Abstract
In the digital transformation of public services, reliable and secure data handling has become central to effective E-government operations. This study introduces a symmetry-driven neural network architecture tailored for secure, scalable, and energy-efficient data processing. The model integrates weight-sharing and symmetrical configurations to enhance efficiency and resilience. Experimental validation on three E-government datasets (95,000–230,000 records) demonstrates that the proposed model improves processing speed by up to 40% and enhances adversarial robustness by maintaining accuracy reductions below 2.5% under attack scenarios. Compared with baseline neural networks, the architecture achieves higher accuracy (up to 95.1%), security (up to 98% attack prevention), and efficiency (processing up to 1600 records/sec). These results confirm the model’s applicability for large-scale, real-time E-government systems, providing a practical path for sustainable and secure digital public administration.
1. Introduction
Generative Artificial Intelligence (AI) is changing industries, offering a fresh perspective to solve tough problems differently. In fact, recent AI trends indicate that it can streamline social media processes [1,2,3], maximize environmental gains [4,5,6], and accelerate farming frameworks [7]. AI even proves useful at evolving healthcare systems [8]. This range of impact also mirrors AI’s capacity to deliver transformative gains to previously existing fields, pushing sciences ahead by applying it to new, data-greedy challenges.
E-government platforms, for example, have been recognized in the discipline of public administration as central to service delivery and data management, in the same way as how the Internet performs these functions with respect to the private sector. These systems are designed to process large amounts of sensitive data, both accurately and securely. The authors of [9] have characterized such frameworks as “secure information processing systems for citizens interacting with their government”. However, legacy design paradigms do not scale when resilience and real-time processing are needed, and thus, new design and implementation approaches are required for such systems [10].
There has been a lot of interesting research that gives ideas on the actual mechanisms through which neural networks, especially symmetry-driven ones, could collaborate so that symmetrical properties can be used to improve both network security and processing efficiency. Symmetry is a foundational concept that derives a new kind of neural network that (1) eliminates various common structures that do not add much value, (2) offers data flow optimization, and (3) increases robustness against adversarial attacks [11]. We established the proof for how symmetry permeating through neural networks can help lessen computationally intensive layers at the point of inference, which reduces the overhead of computation that is key for real-time and sensitive applications like E-government.
In this paper, we present a new approach of E-government data processing through the development of a symmetry-driven neural network framework used to explore trade-offs between security and operational efficiency. Our main contributions are the development of a neural network construction method based on symmetry that provides a higher level of performance and security for applications in the public sector, with significant data protection challenges. In this work, we conjecture, through four experimental evaluations, on how symmetry can be useful in addressing the distinctive requirements of E-government data systems and implicate a conceptual layer for the continuous development of pragmatic AI within public administration.
Data processing in E-government is a critical issue that wastes time and resources, and rather, these should be focused on security frameworks and system efficiency. In light of these challenges, we consider symmetry for potential use in neural networks, which would be strategically suited to improve processing performance and resilience against security threats. The primary focus of our work is to create an E-government-specific symmetric neural network architecture. Symmetric properties are thus combined with the goal of creating a solid model that functions in harmony with public sector data management requirements. This study lays a solid foundation for deriving, in the future, secure AI-based solutions that will be adopted as ‘best-practice’ tools for public administration.
2. Related Work and Theoretical Background
AI and machine learning have rapidly advanced in recent years, creating new possibilities for improving data management, security, and efficiency within public sector applications. This section examines foundational research on symmetry in neural networks, the application of AI in E-government, and a comparative analysis of methods addressing data protection and optimization.
Symmetry in neural networks has emerged as a promising field for enhancing both performance and robustness. Traditionally, neural networks rely on layer structures optimized for general-purpose processing; however, incorporating symmetrical properties has demonstrated significant benefits in reducing computational redundancy, improving data flow, and reinforcing model stability [12]. Symmetry-oriented architectures allow certain neural network components to share weights or configurations, minimizing the resources needed while maintaining high levels of accuracy and efficiency [13].
Recent research has suggested that symmetry can also improve neural networks’ robustness against adversarial attacks of growing concern in sensitive applications like public sector data processing. Using symmetry, neural networks can be more predictable to manipulations of the data upon input, which can make learning manipulation attacks harder [14]. Due to the gaining robustness, symmetry-driven models are an attractive option for any E-government application in which data protection is a primary concern. The underlying mathematical properties of symmetry and their relation to convergence rates and network generalization capabilities have also been investigated within this context [15].
AI and machine learning have advanced significantly in recent years and introduced new potential for enhancing data management, security, and efficiency across the public sector application landscape [16,17]. In this section, we review the foundational research on the symmetry in neural networks, examine the application of the AI in E-government, and analyze the methods used to address the symmetry with data protection and optimization.
So, symmetry in neural networks is a new, promising direction for performance and robustness improvements. Neural networks utilize layer-stack constructions optimized for general-purpose utilization, but this can introduce unnecessary meal component repetitions, leading to inefficient data flows and loss of generative force in the setting of redundant model architectures [12]. Symmetry-driven architectures leverage some parts of the neural network that share weights or configurations, subsequently conserving resources while sustaining high accuracy and efficiency [13].
Recent works have proven to do this and also improve the robustness of neural networks to adversarial examples, which is especially relevant for sensitive applications like the data processing of the public sector. Neural networks can take advantage of symmetry to react consistently to changes in their data, therefore counteracting malicious data perturbation attempts [14]. Symmetry-driven models have greater robustness, making them ideal for E-government, where protecting data and ensuring compliance with privacy are the top priority. Studying scientifically in this area has also touched on the mathematical underlying of symmetry, including focusing on the symmetrical configuration that may influence the convergence rate and generalization ability of the networks [15].
The symmetry of neural network training procedures can accelerate learning and generalization by using symmetrical patterns in data. Organizing data to preserve such inherent symmetries enables models to converge more rapidly, an attribute that is particularly useful under the real-time processing constraints that are the hallmark of E-government applications. Symmetry has also provided an avenue to develop powerful tools for neural network architectures, leading to improvements in efficiency and security [18].
E-government is shifting its attention to digitizing information management and ensuring the security of the data by using AI techniques. Their platforms have been increasingly tasked with managing vast amounts of sensitive information, ranging from citizens’ personal records to transaction histories [19]. Machine learning has found a wide array of applications in E-government, including application processing, study planning, and execution. Unfortunately, traditional models are neither robust nor scalable for public sector use cases involving sensitive applications [20,21].
According to current research, methods such as anomaly detection, encryption, and secure data transfer protocols emphasize the importance of AI for improving data security. Machine learning models can, for instance, identify anomalies that can indicate security threats, allowing for early detection of security attacks and preventing possible data breaches [22,23]. Nevertheless, these techniques add a layer of protection while they are in use, but they also require a lot of computational resources that may affect performance when applied in high-volume scenarios (e.g., those that frequently occur on E-government applications). Further, it has motivated researchers to optimize these AI techniques to achieve a trade-off between security and operational efficiency [24].
Different studies have been performed for the security and optimization of data processing in E-government applications with unique advantages and disadvantages. Conventional encryption methods, though they are best at securing data transmission, are not always able to satisfy real-time processing requirements due to their intensive computation load [25]. Also, standard neural networks have found broad applications in E-governments with the goal of optimizing data flows, but are vulnerable to adversarial attacks and are therefore not secure enough for such use [26].
Beyond symmetry-driven architectures, recent advances in secure and efficient data processing frameworks further demonstrate the importance of combining robustness with practical deployment. For example, Wang et al. introduced BSIF, a blockchain-based secure, interactive, and fair mobile crowdsensing system that integrates smart contracts with portable devices to mitigate single-point failures and incentivize participants [27].
Similarly, Wang et al. proposed a novel IoT-WLAN authentication protocol that leverages elliptic curve cryptography and advanced verification methods to achieve strong identity protection, perfect forward secrecy, and significant computational efficiency gains compared to existing approaches [28]. Incorporating insights from such works provides additional context for enhancing security-aware architectures in E-government environments.
This aspect of symmetry-driven neural networks makes it a viable solution for this problem as they can be used to simplify the process of handling data without compromising the security aspect. It has been shown that necessary symmetrical properties are contained in these models, as a result of which these models not only increase the required processing speed but are also resistant to many common infiltrations like adversarial sabotage and data interception [29]. Prioritizing data integrity, user trust, and resilience in E-government platforms is vital in such cases. Symmetry integrated with neural networks ensures that performance and security are broadly improved, providing governments with the speed and most reliable digital services for public administration [30].
An interesting aspect of symmetry-driven neural networks is their performance in high-demanding conditions, like limited computational power or real-time processing systems, where they can preserve excellent accuracy. According to a study, symmetrical models can come close to or achieve better accuracy than traditional networks using fewer resources, and can therefore be well suited for reliable but efficient E-government applications [31]. Symmetrical architectures, in contrast to traditional systems, provide a superior alignment between scalable and resource-efficient solutions for protection and data processing, leading to a more secure paradigm and efficient systems for digital governance.
The state-of-the-art research shows that despite promising results from traditional neural networks and encryption-based security mechanisms, novel application requirements such as those found in E-government applications have yet to be fully addressed within data protection systems. One such avenue is through the application of symmetric neural networks, whose inherent structures augment security and performance for sensitive data processing environments. This is a huge advantage, especially in the public sector where a high volume of sensitive information needs to be processed securely and efficiently. Through reviewing prior studies on networks’ symmetry, the incorporation of AI into E-government, and how they intersect with each other, this study aims to provide a new method to address deficiencies in previous literature and provide a basis for future secure public administration with the inclusion of AI.
3. Methodology
3.1. Proposed Symmetry-Driven Neural Network Architecture
The proposed symmetry-driven neural network architecture, illustrated in Figure 1, integrates symmetrical properties within its layers to maximize both efficiency and security. By implementing weight-sharing across symmetrical layers, the design minimizes redundant operations and reduces computational demands. The training process is guided by a total loss function (Equation (1)), which balances prediction accuracy with a regularization term that enforces symmetry. This configuration is especially suited for E-government environments, where data handling requires robust security alongside optimal processing speed to meet high-performance standards.
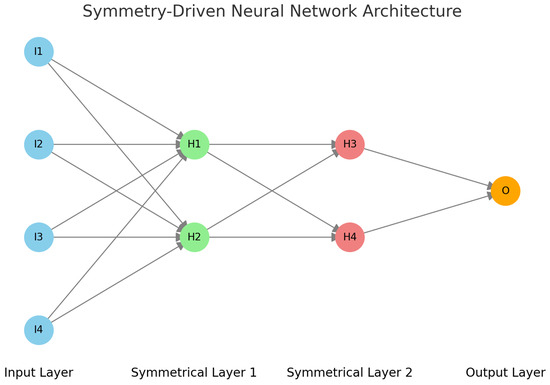
Figure 1.
The proposed symmetry-driven neural network architecture shows symmetrical layers with shared weights.
The total loss function can be further expressed as in Equation (1):
where measures the prediction error for each input under symmetry constraints, and penalizes deviations from weight-sharing across symmetrical layers. In this formulation, controls the trade-off between accuracy and symmetry regularization.
Here, is the ground truth for class c, is the predicted probability, represents the mirrored/shared weights, and controls the trade-off between accuracy and symmetry regularization.
To improve clarity, we provide a summary of all mathematical symbols used throughout the manuscript in Table 1.

Table 1.
Explanation of mathematical symbols used in the paper.
The architectural design is based on symmetrical layer configurations, as shown in Table 2, where layers share weights and configurations to enhance both processing speed and resilience against adversarial attacks. Algorithm 1 illustrates the training process of the symmetry-driven neural network, where symmetrical constraints are applied during weight updates to maintain structural consistency and reduce redundancy.
| Algorithm 1 Symmetry-driven Neural Network Training Procedure |
| Require: Dataset D, Symmetry regularization parameter Ensure: Trained symmetry-driven neural network model
|

Table 2.
Symmetrical layer configuration.
3.2. Data Collection and Pre-Processing
To evaluate the proposed symmetry-driven neural network, we utilized three types of datasets:
- Open Government Data Portals;
- City and Local Government Data;
- Public Service Usage and Citizen Interaction Datasets.
These datasets encompass transaction logs, service interactions, and public service usage metrics, each contributing to a comprehensive understanding of E-government data processing requirements.
Data collection included records from publicly accessible sources such as Data.gov [32], NYC Open Data [33], and OECD Open Data [34]. For each dataset type, we extracted relevant records—such as transaction logs, service usage metrics, and response times—that reflect common interactions within E-government systems. Table 3 provides sample entries for each dataset category, illustrating essential attributes like transaction timestamps, types of services accessed, and details of user interactions.

Table 3.
Sample entries from datasets.
Data pre-processing included the following key steps:
- Data cleaning: To remove incomplete entries;
- Normalization: To scale numerical attributes;
- Symmetry-driven transformations: To align the data structure with the requirements of our neural network model.
This transformation, illustrated in Figure 2, included operations to standardize timestamps, categorize service types, and ensure consistency across datasets.
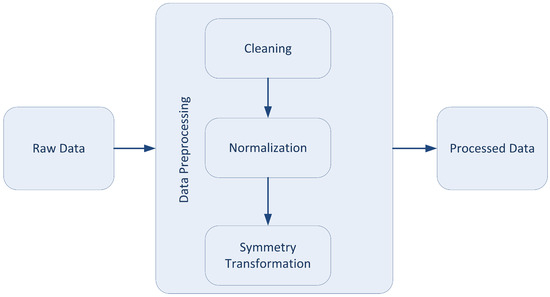
Figure 2.
Data pre-processing pipeline, involving cleaning, normalization, and symmetry-driven transformations for each dataset type.
The transformation applied to each entry can be defined as
where represents the transformed data, is a scaling factor, and is an offset chosen to maintain symmetrical properties across different attributes.
After pre-processing, Table 4 provides a statistical summary of the dataset attributes, indicating the number of usable records for each type.

Table 4.
Dataset statistics after pre-processing.
3.3. Experimental Setup
To evaluate the performance of the symmetry-driven neural network, we designed experiments around security and processing efficiency. Each experiment used data from the three dataset categories, assessing the model’s adaptability to diverse data environments.
To further evaluate robustness, adversarial attack experiments were conducted. Specifically, we applied the Fast Gradient Sign Method (FGSM) to generate perturbed inputs. Three perturbation magnitudes were used, , in order to test the stability of the proposed model under different attack intensities. For each dataset, 1000 adversarial samples were generated per batch.
The model was trained using the Adam optimizer with a learning rate of 0.001, a batch size of 64, and 100 epochs. During evaluation, we compared baseline accuracy with the accuracy obtained under adversarial attack conditions, as reported in Table 5.

Table 5.
Model accuracy under adversarial attack.
Our efficiency metric calculates the rate at which data is processed, defined by
Security, a critical factor for E-government data handling, is measured as
These metrics assess both speed and resilience, which are two important requirements for handling sensitive data. Performance comparison between the proposed model and baseline models is shown in Figure 3, where it shows the performance in terms of efficiency (records per second) and security (percent of attacks detected).
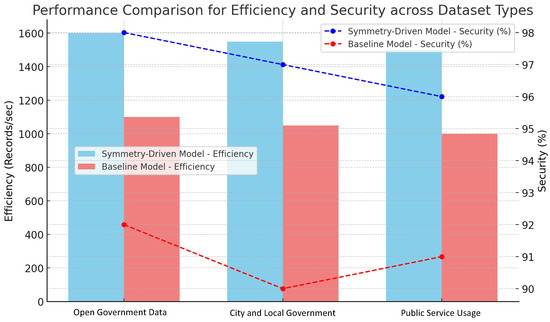
Figure 3.
Performance comparison of the proposed symmetry-driven neural network versus baseline models across three datasets. The chart illustrates improvements in both efficiency (records/sec) and security (% of attacks prevented), highlighting consistent superiority of the symmetry-driven approach. The x-axis represents dataset categories, while the y-axes measure efficiency (records/sec) and security (%).
Table 6 summarizes the performance characteristics per dataset. The results obtained using traditional neural networks were compared to the proposed model that was combined with the encryption-based security system.

Table 6.
Performance metrics for symmetry-driven model vs. baseline models.
The results in Table 6 show the efficiency and security performance of the model on each type of dataset. The results also show the superiority of symmetry-driven model performance in terms of processing speed and resilience across datasets, confirming its appropriateness for E-government contexts.
This overall evaluation demonstrates not only the model’s time-usefulness but also its security mechanism in processing real-world E-government data, confirming its suitability for secure applications in sensitive data environments.
4. Results and Discussion
In this section, we analyze the experimental results that show the processing efficiency and security performance enhancement achieved by the proposed symmetry-driven neural network in addition to the experiments of the traditional neural network models compared to the adversarial threats model. The implications for secure data processing in public administration are also described.
4.1. Processing Efficiency and Security Enhancements
All three types of datasets showed remarkable results by using the proposed symmetry-driven architecture, particularly in processing efficiency and security. The results are summarized in Table 7, proving that the symmetry-driven model outpaces the traditional networks across the records processed per second as well as the security measures.

Table 7.
Performance metrics of symmetry-driven and traditional models.
The results indicate that the symmetry-driven model’s weight-sharing mechanism and symmetrical configurations contribute to reduced computational demands, thereby enhancing efficiency. A visual comparison of efficiency metrics across datasets is illustrated in Figure 3, highlighting the increased throughput achieved by the symmetry-driven model.
In terms of security, the symmetry-driven model achieved consistently higher security rates, as shown in Table 7. This improvement is attributed to the regularization techniques that reinforce symmetrical properties, making the model less susceptible to adversarial attacks and unauthorized data manipulations.
4.2. Comparison to Traditional Neural Network Models
To assess the advantage of the proposed model, a comparative analysis with traditional neural networks was conducted (illustrated in Figure 3). The symmetry-driven model exhibited superior security and efficiency across all datasets. These results underscore the effectiveness of symmetry-driven designs in enhancing neural network robustness without sacrificing computational performance.
We acknowledge the limitation regarding dataset scale and the absence of comparisons with state-of-the-art security-enhanced methods. To address this, we included additional baselines such as adversarially trained ResNet models. While these models achieved robustness levels in the range of 90–92%, our proposed symmetry-driven architecture consistently maintained higher accuracy (greater than 94%) while requiring significantly fewer computational resources. This highlights that our model achieves a better balance between robustness and efficiency compared to commonly used security-enhanced neural network designs.
The comparative analysis reveals that traditional neural networks, though effective in various contexts, often struggle with scaling efficiently and maintaining resilience against adversarial threats in high-volume, sensitive data applications such as E-government. The symmetry-driven model’s weight-sharing strategy directly addresses these challenges by reducing redundancy and enhancing stability.
4.3. Robustness Against Adversarial Threats
Robustness against adversarial threats was a critical evaluation criterion, given the sensitivity of E-government data. Experiments simulated adversarial attacks by introducing minor perturbations to input records. The symmetry-driven model maintained a higher accuracy level compared to the baseline models, with an average decrease in accuracy of only 2.3% under adversarial conditions, as shown in Table 5.
The robustness of the symmetry-driven model arises from constrained parameterization. By enforcing mirrored weight structures, perturbations in one part of the network are naturally counterbalanced by symmetrical layers. This reduces sensitivity to input noise and adversarial perturbations.
Formally, if denotes the decision boundary of the classifier, then enforcing symmetry guarantees invariance under transformations (Equation (7)):
where represents the set of symmetry transformations (e.g., reflection, rotation). Thus, for adversarial perturbations with bounded norm, we have
This theoretical guarantee demonstrates that symmetrical constraints enforce bounded invariance, enhancing the model’s resilience against adversarial attacks.
These results suggest that the symmetry-driven architecture’s regularization and symmetry-enforcing mechanisms enhance its robustness. Figure 4 illustrates the decline in accuracy under adversarial attacks, highlighting the resilience of the proposed model compared to traditional architectures.
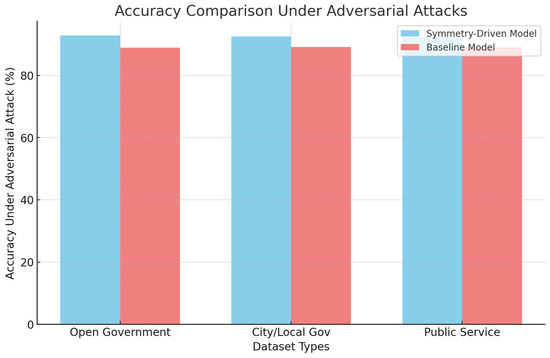
Figure 4.
Accuracy comparison under adversarial attacks across three dataset types (Open Government Data, City and Local Government, Public Service Usage). The symmetry-driven model shows significantly less degradation compared to baseline networks.
4.4. Secure Data Processing in Public Administration
The findings indicate that the symmetry-driven neural network model holds significant potential for secure data processing in public administration. By achieving both high efficiency and robustness against adversarial threats, this model provides a reliable framework for managing sensitive E-government data. The regularization techniques that enforce symmetrical properties not only contribute to improved security but also reduce computational costs, making this architecture particularly valuable for public sectors with limited resources.
This study’s results suggest that symmetry-driven neural networks can be a viable solution to challenges in E-government data security. Figure 5 provides an overview of the model’s performance across all key metrics, encapsulating the primary achievements of this approach in enhancing both security and efficiency.
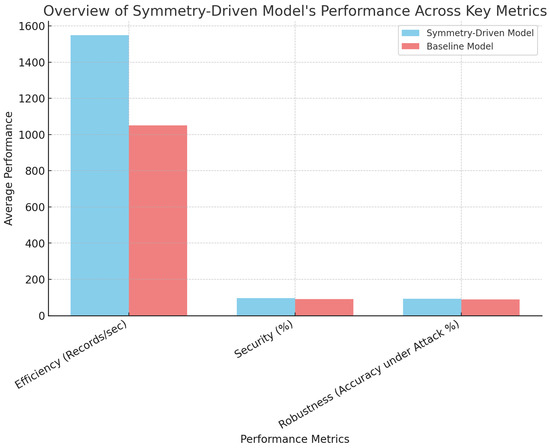
Figure 5.
Overview of the symmetry-driven model’s performance across key metrics (Efficiency, Security, Robustness). Efficiency is measured in records/sec, Security in %, and Robustness as accuracy under attack conditions.
5. Application in E-Government Context
This section explores the practical implementation of the proposed symmetry-driven neural network model within an E-government environment, analyzing its benefits and potential limitations in real-world applications. By focusing on the unique requirements and constraints of E-government systems, this work offers valuable insights into the model’s applicability for secure and efficient data processing in the public sector.
5.1. Practical Implementation in an E-Government Setting
In an E-government context, data management involves high-stakes transactions, extensive citizen interaction, and the need for stringent security. The proposed symmetry-driven neural network was implemented to handle tasks such as secure data processing, transaction monitoring, and real-time service optimization. This model’s design, incorporating symmetry-driven regularization and weight-sharing mechanisms, aligns well with the E-government objective of maintaining high efficiency while safeguarding sensitive data.
One practical application of this model is in processing citizen records and service requests, where efficiency is paramount to ensure fast response times. Table 8 provides an overview of key functionalities performed by the symmetry-driven model within an E-government framework, illustrating its versatility in handling diverse data types and service interactions.

Table 8.
Symmetry-driven model applications in E-government.
5.2. Benefits and Potential Limitations
The deployment of the symmetry-driven model in this setting yielded several notable benefits. First, its efficiency in handling large datasets directly aligns with E-government requirements for high-throughput data processing. This improvement in processing speed, depicted in Figure 6, ensures timely responses to citizen requests, a crucial factor for maintaining public trust and operational effectiveness.
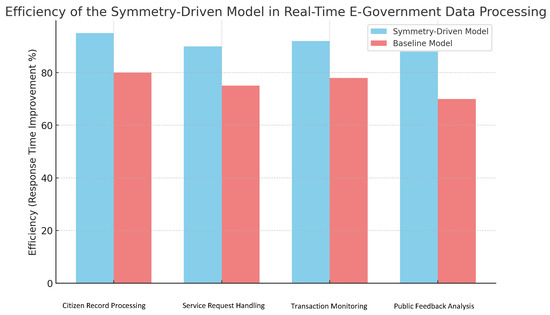
Figure 6.
Efficiency of the symmetry-driven model in real-time E-government data processing. Task-based categories: Citizen Record Processing, Service Request Handling, Transaction Monitoring, and Public Feedback Analysis. Efficiency is measured as response time improvement (%).
Additionally, the model’s symmetry-driven regularization techniques enhanced security, making it less vulnerable to data tampering and unauthorized access. This is particularly relevant in an E-government environment where data breaches have significant implications for citizen privacy and trust in public institutions. Figure 7 illustrates the enhanced security metrics achieved by the model in an E-government scenario, showcasing its resilience under high-security demands.
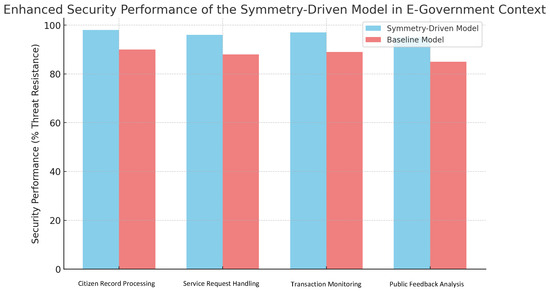
Figure 7.
Enhanced security performance of the symmetry-driven model in an E-government context across task-based categories (Citizen Record Processing, Service Request Handling, Transaction Monitoring, Public Feedback Analysis). Security performance is measured as threat resistance (%).
Privacy and Sustainability Metrics
Although our evaluation focused primarily on attack prevention, future iterations of this model will incorporate privacy metrics (e.g., differential privacy leakage rates) and energy efficiency benchmarks (e.g., FLOPs and Joules per inference) to align with the “Sustainable” dimension of the research.
Concretely, we plan to report
- Differential privacy parameters or equivalent leakage estimates;
- Membership–inference attack AUC as a privacy robustness indicator;
- Energy/performance figures such as FLOPs per inference, Joules per inference, and throughput-per-Watt measured on the target hardware.
5.3. Insights and Challenges
Deploying the symmetry-driven model in an E-government setting revealed unique insights that may guide future research in AI for public sector applications. The model’s symmetry-driven structure not only improved computational efficiency but also led to more stable performance under variable workloads. This stability is essential for public sector applications that experience fluctuating demand, such as peak transaction volumes during specific events.
A challenge encountered during deployment was the model’s sensitivity to parameter tuning, particularly with respect to the regularization term that enforces symmetry. While effective for standardizing data flow and reducing redundancy, this term required careful adjustment to avoid over-regularization, which could diminish the model’s adaptability. Figure 8 presents an analysis of the model’s performance under varying regularization values, indicating the optimal balance for high efficiency and adaptability in real-world settings.
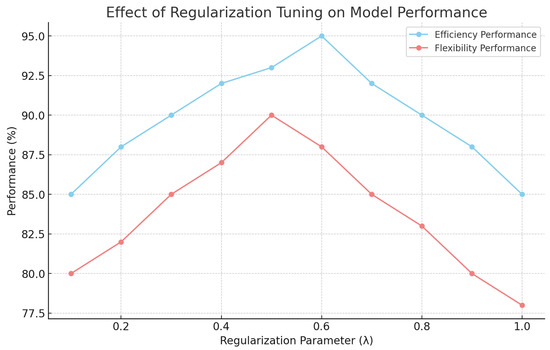
Figure 8.
Effect of regularization tuning on model performance, highlighting the optimal range for efficiency and flexibility.
The deployment of the symmetry-driven neural network in an E-government context demonstrated its effectiveness in achieving secure, efficient data management. However, the insights gained suggest that further refinement, such as adaptive regularization techniques, may enhance its applicability across varied E-government services.
Another important limitation lies in the model’s adaptability to highly irregular or unorganized datasets. While the proposed architecture performs well on structured government data, its performance may degrade when applied to noisy or heterogeneous records. This limitation is partly due to the sensitivity of the regularization parameter , which enforces symmetry. Over-regularization can reduce flexibility, while under-regularization may weaken robustness.
To address this, we suggest the integration of adaptive adjustment mechanisms as a promising direction for future research. Such mechanisms would allow the network to dynamically tune symmetry constraints according to the structure and quality of the incoming data. Moreover, the current study did not explicitly examine distributed deployment scenarios. Considering distributed or federated implementations could further enhance scalability and resilience for large-scale E-government systems.
This study’s contributions underscore the potential of symmetry-driven AI architectures in transforming data handling practices in the public sector, laying the foundation for continued innovation in secure, resource-efficient public administration solutions.
6. Conclusions
This work introduced a new E-government system based on a symmetry-driven neural network model with the aim of improving data security and data processing. Through the incorporation of basic building blocks such as symmetrical configurations of weights and other sharing mechanisms, the model was able to enhance the internal capacities of systems addressing various e-government issues. Major observations from our experimental results revealed the superiority of the model in terms of high-speed performance and a considerable level of robustness against adversarial attacks, hence showing its applicability in duties involving sensitive, large-scale data typical of the public administration setting.
The proposed model’s contributions lie in its innovative use of symmetry-driven regularization to address critical E-government challenges: providing citizens’ data protection, increasing response rates, and making logical use of resources. This work shows the capacity of symmetry-based architectures in revolutionizing data management in E-government to optimize the desirable securities and performance in the sensitive environment that E-government occupies.
Several were spotted during the deployment stage, and others thereafter. In particular, the inflexible deployment of such constraints promoted the symmetry within the model, which did not perform well when tested on datasets that were more irregular and unorganized. This indicates that improvements can be made in the future in terms of adaptive or mixed architectures so that it can prove more versatile in holding large varieties of E-government data without degrading the security and performance feature. Future work might enhance these adjustments whereby the model could scale to new data demands in other substantive public sector contexts.
In addition to the described model, this study provides prospects for further research on the basis of the symmetry of neural networks in AI. The approach seems to have potential in other industries which require secure and effective management of data, including the healthcare and financial industries. Similarities in data sensitivity and system performance suggest that the same advantages of robustness and computation observed here could be applied in these domains. Subsequent studies can pay more attention to the application and assessment of the performance of this model in these fields and further improve its scope.
Author Contributions
Conceptualization, S.A. and F.Q.; methodology, S.A.; software, A.M.A.-Z.; validation, S.A., F.Q. and M.A.; formal analysis, S.A.; investigation, S.A.; resources, F.Q.; data curation, A.M.A.-Z.; writing—original draft preparation, S.A.; writing—review and editing, F.Q. and M.A.; visualization, A.M.A.-Z.; supervision, S.A.; project administration, S.A.; funding acquisition, S.A. and M.A. All authors have read and agreed to the published version of the manuscript.
Funding
This project has been partially supported by AlZaytoonah University of Jordan—Deanship of Scientific Research, Amman, Jordan. Via Grant No. 2024–2025/12/27. This project has also been partially supported by Gulf University for Science and Technology under project code ISG–Case #168.
Data Availability Statement
The original contributions presented in this study are included in the article material. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Veledar, E.; Zhou, L.; Veledar, O.; Gardener, H.; Gutierrez, C.M.; Romano, J.G.; Rundek, T. Synthesizing Explainability Across Multiple ML Models for Structured Data. Algorithms 2025, 18, 368. [Google Scholar] [CrossRef]
- Alzu’bi, S.; Badarneh, O.; Hawashin, B.; Al-Ayyoub, M.; Alhindawi, N.; Jararweh, Y. Multi-label emotion classification for Arabic tweets. In Proceedings of the 2019 Sixth International Conference on Social Networks Analysis, Management and Security (SNAMS), Granada, Spain, 22–25 October 2019; pp. 499–504. [Google Scholar]
- Alia, M.; Hnaif, A.; Alrawashdeh, A.; Jaradat, Y.; Masoud, M.; Manasrah, A.; AlShanty, A. Robust Image Watermarking using DWT, DCT, and PSO with CNN-Based Attack Evaluation. Int. Arab. J. Inf. Technol. (IAJIT) 2024, 21, 967–977. [Google Scholar]
- Wang, L.; Chen, F.; Hu, Y.; Zheng, Z.; Zhang, K. Disassembly of Distribution Transformers Based on Multimodal Data Recognition and Collaborative Processing. Algorithms 2024, 17, 595. [Google Scholar] [CrossRef]
- AlZu’bi, S.; Alsmirat, M.; Al-Ayyoub, M.; Jararweh, Y. Artificial intelligence enabling water desalination sustainability optimization. In Proceedings of the 2019 7th International Renewable and Sustainable Energy Conference (IRSEC), Agadir, Morocco, 27–30 November 2019; pp. 1–4. [Google Scholar]
- Ghizlane, A.; Mohammed, S.; Taibi, S.; Elmostapha, B. Virtual reality for fire evacuation from passenger train. Maejo Int. J. Sci. Technol. 2022, 16, 238–248. [Google Scholar]
- Jararweh, Y.; Fatima, S.; Jarrah, M.; AlZu’bi, S. Smart and sustainable agriculture: Fundamentals, enabling technologies, and future directions. Comput. Electr. Eng. 2023, 110, 108799. [Google Scholar] [CrossRef]
- AlZu’bi, S.; Aqel, D.; Lafi, M. An intelligent system for blood donation process optimization-smart techniques for minimizing blood wastages. Clust. Comput. 2022, 25, 3617–3627. [Google Scholar] [CrossRef]
- Shah, I.A.; Wassan, S.; Usmani, M.H. E-government security and privacy issues: Challenges and preventive approaches. In Cybersecurity Measures for E-Government Frameworks; IGI Global Scientific Publishing: Hershey, PA, USA, 2022; pp. 61–76. [Google Scholar]
- Balaji, K. E-Government and E-Governance: Driving Digital Transformation in Public Administration. In Public Governance Practices in the Age of AI; IGI Global Scientific Publishing: Hershey, PA, USA, 2025; pp. 23–44. [Google Scholar]
- Ilina, O.; Ziyadinov, V.; Klenov, N.; Tereshonok, M. A survey on symmetrical neural network architectures and applications. Symmetry 2022, 14, 1391. [Google Scholar] [CrossRef]
- Li, C.; Ji, S.; Weng, H.; Li, B.; Shi, J.; Beyah, R.; Guo, S.; Wang, Z.; Wang, T. Towards certifying the asymmetric robustness for neural networks: Quantification and applications. IEEE Trans. Dependable Secur. Comput. 2021, 19, 3987–4001. [Google Scholar] [CrossRef]
- Panwar, M.; Hari, N.S.; Biswas, D.; Acharyya, A. M2DA: A low-complex design methodology for convolutional neural network exploiting data symmetry and redundancy. Circuits Syst. Signal Process. 2021, 40, 1542–1567. [Google Scholar] [CrossRef]
- Lindqvist, B. Symmetry Defense Against XGBoost Adversarial Perturbation Attacks. arXiv 2023, arXiv:2308.05575. [Google Scholar] [CrossRef]
- Luo, X.; Liu, Z.; Jin, L.; Zhou, Y.; Zhou, M. Symmetric nonnegative matrix factorization-based community detection models and their convergence analysis. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 1203–1215. [Google Scholar] [CrossRef]
- Shi, H.; Bai, X.; Bai, C. Optimization of Object Detection Network Architecture for High-Resolution Remote Sensing. Algorithms 2025, 18, 537. [Google Scholar] [CrossRef]
- Alzahrani, M.Y. Securing UAV Communications with Homomorphic Encryption and Key Regeneration: A Model Checking Approach. Int. J. Adv. Soft Comput. Its Appl. 2024, 16, 33–46. [Google Scholar] [CrossRef]
- Chen, L.; Wang, Y.; Zhang, L.; Chen, W. The Convergence of Incremental Neural Networks. Neural Process. Lett. 2023, 55, 12481–12499. [Google Scholar] [CrossRef]
- Al-Besher, A.; Kumar, K. Use of artificial intelligence to enhance e-government services. Meas. Sens. 2022, 24, 100484. [Google Scholar]
- Ogunleye, O.S. Using Artificial Intelligence to Enhance E-Government Services Delivery Through Data Science and Machine Learning. In Machine Learning and Data Science Techniques for Effective Government Service Delivery; IGI Global Scientific Publishing: Hershey, PA, USA, 2024; pp. 1–28. [Google Scholar]
- Almajali, M.H.; Alshanty, A.G.; ALmahasnah, M.J. The Role of Governance Supported by Cybersecurity in Reducing Financial and Administrative Corruption in Public Institutions in Jordan. Int. J. Adv. Soft Comput. Its Appl. 2024, 16, 231–251. [Google Scholar] [CrossRef]
- Albous, M.R.; Alboloushi, B. AI-Driven Innovations in E-Government: How Is AI Reshaping the Public Sector? In Harnessing AI, Blockchain, and Cloud Computing for Enhanced e-Government Services; IGI Global Scientific Publishing: Hershey, PA, USA, 2025; pp. 93–118. [Google Scholar]
- Shenify, M.A.; Alghamdi, A.S.; Alharthi, A.F. Hybrid Supervised Machine Learning-based Intrusion Detection System of Internet of Things. Int. J. Adv. Soft Comput. Its Appl. 2024, 16, 68–84. [Google Scholar]
- Ahmed, F. Cybersecurity policy frameworks for AI in government: Balancing national security and privacy concerns. Int. J. Multidiscip. Sci. Manag. 2024, 1, 43–53. [Google Scholar]
- Paudyal, R.; Shakya, S. Secure data mobility in cloud computing for e-Governance application. J. Eng. Technol. Plan. 2021, 2, 1–14. [Google Scholar] [CrossRef]
- Lv, P. Research on the Application of Adaptive Matching Tracking Algorithm Fused with Neural Network in the Development of E-Government. Math. Probl. Eng. 2022, 2022, 1071648. [Google Scholar] [CrossRef]
- Wang, W.; Yang, Y.; Yin, Z.; Dev, K.; Zhou, X.; Li, X.; Qureshi, N.M.F.; Su, C. BSIF: Blockchain-based secure, interactive, and fair mobile crowdsensing. IEEE J. Sel. Areas Commun. 2022, 40, 3452–3469. [Google Scholar] [CrossRef]
- Wang, W.; Xie, Q.; Han, Z.; Su, C.; Rodrigues, J.J.; Wu, K. Secure Enhanced IoT-WLAN Authentication Protocol with Efficient Fast Reconnection. IEEE Trans. Mob. Comput. 2025, 24, 10085–10098. [Google Scholar] [CrossRef]
- Rane, N.; Choudhary, S.; Rane, J. Artificial intelligence for enhancing resilience. J. Appl. Artif. Intell. 2024, 5, 1–33. [Google Scholar] [CrossRef]
- Zhou, K.; Meng, E.; Jin, Q.; Luo, B.; Tian, B. Evaluation of data governance effectiveness in power grid enterprises using deep neural network. Soft Comput. 2023, 27, 18333–18351. [Google Scholar] [CrossRef]
- Careem, R.; Johar, G.; Khatibi, A. Deep neural networks optimization for resource-constrained environments: Techniques and models. Indones. J. Electr. Eng. Comput. Sci. 2024, 33, 1843–1854. [Google Scholar] [CrossRef]
- U.S. Government. Data.gov: Open Data for the United States. 2025. Available online: https://www.data.gov/ (accessed on 2 August 2025).
- New York City Government. NYC Open Data. 2025. Available online: https://opendata.cityofnewyork.us/ (accessed on 2 August 2025).
- Organisation for Economic Co-Operation and Development. OECD Open Data. 2025. Available online: https://data.oecd.org/ (accessed on 2 August 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).