Multi-Authority Revocable Access Control Method Based on CP-ABE in NDN
Abstract
:1. Introduction
2. Related Works
3. Design and Implementation of Access Control Method
3.1. Overall Design of Access Control Method
- 1.
- Central Authorization Center (CA)
- 2.
- Attribute Authorization Centers (Hereinafter abbreviated as AA or )
- 3.
- Content Publisher
- 4.
- NDN cache nodes
- 5.
- Content Consumer
3.2. Access Control Method Implementation
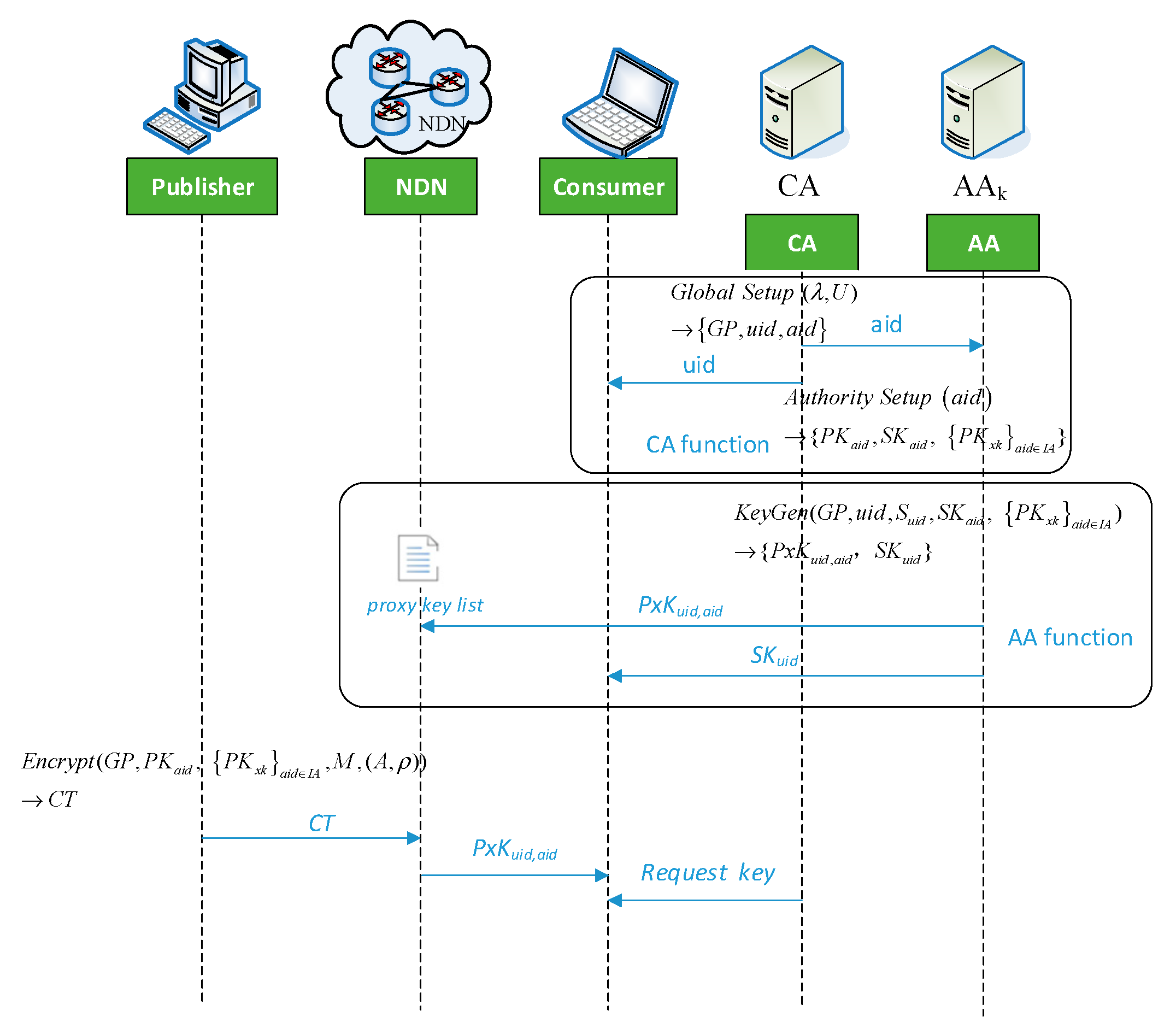
3.2.1. System Initialization
- 1.
- Global Setup
- 2.
- Authority Setup ()→
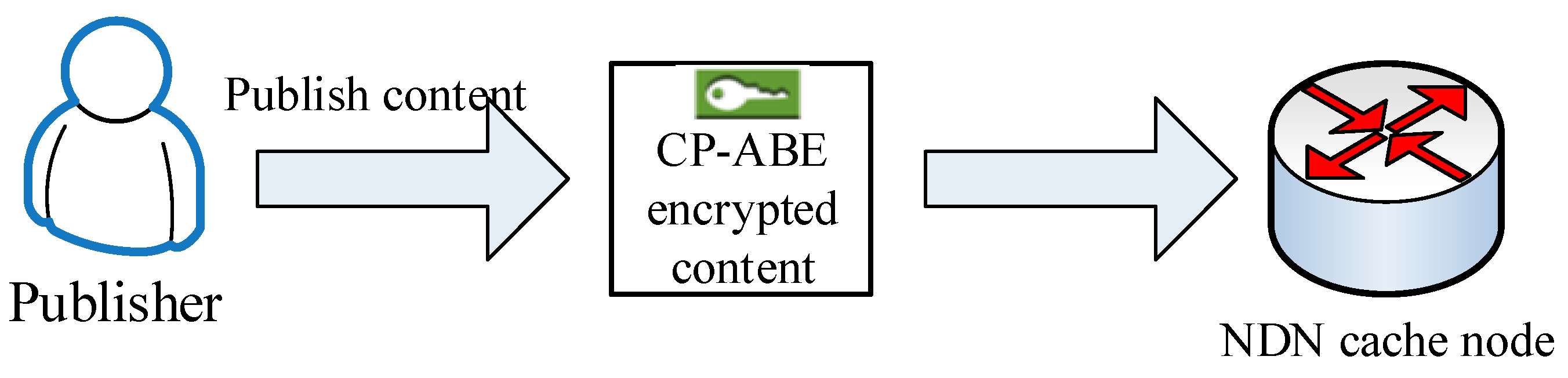
3.2.2. Content Publishing Process
- 3.
- Encrypt
- 4.
- KeyGen
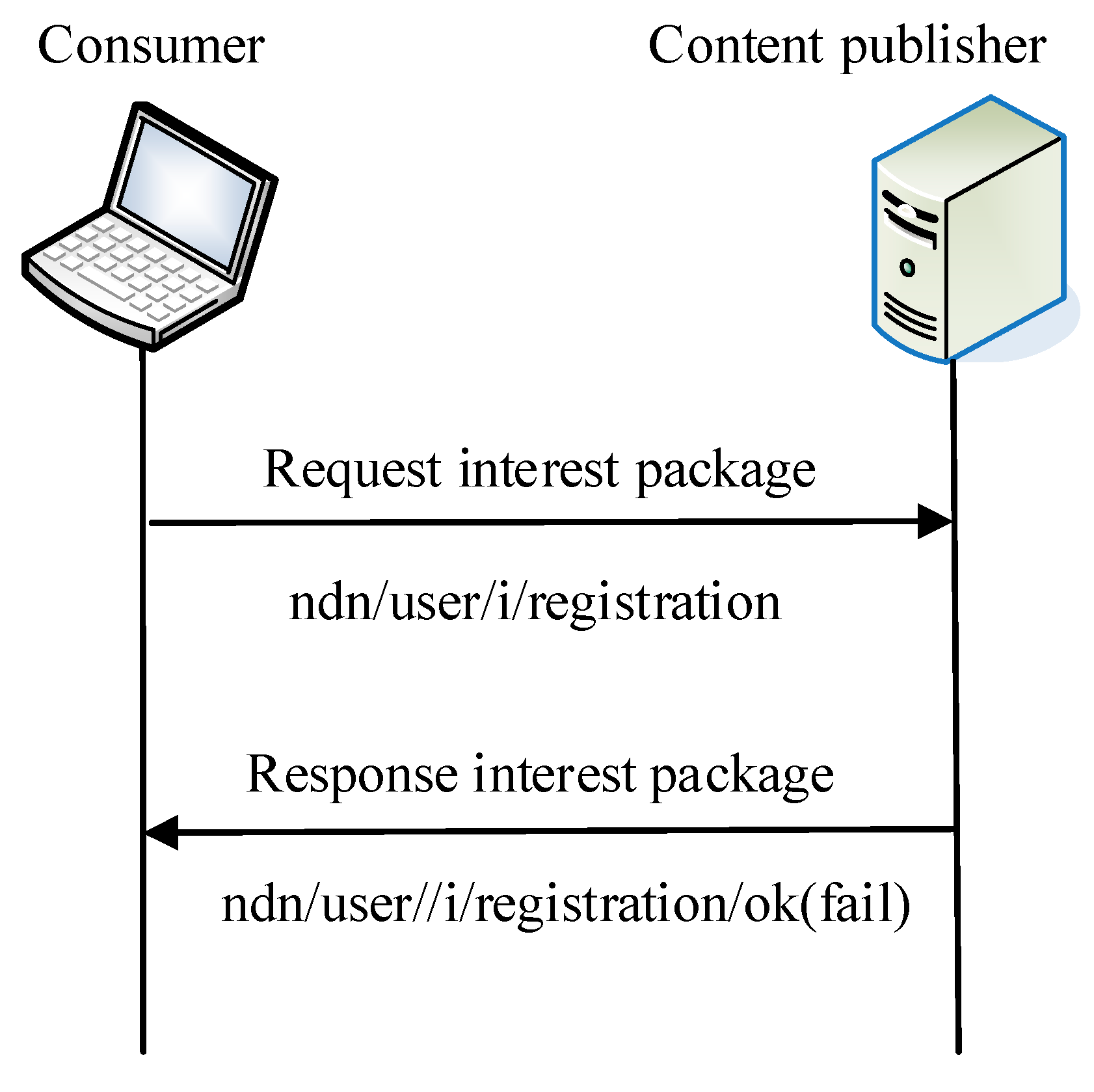
3.2.3. Content Request Process
- 5.
- PxDecry
- 6.
- Udecrypt
3.3. Revocation of Consumer Privilege
Consumer Attribute Revocation
- 7.
- The key update
- ReKeyUpdate
- PxKUpdate
- 8.
- The ciphertext re-encrypted
- CTUpdate
- ReEnc
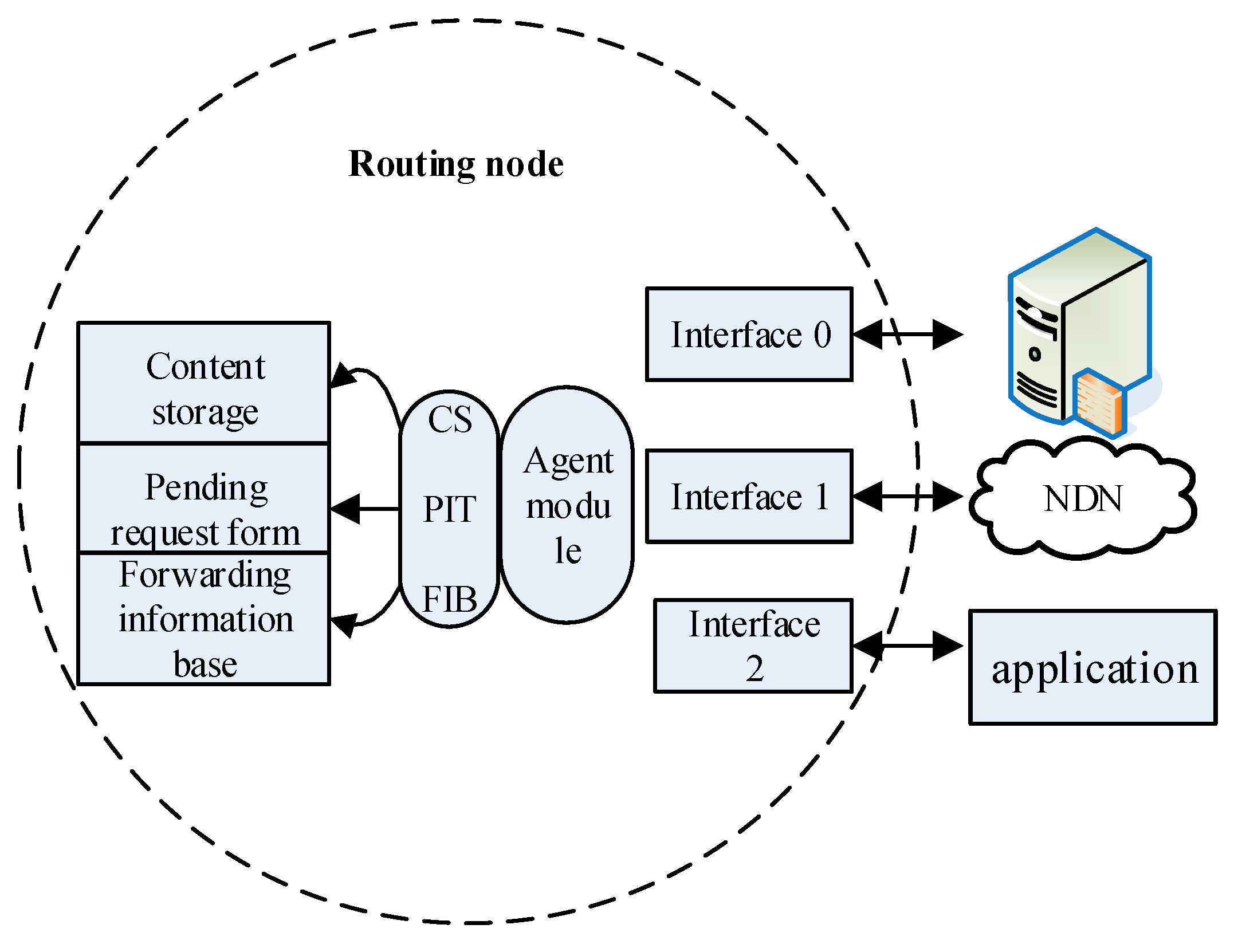
3.4. NDN Router
4. Security Analysis
4.1. Confidentiality of Data
4.2. Forward Security and Post Security
4.3. Collusion Attack
5. Analysis of Performance
5.1. Flexibility Analysis
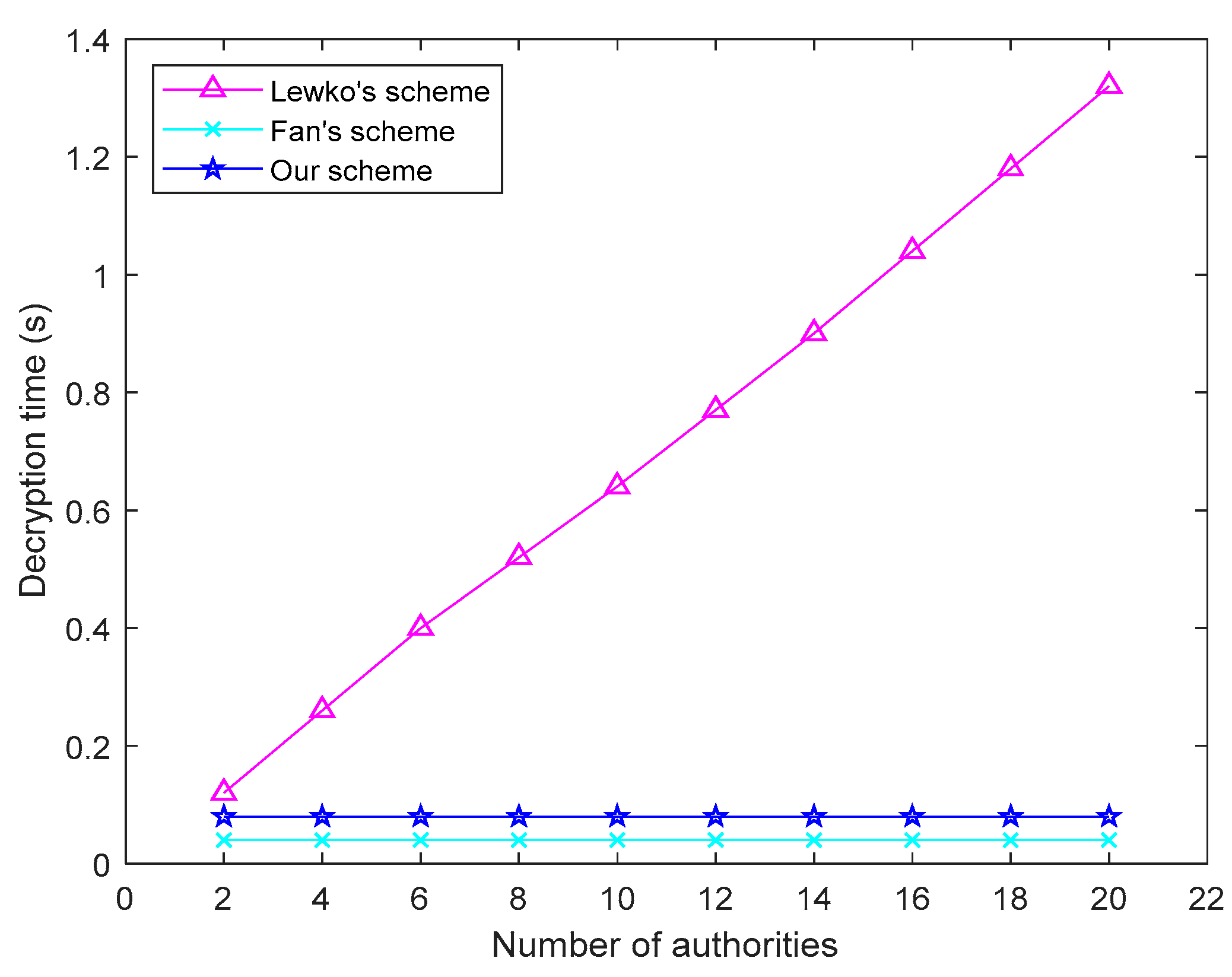
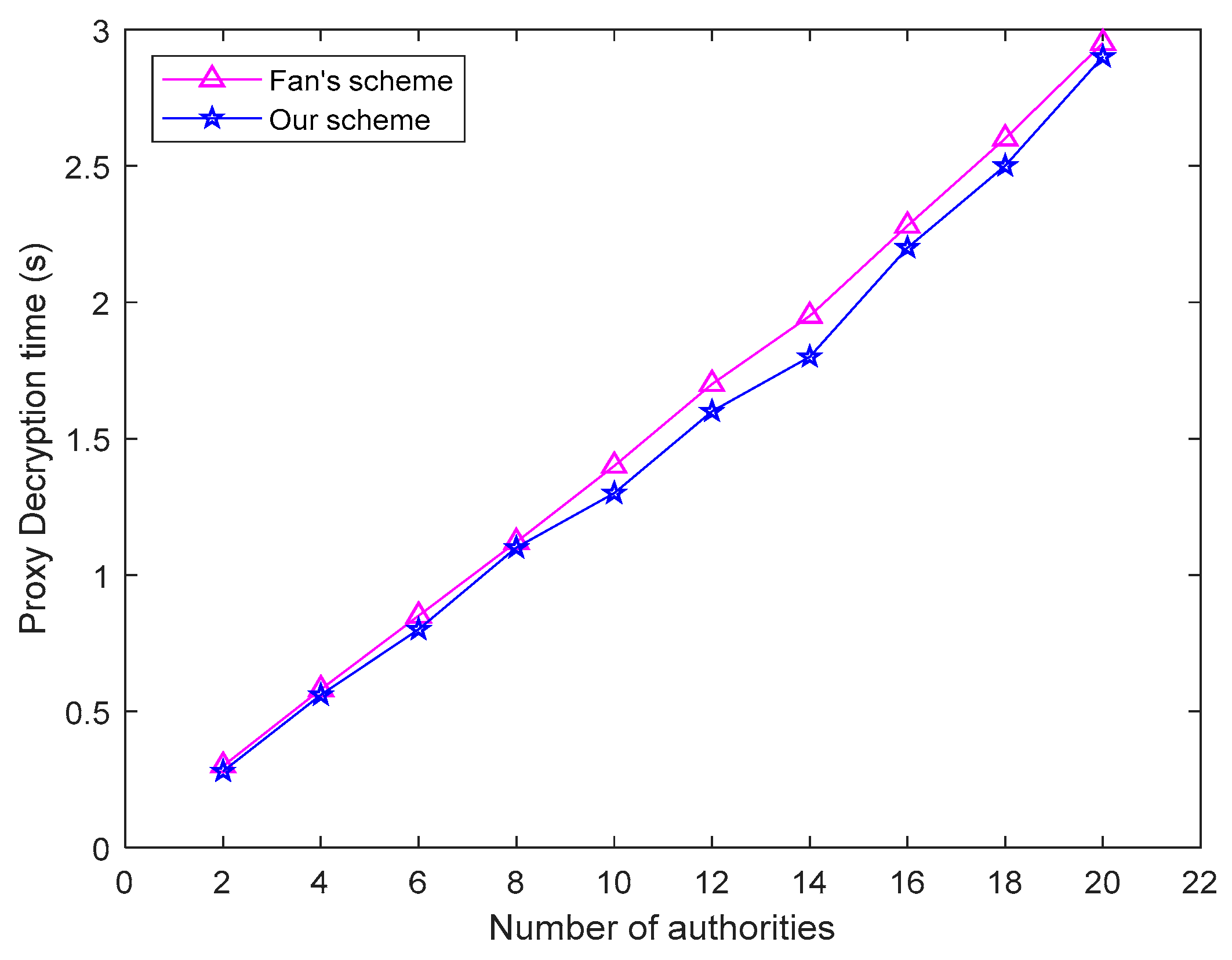
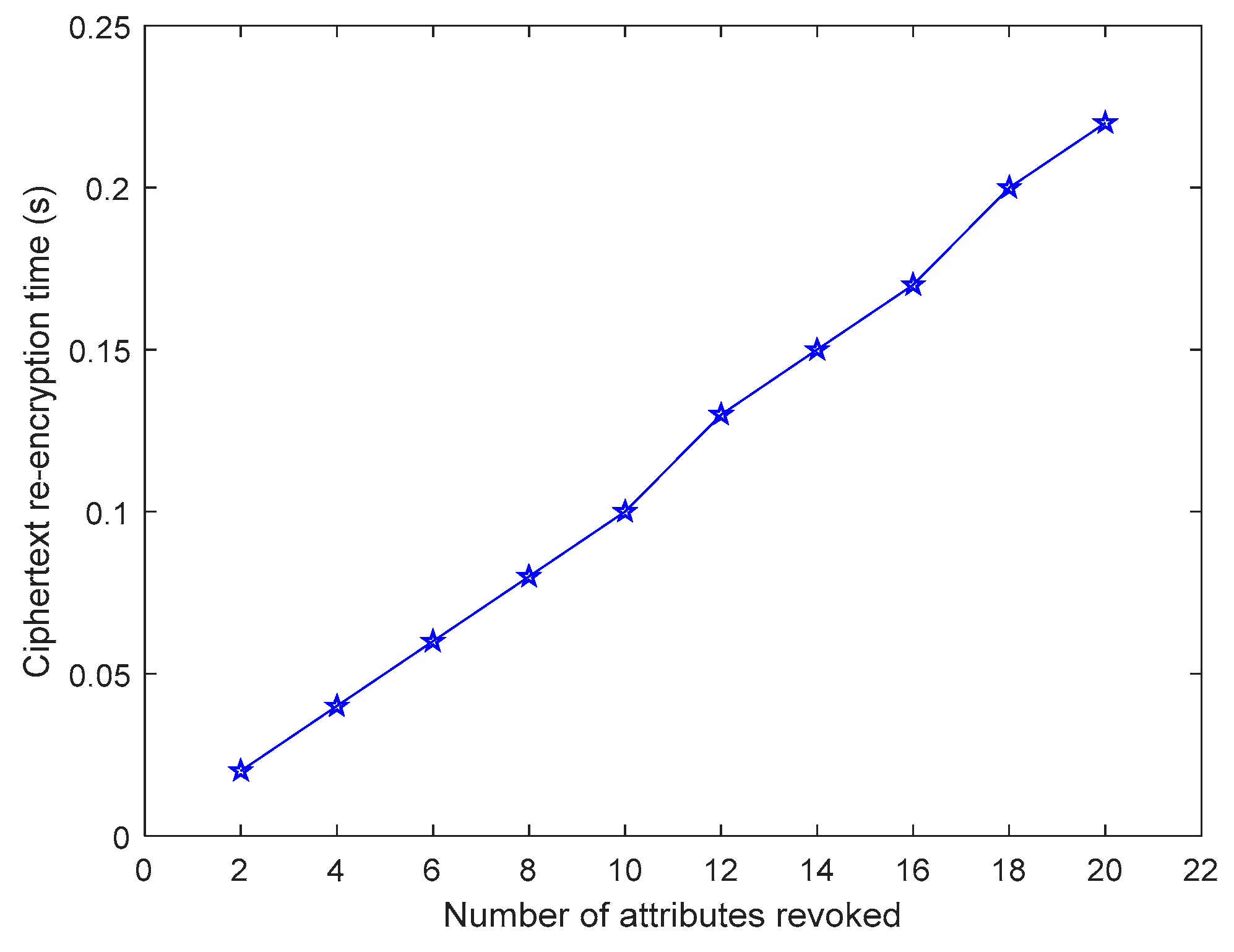
5.2. Calculation Overhead
5.3. Efficiency Analysis
6. Summary
Author Contributions
Funding
Conflicts of Interest
References
- George, X.; Christopher, N.; Vasilios, A. A Survey of Information-Centric Networking Research. IEEE Commun. Surv. Tutor. 2014, 16, 1024–1049. [Google Scholar]
- Wu, Z.; Xu, E.; Liu, L.; Yue, M. CHTDS: A CP-ABE Access Control Scheme Based on Hash Table and Data Segmentation in NDN. In Proceedings of the 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), Rotorua, New Zealand, 5–8 August 2019. [Google Scholar]
- Cisco, V.N.I. Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, Cisco Public Information. 2014. Available online: https://www.researchgate.net/publication/313629843_Cisco_Visual_Networking_Index_Global_Mobile_Data_Traffic_Forecast_Update_2014-2019 (accessed on 15 January 2020).
- Li, Q.; Zhang, X.; Zheng, Q.; Sandhu, R.; Fu, X. LIVE: Lightweight integrity verification and content access control for named data networking. IEEE Trans. Inf. Forensics Secur. 2015, 10, 308–320. [Google Scholar] [CrossRef]
- Da Silva, R.S.; Zorzo, S.D. An access control mechanism to ensure privacy in named data networking using attribute-based encryption with immediate revocation of privileges. In Proceedings of the 2015 12th Annual IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 9–12 January 2015. [Google Scholar]
- Psaras, I.; Chai, W.K.; Pavlou, G. Probabilistic in network caching for information-centric networks. In Proceedings of the Second Edition of the ICN Workshop on Information-Centric Networking, Helsinki, Finland, 17 August 2012; pp. 55–60. [Google Scholar]
- Chaabane, A.; De Cristofaro, E.; Kaafar, M.A.; Uzun, E. Privacy in content-oriented networking: threats and countermeasures. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 25–33. [Google Scholar] [CrossRef]
- Callas, J. Identity-Based Encryption with Conventional Public-Key Infrastructure. In Proceedings of the 4th Annual PKI R&D Workshop (No. 7224, pp. 102–115). Available online: http://p-fb.net/fileadmin/_migrated/content_uploads/callas-conventional_ibe.pdf (accessed on 15 January 2020).
- Sahai, A.; Waters, B. Fuzzy identity based encryption. In Proceedings of the 24th Annual International Conference on Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October 2006; pp. 89–98. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Chase, M.; Chow, S.S. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM conference on Computer and communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 121–130. [Google Scholar]
- Fan, K.; Wang, J.; Wang, X.; Li, H.; Yang, Y. Secure, efficient and revocable data sharing scheme for vehicular fogs. Peer-to-Peer Netw. Appl. 2018, 11, 766–777. [Google Scholar] [CrossRef]
- Hur, J.; Noh, D.K. Attribute-Based Access Control with Efficient Revocation in Data Outsourcing Systems. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 1214–1221. [Google Scholar] [CrossRef]
- Yang, K.; Jia, X. Attributed-based access control for multi-authority systems in cloud storage. In Proceedings of the 2012 32nd IEEE International Conference on Distributed Computing Systems, Macau, China, 18–21 June 2012; pp. 536–545. [Google Scholar]
- Yang, K.; Jia, X. Expressive, efficient, and revocable data access control for multi-authority cloud storage. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1735–1744. [Google Scholar] [CrossRef]
- Fan, K.; Wang, J.; Wang, X.; Yang, Y. Proxy-assisted access control scheme of cloud data for smart cities. Pers. Ubiquitous Comput. 2017, 21, 1–11. [Google Scholar] [CrossRef]
- Li, B.; Huang, D.; Wang, Z.; Zhu, Y. Attribute-based access control for ICN naming scheme. IEEE Trans. Dependable Secur. Comput. 2018, 15, 194–206. [Google Scholar] [CrossRef]
- Feng, T.; Guo, J. A New Access Control System Based on CP-ABE in Named Data Networking. Int. Netw. Secur. 2018, 20, 710–720. [Google Scholar]
- Lewko, A.; Waters, B. Decentralizing attribute-based encryption. In Advances in Cryptology-EUROCRYPT 2011. EUROCRYPT 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 568–588. [Google Scholar]
- Qian, H.; Li, J.; Zhang, Y.; Han, J. Privacy-preserving personal health record using multi-authority attribute-based encryption with revocation. Int. J. Inf. Secur. 2015, 14, 487–497. [Google Scholar] [CrossRef]
- Wu, G.Q. Multi-Authority CP-ABE with Policy Update in Cloud Storage. J. Comput. Res. Dev. 2016, 53, 2393–2399. [Google Scholar]

| Program | Access Structure | Authorization Center Type | Can Resist Collusion Attacks | Authority Revocation |
|---|---|---|---|---|
| Tao [19] | LSSS | Multiple authorization center | Yes | Indirect revocation |
| Silva [5] | Tree structure | Single authorization center | Yes | User revocation |
| Lewko [20] | LSSS | Multiple authorization center | Yes | No |
| Li [18] | Tree structure | Single authorization center | Yes | No |
| This article | LSSS | Multiple authorization center | Yes | Direct revocation |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Z.; Zhang, Y.; Xu, E. Multi-Authority Revocable Access Control Method Based on CP-ABE in NDN. Future Internet 2020, 12, 15. https://doi.org/10.3390/fi12010015
Wu Z, Zhang Y, Xu E. Multi-Authority Revocable Access Control Method Based on CP-ABE in NDN. Future Internet. 2020; 12(1):15. https://doi.org/10.3390/fi12010015
Chicago/Turabian StyleWu, Zhijun, Yun Zhang, and Enzhong Xu. 2020. "Multi-Authority Revocable Access Control Method Based on CP-ABE in NDN" Future Internet 12, no. 1: 15. https://doi.org/10.3390/fi12010015
APA StyleWu, Z., Zhang, Y., & Xu, E. (2020). Multi-Authority Revocable Access Control Method Based on CP-ABE in NDN. Future Internet, 12(1), 15. https://doi.org/10.3390/fi12010015





