Importance Assessment of Distribution Network Nodes Based on an Improved MBCC-HITS Algorithm
Abstract
1. Introduction
2. DCHITS Algorithm
2.1. MBCC-HITS Algorithm
2.2. DCHITS Algorithm
2.2.1. Grid Topological Factor
2.2.2. Grid Flow Factor
2.2.3. Load and Power Supply Factor
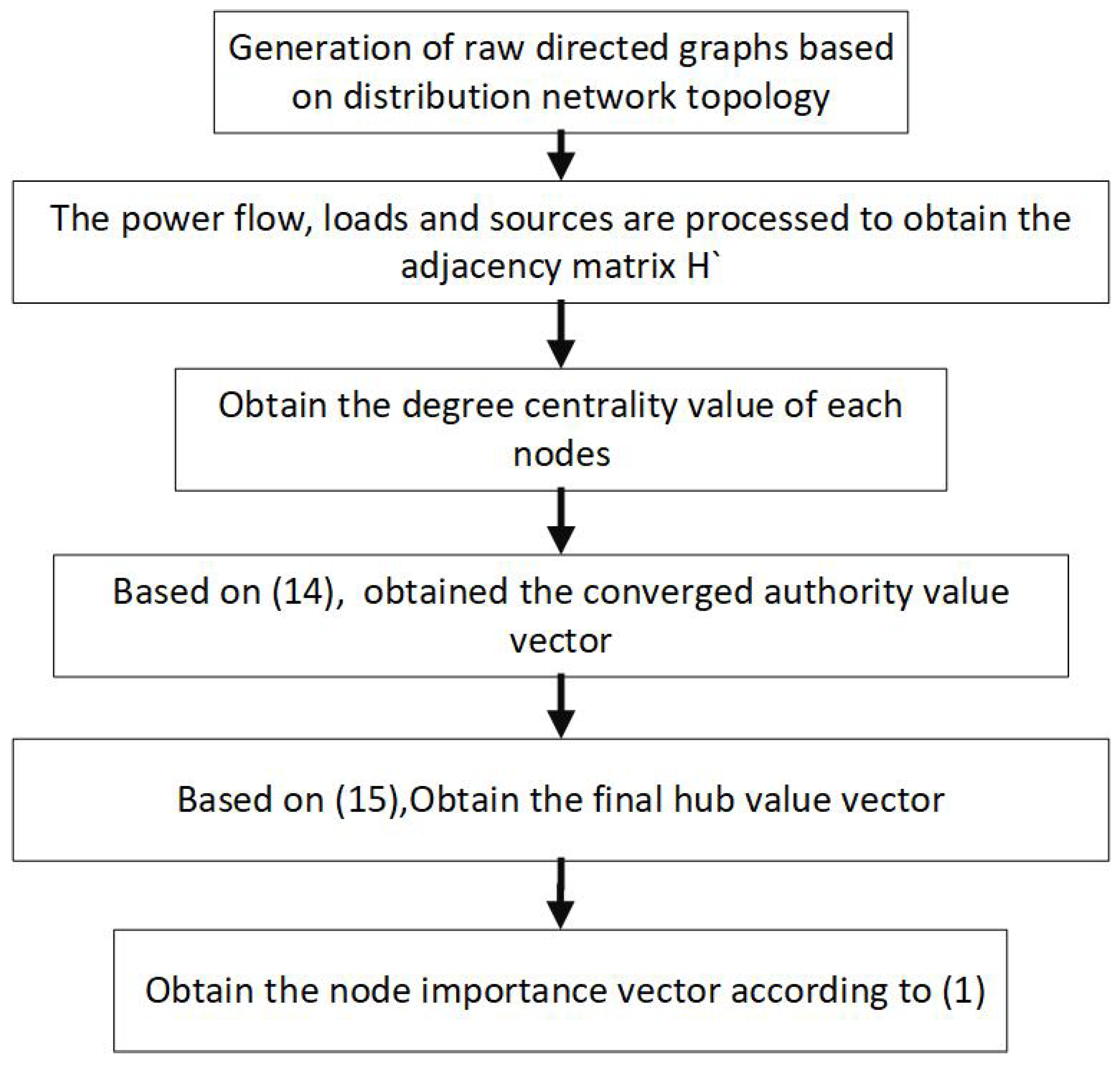
3. DCHITS Algorithm Evaluation Process
- Obtain the initial directed graph based on the topology of the power system;
- Add power and load nodes to the diagram and obtain the adjacency matrix H’ according to (16);
- According to (13), the degree centrality vector of each node is obtained;
- The converged authority value vector is obtained by iterating according to (14), which is the final authority value vector;
- Substitute the converged authority values into Equation (15) to obtain the final hub value vector;
- According to (1), the final authority value is added to the hub value to obtain the final result
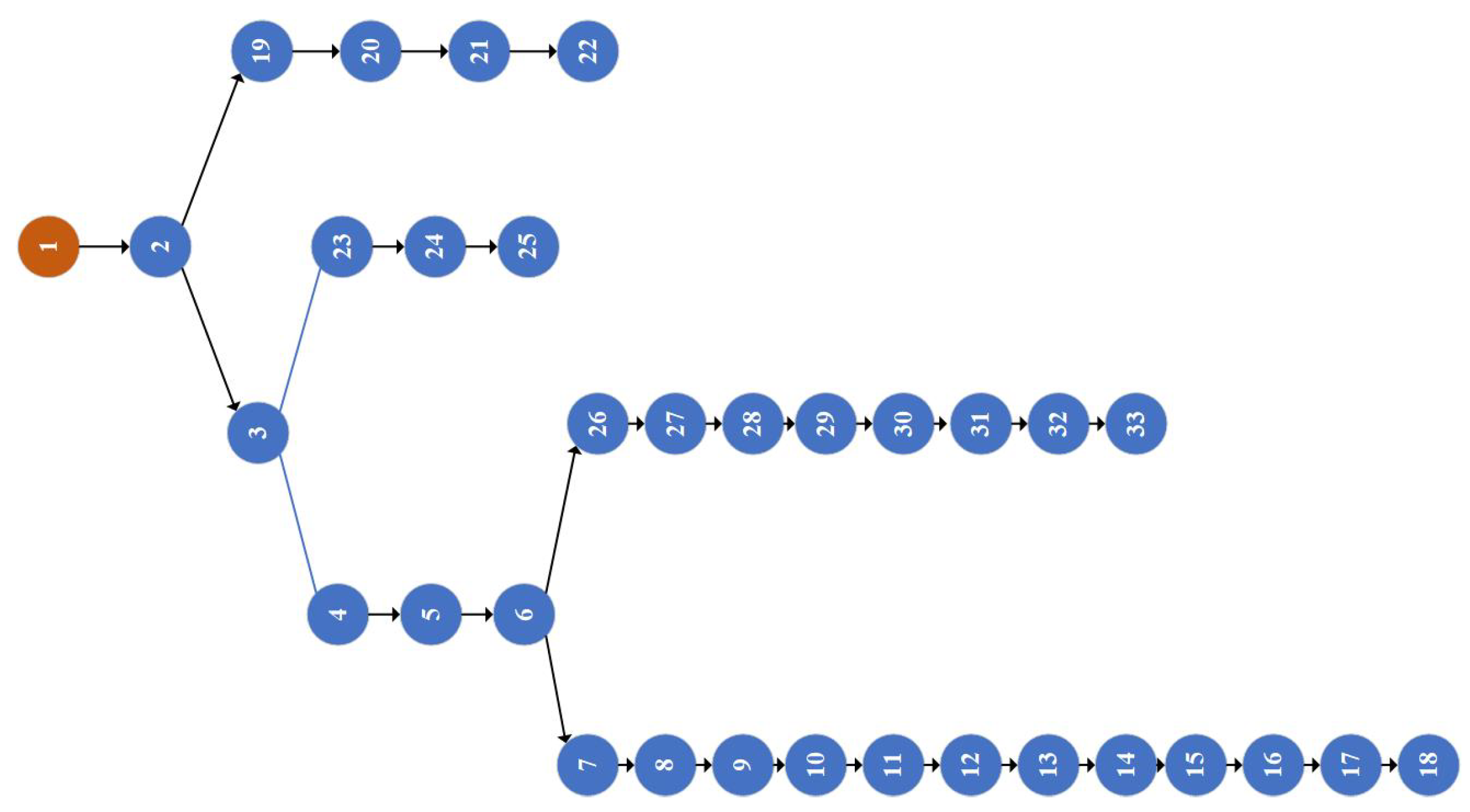
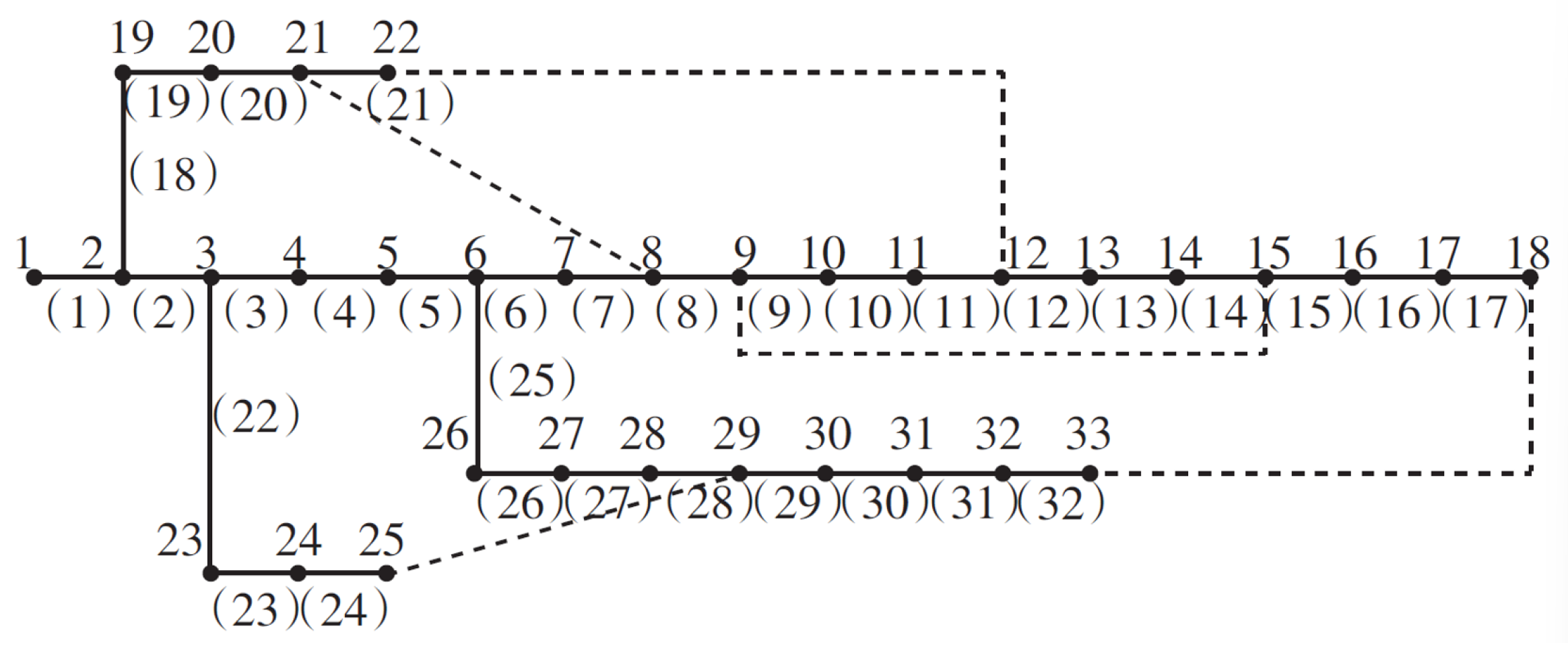
- Abstract the directed topology diagram of the IEEE33 node system shown in Figure 3. Among them, node 1 is a power supply node, and node 2 to node 33 are all load nodes;Figure 3. IEEE33 node system directed topology diagram.
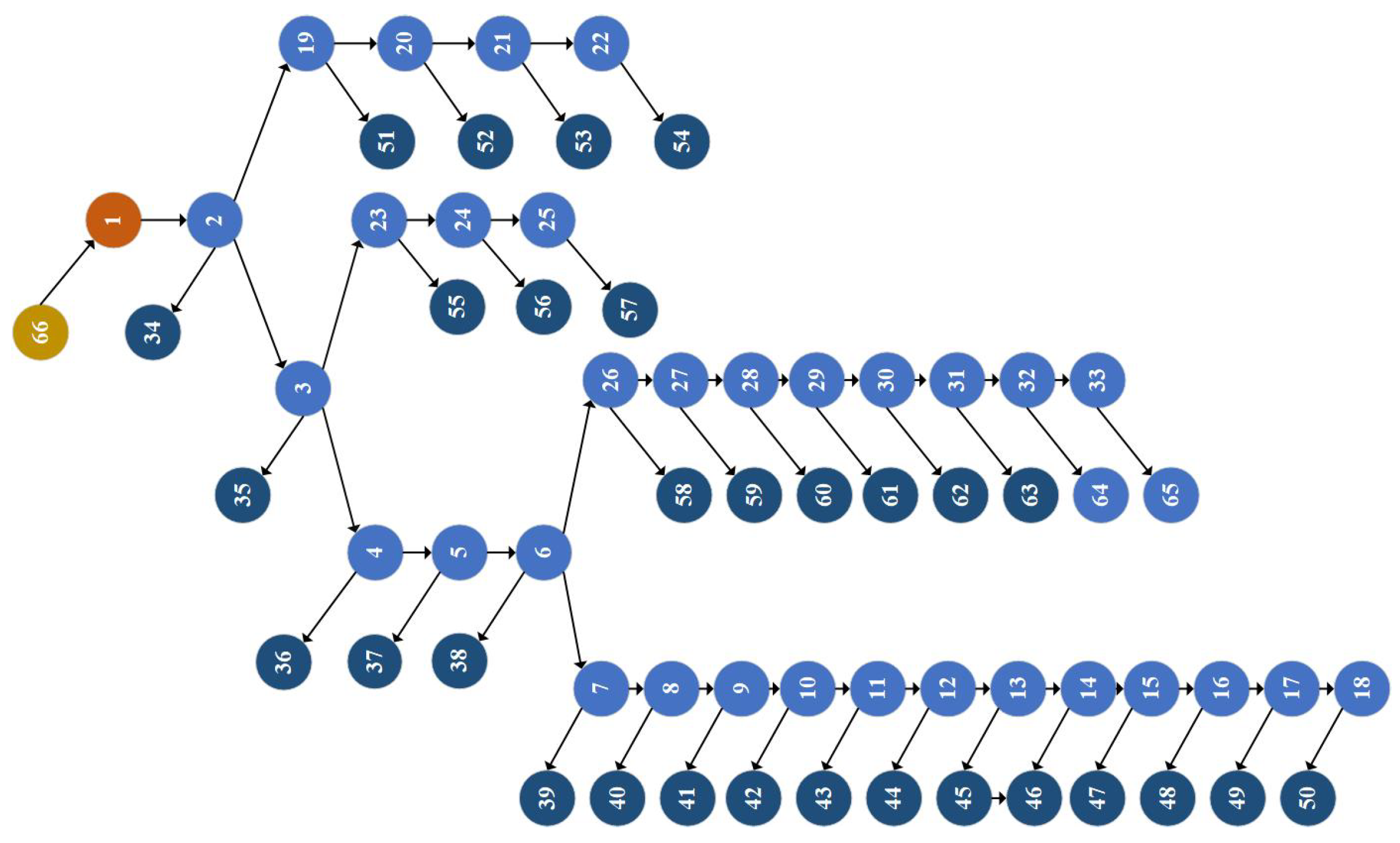
- The directed topology graph shown in Figure 4 is obtained by adding the power nodes and load nodes and the corresponding adjacency matrix H’ can be further obtained from this topology graph;Figure 4. IEEE33 node system directed topology diagram.
- The degree centrality vector is obtained for each node of the system based on the degree centrality formula and the directed topology graph after adding power and negative nodes, denoted as C;
- The final authority and hub value vectors are obtained through (14) and (15), respectively, and are summed to obtain the results of the importance assessment of each node of the IEEE33 node system.
4. Evaluation Indicators
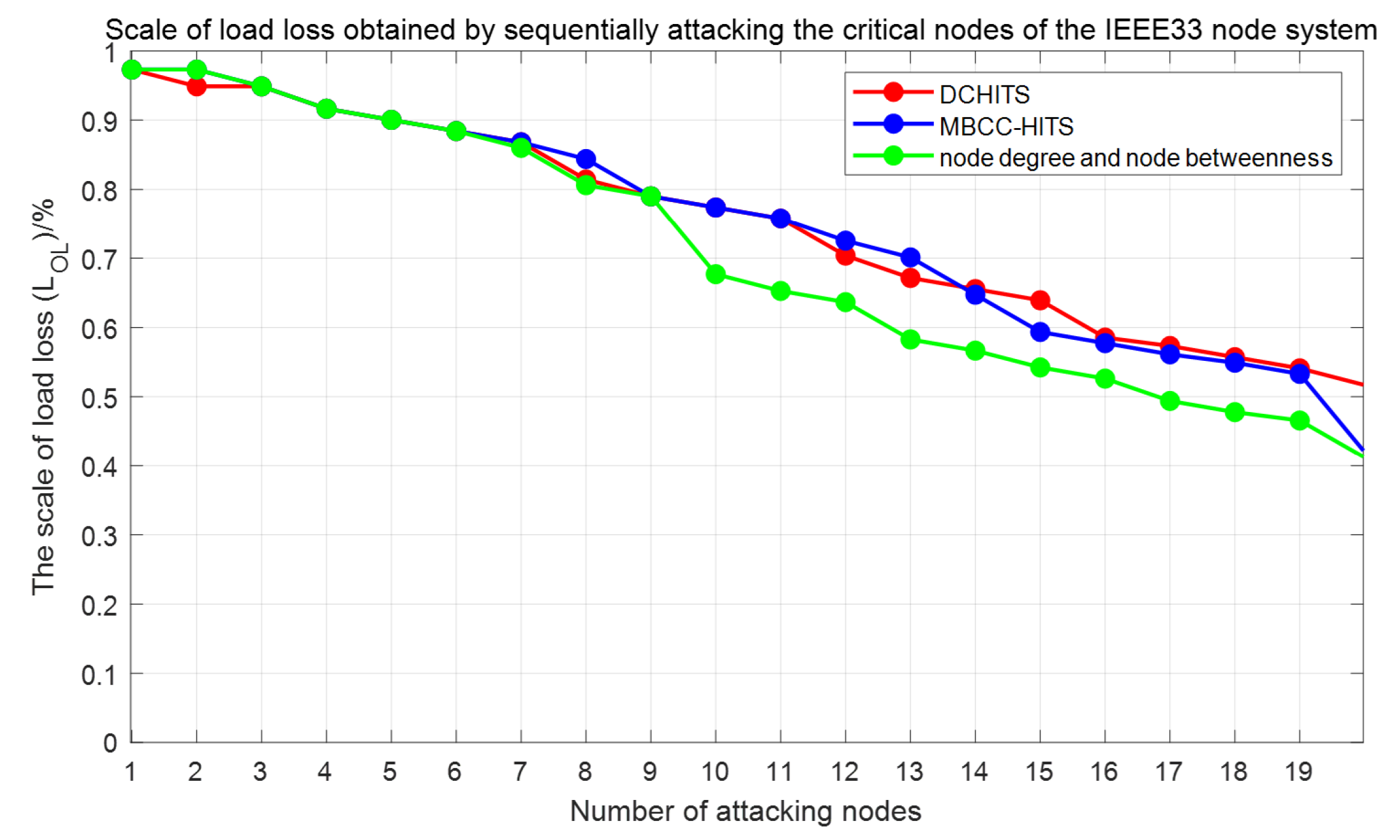
4.1. The Scale of Load Loss
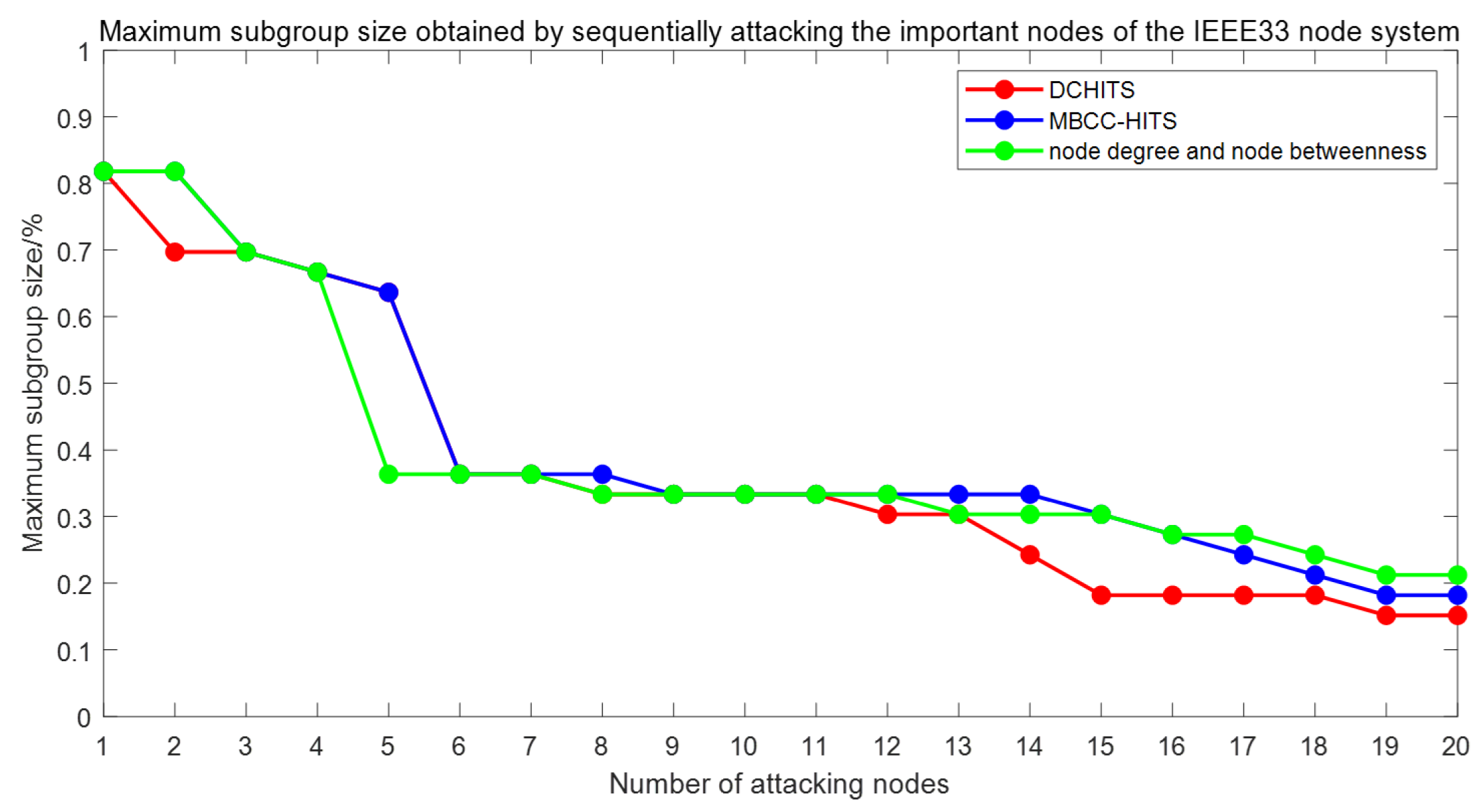
4.2. The Maximum Subgroup Size
5. Experimental Results and Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lu, G.; Deng, J.; Wang, Y.H.; Cao, J.; Yue, Y.F. Analysis of Power System Affected by Extreme Weather and Its Adaptive Strategy. Power Gener. Technol. 2021, 42, 751–764. [Google Scholar] [CrossRef]
- Pan, L.; Hu, Y.; Yang, J.; Wei, X.; Yang, X. Research on the Risk Resilience Assessment of Distribution Network Under Typhoon Weather. Microcomput. Appl. 2024, 40, 247–256. [Google Scholar]
- Chen, B.; Liao, J. Technology for Improving Distribution Network Disaster-Prevention Capabilities for Intercurrent Natural Disasters Areas Under Extreme Weather: Review and Prospect. Electr. Power Constr. 2025, 46, 107–121. [Google Scholar]
- Wang, L.; Tang, J.; Huang, Y.; Wang, K.; Jian, Z. Risk zone assessment of rainstorm induced waterlogging associated outage of distribution system with consideration of micro-topography. J. Electr. Power Sci. Technol. 2024, 39, 84–92. [Google Scholar] [CrossRef]
- Ruan, Q.; Xie, W.; Xu, Y.; Hua, B.; Song, P.; He, J.; Zhang, Q. Concept and key features of resilient power grids. Proc. CSEE 2020, 40, 6773–6784. [Google Scholar] [CrossRef]
- Li, L.; An, Z.; Zhang, S.; Xiao, Z.; Li, Z. Research and prospect on key technologies of resilient power grid. Electr. Meas. Instrum. 2024, 61, 8–16. [Google Scholar] [CrossRef]
- Albert, R.; Albert, I.; Nakarado, G.L. Structural vulnerability of the North American power grid. Phys. Rev. E 2004, 69, 025103. [Google Scholar] [CrossRef] [PubMed]
- Yu, Q.; Ying, Q.; Cao, N.; He, J.; Sun, W.; Zhang, X. Risk Assessment of Online Public Opinion on Power Grid Outage Incidents Based on Attribute Mathematical Theory. Power Syst. Technol. 2025, 49, 719–726. [Google Scholar] [CrossRef]
- Shi, W. Study of Distribution Network Vulnerability Assessment Method Based on Distribution Information. Proc. CSU-EPSA 2018, 30, 125–131. [Google Scholar] [CrossRef]
- Ju, J.; Zhao, J.; Yang, K. Identification of key nodes in distribution networks considering data-driven power flow model. Water Resour. Hydropower Eng. 2023, 54, 26–36. [Google Scholar] [CrossRef]
- Li, Y. Research on Vulnerability Assessment Method of Distribution Network. Master’s Thesis, Shandong University of Technology, Zibo, China, 2022. [Google Scholar] [CrossRef]
- Liu, W. Research and Application of Distribution Network Reliability Considering Distributed Generation. Master’s Thesis, Guangdong University of Technology, Guangzhou, China, 2020. [Google Scholar] [CrossRef]
- Wang, H.; Shan, Z.; Ying, G. Evaluation method of node importance for power grid considering inflow and outflow power. J. Mod. Power Syst. Clean Energy 2017, 5, 696–703. [Google Scholar] [CrossRef]
- Geng, J.; Sun, X.; Song, H.; Qu, Y. Important node evaluation algorithm for electrical power system inspired by internet thinking. J. Natl. Univ. Def. Technol. 2023, 45, 211–218. [Google Scholar] [CrossRef]
- Duan, H.; Guo, C.; Chen, F. Assessment of vulnerable nodes in active distribution networks based on improved K-shell mixed degree decomposition method. J. Electr. Power Sci. Technol. 2025, 40, 67–76. [Google Scholar] [CrossRef]
- Yan, H.; Ma, G.; Qian, Y. Degree-Centrality Based Feature Selection. Data Collect. Process. 2019, 34, 312–321. [Google Scholar] [CrossRef]
- Gibson, D.; Kleinberg, J.; Raghavan, P. Inferring web communities from link topology. In Proceedings of the Ninth ACM Conference on Hypertext and Hypermedia, Pittsburgh, PA, USA, 20–24 June 2019; Volume 1998, pp. 225–234. [Google Scholar] [CrossRef]
- Kleinberg, J.M. Authoritative sources in a hyperlinked environment. J. ACM (JACM) 1999, 46, 604–632. [Google Scholar] [CrossRef]
- Yue, X.; Zhu, T.H. A Model Based on Cocitation for Web Information Retrieval. Math. Probl. Eng. 2014, 2014, 418605. [Google Scholar] [CrossRef]
- Wang, K.; Zhang, B.; Zhang, Z.; Yin, X.; Wang, B. An electical betweenness approach for vulnerability assessment of power grids considering the capacity of generators and load. Phys. A Stat. Mech. Appl. 2011, 390, 4692–4701. [Google Scholar] [CrossRef]
| Node Number | Ranking | |
|---|---|---|
| 2 | 1.0063 | 1 |
| 3 | 0.9086 | 2 |
| 1 | 0.8047 | 3 |
| 4 | 0.6661 | 4 |
| 5 | 0.5525 | 5 |
| 6 | 0.4419 | 6 |
| 26 | 0.2346 | 7 |
| 7 | 0.2018 | 8 |
| 23 | 0.1951 | 9 |
| 27 | 0.1802 | 10 |
| 28 | 0.1633 | 11 |
| 8 | 0.1455 | 12 |
| 29 | 0.1191 | 13 |
| 10 | 0.1081 | 14 |
| 12 | 0.0903 | 15 |
| 30 | 0.0901 | 16 |
| 11 | 0.0796 | 17 |
| 9 | 0.0712 | 18 |
| 13 | 0.0708 | 19 |
| 19 | 0.0631 | 20 |
| 14 | 0.0537 | 21 |
| 15 | 0.0485 | 22 |
| 24 | 0.0421 | 23 |
| 16 | 0.0368 | 24 |
| 31 | 0.0287 | 25 |
| 20 | 0.0285 | 26 |
| 17 | 0.0237 | 27 |
| 32 | 0.0215 | 28 |
| 21 | 0.0156 | 29 |
| 25 | 0.0130 | 30 |
| 18 | 0.0068 | 31 |
| 22 | 0.0067 | 32 |
| 33 | 0.0050 | 33 |
| Ranking | DCHITS | MBCC-HITS | Node Degree and Node Betweenness |
|---|---|---|---|
| 1 | 2 | 2 | 2 |
| 2 | 3 | 1 | 1 |
| 3 | 1 | 3 | 3 |
| 4 | 4 | 4 | 4 |
| 5 | 5 | 5 | 6 |
| 6 | 6 | 6 | 5 |
| 7 | 26 | 23 | 23 |
| 8 | 7 | 26 | 7 |
| 9 | 23 | 7 | 26 |
| 10 | 27 | 27 | 24 |
| 11 | 28 | 28 | 19 |
| 12 | 8 | 29 | 27 |
| 13 | 29 | 19 | 8 |
| 14 | 10 | 30 | 28 |
| 15 | 12 | 8 | 20 |
| 16 | 16 | 9 | 9 |
| 17 | 17 | 10 | 29 |
| 18 | 18 | 11 | 10 |
| 19 | 19 | 12 | 11 |
| 20 | 20 | 24 | 30 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, J.; Chang, Z.; Zhang, W.; Rong, H.; Zeng, T. Importance Assessment of Distribution Network Nodes Based on an Improved MBCC-HITS Algorithm. Algorithms 2025, 18, 589. https://doi.org/10.3390/a18090589
Wu J, Chang Z, Zhang W, Rong H, Zeng T. Importance Assessment of Distribution Network Nodes Based on an Improved MBCC-HITS Algorithm. Algorithms. 2025; 18(9):589. https://doi.org/10.3390/a18090589
Chicago/Turabian StyleWu, Jie, Zhengwei Chang, Wei Zhang, Haina Rong, and Tingting Zeng. 2025. "Importance Assessment of Distribution Network Nodes Based on an Improved MBCC-HITS Algorithm" Algorithms 18, no. 9: 589. https://doi.org/10.3390/a18090589
APA StyleWu, J., Chang, Z., Zhang, W., Rong, H., & Zeng, T. (2025). Importance Assessment of Distribution Network Nodes Based on an Improved MBCC-HITS Algorithm. Algorithms, 18(9), 589. https://doi.org/10.3390/a18090589