Towards Strengthening the Resilience of IoV Networks—A Trust Management Perspective
Abstract
:1. Introduction
- Driving Safety—Driving safety is the most important task of the IoV and is of great significance for protecting people. It mainly includes collision warning, emergency vehicle warning, dangerous road conditions warning, and automatic driving;
- Traffic Efficiency—Traffic efficiency is mainly aimed at alleviating urban traffic congestion and providing green, efficient, and comfortable travel services for people. It mainly includes traffic light control, adaptive cruise, and vehicle choreography;
- Information Services—Information services mainly provide infotainment services, high-precision map download, navigation, and other value-added services. These include multimedia entertainment, high-precision map download, and remote vehicle diagnosis. Therefore, VANETs have huge social and commercial value.
1.1. Contributions of the Paper
- To clarify the development process from VANET to IoV firstly. Owing to certain limitations of VANET, IoV has developed rapidly due to its special advantages.
- This paper conducts comprehensive research on the trust management in the Internet of Vehicles, including the trust model, trust parameters, simulation methods and model evaluation methods. In addition, various security attacks are classified and explained.
- Finally, the future research direction of the IoV trust management mechanism is put forward, which lays the foundation for follow-up research.
1.2. Outline of the Paper
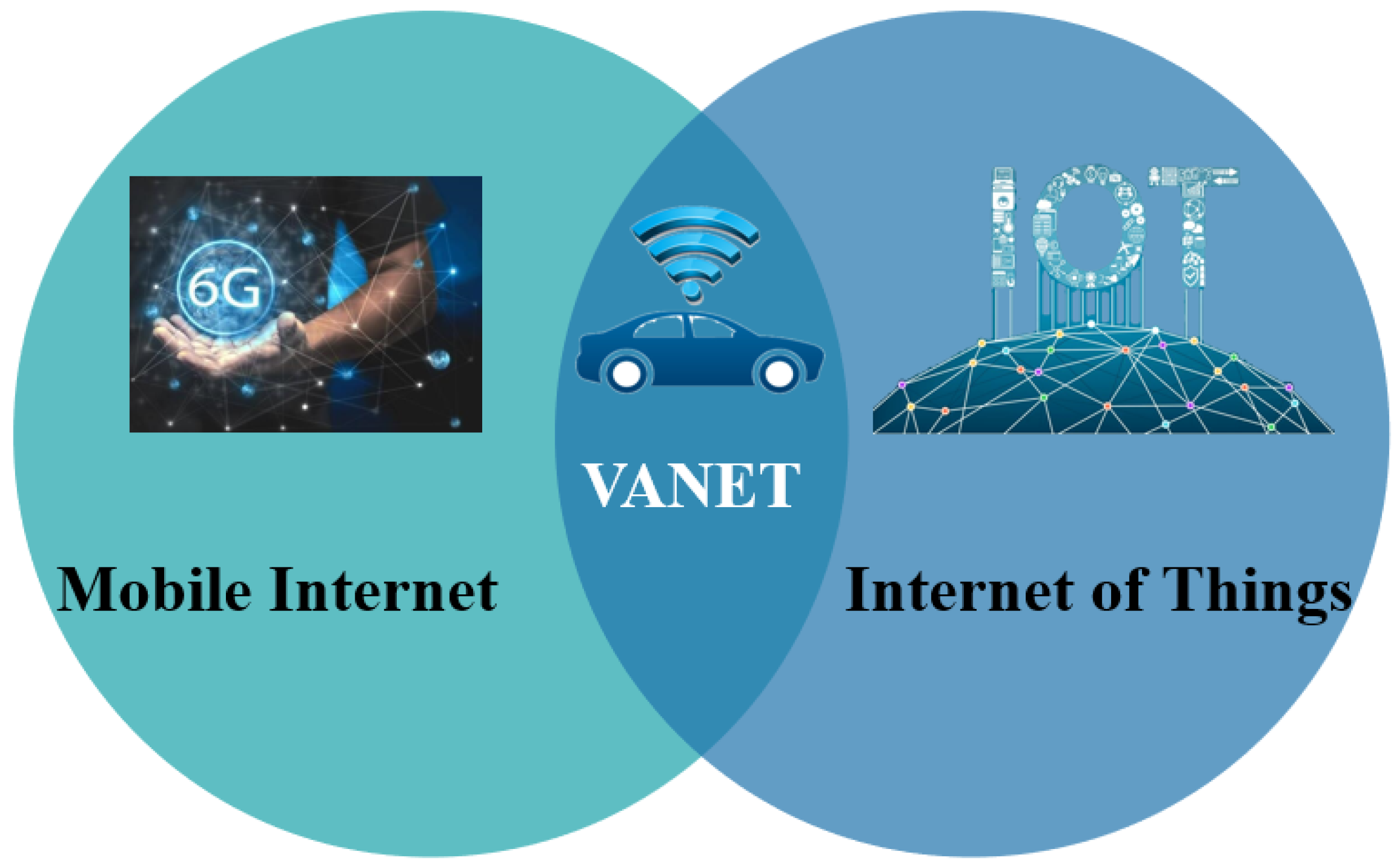
2. From Vehicular Ad Hoc Networks to Internet of Vehicles
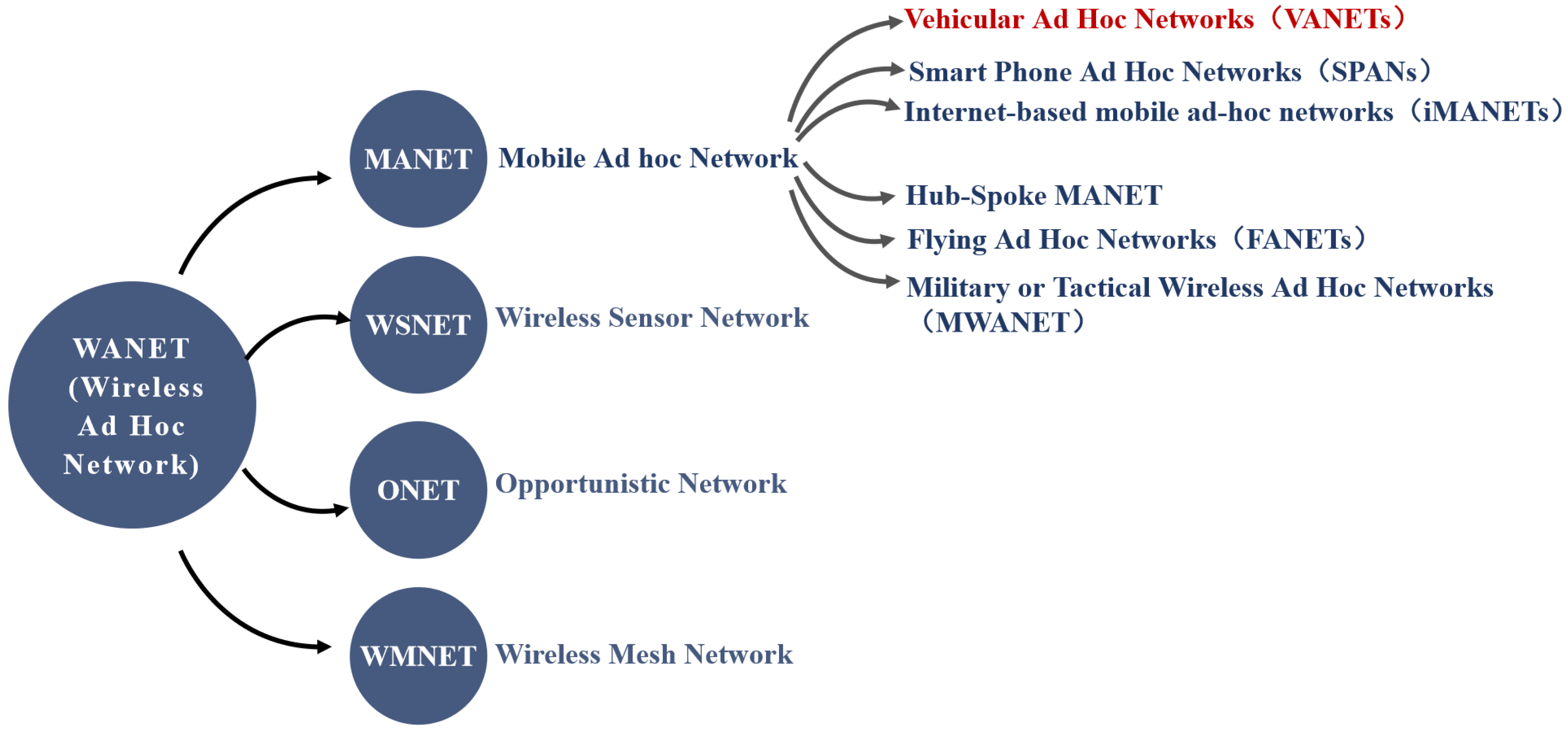
2.1. Vehicle Ad Hoc Networks (VANETS)
- Vehicle Ad Hoc Networks (VANETs)—VANETs realize the coordination of vehicles, people, and roads through V2X, which is an artificial intelligence technology that can help vehicles take actions in an intelligent way when they encounter danger. Its appearance has greatly improved traffic safety and traffic efficiency;
- Smart Phone Ad Hoc Networks (SPANs)—SPANs create peer-to-peer networks using existing hardware devices, independent of cellular operator networks, wireless access points or traditional network infrastructure;
- Internet-based Mobile Ad Hoc Networks (IMANETs)—IMANETs support internet protocols such as TCP/UDP and IP;
- Hub-Spoke MANET—A plurality of sub-mobile ad hoc networks can be connected to the traditional central radiating VPN to create geographically distributed mobile ad hoc networks;
- Military or Tactical Wireless Ad Hoc (MWANET)—MWANET is a special self-organizing network for military departments, with special emphasis on data security, real-time requirements, data rate, radio range and integration, and fast routes in terms of mobility requirements;
- Flying Ad Hoc Networks (FANETs)—FANETs consist of drones, which can achieve great mobility and provide connectivity with remote areas.
- The vehicle can achieve sufficient energy support, and the carrying space of the vehicle can also ensure the good performance of its wireless communication equipment. At the same time, its storage and computing capabilities are also very powerful. In the same way, the traffic facilities on both sides of the road also have sufficient energy supply, and the computing storage capacity and wireless communication capacity are guaranteed;
- The popularity of GPS and GIS (Geographic Information System) makes VANET rich in external auxiliary information, including not only its own location information but also the geographical information of its area, such as road direction, traffic light distribution, etc.;
- As compared with other MANETs, the nodes of VANET move more regularly. The network topology is relatively stable when vehicles travel in the same direction, but when vehicles run in the opposite direction, the network topology will change very quickly, and the life of the whole link will be shortened. It is possible to predict the link state by combining the driving direction, speed and road information of the vehicle.
- The stability of wireless channels is poor, which is influenced by many factors, including the current road condition information, the relative speed and direction between vehicles, the types of vehicles, the buildings along the road, etc.;
- Rapid network topology change and short link life;
- Limited network capacity. The distribution of nodes in VANET is restricted by roads, and it presents a “tubular” shape. According to the calculation method of the network capacity of a random plane, it can be found that its network capacity is more limited than that of the general wireless mobile network;
- As the traffic density changes, the network load will also change greatly, so the nodes must have strong adaptability to this rapid change;
- VANET and driving safety are closely related, while OBU’s operating environment is relatively harsh, which requires more stringent requirements for the reliability and safety of these devices.
2.2. Internet of Vehicle (IoV)
2.2.1. The Structure of IoV
2.2.2. Key Technologies of IoV
- Sensor technology and sensor information integration—Sensor technology is mainly used to sense vehicle and road information, and it is mainly integrated in the OBU of vehicles. The sensor network of vehicles can be divided into in-vehicle sensor networks and out-of-vehicle sensor networks. The sensor network in vehicles is mainly used to provide information about the vehicle’s status. This condition information is needed for remote diagnosis, for example, to analyze and judge the current state of the vehicle. Out-of-vehicle sensor networks are mainly used to sense the external environment of vehicles, such as cameras and anti-collision sensors. Such information can be used to assist driving, and it can also be used to improve driving safety. The road sensor network consists of sensors laid on roads and roadsides. Such sensors are used to sense road condition information and transmit it to vehicles, such as vehicle speed and direction, traffic density, intersection congestion, etc., so that the vehicle-mounted system can obtain road and traffic environment information.
- An intelligent and open vehicle terminal system platform—Based on a terminal system platform that is not sufficiently intelligent and open, it is difficult to build a network ecosystem. In this respect, we can see the importance of this point in the field of smartphones. At present, Google Android will become the mainstream operating system for IoV terminal systems. Being born for network applications, it is designed for touch operation, with rich applications, personalized customization, good user experience, and a huge increase in the number of applications, forming a mature network ecosystem.
- Speech recognition technology—This technology is very mature, which allows drivers to send commands to IoV through their mouths and receive services provided by IoV through their ears. This is most suitable for application in the fast-moving space of vehicles. The “cloud recognition” technology based on server-side technology must be used to solve the storage and computing capacity of vehicles, so as to adapt to the non-fixed command mode of speech recognition technology.
- Server-side computing and service integration technology—IoV uses cloud computing to plan the driving path of a large number of vehicles, analyze real-time road conditions, diagnose vehicles, and dispatch traffic congestion. IoV implements service innovation and provides value-added services through service integration.
- Communication and its application technology—IoV mainly depends on two communication technologies: short-distance wireless communication and long-distance mobile communication technologies. In the former, RFID sensors and WIFI-like communication technologies are predominant, while in the latter, GPRS, LTE, 5G and other mobile communication technologies are the main focus. These communication technologies are more concerned with applications, such as automatic toll collection, data packet transmission, video surveillance and so on.
- Internet technology—IoV can integrate the existing technologies and applications of the Internet and mobile Internet, but it is necessary to develop the characteristic Internet applications of IoV. Only in this way can more commercial benefits be brought to IoV.
3. Trust Management in the Internet of Vehicles
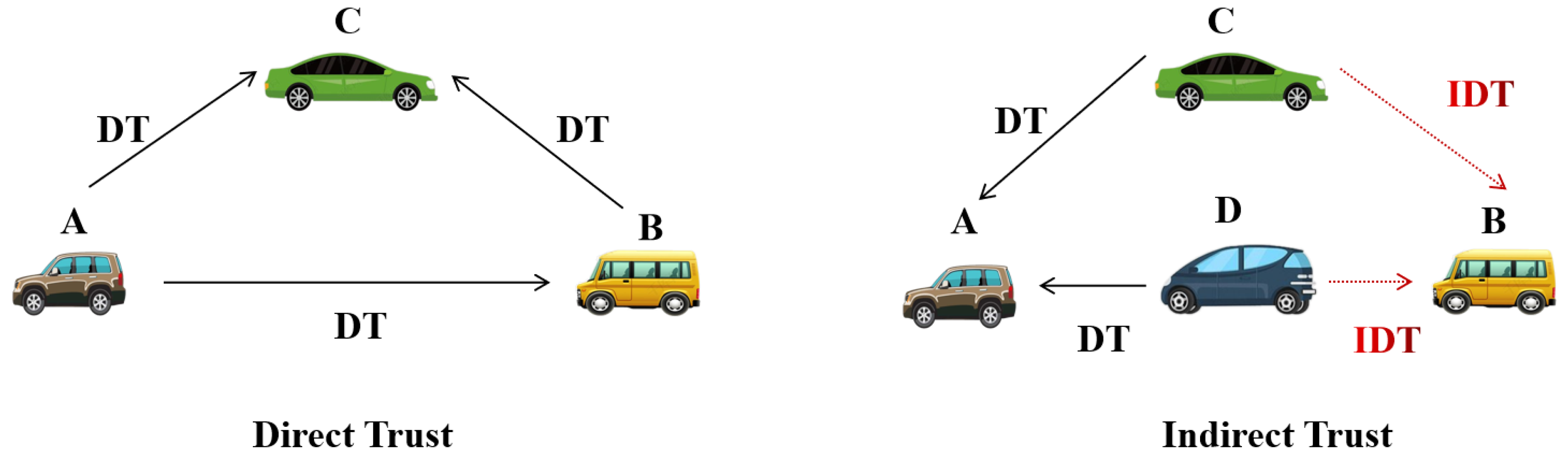
3.1. Classification of Trust
3.1.1. Direct Trust (DT)
3.1.2. Indirect Trust (IDT)
3.2. Trust Models
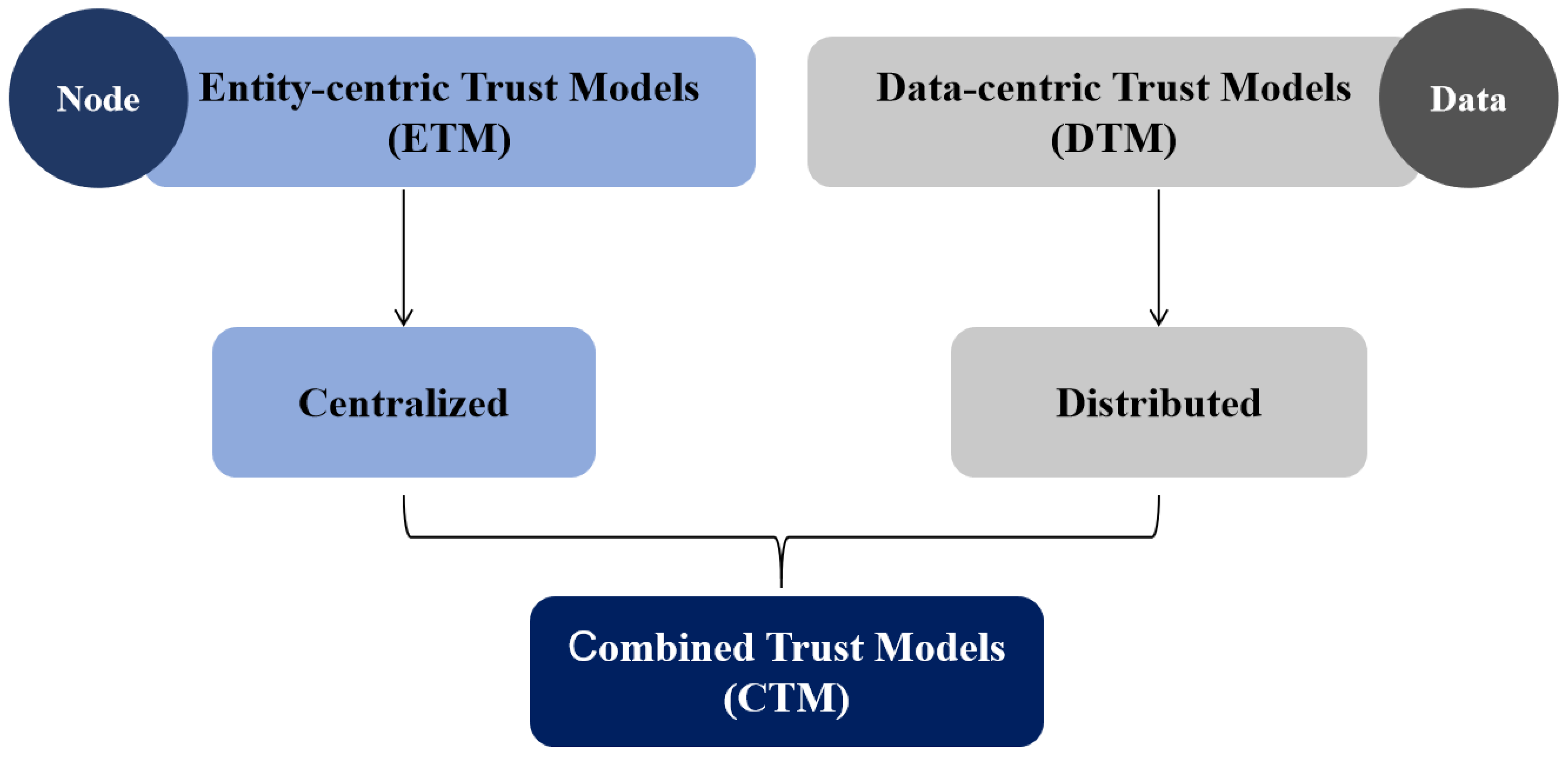
3.2.1. Classification of Trust Models
- Entity-based Trust Model (ETM)The purpose of ETM is to evaluate the credibility of vehicle nodes. Usually, a trust evaluation system can be built by using direct or indirect trust between vehicles, and the trust value of each node can be calculated so as to detect untrustworthy vehicles. Hu [30] et al. put forward a trust model based on the feedback data of users’ vehicles and evaluated the credibility of the first vehicle in the vehicle arrangement scenario, so as to help the user’s vehicle to choose a reliable vehicle to follow. In [12], the social attributes of nodes are used, and three social trust relationships, direct neighbor trust, indirect neighbor trust and friend trust, are considered. The trust degree of nodes is calculated by weighted average.In [32], the main difficulty of an entity-based trust model maintaining the trust relationship between vehicles lies in how to collect enough information to evaluate the trust degree of nodes, especially when vehicles have just joined VANET. Additionally, when there is not enough interactive information, or there are few connections between vehicles and short communication links, e.g., in suburbs with sparse vehicles, these factors can make it difficult to evaluate trust effectively.
- Data-based Trust Model (DTM)DTM mainly evaluates whether the received data are reliable. The model needs to collect messages from various information sources, such as neighbor nodes and RSU, and filter out untrustworthy data to accurately verify the reliability of the received data. Tahani [11] established a distributed trust mechanism based on a direct experience survey between neighboring vehicles according to VANET’s characteristics. Every vehicle first detects whether the received data are reliable, and then, it distributes the trust value to all of their neighbors. Rawat [24] proposed using the received signal strength (RSS) and the geographic location (GPS) of the vehicle to evaluate the trust level of the received message, combining the Bayesian estimation evaluation algorithm with the determined distance calculation method to provide better evaluation results, thus helping to identify malicious message data.The main disadvantage of DTM is that the trust relationship between vehicles can never be formed, and only a short-term trust of the received data can be established. Because data trust is based on events, it is necessary to build the trust relationship for each event again and again, and the previous trust data have not been used. At the same time, when the number of received messages is insufficient, it is difficult to judge the accuracy of the messages.
- Combined Trust Model (CTM)CTM is equivalent to the combination of the above two trust models. This model can not only evaluate the reliability of vehicles but also calculate the reliability of data. Generally, the two trust models are interrelated, that is, the trust value of a node affects the credibility of data to a certain extent, and the trust value of data in turn reflects the credibility of a node. An anti-attack trust management scheme (ART) was proposed by Li [11]: in this system, malicious attacks can be detected and responded, and the credibility of data and mobile nodes in VANET can be evaluated. Data trust evaluation is based on feelings and the data collected by multiple vehicles in two dimensions of node trust evaluation, namely function trust and recommendation trust. Mehmood [33] put forward a cluster-based hybrid VANETs trust management scheme, which can not only classify the information in the cluster but also identify malicious vehicles in real time.
3.2.2. Trust Parameters
- Co-Location Relationship (CLR)—The concept of CLR is that when the trustee and the trustor are very close to each other, the trustor can easily obtain the information needed from the selected trustee, because from the perspective of position, the trustee is more reliable than other objects that are far away.The decision boundary is set according to the distance from the trustor in order to avoid the vehicle leaving the predetermined physical location, as demonstrated in [37], which gathered many parameters such as CWR, RS, CoI, MC, etc., and used the machine learning algorithm to find an optimal boundary to distinguish between trusted and untrusted nodes.
- Co-work Relationship (CWR)—CWR describes the interaction between nodes that are service-dependent rather than physically adjacent. It is the association that one node possesses with another when providing a service, and it can be calculated by multicast interaction. This association represents the relative amount of shared multicast messages in relation to the total messages sent [37].
- Rewards—This parameter is used to evaluate the historical rewards between the trustee and the trustor. The more reasonable the interactions, the higher the reward value. This parameter can track the misbehavior of the trustee and view their history, so that the trustor can determine whether to have further communication with the trustee [37]. In [41,49], using joint deep learning to evaluate the degree of trust between users and task assignors, the author designed a layered incentive mechanism to realize reasonable and fair rewards and punishments, which improved the accuracy of trust evaluation.
- Community of Interest (CoI)—CoI represents the social status of the trustee and describes whether there is a close relationship between the trustor and the trustee in the social network. This parameter indicates the degree of mutual interest between the trustee and trustor. In general, the higher the CoI between the two nodes, the better the interaction between them and the more trustworthy they are deemed to be [37]. In [48], the authors calculated the community-based trust characteristics of the trustee relative to the trustor at time t.
- Mutuality and Centrality (MC)—MC represents the position of the trustee relative to the trustor in the network. The larger the MC is, the more similar the social relationship between them, the more interactions between them, and the higher the degree of trust [37].
- Confidence—Confidence indicates the accuracy of the probability estimate. It can save network resources when the credibility of direct trust is greater than the set threshold, and a node is considered as a trusted node without calculating the recommended credibility [29].
- Packet Delivery Ratio (PDR)—PDR refers to the contact degree between the trustee and the principal, which is generally defined as the packet forwarding rate between nodes. PDR is generally considered a very important parameter in establishing a trust model, calculating the trust value and identifying malicious vehicles [26,50,51].
- Similarity—This parameter is used to measure the similarity in content and service between any two vehicles. Generally expressed as the Euclidean distance, the authors of [31] used the concept of similarity to calculate the similarity between the vehicle information in the infrastructure trust table and the information sent to the vehicle.
- Familiarity—Familiarity indicates the familiarity between the trustor and the trustee, which is a parameter with a high utilization rate. This parameter is used to measure the interaction frequency between the trustee and the trustor. The higher the interaction frequency, the more information can be obtained from the other party, and the more favorable it is to gain higher trust [25].
- End-to-End Delay (E2ED)—This parameter is related to the QoS of trust management, which describes the total delay caused by sharing data packets generated by legitimate vehicles with neighboring vehicles. Of course, the smaller the value of E2ED, the more reasonably the trust mechanism is designed [41].
3.2.3. Evaluation of Trust Models
3.2.4. Trust Model Simulation Method
3.3. Categories of Attacks
- Bad-mouthing attack and Good-mouthing attackAttackers attempt to send fake trust messages to frame legitimate nodes so that they are not detected. Hence, the purpose of this attack is to undermine the proper trust assessment and make malicious attacks hard to identify. In [41], the authors proposed a trust mechanism based on evidence combination, which can resist bad-mouthing attacks. The precision and recall were still higher than 80% under bad-mouthing attack. Compared with bad-mouthing attacks, good-mouthing attacks send positive recommendations about malicious nodes.
- Selective Misbehavior AttackDuring a selective misbehavior attack, malicious nodes only provide false messages to some nodes, which is normal for other nodes, which will lead to inconsistent trust among different nodes that is difficult to detect. During a time-dependent attack, the behavior of nodes changes with time and is not fixed. In [41], three types of attacks were detected: bad-mouthing attacks, selective misbehavior attacks, and time-dependent attacks.
- Time-varying AttackDuring a time-varying attack, the behavior of nodes changes with time and is not fixed. Initially, an attacker would establish itself as a legitimate node for a short period of time, gain the trust of other vehicles, and then launch an attack, sharing malicious messages and ratings with neighboring vehicles. In [47], the authors detected this kind of attack.
- Zig-Zag Attack (On-and-off Attack)During a zig-zag attack, also known as the “on-and-off” attack, malicious nodes attack randomly. At first, these nodes are normal, and when they gain enough trust values, they launch malicious attacks, which are difficult to detect. In [52], the authors proposed an effective attack detection model, which mainly detected man-in-the-middle (MITM) attacks and zig-zag attacks as well as a combination of the two attacks.
- Self-promoting AttackUnlike other types of malicious attacks, selfish attacks gain their own benefits from attacks, which indicates that there is little cooperation between vehicles. For example, in [55], the authors proposed an incentive technology to prevent such attacks.
- Whitewashing Attack/Newcomer AttackDuring a whitewashing attack, a node has a bad history before entering the system, but after re-entering the system, the node adopts a new identity in order to gain more trust and erase its dark history. In order to resist such attacks, in [31], new nodes were given a relatively low trust value, and an adaptive attenuation factor was also introduced so that the trust value of newcomers could reach a relatively high value over a long period of time.
4. Open Research Directions
4.1. Threshold Setting
4.2. Data Collection
4.3. Standards Introduction
4.4. Trust Computing Validation
4.5. Community Formation
4.6. Integration of Blockchain and IoV
5. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Storck, C.R.; Duarte-Figueiredo, F. A 5G V2X Ecosystem Providing Internet of Vehicles. Sensors 2019, 19, 550. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Osibo, B.K.; Zhang, C.; Xia, C.; Zhao, G.; Jin, Z. Security and Privacy in 5G Internet of Vehicles (IoV) Environment. J. Internet Things 2021, 3, 77. [Google Scholar] [CrossRef]
- Wang, S.; Sun, S.; Wang, X.; Ning, Z.; Rodrigues, J.J.P.C. Secure Crowdsensing in 5G Internet of Vehicles: When Deep Reinforcement Learning Meets Blockchain. IEEE Consum. Electron. Mag. 2021, 10, 72–81. [Google Scholar] [CrossRef]
- Kamvar, S.D.; Schlosser, M.T.; Garcia-Molina, H. The eigentrust algorithm for reputation management in p2p networks. In Proceedings of the 12th Internatonal Conference on World Wide Web, Budapest, Hungary, 20–24 May 2003; Assciation for Computing Machinery: New York, NY, USA, 2003. [Google Scholar]
- Blaze, M.; Feigenbaum, J.; Lacy, J. Decentralized trust management. In Proceedings of the 1996 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 6–8 May 1996; pp. 164–173. [Google Scholar]
- Cauteruccio, F.; Cinelli, L.; Fortino, G.; Savaglio, C.; Terracina, G.; Ursino, D.; Virgili, L. An approach to compute the scope of a social object in a Multi-IoT scenario. Pervasive Mob. Comput. 2020, 67, 101223. [Google Scholar] [CrossRef]
- Zhou, R.H.; Wang, K. Powertrust: A robust and scalable reputation system for trusted peer-to-peer computing. IEEE Trans. Parallel Distrubuted Syst. 2007, 18, 460–473. [Google Scholar] [CrossRef]
- Xiong, L.; Liu, L. Peertrust:Supporting reputation-based trust for peer-peer electronic communitities. IEEE Trans. Knowl. Data Eng. 2004, 16, 843–857. [Google Scholar] [CrossRef]
- Srinvtsa, M.; Xiong, L.; Liu, L. TrustGuard:countering vulnerabilities in reputation mangement for decentralized overlay networks. In Proceedings of the 14th International Conference on World Wide Web, Chiba, Japan, 10–14 May 2005; Association for Computing Machinery: New York, NY, USA, 2005. [Google Scholar]
- Tan, S.; Li, X.; Dong, Q. A trust management system for securing data plane of ad-hoc networks. IEEE Trans. Veh. Technol. 2015, 65, 7579–7592. [Google Scholar] [CrossRef]
- Li, W.; Song, H. ART: An attack-resistant trust management scheme for securing vehicular ad hoc networks. IEEE Trans. Parallel Distrubuted Syst. 2015, 17, 960–969. [Google Scholar] [CrossRef]
- Hu, H.; Lu, R.; Zhang, Z.; Shao, J. REPLACE: A reliable trust-based platoon service recommendation scheme in VANET. IEEE Trans. Veh. Technol. 2016, 66, 1786–1797. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Abdullah, A.H.; Zareei, M.; Anisi, M.H.; Mohammad, H.; Vargas-Rosales, C.; Khan, M.K.; Goudarzi, S. A secure trust model based on fuzzy logic in vehicular ad hoc networks with fog computing. IEEE Accesss 2017, 5, 15619–15629. [Google Scholar] [CrossRef]
- Lin, B.; Chen, X.; Wang, L. A cloud-based trust evaluation scheme using a vehicular social Network enviroment. In Proceedings of the 2017 24th Asia-Pacific Software Engineering Conference (APSEC), Nanjing, China, 4–8 December 2017. [Google Scholar]
- Kerrache, C.A.; Lagraa, N.; Calafate, C.T.; Lakas, A. TFDD: A trust-based framework for reliable data delivery and DoS defense in VANETs. Veh. Commun. 2017, 9, 254–267. [Google Scholar] [CrossRef] [Green Version]
- Xiao, Y.; Liu, Y. Bayestrust and vehiclerank: Constructing an implicit web of trust in vanet. IEEE Trans. Veh. Technol. 2019, 68, 2850–2864. [Google Scholar] [CrossRef]
- Barka, E.; Kerrache, C.A.; Benkraouda, H.; Shuaib, K.; Ahmad, F.; Kurugollu, F. Towards a trusted unmanned aerial system using blockchain for the protection of critical infrastructure. Trans. Emerg. Telecommun. Technol. 2019, e3706. [Google Scholar] [CrossRef]
- Gambetta, D. Can we trust. In Trust: Making and Breaking Cooperative Relations; Blackwell Pub: Hoboken, NJ, USA, 2000; Volume 13, pp. 213–237. [Google Scholar]
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An integrative model of organizational trust. Acad. Manag. Rev. 1995, 20, 709–734. [Google Scholar] [CrossRef]
- Azzedin, F.; Maheswaran, M. Evolving and managing trust in grid computing systems. In Proceedings of the IEEE CCECE2002, Canadian Conference on Electrical and Computer Engineering, Conference Proceeding, Winnipeg, MB, Canada, 12–15 May 2002. [Google Scholar]
- Abdul, R.A.; Hailes, S. Supporting trust in virtual communities. In Proceedings of the 33rd annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000. [Google Scholar]
- Li, X.; Gui, X. Research on dynamic trust model in large-scale distributed environment. J. Softw. 2007, 2007, 1510–1521. [Google Scholar] [CrossRef]
- Grandison, T.W.A. Trust Management for Internet Applications; University of London: London, UK, 2003. [Google Scholar]
- Rawat, D.B.; Yan, G.; Bista, B.B.; Weigle, M.C. Trust On the Security of Wireless Vehicular Ad-hoc Networking. Ad Hoc Sens. Wirel. Networks 2015, 24, 283–305. [Google Scholar]
- Siddiqui, S.; Mahmood, A.; Zhang, W.; Sheng, Q. Machine learning based trust model for misbehaviour detection in internet-of-vehicles. Commun. Comput. Inf. Sci. 2019, 1142, 512–520. [Google Scholar] [CrossRef]
- Ahmad, F.; Kurugollu, F.; Adnane, A.; Hussain, R.; Hussain, F. MARINE: Man-in-the-middle Attack Resistant trust model IN connEcted vehicles. IEEE Internet Things 2021, 7, 3310–3322. [Google Scholar] [CrossRef] [Green Version]
- Siddiqui, S.A.; Mahmood, A.; Sheng, Q.Z.; Suzuki, H.; Ni, W. A Time-aware Trust Management Heuristic for the Internet of Vehicles. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 20–22 October 2021; pp. 1–8. [Google Scholar]
- Alnasser, A.; Sun, H.; Jiang, J. Recommendation-based Trust Model for Vehicle-to-Everything (V2X). IEEE Internet Things J. 2020, 7, 440–450. [Google Scholar] [CrossRef] [Green Version]
- Gao, H.H.; Liu, C.; Yin, Y.; Xu, Y.; Li, Y. A Hybrid Approach to Trust Node Assessment and Management for VANETs Cooperative Data Communication: Historical Interaction Perspective. IEEE Trans. Intell. Transp. Syst. 2021. [Google Scholar] [CrossRef]
- Chen, J.M.; Li, T.T.; Panneerselvam, J. TMEC: A Trust Management Based on Evidence Combination on Attack-Resistant and Collaborative Internet of Vehicles. IEEE Access 2019, 7, 148913–148922. [Google Scholar] [CrossRef]
- Mao, M.; Yi, P.; Hu, T.; Zhang, Z.; Lu, X.; Lei, J. Hierarchical Hybrid Trust Management Scheme in SDN-Enabled VANETs. Mob. Inf. Syst. 2021, 2021, 7611619. [Google Scholar] [CrossRef]
- Mahmood, A.; Sheng, Q.Z.; Siddiqui, S.A.; Sagar, S. When Trust Meets the Internet of Vehicles: Opportunities, Challenges, and Future Prospects. In Proceedings of the 2021 IEEE 7th International Conference on Collaboration and Internet Computing CIC, Atlanta, GA, USA, 13–15 December 2021. [Google Scholar]
- Mahmood, A.; Butler, B.; Zhang, W.E.; Sheng, Q.Z.; Siddiqui, S.A. A Hybrid Trust Management Heuristic for VANETs. In Proceedings of the PerVehicle’19—1st International Workshop on Pervasive Computing for Vehicular Systems, Kyoto, Japan, 11–15 March 2019. [Google Scholar]
- Liu, Z.; Ma, J.; Jiang, Z.; Zhu, H.; Miao, Y. LSOT: A Lightweight Self-Organized Trust Model in VANETs. Mob. Inf. Syst. 2016, 2016, 7628231. [Google Scholar] [CrossRef] [Green Version]
- Ahmad, F.; FVirginia, N.L.; Adnane, A. TEAM: A Trust Evaluation and Managemen Framework in Context-Enabled Vehicular Ad-Hoc Network. Digit. Object Identifier 2018, 28643–28660. [Google Scholar] [CrossRef]
- Jamal, R.; Flocchini, A.; Nayak, A. A Fog-based Reputation Evaluation Model for VANETs. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October 2021–2 November 2021. [Google Scholar]
- Jayasinghe, U.; Lee, G.M.; Um, T.W. Machine Learning Based Trust Computational Model for IoT Services. IEEE Trans. Sustain. Comput. 2019, 4, 39–52. [Google Scholar] [CrossRef]
- Jamal, R.; Flocchini, A.; Nayak, A. RTEAM: Risk-Based Trust Evaluation Advanced Model for VANETs. Digit. Object Identifier 2021, 4, 39–52. [Google Scholar]
- Sugumar, R.; Rengarajan, A.; Jayakumar, C. Trust based authentication technique for cluster based vehicular ad hoc networks (VANET). Wirel. Netw. 2018, 24, 373–382. [Google Scholar] [CrossRef]
- Siddiqui, S.A.; Mahmood, A.; Sheng, Q.Z.; Suzuki, H.; Ni, W. A Survey of Trust Management in the Internet of Vehicles. Electronics 2021, 10, 2223. [Google Scholar] [CrossRef]
- Wang, X.D.; Garg, S.; Lin, H.; Kaddoum, G.; Hu, J.; Hassan, M.M. Heterogeneous Blockchain and AI-Driven Hierarchical Trust Evaluation for 5G-Enabled Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2021. [Google Scholar] [CrossRef]
- Fabi, A.K.; Thampi, S.M. A psychology-inspired trust model for emergency message transmission on the Internet of Vehicles (IoV). Int. J. Comput. Appl. 2020, 44, 480–490. [Google Scholar] [CrossRef]
- Truong, N.B.; Um, T.; Zhou, B.; Lee, G.M. From Personal Experience to Global Reputation for Trust Evaluation in the Social Internet of Things. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Mahmood, A.; Zhang, W.E.; Sheng, Q.Z. Software-Defined Heterogeneous Vehicular Networking: The Architectural Design and Open Challenges. Future Internet 2019, 11, 70. [Google Scholar] [CrossRef] [Green Version]
- Oubabas, S.; Aoudjit, R.; Rodrigues, J.J.; Talbi, S. Secure and stable vehicular ad hoc network clustering algorithm based on hybrid mobility similarities and trust management scheme. Veh. Commun. 2018, 13, 128–138. [Google Scholar] [CrossRef]
- Abdo, I.; Shaikh, R.A.; Hassan, S.R. A hybrid dual-mode trust management scheme for vehicular networks. Int. J. Distrib. Sens. Networks 2020, 16, 1550147720939372. [Google Scholar]
- Ahmad, F.; Kurugollu, F.; Kerrache, C.A.; Sezer, S.; Liu, L. NOTRINO: A NOvel hybrid TRust management scheme for Internet-of-vehicles. IEEE Trans. Veh. Technol. 2021, 70, 9244–9257. [Google Scholar] [CrossRef]
- Sagar, S.; Sheng, A.M.M.; Zaib, M.; Zhang, W. Towards a Machine Learning-driven Trust Evaluation Model for Social Internet of Things: A Time-aware Approach. Health Pervasive Comput. Technol. Healthc. 2020, 283–290. [Google Scholar] [CrossRef]
- Mahmood, A.; Siddiqui, S.A.; Sheng, Q.Z.; Zhang, W.E.; Suzuki, H.; Ni, W. Trust on wheels: Towards secure and resource efficient IoV networks. Computing 2022, 104, 1337–1358. [Google Scholar] [CrossRef]
- Wang, D.; Chen, X.; Wu, H.; Yu, R.; Zhao, Y. A Blockchain-Based Vehicle-Trust Management Framework Under a Crowd-sourcing Environment. In Proceedings of the 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 1950–1955. [Google Scholar]
- Yu, Y.; Jia, Z.; Tao, W.; Xue, B.; Lee, C. An Efficient Trust Evaluation Scheme for Node Behavior Detection in the Internet of Things. Wirel. Pers. Commun. 2017, 93, 571–587. [Google Scholar] [CrossRef]
- Satyananda, E.H. A Trust Management Scheme for Securing Transport Networks. Int. J. Comput. Appl. 2017, 180, 38–42. [Google Scholar]
- Fabi, A.K.; Thampi, S.M. A trust management framework using forest fire model to propagate emergency messages in the Internet of Vehicles (IoV). Veh. Commun. 2022, 33, 100404. [Google Scholar] [CrossRef]
- Bangui, H.; Ge, M.; Buhnova, B. A hybrid machine learning model for intrusion detection in VANET. Computing 2021, 104, 503–531. [Google Scholar] [CrossRef]
- Zhang, J.; Zheng, K.; Zhang, D.; Yan, B. AATMS: An Anti-Attack Trust Management Scheme in VANET. Digit. Object Identifier 2020, 8, 21077–21090. [Google Scholar] [CrossRef]
- Lai, C.Z.; Du, Y.Y.; Guo, Q.L.; Zheng, D. A trust-based privacy-preserving friend matching scheme in social Internet of Vehicles. Peer-to-Peer Netw. Appl. 2021, 14, 2011–2025. [Google Scholar] [CrossRef]
- Li, X.; Liu, J.; Li, X.; Sun, W. RGTE: A reputation-based global trust establishment in VANETs. In Proceedings of the 2013 5th International Conference on Intelligent Networking and Collaborative Systems, Xi’an, China, 9–11 September 2013; pp. 210–214. [Google Scholar]
- Patel, P.; Jhaveri, R. A Honeypot Scheme to Detect Selfish Vehicles in Vehicular Ad-hoc Network. In Computing and Network Sustainability, Proceedings of the International Research Symposium on Computing and Network Sustainability (IRSCNS); Springer: Panaji, India, 2016; Volume 7, pp. 1–2. [Google Scholar]
- Hamdan, S.; Hudaib, A.; Awajan, A. Detecting Sybil attacks in vehicular ad hoc networks. Int. J. Parallel Emergent Distrib. Syst. 2019, 36, 69–79. [Google Scholar] [CrossRef] [Green Version]
- Butler, J.K. Toward understanding and measuring conditions of trust: Evolution of a conditions of trust inventory. J. Manag. 1991, 17, 643–663. [Google Scholar] [CrossRef]
- Xia, H.; Xiao, F.; Zhang, S.S.; Hu, C.Q.; Cheng, X.Z. Trustworthiness Inference Framework in the Social Internet of Things: A Context-Aware Approach. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019. [Google Scholar]
- Chen, I.R.; Bao, F.; Guo, J. Trust-based Service Management for Social Internet of Things Systems. IEEE Trans. Dependable Secur. Comput. 2016, 13, 684–696. [Google Scholar] [CrossRef] [Green Version]
- Kerrache, C.A.; Calafate, C.T.; Cano, J.-C.; Lagraa, N.; Manzoni, P. Trust Management for Vehicular Networks: An Adversary-Oriented Overview. IEEE Access 2016, 4, 9293–9307. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Overview of trust provisioning for information and communication technology infrastructures and services. ITU-T Recommendation. 2017. Available online: https://www.itu.int/rec/T-REC-Y.3052-201703-I/en (accessed on 24 May 2022).
- Tufail, A.; Namoun, A.; Sen, A.A.A.; Kim, K.-H.; Alrehaili, A.; Ali, A. Moisture Computing-Based Internet of Vehicles (IoV) Architecture for Smart Cities. Sensors 2021, 21, 3785. [Google Scholar] [CrossRef]
- Xu, X.; Gu, R.; Dai, F.; Qi, L.; Wan, S. Multi-objective computation offloading for Internet of Vehicles in cloud-edge computing. Wirel. Netw. 2020, 26, 1611–1629. [Google Scholar] [CrossRef]
- Kapassa, E.; Themistocleous, M.; Christodoulou, K.; Iosif, E. Blockchain Application in Internet of Vehicles: Challenges, Contributions and Current Limitations. Future Internet 2021, 13, 313. [Google Scholar] [CrossRef]


| Domain | Function |
|---|---|
| In-Vehicle Domain | Communication between the OBU and application units (AUs) within the vehicle. AU can be a specific device, such as a mobile phone, or a virtual module integrated into an OBU. The connection can be wired or wireless, such as WiFi or Bluetooth. |
| Ad Hoc Domain | The wireless communication between OBUs and RSUs can be single-hop or multi-hop, namely V2V and V2R. |
| Infrastructure Domain | OBU and RSU communicate with infrastructure components, such as satellite, hot spot, and 5G, to access the Internet. For RSUs, the connection can be wired. |
| Layer | Function |
|---|---|
| End | The end system is mainly used to collect and obtain relevant information about the vehicle, and it can sense the current driving state of the vehicle and the surrounding environment, which represents the intelligent sensing system of the vehicle. Moreover, it is also a ubiquitous communication terminal, just like V2X communication. Meanwhile, it is also a device that can identify the network credibly and enable the vehicle to have an addressing sum. |
| Management | This layer is used to solve the interconnection between V2X, realize the communication between vehicles and various heterogeneous networks, and ensure the serviceability, real-time performance and network universality from the aspects of function and performance. In the meantime, it unifies the private network and the public network. |
| Cloud | IoV is a cloud-based information platform, including ITS, logistics, mobile Internet, auto repair and auto parts, vehicle management, vehicle rental, insurance, vehicle management of enterprises and institutions, automobile manufacturers, emergency rescue, etc. The aggregation of multi-source mass information requires cloud computing functions such as mass storage, security authentication, virtualization and real-time interaction. |
| No. | Trust Parameters | Contributions |
|---|---|---|
| [25] | Similarity (SMR), familiarity (FMR), packet delivery ratio (PDR) | Five algorithms in machine learning were used to analyze similarity, familiarity, and packet delivery ratio. |
| [28] | Confidence, interactions | This paper proposed a V2X communication trust model based on a recommendation to resist internal attacks. |
| [29] | Confidence, time sliding window, and time decay function | The author proposed a trust evaluation and management model based on the perspective of historical interaction. |
| [30] | Detection rate | Evidence combination-based collaborative trust management scheme against attacks. |
| [31] | Inter-vehicular subjective trust weight, role-based trust weight, original trust of vehicle, neighbor trust calculation | Multi-level Hybrid Trust Management Model (HHTM). |
| [40] | Resource availability, trust score | The author proposed a cluster-based hybrid VANETs trust management scheme. |
| [35] | Location, time closeness, information quality, confidence | Context-based trust assessment and management framework. |
| [36] | Reward | Task-based experience reputation (TER) framework. |
| [37] | Co-location relationship, co-work relationship, frequency and duration, cooperativeness, reward system, mutuality and centrality, community of interest | A quantifiable trust evaluation mechanism based on machine learning. |
| [38] | Likelihood, impact | Risk-based trust evaluation advanced model (RTEAM). |
| [41] | Reward, loss | A heterogeneous blockchain-based Hierarchical Trust Evaluation strategy. |
| [42] | Attitude (AT), subjective norms (SN), perceived behavioral control (PBC) | The author put forward a trust evaluation model based on human psychology. |
| [43] | Development, loss, decay | An integrated trust model, called REK, takes the third party’s opinion, experience and direct observation as three trust indicators. |
| [44] | Friendship similarity, cooperativeness, co-work similarity, Community of Interest | The author proposed a time-aware trust model that utilizes social relationships. |
| [45] | Cooperation, freshness of data | Hybrid trust management mechanism based on communication and data. |
| [46] | Source’s location, event location, rvent time | The author proposed a trust management scheme based on a crediting technique in MATLAB. |
| [47] | Information quality, role-oriented trust, effective distance | Hybrid trust management (NCT and DCT). |
| No. | Evaluation Parameters | Simulation Tools |
|---|---|---|
| [11] | Precision(P), recall (R), communication overhead | GloMoSim 2.03. |
| [27] | FMR (familiarity), PDR | CRAWDAD dataset. MATLAB. |
| [28] | Recommendation usage rate, FNR, prediction rate | Undefined. |
| [29] | Influence of node behavior on direct trust value, influence of the integration of direct trust and recommended trust on PDR, influence of the time sliding window and time decay, function on the direct trust value | Mobile model. |
| [30] | Precision and recall | NS2. |
| [31] | Performance quality level (PQL), feedback accuracy level (FAL) | MATLAB. |
| [35] | End-to-end delay (E2ED), event detection probability (EDP), anomaly ratio (AR), FPR, trusted and untrusted packets | Veins. |
| [36] | FPR, TPR, precision, recall | Network Simulator 2.35 (NS 2.35), the Open Street Map (OSM) database. |
| [37] | FPR, TNR | SIGCOMM-2009 conference, which is available in CRAWDAD. |
| [38] | Undefined cases (UND), true positive rate (TPR) | MATLAB. |
| [53] | TPR, FPR, trust computation error | NS 2.35. |
| [54] | Accuracy, recall, precision, F1-measure | CICIDS2017 dataset MATLAB R2019a on Windows 10 (random forest and coresets models). |
| [45] | The rate of untrust packets, the rate of trust packets, packet delivery ratio | Network Simulator Omnet ++ and Veins (Vehicle in Network). |
| [46] | Travel time, accuracy, CO2 emissions, communication overhead | Veins. |
| [55] | Pairwise orderedness, threshold of trust value, TPR, TNR | Veins. |
| [56] | Precision, recall, F1-score | CRAWDAD dataset. |
| No. | Attack Types |
|---|---|
| [11] | Simple attack (SA), bad-mouthing attack (BMA), zig-zag (on-and-off) attack (ZA). |
| [28] | Blackhole attackers, grayhole attackers. |
| [30] | Bad-mouthing attacks, time-dependent attacks, selective misbehavior attacks. |
| [41] | Task attack, privacy leakage attack. |
| [47] | Man-in-the-Middle (MiTM) attacks, zig-zag attacks. |
| [55] | On-and-off attack, newcomer attack, collusion attack. |
| [56] | Bad-mouthing attack, semi-honest attack. |
| [61] | Cheating attack, grayhole, bad-mouthing attack. |
| [62] | Self-promoting attacks, ballot-stuffing attacks, whitewashing attacks, bad-mouthing attacks, discriminatory attacks. |
| [63] | Certificate replication attack, eavesdropping attack, attacks on privacy. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Zen, H.; Sabri, M.F.M.; Wang, X.; Kho, L.C. Towards Strengthening the Resilience of IoV Networks—A Trust Management Perspective. Future Internet 2022, 14, 202. https://doi.org/10.3390/fi14070202
Wang Y, Zen H, Sabri MFM, Wang X, Kho LC. Towards Strengthening the Resilience of IoV Networks—A Trust Management Perspective. Future Internet. 2022; 14(7):202. https://doi.org/10.3390/fi14070202
Chicago/Turabian StyleWang, Yingxun, Hushairi Zen, Mohamad Faizrizwan Mohd Sabri, Xiang Wang, and Lee Chin Kho. 2022. "Towards Strengthening the Resilience of IoV Networks—A Trust Management Perspective" Future Internet 14, no. 7: 202. https://doi.org/10.3390/fi14070202
APA StyleWang, Y., Zen, H., Sabri, M. F. M., Wang, X., & Kho, L. C. (2022). Towards Strengthening the Resilience of IoV Networks—A Trust Management Perspective. Future Internet, 14(7), 202. https://doi.org/10.3390/fi14070202





