Considering the wide spread adoption of drones for smart cities, to undertake operations and render timely services, associated cyber threats need to be highlighted. Once an intruder is successful in gaining access to a UAV, it can carry out other attacks such as data theft (of sensitive video and image recordings from drone), data corruption, Denial of Service (DoS) or signal jamming, with a motive to sabotage a UAV in flight or to modify its flight path and fly it to an unwarranted waypoint. A compromised drone can be forced to crash through GPS spoofing techniques or by deliberately powering-off the motors in an attempt to rapidly drop its altitude, with an intent to incapacitate (or completely damage) the drone.
Detecting anomalies in a drone through the analysis of its on-device data is, therefore, imperative to foster a secure drone flight and to prevent a cyber attack from occurring. To our knowledge, there does not exist a robust and labeled flight dataset for UAVs to introduce an anomaly detection exercise, and therefore, we proposed a methodology wherein abnormal (outlier) events are found through analysis of flight logs of a DJI Phantom drone are reverse engineered to construe attacks.
Several references discuss the presence of anomalies in drone data. We examine references [
19,
20,
21] to interpret the possibility of anomalous flight patterns in drones. In [
21], motor temperature monitoring is undertaken to identify beyond-normal patterns. In [
19], drone in-flight faults that could cause a crash have been highlighted. To detect such faults, motor speeds and drone altitudes are examined to identify potentially anomalous events in drone logs. Similarly, drone log analysis techniques described in [
22] illustrate the use of drone flight logs for detecting a drone crash. The proposed scheme adopts the analysis of data obtained from the accelerometer, drone motor and altitude, to detect a crash. Based on this, it can be concluded that flight logs are an important source of information, which comprise both normal and anomalous drone flight operation data.
As part of our proposed attack model, we first identify the potentially anomalous flight operations using exploratory data analysis and then identify potential scenarios that might closely match cyber attacks.
3.1. DJI Phantom 4 Data
The DJI Phantom 4 drone dataset was acquired from VTO Labs [
23], comprising DAT files of flight logs, obtained from various flights undertaken by a single drone. The dataset includes 40 flight logs. However, only 18 logs could be adopted for our experiments due to the presence of inconsistencies and errors such as missing parameter values and lack of GPS data or the occurrence of truncated files, which were consequently discarded. These flight logs comprised information recorded by the main components of the UAV, including the flight controller, gyro stabilizer, on-board flight computer communication system, power supply, GPS modules and the likes [
24]. The DAT files were processed and converted into CSV files using the CSVView and DatCon tools as also adopted in previous studies [
25]. The sampling rate chosen in the DatCon tool to extract the CSV formatted file, was set at 10 Hz.
CSV files thus obtained comprised 289 fields (column labels). Categories of data available in these flight logs are listed as follows:
State signals are categorical fields indicating the state of the drone whilst in flight. In contrast, the time-series signals are numerical fields with some observed value of various fields related to its flight. In this work, we only study the time-series fields to avoid unpredictable behavior of machine learning algorithms, given the variability of time series data (i.e., entropy). Specifically, the flight logs from the following file path within the DJI Phantom memory system were considered: “Drone_Forensics > DJI_phantom_4 > df005_DJI_Phantom_4 > 2018_June > flight_logs > flight_logs.zip”. To perform exploratory analysis and classification tasks, only data files that contained the full set of 288 features were considered. Some of the important features related to flight logs are listed in
Table 2.
3.2. Exploratory Analysis—Discerning Malicious Outliers
In order to conduct an exploratory analysis, we first adopted the commonly used clustering algorithm, namely, unsupervised Gaussian mixture models (GMM) for cluster and outlier analysis as shown in
Figure 2. This procedure was undertaken to identify potential anomalous points in the dataset. For the exploratory analysis, we only considered a subset of flight logs. Instead of using Euclidean distances, GMM uses probability distribution of various points (of the feature-value tuples of the dataset), to identify various data distributions that exist in the dataset. The advantage of using GMM is that it considers data points that belong to the same cluster and which follow a Gaussian distribution. Hence, each distribution is defined as a unique cluster.
Figure 3 presents the various clusters formed in the partial dataset, which also contains outlier samples. Further analysis of the flight path data for this data subset yields the finding that there are anomalous flight events in flight log 19, as shown in
Figure 3.
Further analysis of flight19 logs using the CSVView tool indicates more anomalous events during the flight. The data revealed that an anomalous event occurred in the initial stages of the flight operations, which comprised a sharp increase in the pitch angle and a sharp descent of the drone along with a low/zero thrust to the drone, as shown in
Figure 4. The sudden drop in the flight altitude can also be attributed to a cyber attack wherein an intruder deliberately hijacks the drone and suddenly impedes throttle to cause the drone to descend steeply and crash and get destroyed.
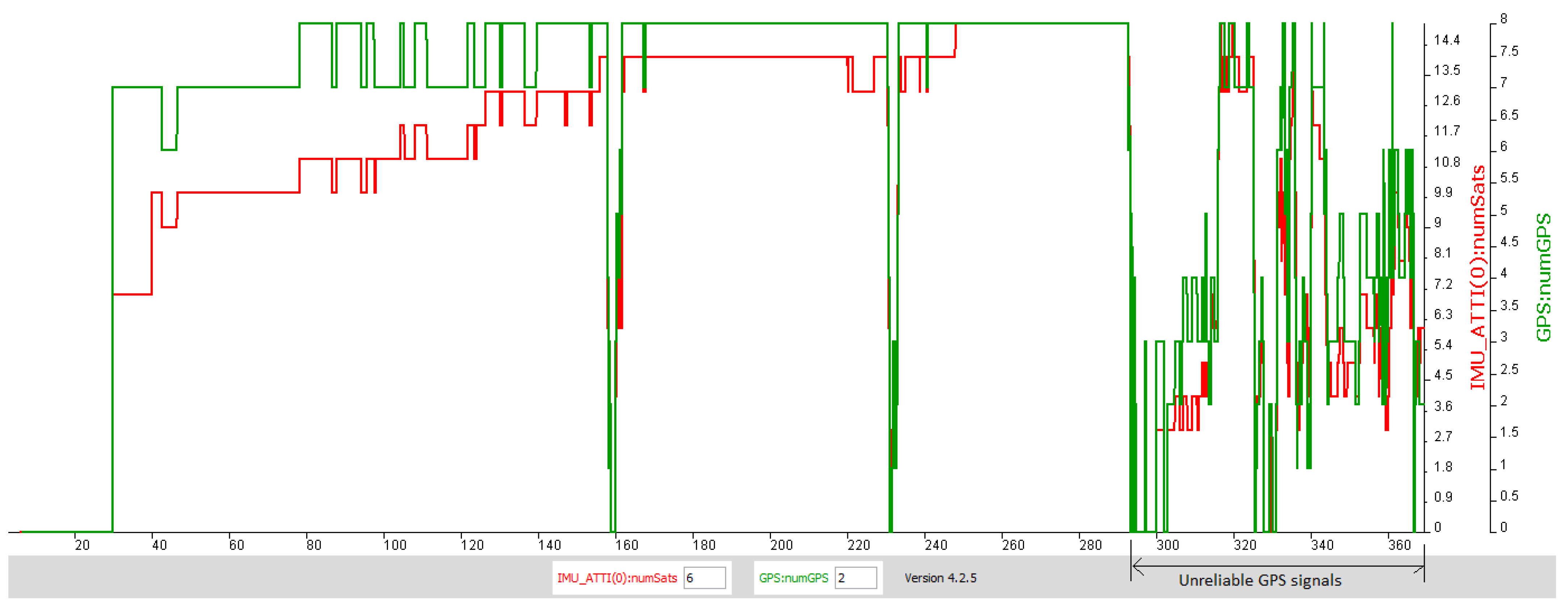
The GPS jamming attack comprises a disruption of GPS signals through jamming of signals (radio) that are transmitted and received between a drone and a ground controller unit.
Figure 5 shows the time window of the flight operation wherein the GPS signals become unreliable. A GPS jamming attack results in a similar situation wherein, GPS signals can be disrupted to cause the drone to loose the ability to identify its flying coordinates, and possibly trigger a Return To Home (RTH) routine [
14].
A DoS event is the occurrence of a sudden loss in the power supply to the drone motors/rotors (hijacking). The thrust to the drone is provided by its four motors (two in front and two in the back), in a typical quadcoptor model. Through switching of these motors, the drones are maneuvered and its height is controlled.
In regard to hijacking attacks, a sudden drop in motor speeds can occur when an intruder successfully gains access to the drone’s ground controller or is successful in hijacking a remote asset such as an intermediary device that the ground controller is communicating with, and can thus deliberately power off the motors. This potential anomalous event is illustrated in
Figure 6.
A variant denial of service (DoS) attack scenario causes the data communication flow between a ground-based radio controller and resulting in significant communication loss. In-flight parameters, namely, ’osd_data:connectedToRC’ and ’RC_Info:frame_lost:D’ capture the status of the connection between the radio controller and the drone. During in-flight drone operations, situations may arise wherein communication between a radio controller and the drone is lost under certain natural weather phenomena. We argue that in the presence of a DoS attack, a similar situation may arise due to the communication between the drone and controller being lost, not as a consequence of a natural phenomena but rather through a malicious event of sabotage perpetrated by the adversary. Hence, we identify the instances of the dataset wherein communication is disrupted, to mark a potential anomaly representative of a DoS attack. It may be noted that a DoS attack even for legacy systems is hard to distinguish from flash crowds comprising legitimate network traffic, though their impact on the victim device (drones in our case) is the same [
26].
For routine operations, DJI drones communicate with the radio controller using some form of wireless communication technology (i.e., ocusync or other versions also use Wi-Fi). If the communication channel is under attack the drone can lose communication with the radio controller. The logs record the communication health with the radio controller using the rc-info-frameloss variable. We ignore arbitrary frame loss for the study, however, we label a continuous frame loss as being part of adversarial dirsuptions, that can refer to a DoS attack.
In addition, we also replicate the frame loss events obtained from flight logs and increase the number of such instances wherein a frame loss has occurred, to add a range of random anomalous (DoS) events to the log file (and to obtain a good balance between normal and anomalous data samples). Similarly, instances where the connection between the radio control (RC) and the drone is lost (indicated by frame_loss) are also marked as a DoS attack, as shown in
Figure 7. Variant versions of DoS attacks (including stealthy attacks) were not considered for our experimental analysis.
As shown in
Figure 8, the parameter rc_connect changes the state to zero, indicating a DoS attack. In
Figure 7, blue lines indicate frame-loss recorded in the flight logs and orange lines indicate the label given to these instances.