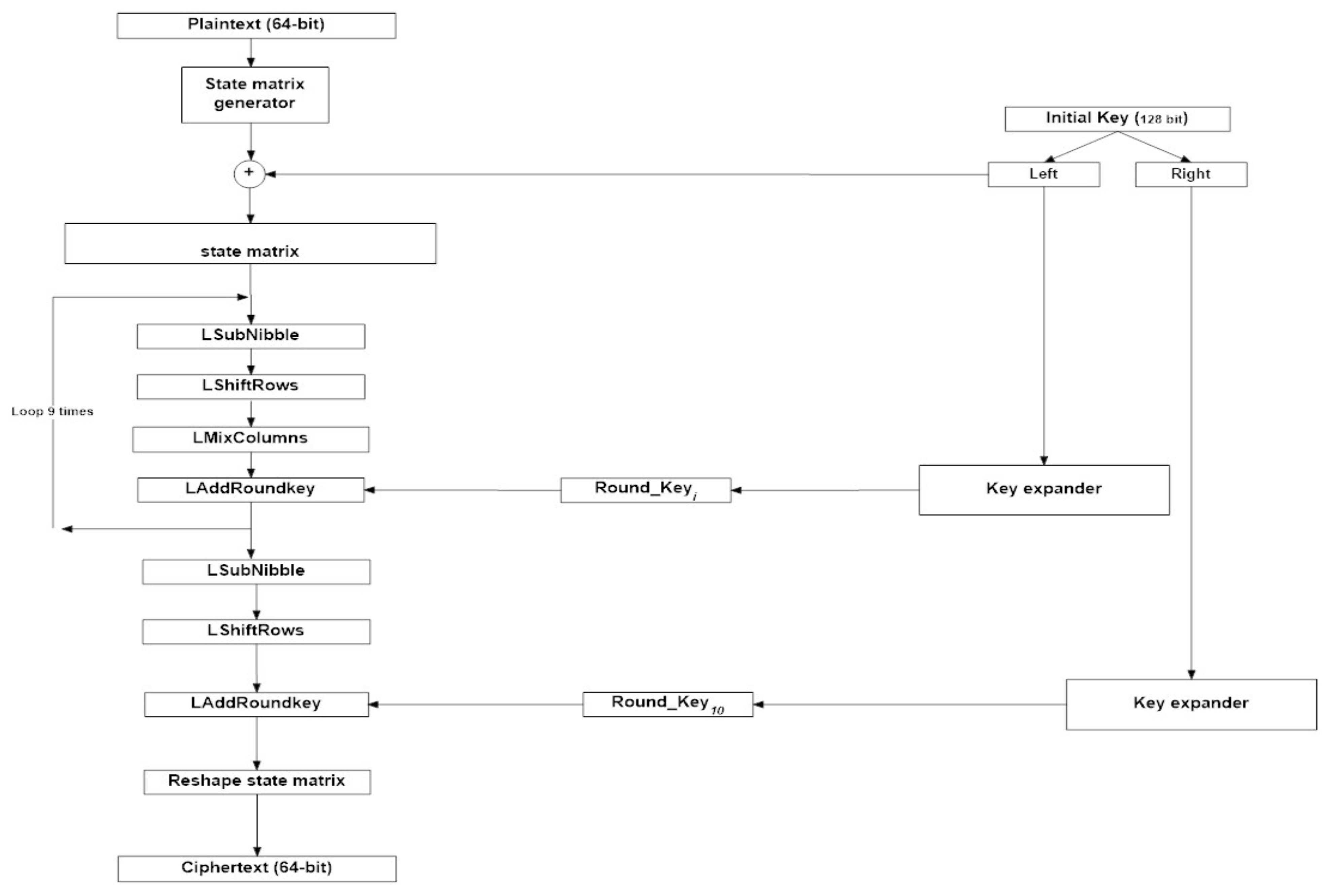
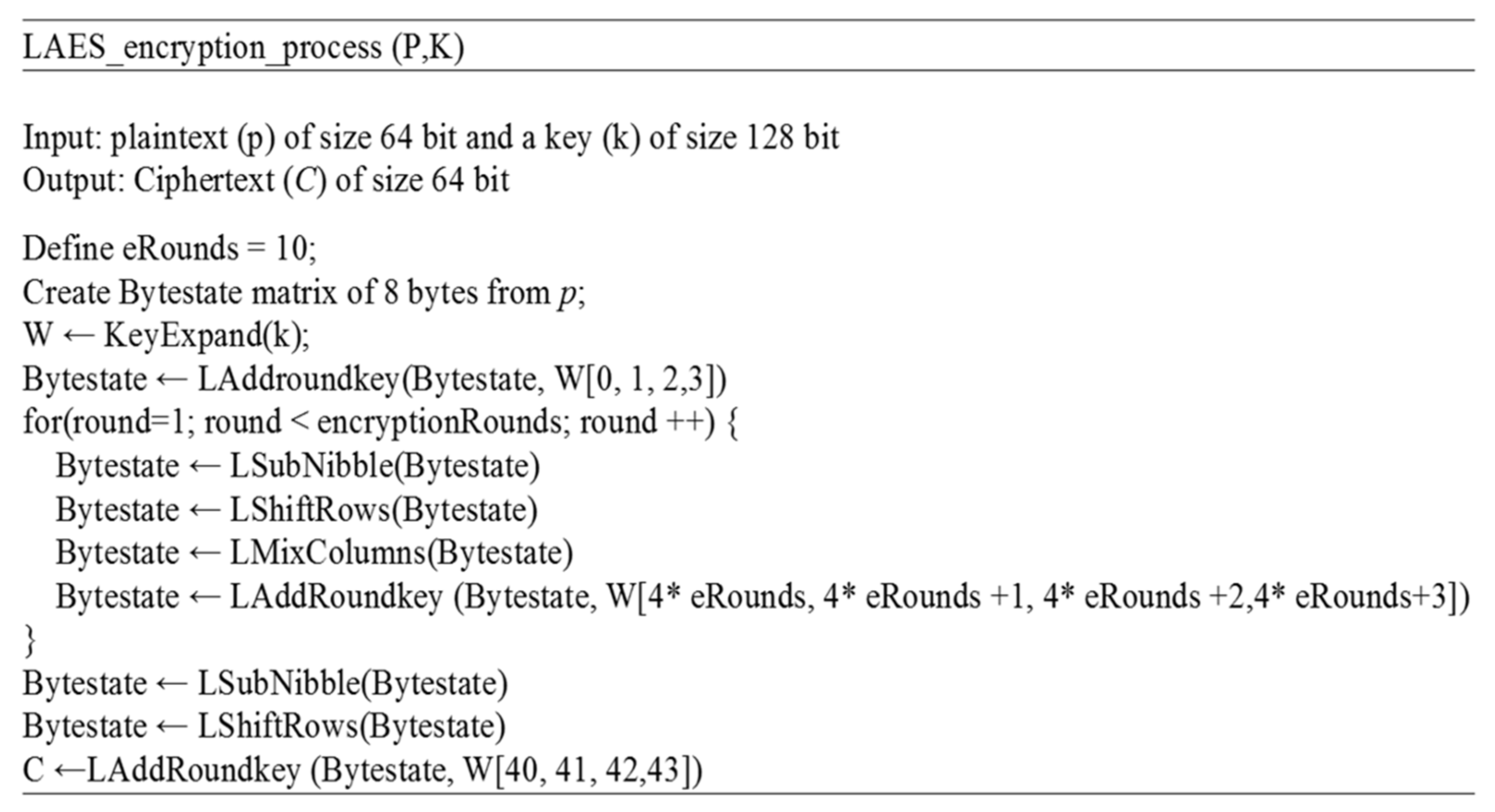
The design of LAES takes into consideration the following modifications: S-box arrangements, operation of finding the inverse in GF(2
4), affine transformation, and key expansion process. These changes allow the algorithm to operate on 64-bit plaintext input. This section presents an overview of the main components of the proposed 64-bit LAES cryptographic algorithm that uses a 128-bit encryption key. The LAES consists of ten rounds that use an expanded key generated from the initial key. The operation of LAES is described as follows, as illustrated in
Figure 1 and
Figure 2 (the major components are described in the next section):
3.4. Affine Transformation
The affine transformation can be achieved in the finite field GF(2
4) modulo of the irreducible polynomial x
4 + x + 1 using Equation (1), for 0 ≤
i < 4, where
bi is the
ith bit of the 4-bit input (b), and
Ci is the
ith bit of a 4-bit constant (C = 0110 b). For example, the affine transformation of 0 is computed by first finding the inverse of 0 from
Table 4, then the affine transformation is computed using the constant
C.
b0’ = b0 ⊕ b2 ⊕ b3 ⊕ c0 = 0 ⊕ 0 ⊕ 0 ⊕ 0 = 0
b1’ = b1 ⊕ b3 ⊕ b0 ⊕ c1 = 0 ⊕0 ⊕ 0 ⊕ 1 = 1
b2’ = b2 ⊕ b0 ⊕ b1 ⊕ c2 = 0 ⊕ 0 ⊕ 0 ⊕ 1 = 1
b3’ = b3 ⊕ b1 ⊕ b2 ⊕ c3 = 0 ⊕ 0 ⊕ 0 ⊕ 0 = 0
Similarly, this transformation can be achieved in a matrix notation in GF(2
4) modulo with the irreducible polynomial f(x) = x
4 + x + 1 using Equation (2), where matrix
A is invertible over GF(2), and
C could be a compatible constant number in GF(2
4). In this design, we set the constant
C to 616, which is equal to the vector 0110. Matrix A used in the current implementation is represented as follows:
where
A has an inverse over GF(2), given by:
The S-box table is constructed using
Table 4 and Equation (1). The entry of the S-box that corresponds to an input x is computed first by finding the inverse of x from
Table 4, then applying the affine transformation in Equation (1) to the output of
Table 4. This produces the S-box lookup shown in
Table 5.
Table 6 shows the Inv S-box lookup table used in the decrypting function. The entries of the Inv S-box table are computed after the multiplicative inverse is applied to the output of Equation (3).
Table 6 illustrates the entries for the Inv S-box over GF(2
4).
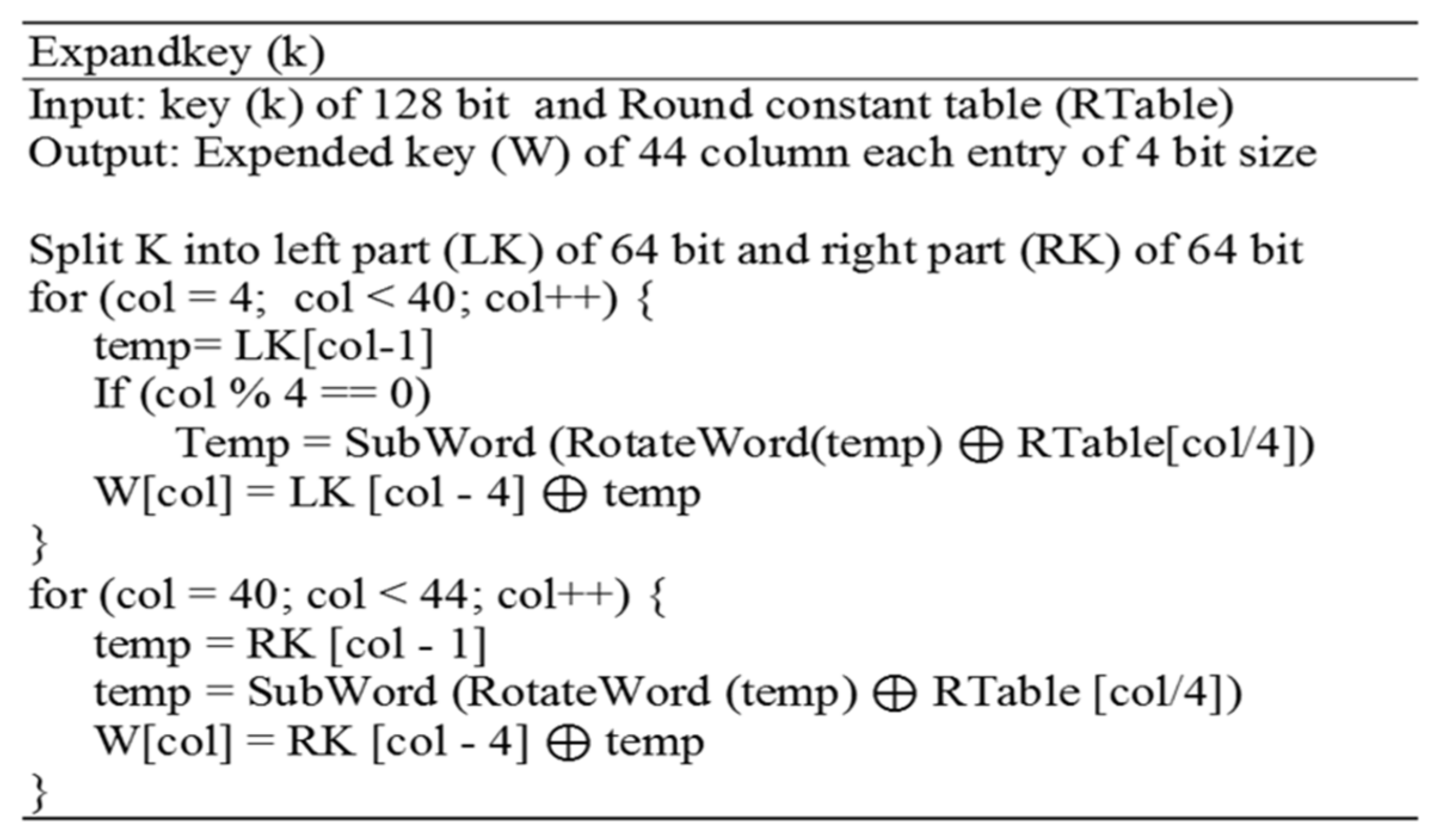
3.5. Key Expander
The 128-bit length of the LAES key keeps the design persistent in terms of the agent’s brute force attack, in comparison to the smaller key size used in previous studies [
32,
35]. The key is divided into two halves, each of which is a 64-bit 4 × 4 matrix. Each entry in the matrix consists of 4 bits, instead of the 8 bits in AES.
The key expander simply expands the left part of the key during each round until the ninth round of LAES is completed. The right part of the key is then expanded during the final round. The basic principles of AES key expansion were followed in the design of LAES [
38]:
The total number of round key bits is equal to the block length multiplied by the number of rounds, plus 1.
The key is expanded into an expanded key.
Round keys are taken from this expanded key.
The S-box lookup and the round constant tables are used during the expansion process of generating 36 new columns from the left part and 4 new columns from the right part. The S-box lookup and the round constant tables are used to minimize the correlation between the key parts, and to eliminate symmetricity and enhance the non-linearity of the expanded key, which affects the LAES diffusion property.
The left part of the key consists of 64 bits arranged into a 4 × 4 matrix, where each entry has 4 bits. The matrix is then expanded by joining 40 more columns. Considering that the initial values of key columns are
C (0),
C (1),
C (2), and
C (3), the new columns are defined as in Equation (4).
where
Tr(
C(
i − 1)) is the transformation of
C(
i − 1) obtained as follows. Let the elements of
C(
i − 1) have the values a, b, c, and d. Shift-left these elements cyclically to obtain
b,
c,
d, and
a, then replace each of these values with the corresponding element in the S-box lookup table, to obtain the values
e,
f,
g, and
h. Finally,
Tr(
C(
i − 1)) is the column vector that equals e ⊕
r(
i),
f,
g, and
h, in which
r(
i) is a round constant of the
ith round. In this way, columns
C(4) …
C(39) are generated from the initial four columns of the left part key. The final four columns generated (
C(40),
C(41),
C(42), and
C(43)) from the right part of the key are obtained using a similar algorithm.
Figure 3 illustrates the algorithm of key expansion in LAES.
3.7. Mix Column Permutation
The AES constant matrix was selected based on factors that provide the encryption and decryption process with less computation and higher diffusion power [
38]. These factors include the linearity over GF(2) and the invertibility of the constant matrix. The matrix should be invertible to perform the decryption process and support a quick handing process. As per AES, an entry of 0 or 1 requires no multiplication process [
38]. In LAES, the choice of the coefficients of C(x) are 3, 2, 1, and 0, which allows easier implementation for software and hardware multiplication process. Columns of the state matrix are considered as a polynomial over GF(2
4) modulo x
4 + x + 1, with a fixed polynomial C(x) = 3x
3 + 1x
2 + 1x + 2. Although the polynomial x
4 + x + 1 is not irreducible, the operation is invertible, since the polynomial C(x) is co-prime to x
4 + x + 1.
The coefficients of the polynomial C(x) and the polynomial of state column matrix are in themselves polynomials in GF(24). The inverse of C(x) is C-1 (x) = 9x3 + Ex2 + Bx + 4, which is needed to construct the matrix in the decryption process.
The 0th column of the constant matrix can be represented by s3,0x3 + s2,0x 2 + s1,0x + s0,0, where the coefficient 3 in C(x) is actually the polynomial x + 1 in GF(24), the coefficient 1 is the polynomial 1, and the coefficient 2 is the polynomial x in GF(24).
The multiplication by C(x) modulo x
4 + x + 1 can also be represented as a matrix transformation. For example, if we take the 0th column, which has four elements (s0,0, s1, 0, s2, 0, s3, 0), the mix columns component produces the 0th column of the result (s’0,0, s’1, 0, s’2, 0, s’3, 0), in the manner seen below. Similarly, the operation is repeated for the other columns.
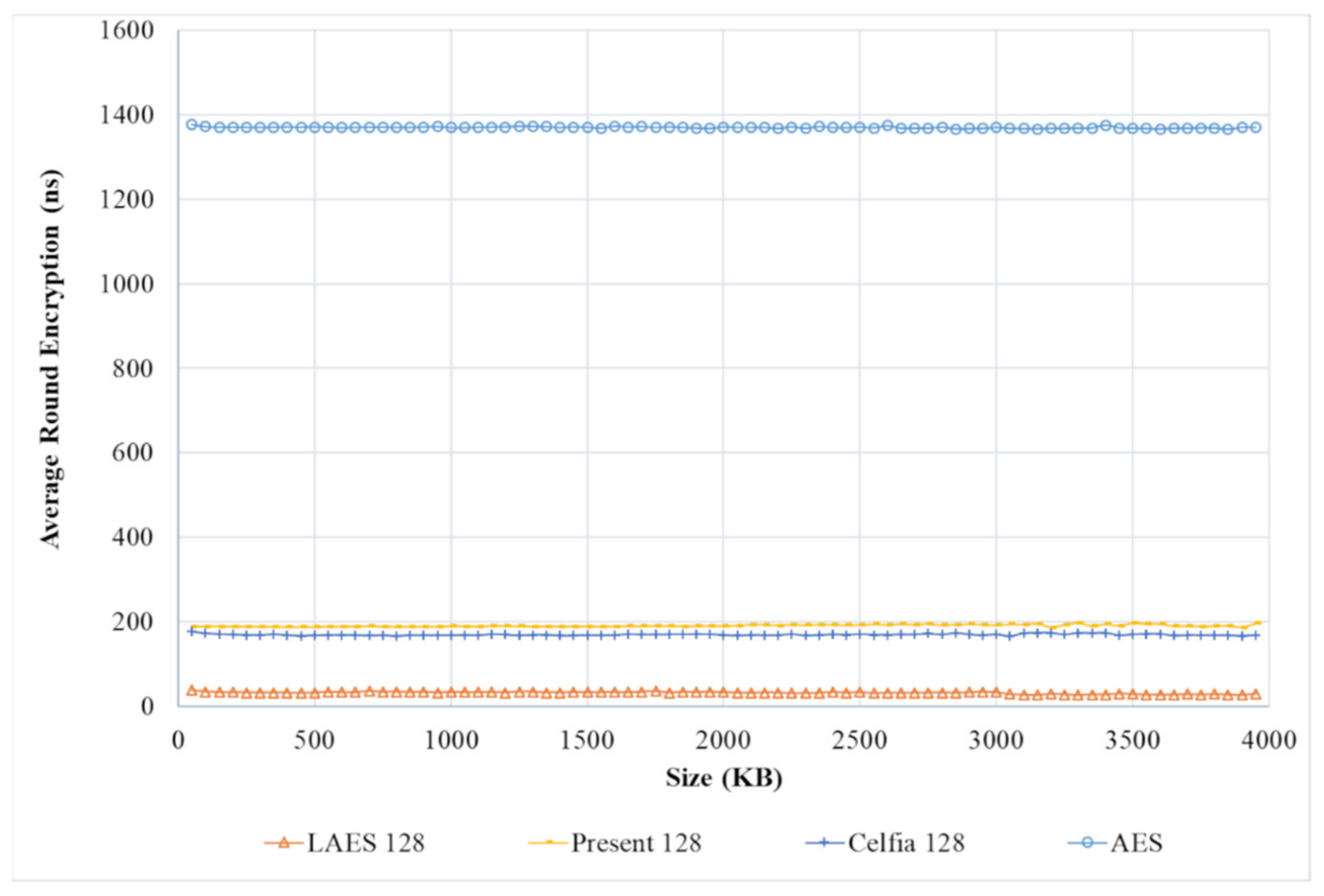
3.8. Encryption Process in LAES
The main transformations components of LAES encryption rounds are mainly inherited from the original AES; however, the AES encryption components operate on GF (28), while the LAES encryption components operate on GF(24). This means that the components of the LAES operate by following the same logical operations of the AES, but the entries of each component are completely different, and operate on a smaller scale. For example, the S-box in the AES is a lookup table of 256 entries, while the S-box of the LAES is a lookup table of 16 entries. The input to the encryption process is a block of 64 bits, and it is reshaped into 4 × 4 matrix. This matrix is called a state matrix, which is modified based on the encryption rounds until the 10th round of the encryption is completed. The first nine rounds of LAES consist of four transformation components: LSubNibble, LShiftRows, LMixColumns, and LAddRoundKey. The final round of LAES contains only three transformations components, similar to the AES, which are LSubNibble, LShiftRows, and LAddRoundKey, as described below.
LSubNibble: This component is used to perform the simple transformation of the state matrix bits into another matrix based on the S-box lookup table (see
Table 5). For example, the state matrix entry of 0 will be transferred into 6. Different bits of the state matrix are transformed into different bits from the S-box lookup table. The S-box is intended to provide an invertible transformation of the state matrix entries during this component, which is inverted by the LInvSubNibble in the decryption process by the entries of the Inv S-box (see
Table 6). In AES, the S-box is a 16 × 16 matrix covering a total of 256 bytes, represented in hexadecimal, and indexed in a column and row pattern. The work in [
45] indicated that the SubBytes component in AES has an egregious processing time and power consumption, and the use of smaller lookup tables with sizes ranging from 16 to 128 bytes has become more reliable for obtaining higher speeds to meet the needs of different lightweight applications, such as smartphone applications, sensor networks, smart cards, and RFID. In LAES, the S-box and the Inv S-box are reduced into 16 nibbles, indexed from 1 to 16, which is expected to improve the processing speed of LAES and provide the required confusion for lightweight applications.
LShiftRows: This component operates similar to the ShiftRows in AES, by shifting the entries of each row of the state matrix cyclically. The LShiftRows operates on a state matrix of 64 bits. The shift is made by certain offsets of 0, 1, 2, and 3 for rows 1 to 4 of the state matrix, respectively. The objective of this component is to avoid the columns of the state matrix form being linearly independent, and to enhance the overall diffusion of the encryption process. For the decryption process, the LInvShiftRows component cyclically shifts the rows of the state matrix to the right by certain offsets of 0, 1, 2, and 3 for rows 1 to 4 of the state matrix, respectively.
LMixColumns: In this component, the state matrix obtained from the LSubNibble is diffused to provide a further level of diffusion following the operation performed by LShiftRows component. The LMixColumns performs permutation at the column level of the state matrix, which provides another level of diffusion over the LShiftRows component.
The LMixColumns transformation is computed as illustrated in Equation (5), where S’ is the new state matrix, P is the polynomial coefficient, and S is the current state matrix.
This transformation can be defined by the polynomial coefficient matrix multiplication on the state matrix as follows:
The inverse mix column transformation, called LInvMixColumns, is defined by the following matrix multiplication:
LAddRoundKey: This component XORs the state matrix and the round key. The LAddRoundKey is a simple transformation that affects every bit of the state matrix. LAddRoundKey and the other LAES components provide the required level of confusion and diffusion. The InvLAddRoundKey is the component that performs the inverse of LAddRoundKey transformation. The decryption process is the reverse of the transformation components of the encryption process. The input to the decryption process is the ciphertext processed by the invertible components.