Expansion Lemma—Variations and Applications to Polynomial-Time Preprocessing
Abstract
1. Introduction
2. Preliminaries
2.1. Parameterized Complexity and Kernelization
- if and only if .
- for some computable function .
2.2. Sets, Numbers, and Graph Theory
- (i)
- ;
- (ii)
- ;
- (iii)
- Every connected component of is factor-critical;
- (iv)
- has perfect matching; and
- (v)
- For every nonempty subset , it holds that .
2.3. Graph Parameters
- (i)
- .
- (ii)
- for each edge , there is such that .
- (iii)
- for each vertex , the set of nodes induces a connected subgraph of T.
3. Crown Decomposition and Applications
- ;
- C is an independent set;
- There is no edge between a vertex of C and a vertex of R, i.e., H separates C from R; and
- There exists a matching of size among the edges .
- Finds a matching of size in G; or
- Finds a crown decomposition of G.
- Finds a matching saturating A; or
- Finds a crown decomposition of G, with and .
3.1. Vertex Cover
| Vertex Cover (VC) |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices for every , , or ? |
3.2. -Coloring
| -Coloring |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a coloring such that whenever ? |
3.3. Maximum Satisfiability
| Maximum Satisfiability |
| Input: A Conjunctive Normal Form (CNF) formula ϕ with n variables and m clauses, and a nonnegative integer k. |
| Parameter: k. |
| Question: Does ϕ have a truth assignment satisfying at least k clauses? |
3.4. -List Coloring
| -List Coloring |
| Input: A graph , an integer k and for every , a set of exactly colors. |
| Parameter: k. |
| Question: Is there a proper coloring of G such that for all , the color assigned to u is in ? |
3.5. Longest Cycle Parameterized by Vertex Cover Size
| Longest Cycle (vc) |
| Input: graph G, integers k and ℓ and a vertex cover S of G such that . |
| Parameter: k. |
| Question: Does G contain a cycle on ℓ vertices? |
3.6. Generic Crown Decomposition and Its Application to Packing and Covering Problems
| d-Hitting Set |
| Input: A family of sets over a universe U, where each set in has a size of, at most, d, and an integer k. |
| Parameter: k. |
| Question: Does there exist a subset , such that X contains at least one element from each set in ? |
| d-Set Packing |
| Input: A family of sets over a universe U, where each set in has a size of, at most, d, and an integer k. |
| Parameter: k. |
| Question: Does there exist a subset such that every element in U is contained in at most one set in ? |
- H is a separator in G, one collection of connected components being C.
- .
- There is an injective mapping , such that
- -
- For all , , and
- -
- Each is a neighbor of, at most, one .
- are the remaining vertices.
| d-Red/Blue Dominating Set |
| Input: A bipartite graph , where , and an integer k. |
| Parameter: k. |
| Question: Does there exist a subset such that X such that ? |
| d-Red/Blue Distance-3 Packing |
| Input: A bipartite graph , where , and an integer k. |
| Parameter: k. |
| Question: Does there exist a subset such that each is a neighbor of, at most, one ? |
- H (the head) separates C from X in G.
- (C is the crown) induces no subgraph that is a tree with r edges.
- There are r injective mappings from H to C called witness functions such that for all , and for each , the vertex set forms a tree with r edges in G.
| r-Edge-Tree-Packing |
| Input: An undirected graph G and an integer k. |
| Parameter: k |
| Question: Is there a set of at least k pairwise disjointed collections of trees with r edges in G? |
| r-Edge-Tree-Covering |
| Input: An undirected graph G and an integer k. |
| Parameter: k |
| Question: Is there a set S of, at most, k vertices, such that has no tree with r edges as a subgraph? |
3.7. Other Examples
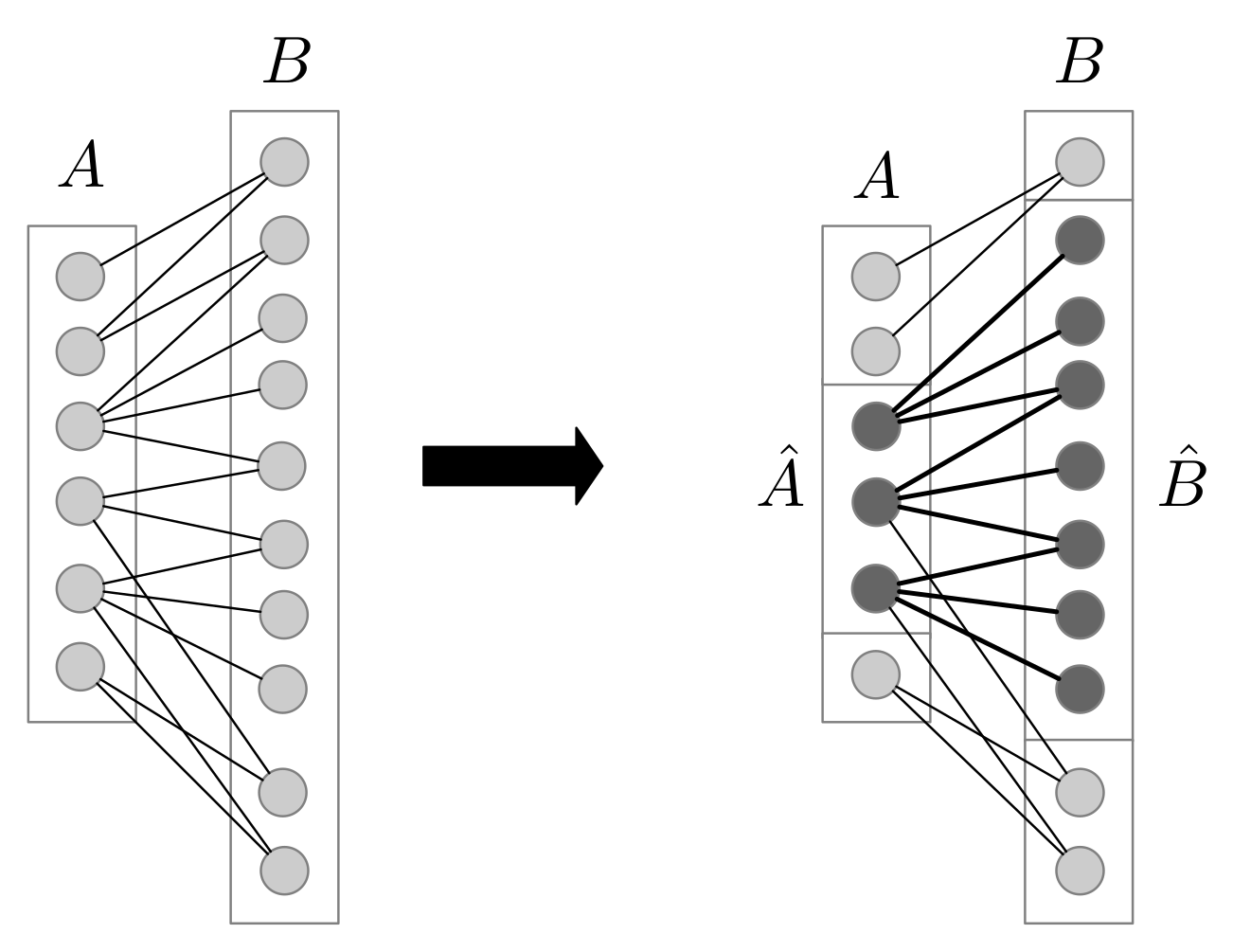
4. (Basic) Expansion Lemma and Applications
- Every vertex of A is incident to exactly q edges of M, and
- M Saturates exactly vertices in B.
- , and
- There are no isolated vertices in B.
- 1.
- There is a q-expansion of X into Y, and
- 2.
- .
4.1. p-Component Order Connectivity
| p-Component Order Connectivity |
| Input: Graph G and an integer k. |
| Parameter: k. |
| Question: Does G contain a subset S of vertices, , such that every connected component of has a size of, at most, p? |
4.2. Undirected Feedback Vertex Set
| Feedback Vertex Set (FVS) |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that is acyclic? |
4.3. Cluster Vertex Deletion
| Cluster Vertex Deletion (cvd) |
| Input: Graph G and an integer k. |
| Parameter: k. |
| Question: Does G contain a subset S of, at most, k vertices, such that every connected component of is a clique? |
4.4. Other Deletion Problems
| d-Path Vertex Cover (d-PVC) |
| Input: An undirected graph and an integer k. |
| Parameter: k |
| Question: Is there a set of, at most, k vertices, such that has no path of length d? |
| VC-2-Mod |
| Input: A graph , a set such that every vertex of has a degree of, at most, 2, and an integer k. |
| Parameter: |
| Question: Does G have a vertex cover with a size of, at most, k? |
| Pathwidth-One Vertex Deletion |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that has a pathwidth of, at most, one? |
| Block Graph Vertex Deletion |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that is a block graph? |
| Chordal Vertex Deletion |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that has no induced cycle of a length of (at least) four? |
| Even Cycle Transversal |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that has no even cycle? |
| Out-Forest Vertex Deletion Set |
| Input: A directed graph and a positive integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that is an out-forest? |
| Independent Feedback Vertex Set |
| Input: An undirected graph and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that S is an independent set and is acyclic? |
4.5. Graph Packing Problems
| Almost t-Disjoint Cycle Packing |
| Input: An undirected graph G and an integer k. |
| Parameter: k. |
| Question: Are there at least k distinct cycles in G, such that every vertex of G appears in, at most, t of these cycles? |
| Pairwise t-Disjoint Cycle Packing (t-PDCP) |
| Input: An undirected graph G and an integer k. |
| Parameter: k. |
| Question: Are there at least k distinct cycles in G such that for every , ? |
| 3-Path Packing |
| Input: An undirected graph and an integer k. |
| Parameter: k |
| Question: Are there k pairwise vertex disjoints inducing in G? |
4.6. Other Problems
| Set splitting |
| Input: A universe , a family of subsets of , and a positive integer k. |
| Parameter: k. |
| Question: Is there a bipartition of such that at least k sets have non-empty intersection with both parts? |
| Maximum internal spanning tree |
| Input: Graph G and a positive integer k. |
| Parameter: k. |
| Question: Is there a spanning tree of G with at least k internal vertices? |
5. Recent Developments
5.1. Weighted q-Expansion Lemma
- for every , , and
- for every , .
- 1.
- ; and
- 2.
- There are no isolated vertices in B.
- f is a weighted q-expansion of X into Y, and
- No vertex in Y has a neighbor outside X, i.e., .
5.2. Stronger Expansion Lemma and Double Expansion Lemma
- 1.
- has a stronger q-expansion into ,
- 2.
- , and
- 3.
- .
- Initially, the authors apply some preprocessing rules to the input graph D and ensure that every arc of D is contained in at most distinct 4-cycles, the pairwise intersection of which is .
- Let be a collection of the maximal set of 4-cycles, such that for every pair of 4-cycles in , there is at most one common vertex. The authors prove that if , then the input is a YES instance.
- So, it can be assumed that . Let be the set of all 3 paths that are contained in the 4-cycle in . As , is . What is left is to bind the number of vertices in .
- The authors construct an auxiliary bipartite graph H with bipartitions A and B where and . For and , there is an edge in H if and only if is a 4-cycle in D.
- One can now apply Lemma 5 with and obtain a stronger 1-expansion with sets and . It ensures that . Let be the set of edges of H such that every vertex of is incident to exactly one vertex of and every vertex of is incident to exactly one vertex of .
- Finally, the authors apply a reduction rule that deletes the set of vertices from , which is not saturated by . The 4-cycles that these vertices are part of can be covered by picking one of the vertices from the corresponding 3-paths in . The matching M ensures that there exists a 4-cycle for each 3-path in . Thus, the reduction rule is safe.
- The reduction rule is no longer applicable when the set of vertices from that is not saturated by is empty. In this case, we have , which is . Thus, we obtain a kernel with vertices.
| Arc Disjoint r-Cycle Packing |
| Input: A directed graph and an integer k. |
| Parameter: k |
| Question: Are there at least k pairwise arc disjoint directed cycles of length r in D? |
| Triangle Packing in Tournaments |
| Input: A tournament and an integer k. |
| Parameter: k. |
| Question: Are there at least k pairwise vertex disjoint directed triangles in D? |
- 1.
- ,
- 2.
- ,
- 3.
- has a stronger q-expansion into and for every , has a stronger q-expansion into in ,
- 4.
- , and
- 5.
- for all , .
| Feedback Vertex Set in Tournaments |
| Input: A tournament and an integer k. |
| Parameter: k. |
| Question: Is there a set of, at most, k vertices, such that is acyclic? |
5.3. Balanced Expansion and Balanced Crown Decomposition
- 1.
- if ,
- 2.
- if ,
- 3.
- for all , , and
- 4.
- .
- 1.
- if ,
- 2.
- if ,
- 3.
- for all , , and
- 4.
- , where for , for and .
- 1.
- there are no edges from C to R,
- 2.
- for each ,
- 3.
- for every ,
- 4.
- for each , and
- 5.
- is connected and for each .
| W-Weight Separator |
| Input: A vertex-weighted undirected graph and integer k. |
| Question: Is there a set of, at most, k vertices, such that every connected component of has a total weight of less than W? |
| W-Weight Packing |
| Input: A vertex-weighted undirected graph and integers k. |
| Question: Are there k pairwise disjoint sets , such that for every , and is connected? |
| Max-Min (Min–Max) Balanced Connected Partition |
| Input: A vertex-weighted undirected graph and integer k. |
| Question: Is there a partition of such that for each , and is connected? |
5.4. Additive Expansion Lemma
- There is a q-additive expansion of into ; and
- No vertex of has the neighbor outside , i.e., .
- First, they consider the LP formulation of Vertex Cover. By Nemhauser and Trotter [62], there is a fractional optimal solution for the LP formulation of Vertex Cover such that all vertices are assigned values of either 0, 1, or 1/2.
- Let denote the vertices that are assigned values 0, 1, 1/2, respectively. If , then the instance is a no-instance.
- Otherwise, they construct an auxiliary bipartite graph, and apply the expansion lemma to obtain a kernel with vertices.
| Partial vertex cover |
| Input: An undirected graph and two integers . |
| Parameter: |
| Question: Is there a set S of, at most, k vertices, such that has (at most) edges? |
6. Conclusions and Future Research
- There are some other well-studied vertex deletion problems in the kernelization perspective, e.g., an vertex kernel for Split Vertex Deletion (see [63]) but it has a kernel lower bound of edges [4]. It would be interesting to see if one of these variants of the expansion lemma can be useful to obtain a sub-quadratic vertex kernel for these problems.
- Recently, Jacob et al. [64,65] introduced the study of vertex deletion problems to scattered graph classes. While they proved parameterized complexity of this problem, kernelization complexity is open and unexplored. It would be nice to explore if the expansion lemma or some of its variants can be useful for this.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cygan, M.; Fomin, F.V.; Kowalik, L.; Lokshtanov, D.; Marx, D.; Pilipczuk, M.; Pilipczuk, M.; Saurabh, S. Parameterized Algorithms; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Bodlaender, H.L.; Downey, R.G.; Fellows, M.R.; Hermelin, D. On problems without polynomial kernels. J. Comput. Syst. Sci. 2009, 75, 423–434. [Google Scholar] [CrossRef]
- Dom, M.; Lokshtanov, D.; Saurabh, S. Kernelization lower bounds through colors and IDs. ACM Trans. Algorithms (TALG) 2014, 11, 1–20. [Google Scholar] [CrossRef]
- Dell, H.; Van Melkebeek, D. Satisfiability allows no nontrivial sparsification unless the polynomial-time hierarchy collapses. J. ACM (JACM) 2014, 61, 1–27. [Google Scholar] [CrossRef]
- Chor, B.; Fellows, M.; Juedes, D. Linear kernels in linear time, or how to save k colors in O(n2) steps. In Proceedings of the International Workshop on Graph-Theoretic Concepts in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; pp. 257–269. [Google Scholar]
- Thomassé, S. A 4k2 kernel for feedback vertex set. ACM Trans. Algorithms 2010, 6, 1–8. [Google Scholar] [CrossRef]
- Niedermeier, R. Invitation to Fixed-Parameter Algorithms; Oxford University Press: Oxford, UK, 2006. [Google Scholar]
- Guo, J.; Niedermeier, R. Invitation to data reduction and problem kernelization. SIGACT News 2007, 38, 31–45. [Google Scholar] [CrossRef]
- Downey, R.G.; Fellows, M.R. Fundamentals of Parameterized Complexity; Texts in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Flum, J.; Grohe, M. Parameterized Complexity Theory; Texts in Theoretical Computer Science. An EATCS Series; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Fomin, F.V.; Lokshtanov, D.; Saurabh, S.; Zehavi, M. Kernelization—Theory of Parameterized Preprocessing; Cambridge University Press: Cambridge, UK, 2019. [Google Scholar]
- Diestel, R. Graph Theory, 4th ed.; Graduate Texts in Mathematics; Springer: Berlin/Heidelberg, Germany, 2012; Volume 173. [Google Scholar]
- Hall, P. On Representatives of Subsets. J. Lond. Math. Soc. 1987, S1–S10, 26–30. [Google Scholar]
- Edmonds, J. Paths, Trees, and Flowers. Can. J. Math. 1965, 17, 449–467. [Google Scholar] [CrossRef]
- Lovasz, L.; Plumber, M.D. Matching Theory; AMS Chelsea Publishing, American Mathematical Society: Providence, RI, USA, 2000. [Google Scholar]
- Robertson, N.; Seymour, P.D. Graph minors. III. Planar tree-width. J. Comb. Theory Ser. B 1984, 36, 49–64. [Google Scholar] [CrossRef]
- Robertson, N.; Seymour, P.D. Graph Minors. II. Algorithmic Aspects of Tree-Width. J. Algorithms 1986, 7, 309–322. [Google Scholar] [CrossRef]
- Robertson, N.; Seymour, P.D. Graph minors. IV. Tree-width and well-quasi-ordering. J. Comb. Theory Ser. B 1990, 48, 227–254. [Google Scholar] [CrossRef]
- Chen, J.; Fernau, H.; Shaw, P.; Wang, J.; Yang, Z. Kernels for packing and covering problems. Theor. Comput. Sci. 2019, 790, 152–166. [Google Scholar] [CrossRef]
- Fellows, M.R. Blow-ups, win/win’s, and crown rules: Some new directions in FPT. In Proceedings of the International Workshop on Graph-Theoretic Concepts in Computer Science; Springer: Berlin/Heidelberg, Germany, 2003; pp. 1–12. [Google Scholar]
- Hopcroft, J.E.; Karp, R.M. An n^5/2 algorithm for maximum matchings in bipartite graphs. SIAM J. Comput. 1973, 2, 225–231. [Google Scholar] [CrossRef]
- Lampis, M. A kernel of order 2k − c log k for vertex cover. Inf. Process. Lett. 2011, 111, 1089–1091. [Google Scholar] [CrossRef]
- Li, W.; Zhu, B. A 2k-kernelization algorithm for Vertex Cover based on Crown Decomposition. Theor. Comput. Sci. 2018, 739, 80–85. [Google Scholar] [CrossRef]
- Li, W.; Ding, Y.; Yang, Y.; Rong, G. A (2 + ϵ)k-vertex kernel for the dual coloring problem. Theor. Comput. Sci. 2021, 868, 6–11. [Google Scholar] [CrossRef]
- Lokshtanov, D. New Methods in Parameterized Algorithms and Complexity; University of Bergen: Bergen, Norway, 2009. [Google Scholar]
- Banik, A.; Jacob, A.; Paliwal, V.K.; Raman, V. Fixed-parameter tractability of (n − k) list coloring. Theory Comput. Syst. 2020, 64, 1307–1316. [Google Scholar] [CrossRef]
- Bodlaender, H.L.; Jansen, B.M.P.; Kratsch, S. Kernel bounds for path and cycle problems. Theor. Comput. Sci. 2013, 511, 117–136. [Google Scholar] [CrossRef]
- Fellows, M.; Heggernes, P.; Rosamond, F.; Sloper, C.; Telle, J.A. Finding k disjoint triangles in an arbitrary graph. In Proceedings of the International Workshop on Graph-Theoretic Concepts in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; pp. 235–244. [Google Scholar]
- Prieto, E.; Sloper, C. Reducing to independent set structure: The case of k-internal spanning tree. Nord. J. Comput. 2005, 12, 308–318. [Google Scholar]
- Chlebík, M.; Chlebíková, J. Crown reductions for the minimum weighted vertex cover problem. Discret. Appl. Math. 2008, 156, 292–312. [Google Scholar] [CrossRef]
- Abu-Khzam, F.N. A kernelization algorithm for d-hitting set. J. Comput. Syst. Sci. 2010, 76, 524–531. [Google Scholar] [CrossRef]
- Abu-Khzam, F.N. An improved kernelization algorithm for r-Set Packing. Inf. Process. Lett. 2010, 110, 621–624. [Google Scholar] [CrossRef]
- Wang, J.; Ning, D.; Feng, Q.; Chen, J. An improved kernelization for P2-packing. Inf. Process. Lett. 2010, 110, 188–192. [Google Scholar] [CrossRef]
- Xiao, M.; Kou, S. Kernelization and Parameterized Algorithms for 3-Path Vertex Cover. In Proceedings of the Theory and Applications of Models of Computation—14th Annual Conference, TAMC 2017, Bern, Switzerland, 20–22 April 2017; Lecture Notes in Computer Science. Gopal, T.V., Jäger, G., Steila, S., Eds.; Volume 10185, pp. 654–668. [Google Scholar]
- Gallai, T. Maximum-minimum Sätze und verallgemeinerte Faktoren von Graphen. Acta Math. Hung. 1961, 12, 131–173. [Google Scholar] [CrossRef]
- Iwata, Y. Linear-Time Kernelization for Feedback Vertex Set. In Proceedings of the 44th International Colloquium on Automata, Languages, and Programming, ICALP 2017, Warsaw, Poland, 10–14 July 2017; LIPIcs. Chatzigiannakis, I., Indyk, P., Kuhn, F., Muscholl, A., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany; Volume 80, pp. 68:1–68:14. [Google Scholar]
- Fomin, F.V.; Le, T.; Lokshtanov, D.; Saurabh, S.; Thomassé, S.; Zehavi, M. Subquadratic Kernels for Implicit 3-Hitting Set and 3-Set Packing Problems. ACM Trans. Algorithms 2019, 15, 13:1–13:44. [Google Scholar] [CrossRef]
- Cervený, R.; Suchý, O. Faster FPT Algorithm for 5-Path Vertex Cover. In Proceedings of the 44th International Symposium on Mathematical Foundations of Computer Science, MFCS 2019, Aachen, Germany, 26–30 August 2019; LIPIcs. Rossmanith, P., Heggernes, P., Katoen, J., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany; Volume 138, pp. 32:1–32:13. [Google Scholar]
- Cervený, R.; Choudhary, P.; Suchý, O. On Kernels for d-Path Vertex Cover. arXiv 2021, arXiv:2107.12245. [Google Scholar]
- Majumdar, D.; Raman, V.; Saurabh, S. Polynomial Kernels for Vertex Cover Parameterized by Small Degree Modulators. Theory Comput. Syst. 2018, 62, 1910–1951. [Google Scholar] [CrossRef]
- Philip, G.; Raman, V.; Villanger, Y. A Quartic Kernel for Pathwidth-One Vertex Deletion. In Proceedings of the Graph Theoretic Concepts in Computer Science—36th International Workshop, WG 2010, Zarós, Crete, Greece, 28–30 June 2010; Lecture Notes in Computer Science. Thilikos, D.M., Ed.; Volume 6410, pp. 196–207. [Google Scholar]
- Cygan, M.; Pilipczuk, M.; Pilipczuk, M.; Wojtaszczyk, J.O. An Improved FPT Algorithm and a Quadratic Kernel for Pathwidth One Vertex Deletion. Algorithmica 2012, 64, 170–188. [Google Scholar] [CrossRef]
- Kim, E.J.; Kwon, O. A Polynomial Kernel for Block Graph Deletion. In Proceedings of the 10th International Symposium on Parameterized and Exact Computation, IPEC 2015, Patras, Greece, 16–18 September 2015; LIPIcs. Husfeldt, T., Kanj, I.A., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany; Volume 43, pp. 270–281. [Google Scholar]
- Agrawal, A.; Kolay, S.; Lokshtanov, D.; Saurabh, S. A Faster FPT Algorithm and a Smaller Kernel for Block Graph Vertex Deletion. In Proceedings of the LATIN 2016: Theoretical Informatics—12th Latin American Symposium, Ensenada, Mexico, 11–15 April 2016; Lecture Notes in Computer Science. Kranakis, E., Navarro, G., Chávez, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9644, pp. 1–13. [Google Scholar]
- Jansen, B.M.P.; Pilipczuk, M. Approximation and Kernelization for Chordal Vertex Deletion. SIAM J. Discret. Math. 2018, 32, 2258–2301. [Google Scholar] [CrossRef]
- Agrawal, A.; Lokshtanov, D.; Misra, P.; Saurabh, S.; Zehavi, M. Feedback vertex set inspired kernel for chordal vertex deletion. ACM Trans. Algorithms (TALG) 2018, 15, 1–28. [Google Scholar]
- Misra, P.; Raman, V.; Ramanujan, M.S.; Saurabh, S. Parameterized Algorithms for Even Cycle Transversal. In Proceedings of the Graph-Theoretic Concepts in Computer Science—38th International Workshop, WG 2012, Jerusalem, Israel, 26–28 June 2012; Revised Selected Papers; Lecture Notes in Computer Science. Golumbic, M.C., Stern, M., Levy, A., Morgenstern, G., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7551, pp. 172–183. [Google Scholar]
- Mnich, M.; van Leeuwen, E.J. Polynomial kernels for deletion to classes of acyclic digraphs. Discret. Optim. 2017, 25, 48–76. [Google Scholar] [CrossRef]
- Agrawal, A.; Saurabh, S.; Sharma, R.; Zehavi, M. Kernels for deletion to classes of acyclic digraphs. J. Comput. Syst. Sci. 2018, 92, 9–21. [Google Scholar]
- Misra, N.; Philip, G.; Raman, V.; Saurabh, S. On Parameterized Independent Feedback Vertex Set. Theor. Comput. Sci. 2012, 461, 65–75. [Google Scholar] [CrossRef]
- Bodlaender, H.L.; Thomassé, S.; Yeo, A. Kernel bounds for disjoint cycles and disjoint paths. Theor. Comput. Sci. 2011, 412, 4570–4578. [Google Scholar] [CrossRef]
- Agrawal, A.; Lokshtanov, D.; Majumdar, D.; Mouawad, A.E.; Saurabh, S. Kernelization of Cycle Packing with Relaxed Disjointness Constraints. SIAM J. Discret. Math. 2018, 32, 1619–1643. [Google Scholar] [CrossRef]
- Bessy, S.; Bougeret, M.; Thilikos, D.M.; Wiederrecht, S. Kernelization for Graph Packing Problems via Rainbow Matching. In Proceedings of the 2023 ACM-SIAM Symposium on Discrete Algorithms, SODA 2023, Florence, Italy, 22–25 January 2023; Bansal, N., Nagarajan, V., Eds.; SIAM: Bangkok, Thailand, 2023; pp. 3654–3663. [Google Scholar]
- Lokshtanov, D.; Saurabh, S. Even faster algorithm for set splitting! In Proceedings of the International Workshop on Parameterized and Exact Computation; Springer: Berlin/Heidelberg, Germany, 2009; pp. 288–299. [Google Scholar]
- Fomin, F.V.; Gaspers, S.; Saurabh, S.; Thomassé, S. A linear vertex kernel for maximum internal spanning tree. J. Comput. Syst. Sci. 2013, 79, 1–6. [Google Scholar] [CrossRef]
- Kumar, M.; Lokshtanov, D. A 2lk Kernel for l-Component Order Connectivity. In Proceedings of the 11th International Symposium on Parameterized and Exact Computation, IPEC 2016, Aarhus, Denmark, 24–26 August 2016; pp. 20:1–20:14. [Google Scholar]
- Xiao, M. Linear kernels for separating a graph into components of bounded size. J. Comput. Syst. Sci. 2017, 88, 260–270. [Google Scholar] [CrossRef]
- Babu, J.; Krithika, R.; Rajendraprasad, D. Packing Arc-Disjoint 4-Cycles in Oriented Graphs. In Proceedings of the 42nd IARCS Annual Conference on Foundations of Software Technology and Theoretical Computer Science, FSTTCS 2022, IIT Madras, Chennai, India, 18–20 December 2022; LIPIcs. Dawar, A., Guruswami, V., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2022; Volume 250, pp. 5:1–5:16. [Google Scholar]
- Mnich, M.; Williams, V.V.; Végh, L.A. A 7/3-Approximation for Feedback Vertex Sets in Tournaments. In Proceedings of the 24th Annual European Symposium on Algorithms, ESA 2016, Aarhus, Denmark, 22–24 August 2016; LIPIcs. Sankowski, P., Zaroliagis, C.D., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2016; Volume 57, pp. 67:1–67:14. [Google Scholar]
- Casel, K.; Friedrich, T.; Issac, D.; Niklanovits, A.; Zeif, Z. Balanced Crown Decomposition for Connectivity Constraints. In Proceedings of the 29th Annual European Symposium on Algorithms, ESA 2021, Lisbon, Portugal, 6–8 September 2021; LIPIcs. Mutzel, P., Pagh, R., Herman, G., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2021; Volume 204, pp. 26:1–26:15. [Google Scholar]
- Koana, T.; Nichterlein, A.; Wünsche, N. Kernelization for Partial Vertex Cover via (Additive) Expansion Lemma. arXiv 2022, arXiv:2211.07001. [Google Scholar]
- Nemhauser, G.L.; Trotter, L.E., Jr. Vertex packings: Structural properties and algorithms. Math. Program. 1975, 8, 232–248. [Google Scholar] [CrossRef]
- Agrawal, A.; Gupta, S.; Jain, P.; Krithika, R. Quadratic vertex kernel for split vertex deletion. Theor. Comput. Sci. 2020, 833, 164–172. [Google Scholar] [CrossRef]
- Jacob, A.; Majumdar, D.; Raman, V. Parameterized Complexity of Deletion to Scattered Graph Classes. In Proceedings of the 15th International Symposium on Parameterized and Exact Computation, IPEC 2020, Hong Kong, China, 14–18 December 2020; LIPIcs. Cao, Y., Pilipczuk, M., Eds.; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2020; Volume 180, pp. 18:1–18:17. [Google Scholar]
- Jacob, A.; Majumdar, D.; Raman, V. Faster FPT Algorithms for Deletion to Pairs of Graph Classes. In Proceedings of the Fundamentals of Computation Theory—23rd International Symposium, FCT 2021, Athens, Greece, 12–15 September 2021; Lecture Notes in Computer Science. Bampis, E., Pagourtzis, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2021; Volume 12867, pp. 314–326. [Google Scholar]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jacob, A.; Majumdar, D.; Raman, V. Expansion Lemma—Variations and Applications to Polynomial-Time Preprocessing. Algorithms 2023, 16, 144. https://doi.org/10.3390/a16030144
Jacob A, Majumdar D, Raman V. Expansion Lemma—Variations and Applications to Polynomial-Time Preprocessing. Algorithms. 2023; 16(3):144. https://doi.org/10.3390/a16030144
Chicago/Turabian StyleJacob, Ashwin, Diptapriyo Majumdar, and Venkatesh Raman. 2023. "Expansion Lemma—Variations and Applications to Polynomial-Time Preprocessing" Algorithms 16, no. 3: 144. https://doi.org/10.3390/a16030144
APA StyleJacob, A., Majumdar, D., & Raman, V. (2023). Expansion Lemma—Variations and Applications to Polynomial-Time Preprocessing. Algorithms, 16(3), 144. https://doi.org/10.3390/a16030144




