and identifies (in pseudonymous form) U in the network.
Each transaction generated by U is signed with the private key . The signed transaction is broadcasted in the blockchain network. Anyone can verify the signature by retrieving the public key of the signer (from the signature and the transaction) and checking that it is equal to the expected public key. Furthermore, the Ethereum address of the signer can be obtained from the public key by applying Keccak256 as described above.
The second type of account is called a contract account, and represents an account controlled by code (i.e., a smart contract). A smart contract [34] can be viewed as a collection of data and functions. To deploy an instance of a smart contract, an EOA sends an Ethereum transaction containing the compiled code (on the Ethereum VM) of the smart contract without specifying any recipient. Each instance has its own data (also called state) and functions, and it is associated with an Ethereum address. To invoke a function of the smart contract, an EOA generates a transaction, including the input of the function, intended for the address of an instance of the smart contract. This function may change the state of such an instance. Since the transaction invoking the function is stored on the blockchain, due to the properties of immutability and non-repudiation, anyone can verify the correct state of any instance at any time.
3. Actors and Notation
Our solution involves four actors:
- The user U: they require access to an anonymous service offered by a service provider .
- The service provider : it offers the anonymous service to U. U interacts with through a pseudonym username not linkable to thereal identity of U.
- The identity gateway : it does not know , but acts as a gateway between an identity provider who knows and the Ethereum network. In principle, it may be included directly in the identity provider. Regardless, we keep it as a separated entity in order to not require technological changes in the identity provider and maintain it as compliant with the eIDAS regulation [35].
- The linkage agency : it is a third independent party that, after receiving an order by a court, is able, through the collaboration of and , to link the real identity with the username .
As discussed in Section 1 and shown in Section 7, the collaboration of just two out of , , and is not enough to associate with , and all three parties have to be involved.
During the interaction between U and , some information is generated and associated with (since does not know the real identity ). We denote by such account information. For example, if is an anonymous social network, is represented by the private messages exchanged between U and other users, the messages posted by U, the “likes" released by U, and so on. Like almost all of the web services, is maintained server-side by . Observe that the access to is what the user has to recover in case of a loss of credentials.
An association among EOAs (see Section 2) and actors is established. Specifically, U owns two Ethereum addresses and . owns the Ethereum address . owns the Ethereum address . Finally, owns the Ethereum address .
Observe that and are pseudonyms of U not linkable between them or with . , , and are made publicly available by , , and , respectively.
As we will see in Section 4, our proposal is based on a challenge–response mechanism implemented by the smart contract reported in Listing 1. A number of instances of such a smart contract are deployed by , , and .
| Listing 1. Smart contract implementing a challenge–response mechanism. |
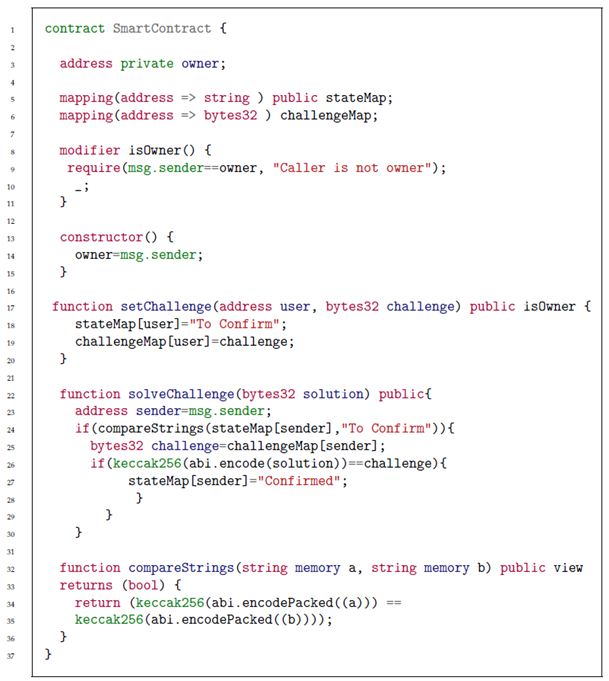 |
Specifically, deploys two instances and with Ethereum addresses and , respectively. is used by U during the registration phase with . It allows to associate the Ethereum address with . Clearly, this operation is performed by without knowing the real identity of U. Moreover, is not publicly disclosed. is used by U to retrieve in case U loses the credentials to connect with .
deploys the instance with Ethereum address . It is used by and the identity provider to associate with the real identity of U without disclosing it to .
Finally, deploys the instance with Ethereum address . is used by to link the Ethereum addresses and of U (without knowing the real identity and the username ).
To conclude this section, we introduce a notation to model the Ethereum transactions. In our application, the transactions are generated by the actors only towards instances of a smart contract to invoke some functions. No user-to-user transaction is performed and no Ether transfer is needed. Therefore, we modeled an Ethereum transaction as a tuple .
represents the Ethereum address of the actor generating the transaction. represents the destination address of the transaction. It can be an instance of the smart contract. Finally, represents the invoked function of the smart contract along with the input parameters.
4. Challenge–Response Mechanism
At the basis of our protocol, there is a challenge–response mechanism implemented by the smart contract reported in Listing 1.
It offers the following three security properties.
- P1: , , and have to be sure that the users really own the claimed Ethereum addresses.
- P2: if the previous check is satisfied and the owner of an address is able to solve a given challenge, then the smart contract sets, in a verifiable way, the state of such an address as “Confirmed”.
- P3: the smart contract allows us to notarize some information.
Even though, at this stage of the paper, it is not clear why we need these properties, we show as the smart contract allows us to satisfy them. Further details are provided in Section 5, where we exploit the proposed mechanism to implement our protocol.
Our smart contract includes two mappings, called stateMap and challengeMap, and two functions, called setChallenge and solveChallenge.
stateMap associates an Ethereum address with a string representing the state of such an address. We admit three possible states: “” (the built-in default state of Ethereum smart contracts), “To Confirm”, and “Confirmed”. By default, all of the addresses are in state “”.
challengeMap associates an Ethereum address with a bytes32 variable containing the challenge that such an address has to solve.
setChallenge can only be invoked by the owner (i.e., the entity who deployed) of the instance of the smart contract (in our application, the owner can be , , or ). It receives as an input an Ethereum address and a challenge. Then, it associates the challenge with the address in the challengeMap and sets the state of the address to "To Confirm" in the stateMap.
solveChallenge can be invoked by anyone and receives the solution to the challenge as an input. The solution to the challenge is a 32-byte word (corresponding to the digest of a cryptographic hash function). The technical detail about how this solution is computed is described in Section 5. First, it checks that the address originating the transaction invoking this function is in state “To Confirm”. This guarantees P1, since only the owner of an Ethereum address can generate a transaction from such an address. If the check is positive, then the function verifies that the solution solves the challenge associated with this address. In the positive case, the state of the address is set to “Confirmed” in the stateMap. This clarifies how the smart contract guarantees P2.
The mechanism to verify the solution to the challenge is straightforward. The smart contract simply checks that .
Regarding P3, the solution to the challenge itself represents the information to notarize. Observe that, since this information is published clearly on the blockchain, it should not compromise the anonymity of the user. This will be explained in the next section, in which, the whole protocol is described.
5. The Proposed Approach
Our solution involves three interactions performed just once (in a registration phase) by U with , , and , respectively. The goal is to obtain accountability only if collaborates with and to discover the real identity of a user performing illegally when using the anonymous service offered by . Furthermore, the proposed approach provides a mechanism to recover the account information when U loses the access credentials.
5.1. Interaction between U and
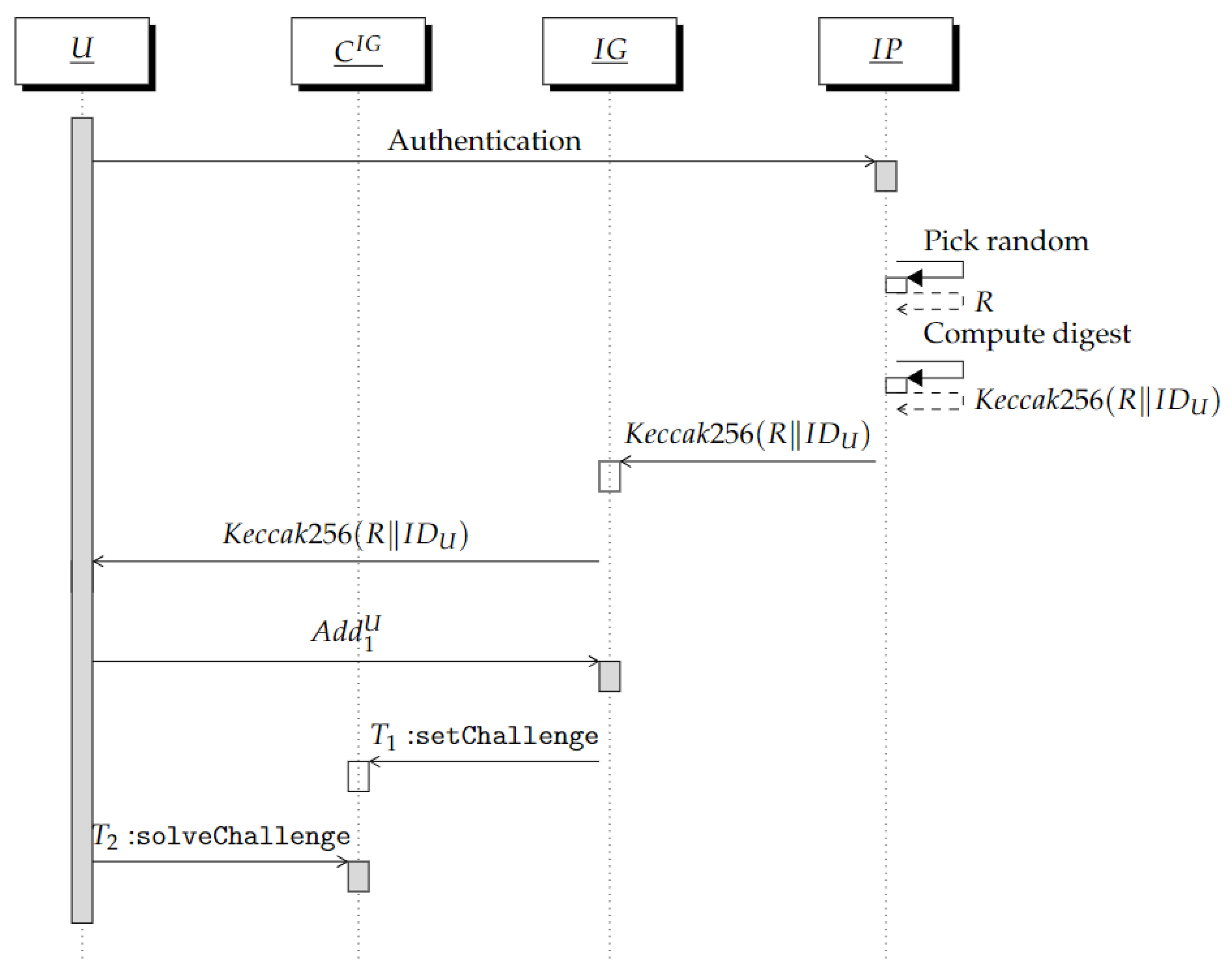
Through this interaction, the Ethereum address is associated with the real identity of U. This is performed without learning anything about . At the end of this phase, will result in state “Confirmed” and will be used by in the next interaction. This phase proceeds as follows.
At the start, we assume that U is registered with an identity provider that knows their real identity .
In our solution, offers a federated-based authentication scheme [36] possibly relying on different identity providers.
First, U authenticates with through the federated scheme by selecting the identity provider that U is registered to. We denote by such an identity provider.
As a standard federated authentication, when identifies U, it provides with a signed assertion not containing information associated with . In this assertion, includes , where R is a random value. R is then associated with and stored along with by .
Once the authentication is performed, U provides with .
Then, computes a challenge and generates a transaction intended for the instance of the smart contract. This transaction invokes the function setChallenge that associates the challenge with the address and sets in state “To Confirm”. Finally, sends U the digest .
After receiving this value, U uses it as solution to the challenge , i.e., , and generates the transaction = .
This proves to that U is the owner of . The function solveChallenge sets in state "Confirmed".
Observe that the random R acts as a salt for the hash function . This way, cannot be reversed by , even when performing dictionary attacks by testing all of the possible real identities. On the other hand, if the identity provider discloses R to , the association can be verified through the instance of the smart contract.
Finally, verifies the state “Confirmed” of the address and locally stores the tuple to provide if needed.
The above steps are summarized in the sequence diagram of Figure 1.
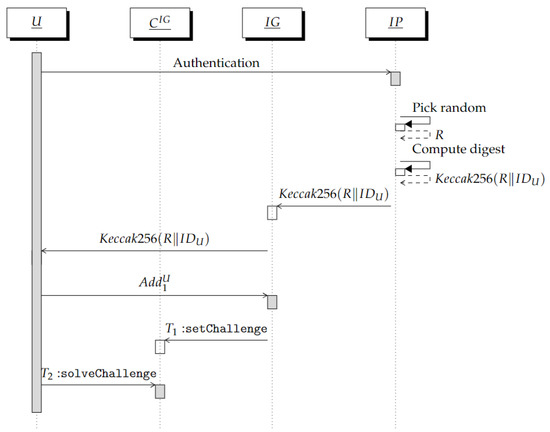
Figure 1.
Sequence diagram of the interaction between U and .
The next two interactions are between U and and between U and , respectively. They have to be performed in anonymous form without any authentication of U. Clearly, to avoid IP geolocation, anonymous communication protocols such as Tor [37] and VPNs [38] can be adopted. We do not treat this aspect in detail since it is out of the scope of this paper.
5.2. Interaction between U and
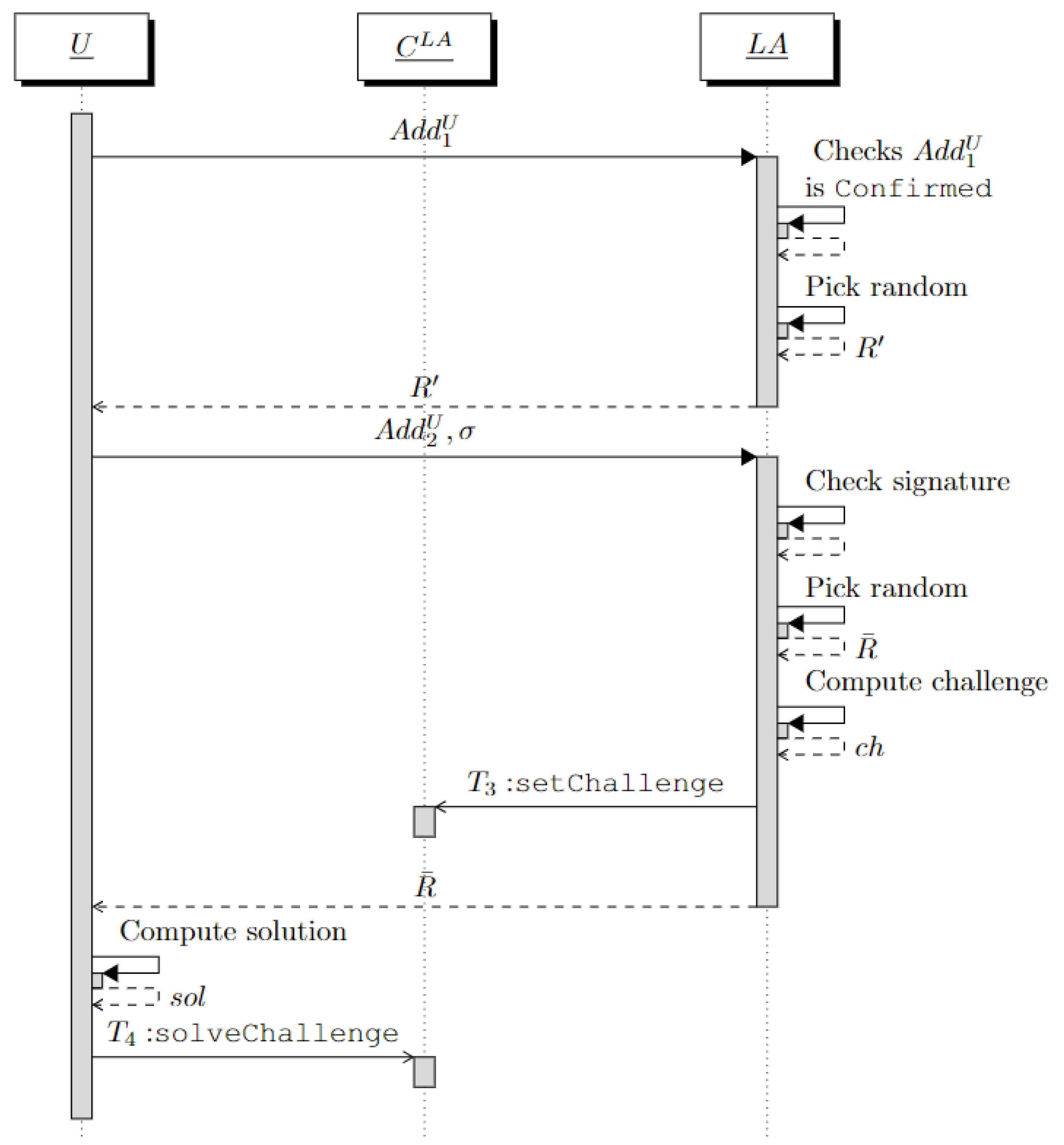
Through this interaction, links and without knowing the real identity of U.
First, U (anonymously) contacts and provides it with . needs to verify two conditions. The first is that is an Ethereum address associated with a real identity. However, does not need to know such a real identity. This condition can be easily verified by checking that is in state “Confirmed” on . The second condition is that really belongs to the user contacting . This is carried out to avoid a user trying to impersonate another user already authenticated with .
Even though the challenge–response mechanism used in the previous section allows this task, we should not use it. Indeed, it requires some interactions through the blockchain that would disclose the linkage to anyone.
Therefore, to verify the second condition, generates a random and provides U with it. U signs with the private key associated with , obtaining a signature . Finally, U replies to with the pair .
Starting from and , verifies the signature and retrieves the public key associated with . Then, as explained in Section 2, computes the hash function Keccak256 on this public key and takes the last 20 bytes to obtain the address . If , then is sure that the user contacting it owns .
At this point, needs to verify that U owns . The same challenge–response mechanism used with is adopted. This way, will move to the state “Confirmed” on the instance and will be used by in the next interaction with U.
In detail, picks a random and generates a challenge .
Then, generates a transaction = . This transaction invokes the function setChallenge that associates the challenge with the address and sets in state “To Confirm”. The random is provided to U.
U computes the solution of the challenge as = and generates the transaction = . This proves to that U is the owner of , which will be set in state “Confirmed” by the function solveChallenge.
Finally, verifies the state “Confirmed” of the address and locally stores the tuple .
The above steps are summarized in the sequence diagram of Figure 2.
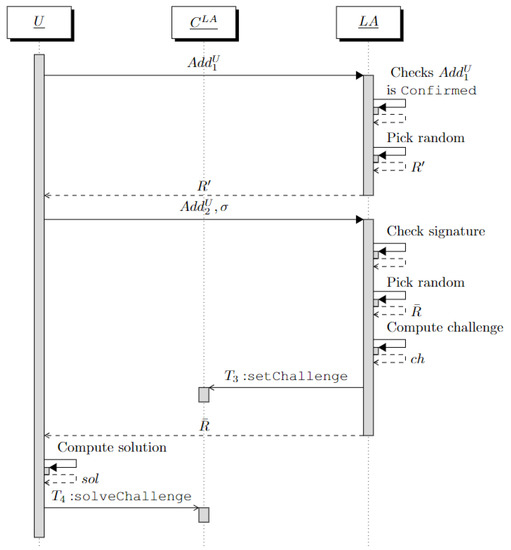
Figure 2.
Sequence diagram of the interaction between U and .
5.3. Interaction between U and
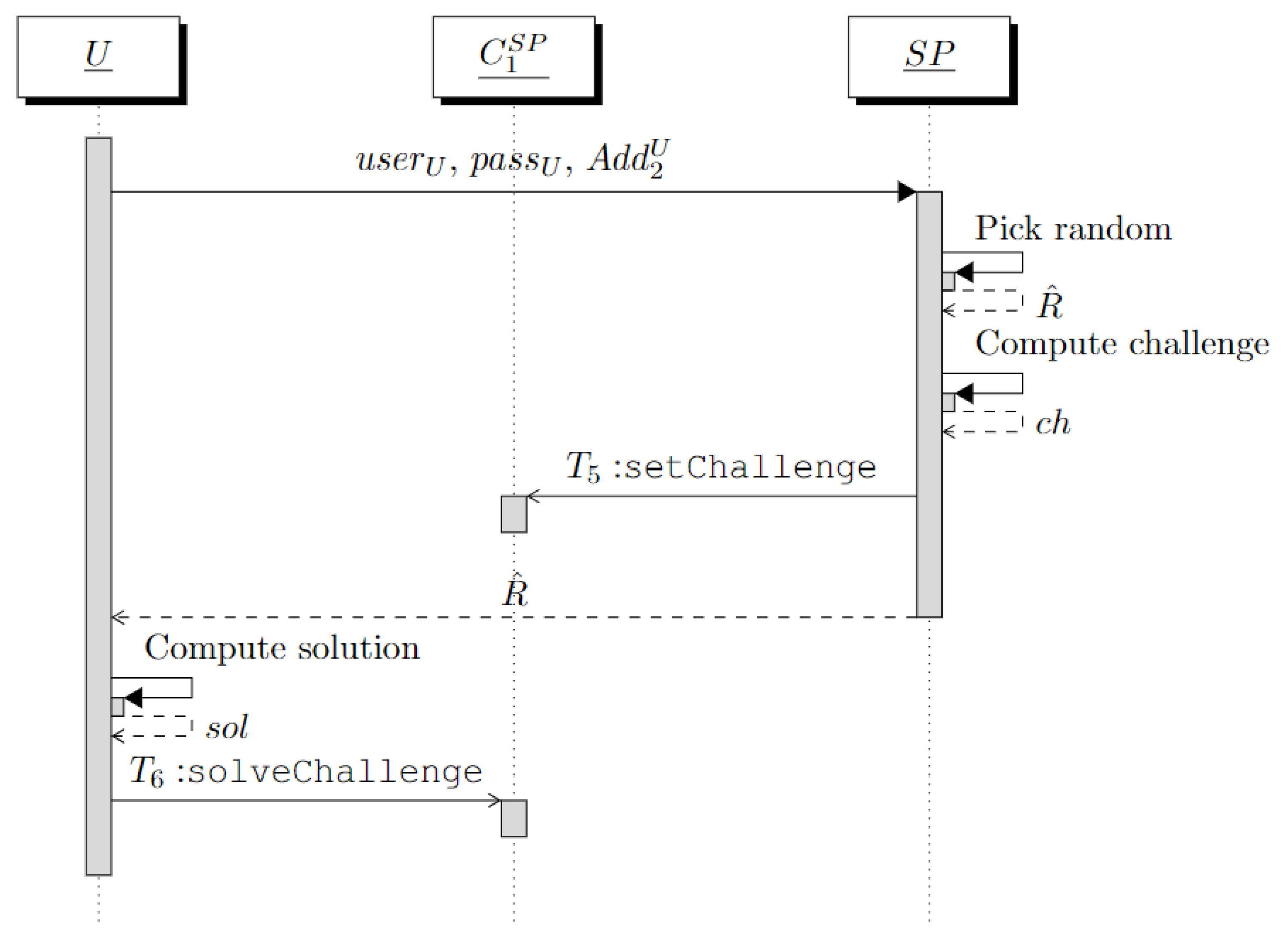
Through the third interaction of our protocol, associates with a pseudonym chosen by U. For simplicity, we assume that the access credentials of U are represented by a username–password pair. However, the password can be replaced by the device ID of the user’s phone, as with Whisper [5].
Again, we exploit the challenge–response mechanism of Section 4.
U provides with , where is the password chosen by U. verifies that is in state “Confirmed” on the instance . Then, it picks a random and generates the challenge . Finally, generates a transaction = . This transaction invokes the function setChallenge, which associates the challenge with the address and sets to state “To Confirm”. The random is provided to U.
U computes the solution to the challenge as and generates the transaction . This proves to that U is the owner of , which will be set to state “Confirmed” by the function solveChallenge.
Finally, verifies the state “Confirmed” of the address on the instance and locally stores the tuple . Observe that the password is not included in the notarized information since it is used by only to authenticate U.
The above steps are summarized in the sequence diagram of Figure 3.
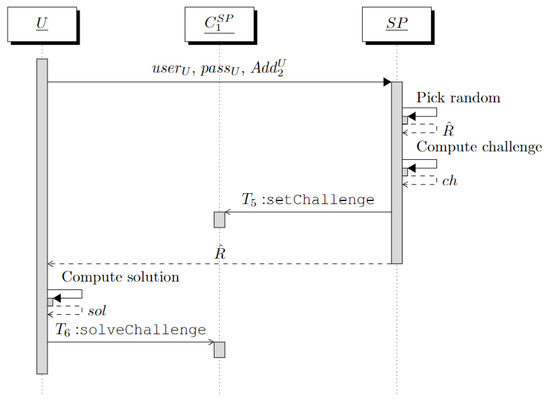
Figure 3.
Sequence diagram of the interaction between U and .
As a final remark, we want to observe that, if the user is not registered with IP, SP does not provide the anonymous service. Indeed, it checks that the address is in the state “Confirmed”. Moreover, this state is set by , which, in turn, verifies that is in the state “Confirmed”. The state “Confirmed” of is set by only after the identity of U is verified by .
We conclude this section by observing that, as we will see in Section 6.2, in order to develop a user-friendly application, almost allof the client-side operations are performed automatically by some scripts without requiring the interaction of the users. They just have to confirm some operations (the generation of the transactions and signature of messages) for security reasons. Furthermore, to simplify the client-side operations, the interactions of U with and are merged into a single interaction with in which the user is redirected to .
5.4. Account Information Recovery
Suppose U loses the access credentials with and wants to recover the account information . U just needs to prove to the ownership of the Ethereum address with which U is registered at . This is carried out, as already discussed in the previous sections, through the challenge–response mechanism involving the instance of the smart contract. After verifying the possession of , enables the standard module to change the password and provides U with .
5.5. Law-Enforced Re-Identification of U
Suppose a law court receives a notification about an illegal behavior of a user with username when leveraging the anonymous service provided by . After verifying whether such behavior violates the law, it emits an order to ask to retrieve, in a verifiable way, the real identity of the user with username . First, contacts to obtain the Ethereum address associated with . Then, retrieves the Ethereum address linked with (this linkage is maintained by itself). Subsequently, contacts to obtain the digest associated with . Finally, contacts to obtain the real identity of U associated with . Observe that the mapping is verifiable through the instance by disclosing the random . Similarly, the mapping is verifiable through the instance by disclosing the random . Finally, the mapping is verifiable through the instance by disclosing the random R.
5.6. Linkage of Multiple Anonymous Accounts
Suppose that a law court wants to monitor the anonymous activity of the user U on multiple service providers. This means that the court wants to associate the identity with all of the usernames used in the various service providers. As in Section 5.5, suppose that the court charges the linkage agency to perform this operation. First, contacts . We recall that stores a set of tuples in the form . Observe that each tuple is associated with a service provider to which U requires an anonymous service. For each tuple T, contacts , and, through , it retrieves the address . Then, through the mapping maintained by itself, retrieves the address used by U with a service provider . Finally, through , discovers the username .
As in Section 5.5, all of the linkages are verifiable on blockchain.
6. Implementation and Time-Cost Analysis
In this section, we describe the prototype developed to implement the solution proposed in Section 5. The source code of our prototype is publicly available on GitHub at https://github.com/SaraLazz/AccountAnon (accessed on 18 August 2022).
6.1. Adopted Technologies
We developed three JAVA web applications to implement , , and . Each application leverages the Apache Struts2 web framework [39]. Struts is an open-source framework that employs a model, view, controller (MVC) architecture and that enables the creation of maintainable and flexible web applications. The view part of our web applications was constructed using JavaServer Pages (JSP) [40]. To improve the user experience, we used asynchronous JavaScript and XML (AJAX) [41], thus allowing the user’s interaction with the application to happen asynchronously.
As explained in the previous sections, our web applications need to interact with the Ethereum blockchain both server-side and client-side.
Regarding server-side, our applications leverage on Infura [42]. The Infura API suite allows us to access the Ethereum network through HTTPS and WebSockets. Infura has the main advantage of providing all of the necessary tools to develop on Ethereum, without the need to locally run any blockchain node.
Regarding client-side, our applications interface with MetaMask [43] via JavaScript. MetaMask is a very popular application that allows users to write on the blockchain. One of the main benefits of using MetaMask is that users’ passwords and keys remain on the user device since they are not shared with any other parties interacting with it.
6.2. Implementation Detail and Prototype Functionalities
Through this section, we describe in detail the implementation of the prototype (including the three web applications) and describe how it works.
The implementation of the web application (whose user interface is represented in Figure 4) follows on from what has been described in Section 5. The selection of the address is executed client-side via JavaScript connecting to MetaMask. It replies with the address that is currently selected in the application. At this point, the challenge–response mechanism starts. generates the challenge server-side and invokes the smart contract function setChallenge via Infura API. After this, the user, client-side, solves the challenge by invoking the smart contract function solveChallenge via MetaMask.
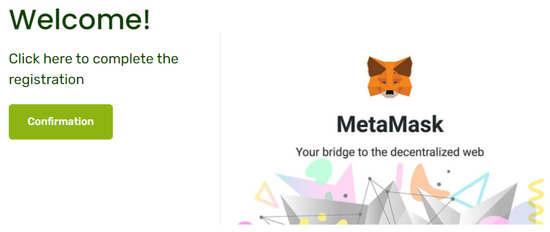
Figure 4.
User interface of .
Now, we move on to the other two applications.
Even though the high-level workflow described in Section 5 only requires separate interactions between U and the two parties and , the technical implementation of the prototype performs this transparently for the user through a redirection of the web traffic from to .
In detail, when the user asks to subscribe to , it will redirect the user to for the verification of their Ethereum addresses. The procedure executed with is divided into four steps, as represented in Figure 5.
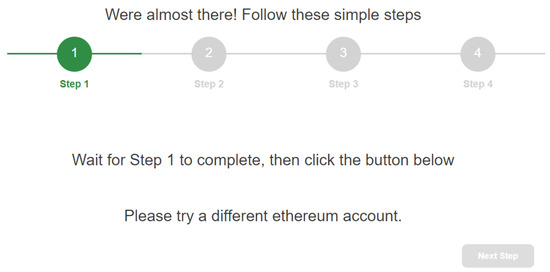
Figure 5.
Selection of a -validated Ethereum account.
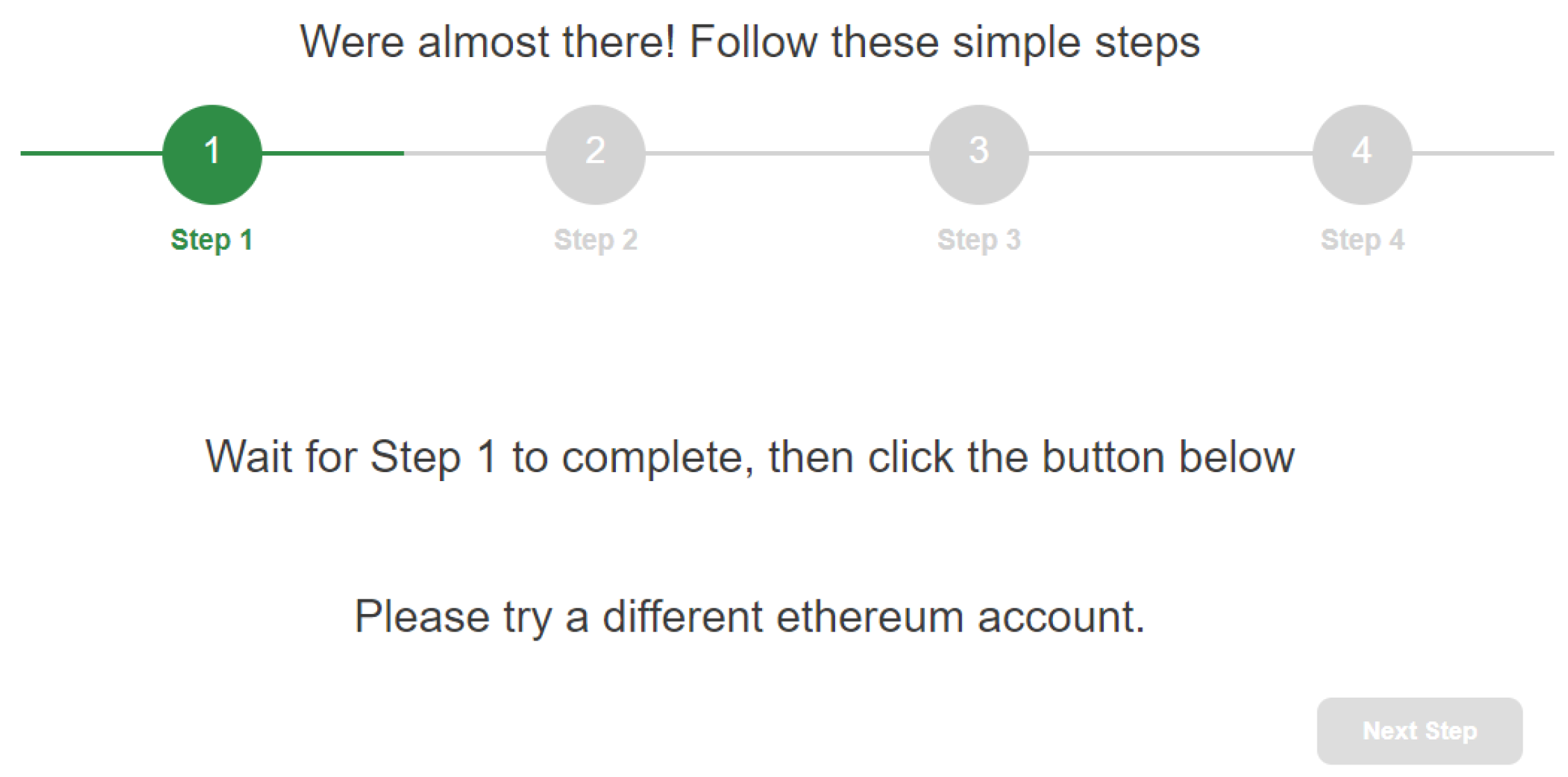
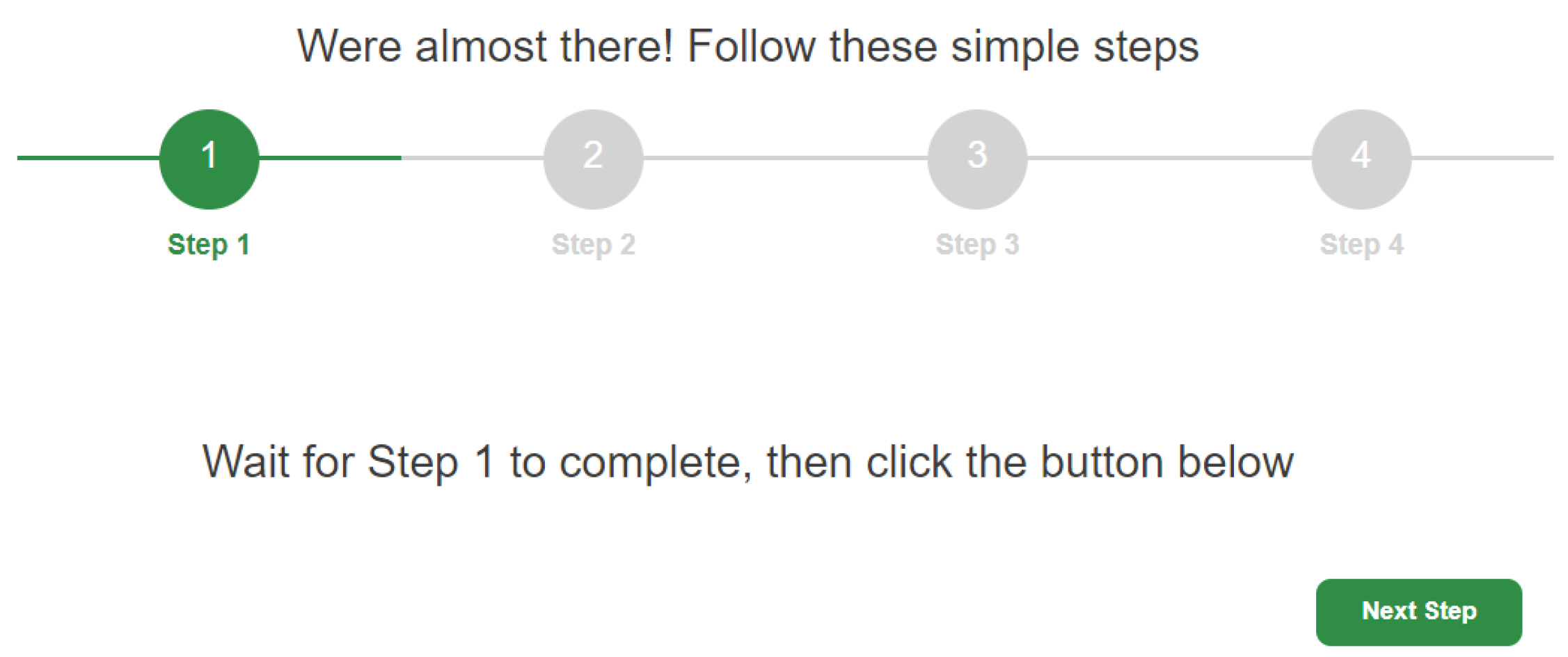
The first step is to aid the user in the selection (on Metamask) of the address so that the user does not have to remember it. The client-side application asks MetaMask the current address selected by the user and verifies whether it is or is not validated by the (i.e., if it is memorized in state “Confirmed” in the instance ). In the case where it is not validated, the application returns to the user a message asking them to select a different address (Figure 5). The procedure continues until the user selects an address validated by . At this point, the user can proceed with the second step (Figure 6).
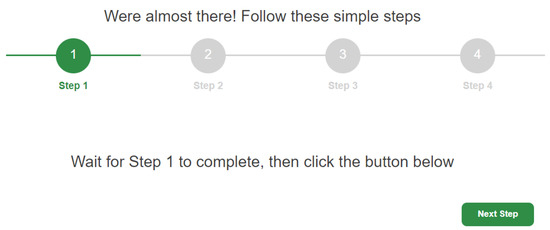
Figure 6.
Completion of Step 1.
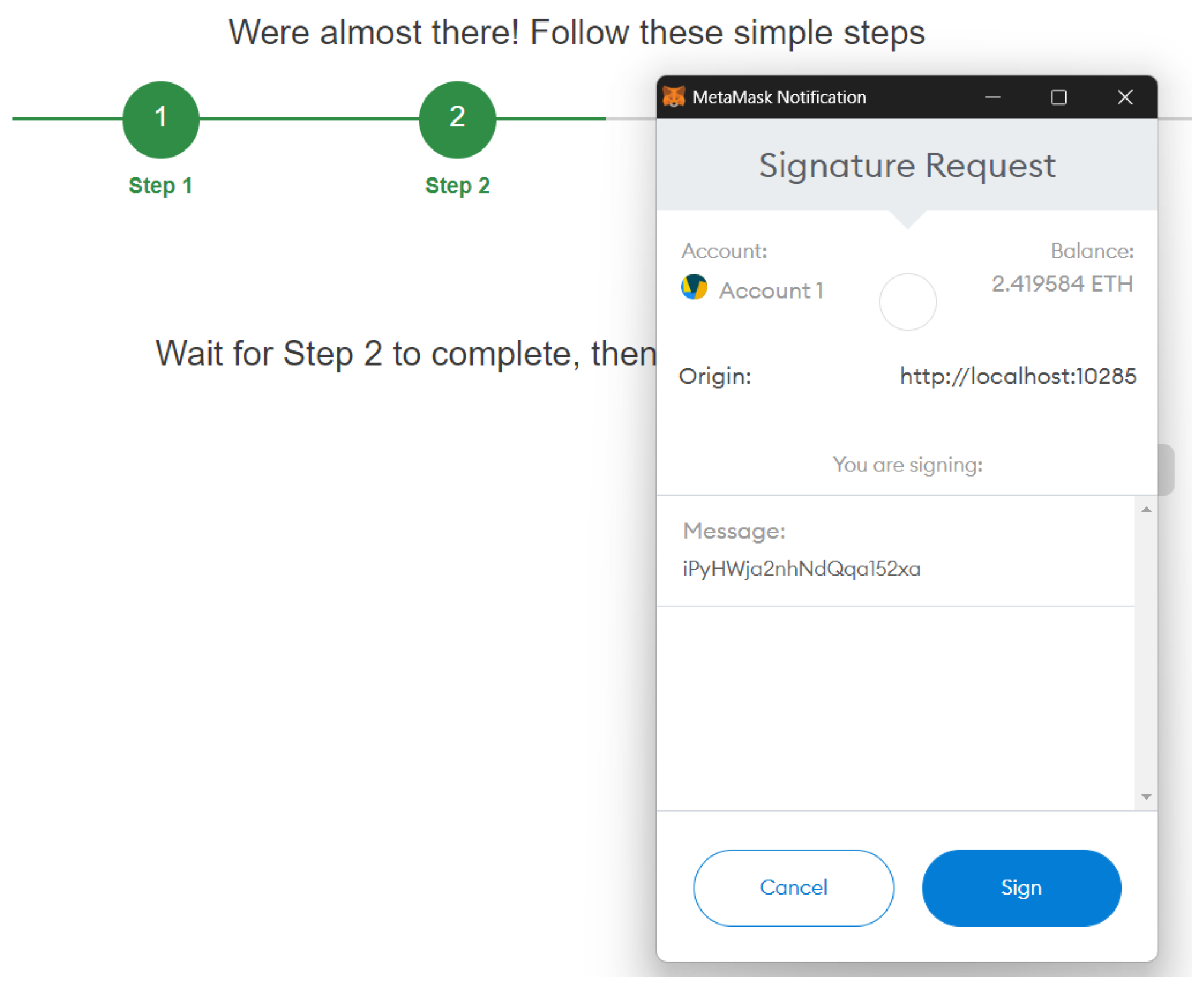
During the second step, the user is asked to sign a random provided by the server (Figure 7). Then, the signature is sent to the server along with the address so that the server can verify that the user owns the address .
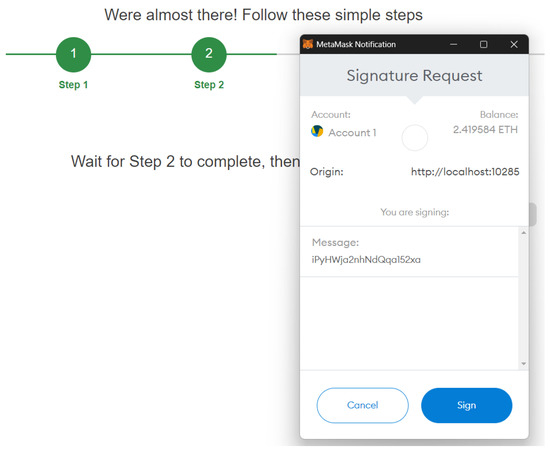
Figure 7.
Signature of the challenge.
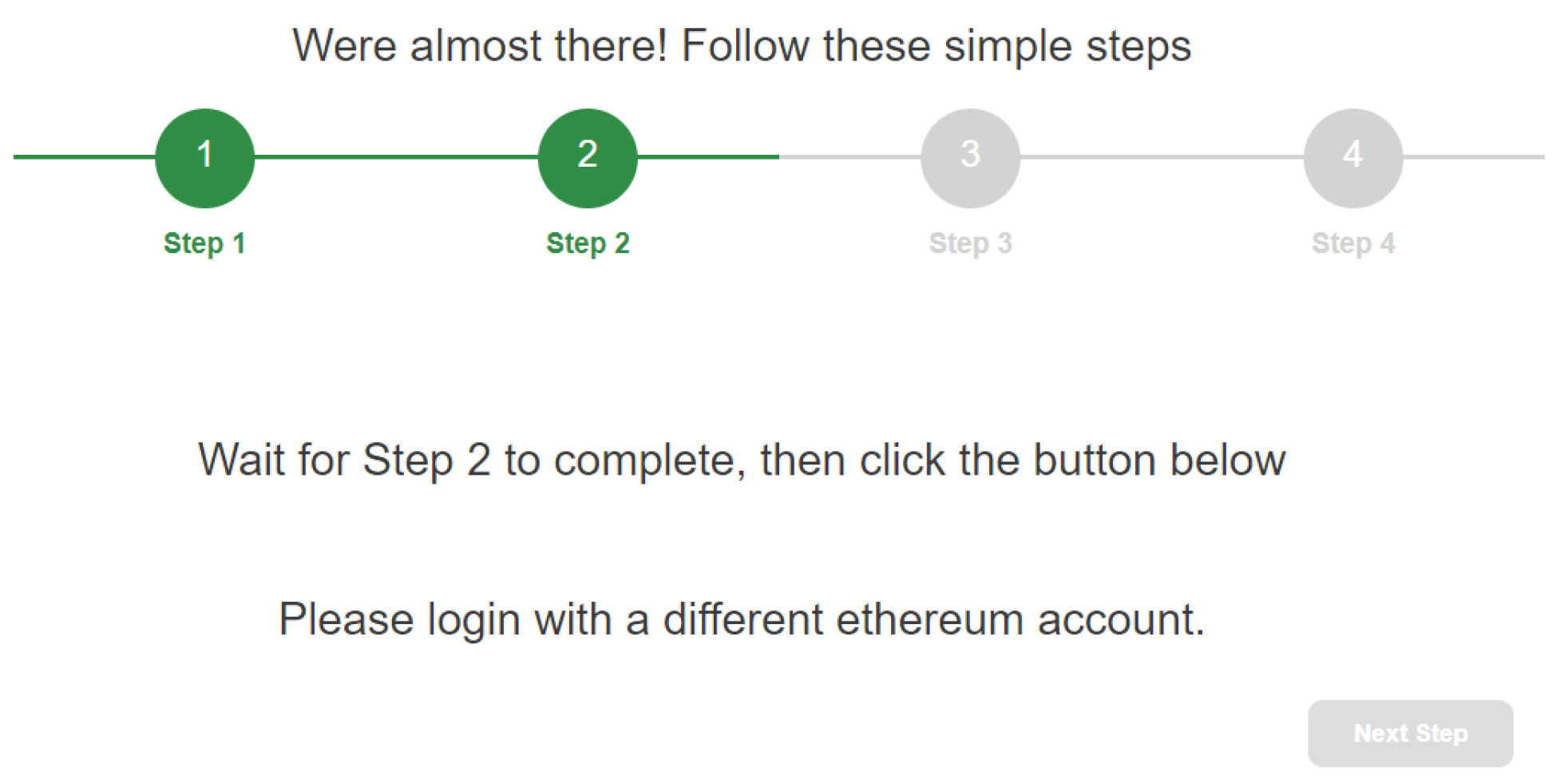
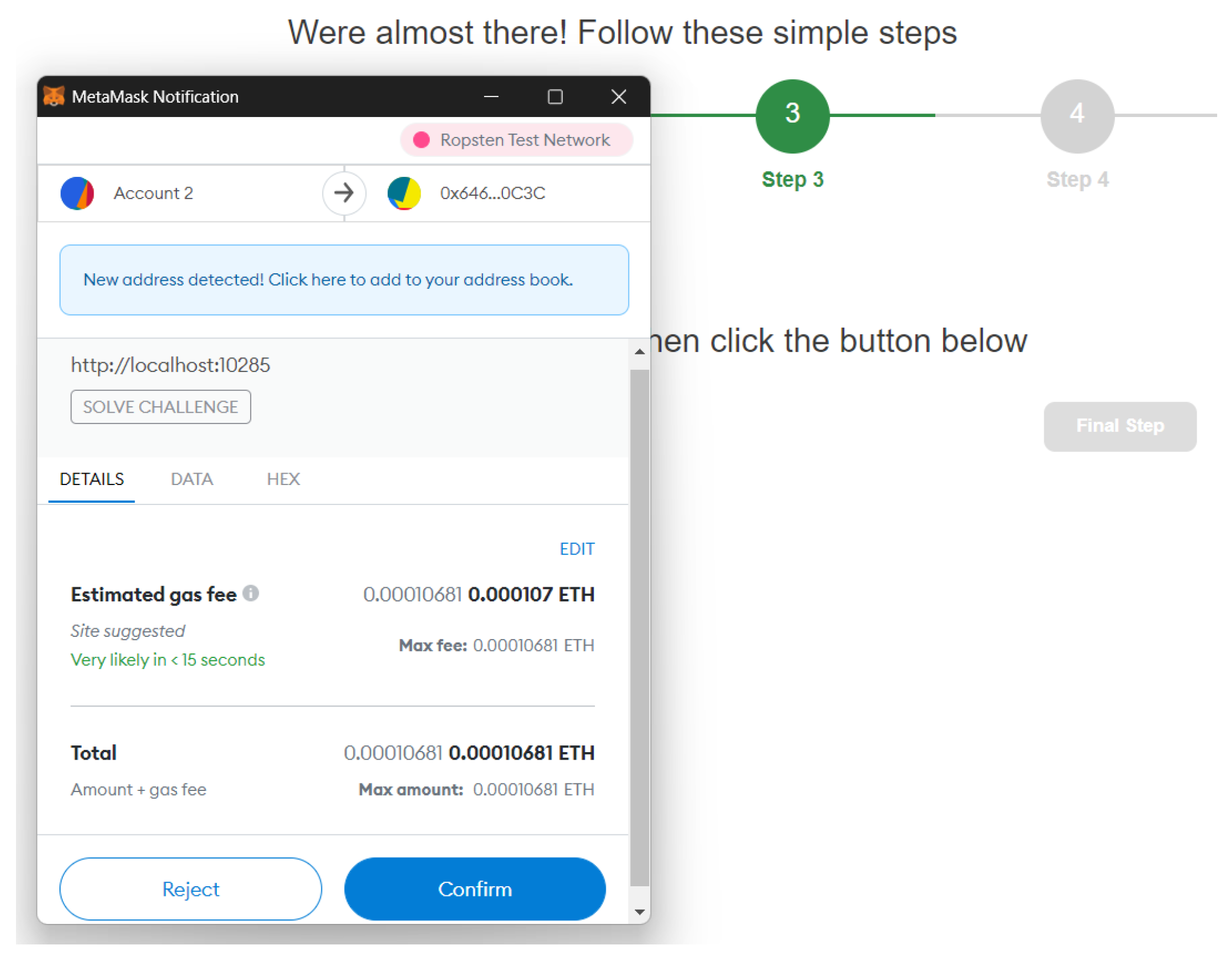
During the third step, the user is asked to switch to an address that is different from (Figure 8). After carrying this out, the newly selected address () is sent to . At this point, the challenge–response mechanism starts. Therefore, sets a challenge on the instance and provides the client with all of the information necessary to solve this challenge (i.e., a random ). Once received, the user just has to authorize the transaction on MetaMask in order to invoke the solveChallenge function of the smart contract (Figure 9).
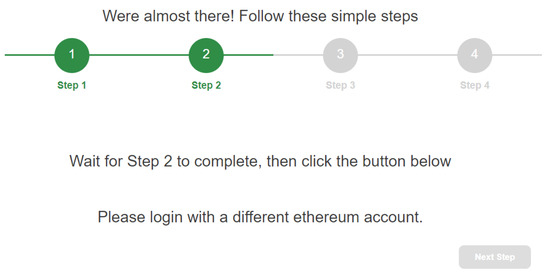
Figure 8.
Selection of the Ethereum address .
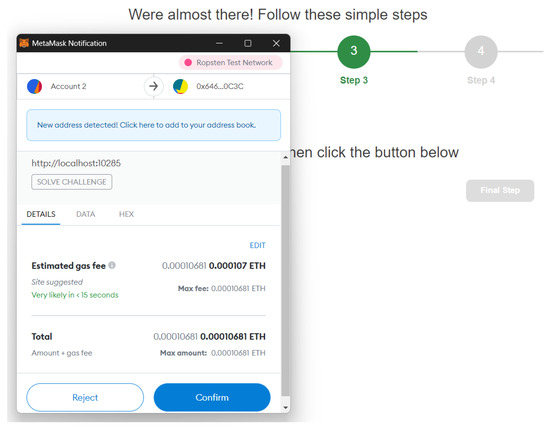
Figure 9.
Transaction to solve the challenge.
Once this transaction is confirmed, the user can proceed to the fourth step, which consists of a message confirming that the whole procedure succeeded. At this point, will redirect the user to , forwarding the address (Figure 10).
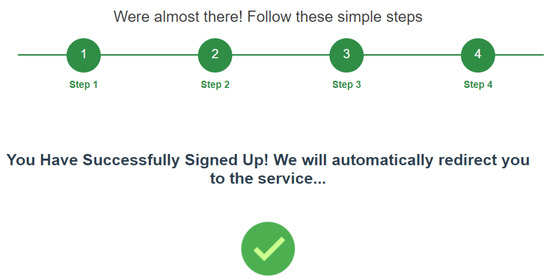
Figure 10.
Completion of the interaction with .
On (Figure 11), after another challenge–response mechanism, the user can subscribe by entering a username and a password that will be memorized by along with the address .
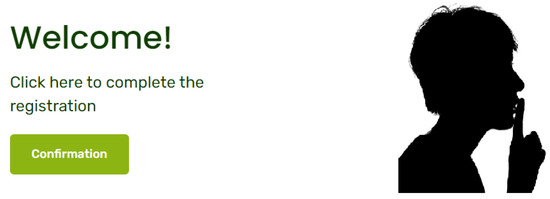
Figure 11.
Subscription to .
This address is also used in the case where the user forgets their login credentials. Again, the procedure used to recover them consists of the application of the challenge–response mechanism. We recall that the user needs to select the right address to invoke the solveChallenge function of the smart contract. To aid the user in the selection of the right address, the client-side module of implements the same mechanism seen in the first step of the procedure executed with . We highlight that this design choice has two main benefits: (i) the user does not have to memorize and, (ii) it being a procedure performed exclusively client-side, the user’s other addresses are not disclosed to the server.
6.3. Time-Cost Analysis
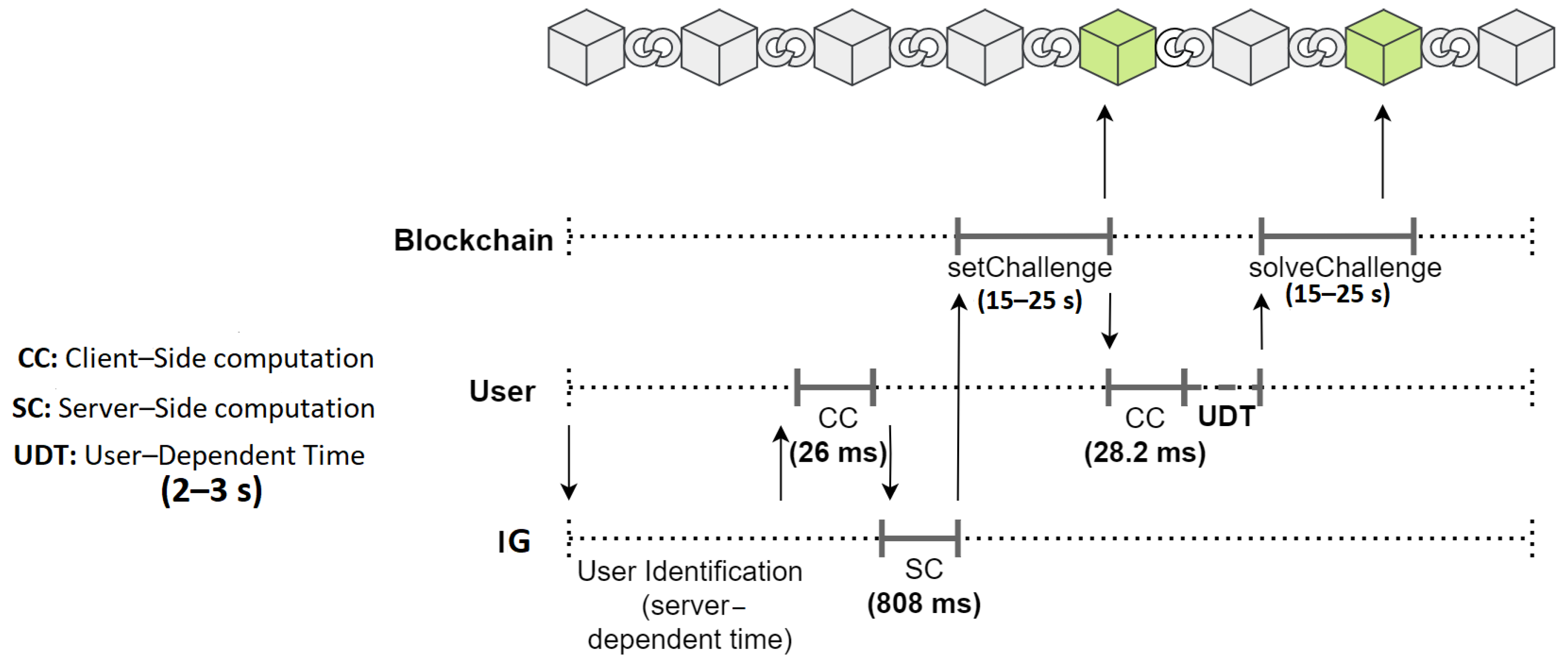
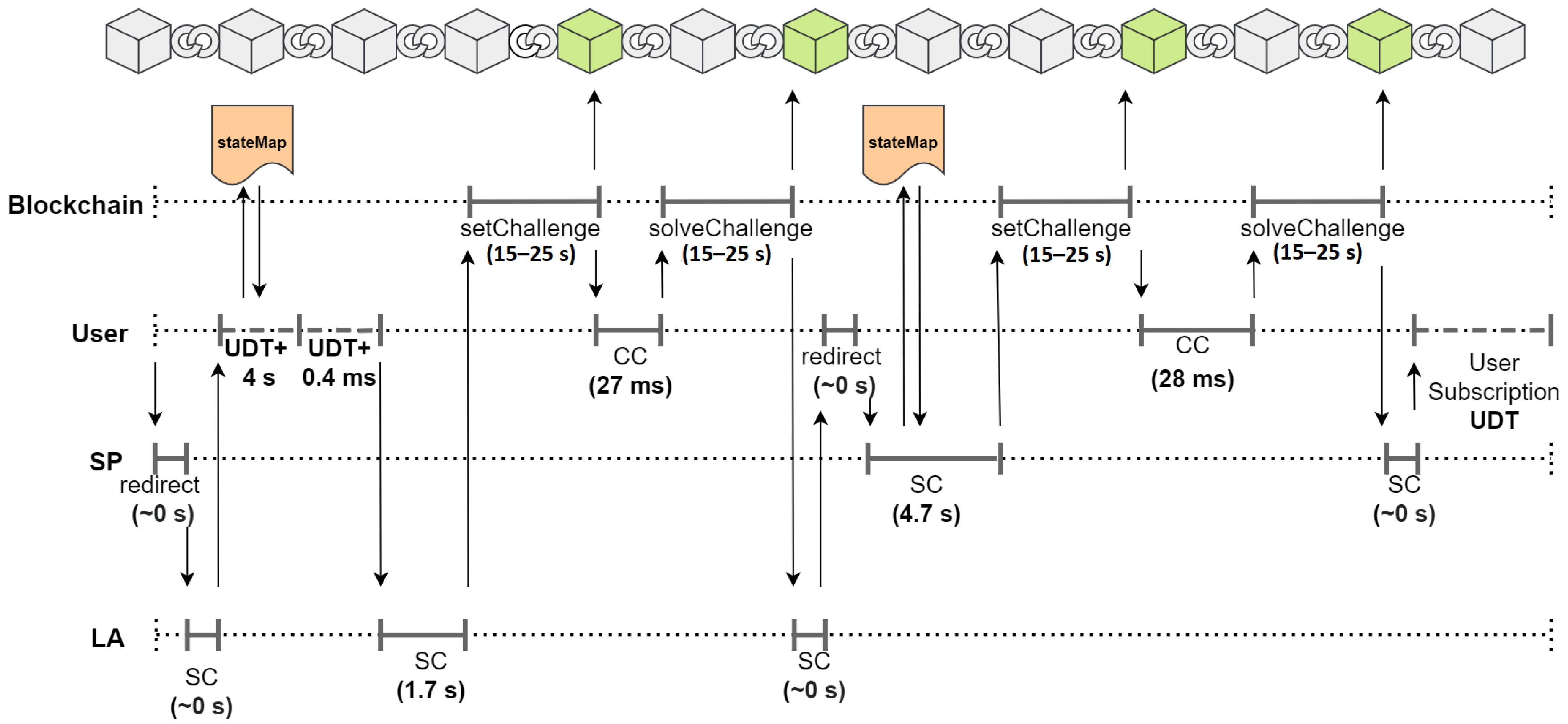
We analyzed our implementation by measuring the time taken to perform the operations required by our solution. The measurements were performed by using a personal computer equipped with a 2.8 GHz Intel i7-1165G7 CPU and 16 GB of RAM. The obtained results are reported in Figure 12 and Figure 13.
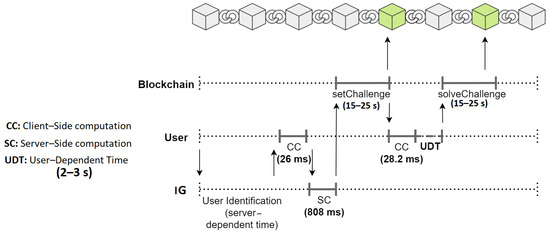
Figure 12.
Timeline of the interactions between user, , and blockchain.
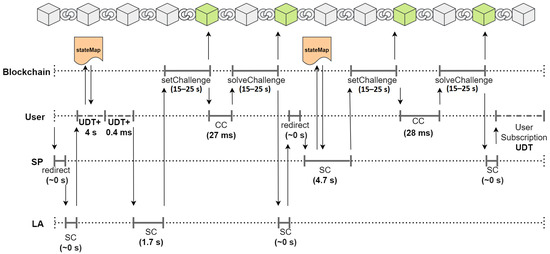
Figure 13.
Timeline of the interactions between user, , , and blockchain.
In Figure 12, the interaction between the user, , and blockchain is represented. In Figure 13, the interaction between the user, , , and blockchain is reported.
We distinguished between the tasks the executed client-side (marked by ) and the tasks executed server-side (marked by ). The time intervals necessary to perform these two kinds of tasks are represented with a solid grey line. For each of these intervals, the time needed to complete it is reported in the figures.
We also represent the user-dependent time intervals (marked by ) with a grey dashed line. Since the duration of these time intervals depends on the time the users need to click the buttons, we assumed realistic average times of 2–3 s.
Finally, the measurements of the time intervals between sending a transaction to the blockchain and confirming the transaction itself are reported in the two figures. To perform these measurements, we chose the Ropsten test network [44], since it is able to reproduce the network conditions of the live Ethereum MainNet.
Our measurements show that the time intervals pertaining to the blockchain timeline lasted 15–25 s. From our experiments, these values, compared to the duration of the other measured time intervals, appear to be predominant but still acceptable.
A factor influencing the duration of the time intervals pertaining to the blockchain is the selected gas price. Indeed, a high gas price causes a transaction to be processed faster, at the cost of greater transaction fees. For our experiments, we adopted the default gas price suggested by Metamask.
To summarize the results, we obtained that the entire registration procedure with requires less than 1 min, whereas the registration procedure with (including the interaction with ) requires less than 2 min.
By using the default gas price suggested by Metamask, we also measured the costs, in terms of Ethers, resulting from the following operations: smart contract deployment, the execution of the setChallenge function, and the execution of the solveChallenge function.
In the following, we report the resulting costs in terms of Ethers (ETH) and US dollars in June 2022:
- Smart contract deployment: 0.00296997 ETH/USD 5.34;
- setChallenge execution: 0.00029962 ETH/USD 0.54;
- solveChallenge execution: 0.00013468 ETH/USD 0.24.
We stress that, although the smart contract deployment has a relatively high cost, it is a one-time operation performed by , , and , and therefore its cost is sustainable.
From the above results, we can estimate the overall cost of a user registration, which is approximately USD . In a real business model, this cost can be charged to the user willing to use the anonymous service. Therefore, our solution does not result in significant costs, neither for the user nor for the service providers.
7. Security Analysis
In this section, we discuss the security guarantees offered by our solution.
We analyze the following two compromises possibly affecting our protocol.
- C1: an adversary, not including the collaboration of , , and simultaneously, is able to discover the link between the username and the real identity of a user.
- C2: an adversary is able to forge a fake link, publicly verifiable on the blockchain, between the username and the real identity of a user.
Regarding C1, it represents a privacy compromise. As already discussed, our protocol allows for the de-anonymization of a username only when , , and collaborate. In the other cases, the real identity–username link should not be disclosed to anyone.
Concerning C2, we refer to attacks in which the adversary attempts to associate a username of a user U with an identity of another user to falsely accuse the latter of an illegal behavior performed by U.
Regarding the trust required to the involved actors, we only make the following assumption.
- A: is honest but curious, in the sense that it legally performs the steps of the protocols but attempts to cause the two compromises C1 and C2.
In other words, A requires that does not swap the real identities of two users. This is a standard assumption of all of the identity management systems. Indeed, the role of an identity provider is just to certify the real identity of users. However, in our threat model, we allow to disclose the identities that it knows and show that this does not affect the privacy of the users.
No assumption is made on , , and . They can be considered fully malicious with respect to the considered compromises.
Now, we discuss in detail the two compromises and show how our protocol prevents them.
Compromise C1. This compromise occurs when the adversary identifies the real identity of a user U associated with a given username .
Since external users just see the transactions originating from some Ethereum addresses on the blockchain, we consider , , , and as adversaries. They can access the blockchain too; then, they have at least the knowledge of all external users. By excluding the collaboration of , , and (by hypothesis), we consider the collaboration of the three tuples , , and as an adversary and show that C1 does not occur.
We start by considering the collaboration of , , and . Given the user U, knows the real identity of U. Through the collaboration with , links with the Ethereum address . Then, through the collaboration with , can discover the Ethereum address linked with . However, no information about the username of U is available to , , and . Indeed, the only public information containing (in obfuscated form) is the transaction generated by U with the address . This transaction contains the solution to the challenge . Without (maintained by ), it is not possible to also reverse the hash function Keccak256 through dictionary attacks on all of the possible usernames.
A similar reasoning applies when considering the collaboration of , , and as an adversary. Their collaboration just allows for the linkage of , , and , but no information is available to , , and about .
Indeed, the only public information containing (in obfuscated form) is the transaction generated by U with the address . This transaction contains the solution to the challenge . Without R (maintained by ), it is not possible to reverse the hash function Keccak256. is the only information received by from , since the assertion does not contain any information linked to .
Finally, consider the adversary composed of the collaboration of , , and . , through , knows the mapping , whereas maintains the mapping . However, without the mapping (maintained by ), they are not able to link with . The only public information containing this mapping (in obfuscated form) is the transaction generated by U. This contains the solution to the challenge . Again, without and (maintained by ), it is not possible to reverse the hash function Keccak256.
Compromise C2. This compromise occurs when an adversary forges a valid link (publicly verifiable on the blockchain) between the real identity of a user and a username of a different user U.
To forge a valid link, has to be present (in obfuscated form) in a transaction intended for the instance . By Assumption A, legally performs the steps of the protocol and does not provide a tampered digest associated with the real identity of a user not requiring the anonymous service. Therefore, we consider as a user with Ethereum address such that the link between and can be verified through the instance and the random R provided by .
To perform the compromise C2, the attacker has two possibilities. The first possibility is to forge a fake link between and verifiable through the instance such that is associated with by . To achieve this, the blockchain would have a transaction originated by including the challenge , where is a signature obtained from the private key associated with the address . Moreover, another transaction originated by , including the solution to the challenge, would be present on the blockchain. Even though the attacker coincides with the collaboration of and U (the only parties that can generate these two transactions), it is not able to forge the signature without the collaboration of . Therefore, this first case cannot occur.
The second possibility is that a valid link between and (both belonging to ) exists and the attacker attempts to forge a fake link between and . However, similar to the previous case, in order to accomplish this, the blockchain would have a transaction originated by , including the challenge , and a transaction originated by , including the solution to the challenge. Even though the attacker coincides with the collaboration of and U, it is able to forge the first transaction but not the second. Therefore, this possibility also cannot occur.
This concludes the security analysis.
8. Conclusions and Discussion
Anonymous services have shown increasing popularity over the years. However, for most of these services, it is crucial to not just provide anonymity to the user but also to implement an accountability mechanism.
In this paper, we propose a blockchain-based approach as a solution to the accountability issue in anonymous services. Our solution requires that only the co-operation of three independent parties (, , and ) can de-anonymize a user who is performing illegally on the platform. This fact represents the main advantage of our solution since it makes an illegitimate attempt to de-anonymize the user unlikely.
To prove that our solution can be applied in real-life contexts, we provide a prototype that takes into account usability aspects, as it aims to reduce the number of operations performed client-side. Moreover we provide a time and cost analysis of our solution in order to demonstrate its feasibility.
According to our cost analysis, the most expensive operation consists in the smart contract deployment in the Ethereum network (approximately USD 5). However, such an operation is meant to be performed only once by , , and . Hence, it is safe to assume that such a cost is sustainable. The other operation that they have to perform is setChallenge, whose cost is estimated to be USD . Even though this operation has to be performed for each user willing to subscribe to an anonymous service, its results are acceptable for the service providers. However, in a possible business model, the provider can charge the user for this cost. On the other hand, the cost to perform the solveChallenge operation is an equally low price (USD ) and is meant to be paid directly by the user.
Considering instead the cost of a complete user registration (which requires the execution of both setChallenge and solveChallenge), it turns out to be very cheap (around USD 2). It is therefore realistic to assume that this cost can be charged to the user in order to not burden the providers.
Regarding the time analysis that we conducted, our study shows that the registration procedure with requires less than 1 min, whereas the registration procedure with and requires less than 2 min. It is worth noting that the time intervals related to the operations involving the blockchain are predominant (ranging from 15 to 25 s). However, despite this tolerable drawback, relying on the blockchain for these operations has the advantage of making them immutable and publicly verifiable. Therefore, untrusted parties (, , and ) cannot hold other users accountable instead of the real misbehaving user. Furthermore, as the entire registration process is one time, the overall time taken to perform a complete registration is reasonable.
To conclude, our solution is shown to be usable and reasonably time and cost-efficient. As for the cost, we may argue that honest users might be encouraged to pay for a service that, in addition to anonymity, would guarantee them the possibility of reporting dishonest users who might take advantage of the anonymous service to threaten them. Moreover, the anonymous service provider itself might be encouraged to employ our solution since accountability guarantees can discourage users from engaging in illegal behaviour, thus improving the overall reputation of the anonymous service provider.
As a future work, we plan to further increase the technology readiness level of our research by proposing its application to real-life environments, possibly with industrial partners.
Author Contributions
Conceptualization, F.B., V.D.A. and S.L.; methodology, F.B., V.D.A. and S.L.; software, V.D.A. and S.L.; validation, F.B., V.D.A. and S.L.; formal analysis, F.B., V.D.A. and S.L.; investigation, F.B., V.D.A. and S.L.; resources, V.D.A. and S.L.; data curation, V.D.A. and S.L.; writing—original draft preparation, F.B., V.D.A. and S.L.; writing—review and editing, F.B., V.D.A. and S.L.; visualization, V.D.A. and S.L.; supervision, F.B.; project administration, F.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
This work has been developed in coordination with the activities of “iCARE” project (CUP J39J14001400007)-action 10.5.12.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| EOA | External Owned Account |
| U | User |
| SP | Service Provider |
| IG | Identity Gateway |
| LA | Linkage Agency |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| VM | Virtual Machine |
| UDT | User-Dependent Time |
| CC | Client-side Computation |
| SC | Server-side Computation |
| ETH | Ether |
| P2P | Peer-to-Peer |
| MVC | Model View Controller |
| JSP | JavaServer Page |
| AJAX | Asynchronous JavaScript and XML |
References
- Harkavy, M.; Tygar, J.D.; Kikuchi, H. Electronic auctions with private bids. In Proceedings of the USENIX Workshop on Electronic Commerce, Boston, MA, USA, 31 August–3 September 1998. [Google Scholar]
- Liu, B.; Xie, S.; Yang, Y.; Wang, R.; Hong, Y. Privacy preserving divisible double auction with a hybridized TEE-blockchain system. Cybersecurity 2021, 4, 1–14. [Google Scholar] [CrossRef]
- Hohenberger, S.; Myers, S.; Pass, R. ANONIZE: A large-scale anonymous survey system. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 375–389. [Google Scholar]
- Carnley, R.; Bagui, S. A Public Infrastructure for a Trusted Wireless World. Future Internet 2022, 14, 200. [Google Scholar] [CrossRef]
- Wang, G.; Wang, B.; Wang, T.; Nika, A.; Zheng, H.; Zhao, B.Y. Whispers in the Dark: Analysis of an Anonymous Social Network. In Proceedings of the 2014 Conference on Internet Measurement Conference (IMC ’14), Vancouver, BC, Canada, 5–7 November 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 137–150. [Google Scholar] [CrossRef]
- Gerhart, N.; Koohikamali, M. Social network migration and anonymity expectations: What anonymous social network apps offer. Comput. Hum. Behav. 2019, 95, 101–113. [Google Scholar] [CrossRef]
- Hosseinmardi, H.; Han, R.; Lv, Q.; Mishra, S.; Ghasemianlangroodi, A. Analyzing negative user behavior in a semi-anonymous social network. arXiv 2014, arXiv:1404.3839v1. [Google Scholar]
- Farkas, C.; Ziegler, G.; Meretei, A.; Lörincz, A. Anonymity and accountability in self-organizing electronic communities. In Proceedings of the 2002 ACM workshop on Privacy in the Electronic Society, Washington, DC, USA, 21 November 2002; pp. 81–90. [Google Scholar]
- Buccafurri, F.; Lax, G.; Nicolazzo, S.; Nocera, A. Accountability-preserving anonymous delivery of cloud services. In International Conference on Trust and Privacy in Digital Business; Springer: Berlin/Heidelberg, Germany, 2015; pp. 124–135. [Google Scholar]
- Buccafurri, F.; De Angelis, V.; Lax, G.; Musarella, L.; Russo, A. An Attribute-Based Privacy-Preserving Ethereum Solution for Service Delivery with Accountability Requirements. In ARES ’19: Proceedings of the 14th International Conference on Availability, Reliability and Security; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Russo, A.; Lax, G.; Dromard, B.; Mezred, M. A System to Access Online Services with Minimal Personal Information Disclosure. Inf. Syst. Front. 2021, 1–13. [Google Scholar] [CrossRef]
- Camenisch, J.; Lysyanskaya, A. An efficient system for non-transferable anonymous credentials with optional anonymity revocation. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2001; pp. 93–118. [Google Scholar]
- Backes, M.; Camenisch, J.; Sommer, D. Anonymous yet accountable access control. In Proceedings of the 2005 ACM Workshop on Privacy in the Electronic Society, Alexandria, VA, USA, 7 November 2005; pp. 40–46. [Google Scholar]
- Teranishi, I.; Sako, K. K-times anonymous authentication with a constant proving cost. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2006; pp. 525–542. [Google Scholar]
- Lysyanskaya, A.; Rivest, R.L.; Sahai, A.; Wolf, S. Pseudonym systems. In International Workshop on Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 1999; pp. 184–199. [Google Scholar]
- Damgård, I.B. Payment systems and credential mechanisms with provable security against abuse by individuals. In Conference on the Theory and Application of Cryptography; Springer: Berlin/Heidelberg, Germany, 1988; pp. 328–335. [Google Scholar]
- Camenisch, J.; Van Herreweghen, E. Design and implementation of the idemix anonymous credential system. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 21–30. [Google Scholar]
- Tsang, P.P.; Smith, S.W. PPAA: Peer-to-peer anonymous authentication. In International Conference on Applied Cryptography and Network Security; Springer: Berlin/Heidelberg, Germany, 2008; pp. 55–74. [Google Scholar]
- Dingledine, R.; Freedman, M.J.; Molnar, D. The free haven project: Distributed anonymous storage service. In Designing Privacy Enhancing Technologies; Springer: Berlin/Heidelberg, Germany, 2001; pp. 67–95. [Google Scholar]
- Durahim, A.O.; Savaş, E. A-MAKE: An efficient, anonymous and accountable authentication framework for WMNs. In Proceedings of the 2010 Fifth International Conference on Internet Monitoring and Protection, Barcelona, Spain, 9–15 May 2010; pp. 54–59. [Google Scholar]
- Backes, M.; Clark, J.; Kate, A.; Simeonovski, M.; Druschel, P. BackRef: Accountability in anonymous communication networks. In International Conference on Applied Cryptography and Network Security; Springer: Berlin/Heidelberg, Germany, 2014; pp. 380–400. [Google Scholar]
- Diaz, C.; Preneel, B. Accountable anonymous communication. In Security, Privacy, and Trust in Modern Data Management; Springer: Berlin/Heidelberg, Germany, 2007; pp. 239–253. [Google Scholar]
- Niu, Y.; Wei, L.; Zhang, C.; Liu, J.; Fang, Y. An anonymous and accountable authentication scheme for Wi-Fi hotspot access with the Bitcoin blockchain. In Proceedings of the 2017 IEEE/CIC International Conference on Communications in China (ICCC), Qingdao, China, 22–24 October 2017; pp. 1–6. [Google Scholar]
- Tsang, P.P.; Au, M.H.; Kapadia, A.; Smith, S.W. PEREA: Towards practical TTP-free revocation in anonymous authentication. In Proceedings of the 15th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008; pp. 333–344. [Google Scholar]
- Maria, A.; Rajasekaran, A.S.; Al-Turjman, F.; Altrjman, C.; Mostarda, L. Baiv: An efficient blockchain-based anonymous authentication and Integrity Preservation Scheme for secure communication in VANETs. Electronics 2022, 11, 488. [Google Scholar] [CrossRef]
- Black, E.W.; Mezzina, K.; Thompson, L.A. Anonymous social media–Understanding the content and context of Yik Yak. Comput. Hum. Behav. 2016, 57, 17–22. [Google Scholar] [CrossRef]
- Chatzistefanou, V.; Limniotis, K. On the (non-) anonymity of anonymous social networks. In International Conference on e-Democracy; Springer: Berlin/Heidelberg, Germany, 2017; pp. 153–168. [Google Scholar]
- Bernabe, J.B.; Canovas, J.L.; Hernandez-Ramos, J.L.; Moreno, R.T.; Skarmeta, A. Privacy-preserving solutions for blockchain: Review and challenges. IEEE Access 2019, 7, 164908–164940. [Google Scholar] [CrossRef]
- Treiblmaier, H. What Is Coming across the Horizon and How Can We Handle It? Bitcoin Scenarios as a Starting Point for Rigorous and Relevant Research. Future Internet 2022, 14, 162. [Google Scholar] [CrossRef]
- Möser, M.; Soska, K.; Heilman, E.; Lee, K.; Heffan, H.; Srivastava, S.; Hogan, K.; Hennessey, J.; Miller, A.; Narayanan, A.; et al. An empirical analysis of traceability in the monero blockchain. arXiv 2017, arXiv:1704.04299. [Google Scholar] [CrossRef]
- Hopwood, D.; Bowe, S.; Hornby, T.; Wilcox, N. Zcash Protocol Specification; GitHub: San Francisco, CA, USA, 2016; p. 1. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Bertoni, G.; Daemen, J.; Peeters, M.; Assche, G.V. Keccak. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2013; pp. 313–314. [Google Scholar]
- Pierro, G.A.; Tonelli, R.; Marchesi, M. An organized repository of ethereum smart contracts’ source codes and metrics. Future Internet 2020, 12, 197. [Google Scholar] [CrossRef]
- European Union. Regulation EU No 910/2014 of the European Parliament and of the Council. 23 July 2014. Available online: http://eur-lex.europa.eu/legal-content/EN/TXT\/HTML/?uri=CELEX%3A32014R0910&from=EN (accessed on 18 August 2022).
- Boehm, O.; Caumanns, J.; Franke, M.; Pfaff, O. Federated authentication and authorization: A case study. In Proceedings of the 2008 12th International IEEE Enterprise Distributed Object Computing Conference, Munich, Germany, 15–19 September 2008; pp. 356–362. [Google Scholar]
- Dingledine, R.; Mathewson, N.; Syverson, P. Tor: The Second-Generation Onion Router; Technical Report; Naval Research Laboratory: Washington, DC, USA, 2004. [Google Scholar]
- Rossberg, M.; Schaefer, G. A survey on automatic configuration of virtual private networks. Comput. Netw. 2011, 55, 1684–1699. [Google Scholar] [CrossRef]
- Roughley, I. Starting Struts 2. 2007. Available online: https://www.infoq.com/minibooks/starting-struts2/ (accessed on 18 August 2022).
- Kurniawan, B. Java for the Web with Servlets, JSP, and EJB; Sams: Carmel, IN, USA, 2002. [Google Scholar]
- Garrett, J.J. Ajax: A New Approach to Web Applications. 2005. Available online: https://immagic.com/eLibrary/ARCHIVES/GENERAL/ADTVPATH/A050218G.pdf (accessed on 18 August 2022).
- Infura The World’s Most Powerful Blockchain Development Suite. Available online: https://infura.io/ (accessed on 18 August 2022).
- MetaMask. A Crypto Wallet & Gateway to Blockchain Apps. Available online: https://metamask.io/ (accessed on 18 August 2022).
- Ropsten Testnet Explorer. 2006. Available online: https://ropsten.etherscan.io (accessed on 18 August 2022).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).