Vulnerability Assessment of Ubiquitous Cities Using the Analytic Hierarchy Process
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Limitations
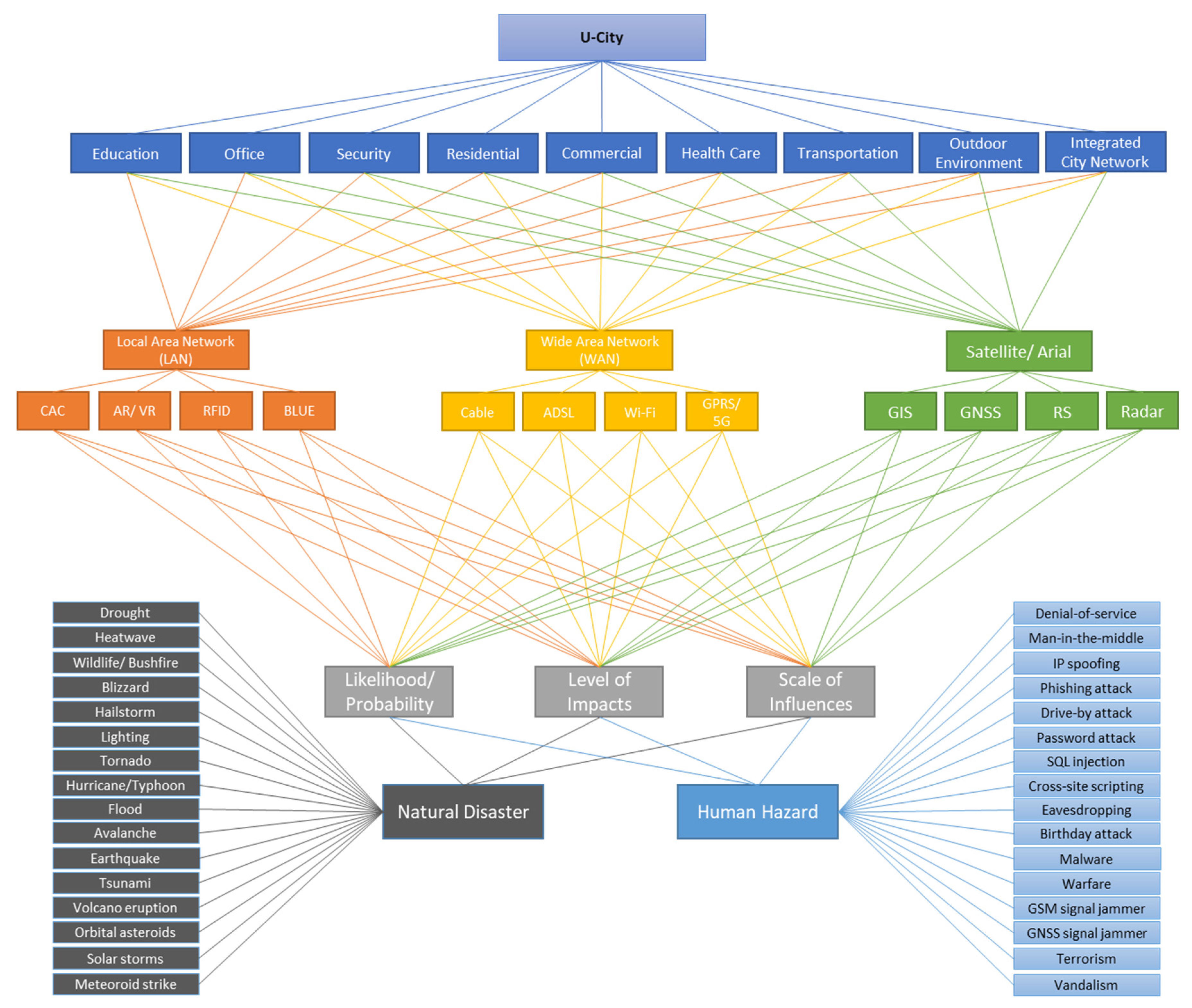
2. The Components of U-Cities and Hazards
2.1. Areas
2.2. Services
2.3. Information and Communication Technologies (ICTs)
2.3.1. Local Area Network (LAN)
2.3.2. Wide Area Network (WAN)
2.3.3. Satellite/Aerial Network
2.3.4. Internet of Things (IoT)
2.4. Hazards to a U-City
2.4.1. Man-Made Hazards
- Lesser crimes like stealing small devices
- Terrorist vandalism on facilities
- Sabotage infrastructures for wars efforts
2.4.2. Natural Hazards
3. Vulnerability Assessment of Cites
3.1. Development of the Framework
- Identify the service areas (performed in Section 2.2)
- Identify the associated ICTs (performed in Section 2.3)
- Identify natural and man-made hazards (performed in Section 2.4)
- Ranking, Likelihood, and area of influence of hazard using AHP (performed in Section 3.3)
- Overall vulnerability assessments of U-city (performed in Section 3.4)
3.2. Interconnectivity of Areas
3.3. Performance of a U-city under Hazards
3.3.1. Analytical Hierarchical Process (AHP)
3.3.2. The Impact of Disasters on ICTs
3.4. Overall Vulnerability Assessments of U-City
4. Conclusions & Recommendations
Author Contributions
Funding
Conflicts of Interest
References
- Management Association. Megacities and Rapid Urbanization; IGI Global: Hershey, PA, USA, 2019. [Google Scholar]
- Charles, A. World Economic Forum. 2017. Available online: https://www.weforum.org/agenda/2017/02/cities-must-tirelessly-innovative-to-respond-to-their-challenges/ (accessed on 10 July 2020).
- Abellá-García, A.; Ortiz- de-Urbina-Criado, M.; De-Pablos-Heredero, C. The Ecosystem of Services around Smart Cities: An Exploratory Analysis. Procedia Comput. Sci. 2015, 64, 1075–1080. [Google Scholar] [CrossRef] [Green Version]
- Garg, S. Impact of Overpopulation on Land Use Pattern. In Megacities and Rapid Urbanization; IGI Global: Hershey, PA, USA, 2019; pp. 1–19. [Google Scholar]
- Agudelo-Vera, C.M.; Mels, A.R.; Keesman, K.J.; Rijnaarts, H.H.M. Resource management as a key factor for sustainable urban planning. J. Environ. Manag. 2011, 92, 2295–2303. [Google Scholar] [CrossRef] [PubMed]
- Girardet, H. Cities, People, Planet: Urban Development and Climate Change; John Wiley & Sons Ltd.: Chichester, UK, 2008. [Google Scholar]
- Shin, D.-H. Ubiquitous City: Urban Technologies, Urban Infrastructure and Urban Informatics. J. Inf. Sci. 2009, 35, 515–526. [Google Scholar] [CrossRef]
- Jo, S.-S. An Analysis on the Evolutionary Characteristics of Ubiquitous City through Evolutionary Map of Ubiquitous City. J. Korean Assoc. Geogr. Inf. Stud. 2015, 18, 75–91. [Google Scholar] [CrossRef]
- Wong, S.W.; Tang, B.S.; van Horen, B. Strategic urban management in China: A case study of Guangzhou Development District. Habitat. Int. 2006, 30, 645–667. [Google Scholar] [CrossRef] [Green Version]
- The Free Library. Incheon FEZ Expects Upturn from Smart City Project. 2018. Available online: https://www.thefreelibrary.com/Incheon+FEZ+expects+upturn+from+Smart+City+project.-a0531750388 (accessed on 20 November 2019).
- Engin, Z.; van Dijk, J.; Lan, T.; Longley, P.A.; Treleaven, P.; Batty, M.; Penn, A. Data-driven urban management: Mapping the landscape. J. Urban Manag. 2019, 9, 140–150. [Google Scholar] [CrossRef]
- Poslad, S. Ubiquitous Computing: Smart Devices, Environments and Interactions; John Wiley & Sons Ltd.: Chichester, UK, 2009. [Google Scholar]
- Hwang, B.J.; Kim, B.S.; Lee, J.Y. Proposes on Essential Ubiquitous City Service to Guarantee Minimum Quality of Ubiquitous City. J. Korean Soc. Geospat. Inf. Syst. 2013, 21, 53–64. [Google Scholar]
- Zhu, W.; Panteli, M.; Milanovic, J.V. Reliability and Vulnerability Assessment of Interconnected ICT and Power Networks Using Complex Network Theory. In Proceedings of the 2018 IEEE Power and Energy Society General Meeting (PESGM), Portland, OR, USA, 5–10 August 2018; IEEE: New York, NY, USA, 2018. [Google Scholar] [CrossRef] [Green Version]
- Kim, S.H.; Leem, C.S. Security threats and their countermeasures of mobile portable computing devices in ubiquitous computing environments. In Lecture Notes in Computer Science; Springer: Berlin, Germany, 2005; Volume 3483, pp. 79–85. [Google Scholar] [CrossRef]
- van Niekerk, B. Vulnerability Assessment of Modern ICT Infrastructure from an Information Warfare Perspective. Ph.D. Thesis, University of Kwazulu-Natal, Durban, South African, 2011. Available online: http://hdl.handle.net/10413/12295 (accessed on 23 January 2020).
- Mehmood, Y.; Ahmad, F.; Yaqoob, I.; Adnane, A.; Imran, M.; Guizani, S. Internet-of-Things-Based Smart Cities: Recent Advances and Challenges. IEEE Commun. Mag. 2017, 55, 16–24. [Google Scholar] [CrossRef]
- Weiser, M. Some computer science issues in ubiquitous computing. Commun. ACM 1993, 36, 75–84. [Google Scholar] [CrossRef]
- Weiser, M.; Gold, R.; Brown, J.; Weiser, G.; Brown, J.M.R. The origins of ubiquitous computing research at PARC in the Late 1980s. IBM Syst. J. 1999, 38, 693–696. [Google Scholar] [CrossRef]
- Papa, R.; Gargiulo, C.; Galderisi, A. Towards an urban planners’ perspective on Smart City. TeMA 2013, 6, 5–17. [Google Scholar] [CrossRef]
- Lee, J.; Oh, J. New Songdo City and the Value of Flexibility: A Case Study of Implementation and Analysis of a Mega-Scale Project. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2008. Available online: http://hdl.handle.net/1721.1/58657 (accessed on 23 February 2020).
- Lee, M.; Uhm, Y.; Hwang, Z.; Kim, Y.; Jo, J.; Park, S. An Urban Computing Framework for Autonomous Services in A U-City. In Proceedings of the 2007 International Conference on Convergence Information Technology (ICCIT 2007), Gyeongju, Korea, 21–23 November 2007. [Google Scholar] [CrossRef]
- Hashemi, M.; Sadeghi-Niaraki, A. A theoretical framework for ubiquitous computing. Int. J. Adv. Pervasive Ubiquitous Comput. 2016, 8, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Jang, M.; Suh, S.T. U-City: New Trends of Urban Planning in Korea Based on Pervasive and Ubiquitous Geotechnology and Geoinformation. In Proceedings of the Computational Science and Its Applications—ICCSA 2010, Fukuoka, Japan, 23–26 March 2010; Lecture Notes in Computer Science. Taniar, D., Gervasi, O., Murgante, B., Pardede, E., Apduhan, B.O., Eds.; Springer: Heidelberg, Germany, 2010; Volume 6016. [Google Scholar] [CrossRef]
- Bell, G.; Dourish, P. Esterday’s tomorrows: Notes on ubiquitous computing’s dominant vision. Pers. Ubiquitous Comput. 2007, 11, 133–143. [Google Scholar] [CrossRef]
- Lee, J.; Lee, H.; Kim, T. Evaluating and assessing a typology of ubiquitous city services by classifying and assigning actual services from an inventory of identified services in practice. In Proceedings of the 6th International Conference on Theory and Practice of Electronic Governance; ACM International Conference Proceeding Series; ACM: Albany, NY, USA, 2012; pp. 279–285. [Google Scholar] [CrossRef]
- Lee, S.H.; Han, J.H.; Leem, Y.T.; Yigitcanlar, T. Towards Ubiquitous City: Concept, Planning, and Experiences in the Republic of Korea; IGI Global: Hershey, PA, USA, 2008. [Google Scholar]
- Capeluto, I.G.; Ben-Avraham, O.; Capeluto, O.B.-A.I.G. Assessing the green potetial of existing buildings towards smart cities and districts. Indoor Built Environ. 2015, 25, 1124–1135. [Google Scholar] [CrossRef]
- Gaddis, J.L. Rethinking Cold War History; Oxford University Press: New York, NY, USA, 1997. [Google Scholar]
- Villa, V. Progressive energy retrofit for the educational building stock in a smart city. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 3 October 2016; p. 1. [Google Scholar] [CrossRef]
- Lee, J.; Baik, S.; Lee, C.C. Building an integrated service management platform for ubiquitous cities. Computer 2011, 44, 56–63. [Google Scholar] [CrossRef]
- Leem, C.S.; Kim, B.G. Taxonomy of ubiquitous computing service for city development. Pers. Ubiquitous Comput. 2013, 17, 1475–1483. [Google Scholar] [CrossRef]
- Suopajärvi, T.; Ylipulli, J.; Kinnunen, T. ‘Realities behind ICT Dreams’ Designing a Ubiquitous City in a Living Lab Environment. Int. J. Gend. Sci. Technol. 2012, 4, 231–252. [Google Scholar]
- What Determines Bluetooth Range? Available online: https://www.bluetooth.com/learn-about-bluetooth/bluetooth-technology/range/ (accessed on 13 November 2020).
- Rouse, M. RFID (Radio Frequency Identification). 2007. Available online: https://internetofthingsagenda.techtarget.com/definition/RFID-radio-frequency-identification (accessed on 13 November 2020).
- Wei, E.J.Y.; Chan, A.T.S. Towards Context-Awareness in Ubiquitous Computing. In Embedded and Ubiquitous Computing 2007; Springer: Heidelberg, Germany, 2007; pp. 706–717. [Google Scholar] [CrossRef] [Green Version]
- The Important Difference between Virtual Reality, Augmented Reality and Mixed Reality. 2019. Available online: https://www.forbes.com/sites/bernardmarr/2019/07/19/the-important-difference-between-virtual-reality-augmented-reality-and-mixed-reality/?sh=585ee3dc35d3 (accessed on 13 November 2020).
- Telstra. ADSL2+, ADSL Plans. 2020. Available online: https://www.telstra.com.au/internet/adsl (accessed on 13 November 2020).
- Beal, V. ADSL-Asymmetric Digital Subscriber Line. 2020. Available online: https://www.webopedia.com/TERM/A/ADSL.html (accessed on 13 November 2020).
- ICACT. Broadband Convergence Network [BcN] for ubiquitous Korea vision. In Proceedings of the 7th International Conference on Advanced Communication Technology, Phoenix Park, Korea, 21–23 February 2005; pp. 168–181. [Google Scholar] [CrossRef]
- FTTP vs. FTTN vs. FTTC: Connections to the National Broadband Network Explained, Aussie Broadband Blog. 2018. Available online: https://www.aussiebroadband.com.au/blog/fttp-vs-fttn-connections-national-broadband-network-explained/ (accessed on 13 November 2020).
- A Brief History of GPRS, 3G, 4G and the Latest 5G Mobile Network Technology. 2018. Available online: https://www.raptorhub.com/guides/4g (accessed on 13 November 2020).
- Evers, J. Encyclopedic Entry: GIS (Geographic Information System). National Geographic Society. 2017. Available online: https://www.nationalgeographic.org/encyclopedia/geographic-information-system-gis/#:~:text=Ageographicinformationsystem (accessed on 13 November 2020).
- Ferreira, R. White Paper: Where to Place the Frotcom GPS Terminal Inside a Vehicle; Frotcom: Piatra Neamt, Romania, 2019. [Google Scholar]
- NOAA. What Is Remote Sensing? 2020. Available online: https://oceanservice.noaa.gov/facts/remotesensing.html (accessed on 14 November 2020).
- RADAR-Basics, Types & Applications. 2020. Available online: https://www.elprocus.com/radar-basics-types-and-applications/ (accessed on 14 November 2020).
- Lea, R.; Blackstock, M. City hub: A cloud-based IoT platform for smart cities. In Proceedings of the 2014 IEEE 6th International Conference on Cloud Computing Technology and Science, Singapore, 15–18 December 2014; IEEE: Singapore, 2015; pp. 799–804. [Google Scholar] [CrossRef] [Green Version]
- Farahzadi, A.; Shams, P.; Rezazadeh, J.; Farahbakhsh, R. Middleware technologies for cloud of things: A survey. Digit. Commun. Netw. 2018, 4, 176–188. [Google Scholar] [CrossRef]
- Saxby, R. The Advancing Importance of System on a Chip Technology & Application. In TechTarget; IET: London, UK, 2003; Available online: https://search.ebscohost.com/login.aspx?direct=true&AuthType=shib&db=cat06414a&AN=vic.b4585372&site=eds-live (accessed on 14 November 2020).
- Botta, A.; de Donato, W.; Persico, V.; Pescapé, A. On the Integration of Cloud Computing and Internet of Things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud, Barcelona, Spain, 27–29 August 2014; IEEE: Barcelona, Spain, 2014; pp. 23–30. [Google Scholar] [CrossRef]
- Bachani, M.; Memon, A.; Shaikh, F.K. Sensors network: In regard with the security aspect and counter measures. In Network Security Attacks and Countermeasures; IGI Global: Hershey, PA, USA, 2016; pp. 176–196. [Google Scholar] [CrossRef]
- Kibirige, G.W.; Sanga, C.A. Attacks in wireless sensor networks. In Network Security Attacks and Countermeasures; IGI Global: Hershey, PA, USA, 2016; pp. 157–175. [Google Scholar] [CrossRef]
- Virupakshar, K.B.; Asundi, M.; Channal, K.; Shettar, P.; Patil, S.; Narayan, D.G. Distributed Denial of Service (DDoS) Attacks Detection System for OpenStack-based Private Cloud. Procedia Comput. Sci. 2020, 167, 2297–2307. [Google Scholar] [CrossRef]
- Al-Hababi, A.; Tokgoz, S.C. Man-in-the-Middle Attacks to Detect and Identify Services in Encrypted Network Flows using Machine Learning. In Proceedings of the 2020 3rd International Conference on Advanced Communication Technologies and Networking (CommNet), Marrakech, Morocco, 4–6 September 2020. [Google Scholar] [CrossRef]
- Spitzner, L. Endpoint Protection-Symantec Enterprise. IP Spoofing: An Introduction. 2003. Available online: https://community.broadcom.com/symantecenterprise/communities/community-home/librarydocuments/viewdocument?DocumentKey=9d18fc06-b229-4c4a-8ca5-7386d0870c01&CommunityKey=1ecf5f55-9545-44d6-b0f4-4e4a7f5f5e68&tab=librarydocuments (accessed on 16 November 2020).
- The Difference between Phishing and Spear Phishing|PhishProtection.com. Available online: https://www.phishprotection.com/content/phishing-prevention/difference-between-phishing-and-spear-phishing/ (accessed on 16 November 2020).
- Simmonds, M. Beware the drive-by attack. Comput. Fraud Secur. 2016, 2016, 19–20. [Google Scholar] [CrossRef]
- Password Attacks|Infosavvy Security and IT Management Training. Available online: https://info-savvy.com/password-attacks/ (accessed on 16 November 2020).
- Porup, J.M. What Is sql Injection? How SQLi Attacks Work and How to Prevent Them|CSO Online. 2018. Available online: https://www.csoonline.com/article/3257429/what-is-sql-injection-how-these-attacks-work-and-how-to-prevent-them.html (accessed on 16 November 2020).
- What Is a Cross-Site Scripting (XSS) Attack: Definition & Examples. Available online: https://www.ptsecurity.com/ww-en/analytics/knowledge-base/what-is-a-cross-site-scripting-xss-attack/ (accessed on 16 November 2020).
- York, D. Chapter 3—Eavesdropping and Modification. In Seven Deadliest Unified Communications Attacks; York, D., Ed.; Elsevier: Burlington, VT, USA, 2010; pp. 41–69. [Google Scholar] [CrossRef]
- What Is a Birthday Attack and How to Prevent It? Available online: https://www.internetsecurity.tips/birthday-attack/ (accessed on 16 November 2020).
- Patel, V.; Choe, S.; Halabi, T. Predicting Future Malware Attacks on Cloud Systems using Machine Learning. In Proceedings of the 2020 IEEE 6th International Conference on Big Data Security on Cloud, Baltimore, MD, USA, 25–27 May 2020; pp. 151–156. [Google Scholar] [CrossRef]
- GNSS Jammers and Its Impacts in Military Defense—VisionSpace Blog. Available online: https://visionspace.blog/blog/2020/2/27/gnss-jammers-and-its-impacts-in-military-defense (accessed on 16 November 2020).
- Do Weather Conditions Affect GPS Accuracy? 2016. Available online: https://www.frotcom.com/blog/2016/11/do-weather-conditions-affect-gps-accuracy (accessed on 17 November 2020).
- El-Sayed, K.A.; Sakr, M.A.; Awad, E.A. National Seismic Network and Earthquake Activities in Egypt. Earthq. Hazards Mitig. 2007, 7, 88–101. [Google Scholar]
- Surge and Lightning Damage to Electronics. 2016. Available online: https://strikecheck.com/webinars/surge-and-lightning-damage-to-electronics/ (accessed on 17 November 2020).
- Carlos. Can Solar Panels Be Damaged by Hail? 2019. Available online: https://ecotality.com/can-solar-panels-be-damaged-by-hail/ (accessed on 17 November 2020).
- How Summer Heat Can Affect Your Internet. 2018. Available online: https://www.softcom.net/how-summer-heat-can-affect-your-internet/ (accessed on 17 November 2020).
- Hale, J. Can the Weather Affect Your Wi-Fi? Here’s Why Your Internet Seems Slow When It’s Gross Out. 2018. Available online: https://www.bustle.com/p/can-the-weather-affect-your-wi-fi-heres-why-your-internet-seems-slow-when-its-gross-out-9215741 (accessed on 17 November 2020).
- Byrd, D. Are Solar Storms Dangerous to Us? 2020. Available online: https://earthsky.org/space/are-solar-storms-dangerous-to-us (accessed on 18 November 2020).
- Tornadoes, Explained: Learn How These Deadly Storms Form and Wreak Havoc, and How You can Reduce Your Risk. National Geographic Society. 2019. Available online: https://www.nationalgeographic.com/environment/natural-disasters/tornadoes/ (accessed on 18 November 2020).
- Deziel, C. What Damage Do Tsunamis Cause? 2018. Available online: https://sciencing.com/tsunami-created-8747310.html (accessed on 18 November 2020).
- Xiao, R.; He, X.; Zhang, Y.; Ferreira, V.G.; Chang, L. Monitoring groundwater variations from satellite gravimetry and hydrological models: A comparison with in-situ measurements in the mid-atlantic region of the United States. Remote Sens. 2015, 7, 686–703. [Google Scholar] [CrossRef] [Green Version]
- Tonkin, C. Telcos Scramble to Fix Networks during Bushfires. 2020. Available online: https://ia.acs.org.au/article/2020/telcos-scramble-to-fix-rural-networks-during-bushfires.html (accessed on 18 November 2020).
- Gandini, A.; Garmendia, L.; Prieto, I.; Álvarez, I.; San-José, J.-T. A holistic and multi-stakeholder methodology for vulnerability assessment of cities to flooding and extreme precipitation events. Sustain. Cities Soc. 2020, 63, 102437. [Google Scholar] [CrossRef]
- Tapia, C. Profiling urban vulnerabilities to climate change: An indicator-based vulnerability assessment for European cities. Ecol. Indic. 2017, 78, 142–155. [Google Scholar] [CrossRef]
- Mohamed, S.A.; El-Raey, M.E. Vulnerability assessment for flash floods using GIS spatial modeling and remotely sensed data in El-Arish City, North Sinai, Egypt. Nat. Hazards 2020, 102, 707–728. [Google Scholar] [CrossRef]
- Murali, R.M.; Riyas, M.J.; Reshma, K.N.; Kumar, S.S. Climate change impact and vulnerability assessment of Mumbai city, India. Nat. Hazards 2020, 102, 575–589. [Google Scholar] [CrossRef]
- Arouq, M.K.; Esmaeilpour, M.; Sarvar, H. Vulnerability assessment of cities to earthquake based on the catastrophe theory: A case study of Tabriz city, Iran. Environ. Earth Sci. 2020, 79, 354. [Google Scholar] [CrossRef]
- Adnan, S.; Ullah, K. Development of drought hazard index for vulnerability assessment in Pakistan. Nat. Hazards 2020, 103, 2989–3010. [Google Scholar] [CrossRef]
- Alelaiwi, A. Evaluating distributed IoT databases for edge/cloud platforms using the analytic hierarchy process. J. Parallel Distrib. Comput. 2019, 124. [Google Scholar] [CrossRef]
- Myeong, S.; Jung, Y.; Lee, E. A study on determinant factors in smart city development: An analytic hierarchy process analysis. Sustainability 2018, 10, 2606. [Google Scholar] [CrossRef] [Green Version]
- Jnr, B.A. Validating the usability attributes of AHP-software risk prioritization model using partial least square-structural equation modeling. J. Sci. Technol. Policy Manag. 2019, 10. [Google Scholar] [CrossRef]
- Pal, S.C.; Das, B.; Malik, S. Potential Landslide Vulnerability Zonation Using Integrated Analytic Hierarchy Process and GIS Technique of Upper Rangit Catchment Area, West Sikkim, India. J. Indian Soc. Remote Sens. 2019, 47, 1643–1655. [Google Scholar] [CrossRef]
- Sami, G.; Hadda, D.; Mahdi, K.; Abdelwahhab, F. A Multi-criteria Analytical Hierarchy Process (AHP) to Flood Vulnerability Assessment in Batna Watershed (Algeria). Analele Univ. Oradea Ser. Geogr. 2020, 30. [Google Scholar] [CrossRef]
- Dandapat, K.; Panda, G.K. Flood vulnerability analysis and risk assessment using analytical hierarchy process. Model. Earth Syst. Environ. 2017, 3, 1627–1646. [Google Scholar] [CrossRef]
- Ghosh, A.; Kar, S.K. Application of analytical hierarchy process (AHP) for flood risk assessment: A case study in Malda district of West Bengal, India. Nat. Hazards 2018, 94, 349–368. [Google Scholar] [CrossRef]
- Behera, R.; Kar, A.; Das, M.R.; Panda, P.P. GIS-based vulnerability mapping of the coastal stretch from Puri to Konark in Odisha using analytical hierarchy process. Nat. Hazards 2019, 96, 731–751. [Google Scholar] [CrossRef]
- Monjardin, C.E.F.; Tan, F.J.; Uy, F.A.A.; Bale, F.J.P.; Voluntad, E.O.; Batac, R.M.N. Assessment of the Existing Drainage System in Infanta, Quezon Province for Flood Hazard Management using Analytical Hierarchy Process. In Proceedings of the 2020 IEEE Conference on Technologies for Sustainability (SusTech), Santa Ana, CA, USA, 23–25 April 2020; IEEE: Santa Ana, CA, USA, 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Hwang, Y.H. IoT Security & Privacy: Threats and Challenges. In Proceedings of the 1st ACM Workshop on IoT Privacy, Trust, and Security, New York, NY, USA, April 2015; p. 1. Available online: https://dl.acm.org/citation.cfm?id=2732216 (accessed on 21 December 2020). [CrossRef]
- Kim, J.; Choi, H.; Ryou, J. Countermeasures to Vulnerability of Certificate Application in u-City. In Proceedings of the 2010 5th International Conference on Ubiquitous Information Technologies and Applications, Sanya, China, 16–18 December 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Forsström, S.; Butun, I.; Eldefrawy, M.; Jennehag, U.; Gidlund, M. Challenges of Securing the Industrial Internet of Things Value Chain. In Proceedings of the 2018 Workshop on Metrology for Industry 4.0 and IoT, Brescia, Italy, 16–18 April 2018; pp. 218–223. [Google Scholar] [CrossRef] [Green Version]
- Yin, M.; Wang, Q.; Cao, M. An Attack Vector Evaluation Method for Smart City Security Protection. In Proceedings of the 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 21–23 October 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Kazemi, Z.; Fazeli, M.; Hely, D.; Beroulle, V. Hardware Security Vulnerability Assessment to Identify the Potential Risks in a Critical Embedded Application. In Proceedings of the 2020 IEEE 26th International Symposium on On-Line Testing and Robust System Design (IOLTS), Napoli, Italy, 13–15 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Tariq, M.A.U.R.; van de Giesen, N.C. Risk-Based Planning and Optimization of Flood Management Measures in Developing Countries: Case Pakistan Volume. Ph.D. Thesis, Delft University of Technology, Delft, The Netherlands, 2011; p. 163. [Google Scholar]
- Roy, U.; Majumder, M. Vulnerability of Watersheds to Climate Change Assessed by Neural Network and Analytical Hierarchy Process; Springer: Singapore, 2016; ISBN 978-981-287-344-6. [Google Scholar]
- Bany Abdelnabi, A.A. An Analytical Hierarchical Process Model to Select Programming Language for Novice Programmers for Data Analytics Applications. In Proceedings of the 2019 International Arab Conference on Information Technology (ACIT), Al Ain, UAE, 3–5 December 2019; pp. 128–132. [Google Scholar] [CrossRef]
- Alaneme, G.U.; Ezeokpube, G.C.; Mbadike, E.M. Failure Analysis of a Partially Collapsed Building using Analytical Hierarchical Process. J. Fail. Anal. Prev. 2020, 1–12. [Google Scholar] [CrossRef]










Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tariq, M.A.U.R.; Wai, C.Y.; Muttil, N. Vulnerability Assessment of Ubiquitous Cities Using the Analytic Hierarchy Process. Future Internet 2020, 12, 235. https://doi.org/10.3390/fi12120235
Tariq MAUR, Wai CY, Muttil N. Vulnerability Assessment of Ubiquitous Cities Using the Analytic Hierarchy Process. Future Internet. 2020; 12(12):235. https://doi.org/10.3390/fi12120235
Chicago/Turabian StyleTariq, Muhammad Atiq Ur Rehman, Cheuk Yin Wai, and Nitin Muttil. 2020. "Vulnerability Assessment of Ubiquitous Cities Using the Analytic Hierarchy Process" Future Internet 12, no. 12: 235. https://doi.org/10.3390/fi12120235
APA StyleTariq, M. A. U. R., Wai, C. Y., & Muttil, N. (2020). Vulnerability Assessment of Ubiquitous Cities Using the Analytic Hierarchy Process. Future Internet, 12(12), 235. https://doi.org/10.3390/fi12120235






