Automated Penetration Testing Framework for Smart-Home-Based IoT Devices
Abstract
:1. Introduction
- Hardware: It includes all the physical components of the device (including the firmware).
- User interface: The devices used by the user to access the IoT devices (i.e. The user’s PC or Mobile Phone).
- Web Application: It helps in configuring, accessing, or controlling a device. In most cases, it is hosted on a web server residing in the device itself.
- Mobile Application: It is like a web application, but with more features and is more practical for the user’s use.
- Network and Cloud: All the communications between the devices and the applications happen to go through the network and the data is stored in the cloud.
- API (Application Protocol Interface): This plays a crucial role in making interoperability and interaction between the device, application, and the cloud possible.
- Design and implement an automated penetration framework, which can be used by both technical and non-technical persons with ease.
- Demonstrate how to use an automated penetration testing framework to test the security of different available smart home solutions.
2. Background and Related Work
- Interface Testing: Performed on the interfaces that interact with IoT devices, which handles input validation testing.
- Transport Testing: Performed on the network of the IoT devices, the associated cryptographic schemes and communication protocols for messages (protected).
- System Testing: Performed on the software, firmware, Oss, and system services to test implementation flaws, insecure system settings, and other known vulnerabilities. It also involves intelligent grey-box testing.
3. Proposed Framework
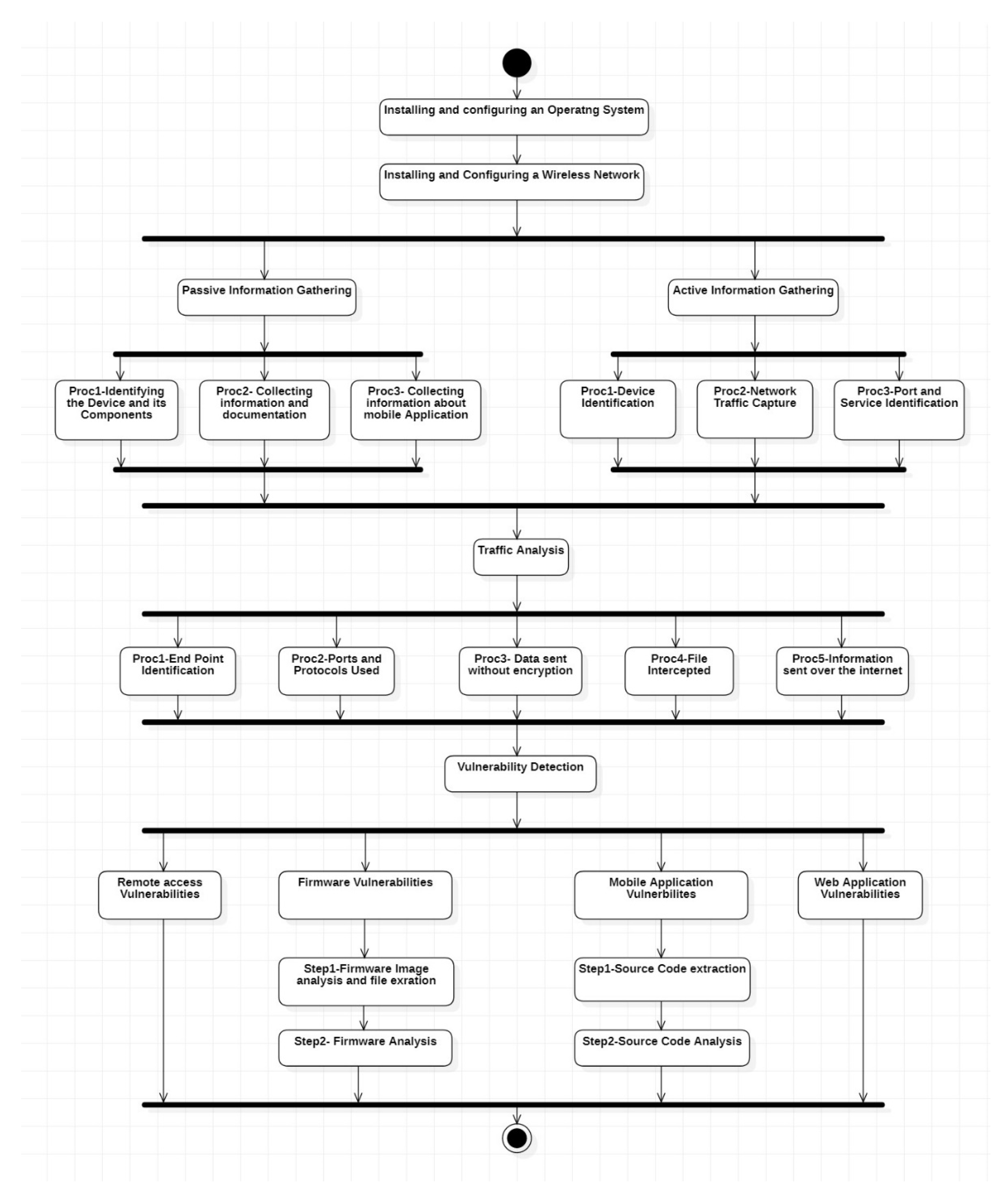
3.1. Design of the Framework
- Insecure Web Interface: IoT-based devices come with a corresponding application that handles the operation of the device. In the present era, all these applications are mobile-based, however, some devices still use a web application or have a web interface for handling their operation. For such devices, the framework has been designed to detect the presence of any web interface-based vulnerabilities, i.e., if the device has a web interface. The framework scans for any common web interface-based vulnerabilities, such as SQL injection, cross-site scripting, and many others, and reports its findings. This is done by using a tool called ‘Owasp Zap’.
- Remote Access Vulnerability (Improper Authentication): Some of the IoT devices can be accessed remotely from another system by using various remote access protocols. The most known remote access protocols for IoT devices are SSH and Telnet [11]. Any IoT device can be remotely accessed only if the ports corresponding to SSH and Telnet protocols are open, i.e., Port 22 (SSH) and Port 23 (Telnet), respectively. For such devices, the framework has been designed to detect any remote access vulnerabilities present by brute-forcing a password list on a user, mostly root, or a list of users. It scans for both SSH and Telnet-based remote access vulnerabilities. The tool used in the framework for doing this is ‘Medusa’.
- Insecure Network Services: Some IoT devices might be having unwanted services, unwanted ports open or services like FTP, Telnet or SSH, on open ports, which might be dangerous as attackers can use these ports to gain access to the device [17]. The framework is designed to detect any such insecure network services vulnerabilities by reading the captured pcap files and through the Nmap frameworks using the Nmap Search Engine (NSE).
- Lack of Transport Encryption: Most IoT devices, even after several updates, still tend to use the HTTP protocol instead of the HTTPS protocol, which can be dangerous as most of the information transported over the internet in such a manner is usually unencrypted. An attacker can easily intercept the traffic and analyse an HTTP packet and retrieve all the sensitive information about the device [18]. The framework is designed to detect any such vulnerabilities by following a similar methodology. It detects if any of the sensitive information is transported in an unencrypted manner, i.e., using the HTTP protocol. This is done using the tool ‘tshark’.
- Insecure Firmware/Software: IoT devices need to be updated quite often as manufacturers keep fixing bugs in the software. Some of these devices, while going through an update, use the HTTP protocol to get the firmware files from the cloud. This can be vulnerable if someone intercepts the traffic; the firmware files can be captured easily as they would be unencrypted and according to OWASP top 10 IoT vulnerabilities, if the update file is transferred via HTTP or if it is unencrypted (human-readable), then it is an insecure firmware vulnerability [19]. The framework is designed to detect these types of vulnerabilities using ‘tshark’.
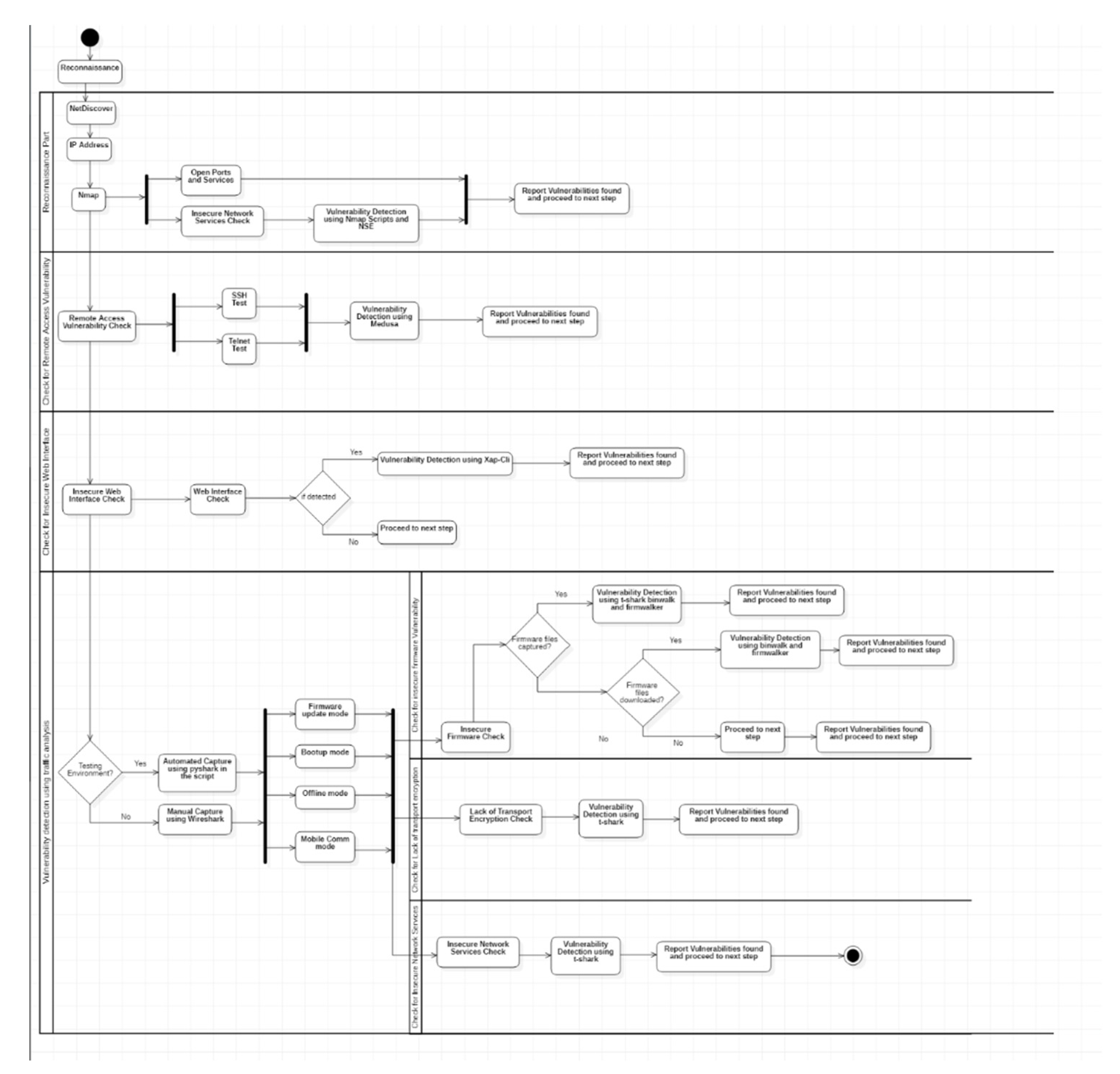
- Reconnaissance part (Net Discover and Nmap Scan): Initially, the framework does a Net Discover scan over an interface, usually the one to which the IoT device is connected, and retrieves the IP Address and the MAC Vendor Name (device manufacturer name) of the device. After that, a Nmap scan is done by the framework over the IP Address that has been retrieved through the Net Discover scan, and the results of this scan, which contains the list of open ports and the corresponding services running on them, are stored in a corresponding Nmap log file. The framework reports these results and proceeds to the next part.
- Check for Remote Access Vulnerability: In this part, the framework uses Medusa to conduct a brute force password attack over the IP Address of the device, retrieved via the ‘Net Discover’ part, to check whether any remote access vulnerabilities are present. It takes the user to run the check on, the password list, and the remote access protocol to check as an input, and executes the ‘Medusa’ tool with these corresponding flags to detect if the device can remotely be accessed using any of these passwords in the given password list. The input can vary between one user and a list of users, and the protocols it checks on are ‘SSH’ and ‘Telnet’, which are the two most common protocols used by IoT devices. The framework stores the output of the ‘Medusa’ tool executed with the provided input flags in a corresponding log file; this log file is scanned to check whether any of the passwords in the list could successfully brute force and provide access. If yes, a remote access vulnerability is recorded and reported and the framework proceeds to the next part.
- Check for Insecure Web Interface: This part can be divided into two steps.
- Step 1: The framework first checks whether the device has a corresponding web interface. For this, it uses the ‘whatweb’ tool, which checks whether HTTP is running over the device and reports its status, since HTTP is required for any device to have a web interface. If ‘whatweb’ detects HTTP running over the device, then it proceeds to the next step, or else the framework checks whether port 80 (HTTP) or port 443 (HTTPS) are open, and asks the user manually if he wishes to check for an insecure web interface. This step has been added for the cases where the ‘whatweb’ tool cannot detect ‘HTTP’, or when the devices use ‘HTTPS’, or when these protocols run over different ports, among others. If the framework detects the presence of a web interface it proceeds to the next step, else it reports that the device does not have a corresponding web interface.
- Step 2: If the framework detects the presence of a web interface, this step gets executed, or else the framework moves to part four. In this step, the framework uses the tool Zap-Cli with corresponding flags as input, and actively scans the web interface for all the vulnerabilities like SQL Injection, Cross-Site Scripting, Cross-Site Request Forgery, and many others. The results of this scan are stored in a corresponding log file and this log file is then string processed to check for any vulnerabilities detected by Zap-Cli. If the framework detects issues in the log file, then an insecure web interface vulnerability is recorded and reported and the framework proceeds to the next part.
- Automated Traffic Capture: In this part, initially, the framework asks the user whether he wishes to capture the traffic automatically using the framework or manually capture using Wireshark. This has been added as sometimes automated capture cannot guarantee accurate results if the testing environment is not rightly configured. This provides the user flexibility to capture the files manually or automatically, depending on his will. This part of the framework gets executed only if the user selects ‘Automatically’. Otherwise, the framework proceeds to the next part.Once the automatic option is selected, the framework asks the user for the state of the device, there are four possible states which are: Booting device, when the device boots up; Mobile Application Interaction, when the device interacts with its corresponding mobile application; Firmware mode, when the device goes through a firmware update; and Offline Mode when the device does not have an internet connection. The framework takes these states as input to capture the traffic in four different states and stores it in four different .pcap files (for analysing later). The capture is done using ‘pyshark’. The framework prompts the user to capture in all the states to ensure completeness of the capture. Once the capture is complete the framework proceeds to the next part.Note: the user needs to make sure manually that the device is in these states while selecting that corresponding state as input in the framework.
- Vulnerability detection through traffic analysis: After the capture is complete, either automatically through the framework or manually, the framework then analyses these captured .pcap files and checks for vulnerabilities present in them. To make the explanation easier, this part has further been divided into three parts, which are executed one after the other.
- Check for Insecure firmware: Initially, the framework asks the user whether the firmware files have been captured during a firmware update or downloaded from the manufacturer’s website. If neither is true, then the framework proceeds to the next step.If the firmware files have been captured:The framework uses ‘tshark’ to read the .pcap file, captured during the firmware update, to fetch the URL link to the binary image file of the firmware (which is on the cloud interface of the device). Once, it gets access to the URL link, the framework automatically downloads the binary image file (.bin file) and stores it in the same directory on the user’s system. The framework then extracts the firmware file system from the .bin file using the ‘binwalk’ tool. After that, the extracted firmware file system is searched using the ‘firmwalker’ tool for any firmware-based vulnerabilities. The framework records and reports an ‘insecure firmware vulnerability’ once it finds the URI link in ‘HTTP’, or once the download is successful, irrespective of whether the extraction of the firmware file system through binwalk or the firmwalker search was successful or not [19]. Post the ‘firmwalker’ scan, and once the check is complete, the framework proceeds to the next part.If the firmware files have been downloaded from the manufacturer’s website:The framework extracts the firmware file system from the .bin file using the ‘binwalk’ tool. After that, the extracted firmware file system is searched by the framework using the ‘firmwalker’ tool for any firmware-based vulnerabilities. If the firmwalker tool finds any firmware-based vulnerabilities, then the framework records and reports them, or else the framework proceeds to the next part.
- Check for Lack of transport encryption: The framework uses ‘tshark’ to read the pcap file, captured during the firmware update, to fetch the URL link, through which the device communicates with its corresponding cloud interface; generally, this is like the .bin file HTTP link, as above. Once it gets access to the URL link, the framework checks whether the device uses HTTP to communicate with the cloud interface to download the firmware files [18]. If the device uses HTTP, then ‘lack of transport encryption vulnerability’ is recorded and reported, or else the framework proceeds to the next part.
- Check for Insecure Network Services: The framework uses ‘tshark’ to read all the pcap files, captured in all the different modes, and to check for any insecure network-based vulnerabilities. This is done by checking the following:
- Any unwanted or unknown services are on open ports.
- If services like SSH, Telnet, and FTP, are on open ports.
- If any of the protocols like TCP, SSL, or TLS, have vulnerable older versions.
- If the services used by the device are not properly authenticated by the server.
If the framework detects any of the above, then the ‘Insecure Network Services’ vulnerability is recorded and reported. If not, the framework proceeds to the next part.
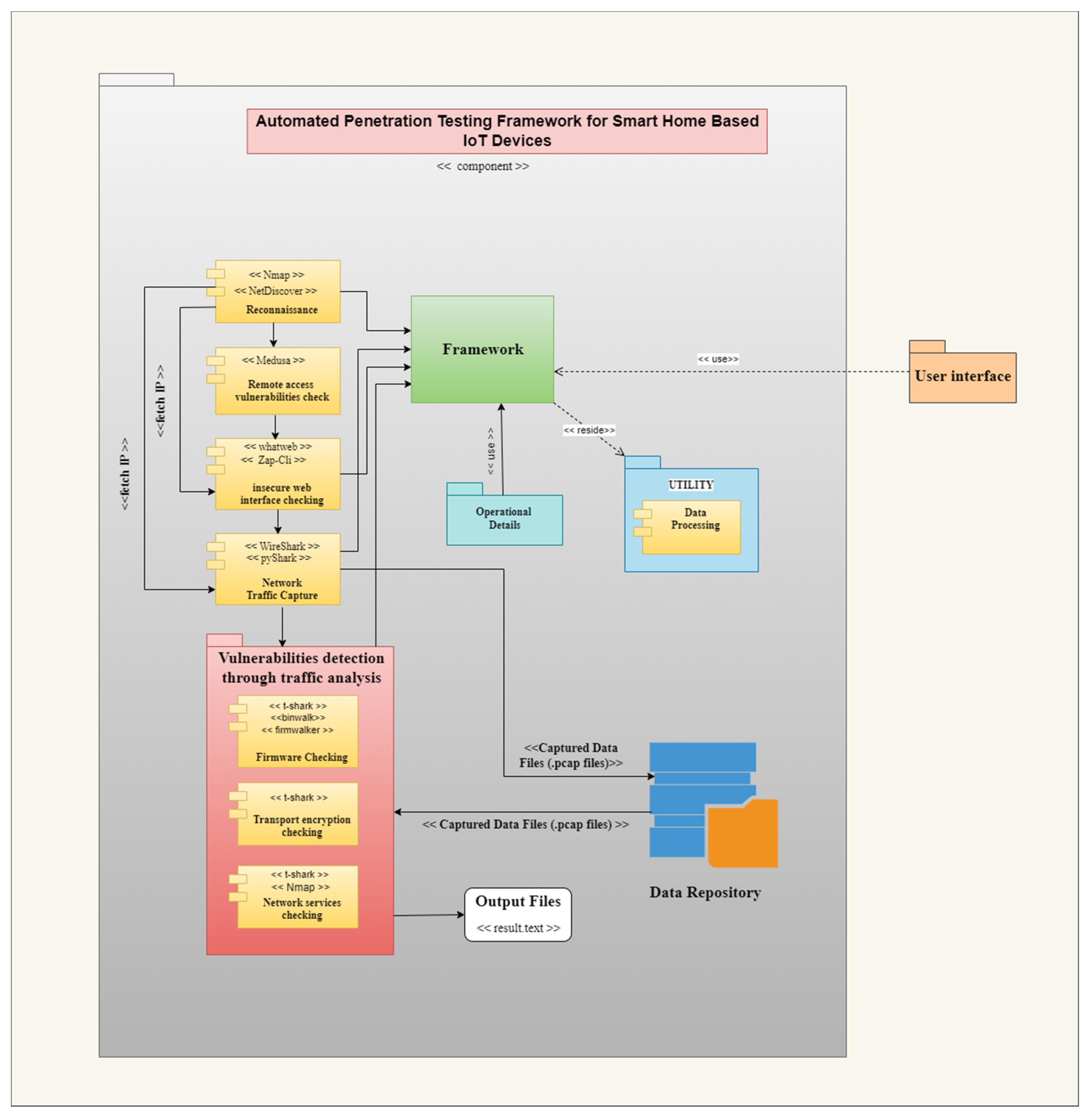
3.2. Implementation
4. Results and Analysis
- Pip3-based packages ‘pyshark’ and ‘scapy’ need to be installed using the commands “pip3 install pyshark” and “pip3 install scapy”, respectively, on the terminal.
- Zap-Cli needs to be installed using the command “pip3 install –upgrade zap-cli” on the terminal, and the $ZAP_PATH and $ZAP_PORT environment variables need to be set [22].
- Firmwalker needs to be installed in the same directory in which the folder containing the script is present. It can be installed using the command “git clone https://github.com/craigz28/firmwalker.git” [23].
5. Discussion
5.1. Scope
- The framework can run on other Unix platforms (apart from Kali Linux) provided that Python 3.6, the tools mentioned in the Design chapter, and the python-pip packages like ‘scapy’, and ‘pyshark’ are installed.
- This research only deals with the top five list of vulnerabilities mentioned in the Design subsection of the Proposed Framework section. It does not involve detecting cloud, mobile application, hardware, and physical device vulnerabilities.
- Although the Common Vulnerability Scoring System (CVSS) score depends on several metrics, this research mainly focuses on the base metrics and impact metrics, i.e., the base score for determining the severity of the vulnerability.
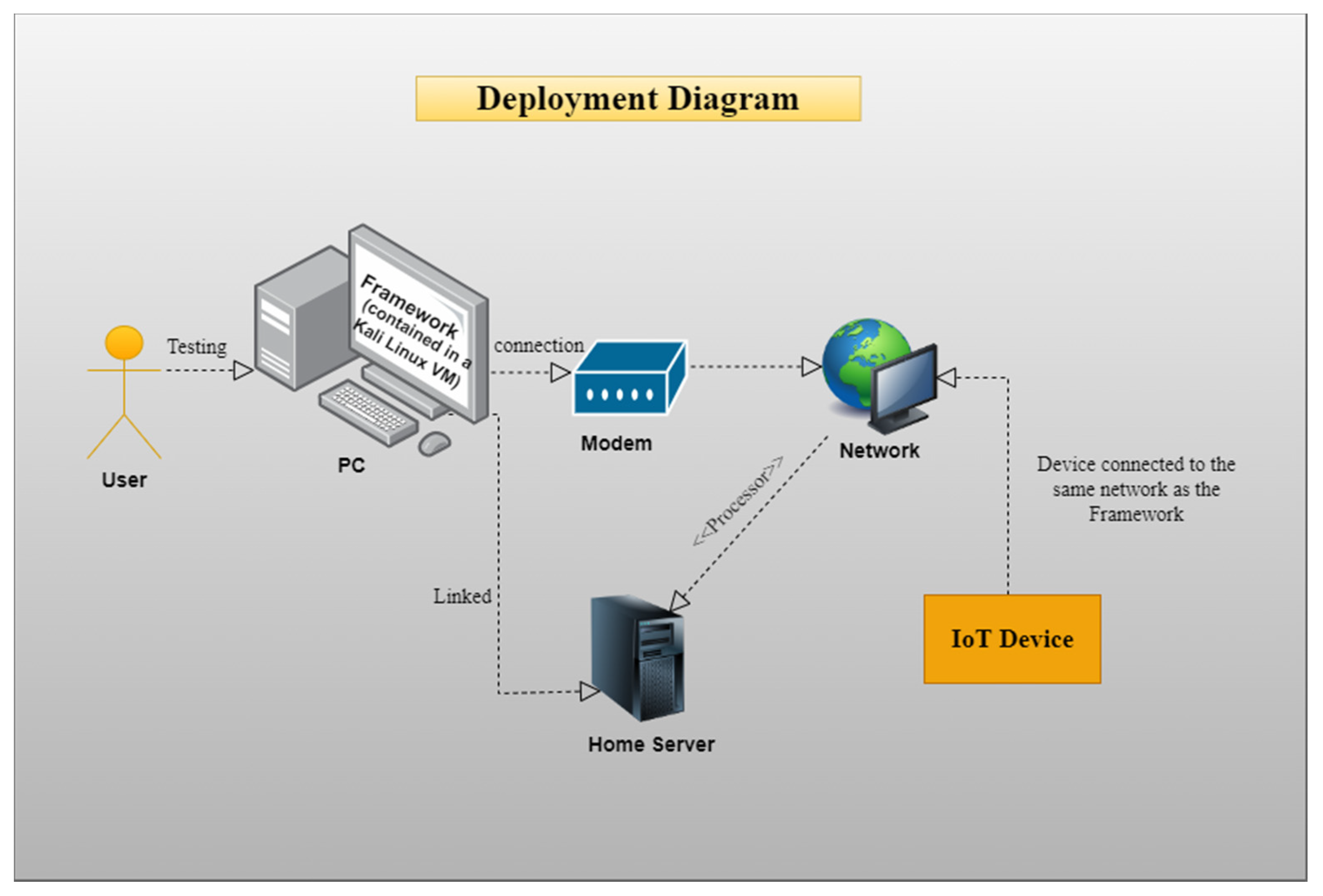
- Currently, the framework can only test the devices which are accessible over the network and, preferably, on the same network.
- Currently, this research does not involve providing a fix for the vulnerabilities found, it only involves discovering them.
5.2. Risks and Constraints
- Each device has its configuration process, so there is a risk of not being able to configure them properly for testing. Therefore, there is a possibility that devices may not be successfully configured, or misconfigured.
- It might be challenging to divert the network traffic from the IoT device to Kali Linux as its gateway. i.e., configuring a hotspot on Kali Linux.
- The automated network traffic capture of the framework might not work properly in case the testing environment is not properly configured, i.e., the traffic from the device does not have the testing OS Kali Linux as its gateway.
5.3. Contingency Planning
5.4. Limitations
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Source Code
References
- Sachidananda, V.; Toh, J.; Siboni, S.; Bhairav, S.; Shabtai, A.; Elovici, Y. Let the Cat out of the Bag: A Holistic Approach towards Security Analysis of the Internet of Things. In Proceedings of the 3rd ACM International Workshop on IoT Privacy, Trust, and Security, co-located with ASIA CCS 2017, New York, NY, USA, 2 April 2017; pp. 3–10. [Google Scholar] [CrossRef]
- Visoottiviseth, V.; Akarasiriwong, P.; Chaiyasart, S.; Chotivatunyu, S. PENTOS: Penetration Testing Tool for Internet of Thing Devices. In Proceedings of the IEEE Region 10 Annual International Conference, Proceedings/TENCON, Penang, Malaysia, 5–8 November 2017; pp. 2279–2284. [Google Scholar] [CrossRef]
- Papatsimouli, M.; Lazaridis, L.; Ziouzios, D.; Dasygenis, M.; Fragulis, G. Internet Of Things (IoT) Awareness in Greece. SHS Web Conf. 2022, 139, 3013. [Google Scholar] [CrossRef]
- Patton, M.; Gross, E.; Chinn, R.; Forbis, S.; Walker, L.; Chen, H. Uninvited Connections: A Study of Vulnerable Devices on the Internet of Things (IoT). In Proceedings of the 2014 IEEE Joint Intelligence and Security Informatics Conference, JISIC 2014, The Hague, The Netherlands, 24–26 September 2014; pp. 232–235. [Google Scholar] [CrossRef]
- Zhang, Z.K.; Cho, M.C.Y.; Wang, C.W.; Hsu, C.W.; Chen, C.K.; Shieh, S. IoT Security: Ongoing Challenges and Research Opportunities. In Proceedings of the IEEE 7th International Conference on Service-Oriented Computing and Applications, SOCA 2014, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar] [CrossRef]
- Duggan, D.P. Penetration Testing of Industrial Control Systems; Sandia National Laboratories: Albuquerque, New Mexico; Livermore, CA, USA, 2005. [Google Scholar]
- Lee, J.; Elovici, Y.; Shabtai, A.; Tippenhauer, N.O.; Siboni, S. Advanced Security Testbed Framework for Wearable IoT Devices. ACM Trans. Internet Technol. 2016, 16, 1–25. [Google Scholar] [CrossRef]
- Bing, K.; Fu, L.; Zhuo, Y.; Yanlei, L. Design of an Internet of Things-Based Smart Home System. In Proceedings of the 2nd International Conference on Intelligent Control and Information Processing, ICICIP 2011, Harbin, China, 25–28 July 2011; Volume 2, pp. 921–924. [Google Scholar] [CrossRef]
- Ghaffarianhoseini, A.; Ghaffarianhoseini, A.; Tookey, J.; Omrany, H.; Fleury, A.; Naismith, N.; Ghaffarianhoseini, M. The Essence of Smart Homes: Application of Intelligent Technologies towards Smarter Urban Future. Artif. Intell. Concepts Methodol. Tools Appl. 2016, 1, 79–121. [Google Scholar] [CrossRef]
- Yu, M.; Zhuge, J.; Cao, M.; Shi, Z.; Jiang, L. A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices. Future Internet 2020, 12, 27. [Google Scholar] [CrossRef]
- Costa, L.; Barros, J.P.; Tavares, M. Vulnerabilities in IoT Devices for Smart Home Environment. In Proceedings of the 5th International Conference on Information Systems Security and Privacy–ICISSP 2019, Prague, Czech Republic, 23–25 February 2019; pp. 615–622. [Google Scholar] [CrossRef]
- Myridakis, D.; Spathoulas, G.; Kakarountas, A.; Schinianakis, D. Smart Devices Security Enhancement via Power Supply Monitoring. Future Internet 2020, 12, 48. [Google Scholar] [CrossRef]
- Chu, G.; Lisitsa, A. Penetration Testing for Internet of Things and Its Automation. In Proceedings of the 20th International Conference on High Performance Computing and Communications, 16th International Conference on Smart City and 4th International Conference on Data Science and Systems, HPCC/SmartCity/DSS 2018, Exeter, UK, 28–30 June 2018; pp. 1479–1484. [Google Scholar] [CrossRef]
- Rak, M.; Salzillo, G.; Granata, D. ESSecA: An Automated Expert System for Threat Modelling and Penetration Testing for IoT Ecosystems. Comput. Electr. Eng. 2022, 99, 107721. [Google Scholar] [CrossRef]
- Chen, C.K.; Zhang, Z.K.; Lee, S.H.; Shieh, S. Penetration Testing in the IoT Age. Computer (Long Beach Calif) 2018, 51, 82–85. [Google Scholar] [CrossRef]
- OWASP Internet of Things Project–OWASP. Available online: https://wiki.owasp.org/index.php/OWASP_Internet_of_Things_Project#tab=IoT_Top_10 (accessed on 29 July 2022).
- Smith, C. Top 10 2014-I3 Insecure Network Services–OWASP. Available online: https://wiki.owasp.org/index.php/Top_10_2014-I3_Insecure_Network_Services (accessed on 29 July 2022).
- Smith, C. Top 10 2014-I4 Lack of Transport Encryption–OWASP. Available online: https://wiki.owasp.org/index.php/Top_10_2014-I4_Lack_of_Transport_Encryption (accessed on 29 July 2022).
- Smith, C. Top 10 2014-I9 Insecure Software/Firmware–OWASP. Available online: https://wiki.owasp.org/index.php/Top_10_2014-I9_Insecure_Software/Firmware (accessed on 29 July 2022).
- Kruchten, P.B. The 4+1 View Model of Architecture. IEEE Softw 1995, 12, 42–50. [Google Scholar] [CrossRef]
- Górski, T. The 1+5 Architectural Views Model in Designing Blockchain and IT System Integration Solutions. Symmetry 2021, 13, 2000. [Google Scholar] [CrossRef]
- Grunwell, D. GitHub–Grunny/Zap-Cli: A Simple Tool for Interacting with OWASP ZAP from the Commandline. Available online: https://github.com/Grunny/zap-cli (accessed on 20 September 2019).
- Smith, C. GitHub–Craigz28/Firmwalker: Script for Searching the Extracted Firmware File System for Goodies! Available online: https://github.com/craigz28/firmwalker (accessed on 20 September 2019).
- CVSS v3.1 Specification Document. Available online: https://www.first.org/cvss/v3.1/specification-document (accessed on 29 July 2022).
- Fernandez, E.B.; Washizaki, H.; Yoshioka, N.; Okubo, T. The Design of Secure IoT Applications Using Patterns: State of the Art and Directions for Research. Internet Things 2021, 15, 100408. [Google Scholar] [CrossRef]
- Kumar, R.; Sharma, R. Leveraging Blockchain for Ensuring Trust in IoT: A Survey. J. King Saud Univ.–Comput. Inf. Sci. 2021. [Google Scholar] [CrossRef]
- Adhikari, U.; Morris, T.; Pan, S. WAMS Cyber-Physical Test Bed for Power System, Cybersecurity Study, and Data Mining. IEEE Trans. Smart Grid. 2017, 8, 2744–2753. [Google Scholar] [CrossRef]
- GitHub - Rocky9624/Automated-Penetration-Testing-Framework. Available online: https://github.com/rocky9624/Automated-Penetration-testing-Framework (accessed on 18 September 2022).

| Test Case | Description | Device Tested | Vulnerabilities Detected by the Framework | Execution Time for Testing by the Framework |
|---|---|---|---|---|
| 1 | Used the framework to test for the top vulnerabilities in the Smart plug. | Tp-Link Smart Plug | A probable Insecure Network Services vulnerability. | 2–3 s (approximately) |
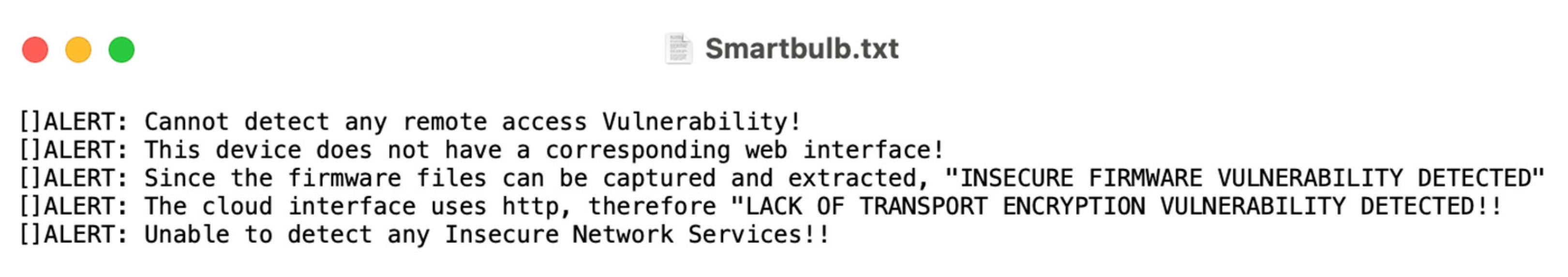
| 2 | Used the framework to test for the top vulnerabilities in the Smart bulb. | Tp-Link Smart bulb | Lack of Transport Encryption and Insecure Firmware Vulnerability. | 5–8 s (approximately) |
| 3 | Used the framework to test for the top vulnerabilities in the Smart Camera. | Tp-Link Smart Camera | Lack of Transport Encryption and Insecure Firmware Vulnerability. | 5–8 s (approximately) |
| 4 | Used the framework to test for the top vulnerabilities in the Google Home Mini. | Google Home Mini | No Vulnerabilities were detected. | 1–2 s (approximately) |
| 5 | Used the framework to test for the top vulnerabilities in the LIFX Smart bulb. | LIFX Smart bulb | No Vulnerabilities were detected. | 1–2 s (approximately) |
| Device | Total Score |
|---|---|
| Tp-Link Smart Plug | N/A |
| Tp-Link Smart Bulb | 14.4 |
| Tp-Link Smart Camera | 14.4 |
| Google Home Mini | 0 |
| LIFX Smart Bulb | 0 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Akhilesh, R.; Bills, O.; Chilamkurti, N.; Chowdhury, M.J.M. Automated Penetration Testing Framework for Smart-Home-Based IoT Devices. Future Internet 2022, 14, 276. https://doi.org/10.3390/fi14100276
Akhilesh R, Bills O, Chilamkurti N, Chowdhury MJM. Automated Penetration Testing Framework for Smart-Home-Based IoT Devices. Future Internet. 2022; 14(10):276. https://doi.org/10.3390/fi14100276
Chicago/Turabian StyleAkhilesh, Rohit, Oliver Bills, Naveen Chilamkurti, and Mohammad Jabed Morshed Chowdhury. 2022. "Automated Penetration Testing Framework for Smart-Home-Based IoT Devices" Future Internet 14, no. 10: 276. https://doi.org/10.3390/fi14100276
APA StyleAkhilesh, R., Bills, O., Chilamkurti, N., & Chowdhury, M. J. M. (2022). Automated Penetration Testing Framework for Smart-Home-Based IoT Devices. Future Internet, 14(10), 276. https://doi.org/10.3390/fi14100276








