Decoupling-Based Channel Access Mechanism for Improving Throughput and Fairness in Dense Multi-Rate WLANs
Abstract
1. Introduction
- Firstly, an efficient hybrid channel access mechanism DMAC for dense multi-rate network is proposed. The proposed mechanism can achieve collision-free data transmission by decoupling channel contention and data transmission. Additionally, an adaptive algorithm is designed in DMAC to dynamically adjust the length of CP and further improve the channel utilization.
- Secondly, we also propose two airtime fairness algorithms I-DMAC1 and I-DMAC2 based on DMAC, and tackle the performance anomaly for different application scenarios in multi-rate network, such as delay-sensitive and high-throughput networks, respectively.
- Thirdly, we establish a mathematical analysis model for DMAC. It is theoretically proven that the system throughput can be improved by decoupling the data transmission and contention process.
- Lastly, we extensively evaluate the performance of the proposed algorithms in saturated and non-saturated network scenarios, and the simulation results verify that I-DMAC1 algorithm is more suitable to the delay-sensitive data transmission scenarios and I-DMAC2 algorithm can perform the better performance in some high throughput demand scenarios.
2. Related Work
3. System Framework and Algorithm Procedure
3.1. Overview
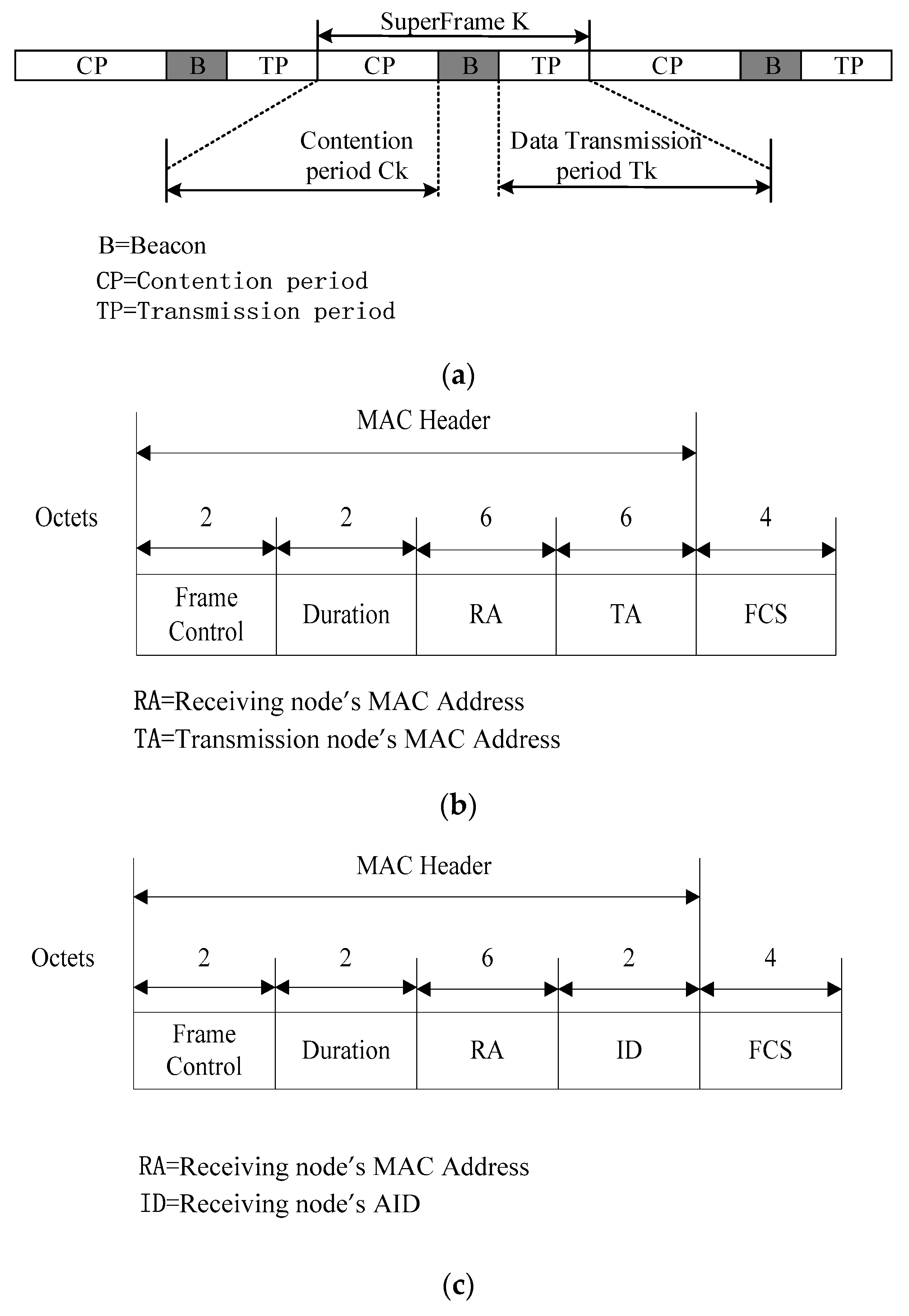
3.2. Frame Format
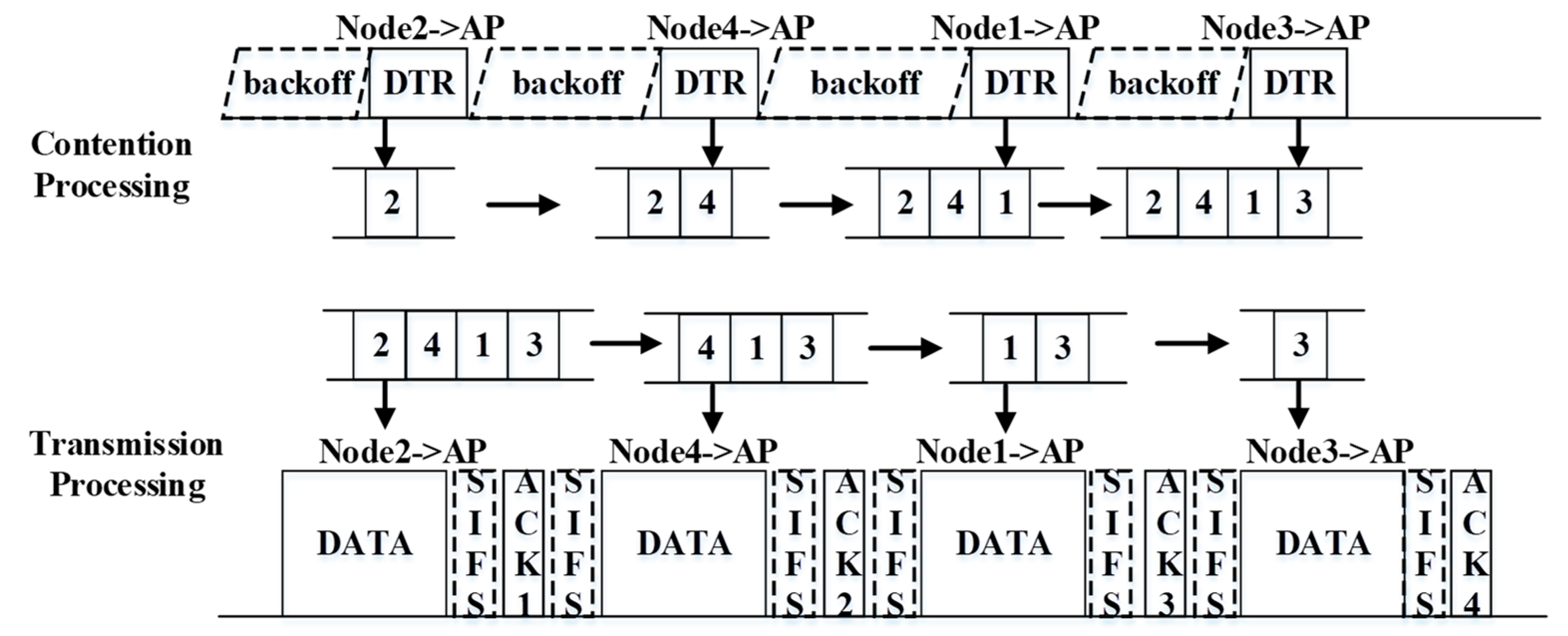
3.3. Basic DMAC Procedure
3.4. Improved DMAC (I-DMAC) Algorithm
| Algorithm 1 Contention Processing for I-DMAC1 |
| Input: The number of nodes Output: The transmission order stored in Contention Queue Buffer Initial: AP broadcasts Beacon 1: If the node receives a Beacon frame 2: -Initializes the Contention Window value 3: Data Transmission Processing 4: If idle_time == DIFS and the node’s back-off_value != 0 5: -Performs the back-off process 6: If back-off_value == 0 and the channel is idle 7: -Transmits a DTR 8: -Increment the competition counter (NumComp++) 9: If NumComp <= R/Rmin /* does not reach the maximum number of competitions*/ 10: -Chooses a random back-off value 11: -Go to step 4 |
| Algorithm 2 Data Transmission Processing for I-DMAC2 |
| Input: A Beacon piggybacking the first ID of Contention Queue Buffer, R, Rmin Output: The node in Contention Queue Buffer transmits data Initial: AP broadcasts Beacon 1: If a node receives a Beacon frame and its ID is piggybacked in the beacon 2: -Transmits a data frame 3: -AP transmits ACK frame 4: If a node receives an ACK frame and its ID is piggybacked in this ACK frame 5: -Transmits a data frame 6: -Increment the transmission counter (NumTran ++) 7: If NumTran <= R/Rmin /* does not reach the maximum number of transmissions*/ 8: -Go to step 5 |
3.5. Contention Period Optimization
4. Performance Analysis
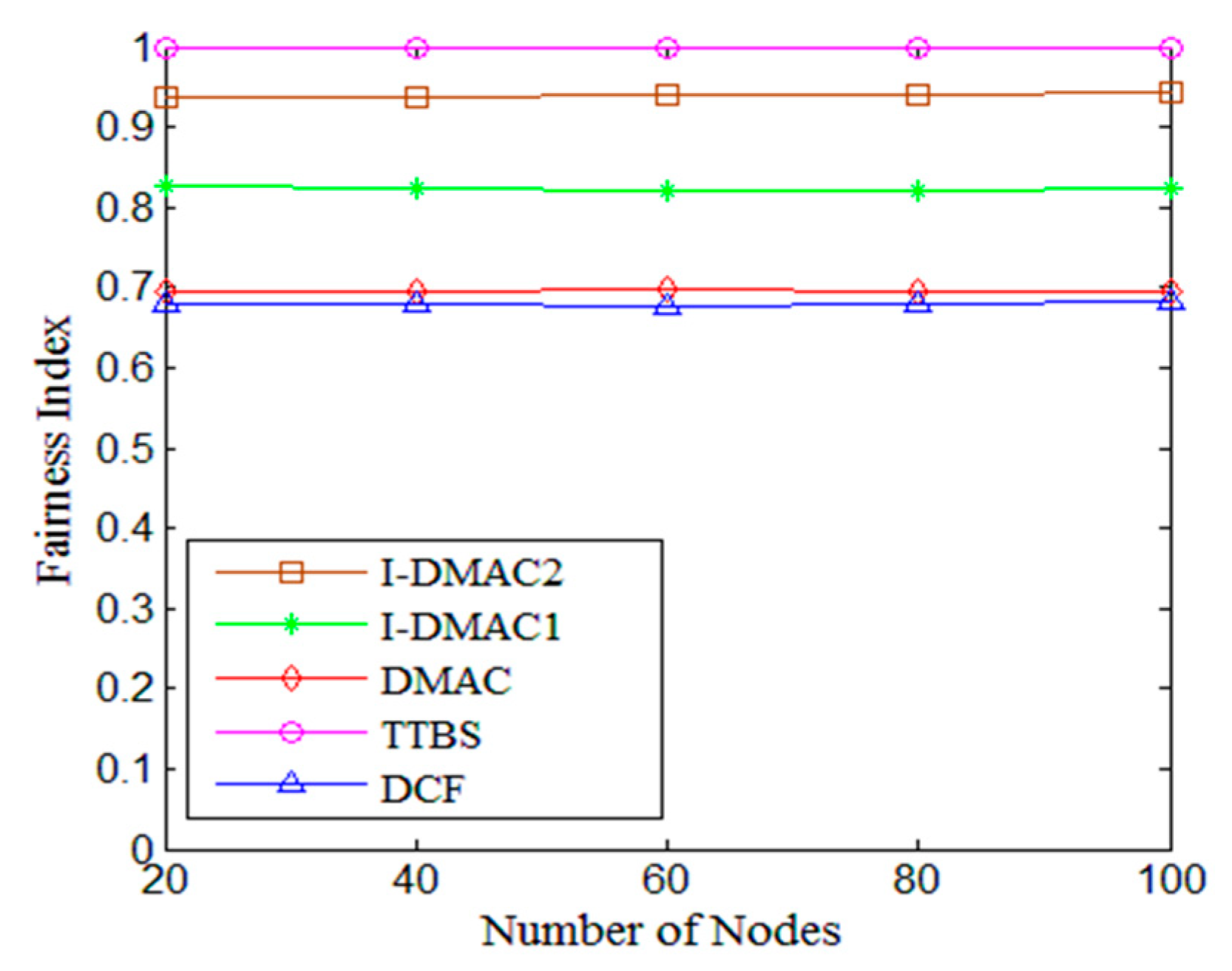
5. Simulation Results
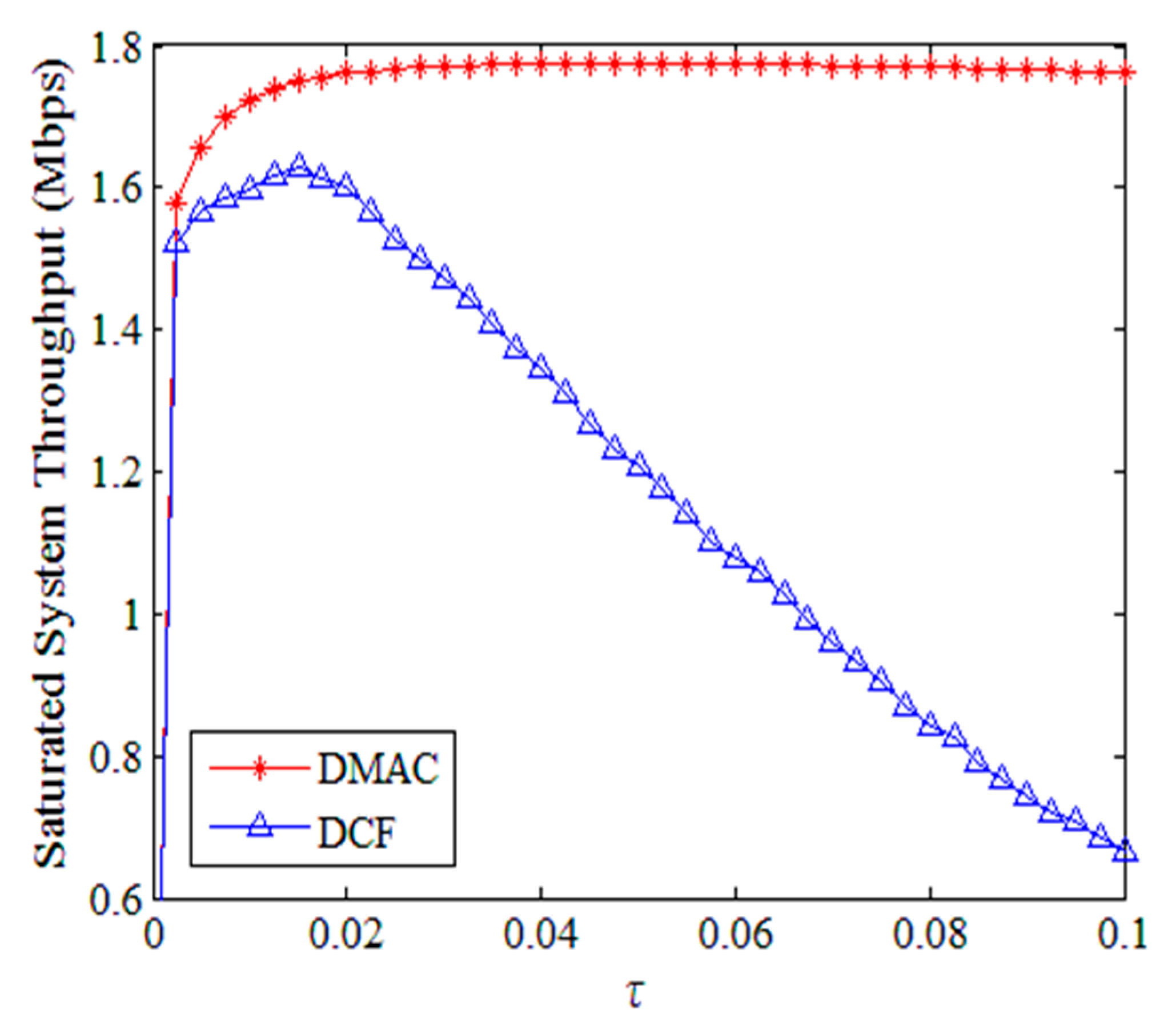
5.1. DMAC
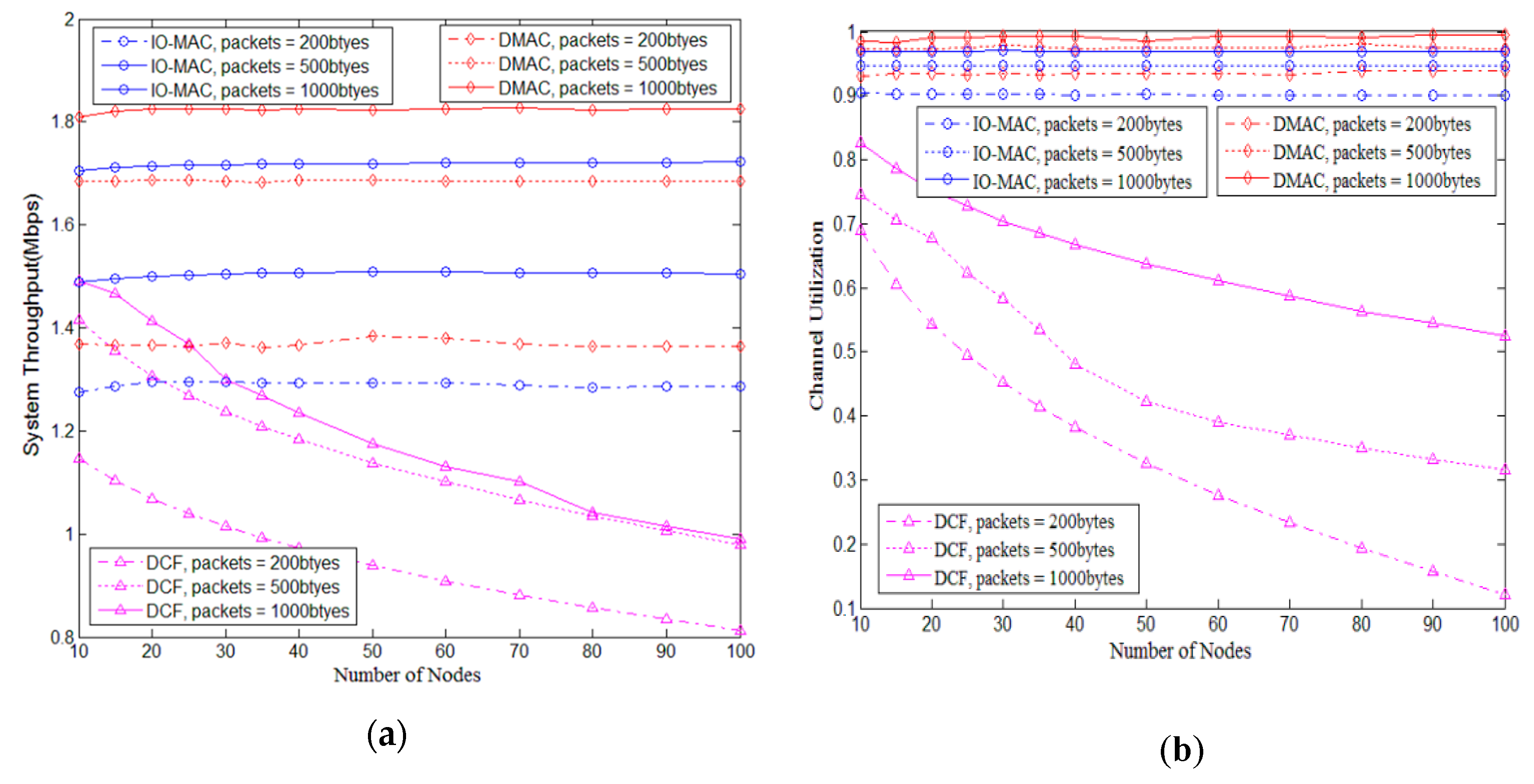
5.2. I-DMAC
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- IEEE. Standard 802.11-2012-IEEE Standard for Information Technology–Telecommunications and Information Exchange Between Systems Local and Metropolitan Area Networks–Specifific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specififications; IEEE: Piscataway, NJ, USA, 2012; pp. 1–425. [Google Scholar]
- Heusse, M.; Rousseau, F.; Berger-Sabbatel, G.; Duda, A. Performance anomaly of 802.11 b. In Proceedings of the IEEE INFOCOM, San Francisco, CA, USA, 30 March–3 April 2003; pp. 836–843. [Google Scholar]
- Le, Y.; Ma, L.; Cheng, W.; Cheng, X.Z. A Time Fairness-Based MAC Algorithm for Throughput Maximization in 802.11 Networks. IEEE Trans. Comput. 2015, 64, 19–31. [Google Scholar] [CrossRef]
- Morino, Y.; Hiraguri, T.; Yoshino, H. A Novel Contention Window Control Scheme Based on a Markov Chain Model in Dense WLAN Environment. In Proceedings of the 3rd International Conference on Artificial Intelligence, Modelling and Simulation, Kota Kinabalu, Malaysia, 2–4 October 2015; pp. 417–421. [Google Scholar]
- Ali, R.; Shahin, N.; Kim, S.W. Channel observation-based scaled backoff mechanism for high-efficiency WLANs. Electron. Lett. 2018, 54, 663–665. [Google Scholar] [CrossRef]
- Shahin, N.; Ali, R.; Kim, S.W.; Kim, Y.T. Cognitive backoff mechanism for IEEE802.11ax high-efficiency WLANs. J. Commun. Netw. 2019, 21, 158–167. [Google Scholar] [CrossRef]
- Yu, Q.; Zhuang, Y.; Ma, L. Dynamic contention window adjustment scheme for improving throughput and fairness in IEEE 802.11 wireless LANs. In Proceedings of the Global Communications Conference (GLOBECOM 2012), Anaheim, CA, USA, 3–7 December 2012; pp. 5074–5080. [Google Scholar]
- Hong, K.; Lee, S.K.; Kim, K. Channel Condition Based Contention Window Adaptation in IEEE 802.11 WLANs. IEEE Trans. Commun. 2012, 60, 469–478. [Google Scholar] [CrossRef]
- Le, Y.; Ma, L.; Cheng, W.; Cheng, X.Z.; Chen, B. Maximizing throughput when achieving time fairness in multi-rate wireless LANs. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 23–30 March 2012; pp. 2911–2915. [Google Scholar]
- Bellalta, B. IEEE 802.11ax: High-efficiency WLANS. IEEE Wirel. Communs. 2016, 23, 38–46. [Google Scholar] [CrossRef]
- Ali, R.; Shahin, N.; Bajracharya, R.; Kim, B.S.; Kim, S.W. A Self-Scrutinized Backoff Mechanism for IEEE 802.11ax in 5G Unlicensed Networks. Sustainability 2018, 10, 1201. [Google Scholar] [CrossRef]
- Ali, R.; Kim, S.W.; Kim, B.S. Design of MAC Layer Resource Allocation Schemes for IEEE 802.11ax: Future Directions. IETE Tech. Rev. 2018, 35, 28–52. [Google Scholar] [CrossRef]
- Lei, J.J.; Yun, H. Decoupling Channel Contention and Data Transmission in Dense Wireless Infrastructure Network. In Proceedings of the 8th Computer Science On-line Conference, Hlavni Mesto Praha, Czech Republic, 24–27 April 2019. [Google Scholar]
- Bianchi, G. Performance utanalysis of the IEEE 802.11 distribed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Karaca, M.; Bastani, S.; Landfeldt, B. Modifying Backoff Freezing Mechanism to Optimize Dense IEEE 802.11 Networks. IEEE Trans. Veh. Technol. 2017, 66, 9470–9482. [Google Scholar] [CrossRef]
- Kim, J.D.; Laurenson, D.I.; Thompson, J.S. Centralized Random Backoff for Collision Resolution in Wi-Fi Networks. IEEE Trans. Wirel. Commun. 2017, 16, 5838–5852. [Google Scholar] [CrossRef]
- Hosseinabadi, G.; Vaidya, N. Token-DCF: An Opportunistic MAC protocol for Wireless Networks. In Proceedings of the Fifth International Conference on Communication Systems and Networks (COMSNETS 2013), Bangalore, India, 7–10 January 2013; pp. 1–9. [Google Scholar]
- Ko, H.; Lee, G.; Kim, C. IO-MAC: An Enhancement of IEEE 802.11 DCF Using Implicit Ordering. Wirel. Pers. Commun. 2013, 2, 1467–1473. [Google Scholar] [CrossRef]
- Feng, B.; Hong, S.; Wang, Z. IO-MAC: A novel hybrid MAC protocol with implicit ordering in WLANs. In Proceedings of the Sixth International Conference on Wireless Communications and Signal Processing (WCSP 2014), Hefei, China, 23–25 October 2014. [Google Scholar]
- Zhao, Q.; Xu, F.; Yang, J. CSMA/CQ: A Novel SDN-Based Design to Enable Concurrent Execution of Channel Contention and Data Transmission in IEEE 802.11 Networks. IEEE Access 2017, 5, 2534–2549. [Google Scholar] [CrossRef]
- Lin, P.; Chou, W.; Lin, T. Achieving airtime fairness of delay-sensitive applications in multirate IEEE 802.11 wireless LANs. IEEE Commun. Mag. 2011, 49, 169–175. [Google Scholar] [CrossRef]
- Cali, F.; Conti, M.; Gregori, E. Dynamic Tuning of the IEEE 802.11 Protocol to Achieve A Theoretical Throughput Limit. IEEE ACM Trans. Netw. 2000, 6, 785–799. [Google Scholar] [CrossRef]
- Heusse, M.; Rousseau, F.; Guillier, R. Idle sense: An Optimal Access Method for High Throughput and Fairness in Rate Diverse Wireless LANs. In Proceedings of the ACM SIGCOMM Computer Communication Review, Philadelphia, PA, USA, 22–26 August 2005; pp. 121–132. [Google Scholar]
- Yazici, M.A.; Akar, N. Running Multiple Instances of the Distributed Coordination Function for Air-Time Fairness in Multi-Rate WLANs. IEEE Commun. Mag. 2013, 12, 5067–5076. [Google Scholar] [CrossRef]
- Alhaji, I.A.; Tijjani, B.I.; Ali, M.H. Determination of Performance Enhancement in IEEE 802.11 multi-rate WLAN. Int. J. Digit. Inf. Wirel. Commun. 2015, 5, 257–269. [Google Scholar]
- Hu, S.; Li, J.; Pan, G. Performance and Fairness Enhancement in IEEE 802.11 WLAN networks. AEU-Int. J. Electron. Commun. 2014, 68, 667–675. [Google Scholar] [CrossRef]
- Shahin, N.; Ali, R.; Kim, Y.T. Hybrid slotted-csma/ca-tdma for efficient massive registration of iot devices. IEEE Access 2018, 6, 18366–18382. [Google Scholar] [CrossRef]
- Jian, R.; Chiu, D.M.; Hawe, W. A Quantitative Measure of Fairness and Discrimination for Resource Allocation in Shared Computer Systems. Digital Equipment Corporation; Eastern Research Laboratory: Hudson, MA, USA, 1984. [Google Scholar]
- Ali, R.; Shahin, N.; Zikria, Y.B. Deep Reinforcement Learning Paradigm for Performance Optimization of Channel Observation–based MAC Protocols in Dense WLANs. IEEE Access 2018, 99, 3500–3511. [Google Scholar] [CrossRef]
- Ali, R.; Qadri, Y.A.; Zikria, Y.B. Q-learning-enabled channel access in next-generation dense wireless networks for IoT-based eHealth systems. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 1–12. [Google Scholar] [CrossRef]
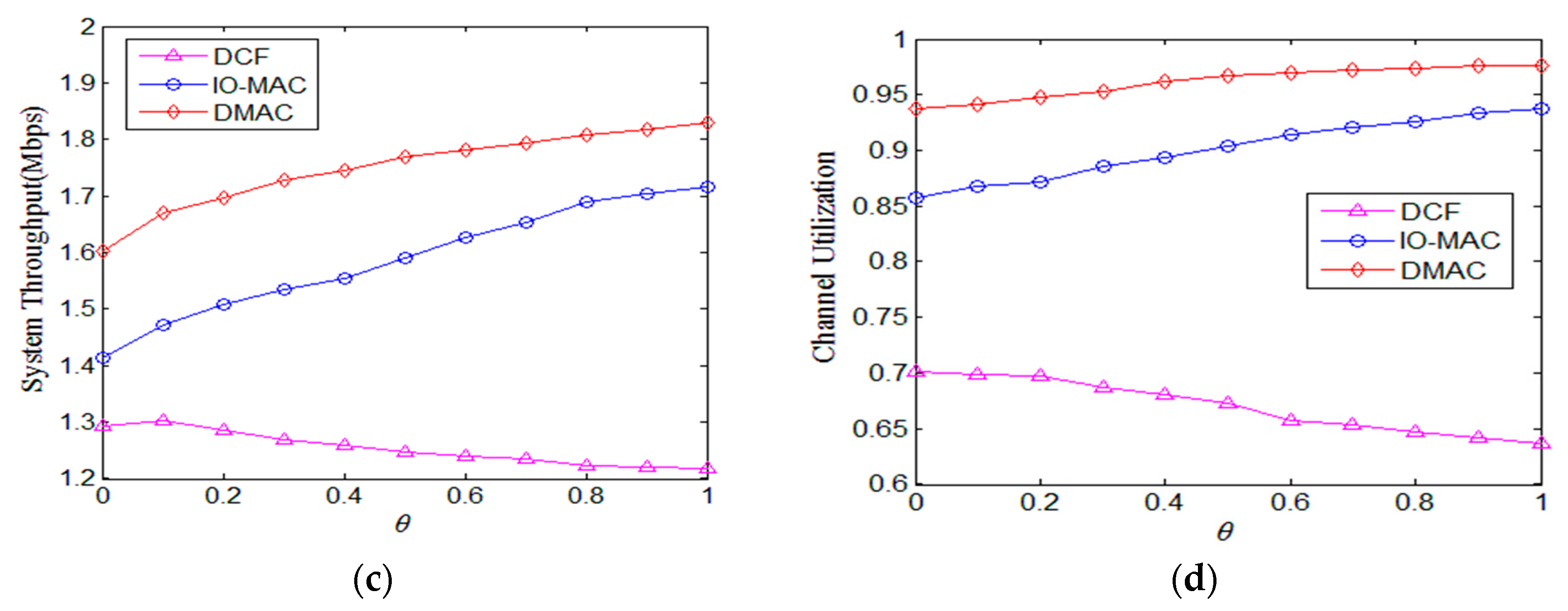
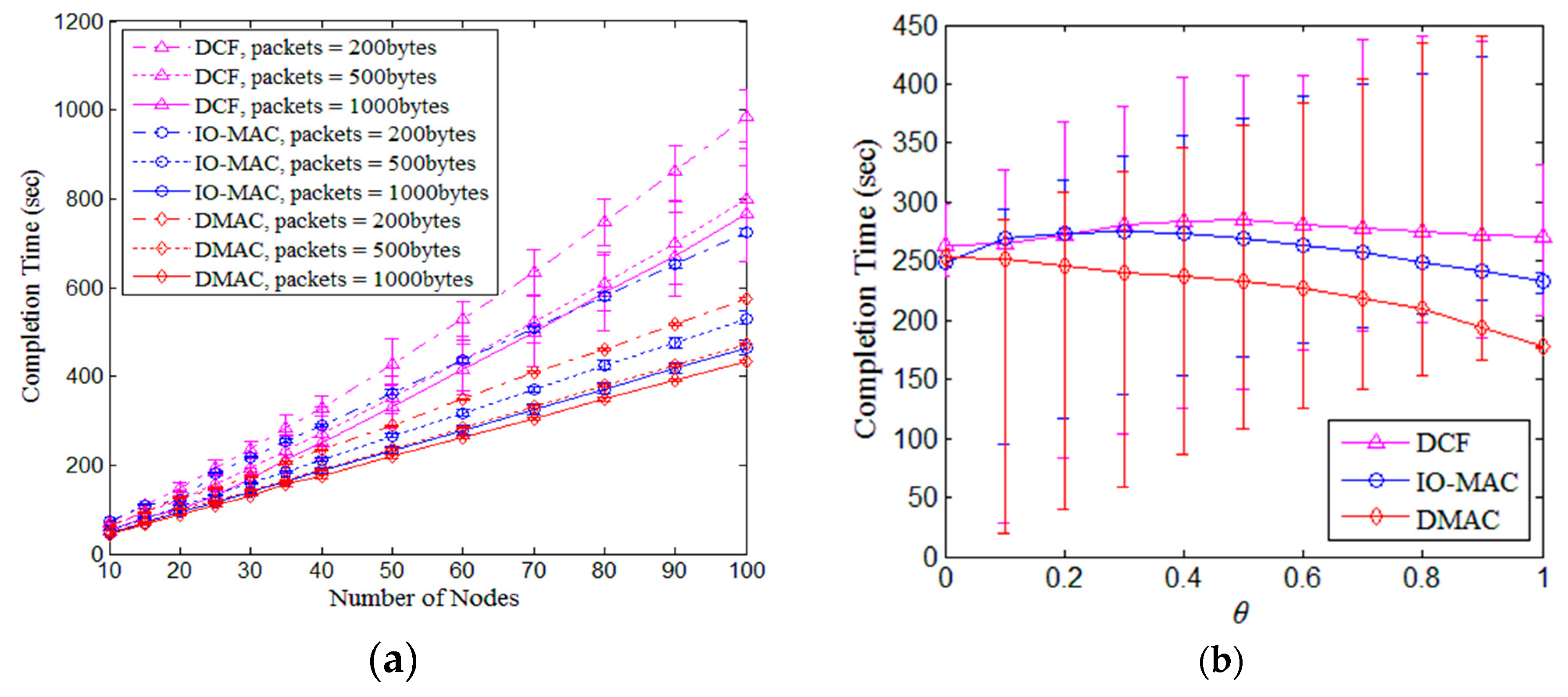
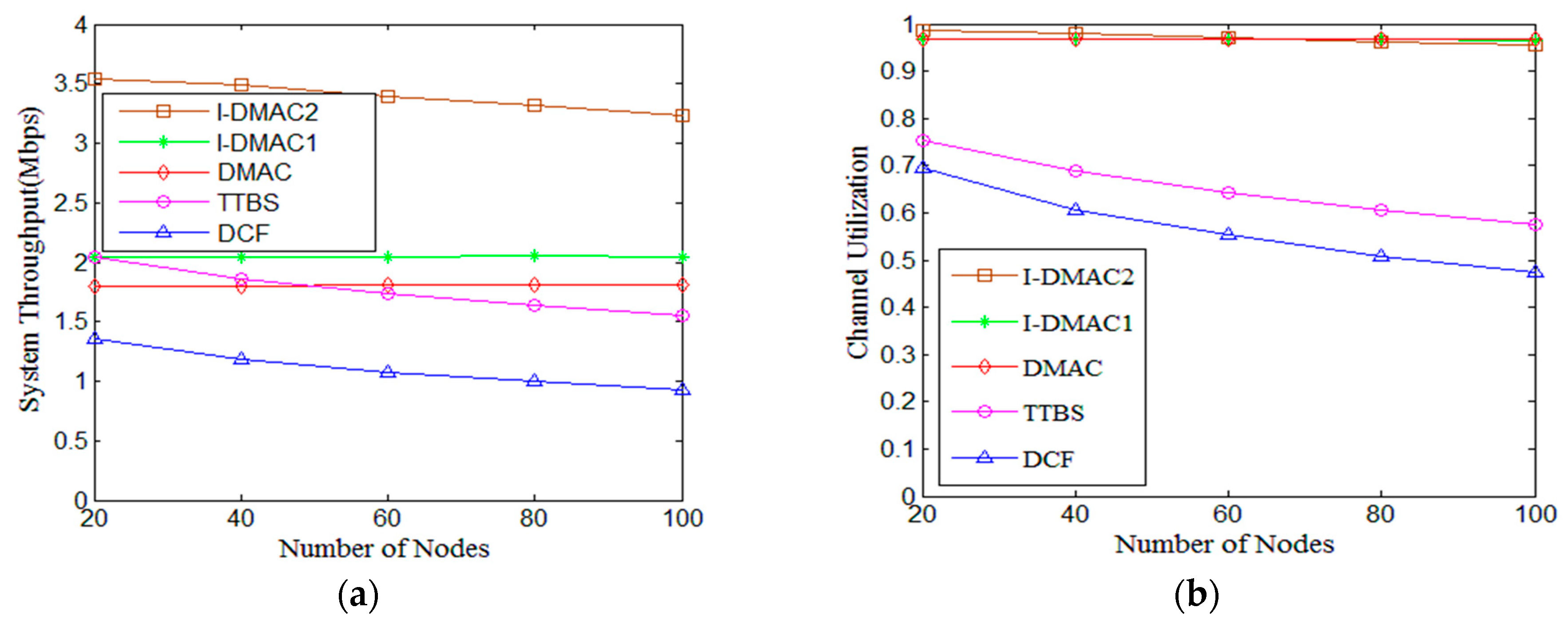
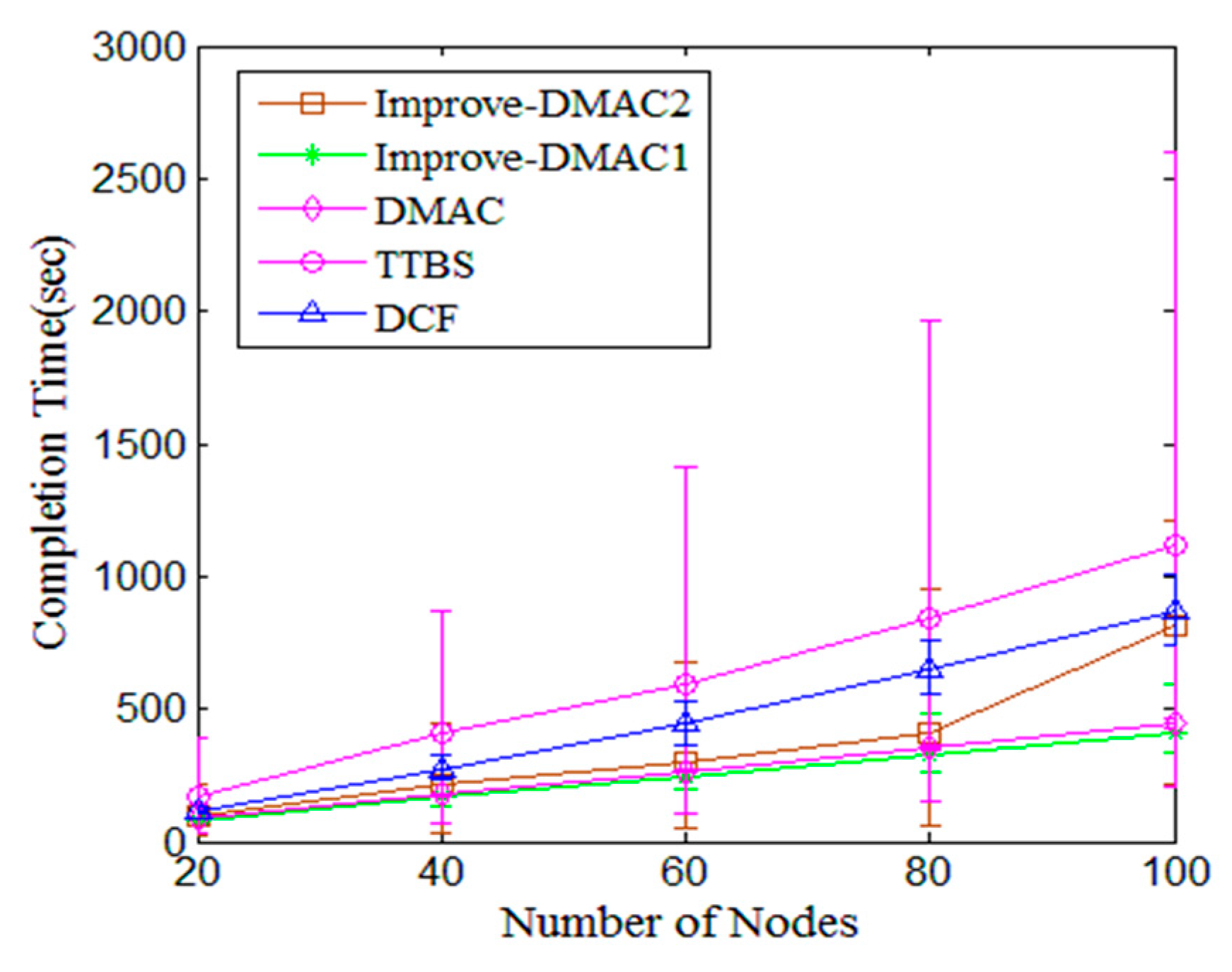
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| Packet_Payload | 200,500,1000 bytes | Slot_Time | 20 us |
| MAC_Header | 224 bits | DIFS | 50 us |
| PHY_Header | 192 bits | SIFS | 10 us |
| Data_Frame_Rate | 2 Mbps | ACK | 128 bits |
| Simulation_Time | 1800 s | DTR | 160 bits |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lei, J.; Wang, Y.; Yun, H. Decoupling-Based Channel Access Mechanism for Improving Throughput and Fairness in Dense Multi-Rate WLANs. Future Internet 2020, 12, 3. https://doi.org/10.3390/fi12010003
Lei J, Wang Y, Yun H. Decoupling-Based Channel Access Mechanism for Improving Throughput and Fairness in Dense Multi-Rate WLANs. Future Internet. 2020; 12(1):3. https://doi.org/10.3390/fi12010003
Chicago/Turabian StyleLei, Jianjun, Ying Wang, and Hong Yun. 2020. "Decoupling-Based Channel Access Mechanism for Improving Throughput and Fairness in Dense Multi-Rate WLANs" Future Internet 12, no. 1: 3. https://doi.org/10.3390/fi12010003
APA StyleLei, J., Wang, Y., & Yun, H. (2020). Decoupling-Based Channel Access Mechanism for Improving Throughput and Fairness in Dense Multi-Rate WLANs. Future Internet, 12(1), 3. https://doi.org/10.3390/fi12010003





