1. Introduction
As geographic information data, high resolution remote sensing (HRRS) images have the characteristics of rich information, high security, and rapid updating, which can provide a lot of valuable information for geoscience research. While HRRS images are widely used in urban planning, disaster relief, resource development, the military, and other fields [
1,
2,
3], the integrity authentication of HRRS images is exposed. The rapid development of information and network technology has made the acquisition, transmission, and storage of HRRS images very convenient and frequent, but has also made the traditional technology-oriented authentication move towards a stand-alone mode, and is thus in trouble. The rise of blockchain technology provides new technical support for solving the problem of HRRS image authentication in a cloud network environment. Blockchains have been successfully applied to the protection of images [
4,
5] and videos [
6], showing great application potential. In addition, some scholars have begun to apply blockchain technology to the sharing of remote sensing images [
7,
8].
However, the mainstream blockchain with the cryptographic hash function as the main technical means is too sensitive to data changes at the binary level and cannot fully meet the integrity authentication requirements of HRRS images. For example, after HRRS image format conversion (such as from TIFF format to PNG format), the content of the HRRS image has not changed. Still, its binary representation has undergone massive changes. In this case, the mainstream blockchain still believes that the HRRS image has been tampered with, which is obviously unreasonable. Subject-sensitive hashing can solve the above problems very well.
Subject-sensitive hashing [
9] is a new type of hashing technology developed on the basis of perceptual hashing [
10,
11,
12]. The main difference between subject-sensitive hashing and perceptual hashing is “subject sensitivity”. Subject-sensitive hashing retains the robustness of perceptual hashing and can perform stricter integrity authentication on the image content that users pay attention to. However, the existing subject-sensitive hashing for HRRS images focuses on the overall performance of the algorithm, while the subject-sensitive hashing used in the blockchain should be more sensitive to tampering than in the conventional environment, because the data on the blockchain are difficult to change after they are on the chain.
In this paper, based on the analysis of the blockchain’s demand for subject-sensitive hashing, we propose a subject-sensitive hashing algorithm specially used for HRRS image blockchains, which overcomes the deficiency that mainstream blockchain technologies can only perform a binary-level authentication for HRRS images. The contributions of this paper can be summarized as follows:
- (1)
We provide an in-depth analysis of the requirements for blockchain-oriented subject-sensitive hashing.
- (2)
We refine the improved blockchain model based on subject-sensitive hashing for HRRS images.
- (3)
We propose a new deep neural network MultiRes-RCF for extracting subject-sensitive features of HRRS images and implement a subject-sensitive hashing algorithm based on MultiRes-RCF.
The rest of the paper is composed as follows: The related works are described in
Section 2.
Section 3 discusses the details of our proposed method. The details of the experiments and discussion are presented in
Section 4, and the conclusions are drawn in
Section 5.
2. Preliminaries
2.1. Blockchain
A blockchain [
13] is a chain structure with data blocks as the basic unit. Blockchains were initially used in the field of digital currency and later expanded to many industries such as the Internet of Things [
14,
15], supply chain management [
16,
17], medical care [
18], education [
19] and e-commerce [
20]. Essentially, a blockchain is a decentralized database: instead of just one master database storing the blockchain’s data, multiple copies of the same blockchain data are distributed across a peer-to-peer network. In a blockchain, data are stored on the chain in the form of blocks. Each block is connected in chronological order and is mainly composed of a block header containing metadata and a block body containing the specific block data stored in this block [
21]. The implementation process of a blockchain integrates various technologies such as cryptography and distributed systems to build a distributed environment, in which transactions can be performed safely without mutual trust and solves the problems of data storage security that may be caused by central institutions. With the in-depth development of blockchain technology, it has also been initially developed and applied in remote sensing [
7,
8]. The immutability guarantees the integrity of the on-chain HRRS image to a large extent.
However, there are still many deficiencies in the authentication technology of a HRRS images’ blockchain. The outstanding problem is that the blockchain is too sensitive to changes in the content of HRRS images. For example, after the format conversion of the HRRS image on the chain, although the image has changed a lot at the binary level, its effective content has not changed significantly. In fact, the users of HRRS images are more concerned about whether the effective content of the HRRS images has been tampered with, rather than whether the carrier of the content has changed. The root of the above problem is that the blockchain uses a cryptographic hash function (SHA-1 or SHA-256) to generate the digital digest of the HRRS image, which can be solved by subject-sensitive hashing.
2.2. Subject-Sensitive Hashing
Subject-sensitive hashing [
9], also known as the subject-sensitive hash algorithm, is a new hashing technology based on perceptual hashing. Subject-sensitive hashing focuses the goal of integrity authentication on the types of features that users are interested in. It overcomes the insufficiency of perceptual hashing and can achieve “customized” integrity authentication according to the actual needs of the users. A subject-sensitive hashing algorithm generally includes the following steps: subject-sensitive feature extraction, feature quantization, and feature encoding. In the above steps, subject-sensitive feature extraction focuses on extracting the type of information that users pay attention to, taking into account other types of feature information; feature quantization is conducted to remove the redundancy of the extracted features; and feature encoding is performed to compress and encrypt the quantized features to obtain a subject-sensitive hash sequence. Among them, feature extraction is the key step.
The existing subject-sensitive hashing algorithms for HRRS images are mainly implemented based on deep learning. In [
9], a deep neural network model MUM-Net for subject-sensitive hashing is proposed. The subject-sensitive hash algorithm based on MUM-Net has good robustness and tamper sensitivity, but the model has high computational complexity. In [
22], a lightweight deep neural network Semi-U-net is proposed, which overcomes the shortcomings of MUM-Net’s low computational efficiency and overly complex model. In [
23], a deep neural network model AAU-Net based on the Attention mechanism was proposed, which significantly enhanced the distinction between “subject-related tampering” and “subject-unrelated tampering”.
Different subject-sensitive hashing algorithms often have significant differences in specific properties. For example, the Attention ResU-Net-based subject-sensitive hashing algorithm has good robustness, but its tamper sensitivity is not good, making it unsuitable for HRRS image integrity authentication [
23]. This means that the specific subject-sensitive hashing algorithm implementation process should be determined according to the application requirements of the algorithm.
However, to the best of our knowledge, there is no research on subject-sensitive hashing algorithms specifically for blockchains. We believe that subject-sensitive hashing algorithms for blockchains should meet the following requirements:
- (1)
Since the authentication information of HRRS images cannot be modified once it is uploaded to the chain, the subject-sensitive hashing algorithm should be as sensitive as possible to the feature information on multi-level scales to satisfy the later integrity authentication in various environments.
- (2)
Due to the difference in cost sensitivity, undetected tampering often causes more harm to HRRS images. Therefore, the subject-sensitive hashing algorithm used in blockchains should have good tamper sensitivity, and slight tampering of HRRS images should be detected, especially tampering of changing only a few pixels, which is not usually considered tampering in some other applications.
- (3)
The scope of maintaining robustness should not be broad, i.e., it can only maintain robustness for operations that do not affect the later application of HRRS images, such as format conversion and copyright watermark embedding.
Based on the aforementioned considerations, we designed a blockchain-oriented subject-sensitive hashing algorithm in this paper.
3. The Proposed Method
Aiming at the problem that blockchains are too sensitive to image changes in HRRS image authentication, we refined the improved blockchain for HRRS image authentication based on subject-sensitive hashing and propose a subject-sensitive hashing algorithm specifically for this improved blockchain.
3.1. Structure of the Improved Blockchain Based on Subject-Sensitive Hashing
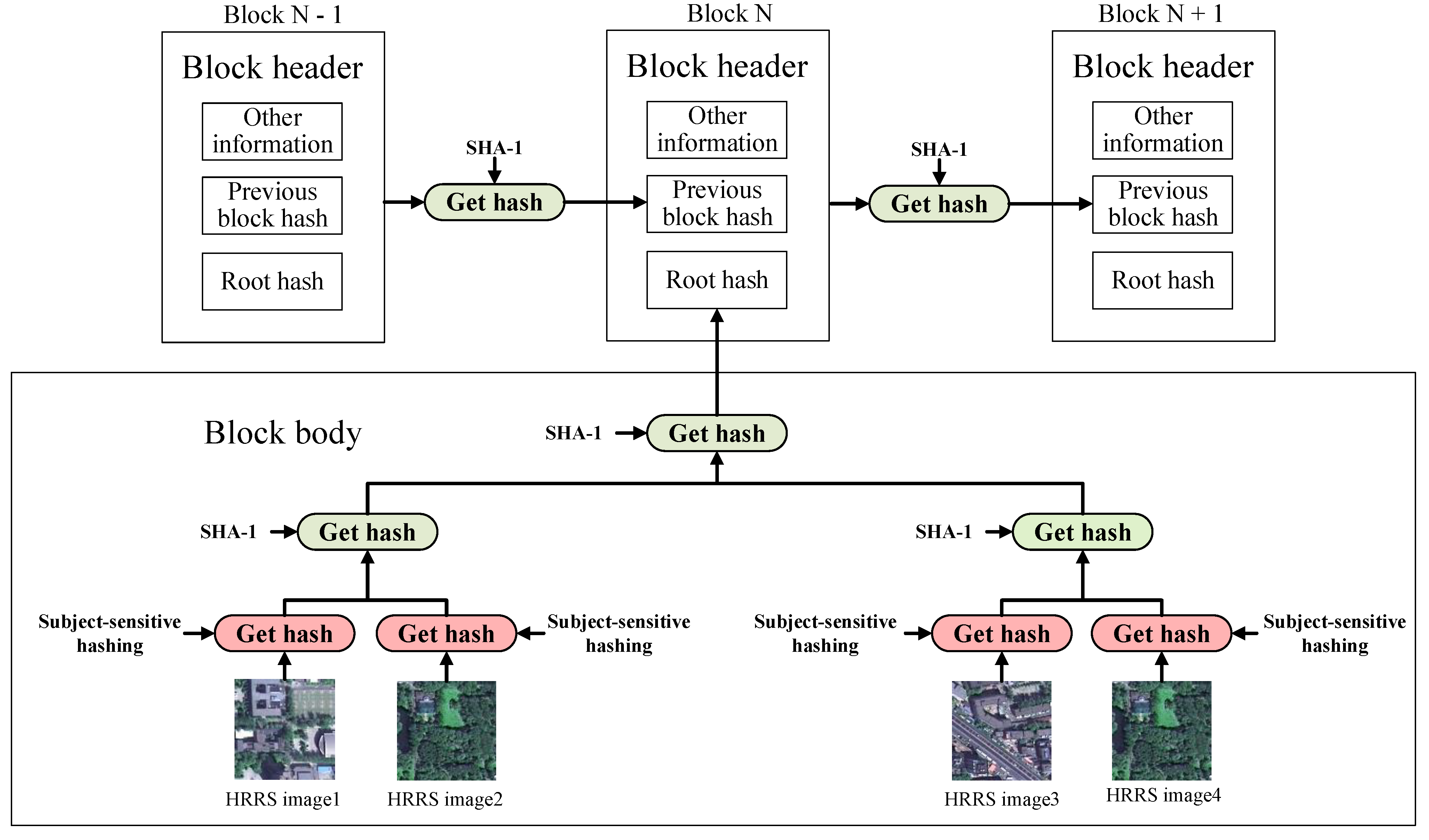
The structure of the improved blockchain is shown in
Figure 1. The most obvious improvement is using two kinds of hashing methods, subject-sensitive hashing and SHA-1, instead of just a cryptographic hash function. The subject-sensitive hashing is used to calculate the digital digest of the HRRS image, that is, the subject-sensitive hash sequence; SHA-1 is used to ensure the security of the blockchain. Furthermore, we propose a subject-sensitive hashing algorithm dedicated to this method, which will be discussed in detail in
Section 3.2.
As shown in
Figure 1, the structure of the block header of the improved blockchain is the same as that of the conventional blockchain, but the block body has specific differences. The block header contains the following information:
- (1)
The root hash is the hash value of the block body. If there is only one HRRS image, the root hash can use a subject-sensitive hash sequence instead of compressing multiple subject-sensitive hash sequences with SHA-1.
- (2)
The previous block hash is the hash sequence of the previous block header, which is calculated by SHA-1 to ensure the security of the blockchain itself.
- (3)
Other information in the block header includes additional information such as timestamps and the version number.
In the block body, the hash sequence of each HRRS image is calculated by subject-sensitive hashing instead of a cryptographic hash. After the subject-sensitive hash sequence of the HRRS image is compressed by SHA-1 (other cryptographic hash functions can also be used), the final hash value obtained is used as the root hash of the block header.
3.2. MultiRes-RCF-Based Subject-Sensitive Hashing for HRRS Images
As discussed in
Section 2.1, the subject-sensitive hashing algorithm is characterized by a relatively high tamper sensitivity. We propose a subject-sensitive hashing algorithm specifically for blockchains.
The key to the subject-sensitive hashing algorithm is the deep neural network model used by the algorithm [
9,
23]; the extraction method of the subject-sensitive features based on the deep neural network not only reduces the complexity of the feature design, but can also mine the hidden essential information of the HRRS images, laying the foundation for the integrity authentication of the HRRS images. According to the algorithm requirements, the existing subject-sensitive hashing algorithms of the HRRS images use different deep neural networks. Since various deep neural networks often determine different performances of algorithms, the existing subject-sensitive hashing algorithms of HRRS images use different deep neural networks according to the algorithm requirements. Our algorithm faces the application environment of the HRRS image blockchain and has to have better tamper sensitivity. Therefore, we propose a deep neural network named MultiRes-RCF that can extract multi-scale HRRS image features to meet the algorithm’s sensitivity to tampering.
3.2.1. Network Architecture of MultiRes-RCF
Scale is an important feature of HRRS images. It generally refers to the relative size of the spatial range and the relative length of time expressed by the data. In the analysis and use of HRRS images, there are obvious scale differences in identifying different ground objects [
24,
25]. As the same type of features may have different descriptions at different scales, feature extraction at a single scale cannot satisfy all analyses and applications, while multi-scale analysis methods can form a feature set with a hierarchical structure and can obtain more accurate and objective information. The subject-sensitive hash algorithm based on a multi-scale strategy can not only enhance the tamper sensitivity of the algorithm, but also expand the application scope of the authentication algorithm.
However, it is difficult to predict at which scale the content of HRRS images can be better detected in most cases. We believe that blockchain-oriented subject-sensitive hashing should be able to detect and identify objects of different scales. On the basis of richer convolutional features (RCF) [
26], we propose a network named MultiRes-RCF (richer convolutional features). MultiRes-RCF is based on the MultiRes mechanism [
27] to improve the performance of the RCF network to extract multi-scale features of HRRS images.
A neat contribution of the RCF architecture is to fully utilize the CNN features from all convolutional layers, making good use of the rich feature hierarchy. The network structure of RCF is built based on the VGG16, and all the fully connected layers and the fifth pooling layer of VGG16 are removed. RCF divide the convolution into five stages, and the pooling layers downsample the two adjacent stages. This enables RCF to automatically combine complementary information from all layers of the CNN to obtain accurate representations of the objects. However, the 3 × 3 convolutional layers used by RCF do not have many advantages in extracting multi-scale features. Moreover, as the width and depth of deep neural networks increase, they face the problem of network degradation caused by vanishing gradients or exploding gradients. In MultiResU-Net [
27], the sequence of two convolutional layers of the original U-Net [
28] is replaced by MultiRes blocks to solve the problem of different scales of images.
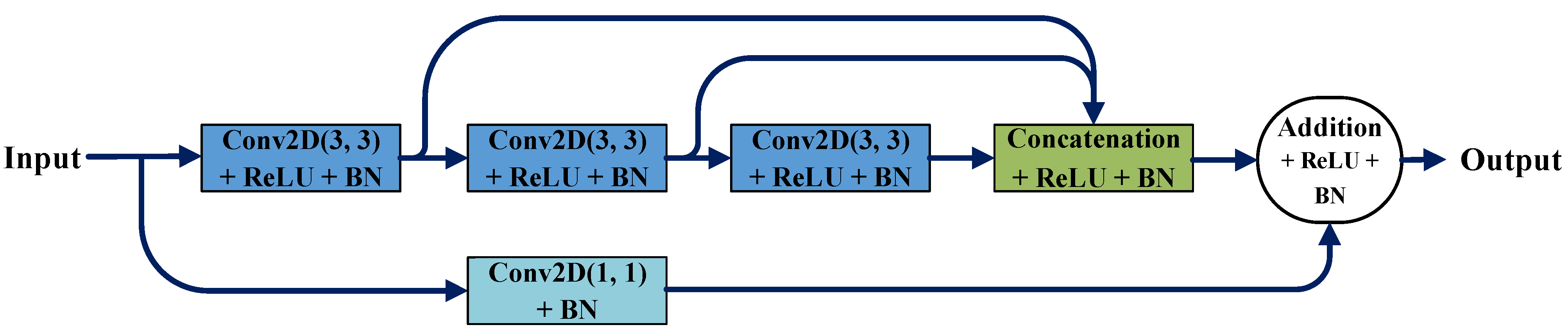
As shown in
Figure 2, a series of 3 × 3 convolution kernels are used in the MultiRes block to simulate the receptive fields of 5 × 5 convolution kernels and 7 × 7 convolution kernels. At the same time, the input of these convolution kernels is directly superimposed with the output of these convolution kernels through the residual path after 1 × 1 convolution. This can not only extract image features of different scales but can also reduce the amount of network computation. After all, it is very computationally expensive to directly use 5 × 5 convolution kernels and 7 × 7 convolution kernels to extract multi-scale features.
Our proposed MultiRes-RCF is based on MultiRes blocks to improve the RCF and enhance its ability to extract multi-scale features without significantly increasing the scale and computational complexity of the model.
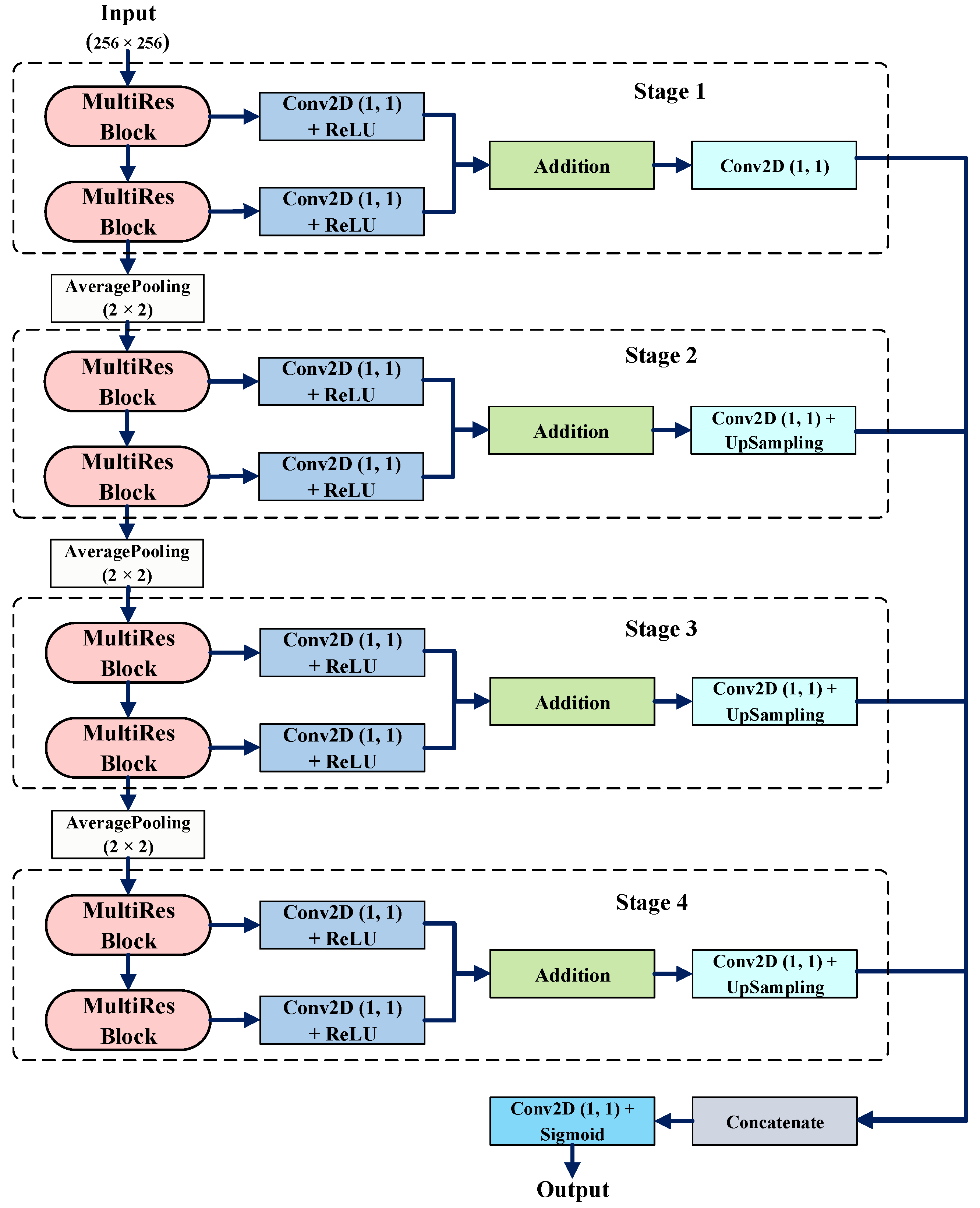
As shown in
Figure 3, the network input size of MultiRes-RCF is 256 × 256 pixels. MultiRes-RCF consists of 4 stages—1 stage less than the original RCF. This is because each stage of RCF contains 2 or 3 3 × 3 convolution kernels, while each stage of MultiRes-RCF contains 2 MultiRes blocks, implementing 3 × 3, 5 × 5, and 7 × 7 convolution operations to merge in parallel. Except for the output layer, the activation function of all the convolutional layers in this network is the ReLU (Rectified Linear Unit), and each convolutional layer is batch normalized.
The improved blockchain based on subject-sensitive hashing needs to train the deep neural network model used for feature extraction, which is a significant difference between our method and mainstream blockchains. The training process and training dataset of MultiRes-RCF will be discussed in
Section 4.1.
3.2.2. The Flow of the Subject-Sensitive Hashing Algorithm Based on MultiRes-RCF
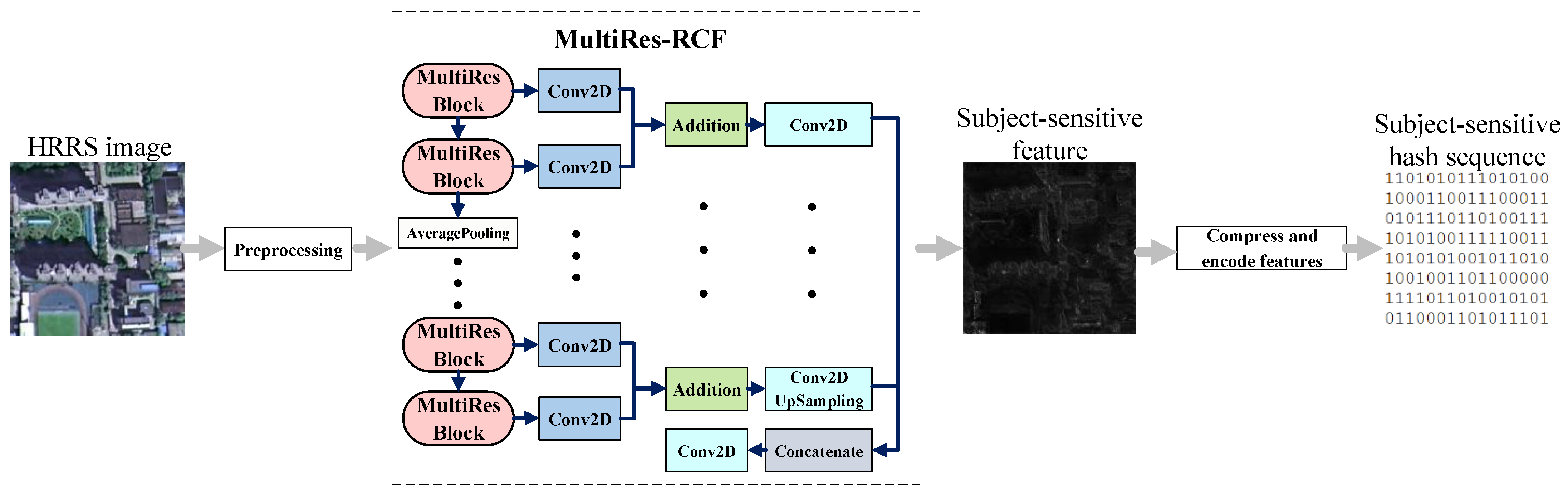
The flow of our subject-sensitive hashing algorithm is shown in
Figure 4. Before the feature extraction based on MultiRes-RCF, the HRRS image needs to be preprocessed to make it meet the input conditions of MultiRes-RCF; the output of MultiRes-RCF is then compressed and encoded to obtain a subject-sensitive hash sequence.
In the process of feature compression, we adopted the principal component analysis (PCA)-based compression method and took the principal components of the feature matrix as the compressed feature, which is similar to the existing subject-sensitive hashing [
9,
23]. The encoding process of the features takes the binary high-order part of the principal component value and fills the insufficient parts with zeros. The encoded hash sequence is in binary form and can also be represented as hexadecimal, which is easier to store.
To ensure the security of the hash sequence itself, the hash sequence can also be encrypted, which is a commonly used security enhancement method for subject-sensitive hashing algorithms. However, in our subject-sensitive hashing algorithm, the process of encrypting the hash sequence is not adopted, because the blockchain mechanism can already guarantee its security and the additional encryption process increases the burden of key management. This is also a feature that distinguishes our algorithm from other subject-sensitive hashings.
3.3. The Authentication Process of HRRS Images Based on this Method
The authentication process of our improved blockchain differs significantly from mainstream blockchains: the authentication process based on our method does not require that the hash sequence of the HRRS image to be authenticated is the same as the on-chain subject-sensitive hash sequence, as only the difference between the two is required to be lower than the set threshold T.
The hamming distance can measure the number of changed characters between two string sequences. However, the length of the subject-sensitive hash sequences may vary with the change in the algorithm parameters. We used the “normalized Hamming distance” to measure the difference between two subject-sensitive hash sequences as shown below, where
h1 and
h2 are subject-sensitive hash sequences of length
L.
This threshold-based integrity authentication process is more flexible than the traditional blockchain that uses the cryptographic hash function to calculate the image hash value directly. It overcomes some deficiencies caused by the “immutability” of traditional blockchains: after the HRRS image on the chain undergoes operations such as format conversion and watermark embedding, as long as the change in the subject-sensitive hash sequences is lower than the pre-set threshold T, we consider that the content of the HRRS image has not changed, regardless of whether the HRRS image has changed at the binary level. The integrity authentication process can be adjusted by setting different thresholds T, unlike traditional blockchains in which users have no intervention in the authentication process.
4. Experiments and Discussion
In this section, we will verify the effectiveness of our proposed method through experiments but have no intention to develop a complete blockchain system. We implemented a simple blockchain simulator in Python 3.7.5 and compared our method with the following two methods:
- (1)
The blockchain authentication method based entirely on cryptography. This class of methods uses a cryptographic hash function in computing the hash sequence of the HRRS images, and other steps are the same as our method. In the experiments in this paper, we chose MD5 and SHA-1 as the comparison methods, respectively.
- (2)
The improved blockchain based on other existing subject-sensitive hashing algorithms. These methods are also improved blockchains based on subject-sensitive hashing algorithms but are based on other deep neural networks. In this experiment, we chose the RCF [
26] -based algorithm, MultiResU-Net [
27] -based algorithm, Attention U-Net [
29] -based algorithm, and AAU-Net [
23] -based algorithm as the comparison method.
To focus the experimental comparison on the core improvement of our method, the blockchains based on each comparison hash algorithm only used different hash algorithms in the process of calculating the hash sequence of the HRRS image; the other steps were entirely the same, and the programming language was Python 3.7.5.
4.1. Performance Evaluation Metrics and Experimental Settings
4.1.1. Performance Evaluation Metrics
The specific environment of the blockchain determines that the requirements of the subject-sensitive hashing algorithm specifically for blockchains are different from other subject-sensitive hashing algorithms, as analyzed in
Section 2.1. In the experiments, we will evaluate our method and the comparison methods from the following two points:
- (1)
For operations that do not change the content of the HRRS images, such as image format conversion and copyright watermark embedding, keep them as robust as possible. The robustness evaluation index is defined as:
where
represents the total number of images for robustness testing and
represents the number of images whose hash sequence variation is lower than the preset threshold
T.
- (2)
Regarding the tamper sensitivity, even pixel-level content changes should be detected as much as possible. The tamper sensitivity index is defined as:
where
represents the number of tampered HRRS images detected under the threshold
T.
4.1.2. Training Process and Training Dataset of MultiRes-RCF
In the experiments, we implemented our proposed Multi-RCF network using Keras (Tensorflow as the backend) on a GPU workstation equipped with NVIDIA RTX 2080Ti GPU (11 G memory and 4352 cores) and an Intel i7-9700K CPU. The training process of each models adopted the same dataset as [
9,
23]. This dataset combines the existing WHU building dataset [
30] and the method of manually drawing robust edge images, including a total of 3166 pairs of training samples. The construction of this training dataset can be divided into two steps: First, modify the WHU building dataset to meet the needs of our model; then, draw the training samples manually with the false edges removed.
As edge pixels occupy a small proportion in the training samples, an α-balanced variant of focal loss [
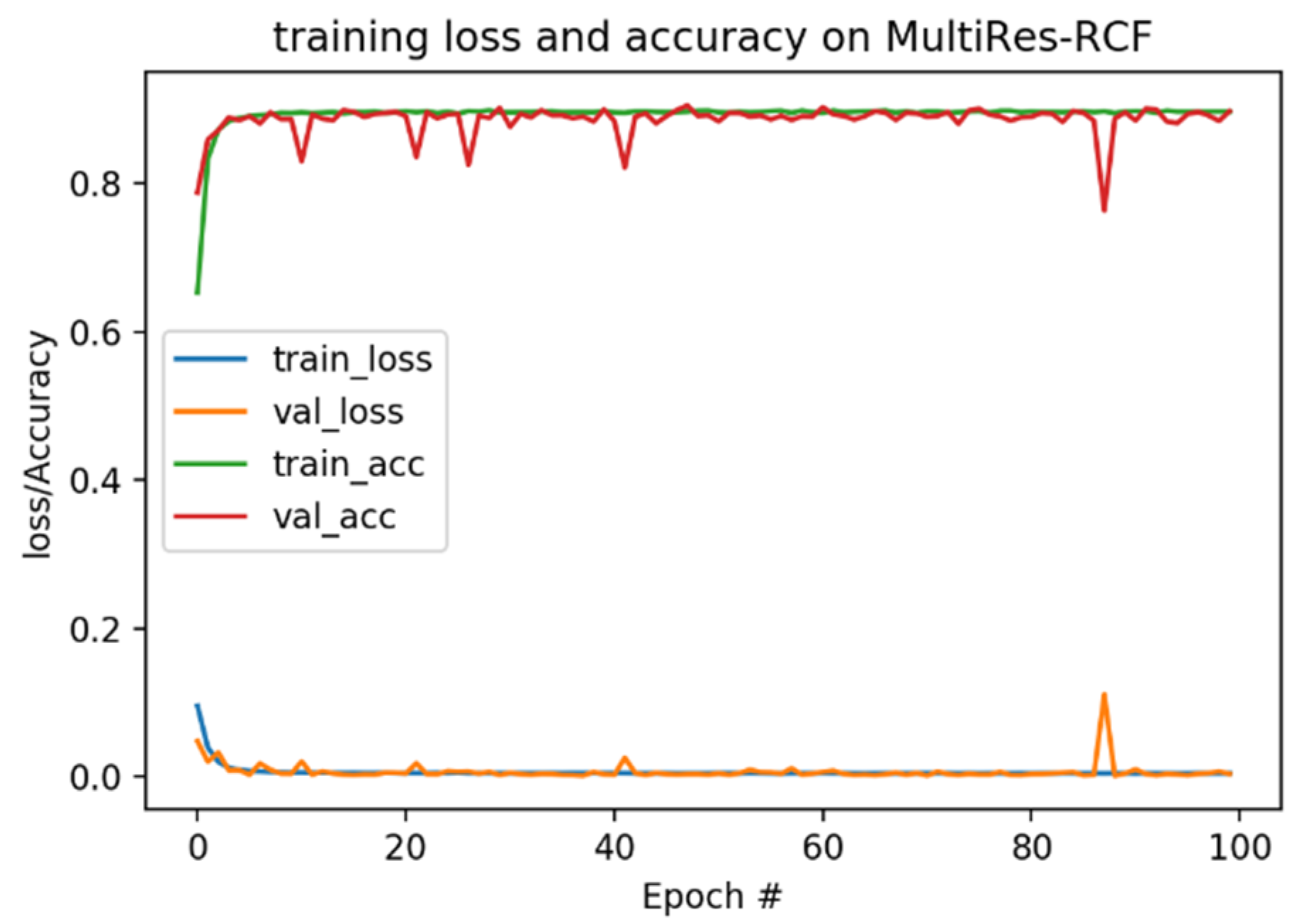
31] was taken as the activation function of MultiRes-RCF. Due to the limitation of the GPU memory size, the batch size was set to four, and the epochs was set to 100 during the training of the model. As shown in
Figure 5, the training loss curve distribution and the validation loss after each epoch are plotted.
We took the following three evaluation metrics to compare the complexity of each model: the number of parameters, the size of the storage space consumed, and the Floating Point Operations Per Second (FLOPs). The results are shown in
Table 1:
As can be seen from the table above, our MultiRes-RCF significantly reduced the number of parameters, storage size, and FLOPs compared to the existing models, and had certain potential advantages in further lightweighting.
4.2. Comparative Example of Integrity Authentication
To more intuitively illustrate the difference between our improved method and traditional blockchains, we chose the HRRS image shown in
Figure 6a as an example to present. In
Figure 6,
Figure 6a is the original HRRS image in TIFF format;
Figure 6b,c are the images after format conversion (TIFF format to PNG format) and watermark embedding (embedding 32-bit watermark information). The contents of the HRRS images of
Figure 6b,c have not changed but the two images have changed greatly at the binary level.
Figure 6d,e are the tampered HRRS images, respectively, and the contents and binary-level representations of these two tampered images have changed greatly.
The hash sequences generated by each comparison algorithm for each HRRS image in
Figure 6 are shown in
Table 2. The normalized Hamming distance of each subject-sensitive hash algorithm in
Table 2 after each operation on the HRRS images is shown in
Table 3. In
Table 3, there is no normalized Hamming distance of the cryptographic hash function; this is because the normalized Hamming distance between the hash sequences obtained by the cryptographic hash function has no practical significance while the subject-sensitive hashing algorithm judges whether the image has changed according to the normalized Hamming distance between the hash sequences.
According to the experimental results in
Table 2 and
Table 3, we can obtain the integrity authentication results of each comparison algorithm when the threshold
T is set to 0.02, as shown in
Table 4.
It can be seen from
Table 4 that the cryptographic Hash functions represented by MD5 and SHA1 take operations such as format conversion and digital watermarking that do not change the image content as tampering, which is not suitable for the blockchain of HRRS images. The four subject-sensitive hashing algorithms based on different deep neural networks can maintain good robustness to operations that do not change the image content and detect operations that change the image content simultaneously, which overcomes the inadequacy of the cryptographic hash function in the blockchain of HRRS images.
The above experimental results show that the improved blockchain based on subject-sensitive hashing is more suitable for the integrity authentication of HRRS images than the traditional blockchain. Next, we will prove that our proposed MultiRes-RCF is more suitable for the blockchain of HRRS images.
4.3. Performance Analysis
Since our improved blockchain differs from mainstream blockchains by using a subject-sensitive hashing algorithm when computing the hash sequence of HRRS images, we next focus on evaluating the performance of our MultiRes-RCF-based subject-sensitive hashing algorithm.
4.3.1. Robustness Test
Robustness is the most obvious difference between subject-sensitive hashing and cryptographic hashing. Unlike applications of deep neural networks such as image recognition and image segmentation, subject-sensitive hashing requires a large amount of data to be tested to make the results more convincing and reliable. We adopted the dataset
Datasets10,000 in [
23] to test the robustness of each algorithm. This dataset contains 10,000 HRRS images of 256 × 256 pixels stored in TIFF format, consisting of Gaofen-2 (GF-2) satellite, DOTA [
32], and some test images from [
9,
22].
First, we tested the robustness of each algorithm to format conversion. Here, we converted the images in TIFF format in
Datasets10,000 to PNG format without data compression and then compared the normalized Hamming distance between the hash sequences before and after the format conversion. Under different thresholds
T, the robustness test results of each algorithm are shown in
Table 5:
It can be seen from
Table 5 that due to the image of avalanche effect, the two cryptographic hash functions MD5 and SHA1 were not robust to format conversion, i.e., the HRRS images before and after format conversion were regarded as two different images by MD5 and SHA1, which is obviously not conducive to the integrity authentication of HRRS images. All the subject-sensitive hash algorithms involved in the test had a better robustness-to-format conversion.
Next, we tested the robustness of each algorithm to digital watermark embedding. In watermark embedding, 24-bit watermark information is embedded in a single band of the image, and the other bands remain unchanged. The watermark information of each bit is embedded in the second most significant bit of the pixel. The robustness test results after watermark embedding are shown in
Table 6:
It can be seen from
Table 6 that each subject-sensitive hashing algorithm had better robustness to digital watermark embedding. For example, for the MultiRes-RCF-based method, if the threshold
T is set to 0.02, 99.9% of HRRS images can pass the integrity authentication after watermark embedding, i.e., the normalized Hamming distance of the hash sequence before and after the watermark embedding is lower than 0.02. If the threshold
T is set to a value of 0.03 or greater, all HRRS images can pass the integrity authentication after embedding the watermark.
4.3.2. Tamper Sensitivity Test
Better tamper sensitivity is an important feature of blockchain-oriented subject-sensitive hashing algorithms, especially for detecting subtle tampering in HRRS images.
First, we tested the tampering sensitivity of each algorithm based on
Datasets10,000: each HRRS image was tampered at random positions, and the size of the tampered area was 16 × 16 pixels, which can simulate subtle tampering of the HRRS image as much as possible. We used the ratio of tampering detected by each algorithm under different thresholds to represent the tampering sensitivity, and the results are shown in
Table 7.
It can be seen from
Table 7 that although the tamper sensitivity of each subject-sensitive hash algorithm could be compared with the cryptographic hash algorithms, the tamper sensitivity of the subject-sensitive hashing algorithm based on MultiRes-RCF was better than the other subject-sensitive hash algorithms.
Next, we tested the tamper sensitivity of each algorithm to pixel-level modifications. Additionally, based on the
Datasets10,000 dataset, we constructed a tampered dataset: we randomly selected 16-pixel positions of the HRRS image and set the pixels of the three bands in this position to 0. This kind of subtle tampering is not easy to be detected by the human eye, but it can change the feature information carried by HRRS images. The ratio of the tampered images detected is also used to describe the tamper sensitivity of the algorithm, and the results are shown in
Table 8:
It can be seen from
Table 8 that the tamper sensitivity of the subject-sensitive hashing algorithm based on the MultiRes-RCF we proposed is still the best, and it can detect these pixel-level tampering well. Of course, there is still a gap compared with the cryptographic hash algorithms.
Subject-sensitive hashing is a special case of perceptual hashing, distinguished by its sensitivity to a particular subject. We adopted the dataset
Datasets400 in [
23] to test the tamper sensitivity of each algorithm to subject-unrelated tampering. This dataset contains 400 instances of tampering. Since
Datasets400 takes buildings as the subject, the tampering in this dataset does not affect the building information but tampers with trees, grasses, and lakes. The tamper sensitivity test results on
Datasets400 are shown in
Table 9:
It can be seen from
Table 9 that the tampering detection ability of the MultiRes-RCF-based method to the unrelated subject is roughly equivalent to the AAU-Net-based method and the Attention U-Net-based method, and even better when the threshold
T is small.
4.4. Discussion
Blockchain-oriented subject-sensitive hashing should emphasize tamper sensitivity, especially to maintain tamper sensitivity for subtle tampering at the pixel level, which is different from existing subject-sensitive hashing algorithms. At the same time, it should maintain robustness to operations that do not affect users at all, which is different from traditional blockchains.
We propose a subject-sensitive hashing algorithm based on MultiRes-RCF, which borrows the MultiRes mechanism of MultiResU-Net to improve the RCF network. Through the experiments in this paper, we can draw the following conclusions:
From
Table 6 to
Table 8, the tamper sensitivity of the subject-sensitive hash algorithm based on MultiRes-RCF is better than that of other subject-sensitive hashing algorithms. Of course, the tamper sensitivity of subject-sensitive hashing algorithms is not as good as cryptographic hashing. After all, subject-sensitive hashing algorithms do not perform binary-level integrity authentication, and it will not be considered that the image has been tampered just because one bit of the image has changed.
- (2)
Robustness.
The MultiRes-RCF-based subject-sensitive hashing algorithm can maintain a good robustness to operations such as format conversion and digital watermark embedding that do not affect the user’s use. It has no advantages over the existing subject-sensitive hashing algorithms but still overcomes the lack of robustness of the cryptographic hashing algorithms. Robustness is also an advantage of our improved blockchain over the existing blockchains entirely based on cryptography.
As subject-sensitive hashing needs to measure the degree of change in the image content, instead of only detecting whether the image has changed, the hash sequence length of subject-sensitive hashing is not as immutable as the cryptographic hash algorithm function. If the feature compression and encoding process of the algorithm is modified, a longer hash sequence can be obtained.
Overall, the overall performance of our proposed MultiRes-RCF-based subject-sensitive hashing algorithm is more suitable for HRRS image blockchains than for existing algorithms.
5. Conclusions
In this study, we propose a subject-sensitive hashing algorithm for HRRS image blockchains, which overcomes the deficiency that mainstream blockchain technologies can only perform binary-level authentication for HRRS images. The key to this subject-sensitive hashing algorithm lies in the MultiRes-RCF network, which is constructed by improving the RCF network by borrowing the MultiRes mechanism of MultiResU-Net. Compared with the existing algorithms, our MultiRes-RCF-based subject-sensitive hashing algorithm has stronger tamper sensitivity. It maintains good robustness to operations that do not change the HRRS image content.
The next research focus of this research is to study the subject-sensitive hash algorithm from the perspective of a lightweight model and low power consumption.
Author Contributions
All authors made a valuable contribution to this paper. K.D. and S.C. conceived, researched, and wrote the paper; Y.L. contributed research framing, ideas, and context; J.Y. and J.Z. participated in collecting and collating the experimental data. All authors have read and agreed to the published version of the manuscript.
Funding
This study was patricianly supported by grants from (a) China’s National Natural Science Foundation (Grant Nos. 41801303, 61902163, and 42101430) and (b) Funds for the Nanjing City Sci-Tech Innovation Team of Smart Transportation and Vehicle-Road Collaboration.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
The authors thank the anonymous referees for their constructive comments, which improved the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zakeri, F.; Mariethoz, G. A review of geostatistical simulation models applied to satellite remote sensing: Methods and appli-cations. Remote Sens. Environ. 2021, 259, 112381. [Google Scholar] [CrossRef]
- Chen, T.; Lu, Z.; Yang, Y.; Du, B.; Plaza, A. A Siamese Network Based U-Net for Change Detection in High Resolution Remote Sensing Images. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2022, 15, 2357–2369. [Google Scholar] [CrossRef]
- Feng, L.; Chen, S.S.; Zhang, C.; Zhang, Y.Z.; He, Y. A comprehensive review on recent applications of unmanned aerial vehicle remote sensing with various sensors for high-throughput plant phenotyping. Comput. Electron. 2021, 182, 106033. [Google Scholar] [CrossRef]
- Li, R.P. Fingerprint-related chaotic image encryption scheme based on blockchain framework. Multimed. Tools Appl. 2021, 80, 30583–30603. [Google Scholar] [CrossRef]
- Kumar, R.; Wang, W.Y.; Kumar, J.; Yang, T.; Khan, A.; Ali, W.; Ali, I. An Integration of blockchain and AI for secure data sharing and detection of CT images for the hospitals. Comput. Med. Imaging Graph. 2021, 87, 101812. [Google Scholar] [CrossRef]
- Alizadeh, M.; Andersson, K.; Schelén, O. DHT- and blockchain-based smart identification for video conferencing. Blockchain Res. Appl. 2022, 3, 100066. [Google Scholar] [CrossRef]
- Zhang, L.; Gao, Y.H.; Chen, J.Y.; Wang, X.H.; Huang, Z.Y.; Wei, D. Research on remote sensing data sharing model based on blockchain technology. In Proceedings of the 2019 2nd International Conference on Blockchain Technology and Applications (ICBTA 2019), Xi’an, China, 9–11 December 2019. [Google Scholar]
- Pincheira, M.; Donini, E.; Giaffreda, R.; Vecchio, M. A Blockchain-Based Approach to Enable Remote Sensing Trusted Data. In Proceedings of the 2020 IEEE Latin American GRSS & ISPRS Remote Sensing Conference (LAGIRS), Santiago, Chile, 22–26 March 2020. [Google Scholar]
- Ding, K.; Liu, Y.; Xu, Q.; Lu, F. A Subject-Sensitive Perceptual Hash Based on MUM-Net for the Integrity Authentication of High Resolution Remote Sensing Images. ISPRS Int. J. Geo-Inf. 2020, 9, 485. [Google Scholar] [CrossRef]
- Niu, X.M.; Jiao, Y.H. An Overview of Perceptual Hashing. Acta Electron. Sin. 2008, 36, 1405–1411. [Google Scholar]
- Yang, H.; Yin, J.; Jiang, M. Perceptual Image Hashing Using Latent Low-Rank Representation and Uniform LBP. Appl. Sci. 2018, 8, 317. [Google Scholar] [CrossRef] [Green Version]
- Du, L.; Ho, A.T.S.; Cong, R. Perceptual hashing for image authentication: A survey. Signal Process. Image Commun. 2020, 81, 115713. [Google Scholar] [CrossRef]
- Nakamoto, S. A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 April 2021).
- Zhai, P.; He, J.; Zhu, N. Blockchain-Based Internet of Things Access Control Technology in Intelligent Manufacturing. Appl. Sci. 2022, 12, 3692. [Google Scholar] [CrossRef]
- Meidute-Kavaliauskiene, I.; Yazdi, A.K.; Mehdiabadi, A. Integration of Blockchain Technology and Prioritization of Deploy-ment Barriers in the Blood Supply Chain. Logistics 2022, 6, 21. [Google Scholar] [CrossRef]
- Li, Z.-P.; Ceong, H.-T.; Lee, S.-J. The Effect of Blockchain Operation Capabilities on Competitive Performance in Supply Chain Management. Sustainability 2021, 13, 12078. [Google Scholar] [CrossRef]
- Venkatraman, S.; Parvin, S. Developing an IoT Identity Management System Using Blockchain. Systems 2022, 10, 39. [Google Scholar] [CrossRef]
- Butt, G.Q.; Sayed, T.A.; Riaz, R.; Rizvi, S.S.; Paul, A. Secure Healthcare Record Sharing Mechanism with Blockchain. Appl. Sci. 2022, 12, 2307. [Google Scholar] [CrossRef]
- Chivu, R.-G.; Popa, I.-C.; Orzan, M.-C.; Marinescu, C.; Florescu, M.S.; Orzan, A.-O. The Role of Blockchain Technologies in the Sustainable Development of Students’ Learning Process. Sustainability 2022, 14, 1406. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhou, C.; Guo, X.; Song, Y.; Chen, C. A Novel Decentralized E-Commerce Transaction System Based on Blockchain. Appl. Sci. 2022, 12, 5770. [Google Scholar] [CrossRef]
- Yunianto, E.; Prayudi, Y.; Sugiantoro, B. B-DEC: Digital evidence cabinet based on blockchain for evidence management. Int. J. Comput. Appl. 2019, 181, 22–29. [Google Scholar] [CrossRef]
- Ding, K.M.; Su, S.B.; Xu, N.; Jiang, T.T. Semi-U-Net: A Lightweight Deep Neural Network for Subject-Sensitive Hashing of HRRS Images. IEEE Access 2021, 9, 60280–60295. [Google Scholar] [CrossRef]
- Ding, K.M.; Chen, S.B.; Wang, Y.; Liu, Y.M.; Zeng, Y.; Tian, J. AAU-Net: Attention-Based Asymmetric U-Net for Sub-ject-Sensitive Hashing of Remote Sensing Images. Remote Sens. 2021, 13, 5109. [Google Scholar] [CrossRef]
- Liu, J.; Yang, D.; Hu, F. Multiscale Object Detection in Remote Sensing Images Combined with Multi-Receptive-Field Features and Relation-Connected Attention. Remote Sens. 2022, 14, 427. [Google Scholar] [CrossRef]
- Zheng, Y.; Yang, M.; Wang, M.; Qian, X.; Yang, R.; Zhang, X.; Dong, W. Semi-Supervised Adversarial Semantic Segmentation Network Using Transformer and Multiscale Convolution for High-Resolution Remote Sensing Imagery. Remote Sens. 2022, 14, 1786. [Google Scholar] [CrossRef]
- Liu, Y.; Cheng, M.M.; Hu, X.W.; Bian, J.W.; Zhang, L.; Bai, X.; Tang, J.H. Richer Convolutional Features for Edge Detection. IEEE Trans. Pattern Anal. Mach. Intell. 2019, 41, 1939–1946. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ibtehaz, N.; Rahman, M.S. MultiResUNet: Rethinking the U-Net architecture for multimodal biomedical image segmentation. Neural Netw. 2020, 121, 74–87. [Google Scholar] [CrossRef]
- Ronneberger, O.; Fischer, P.; Brox, T. U-net: Convolutional networks for biomedical image segmentation. In Proceedings of the 18th International Conference on Medical Image Computing and Computer-Assisted Intervention, Munich, Germany, 5–9 October 2015; pp. 234–241. [Google Scholar]
- Oktay, O.; Schlemper, J.; Folgoc, L.L.; Lee, M.; Heinrich, M.; Misawa, K.; Mori, K.; McDonagh, S.; Hammerla, N.Y.; Kainz, B.; et al. Attention u-net: Learning where to look for the pancreas. arXiv 2018, arXiv:1804.03999. [Google Scholar]
- Ji, S.P.; Wei, S.Y. Building extraction via convolutional neural networks from an open remote sensing building dataset. Acta Geod. Cartogr. Sin. 2019, 48, 448–459. [Google Scholar]
- Lin, T.; Goyal, P.; Girshick, R.; He, K.; Dollár, P. Focal Loss for Dense Object Detection. IEEE Trans. Pattern Anal. Mach. Intell. 2020, 42, 318–327. [Google Scholar] [CrossRef] [Green Version]
- Xia, G.S.; Bai, X.; Ding, J.; Zhu, Z.; Belongie, S.; Luo, J.; Zhang, L. DOTA: A large-scale dataset for object detection in aerial images. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Salt Lake City, UT, USA, 18–22 June 2018; pp. 3974–3983. [Google Scholar]
| Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).