1. Introduction
Computer viruses represent a significant and ever-growing threat to cybersecurity in an increasingly digital world. These malicious programs are designed to self-replicate, spreading from one system to another by attaching themselves to legitimate files or software. Unlike different types of malware, such as worms or Trojans, viruses typically require some form of user interaction to execute and begin their propagation [
1,
2]. The consequences of a virus infection can be devastating, ranging from the corruption and loss of critical data and system failures to substantial financial losses, widespread operational disruption, and severe breaches of privacy [
3,
4]. In today’s interconnected world, the impact of a successful virus attack can ripple outward, affecting individuals, organizations, and even critical infrastructure. The evolution of computer viruses has been marked by a steady increase in complexity and sophistication. Early viruses, such as the Creeper program of the 1970s, were relatively harmless, often serving as experimental projects [
5]. However, these early examples quickly gave way to more malicious creations. Notable viruses like Stuxnet demonstrated the potential for viruses to inflict massive economic damage and even target critical infrastructure, highlighting the real-world consequences of these digital threats [
6]. Modern viruses employ increasingly sophisticated techniques to evade detection and maintain persistence within digital environments. For example, polymorphic and metamorphic viruses dynamically alter their code, making it extremely difficult for traditional signature-based detection systems to identify and neutralize them [
7]. This constant evolution necessitates a continuous adaptation of cybersecurity defense mechanisms.
In the ongoing battle against computer viruses, studies have turned to mathematical modeling as a critical tool for understanding virus propagation and developing effective containment strategies [
8]. Drawing inspiration from biological epidemiology, various methods have been adapted from traditional epidemic models to analyze and predict the spread of viruses within computer networks [
9]. Among these, the Susceptible-Infected (SI) model is a widely used framework for examining virus behavior. However, the standard integer-order versions of these models often fall short when attempting to capture long-term dependencies and memory effects frequently observed in real-world cyber threats [
10]. Standard models frequently employ simplifications of intricate interactions and fail to account for the historical context of virus spread. This limitation has led to a growing interest in fractional-order models, which incorporate historical interactions and offer a more detailed and precise depiction of virus propagation [
11]. By integrating memory effects, fractional-order models offer a more realistic and powerful tool for predicting and mitigating the impact of evolving digital threats. In parallel, some studies have analyzed the spread of actual computer viruses such as Code Red, Slammer, Conficker, and Stuxnet, using parameterized statistical distributions to fit real outbreak data [
12]. These works provide a valuable benchmark for validating the qualitative behavior of theoretical models, including those based on fractional calculus.
Fractional calculus, extending classical calculus, extends differentiation and integration concepts to non-integer orders. This mathematical framework offers unique advantages for modeling complex systems by incorporating memory effects and hereditary properties [
13]. Unlike traditional integer-order derivatives, which analyze only local changes, fractional derivatives consider the influence of past events on the present and future behavior of a system [
14]. This property makes fractional calculus highly effective in studying systems with long-term dependencies, such as the spread of viruses in digital networks [
15]. The application of fractional calculus in mathematical modeling has gained traction within a diverse range of fields, notably physics, biology, engineering, and finance [
16]. In epidemiology and cybersecurity, fractional models have been particularly successful in capturing the history-dependent nature of disease and virus propagation [
17]. By incorporating fractional derivatives, it is possible to better understand how past infections influence current and future outbreaks, leading to more accurate predictive models [
18]. In discrete systems, fractional calculus provides a robust framework for analyzing systems that evolve in discrete time steps, making it highly suitable for modeling digital networks and computational processes. Unlike continuous-time models, which may not fully capture digital environments’ complexities, discrete fractional models offer a more precise approach to studying virus spread in cyberspace. These models account for the cumulative impact of previous infections, providing valuable insights into how viruses persist, adapt, and evolve over time [
19].
A fractional discrete SI model extends the classical SI model by incorporating fractional-order derivatives to capture long-term dependencies in virus transmission. While traditional SI models assume that the rate of infection relies solely on the information contained in the current system state, the fractional framework considers historical infection trends, leading to a more accurate representation of real-world virus behavior [
20]. The utilization of discrete fractional models in cybersecurity makes it possible to identify hidden patterns, predict outbreaks, and develop proactive defense mechanisms [
21]. By analyzing the system’s dynamics, one can determine the conditions under which a virus persists, dies out, or exhibits chaotic behavior [
22]. This insight is crucial for designing effective cybersecurity policies, intrusion detection systems, and digital defense strategies. Furthermore, nonlinear analysis, particularly bifurcation theory, is key to understanding the critical points where small changes in system parameters can lead to drastic shifts in behavior, such as the transition from stable infection dynamics to chaotic outbreaks. This allows for a more detailed exploration of how digital epidemics evolve and how they may be controlled or mitigated.
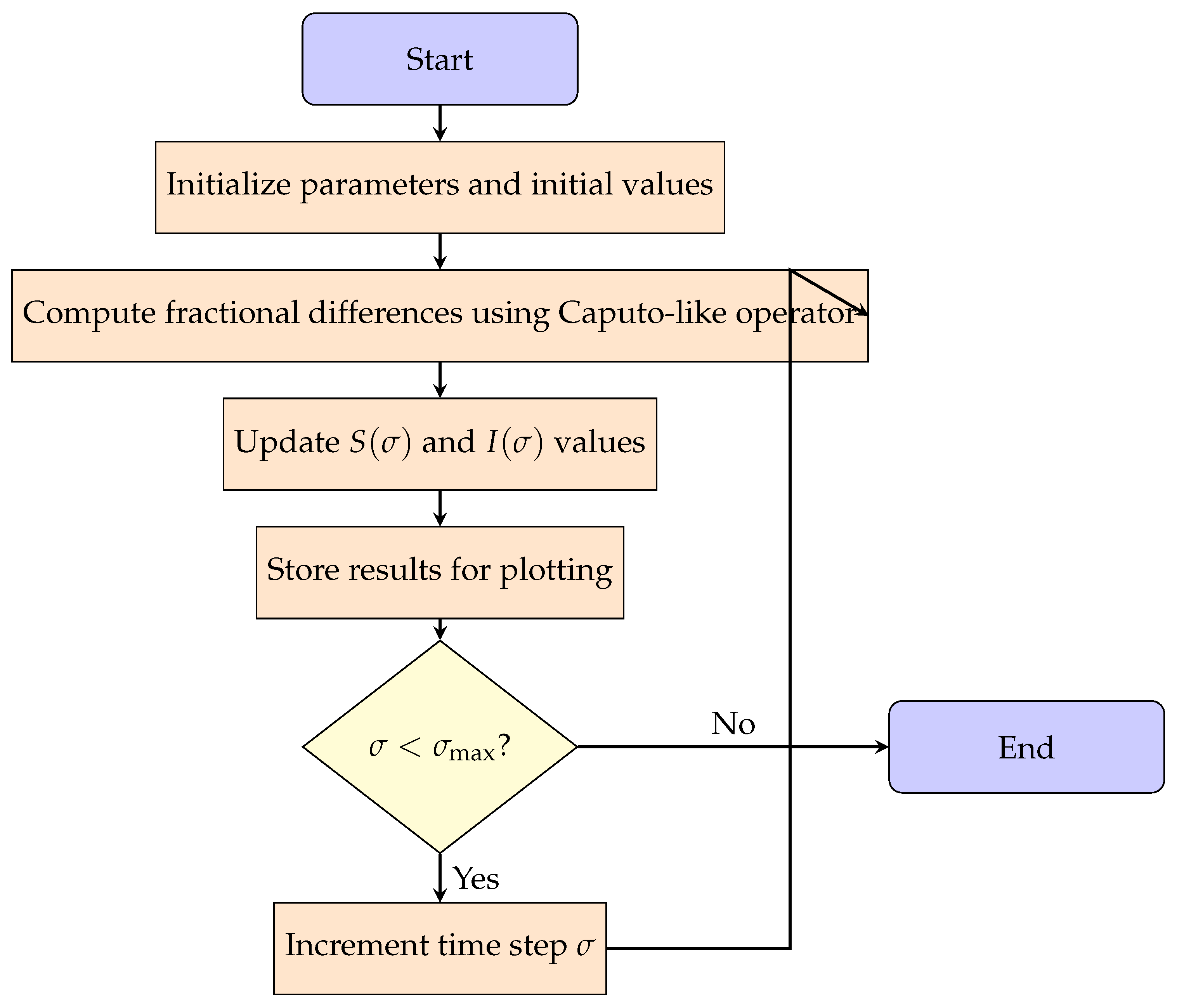
This research investigates the stability and chaotic dynamics of a susceptible-infected (SI) model for computer virus propagation with fractional discrete dynamics, using the Caputo-like difference operator. The key motivation behind this work lies in the growing challenge of controlling sophisticated computer viruses whose spread exhibits unpredictable and highly sensitive dynamics. Understanding such chaotic behavior is essential for designing robust and adaptive cybersecurity strategies. In this context, fractional calculus offers a powerful framework for modeling long-term dependencies and capturing non-local behavior that classical models may overlook. When a virus exhibits chaotic behavior, even minor variations in initial conditions can lead to drastically different outcomes, making prediction and control significantly more difficult. This study provides an in-depth analysis of the relationship between fractional calculus and chaotic dynamics, contributing to the development of more resilient digital defense mechanisms. Unlike normalized continuous-time fractional SIR models [
23], which use the Caputo derivative, our model employs a discrete-time Caputo-like fractional difference operator. This approach is more appropriate for modeling digital systems like computer virus spread, where interactions naturally occur at discrete time intervals. The novelty of our work lies in constructing a fractional discrete SI model with both commensurate and incommensurate fractional orders and uncovering its chaotic behavior using advanced nonlinear tools. To the best of our knowledge, our model is the first to explore chaotic dynamics in a discrete fractional SI framework with both commensurate and incommensurate orders. This analysis enables a deeper understanding of virus dynamics and offers insights for designing more robust cybersecurity mechanisms.
The main contributions of this work are as follows:
We derive the stability conditions of the proposed fractional discrete SI model using the basic reproduction number , which helps predict whether a virus outbreak will persist or die out.
We examine the influence of both commensurate and incommensurate fractional orders on the system’s dynamics, emphasizing their ability to capture memory effects in digital virus propagation.
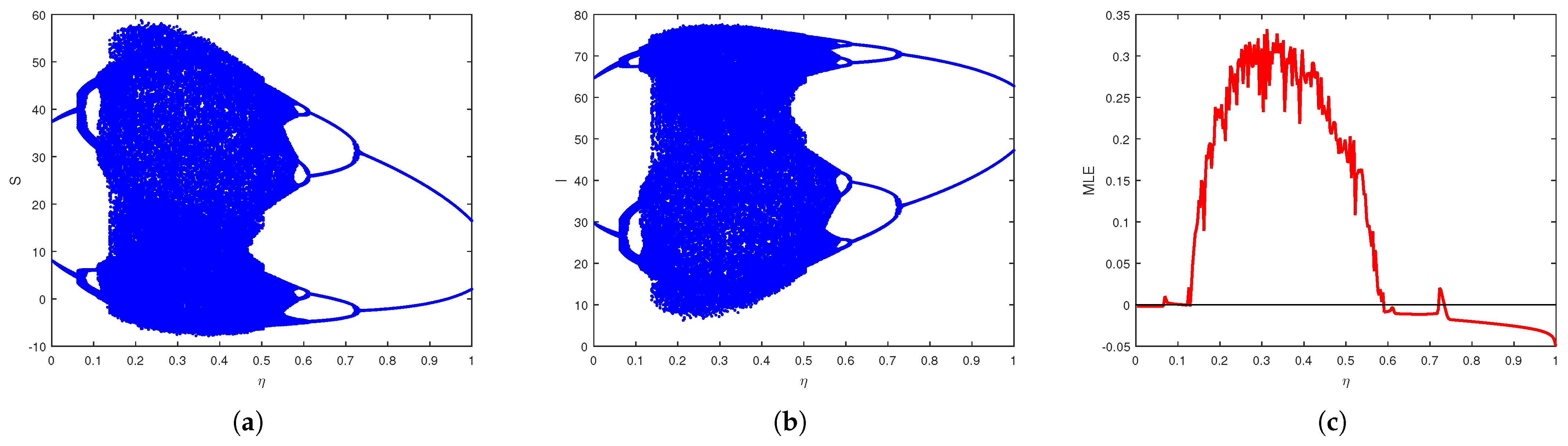
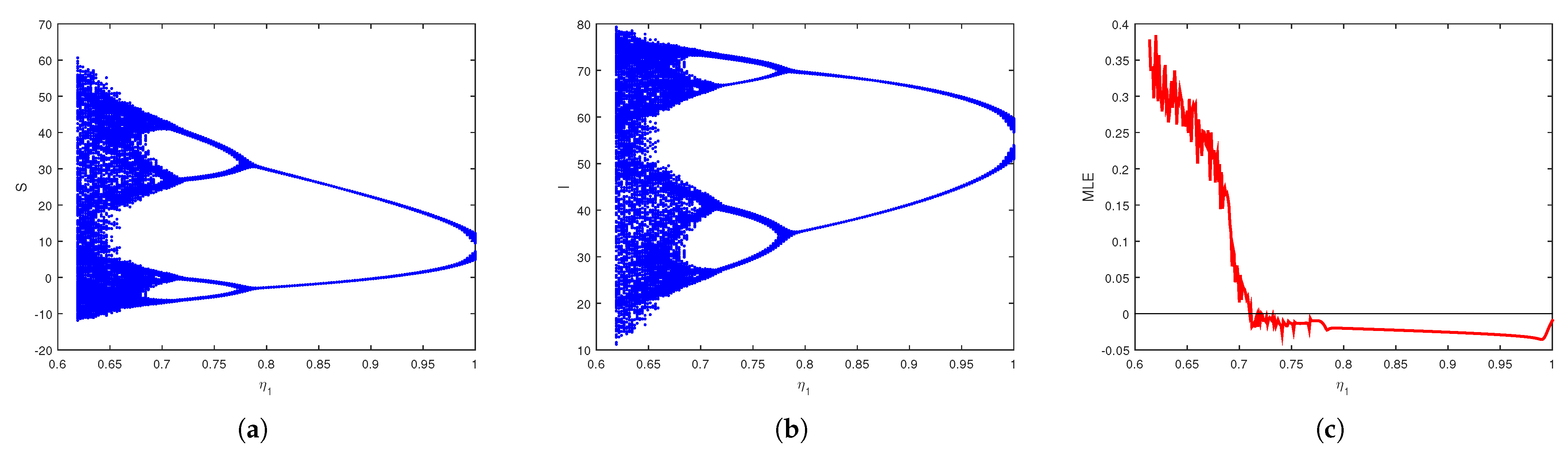
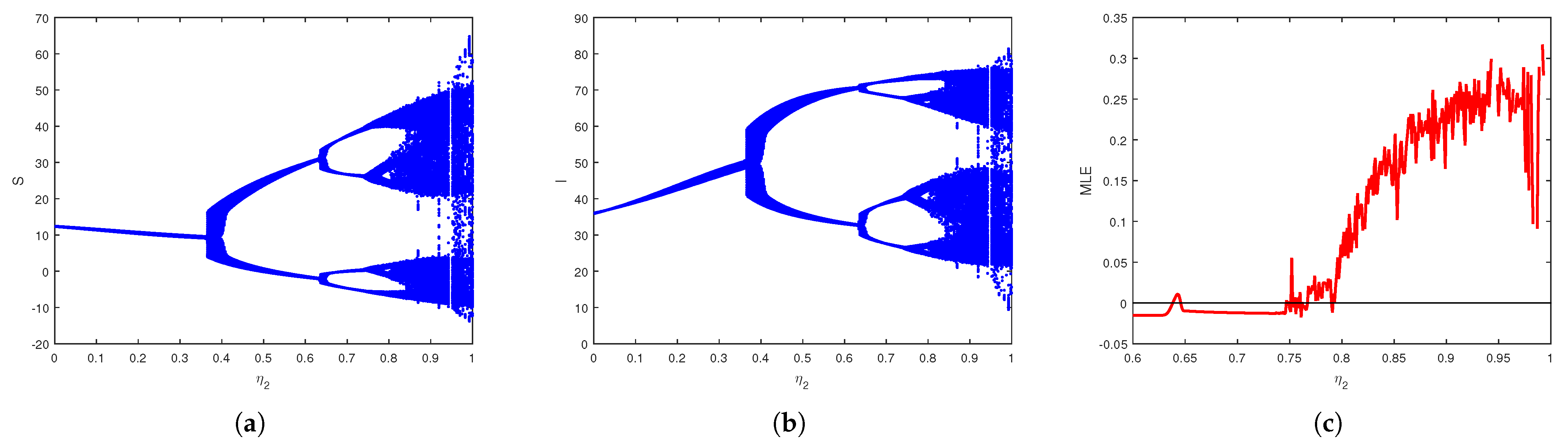
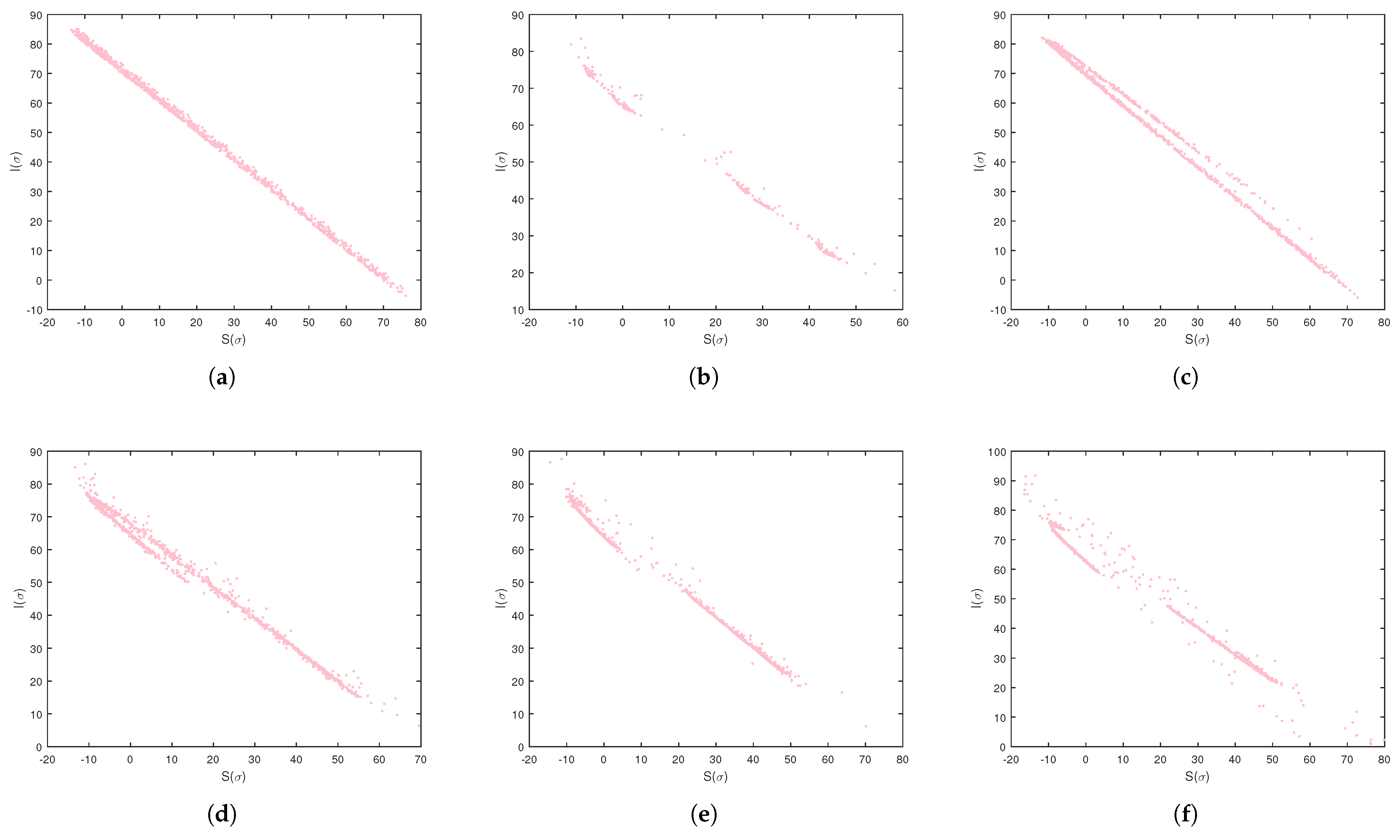
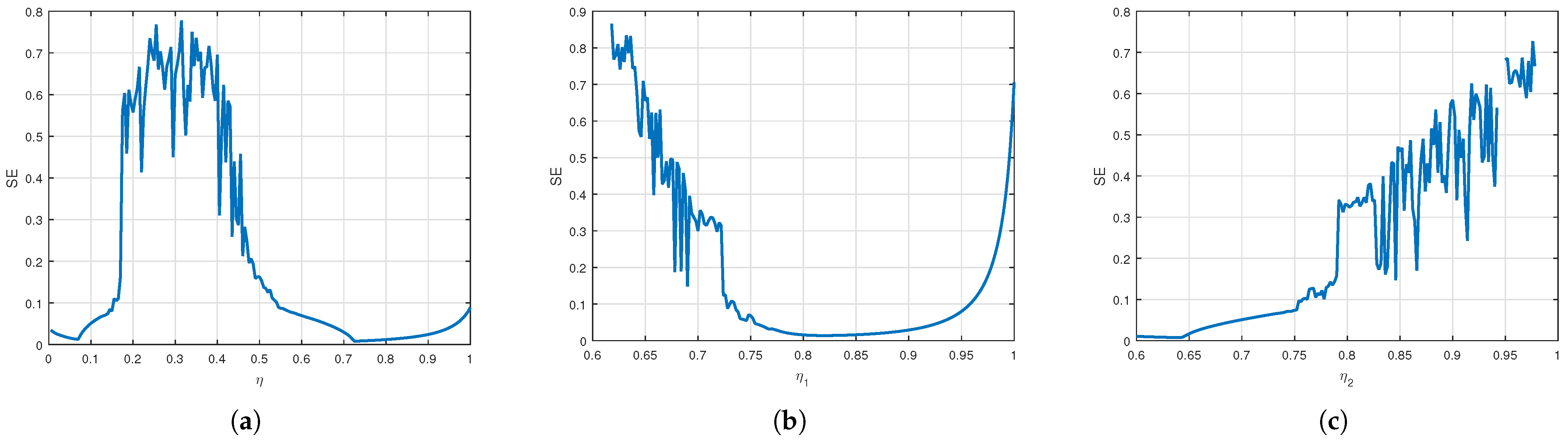
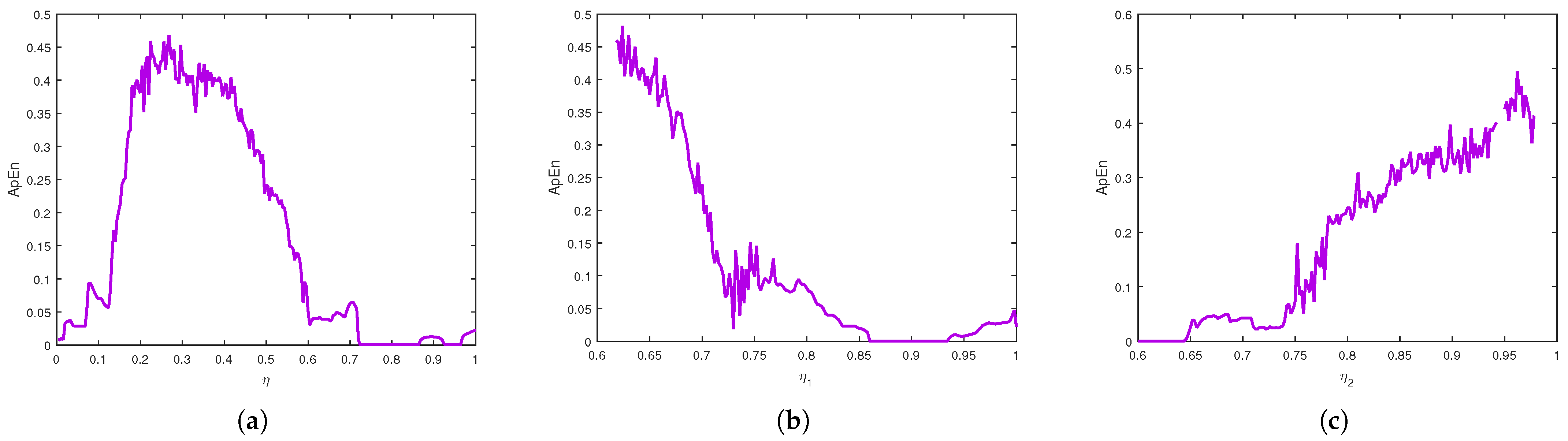
We apply several chaos detection and complexity analysis tools, including bifurcation diagrams, phase portraits, maximum Lyapunov exponents, spectral entropy, approximate entropy, and the test for chaos, to reveal nonlinear and chaotic behaviors in the model.
We demonstrate through extensive numerical simulations that the model can exhibit chaos under specific parameter values, revealing the complex and unpredictable nature of virus spread in cyberspace.
The research in this study begins in
Section 2 by establishing the necessary background on fractional calculus in discrete time and deriving the Caputo-like fractional discrete computer virus model.
Section 3 then focuses on the model under commensurate and incommensurate fractional orders, analyzing its equilibrium points and their stability. Dynamical analysis and simulation results of the fractional model are considered in
Section 4.
Section 5 explores the complexity of chaos using the SE complexity algorithm, approximate entropy, and the
test. The paper concludes in
Section 6, summarizing key results and outlining future work.
3. Stability Analysis of Equilibria
Here, an analysis is carried out to assess the stability and dynamics of the fractional discrete computer virus system (
12) under commensurate and incommensurate orders.
Setting
and applying Theorem 1, the fractional discrete model’s numerical Formula (
12) is
A crucial step in analyzing the dynamics of System (
12) is determining its fixed points. To achieve this, it is necessary to solve the following nonlinear system:
Equation (
14) has a virus-free equilibrium
and a positive solution
.
, identified as the basic reproduction number, is a fundamental epidemiological parameter that denotes the mean measure of new infections attributable to a single infective in a population of susceptible individuals. In the context of computer virus propagation,
can be thought of as the average number of devices or systems that a single infected device will successfully compromise within a fully vulnerable network. An
value greater than 1 indicates the potential for a virus to spread throughout the network, while a value less than 1 suggests that the virus is unlikely to propagate.
is calculated using the dominant eigenvalue of the next-generation matrix
, as described in [
31], where
so
Calculating the eigenvalues of
yields the reproduction number
which implies
and
3.1. The Commensurate Case
The next step is to establish sufficient conditions regarding the long-term stability of the two fixed points of System (
12). Prior to examining stability, the following theorem is needed:
Theorem 2 ([
32])
. Take into account the fractional difference system where , and are the eigenvalues of . If all fulfill this condition then the asymptotic stability of the zero solution of (
18)
is achieved. The zero equilibrium point’s stability in fractional discrete maps is able to be assessed following Theorem 2. However, for non-zero equilibrium points, a distinct approach is necessary. To this end, the following change of variables is considered.
The transformation yields two new maps, both of which have a zero equilibrium
and
Proposition 1. The virus-free fixed point, denoted , of Model (
12)
is shown to be stable in a local asymptotic sense if the conditions outlined below are verified Proof. Determining the Jacobian matrix for model (
21) at the zero equilibrium point yields
the corresponding characteristic equation:
the eigenvalues of
are
and
.
For
the condition
is satisfied if
.
For
the condition
is satisfied if
, the condition
, is satisfied if
i.e.,
.
So the hypothesis of Theorem
13 is satisfied; the virus-free fixed point of (
12) reveals local asymptotic stability. □
Proposition 2. Local asymptotic stability of is guaranteed if either one of the following two conditions is verified.orwhere and Proof. The Jacobian matrix is computed
The characteristic equation determines the eigenvalues of
with
which implies
for
The eigenvalues
have arguments of
when
which is fulfilled if
this leads to
. The condition
is valid if
.
For
, in this case,
are complex. The requirements for stability hold true if
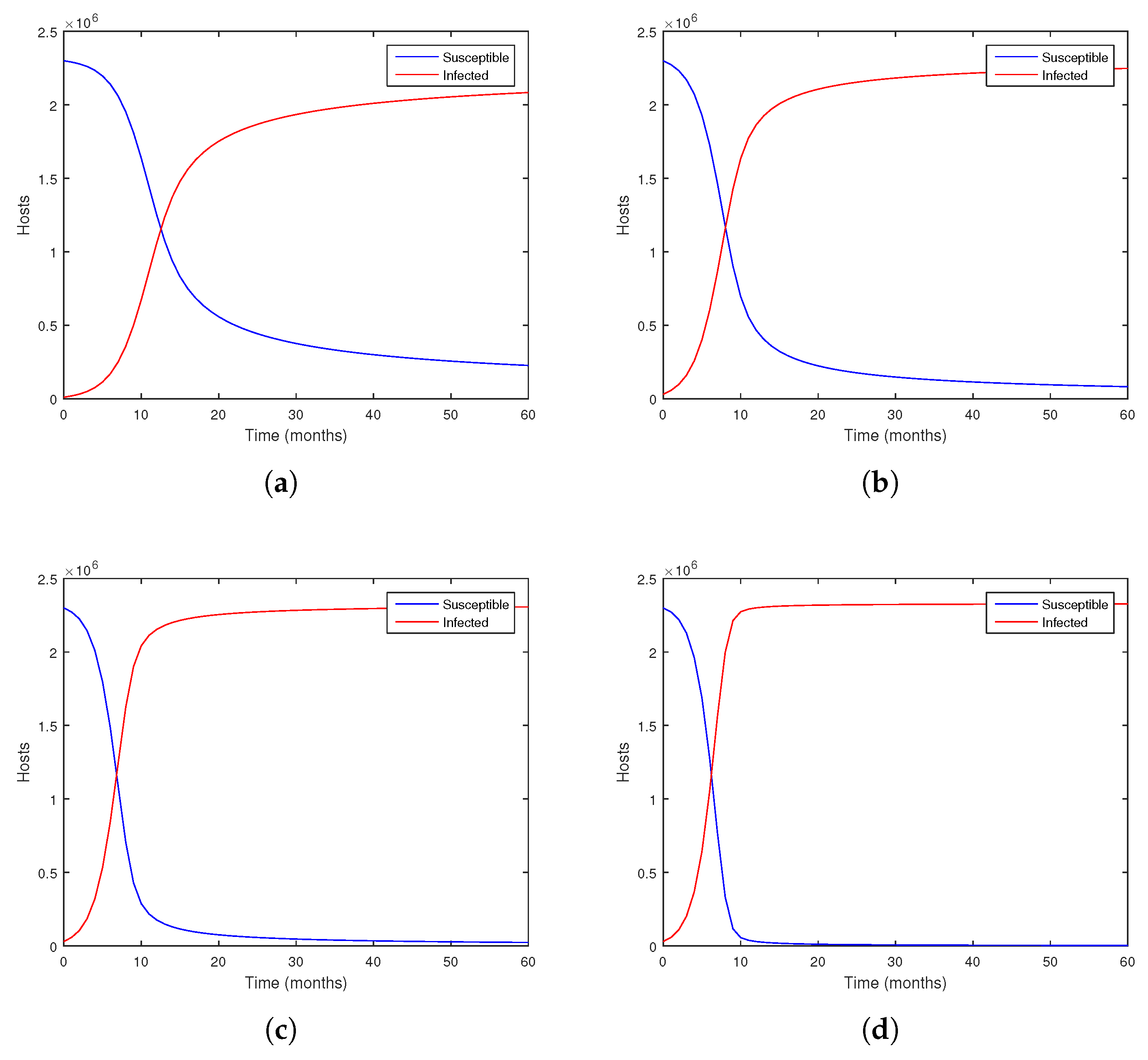
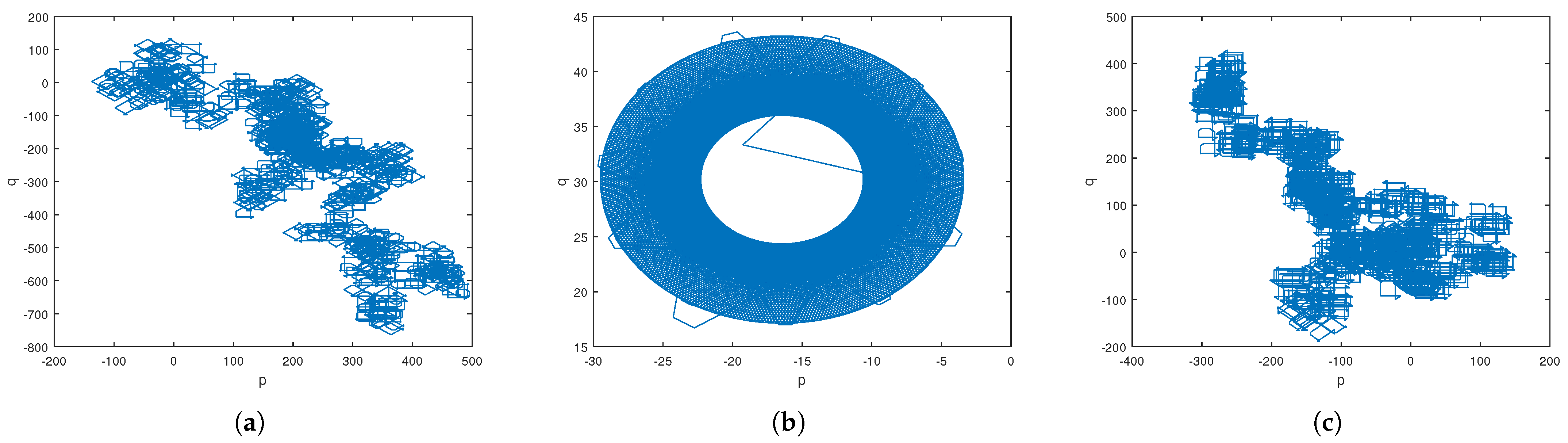
Example 1. Consider System (
12)
with parameters and , which implies that . Figure 1a demonstrates the stability of . Example 2. Let System (
12)
with parameters and , which implies that . In Figure 1b, is confirmed to be stable. Example 3. Consider System (
12)
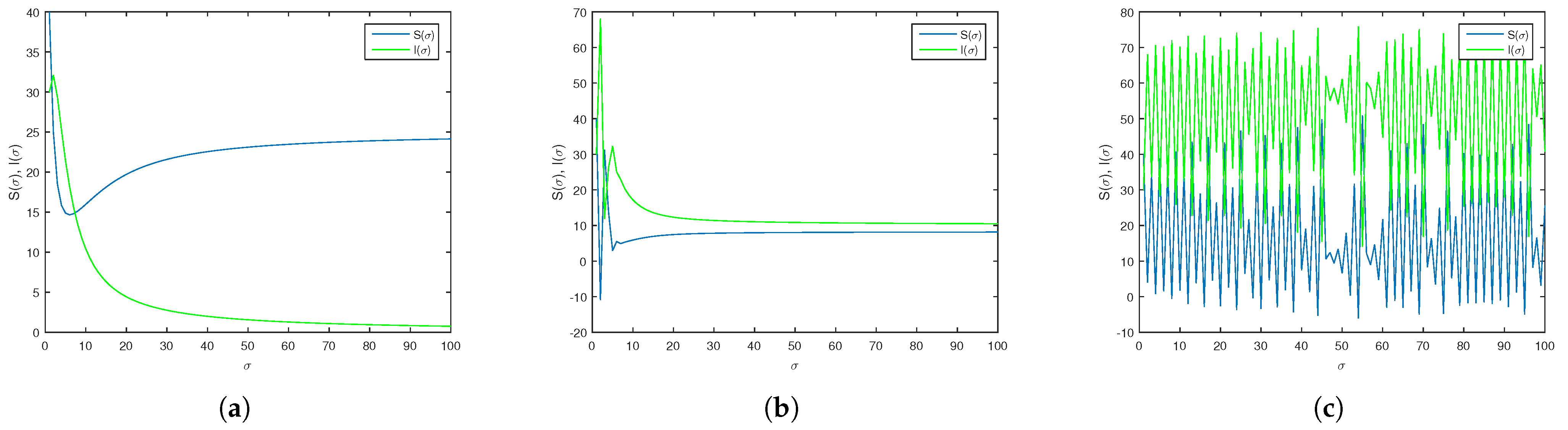
with parameters and , which implies that . Figure 1c highlights the chaotic dynamics of the system characterized by irregular and unpredictable fluctuations in its states. This behavior is typical of systems with sensitive parameters and fractional order variations, where small changes can lead to significantly different outcomes. 3.2. The Incommensurate Case
The focus of this section is the discrete computer virus model with incommensurate fractional orders. In such systems, each equation is governed by a distinct fractional order. The model is represented as follows:
Theorem
1 yields the following numerical model for system (
36):
Here, the stability properties of the discrete computer virus model with incommensurate orders are explored. The theorem presented below serves as a basis for investigating the stability of discrete fractional nonlinear models with incommensurate orders.
Theorem 3 ([
33])
. For the following system where for . where and . M is the LCM of the denominators of , where , and for . Put . such that is the Jacobian matrix of (
38).
If all eigenvalues of Equation (
39)
remain within , Then, system (
38)
has a locally asymptotically stable trivial solution, such that Example 4. Consider system (
36)
with parameters , it follows that Let , which implies that ,equivalent to Solving Equation (
43)
yields 100 solutions, . All solutions remain within . Theorem 3 proves the local asymptotic stability of . Example 5. Consider System (
36)
with parameters , it follows that Let , which implies that ,equivalent to Solving Equation (
46)
yields 100 solutions, . All solutions remain in . Theorem 3 demonstrates the local asymptotic stability of . Example 6. Consider System (
36)
with parameters , it follows that Let , which implies that ,equivalent to Solving Equation (
49)
yields 100 solutions, . Specifically, , satisfying . Theorem 3 provides a sufficient condition for the instability of . And we have thus, equivalent to Solving Equation (
52)
yields 100 solutions, . There’s , satisfying . By Theorem 3, is unstable. Based on the above, the computer virus incommensurate Model (
36) is shown to satisfy a requirement for a chaotic attractor.
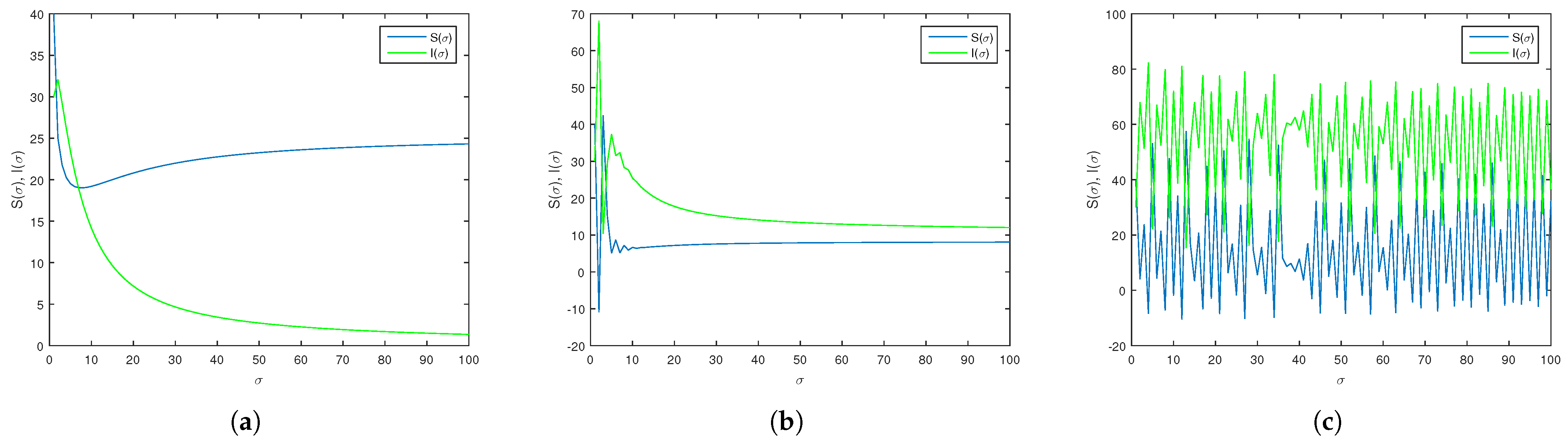
Figure 2 shows the state evolution for the incommensurate Model (
36) of the three previous examples with
. In the following section, advanced analytical and numerical tools, such as Lyapunov exponents, bifurcation analysis, or phase space reconstruction, are necessary to fully understand and characterize its dynamics.
6. Conclusions and Future Directions
This study investigates the stability and chaotic dynamical behavior exhibited by a fractional discrete SI model designed for computer viruses, focusing on both commensurate and incommensurate fractional orders. By leveraging fractional calculus, long-term dependencies in virus transmission are captured, offering a more realistic depiction of digital epidemics. The stability analysis, based on the reproduction number , delineates the conditions under which the virus spreads is either contained or persists.
Moreover, numerical investigations reveal that the system exhibits chaotic behavior in certain parameter regimes, with commensurate and incommensurate fractional orders introducing more intricate and unpredictable dynamics. To systematically examine the chaotic nature of the model, multiple analytical techniques were employed, including bifurcation diagrams, phase portraits, and the maximum Lyapunov exponent. Sophisticated complexity algorithms confirmed the system’s nonlinear and chaotic nature, utilizing spectral entropy, approximate entropy, and the test. These tools provided a comprehensive characterization of the system’s nonlinear behavior, confirming that fractional order plays a crucial role in shaping the model’s dynamical properties. The findings indicate that fractional orders contribute to heightened complexity, emphasizing the need for advanced cybersecurity strategies to address unpredictable virus propagation.
While the current study initially focused on theoretical development and numerical analysis, a critical step towards demonstrating its practical utility involved bridging the gap to real-world applicability by applying the model to the well-documented case of the Stuxnet worm. Using empirical time-series data from Masood et al. [
36], the parameters were calibrated, and the fractional-order model was shown to accurately reproduce the virus’s diffusion trajectory. This real-world validation highlights the model’s practical potential.
Although retrospective modeling approaches, such as the one by Milošević [
35], offer valuable statistical descriptions of cyberattacks, they often lack dynamic interpretability and flexibility. In contrast, the fractional-order framework proposed here offers a dynamic and tunable structure that can simulate complex virus behaviors, including chaos via memory effects and fractional parameters. Although tailored for computer virus propagation, the proposed model structure can be adapted to study biological epidemics by redefining the compartments and transition parameters, making it broadly applicable in epidemiological modeling.
In future work, this validation will be extended to other real cyber threats, such as Conficker or WannaCry, and the generalizability of the model across different virus types will be explored. Plans also include integrating optimization-based data-fitting techniques to refine parameter estimation and collaborating with cybersecurity professionals to evaluate the model’s integration into early detection systems, response mechanisms, and cryptographic schemes that leverage chaotic dynamics. By building on real-world data, the aim is to further enhance the impact of this model on both theoretical understanding and practical cybersecurity applications.