Performance Model for Video Service in 5G Networks
Abstract
1. Introduction
Contribution
- Our proposed approach targets improvement in performance models that map high-level customer-friendly business requirements to low-level network parameters and achieve QoS assurance for delay-sensitive traffic.
- The data analytics and ML approach is employed to construct the QoS performance model for network design and optimization, to identify the relationships and dependencies between SLA high-level requirements and low-level network attributes.
2. Problem Description
3. Approaches
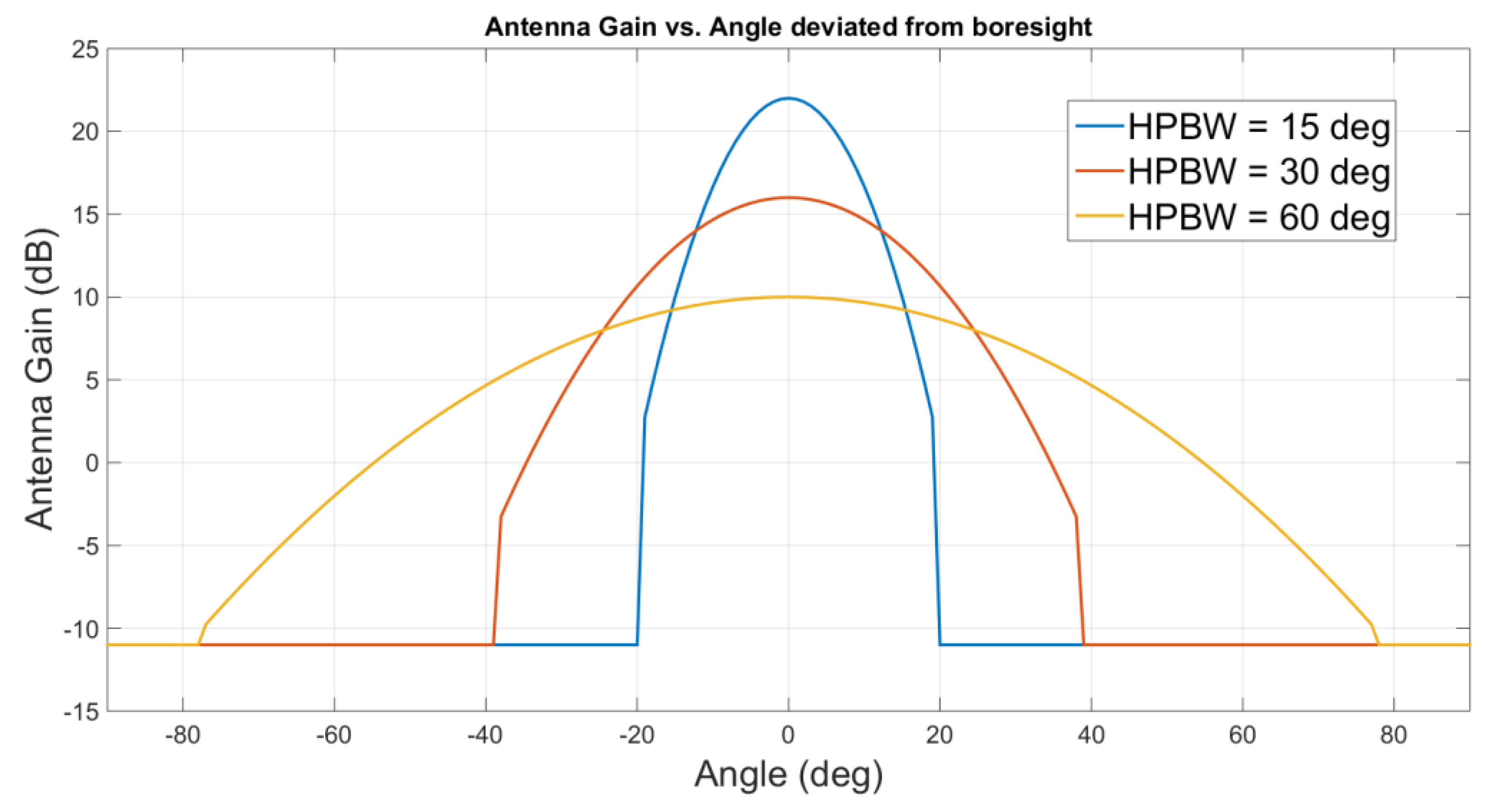
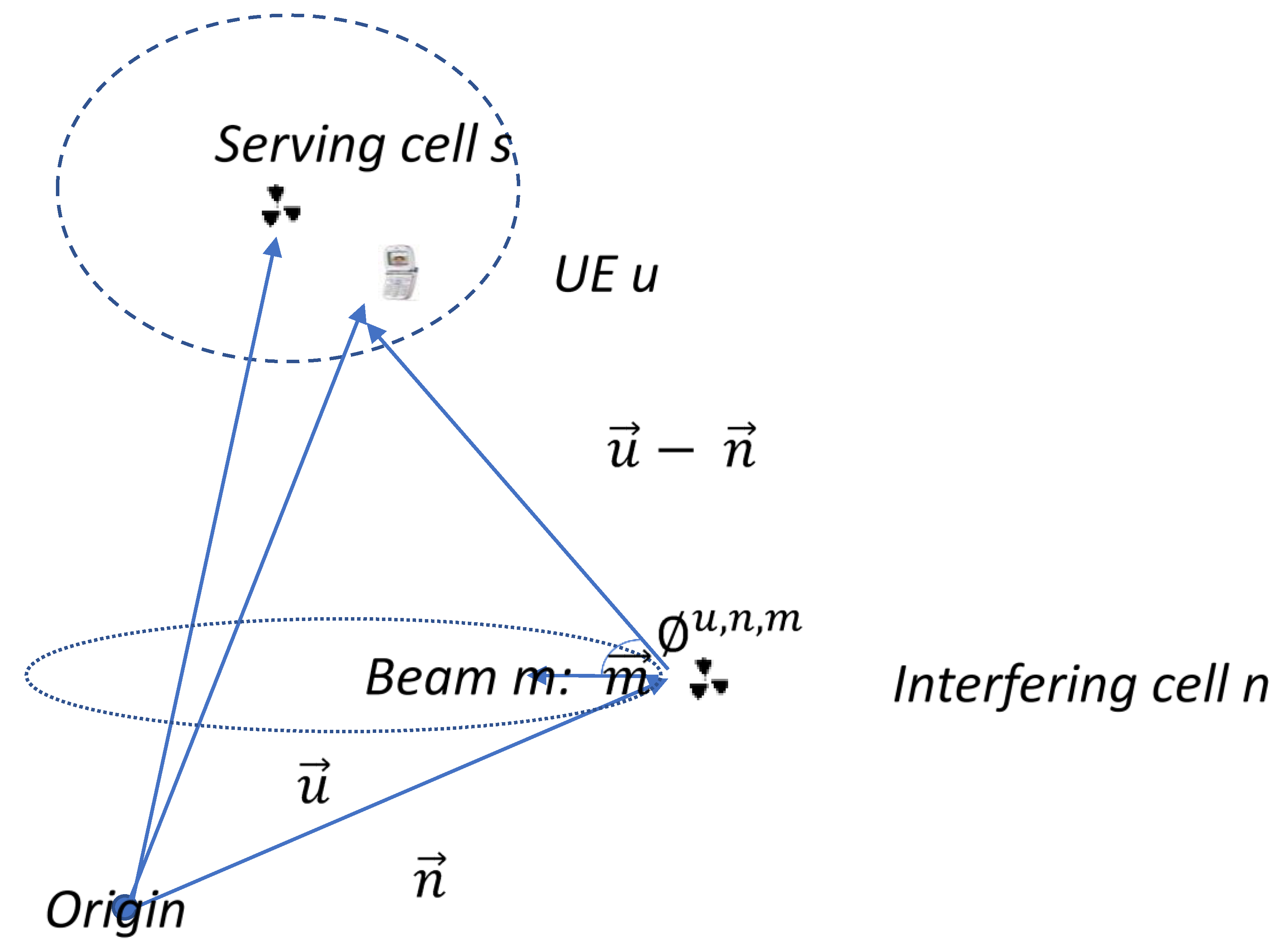
3.1. Interference Coordination Approach
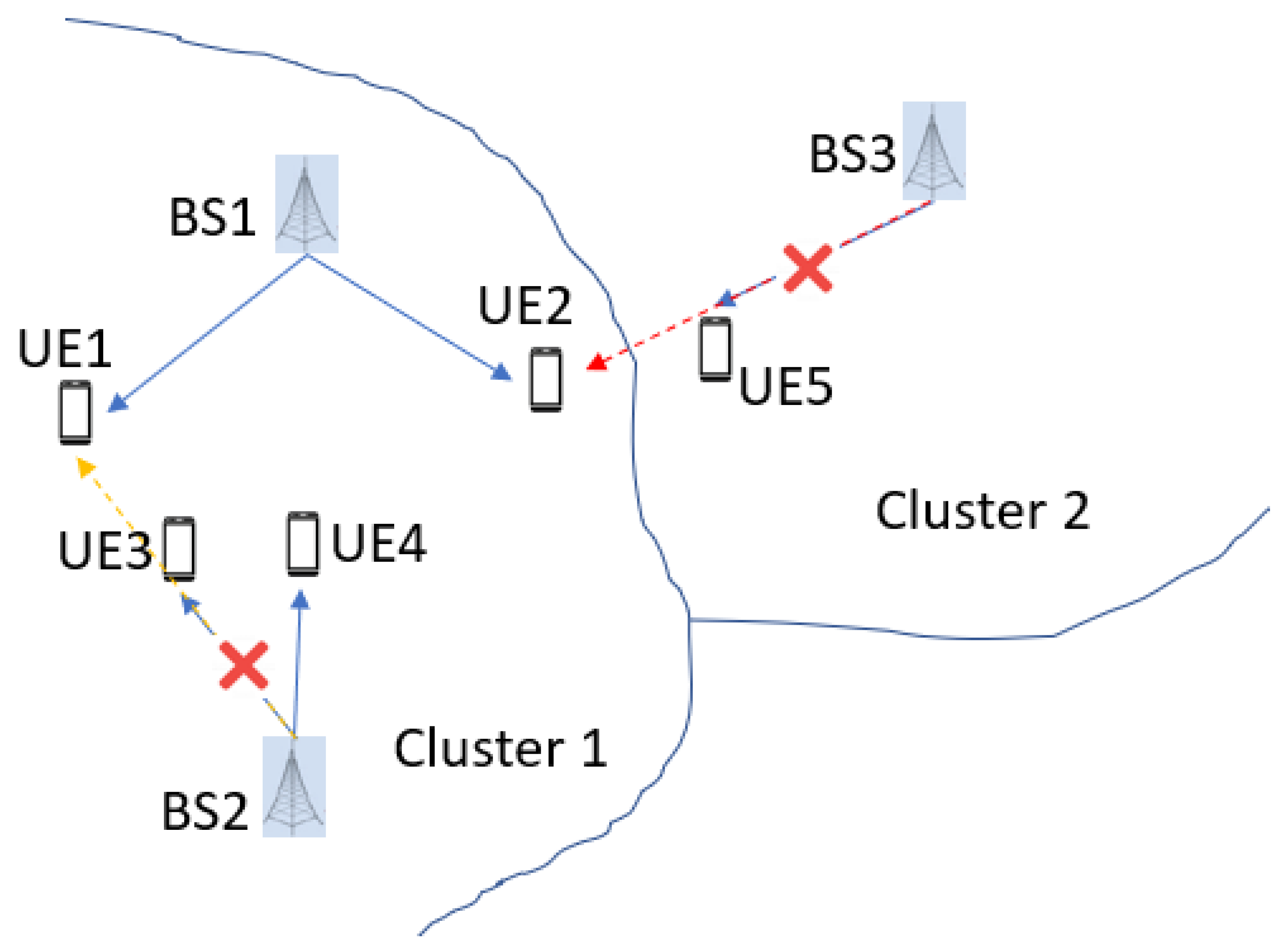
3.1.1. Network Clustering
3.1.2. Intra-cluster Interference Graph Construction
3.1.3. Interference Coordination
| Algorithm 1 Intra-cluster scheduling algorithm |
| For each cluster c Scheduled UE at this intra-cluster coordination period: U Initialization: Scheduled UE at this TTI and this sub-band: Randomly select cell c1 from cluster c Randomly select UE u from cell c1 If u U , ; End if Execution: For all cell c1 from cluster c For all UE u in cell c1 If u U && size () < IC-P1: IC-P2: End if End For End For IC-P1: ; IC-P2: if < ; End if |
| End For |
| Algorithm 2 Inter-cluster scheduling algorithm |
| For the network n Scheduled UE at this TTI and sub-band: U Execution: For all cell c1 from cluster c in network n For all UE u in cell c1 If u U and < Sort ; For all UE u1 U & u1 IC-P2: Remove u1 from U Re-calculate If ! < Break Loop; End if IC-P1: If Remove u1 from U End if End For End if End For End For |
| End For |
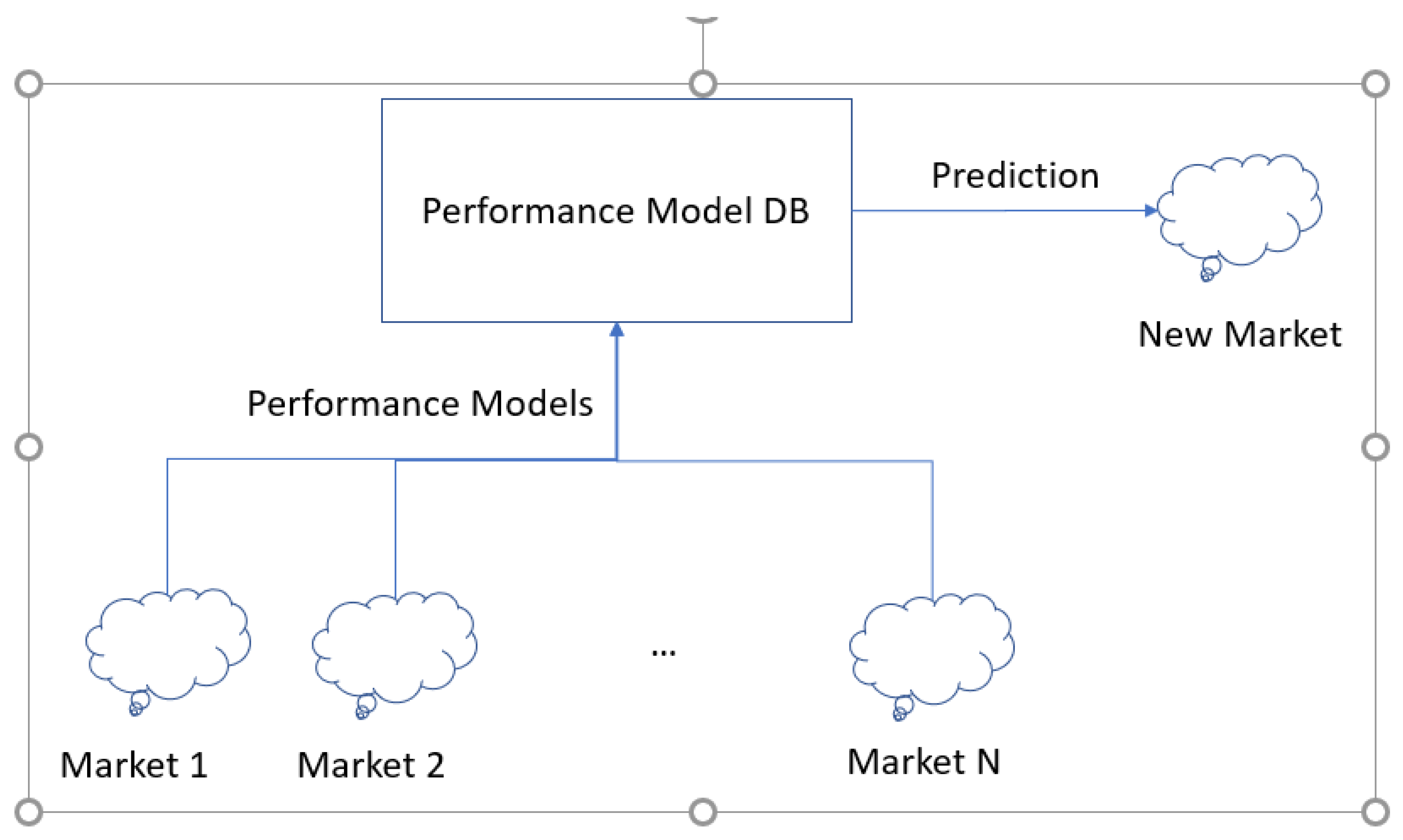
3.2. Network Design Approach
| Algorithm 3 Performance model construction |
| For service s, number of UE u, number of beams b, and ISD isd, the average UE distance to serving cell dis, and traffic demand variance varT Initial with small Bandwidth: loop: With picked IC, calculate QoS (s, u, b, isd, ): For all cell j from cluster i in network n For all UE k in cell j If QoS (k) Valid(k) = true; End if End For End For while TotalValidUE < UETHRESHOLD * = 2; deltaW = ; Go to loop Else = − deltaW; Break; Iteration = N; For I = 1:N If TotalValidUE < UETHRESHOLD deltaW = deltaW/2; Else = End If With picked IC, calculate QoS (s, u, b, isd, ) End For |
| End For |
| Algorithm 4 Service mapping |
| For total bandwidth W Initial with ISD: loop: Calculate users per site for each service s Calculate the bandwidth per service using the performance model Sum up bandwidth w = If w < W save and ; = + delta; go to loop Else return saved and of previous iteration End If |
| End For |
3.3. Network Optimization Approach
| Algorithm 5 Network optimization |
| For service s, UE number u, beam number b, and ISD isd, Initial with design bandwidth: search database with (s, u, b, isd, Var(u), Var(s)) maxBW = max(BW(s, u, b, isd, Var(u), Var(s)) minBW = min(BW(s, u, b, isd, Var(u), Var(s)) Iteration = N; Calculate QoS (s, u, b, isd, ) If TotalValidUE < UETHRESHOLD While(true) deltaW = (maxBW − minBW)/N; deltaW Calculate QoS (s, u, b, isd, ) If TotalValidUE > UETHRESHOLD Break; Add new to database EndIf else While(true) deltaW = (maxBW −s minBW)/N; deltaW Calculate QoS (s, u, b, isd, ) If TotalValidUE < UETHRESHOLD Break; Roll back to previous End If End For End If |
| End For |
4. Simulation Methodology
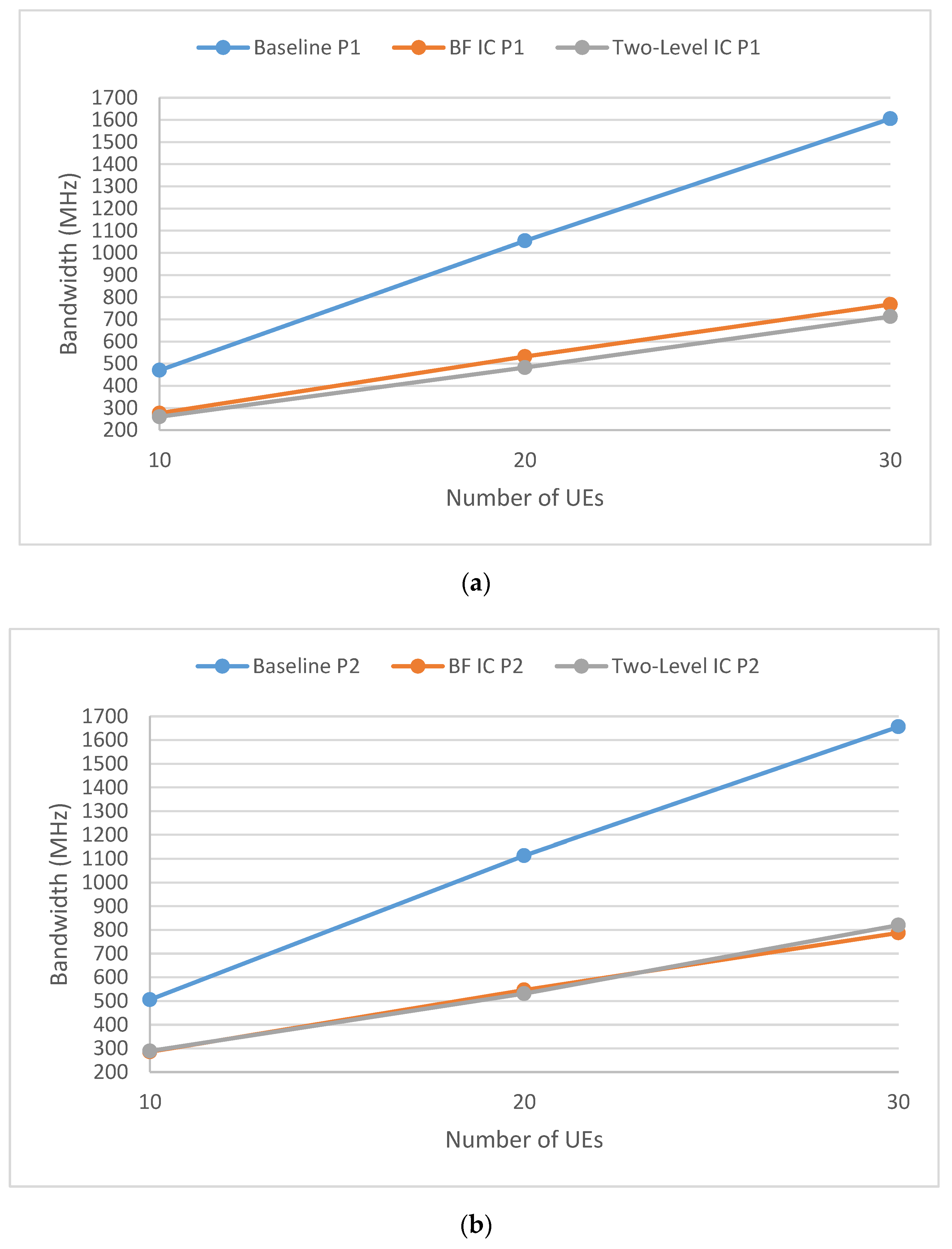
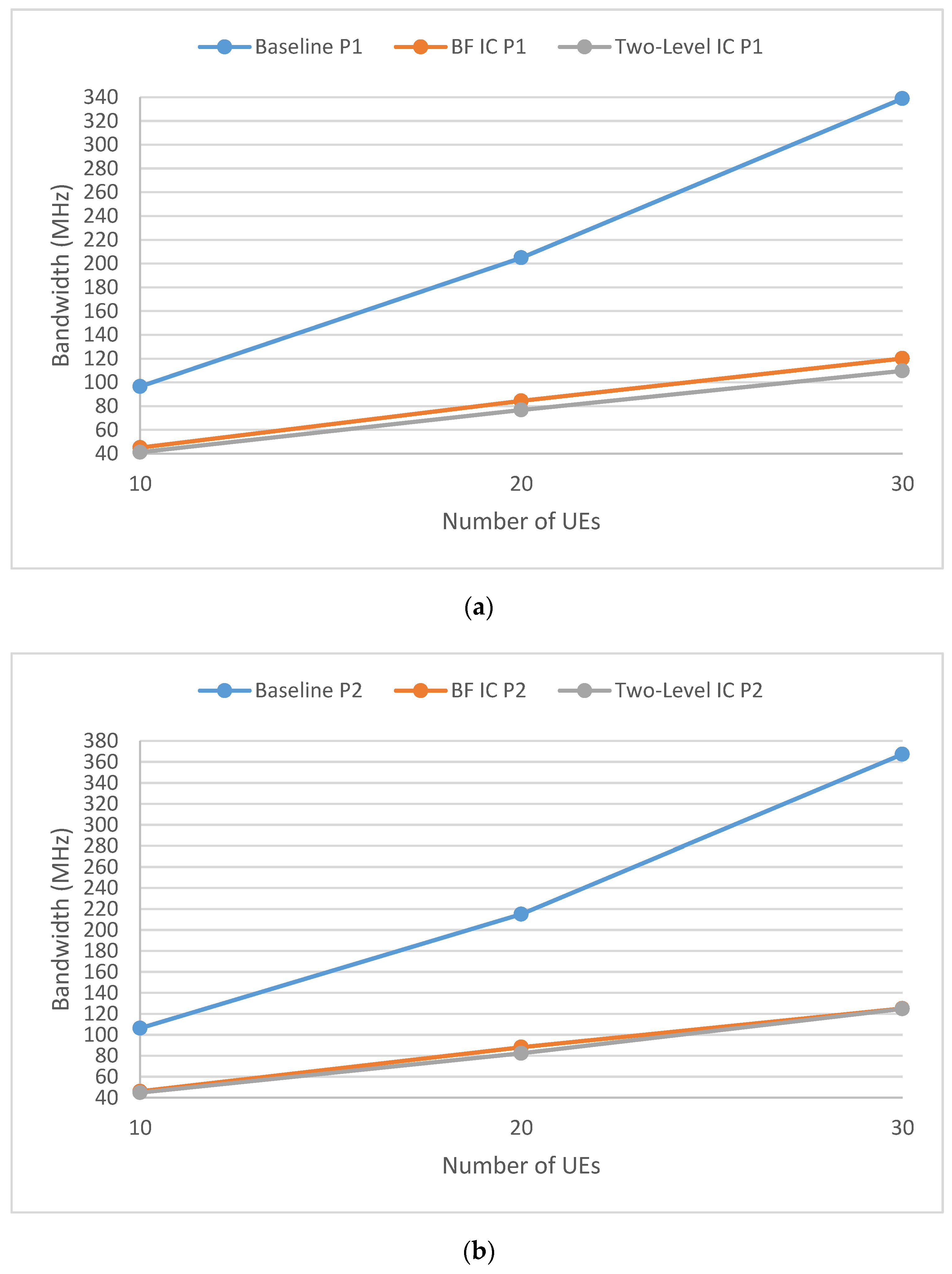
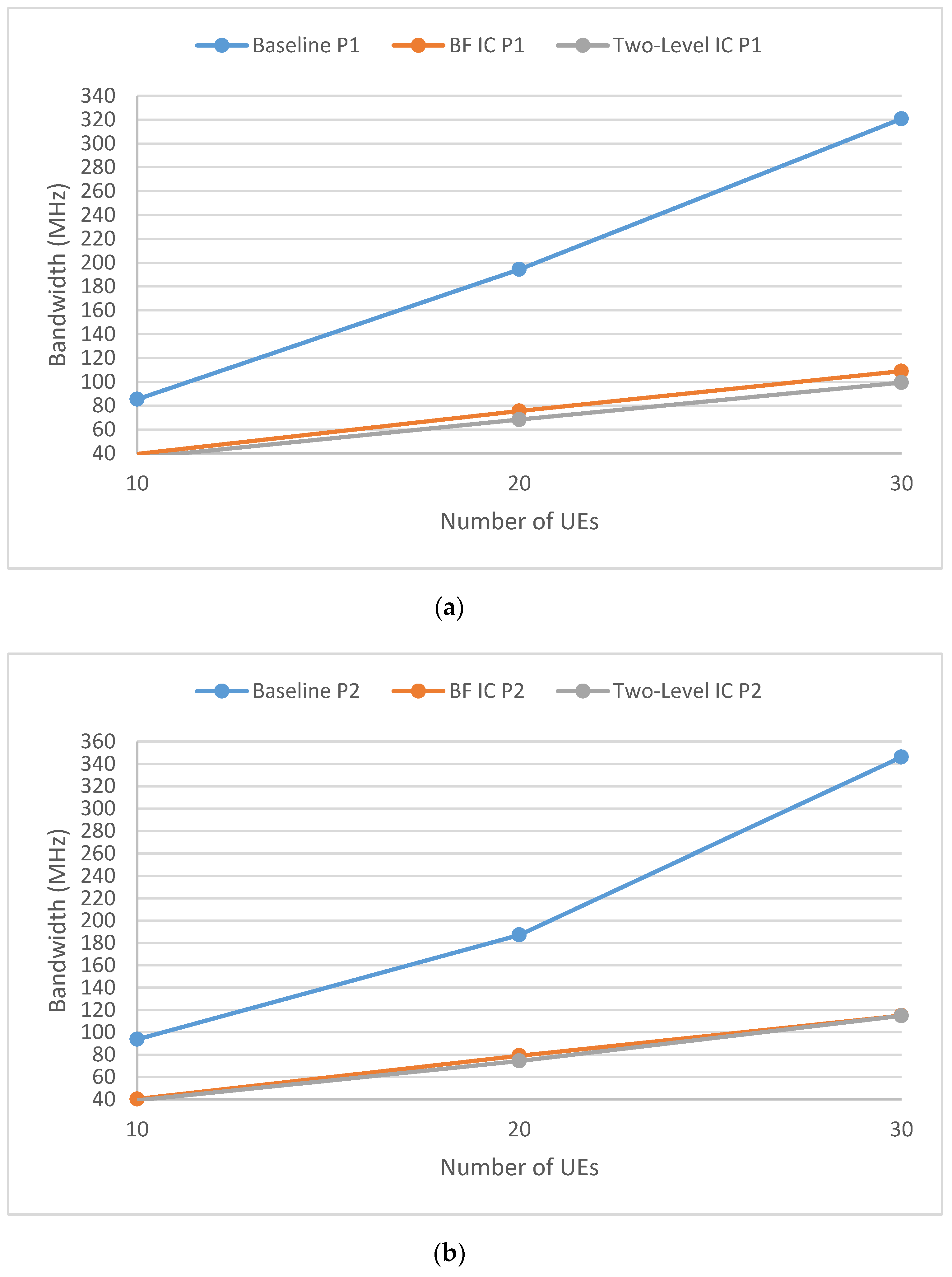
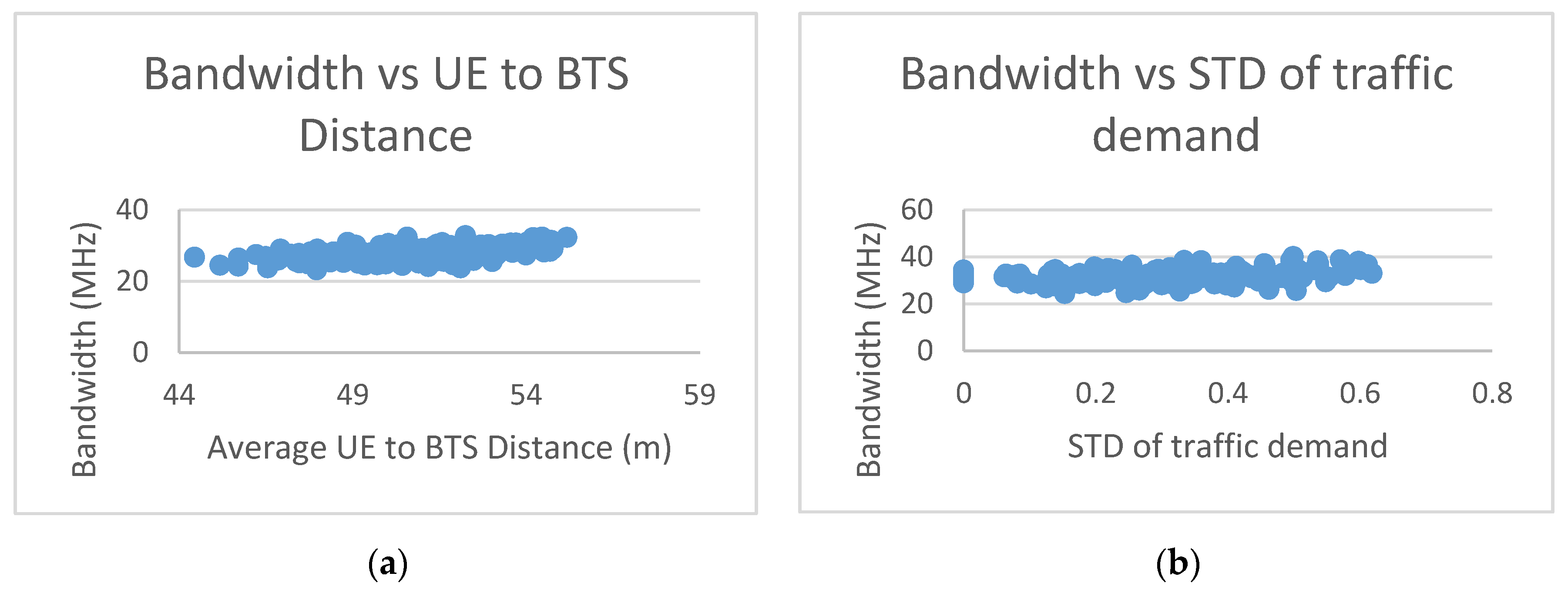
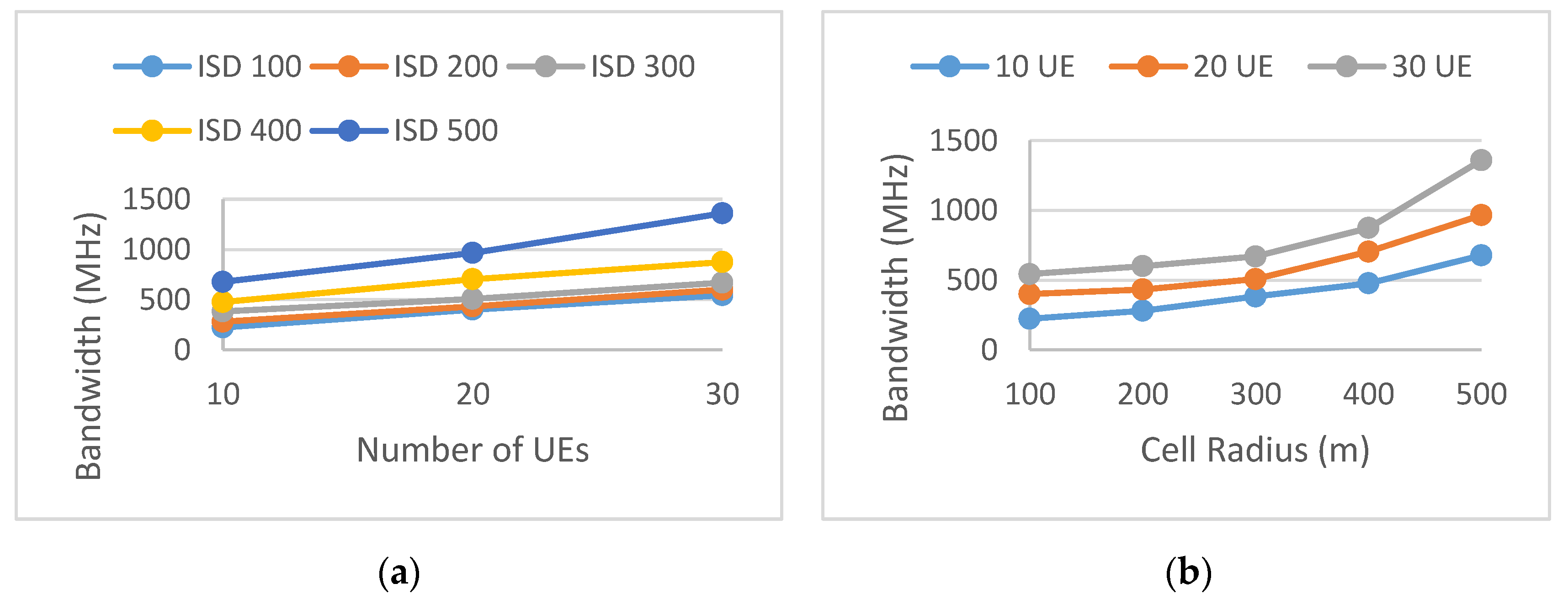
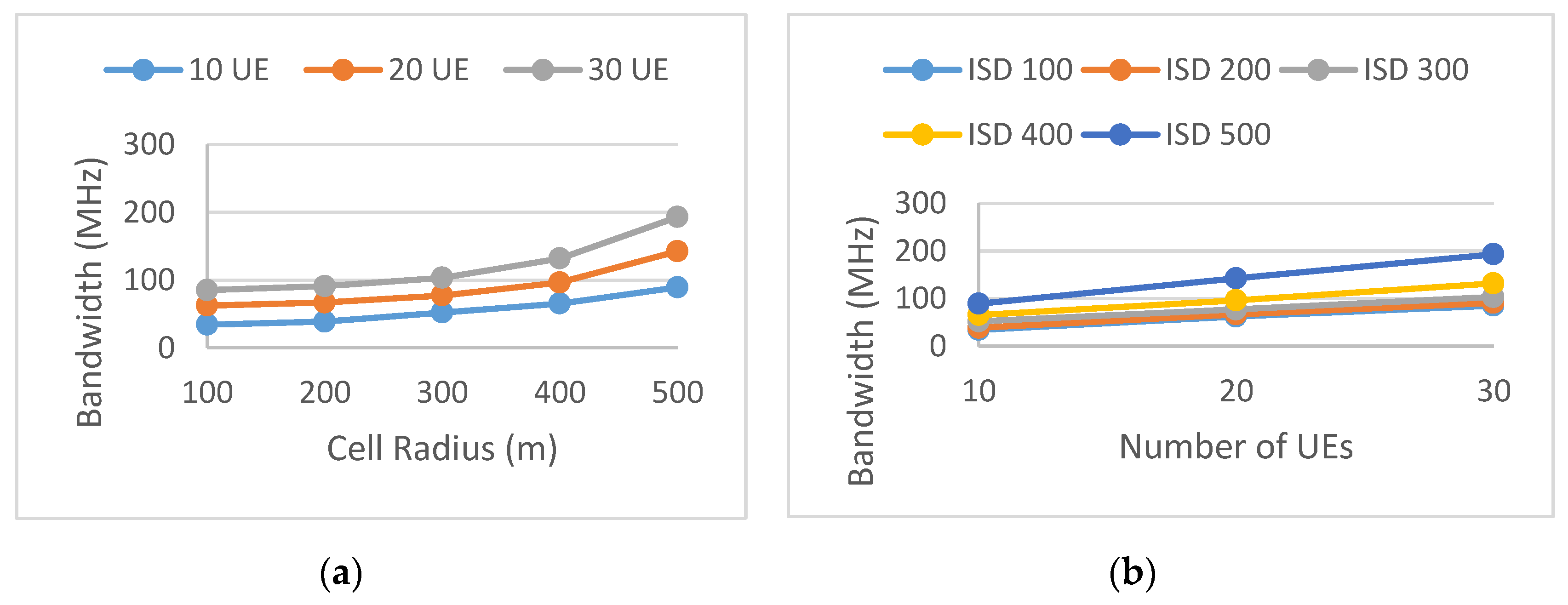
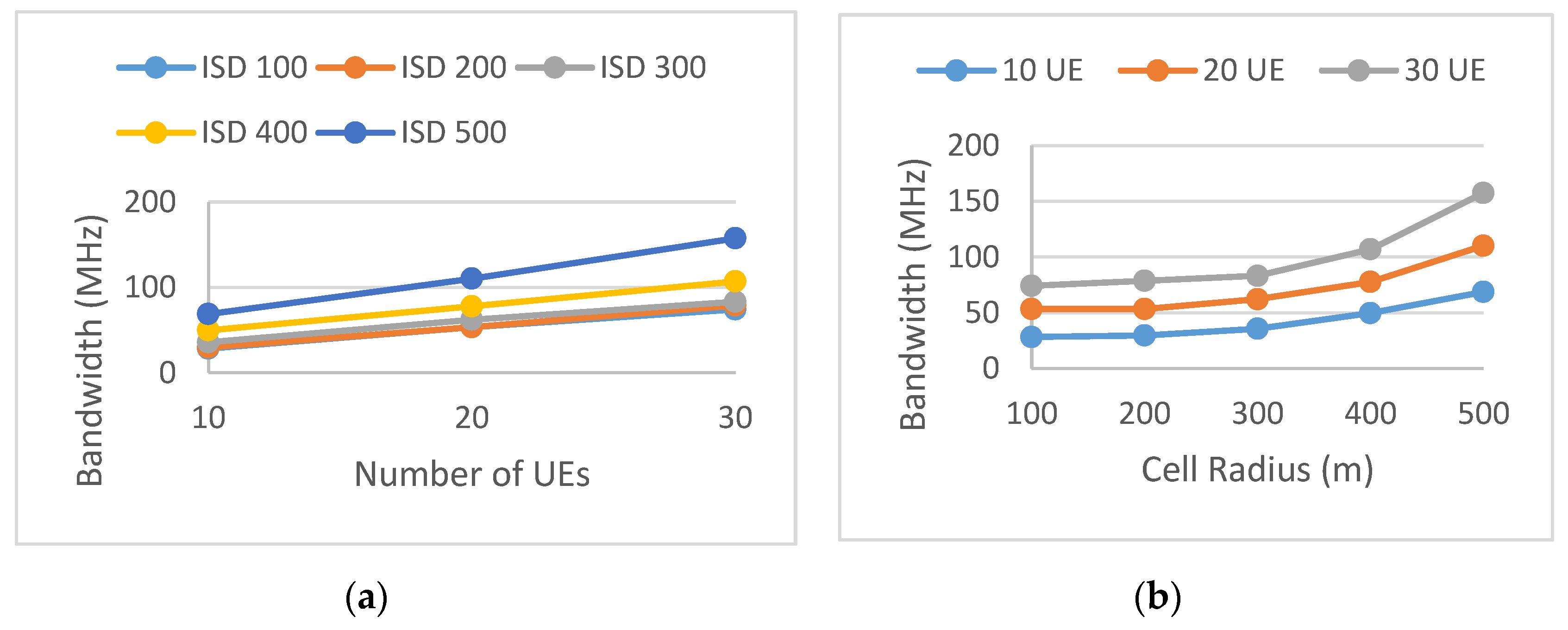
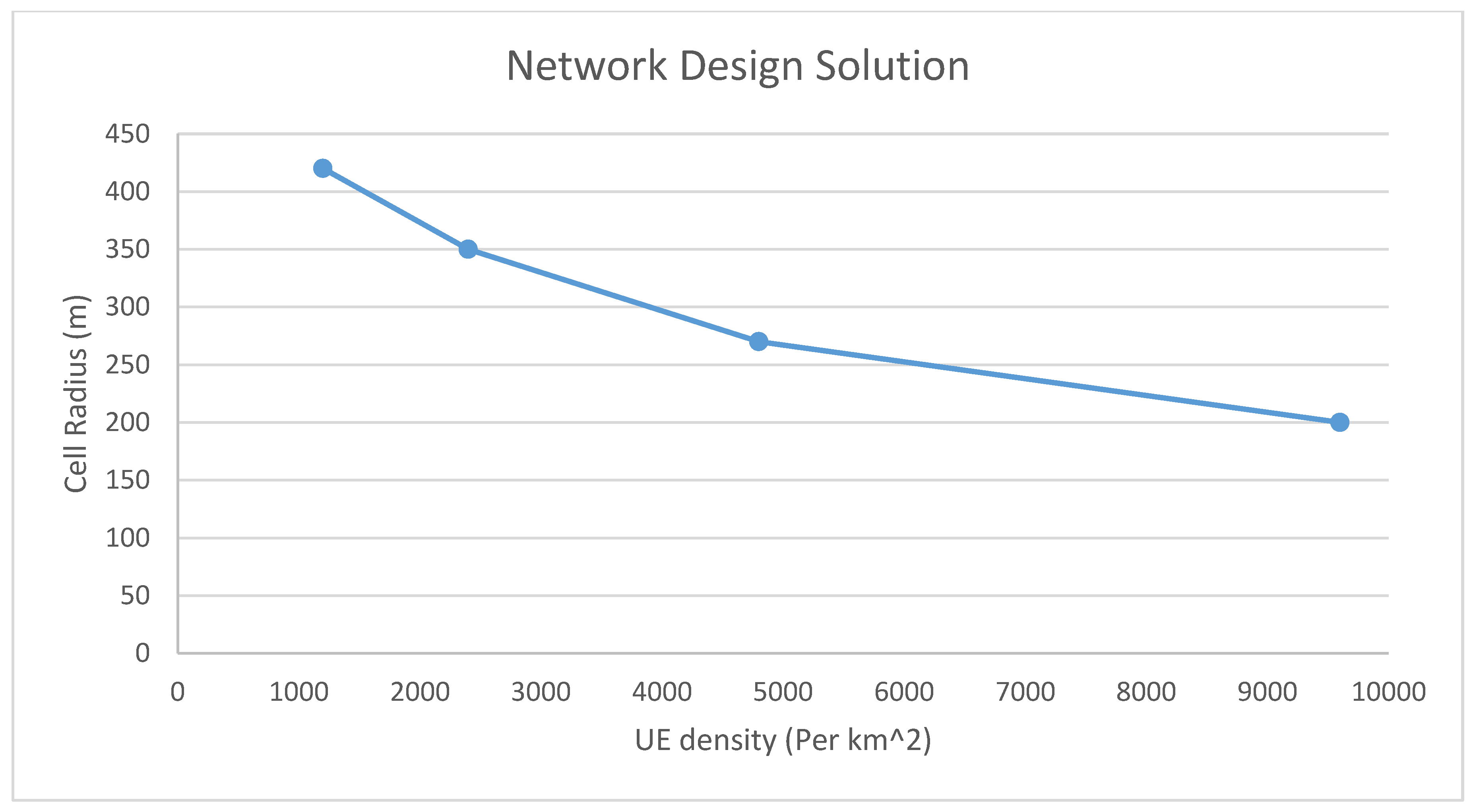
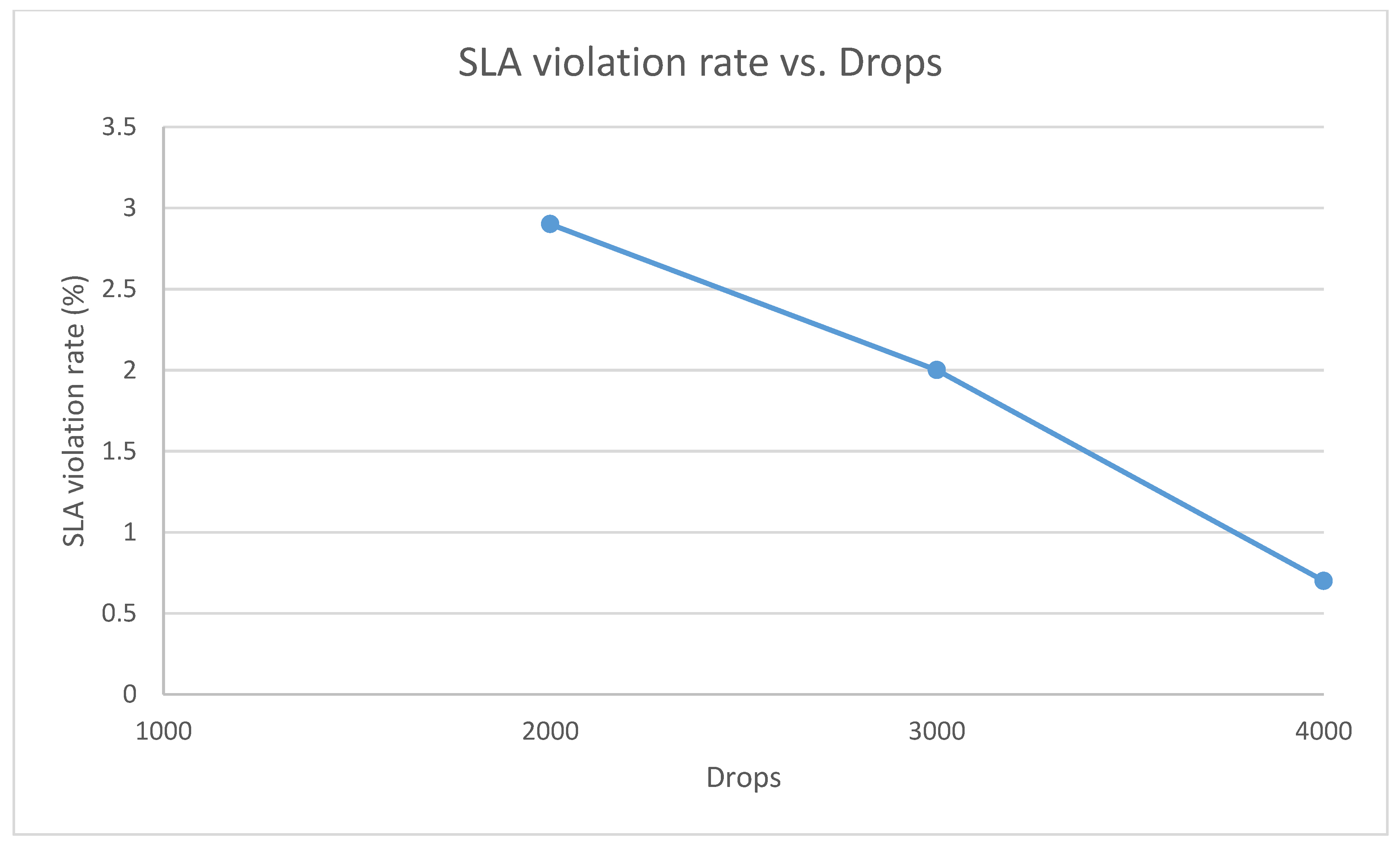
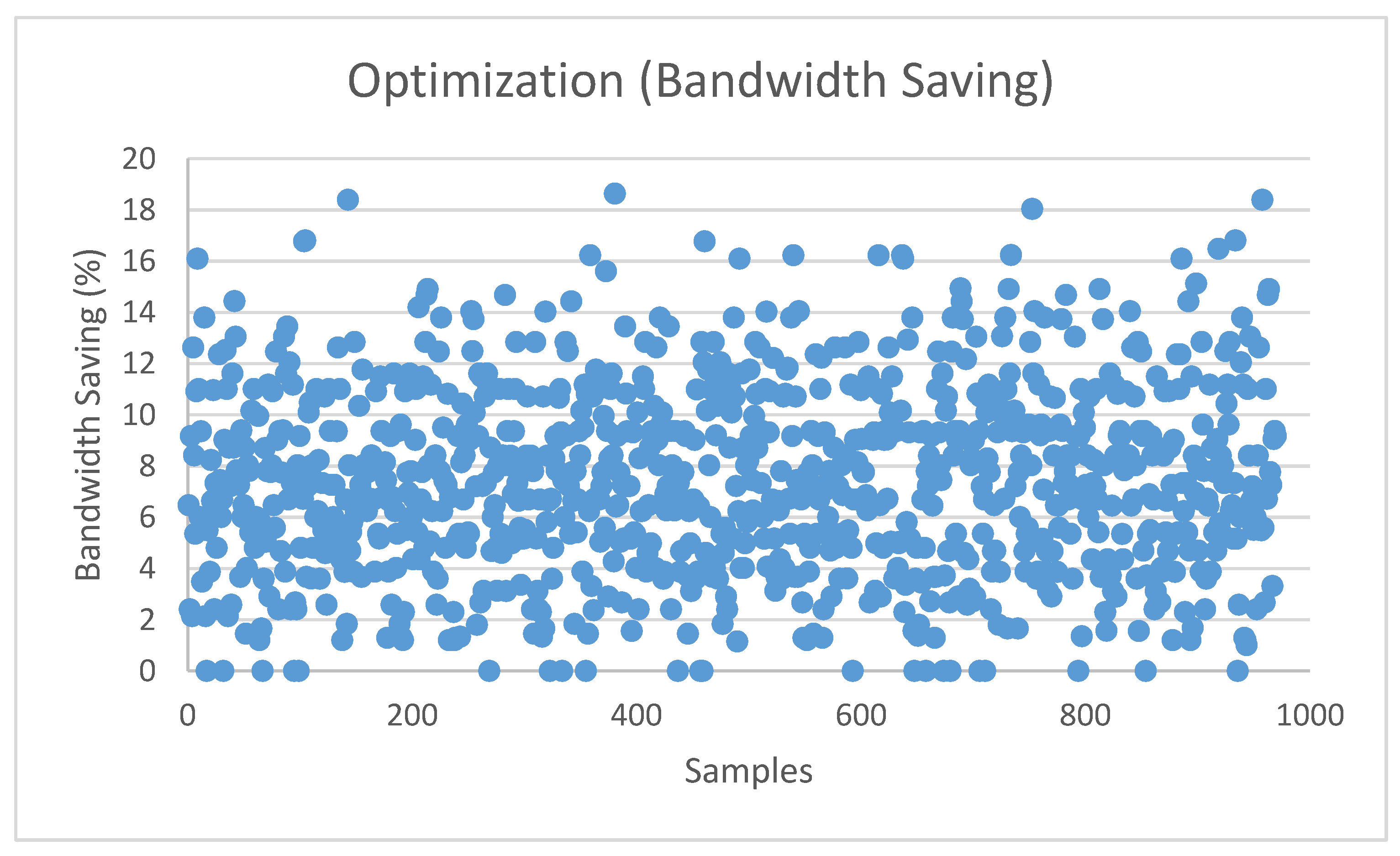
5. Simulation Results
6. Complexity Analysis
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Li, R.-P.; Zhao, Z.; Sun, Q.; Chih-Lin, I.; Yang, C.; Chen, X.; Zhao, M.; Zhang, H. Deep Reinforcement Learning for Resource Management in Network Slicing. IEEE Access 2018, 6, 74429–74441. [Google Scholar] [CrossRef]
- Kapassa, E.; Touloupou, M.; Kyriazis, D. SLAs in 5G: A Complete Framework Facilitating VNF- and NS- Tailored SLAs Management. In Proceedings of the 2018 32nd International Conference on Advanced Information Networking and Applications Workshops (WAINA), Krakow, Poland, 16–18 May 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA; pp. 469–474. [Google Scholar] [CrossRef]
- Kwan, R.; Leung, C. A Survey of Scheduling and Interference Mitigation in LTE. J. Electr. Comput. Eng. 2010, 2010, 1–10. [Google Scholar] [CrossRef]
- Elayoubi, S.-E.; Ben Haddada, O.; Fourestie, B. Performance evaluation of frequency planning schemes in OFDMA-based networks. IEEE Trans. Wirel. Commun. 2008, 7, 1623–1633. [Google Scholar] [CrossRef]
- Garcia-Morales, J.; Femenias, G.; Riera-Palou, F. Higher Order Sectorization in FFR-Aided OFDMA Cellular Networks: Spectral- and Energy-Efficiency. IEEE Access 2019, 7, 11127–11139. [Google Scholar] [CrossRef]
- Fan, X.; Chen, S.; Zhang, X.; Xiangning, F.; Si, C.; Xiaodong, Z. An Inter-Cell Interference Coordination Technique Based on Users’ Ratio and Multi-Level Frequency Allocations. In Proceedings of the 2007 International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM ’07), Shanghai, China, 21–25 September 2007; pp. 799–802. [Google Scholar]
- Al-Falahy, N.; Alani, O.Y. Network Capacity Optimisation in Millimetre Wave Band Using Fractional Frequency Reuse. IEEE Access 2017, 6, 10924–10932. [Google Scholar] [CrossRef]
- Pastor-Perez, J.; Riera-Palou, F.; Femenias, G. Clustering and subband allocation for CoMP-based MIMO-OFDMA networks with soft frequency reuse. In Proceedings of the European Wireless 2017; 23th European Wireless Conference, Dresden, Germany, 17–19 May 2017; pp. 1–8. [Google Scholar]
- Attia, E.S.; El-Dolil, S.A.; Abd-Elnaby, M. Performance enhancement based resource allocation scheme using soft frequency reuse for LTE femtocell networks. In Proceedings of the 2017 34th National Radio Science Conference (NRSC), Alexandria, Egypt, 13–16 March 2017; pp. 246–255. [Google Scholar] [CrossRef]
- Novlan, T.; Andrews, J.G.; Sohn, I.; Ganti, R.K.; Ghosh, A. Comparison of Fractional Frequency Reuse Approaches in the OFDMA Cellular Downlink. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010; pp. 1–5. [Google Scholar]
- Adejo, A.; Boussakta, S.; Neasham, J. Interference modelling for soft frequency reuse in irregular heterogeneous cellular networks. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 381–386. [Google Scholar] [CrossRef]
- Lindbom, L.; Love, R.; Krishnamurthy, S.; Yao, C.; Miki, N.; Chandrasekhar, V. Enhanced Inter-Cell Interference Coordination for Heterogeneous Networks in Lte-Advanced: A Survey; Cornell University Library: Ithaca, NY, USA, December 2011. [Google Scholar]
- Ramli, H.A.M.; Asnawi, A.L.; Isa, F.N.M.; Azman, A.W. A survey of component carrier selection algorithms for carrier aggregation in long term evolution-advanced. In Proceedings of the 2017 IEEE 4th International Conference on Smart Instrumentation, Measurement and Application (ICSIMA); Institute of Electrical and Electronics Engineers (IEEE), Putrajaya, Malaysia, 28–30 November 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Deb, S.; Monogioudis, P.; Miernik, J.; Seymour, J.P. Algorithms for Enhanced Inter-Cell Interference Coordination (eICIC) in LTE HetNets. IEEE/ACM Trans. Netw. 2013, 22, 137–150. [Google Scholar] [CrossRef]
- Ali, S. An Overview on Interference Management in 3GPP LTE-Advanced Heterogeneous Networks. Int. J. Futur. Gener. Commun. Netw. 2015, 8, 55–68. [Google Scholar] [CrossRef]
- Luo, H.; Ni, Q.; Zhang, Y.; Huang, L.-K.; Cosmas, J.; Li, W. CRS interference cancellation algorithm for heterogeneous network. Electron. Lett. 2016, 52, 77–79. [Google Scholar] [CrossRef]
- Qu, D.; Zhou, Y.; Tian, L.; Shi, J. User-Centric QoS-Aware Interference Coordination for Ultra Dense Cellular Networks. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA; pp. 1–6. [Google Scholar] [CrossRef]
- Chang, Y.-J.; Tao, Z.; Zhang, J.; Kuo, C.-C.J. A Graph-Based Approach to Multi-Cell OFDMA Downlink Resource Allocation. In Proceedings of the IEEE GLOBECOM 2008—2008 IEEE Global Telecommunications Conference, New Orleans, LO, USA, 30 November–4 December 2008; pp. 1–6. [Google Scholar]
- Chang, R.Y.; Tao, Z.; Zhang, J.; Kuo, C.-C. A Graph Approach to Dynamic Fractional Frequency Reuse (FFR) in Multi-Cell OFDMA Networks. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–6. [Google Scholar]
- Zhang, C.; Varma, V.; Lasaulce, S.; Visoz, R. Interference Coordination via Power Domain Channel Estimation. IEEE Trans. Wirel. Commun. 2017, 16, 6779–6794. [Google Scholar] [CrossRef]
- Rahman, M. Dynamic Inter-Cell Interference Coordination in Cellular OFDMA Networks. Ph.D. Thesis, Department of System and Computer Engineering, Queens University, Kingston, ON, Canada, July 2011; pp. 1–117. [Google Scholar]
- Rahman, M.; Yanikomeroglu, H.; Wong, W. Interference Avoidance with Dynamic Inter-Cell Coordination for Downlink LTE System. In Proceedings of the 2009 IEEE Wireless Communications and Networking Conference, Budapest, Hungary, 5–8 April 2009; pp. 1–6. [Google Scholar]
- Wang, J.; Weitzen, J.; Bayat, O.; Sevindik, V.; Li, M. Interference coordination for millimeter wave communications in 5G networks for performance optimization. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 46. [Google Scholar] [CrossRef]
- Wong, V.W.; Schober, R.; Ng, D.W.K.; Wang, L.-C. Key Technologies for 5G Wireless Systems; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Hoshino, K.; Mikami, M. Experimental Evaluation of Simple Precoding Technique for Multi-Cell Coordinated MU-MIMO. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar]
- Nguyen, D.H.N.; Le-Ngoc, T. Multiuser Downlink Beamforming in Multicell Wireless Systems: A Game Theoretical Approach. IEEE Trans. Signal Process. 2011, 59, 3326–3338. [Google Scholar] [CrossRef]
- Wang, J.; Zhu, H. Beam allocation and performance evaluation in switched-beam based massive MIMO systems. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 2387–2392. [Google Scholar]
- Maruta, K.; Ahn, C.-J. Uplink Interference Suppression by Semi-Blind Adaptive Array with Decision Feedback Channel Estimation on Multicell Massive MIMO Systems. IEEE Trans. Commun. 2018, 66, 6123–6134. [Google Scholar] [CrossRef]
- Niu, Y.; Li, Y.; Jin, D.; Su, L.; Vasilakos, A.V. A survey of millimeter wave communications (mmWave) for 5G: Opportunities and challenges. Wirel. Netw. 2015, 21, 2657–2676. [Google Scholar] [CrossRef]
- Tung, C.-Y.; Chen, C.-Y.; Wei, H.-Y. Next-Generation Directional mmWave MAC Time-Spatial Resource Allocation. In Proceedings of the 11th EAI International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness, Taipei, Taiwan, 19–20 August 2015; pp. 728–742. [Google Scholar]
- 3GPP. Technical Specification Group Radio Access Network, Channel model for frequency spectrum above 6 GHz. Available online: https://itectec.com/archive/3gpp-specification-tr-38-900/ (accessed on 6 June 2020).

| IC Approach | IntraCluster Level | InterCluster Level |
|---|---|---|
| Two level IC - P2 | IC-P2 | IC-P2 |
| Two level IC - P1 | IC-P1 | IC-P1 |
| UE | ServingCell | ConflictUE | ConflictBM | ConflictCell | ConflictUEUtil | ConflictUEOffUtil | ConflictUEOnUtil |
|---|---|---|---|---|---|---|---|
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, J.; Weitzen, J.; Bayat, O.; Sevindik, V.; Li, M. Performance Model for Video Service in 5G Networks. Future Internet 2020, 12, 99. https://doi.org/10.3390/fi12060099
Wang J, Weitzen J, Bayat O, Sevindik V, Li M. Performance Model for Video Service in 5G Networks. Future Internet. 2020; 12(6):99. https://doi.org/10.3390/fi12060099
Chicago/Turabian StyleWang, Jiao, Jay Weitzen, Oguz Bayat, Volkan Sevindik, and Mingzhe Li. 2020. "Performance Model for Video Service in 5G Networks" Future Internet 12, no. 6: 99. https://doi.org/10.3390/fi12060099
APA StyleWang, J., Weitzen, J., Bayat, O., Sevindik, V., & Li, M. (2020). Performance Model for Video Service in 5G Networks. Future Internet, 12(6), 99. https://doi.org/10.3390/fi12060099





