A GNN-Based False Data Detection Scheme for Smart Grids
Abstract
1. Introduction
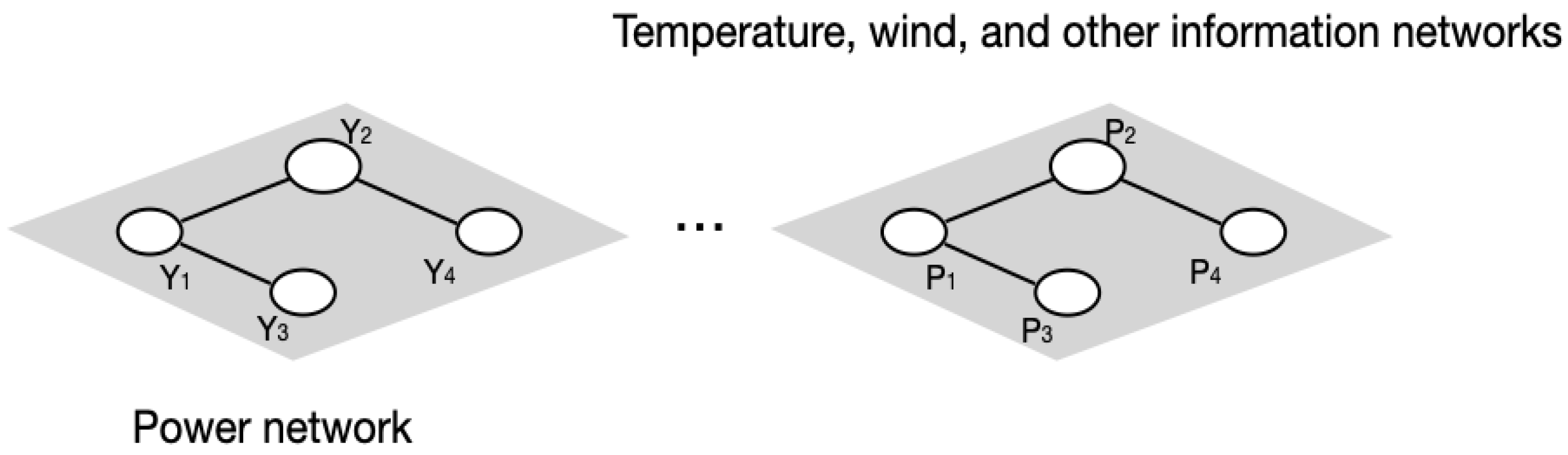
- The information graph was modeled by aggregating the structure and features of the network. The graph processed the communication layer dataset, converted the traffic data into graph structures, and used them as inputs for the model to ensure effective integration of the feature information.
- A spatio-temporal graph neural network (STGNN) was developed to process several information networks obtained from sensor measurements to forecast the network state.
- A loss function was designed to bridge the differences between different domains. The abnormal information from communication and transmission systems was utilized to analyze and detect anomaly information between real data and normal data.
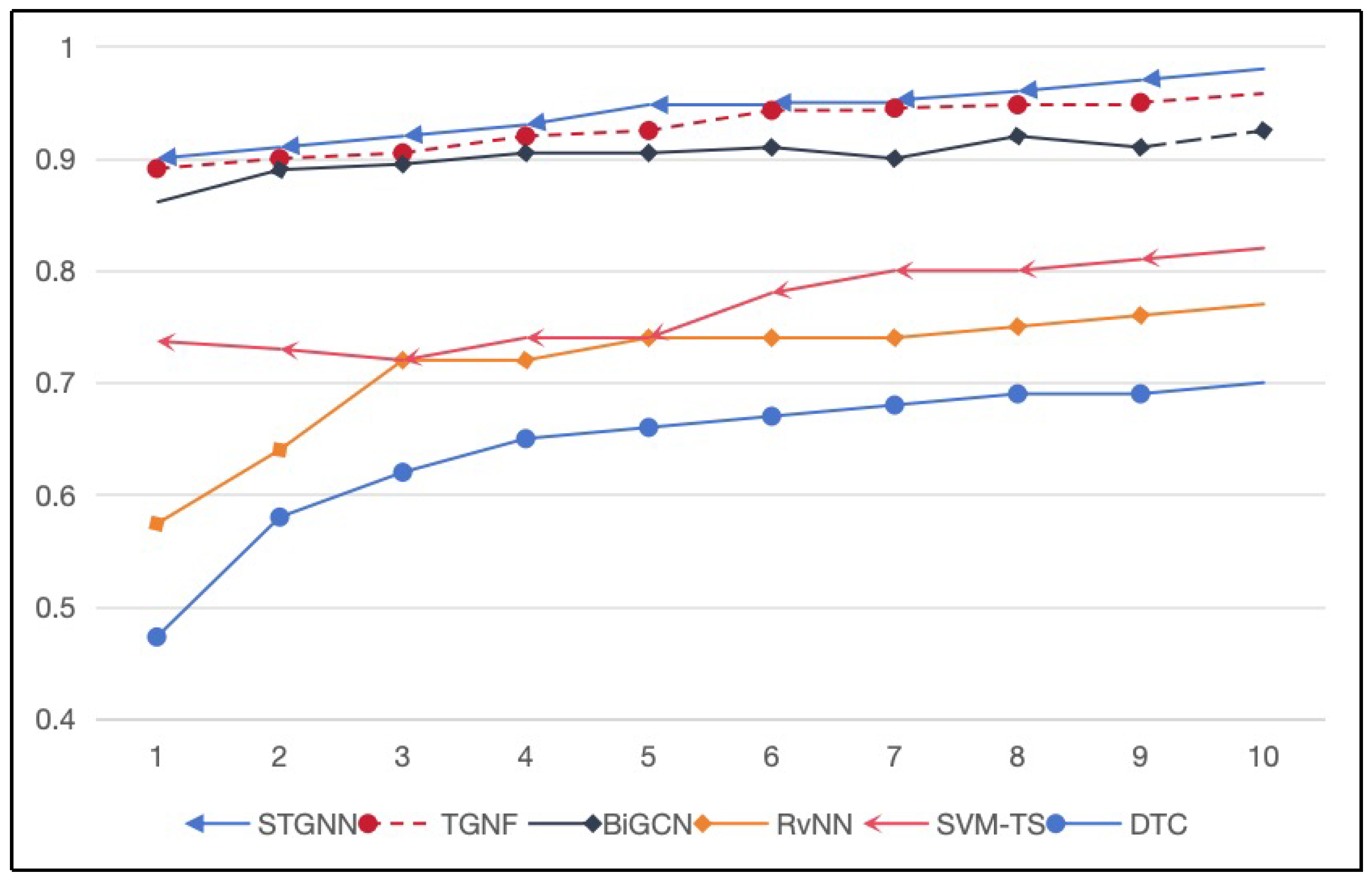
- The experiment revealed that the proposed scheme outperformed other comparative methods with respect to anomaly detection tasks and could accurately identify anomalous data in the early stages of data transmission.
2. Related Work
2.1. Anomaly Detection
2.2. Spatial Temporal Graph Neural Networks, STGNNs
3. Preliminaries
3.1. Problem Formulation
3.2. Graph Neural Networks
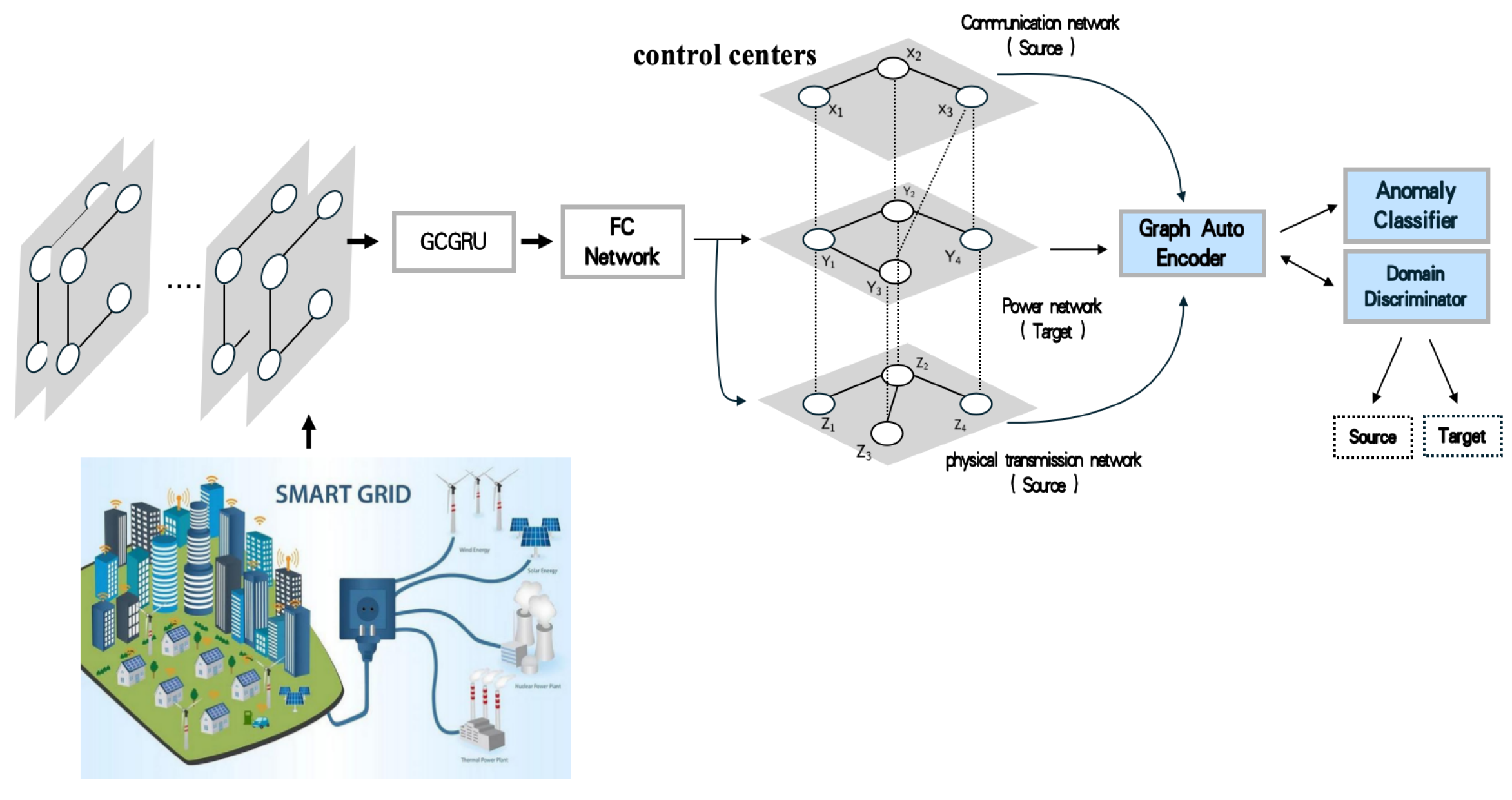
4. The GNN-Based False Data Detection Scheme
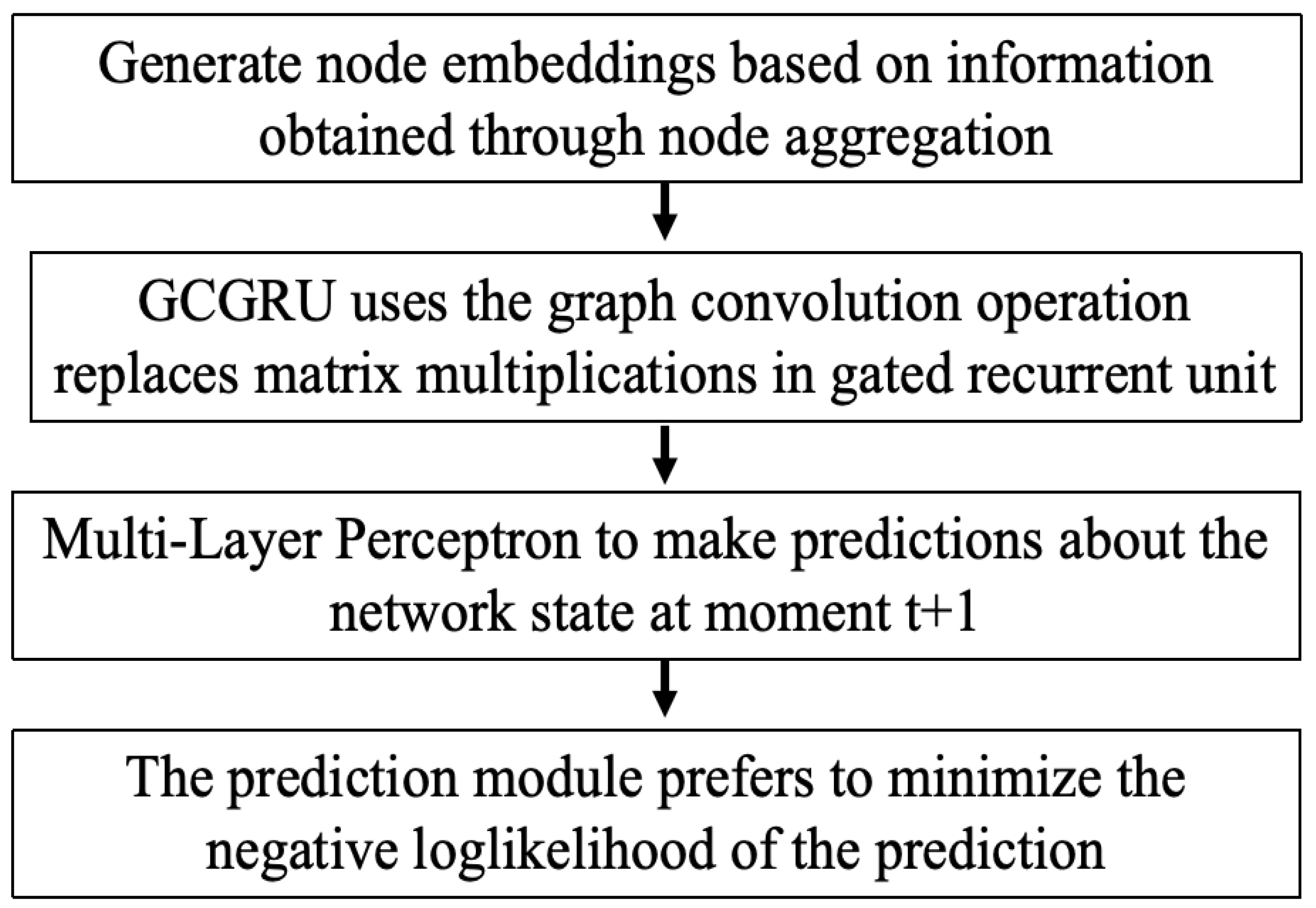
4.1. STGNN for Information Network Prediction
| Algorithm 1 STGNN for Information Network Prediction |
Input: A attributed graph , time slices Output: The network state at moment for , , do for do end for end for return given the predicted value |
4.2. Cross-Domain Anomaly Detection
| Algorithm 2 Cross-Domain Anomaly Detection |
Input: Layer l, node Output: function of cross-domain anomaly detection
|
5. Performance Evaluation
Experimental Settings
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lee, E.A. Cyber physical systems: Design challenges. In Proceedings of the 2008 11th IEEE International Symposium on Object and Component-Oriented Real-Time Distributed Computing (ISORC), Orlando, FL, USA, 5–7 May 2008; pp. 363–369. [Google Scholar]
- Li, D.; Chen, D.; Jin, B.; Shi, L.; Goh, J.; Ng, S. MAD-GAN: Multivariate anomaly detection for time series data with generative adversarial networks. In Proceedings of the 28th International Conference on Artificial Neural Networks, Munich, Germany, 17–19 September 2019; pp. 703–716. [Google Scholar]
- Li, B.; Wu, Y.; Song, J.; Lu, R.; Li, T.; Zhao, L. Deepfed: Federated deep learning for intrusion detection in industrial cyber-physical systems. IEEE Trans. Ind. Inform. 2021, 17, 5615–5624. [Google Scholar] [CrossRef]
- Devanny, J.; Goldoni, L.; Medeiros, B. The 2019 venezuelan blackout and the consequences of cyber uncertainty. Rev. Bras. Estud. Def. 2020, 7, 2. [Google Scholar] [CrossRef]
- Audibert, J.; Michiardi, P.; Guyard, F.; Marti, S.; Zuluaga, M.A. USAD: Unsupervised anomaly detection on multivariate time series. In Proceedings of the 26th ACM SIGKDD Conference on Knowledge Discovery and Data Mining (KDD ’20), Virtual, 23–27 August 2020; pp. 3395–3404. [Google Scholar]
- Zhang, X.; Ma, X.; Huyan, N.; Gu, J.; Tang, X.; Jiao, L. Spectral-difference low-rank representation learning for hyperspectral anomaly detection. IEEE Trans. Geosci. Remote Sens. 2021, 59, 10364–10377. [Google Scholar] [CrossRef]
- Zheng, Z.; Yang, Y.; Niu, X.; Dai, H.; Zhou, Y. Wide and deep convolutional neural networks for electricity-theft detection to secure smart grids. IEEE Trans. Ind. Inform. 2018, 14, 1606–1615. [Google Scholar] [CrossRef]
- Liao, W.; Yang, D.; Wang, Y.; Ren, X. Fault diagnosis of power transformers using graph convolutional network. CSEE J. Power Energy Syst. 2021, 7, 241–249. [Google Scholar]
- Qi, P.; Li, D.; Ng, S. MAD-SGCN: Multivariate anomaly detection with self-learning graph convolutional networks. In Proceedings of the 2022 IEEE 38th International Conference on Data Engineering (ICDE), Kuala Lumpur, Malaysia, 9–12 May 2022; pp. 1232–1244. [Google Scholar]
- Li, Z.; Wei, Y.; Zhang, Y.; Yang, Q. Hierarchical attention transfer network for cross-domain sentiment classification. Proc. AAAI Conf. Artif. Intell. 2018, 32, 5852–5859. [Google Scholar] [CrossRef]
- Shu, Y.; Cao, Z.; Long, M.; Wang, J. Transferable curriculum for weakly-supervised domain adaptation. Proc. AAAI Conf. Artif. Intell. 2019, 33, 4951–4958. [Google Scholar] [CrossRef]
- Ding, K.; Shu, K.; Shan, X.; Li, J.; Liu, H. Cross-domain graph anomaly detection. IEEE Trans. Neural Netw. Learn. Syst. 2022, 33, 2406–2415. [Google Scholar] [CrossRef]
- Kong, X.; Wang, J.; Hu, Z.; He, Y.; Zhao, X.; Shen, G. Mobile trajectory anomaly detection: Taxonomy, methodology, challenges, and directions. IEEE Internet Things J. 2024, 11, 19210–19231. [Google Scholar] [CrossRef]
- Tang, W.; Liu, J.; Zhou, Y.; Ding, Z. Causality-guided counterfactual debiasing for anomaly detection of cyber-physical systems. IEEE Trans. Ind. Inform. 2024, 20, 4582–4593. [Google Scholar] [CrossRef]
- Xi, L.; Miao, D.; Li, M.; Wang, R.; Liu, H.; Huang, X. Adaptive-correlation-aware unsupervised deep learning for anomaly detection in cyber-physical systems. IEEE Trans. Dependable Secur. Comput. 2024, 21, 2888–2899. [Google Scholar] [CrossRef]
- Li, Z.; Xu, X.; Hang, T.; Xiang, H.; Cui, Y.; Qi, L.; Zhou, X. A knowledge-driven anomaly detection framework for social production system. IEEE Trans. Comput. Soc. Syst. 2024, 11, 3179–3192. [Google Scholar] [CrossRef]
- Zhu, H.; Yi, C.; Rho, S.; Liu, S.; Jiang, F. An interpretable multivariate time-series anomaly detection method in cyber-physical systems based on adaptive mask. IEEE Internet Things J. 2024, 11, 2728–2740. [Google Scholar] [CrossRef]
- Xu, S.; Yu, H.; Wang, H.; Chai, H.; Ma, M.; Chen, H.; Zheng, W.X. Simultaneous diagnosis of Open-Switch and current sensor faults of inverters in IM drives through reduced-order interval iObserver. IEEE Trans. Ind. Electron. 2024, 1–12. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P.; Zhou, J.; Sun, L.; Du, B.; Fu, Y. Defending water treatment networks: Exploiting spatio-temporal effects for cyber attack detection. In Proceedings of the 2020 IEEE International Conference on Data Mining (ICDM), Sorrento, Italy, 17–20 November 2020; pp. 32–41. [Google Scholar]
- He, Q.; Zheng, Y.J.; Zhang, C.; Wang, H. MTAD-TF: Multivariate time series anomaly detection using the combination of temporal pattern and feature pattern. Complex 2020, 8846, 608:1–608:9. [Google Scholar] [CrossRef]
- Zhao, H.; Wang, Y.; Duan, J.; Huang, C.; Cao, D.; Tong, Y.; Xu, B.; Bai, J.; Tong, J.; Zhang, Q. Multivariate time-series anomaly detection via graph attention network. In Proceedings of the 2020 IEEE International Conference on Data Mining (ICDM), Sorrento, Italy, 17–20 November 2020; pp. 841–850. [Google Scholar]
- Deng, L.; Lian, D.; Huang, Z.; Chen, E. Graph convolutional adversarial networks for spatiotemporal anomaly detection. IEEE Trans. Neural Netw. Learn. Syst. 2022, 33, 2416–2428. [Google Scholar] [CrossRef]
- Akoglu, L.; Tong, H.; Koutra, D. Graph based anomaly detection and description: A survey. Data Min. Knowl. Discov. 2015, 29, 626–688. [Google Scholar] [CrossRef]
- Xu, K.; Hu, W.; Leskovec, J.; Jegelka, S. How powerful are graph neural networks? In Proceedings of the 7th International Conference on Learning Representations, New Orleans, LA, USA, 6–9 May 2019. [Google Scholar]
- Hamilton, W.L.; Ying, Z.; Leskovec, J. Inductive representation learning on large graphs. Adv. Neural Inf. Process. Syst. 2017, 30, 1024–1034. [Google Scholar]
- Seo, Y.; Defferrard, M.; Vandergheynst, P.; Bresson, X. Structured sequence modeling with graph convolutional recurrent networks. In Proceedings of the Neural Information Processing: 25th International Conference, ICONIP 2018, Siem Reap, Cambodia, 13–16 December 2018; pp. 362–373. [Google Scholar]
- Chung, J.; Gülçehre, Ç.; Cho, K.; Bengio, Y. Empirical evaluation of gated recurrent neural networks on sequence modeling. arXiv 2014, arXiv:1412.3555. [Google Scholar]
- Goodfellow, I.J.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.C.; Bengio, Y. Generative adversarial nets. In Proceedings of the NeurIPS 2014, Montreal, QC, Canada, 8–13 December 2014; pp. 2672–2680. [Google Scholar]
- Pan, S.; Hu, R.; Fung, S.; Long, G.; Jiang, J.; Zhang, C. Learning graph embedding with adversarial training methods. IEEE Trans. Cybern. 2020, 50, 2475–2487. [Google Scholar] [CrossRef]
- Castillo, C.; Mendoza, M.; Poblete, B. Information credibility on twitter. In Proceedings of the 20th International Conference on World Wide Web, Hyderabad, India, 28 March–1 April 2011. [Google Scholar] [CrossRef]
- Ma, J.; Gao, W.; Wei, Z.; Lu, Y.; Wong, K. Detect rumors using time series of social context information on microblogging websites. In Proceedings of the 24th ACM International on Conference on Information and Knowledge Management, Melbourne, Australia, 18–23 October 2015. [Google Scholar] [CrossRef]
- Ma, J.; Gao, W.; Mitra, P.; Kwon, S.; Jansen, B.J.; Wong, K.; Cha, M. Detecting Rumors from Microblogs with Recurrent Neural Networks. JCAI. 2016. Available online: http://www.ijcai.org/Abstract/16/537 (accessed on 27 February 2025).
- Bian, T.; Xiao, X.; Xu, T.; Zhao, P.; Huang, W.; Rong, Y.; Huang, J. Rumor detection on social media with bi-directional graph convolutional networks. AAAI 2020, 34, 549–556. [Google Scholar] [CrossRef]
- Song, C.; Shu, K.; Wu, B. Temporally evolving graph neural network for fake news detection. Inf. Process. Manag. 2021, 58, 102712. [Google Scholar] [CrossRef]
| Model | Accuracy | Event Type | Precision | Recall | F1 |
|---|---|---|---|---|---|
| DTC | 0.473 | F | 0.826 | 0.814 | 0.821 |
| N | 0.813 | 0.824 | 0.847 | ||
| SVM-TS | 0.574 | F | 0.801 | 0.887 | 0.894 |
| N | 0.875 | 0.824 | 0.847 | ||
| RvNN | 0.737 | F | 0.908 | 0.89 | 0.899 |
| N | 0.897 | 0.914 | 0.905 | ||
| BiGGCN | 0.861 | F | 0.921 | 0.92 | 0.915 |
| N | 0.92 | 0.919 | 0.914 | ||
| TGNF | 0.897 | F | 0.948 | 0.937 | 0.942 |
| N | 0.938 | 0.949 | 0.944 | ||
| STGNN | 0.892 | F | 0.951 | 0.96 | 0.955 |
| N | 0.96 | 0.951 | 0.955 |
| Model | Accuracy | F1 | |||
|---|---|---|---|---|---|
| D | F | C | N | ||
| DTC | 0.473 | 0.254 | 0.08 | 0.19 | 0.482 |
| SVM-TS | 0.574 | 0.755 | 0.42 | 0.571 | 0.526 |
| RvNN | 0.737 | 0.662 | 0.743 | 0.835 | 0.708 |
| BiGGCN | 0.861 | 0.772 | 0.867 | 0.931 | 0.861 |
| TGNF | 0.897 | 0.913 | 0.857 | 0.938 | 0.876 |
| STGNN | 0.892 | 0.905 | 0.893 | 0.908 | 0.897 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qiu, J.; Zhang, X.; Wang, T.; Hou, H.; Wang, S.; Yang, T. A GNN-Based False Data Detection Scheme for Smart Grids. Algorithms 2025, 18, 166. https://doi.org/10.3390/a18030166
Qiu J, Zhang X, Wang T, Hou H, Wang S, Yang T. A GNN-Based False Data Detection Scheme for Smart Grids. Algorithms. 2025; 18(3):166. https://doi.org/10.3390/a18030166
Chicago/Turabian StyleQiu, Junhong, Xinxin Zhang, Tao Wang, Huiying Hou, Siyuan Wang, and Tiejun Yang. 2025. "A GNN-Based False Data Detection Scheme for Smart Grids" Algorithms 18, no. 3: 166. https://doi.org/10.3390/a18030166
APA StyleQiu, J., Zhang, X., Wang, T., Hou, H., Wang, S., & Yang, T. (2025). A GNN-Based False Data Detection Scheme for Smart Grids. Algorithms, 18(3), 166. https://doi.org/10.3390/a18030166








