1. Introduction
The COVID-19 pandemic turned an unprepared world upside down. Millions worldwide were either out of work or teleworking for the first time. Businesses had to adapt quickly, and the first few months were wrought with one mishap or the other. A mobile world filled with an exploding volume of Internet of Things (IoT) was not prepared to securely handle working from home. Safeguards that are in place on the premises of government and industry are not in place at their employee’s homes. Moreover, all of this happened during an election year for the United States (US).
Citizens of the US were warned that they would put their lives as well as the lives of others in danger if they voted in person at the polls. They were also warned of the unreliability of voting by mail while at the same time being told of the safety of voting by mail. Then there were all of the claims of voter fraud [
1]. US citizens either took a side or were confused about the right thing to do. This left many asking why, in this 21st century, in a technological age where majority of the business transactions are taking place online, we do not have the capability to cast votes online [
2]. The primary reasons are privacy, tampering, and security. How do we allow individuals to vote online and prove their identity? How do we allow them to vote only once? How do we keep their vote private? How do we keep our voting systems tamper-proof from hackers [
3]? We do this by utilizing the ideas first put forth within the Mobile Identity, Credential, and Access Management(ICAM) framework. These ideas will be elaborated upon throughout this paper [
4].
Since the pace of the usage of IoT has increased within industry at the same rate as that of personal devices, it is high time for trusted digital identities that can scale from on-site to the cloud to personal residences. A digital identity is the computerized representation of an entity that exists in the physical world. This entity may be a person, organization, application, or device. As telework becomes more and more the norm, with smart phone users increasing annually and the mobile web flourishing, it is critical to implement stronger security. From personal devices to industry to government, the internet has become the primary means of modern communication. People want secure communication. US citizens want to vote online. This has further increased the need for a method of tracking and securing these devices. An organization must not only know the identity of the users on their networks and have the capability of tracing the actions performed by a user, but the organization must also trust the system providing this knowledge. Online retailers are faced with the challenge of authenticating a card remotely and proving that the person making the purchase is the actual card holder. A person cannot claim their transaction is fraudulent if they cannot prove it was not them making the online purchase.
Hence, the novelty of this work lies in examining how 5G, blockchain-based public key infrastructure (PKI), near field communication (NFC), and zero trust architecture securely provides not only a trusted digital identity for telework but also provides a trusted digital identity for secure online voting. This paper goes on to discuss how blockchain-based PKI, NFC, and the cloud provide a roadmap for how industry and governments can update existing frameworks to obtain a trusted digital identity that would provide secure telework and online voting capabilities. A framework is provided for trusted digital identity in cyberspace.
Section 2 presents a summary of blockchain-based PKI followed by a description of NFC and digital identities.
Section 3 discusses the challenges. The usage of cloud computing and the types available are defined to offer context for how many organizations are currently facing their telework challenges.
Section 4 presents an examination of how blockchain-based PKI, NFC, and the cloud may provide a roadmap for how industry and governments can update existing frameworks to obtain a trusted digital identity that would provide secure telework and online voting capabilities.
Section 5 presents a framework for updating the existing frameworks.
Section 6 discusses the security within the system and
Section 7 presents the conclusion and future work.
4. Literature Review
The idea of using blockchain for an e-voting system is not new. There is the Universiti Tun Hussein Onn Malaysia (UTHM) e-voting system. It is based on common blockchain concepts from Nakamoto and offers no registration process as a method to ensure anonymity. A group of students from UTHM designed the e-voting system using the web browser as the frontend of the system, where it was never explained how a voter would be authenticated. Then, the browser acting as the client sends the user’s vote to the blockchain e-voting system’s backend [
21].
An e-voting system using blockchain that consists of a voter list, administration management services, and election preparation services has also been proposed [
22]. It hails all of the integrity benefits and warns of the risks of central authority control but using no trusted digital identities. There is nothing similar to PKI to ensure the integrity of the system nor ensure the system itself is tamper-proof.
Blockchain as a service for e-voting has also been proposed. It works by using a permissioned Proof-of-Authority (POA) blockchain that consists of two types of nodes: a district node and a bootnode. A district node represents a voting district, while the bootnode is a service that allows the districts to communicate with each other. This system allows the users to authenticate themselves as well as authenticate their vote [
23]. It would take little effort for individuals to vote multiple times within this proposed blockchain as a service e-voting machine.
Another idea for blockchain-based e-voting is e-vote-as-a-service. This system would be hosted within a cloud and is business/corporation-structured. It does have a clear voter authentication mechanism using tokens and places voters from a list into a pool. The purpose of this pool seems to be a way to loosely define a county or a district so the e-vote can be a service. The voting session established by the use of a token can provide some voter anonymity until the vote is placed on a blockchain via the blockchain configurator [
24].
Building upon the e-vote-as-a-service is the blockchain e-voting within a smart city concept called smart e-voting. The proposed framework relies heavily upon existing blockchain infrastructures and Dijkstra’s algorithm for trust [
25]. However, it is quick to see that a random trust value does not provide the same level of trust that a PKI framework can provide. Blockchain-based PKI has built-in trust that meets all tenets of ZTA.
Finally, there is VoteChain, which is, as its name makes clear, a blockchain-based e-voting system. VoteChain makes use of three nodes and a gateway node. This blockchain network consists of a 6-core processor, 1 TB SSD storage, and a 1 Gbps local area network. Each vote block has the previous block’s hash value, proof of work, and a root of the Merkle tree of votes. Each vote contains a hash of the entire vote, timestamp, vote data, voter identification, which is a unique ID to verify a user’s identity, and a one-time password [
26]. This system would not work in the real world. Not all voters have 1 Gbps networks, nor do they have multicore processors, much less 6-core processors. Plus, how many voters want their name tied to their vote?
5. A Roadmap for Updating Existing Frameworks to Obtain Trusted Digital Identities
In order to manage the vast number of devices, in addition to making people feel confident that a machine such as an e-voting system or a person is who they say they are, companies must deploy digital-credentialing systems and methods. Since trust is more of a social construct, giving it meaning and finding measurements within an electronic system proves challenging. The existing self-sovereign identities of the internet must be changed. Public key infrastructure (PKI) has been around for decades as a means of identifying and authenticating individuals and machines. A PKI will provide the policies, roles, software, hardware, and procedures necessary to create, manage, distribute, use, store, and revoke digital certificates. The most important aspect of PKI is that it establishes the identities of people, devices, and services [
14]. However, PKI is outdated and in need of a facelift. Blockchain provides a mechanism to update PKI in order to meet the demands of a mobile 21st century. The PKI framework, as it currently exists, has vulnerabilities. Reporting unauthorized certificates is a time-consuming and labor-intensive effort that leaves a CA open to a man-in-the-middle (MITM) attack. If the CAs are not operating correctly, the introduction of encryption has no value. Blockchain-based PKI techniques provide methods to secure the CA vulnerabilities immediately in real time [
27].
In order to affectively implement blockchain within PKI, establishing trust would be necessary to instantiate security measures against interference, breach, and eavesdropping [
28]. A considerable vulnerability to PKI applications and platforms is their dependence on a centralized cloud. PKI, in its current form, is centralized, relying on trusted third parties. Decentralizing and incorporating blockchains provides the means of overcoming several of the problems linked with the centralized cloud approach. Provenance and other startups are using blockchain to promote trust in product transactions from the source to the customer [
29]. Blockchains can cryptographically sign transactions and verify the originator’s cryptographic signature to guarantee a message’s origin [
29]. Blockchains also provide secure traceability of certifications and other relevant data in supply chains. Blockchain’s public availability ensures transactions can be linked to identify vulnerable mobile devices [
28]. Suitable for registering time, location, price, parties, and data, as they move through the supply chain, blockchain-based PKI systems will help strengthen mobile device security [
29]. A blockchain-based PKI running on a 5G network will allow for significantly improved performance and capabilities within mobile devices. Blockchain-based PKI’s authentication service will improve because 5G will employ higher and more directional frequencies such that the data signals can transmit more precisely using less energy [
16].
In addition, blockchain-based PKI allays several deficiencies of the existing CA within PKI, the primary deficiency being the centralization of the CA [
30]. Following the Identity, Credential, and Access Management (ICAM) framework laid out in Trusted Digital Identities for Mobile Devices, the CA can be made distributed [
20]. A distributed system is where all of the parties work together as a single coherent system. It has qualities of centralization and decentralization. There is still a central authority that has some control over the other parties in governing processes, yet the other parties can make many of their own decisions and work autonomously. Distribution improves availability, reliability, fault tolerance, performance, and scalability [
7].
Blockchain-based PKI utilizing NFC, as proposed in the ICAM framework [
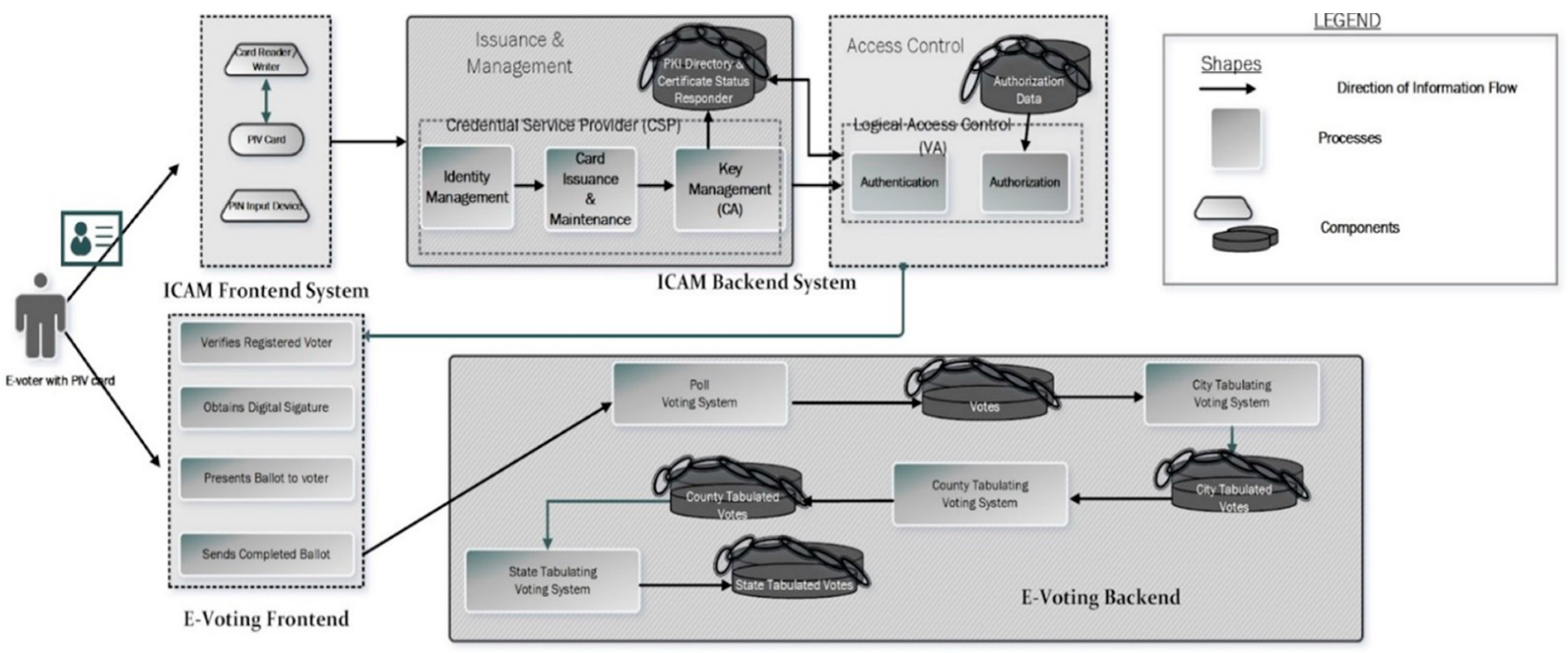
20], allows PKI to solve the challenges faced with online voting and BYOD. The ICAM system provides the authentication/authorization piece to the blockchain-based PKI e-voting system (BPES). Once authenticated through the ICAM and the BPES e-voting frontend, as shown in
Figure 1, the BPES e-voting frontend presents a ballot based on where the authorized user is registered to vote. The ballot displayed will contain the user’s city, county, state, and national choices for the current election. The frontend can be presented on a screen in-person at a voting poll or via a website.
Other blockchain-based e-voting systems have already been proposed using HTTP and WebSocket [
31]. BPES would utilize HTTPS and other defense in-depth per the tenets of ZTA such as those explained within [
32]. Incorporated with NFC capabilities, the website can be accessed via a mobile device. Once the user is finished, the filled-out ballot is sent to the e-voting backend, as shown in
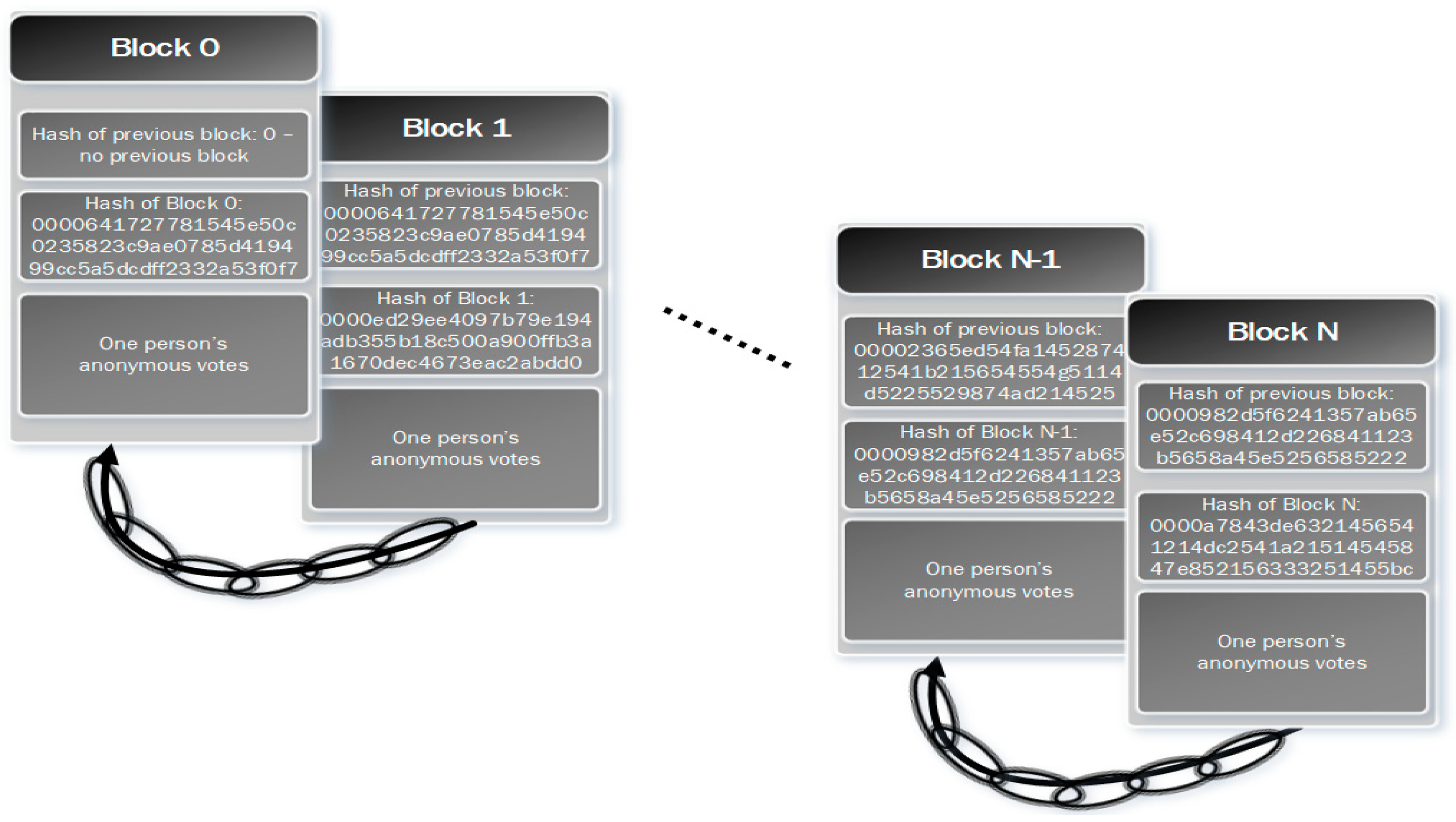
Figure 1. The vote for one user is contained on one BPES blockchain. It does not contain any identifying information about the voter. It only contains the voter’s selection digitally signed by the e-voting frontend. This digital signature allows for the nonrepudiation and traceability of the ballot’s origin. The integrity of the ballot is guaranteed through blockchain’s security and transparency.
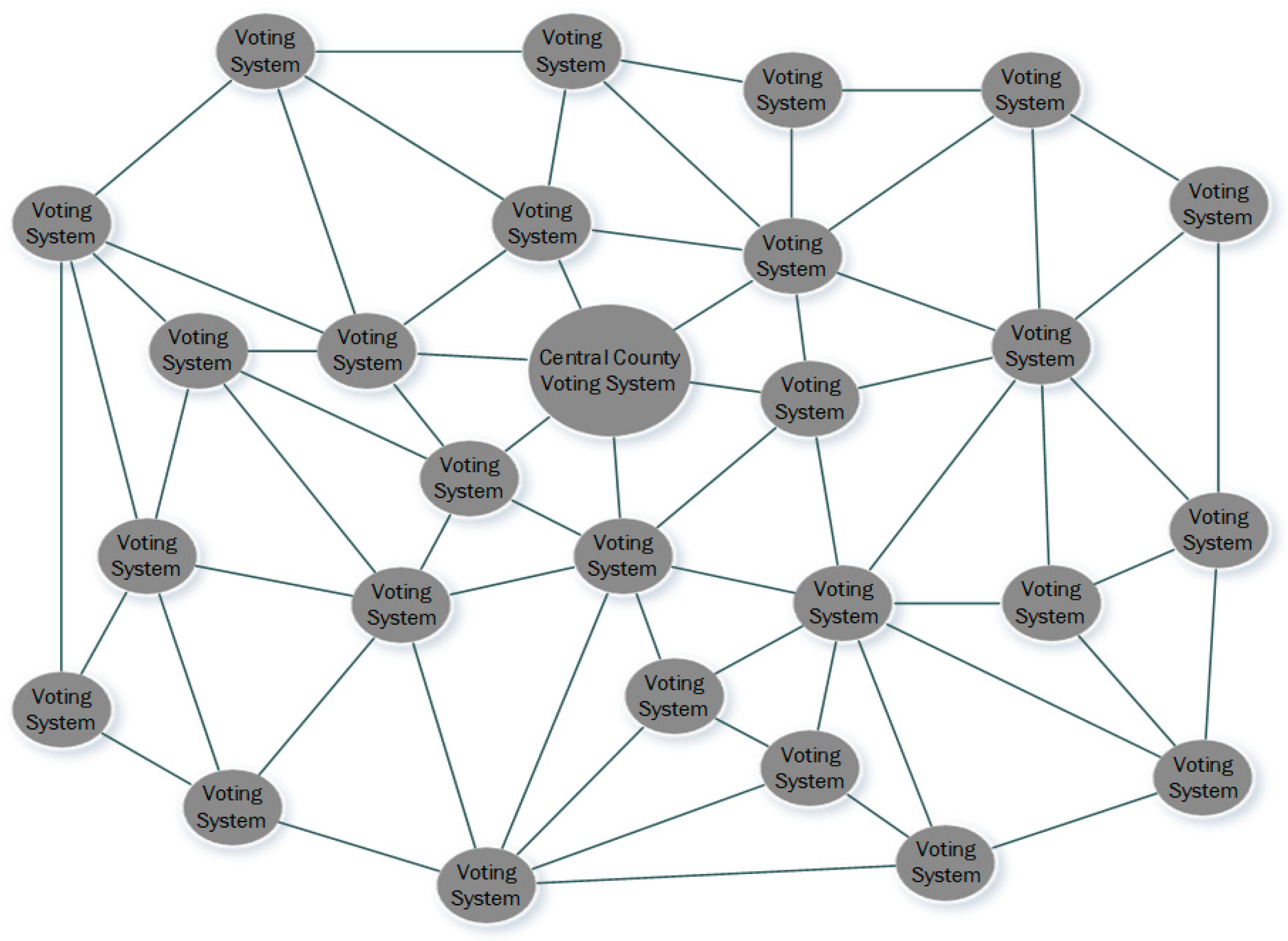
The city’s BPES would be independent yet connected to the county’s BPES, as shown in
Figure 2. The city may have any number of poll voting systems that act independently of the county system. However, one primary city system in the county will send a tally to the county system. A county has votes during an election that include their county or cities in addition to any votes necessary at the state level. The results for each county are added to a blockchain on a similar state system working in conjunction with the county’s independent system for the votes the state needs. Basically, the county-centralized system sends the tally of their county’s state votes on the blockchain part of the state’s system, much like the city did to the county system. The blockchain would look like
Figure 3 but would be one county’s votes, and that county would not be anonymous. It would include that county’s digital ID. It would be an extra security protocol, as that county’s public key would sign the blockchain, providing a means of nonrepudiation and integrity for each county. This would allow one to know where the votes came from and if the votes had been tampered with.
BPES relies on a distributed system shown in
Figure 4, with each system having a trusted ICAM digital ID all working interdependently. A central system maintains the tallies as necessary on each level with each central system forming another distributed system at the higher levels. This allows each system to retain a certain amount of independence while still functioning as a whole for a county, state, or national system. Not only does BPES provide a means for the autonomy of city, state, and federal entities but it also provides a means for trust and verification by city, state, and federal entities as well. The BPES provides the validation of a tamper-proof election through encryption.
The state voting system would look much like
Figure 2 but would consist of a distributed system made of the central blockchain-based PKI e-voting system from each county within the state. Each county’s central system would keep their county’s particular votes and send on to the state’s central system the state and federal votes. Then, the state’s central system would keep that state’s particular votes and send on to the federal central system that state’s votes. This would work for any nation state, but using the US as an example, all 50 states’ BPES central systems would form an additional distributed system at the federal level, systems within systems that function interpedently.
This enables the BPES to provide full functionality with all IoT things because ICAM ensures that the same security mechanisms that an employer has on their premises, for example, are utilized when their employees are teleworking. Therefore, utilizing ICAM with BPES guarantees the same level of security that is in place while voting in person is there when voting online regardless of the device used to cast a vote. A cryptographic challenge response protocol based on PKC and PKI has been developed for protecting NFC tags from attacks. This proposed framework consists of using symmetric cryptography [
27]. A digital identity given to an e-voting system within a blockchain-based PKI such as BPES ensures the confidentiality, integrity, availability, and traceability of online voting. Several experiments are being conducted with blockchain e-voting systems, but there are several concerns with a purely blockchain voting system [
24]. A blockchain-based PKI provides the trusted digital identity lacking in a blockchain-only e-voting system. Utilizing the ICAM framework, a city/county can gather their election results. There would be a variety of polling places across the county collecting citizens’ votes. The ICAM system, following all of the tenets of the framework, would be the frontend that would confirm a person’s identity online. Each polling location system would digitally sign the blockchain, adding another layer of defense to the blockchain-based PKI e-voting machine, whether it be an online system or within a physical location for in-person voting. The system would work seamlessly both for in-person and online voting.