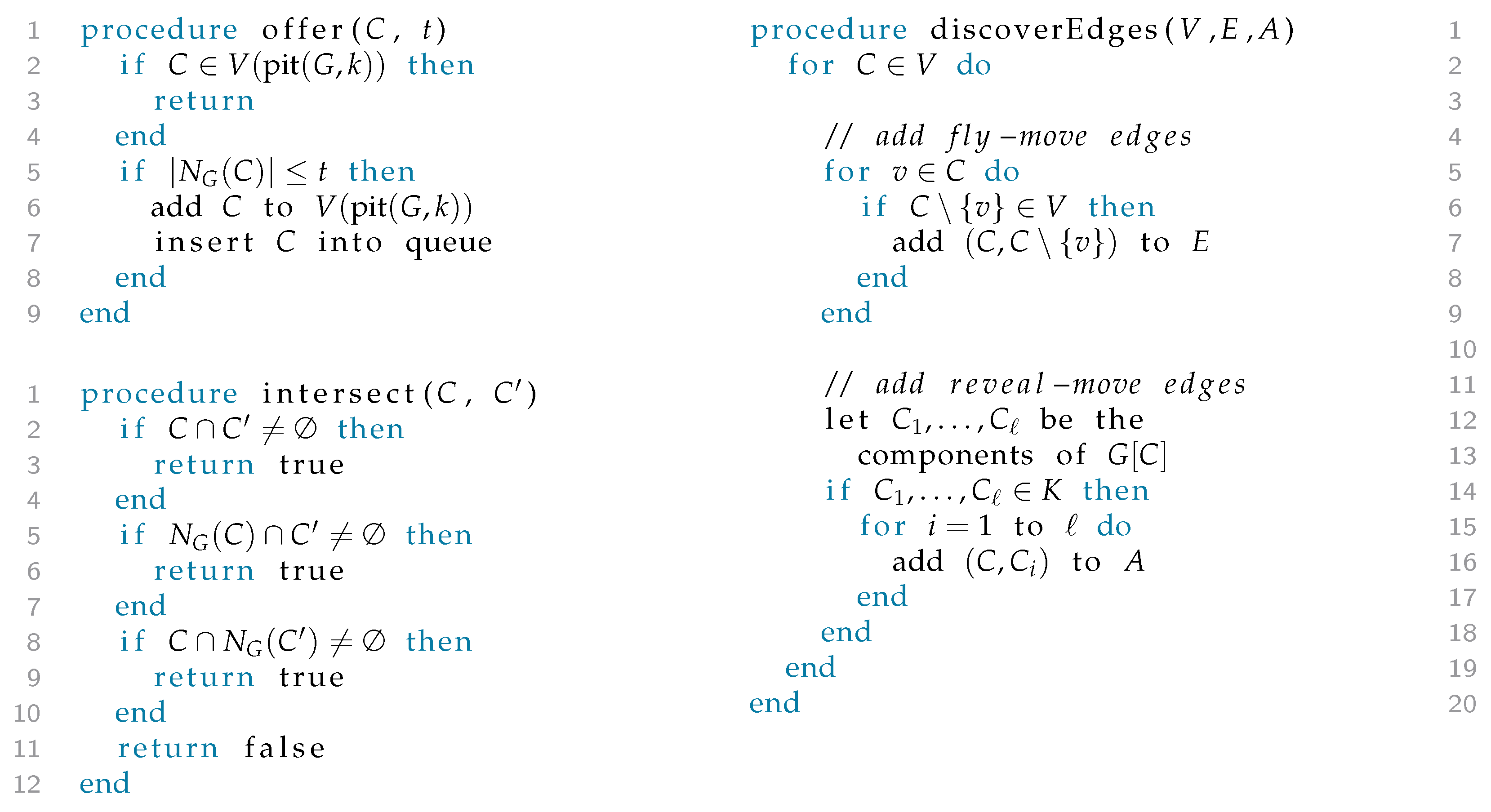1. Introduction
Graph decompositions are an important tool in modern algorithmic graph theory that provide a structured representation of a graph. A graph decomposition comes along with a
width measure that indicates how well a graph can be decomposed. Many problems that presumably
cannot be solved in polynomial time on general graphs
can be solved efficiently on graphs that admit a certain decomposition of small width [
1].
The most prominent example of a width measure is
treewidth, which (on an intuitive level) measures the similarity of a graph to a tree. This parameter is a cornerstone of parameterized algorithms [
2] and its success has led to its integration into many different fields. For instance, treewidth has been studied in the context of machine learning [
3,
4,
5], model-checking [
6,
7],
SAT-solving [
8,
9,
10],
QBF-solving [
11,
12],
CSP-solving [
13,
14], or
ILPs [
15,
16,
17,
18,
19]. Tools such as
Jdrasil [
20] that compute tree decompositions of minimum width or that try to find good heuristic solutions are actively used, for instance, in the analysis of large
SPARQL query logs [
21] or in propositional model counting [
22,
23,
24]. A large-scale experimental study that classifies real-world data sets according to their treewidth was recently performed by Maniu, Senellart, and Jog [
25].
However, treewidth is often too general and we require more restrictive width measures in order to obtain an algorithmic advantage [
26,
27]. Close relatives of treewidth are the width measures
pathwidth and
treedepth, which (again on an intuitive level) measure the similarity of the graph to a path or a star, respectively. These graph parameters can be naturally ordered in the sense that some of them are more restrictive than others, that is, a graph of bounded treedepth has bounded pathwidth as well, and a graph of bounded pathwidth has also bounded treewidth. Tools that compute treedepth decompositions of small width can be used to efficiently solve the mixed Chinese postman problem [
26] or to design algorithms for mixed integer linear programs [
28]. Pathwidth was recently used as structural parameter to prove that the well-known vertex cover problem can be solved in polynomial time with high probability on hyperbolic random graphs (which are frequently used to model real-world networks) [
29].
No matter which of these width measures we wish to utilize for a task at hand, we have to be able to compute it quickly. More crucially, most algorithms also need a witness in the form of a
decomposition. A lot of
theoretical research has been performed in this direction [
30,
31] and width measures such as treewidth can even be computed in linear fpt-time by Bodlaender’s famous algorithm [
32]. Unfortunately, it is known that this algorithm does
not work in practice due to huge constants [
33] (the same holds for similar algorithms for the other width measures). When it comes to implementations, small progress has been made with classical exact exponential time algorithms, which are only able to solve graphs with about 50–100 vertices. See, for instance, the
QuickBB algorithm for treewidth [
34], the algorithm by Coudert, Mazauric, and Nisse for pathwidth [
35], or a recent branch-and-bound algorithm for treedepth [
36]. More progress was made with heuristics, see, for instance, [
37,
38,
39] for treewidth, the algorithm by Kobayashi et al. for pathwidth [
40], and Section 24 in [
41] for treedepth. We may argue that, indeed, a heuristic is sufficient, as the attached solver will work correctly independently of the width of the provided decomposition—and the heuristic may produce a decomposition of “small enough” width. However, even a small error, something as “off by 5”, may put the parameter to a computationally intractable range, as the dependency on the width is usually at least exponential. For instance, it was observed that small changes (even by just one or two) in the width of a tree decomposition can have a huge impact on the inference time in probabilistic networks [
42]. A similar effect was observed in recent advances of implementing a lightweight model checker for a fragment of MSO [
7], where it turned out to be beneficial to invest additional time in order to obtain an optimal tree decomposition rather than relying on faster heuristics. It is therefore a natural and important task to build practical fast algorithms to determine parameters such as the treewidth, pathwidth, or treedepth of a graph exactly.
To tackle this issue, the fpt-community came up with a contest, the Parameterized Algorithms and Computational Experiments (PACE) challenge [
43,
44,
45], with the goal of finding new exact algorithms to determine the exact treewidth or treedepth of a graph. Besides many, one important result of the challenge was a new combinatorial algorithm due to Tamaki, which computes the treewidth of an input graph exactly and astonishingly fast on a wide range of instances. An implementation of this algorithm by Tamaki himself [
46] won the corresponding track in the PACE challenge in 2016 [
43] and an alternative implementation due to Larisch and Salfelder [
47] won in 2017 [
44]. In 2020, many participants adapted the original algorithm to treedepth [
45,
48,
49].
Tamaki’s original algorithm is based on a dynamic program by Arnborg, Corneil, and Proskurowski [
50] for computing tree decompositions. This algorithm has a game theoretic characterization that can be used to generalize the algorithm to other width measures such as treedepth. Tamaki has improved his algorithm for the second iteration of the PACE by applying his framework to the algorithm by Bouchitté and Todinca [
51,
52], see, for instance, [
53] for a recent evaluation of this version of the algorithm. While Bouchitté and Todinca’s algorithm has a game theoretic characterization as well [
54], it is still unclear how it can be generalized to other width measures.
We focus on Tamaki’s first algorithm and characterize it in a unifying way that allows us to compute not just the treewidth of a graph but, with the same algorithm, the pathwidth, treedepth,
q-branched treewidth, and dependency treewidth as well. Perhaps even more importantly, our description of the algorithm in a game theoretic framework is simple and intuitive and can be implemented quite directly. In fact, our treewidth and treedepth solvers
Jdrasil and
PID are based on this characterization [
20,
49]. The detailed contributions of this paper are the following:
Contribution I: A Simple Description of Tamaki’s First Algorithm.
We describe Tamaki’s algorithm as a well-known graph searching game. This provides a link to known theory and allows us to analyze the algorithm in depth.
Contribution II. Extending Tamaki’s Algorithm to Other Parameters
The game theoretic point of view allows us to extend the algorithm naturally to various other parameters—including pathwidth and treedepth.
Contribution III: A Novel Randomized Data Structure.
The bottleneck in positive-instance driven algorithms is the enumeration of already computed solutions. We present a lazily constructed randomized data structure that, in contrast to existing data structures for this task, provides a guarantee that certain useless solutions are not enumerated with high probability.
1.1. Related Work
The concepts of pathwidth and treewidth were rediscovered several times in the literature [
55,
56,
57]. Treedepth was discovered and analyzed by Nešetřil and de Mendez in their study of sparsity [
58]. The game theoretic characterization of treewidth goes back to Seymour and Thomas [
59]. Kirousis and Papadimitriou have studied a similar game for pathwidth [
60], and Giannopoulou, Hunter and Thilikos have studied game theoretic approaches for treedepth [
61]. The generalized version of this game, which we will use in this paper, was introduced by Fomin, Fraigniaud, and Nisse [
62].
The potential success of positive-instance driven algorithms was demonstrated by Tamaki, who implemented a positive-instance driven version of Arnborg, Corneil, and Proskurowski’s treewidth algorithm for the PACE 2016 [
46]. This algorithm outperformed all other submissions (including one by the authors) by far [
43]. The winning algorithm of the PACE 2017 also “is basically Hisao Tamakis implementation” [
44,
47]. Tamaki later adapted his algorithm to the algorithm by Bouchitté and Todinca in his pioneering work introducing positive-instance driven dynamic programming [
52]. Ongoing research constantly improves the performance of this version of the algorithm [
39,
53,
63].
Positive-instance driven dynamic programming also played a key role in many submissions for the PACE 2020, where the goal was to compute the treedepth of a graph rather than the treewidth [
45], for instance, in the winning submission by Trimble [
48]. However, it should be noted that in contrast to treewidth, the dominance of positive-instance driven algorithms compared to other strategies (such as enumerating minimal separators [
64,
65]) was less dramatic for the computation of treedepth [
45].
Besides the development of dedicated algorithms for these graph parameters, there is also ongoing research in implementing a unifying way of computing all these parameters using
sat or
maxsat solvers. See, for instance, [
20,
66,
67,
68,
69,
70,
71].
1.2. Organization of This Paper
We provide some preliminaries about graphs and their decompositions in
Section 2. We then invite the reader, in
Section 3, to a gentle introduction to positive-instance driven graph searching with the example of computing the treedepth of a graph—while not directly necessary for the remaining paper, this section should make it easier to follow the more general approach presented later on.
Section 4 lifts the game theoretic approach to a unifying algorithm that allows us to compute not just the treewidth or treedepth of a given graph but also its pathwidth and dependency treewidth. The somewhat technical proof of Theorem
Section 4.5 is only sketched within the main text and we dedicate
Appendix A to fill in the details.
After the main part of the paper, in
Section 5 we identify a bottleneck of the positive-instance driven graph searching approach that was observed experimentally in various solvers. We extend a known data structure used by such algorithms, called
block sieve, with a randomized component based on the well-known color coding technique. We illustrate the gained performance exemplarily in our treedepth solver
PID in
Section 6.
We conclude our findings and discuss further research directions in
Section 7.
1.3. Difference to the Conference Paper
This paper is an extended version of our paper
Positive-Instance Driven Dynamic Programming for Graph Searching presented at WADS 2019 [
72]. In the conference version, we already presented the unifying approach now discussed in
Section 4. Because of this, the structure and content of this section have barely changed. In the present work, we improve the presentation of the algorithm and extend the approach further to directed treewidth (
Section 4.6).
A new contribution, compared to [
72], is the gentle introduction to positive-instance driven graph searching in
Section 3. It is based on insights we gained during the development of our treedepth solver
PID [
49] and its aim is to help the reader in following the more general algorithm presented later.
A new technical contribution is the lazily constructed randomized data structure (dubbed
color coding sieve) presented in
Section 5. The most expensive part of a positive-instance driven algorithm (be it for treewidth, treedepth, or any other width measure) is the enumeration of already computed positive subproblems that are
compatible with each other [
20,
48,
49,
52,
63]. Previous solvers use a data structure called
block sieves to accelerate this process, which are basically set tries that store the positive subproblems and that can prune
some non-compatible elements during the enumeration process. However, set tries are cumbersome and do
not provide any guarantees on the number of non-compatible elements that actually get pruned. Our color coding sieves, in contrast, are (i) much more compact, as they are lazily constructed, (ii) use randomization to provide a guarantee that non-compatible elements are pruned with high probability, and (iii) allow a trade-off between the time spend in the data structure and the amount of elements that will be pruned. We extend this theoretical analysis by an implementation of the data structure in our treedepth solver
PID and an experimental evaluation (
Section 6).
3. A Gentle Introduction to Positive-Instance Driven Graph Searching
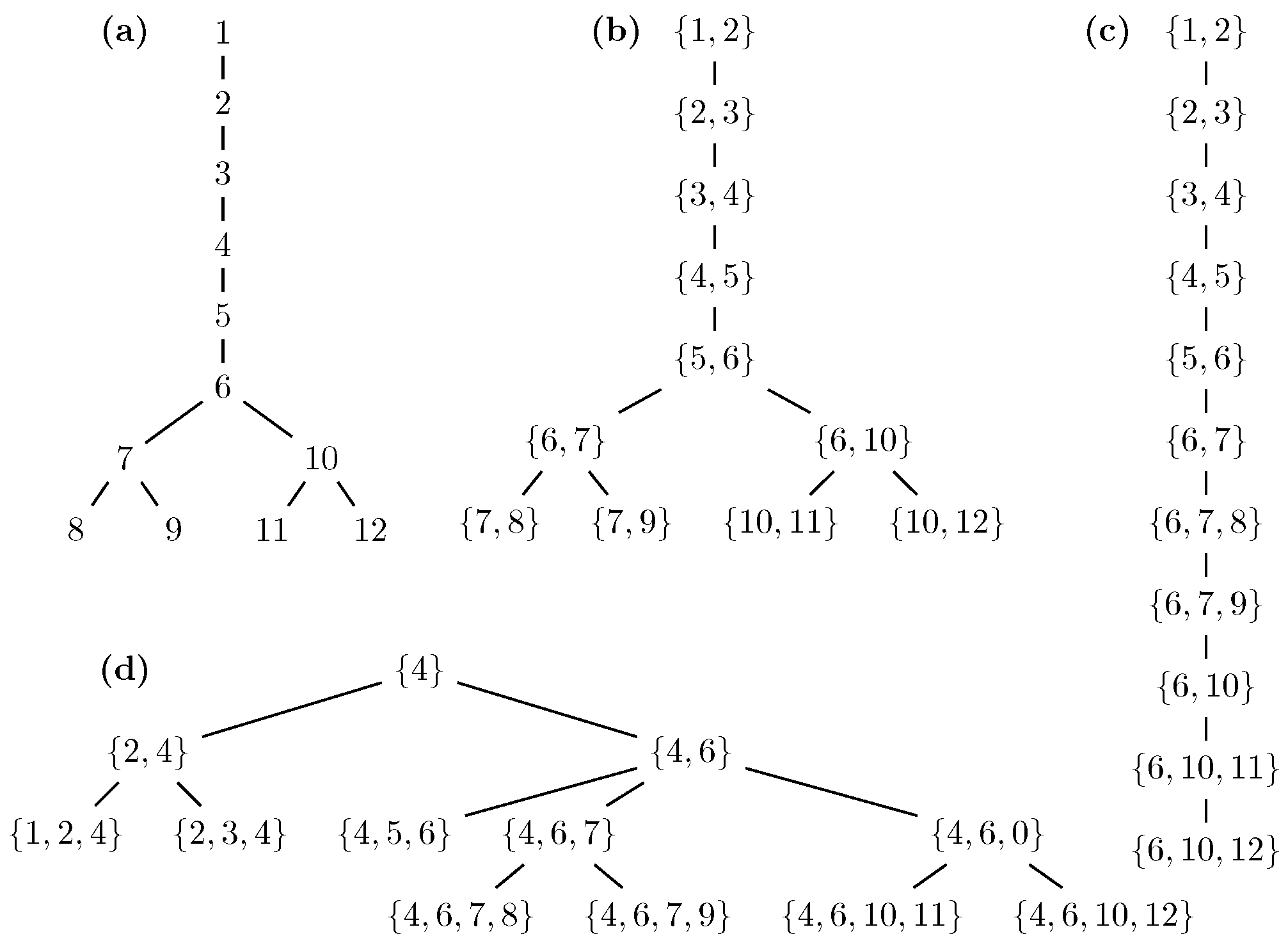
Before we describe a unifying algorithm that can compute all the graph decompositions shown in
Figure 1, we will illustrate the positive-instance driven graph searching technique in a simpler example. Our goal in this section is to describe a game theoretic positive-instance driven algorithm for the width measure
treedepth alone. For that end, let us use the following equivalent definition of this parameter: the treedepth of a graph
is the minimum height of a rooted forest
F such that
G is a subgraph of the closure of
F. This forest is called a
treedepth decomposition of
G. Since the treedepth of a graph is the maximum treedepth of its connected components, we can restrict ourselves to connected graphs. In this case, a treedepth decomposition of
G is an
elimination tree. 3.1. Graph Searching
Many graph decompositions have game theoretic characterizations in the form of
vertex pursuit-evasion games [
74]. Such games, which are also known as
graph searching or
cops and robber, are played by two players on an undirected graph
. In the game for treedepth, the first player places a team of
ksearchers iteratively on the vertices of
G, while the second player controls a single
fugitive that hides in a connected component. The game is played in rounds as follows [
61,
75]: Initially, the fugitive hides in the vertex set
(which we assume to be connected). The vertices in
C are said to be
contaminated. In each round, both players perform one action:
The searchers pick a vertex on which they want to place the next searcher. We say they clean the vertex v.
The fugitive responds by picking a component of . The contaminated area is reduced to and the game proceeds only on this subgraph.
The game ends when the contaminated area shrinks to the empty set or if the searchers have placed all
k members of their team and
C is still non-empty. In the first case, the graph was
cleaned and the fugitive was
caught; in the second case, the fugitive
escaped. The searchers win if they catch the fugitive, otherwise the fugitive wins. Note that in this version of the game, the searchers are not allowed to remove an already placed searcher from the graph. The game is therefore monotone and always ends after, at most,
k rounds. Further observe that the fugitive is
visible in the sense that the searchers know in which connected component she hides—in contrast, an invisible fugitive could hide in subgraphs that are not connected (which notably complicates the arguments). The game is illustrated in
Figure 2 on a small graph with eight vertices.
The configurations of this game are blocks, which are tuple with and being a connected subgraph with . Informally, C is the (connected) contaminated area, and is the number of remaining searchers. We require as the neighborhood of C has to be cleaned in order to have C as contaminated area. We denote the set of blocks of the game played on a graph G with k searchers by . Two blocks and intersect if , or . The start configuration of the game is and the winning configurations for the searchers are . We say the searchers have a winning strategy on a block if, starting with configuration , they can ensure to reach a winning configuration no matter how the fugitive acts. The set of blocks that guarantee such a strategy is the winning region, which we denote by —the elements in this region are said to be positive. The connection between the game and the width measure treedepth is established by the following fact:
Fact 1 ([61]). Let be a graph and . Then .
3.2. Simple Positive-Instance Driven Graph Searching
By Fact
Section 3.1, it is sufficient to compute the set
in order to test whether the treedepth of
G is at most
k. One way of doing so would be to first compute
, then build an auxiliary graph on top of this set, and finally compute
by solving reachability queries on this auxiliary graph. We can estimate the number of configurations with
, as there are
possible ways of placing
k searchers on an
n-vertex graph—at most
n connected components adjacent to a separator—and we have
. Therefore, the sketched algorithm achieves a run time of
, which is not feasible in practice for even moderate values of
k.
To make the game theoretic approach feasible, we present an
output-sensitive algorithm that computes just
— without “touching” the rest of
.
Figure 3 illustrates why we may hope that
is smaller than
. In the remainder of this section, we will develop some intuition about how to compute the set
. The formal details are postponed to the unifying version of the algorithm in the next section.
Surely, we cannot start at some block, say
, and just simulate the game in a top-down fashion—we could touch a lot of blocks in
without even noticing it (in
Figure 3, that would mean starting a graph traversal from
s, which could explore any leg of the spider). After all, we do not know whether
. We do know, however, that
is a winning configuration (vertex
t in
Figure 3). So, let us start with the set
and then try to grow it to
in a bottom-up fashion. We can first ask which configurations of the game lead to
, i. e., what are configurations in which the searchers immediately win in the next round? These are the configurations
with
, as in these the searchers can surround the fugitive and have a searcher left to place it on top of her (in
Figure 3, this corresponds to the predecessor of
t).
Now, assume that we have currently a set
that had already grown a little. What does a configuration
that is “close to”
look like (that is, we wish to traverse the
s-
t-path of
Figure 3 in reverse direction)? The set
C is connected by definition and, since the searchers have a winning strategy from
, there is a vertex
such that
has connected components
(
is possible) with
for all
. To find
, we first guess the vertex
v, scan the sets of pairwise non-intersecting blocks
, and generate the new blocks
. Note that we can prune a set
X if
, as this neighborhood has to be cleaned by the searchers before they clean one of the components
. This will be utilized by the randomized data structure that we develop later in
Section 5.
Figure 4 illustrates this step of the algorithm, which we call a
glue operation. We refer the reader who is interested in the details of implementing this algorithm for treedepth efficiently to the description of our solver
PID [
49]. In the next section, we present a formal and more general version of the sketched strategy—which does not just work for treedepth, but for treewidth, pathwidth and many other width measures, too.
3.3. Alternative Characterization
Let us briefly sketch an interpretation of the algorithm without the game theoretic point of view. One can think of it as a procedure that, given a connected graph , lists ever growing treedepth decompositions of subgraphs of G. In detail, a collection of trees of depth at most d for some is managed—starting with the trivial trees of depth 1 (i. e., single vertices) we have . Then, for ever larger d, the set is computed by picking a new root and a collection of previously computed trees , and by arranging the trees of to a new tree by connecting their roots to r. Of course, in order to obtain a valid treedepth decomposition, the elements of must be pairwise disjoint and non-adjacent. The selection of the set is what was the glue operation and what will be a universal step in the algorithm presented in the next section, and the value d corresponds to and will be the distance that we will compute. Let us stress out that, in this characterization, the trees in are, indeed, trees and thus connected. This is an invariant that the following algorithm cannot guarantee for all parameters but which improves the performance of the algorithm if met.
3.4. Execution Modes
It is worth noting that positive-instance driven algorithms only solve the problem for a fixed
k. Hence, to obtain an
optimal treedepth decomposition (or any other decomposition), one has to run the algorithm for various values of
k. The order in which these values are tested is called the
execution mode of the algorithm. Positive-instance driven algorithms differ from other strategies with respect to values that are “easy”. For instance, branch-and-bound algorithms usually solve the problem quickly if
k overestimates the optimal value. However, overestimating
k means
more positive subproblems, making these instances hard for positive-instance driven algorithms. On the other hand, underestimating the optimal value yields instances that are usually hard but that are solved quickly by positive-instance driven algorithms as there are only few positive instances. Positive-instance driven graph searching is, thus, especially suited to compute lower bounds [
63]. Therefore, the typical execution mode is to start with
and to increase this lower bound until either an optimal solution was found or a heuristically obtained upper bound is met [
48,
49].
4. A Unifying Take on Positive-Instance Driven Graph Searching
Our goal is to generalize the algorithm that we just sketched in
Section 3.2 to other graph measures such as treewidth and pathwidth. When we generalize from treedepth to other parameters, there are two main obstacles that we have to face. First, the sketched algorithm for treedepth “guessed” a root vertex in every iteration and glued already computed blocks to it. In more flexible graph decompositions such as tree decompositions, the root no longer is a single vertex but a
set of up to k vertices. Clearly, we cannot guess such a set and, hence, have to compute it implicitly. Second, the treedepth algorithm explicitly carried the number of remaining searchers
around (they were part of the blocks). In more flexible graph measures, we may remove and reuse already placed searchers and, thus, have to encode this information in a different way. We will handle this issue by splitting the computation into two phases, where the first phase mainly computes a configuration graph (intuitively, this graph contains blocks for various values of
) and where the second phase then computes distances in this configuration graph (hence, computes best possible
-values for the blocks). However, let us postpone the fiddling with distance queries to
Section 4.5 and focus solely on the more general search game in the first part of this section.
We study graph searching in a setting proposed by Fomin, Fraigniaud, and Nisse [
62]. The input is again an undirected graph
and a number
, and the question is whether a team of
k searchers can catch an
invisible fugitive on
G by the following set of rules: At the beginning, the fugitive picks a connected component
C of
G in which she hides—since the fugitive is invisible, in contrast to
Section 3.2, the game is continued on
G and
not on
and we say that the set
V is
contaminated. In each round, the player now follows a similar procedure as in the previous game, but the searchers have a larger set of possible moves:
We follow the same terminology as before, i. e, we say a contaminated vertex becomes
clean if a searcher is placed on it. In contrast to the previous game, a vertex
v may now become
recontaminated if a searcher is removed from it and there is a contaminated vertex adjacent to
v. The searchers win the game if they manage to clean all vertices, i. e., if they catch the fugitive; the fugitive wins if, at any point, a recontamination occurs or if she can escape infinitely long. Note that this implies that the searchers have to catch the fugitive in a
monotone way. A priori, one could assume that the later condition gives the fugitive an advantage (recontamination could be necessary for the cleaning strategy); however, a crucial result in graph searching is that “recontamination does not help” in all variants of the game that we consider [
59,
61,
76,
77,
78].
4.1. Entering the Arena and the Colosseum
Our primary goal is to determine whether the searchers have a winning strategy. A folklore algorithm for this task is to construct an alternating graph called
the arena:
that contains for each position of the searchers (
with
) and each position of the fugitive (
) two copies of the vertex
, one in
and one in
(see, for instance, Section 7.4 in [
2]). Vertices in
correspond to a configuration in which the searchers perform the next move (they are existential) and vertices in
correspond to fugitive moves (they are universal). The edges
are constructed according to all possible moves. The question is now whether there is an alternating path from a start configuration to some configuration in which the fugitive is caught. Since alternating paths can be computed in linear time ([
79], Section 3.4), we immediately obtain an
algorithm.
Modeling a configuration of the game as tuple comes, however, with a major drawback: The size of the arena does directly depend on n and k and does not depend on some further structure of the input. For instance, the arena of a path of length n and any other graph on n vertices will have the same size for any fixed value k. As the major goal of parameterized complexity is to gain insight into structural parameters beyond the input size n, such a fixed-size approach is not what we are looking for.
A bit counter intuitive, we will tackle this problem by, firstly, defining an alternating graph that is larger than the arena: the colosseum. As it befits for any good colosseum, it is not only larger but, in particular, “prettier” than the arena (which here means that it adapts to the input structure of the graph).
Once we can capture the structure in the colosseum, we will introduce yet another alternating graph that, finally, is actually small. This graph, which will be a subset of the colosseum, is called the pit—where only true champions can survive!
4.2. Simplifying the Game
Before we define all the locations of potential gladiator fights in graph theoretic terms, let us start with some simplifications of the game. We restrict the fugitive as follows: Since she is invisible, there is no need for her to take regular actions. Instead, the only moment when she is actually active is when the searchers perform a reveal. If C is the set of contaminated vertices, consisting of the induced components , a reveal will uncover the component in which the fugitive hides and, as a result, reduce C to for some . The only task of the fugitive is to answer a reveal with such a number i. The complete process of the searcher performing a reveal, the fugitive answering it, and finally of reducing C to is called a reveal-move.
We also restrict the searchers by the concept of implicit searcher removal. Let be the set of vertices currently occupied by the searchers, and let be the set of contaminated vertices. We call a vertex covered if every path between v and C contains a vertex with .
Lemma 1. A covered searcher can be removed safely.
Proof. As we have , the removal of v will not increase the contaminated area. Furthermore, v cannot be recontaminated at a later point, unless a neighbor of v becomes recontaminated as well (in which case the game would already be over). □
Lemma 2. Only covered searchers can be removed safely.
Proof. Since for any other vertex we have , the removal of w would recontaminate w and, hence, would result in a defeat of the searchers. □
Both lemmas together imply that the searchers never have to decide to remove a searcher but rather can do it implicitly. We restrict the possible moves of the searchers to a combined move of placing a searcher and immediately removing searchers from all covered vertices. This is called a fly-move. Observe that the sequence of original moves mimicked by a fly-move does not contain a reveal and, thus, may be performed independently of any action of the fugitive.
4.3. Building the Colosseum
We are now ready to define the colosseum. As for the arena, we could define it as an alternating graph. However, as only the searchers perform actions in the simplified game, we find it more natural to express this game as an edge-alternating graph—a generalization of alternating graphs. An edge-alternating graph is a triple consisting of a vertex set V, an existential edge relation , and a universal edge relation . The neighborhoods of a vertex v are the existential neighborhood , the universal neighborhood , and the complete neighborhood . An edge-alternating s-t-path is a set such that (i) and (ii) for all with we have either or or both. We write if such a path exists and define for as the set of vertices on edge-alternating paths leading to Q. We say that an edge-alternating s-t-path P is q-branched if (i) H is acyclic and (ii) every (classical) directed path from s to t in H with uses at most q universal edges.
For and , the is the edge-alternating graph H with and the following edge sets: for all pairs there is an existential edge if, and only if, for some and ; furthermore, for all with at least two components we have universal edges .
The nodes of the colosseum are called
blocks and, thinking of
Section 3.2, we have
(but note that the definition of “block” has slightly changed). The
start configuration of the game is the block
, i. e., all vertices are contaminated. We define
to be the set of
winning configurations, as at least one searcher is available to catch the fugitive. Therefore, the searchers have a winning strategy if, and only if,
and we will therefore refer to
as the
winning region (we did so similarly in
Section 3.2, but we did not have the notation of edge-alternating graphs then). Observe that the colosseum is acyclic (that is, the digraph
is acyclic) as we have for every edge
that
, and observe that
Q is a subset of the sinks of this graph. Hence, we can test if
in time
. Finally, note that the size of
may be of order
rather than
, giving us a slightly worse overall runtime. This larger structure is required to encode that the fugitive is invisible.
4.4. Fighting in the Pit
The sketched algorithms have running time proportional to the size of the arena and the colosseum. Both of these auxiliary graphs might be large, as the arena has fixed size of order while the colosseum may even have size . Additionally, both graphs can contain unnecessary configurations, that is, configurations not part of the winning region. In the light of dynamic programming, this is the same as listing all possible configurations, and in the light of positive-instance driven dynamic programming, we would like to list only the positive instances—which is exactly the winning region .
The pit inside the colosseum is now formally defined as the subgraph of induced by , that is, as the induced subgraph on the winning region. The key insight is that may be smaller than or even on various graph classes. Our primary goal for this section will therefore be the development of an algorithm that computes the pit in time depending only on the size of the pit (rather the size of the arena or the colosseum).
The algorithm traverses the colosseum “backwards” starting from the winning configurations
Q and uncovering
layer by layer. In order to achieve this, we need to compute the predecessors of a block
C. This is easy if
C was reached by a fly-move as we can simply enumerate the
n possible predecessors. Reversing a reveal-move, that is, finding the universal predecessors, is significantly more involved. A simple approach is to test for every subset of already explored configurations if we can “glue” them together—as we did in the sketched algorithm in
Section 3.2. However, this results in an even worse runtime of
. To avoid this exponential blow-up, we require the following structural property of the colosseum.
Definition 1 (Universal Consistent)
. We say that an edge-alternating graph is universal consistent with respect to a set if for all with and we have (1) and (2) for every with there is a vertex with and .
Intuitively, Definition 1 implies that for every vertex with high universal-degree, there is a set of vertices that can be arranged in a tree-like fashion to realize the same adjacency relation. This allows us to glue only two configurations at a time and, thus, removes the exponential dependency. The definition is illustrated in Example 1.
Example 1. Consider the following three edge-alternating graphs, where black edges are existential and the blue edges are universal. The set Q contains a single vertex that is highlighted. From left to right: the first graph is universal consistent, the second and third one are not. The second graph conflicts the condition that implies , as the vertex on the very left is contained in by the top path, while its universal neighbor on the bottom path is not contained in . The third graph conflicts the condition that implies that for every with there is a vertex with and as witnessed by the vertex with three outgoing universal edges.
Lemma 3. For every graph G and number k, the edge-alternating graph is universal consistent.
Proof. For the first property, observe that “reveals do not harm”: Searchers that can catch the fugitive without knowing where she hides, certainly can do so if they know.
For the second property, consider any configuration that has universal edges to . By definition, we have and for all . Therefore, we have for every and that and and, thus, . □
The algorithm for computing the pit, see
Figure 5 and
Figure 6, runs in three phases: it first computes the set
Q of winning configurations; then the winning region
(the vertices of
); and finally, it computes the edges of
.
Theorem 1. The algorithm discover(G,k) finishes in at most steps and correctly outputs .
Proof. The algorithm computes Q in phase I, the winning region in phase II, and the edges of in phase III. First observe that Q is correctly computed in phase I by the definition of Q.
For the correctness of the second phase, we show that the computed set equals . Let us refer to the set during the computation as K and observe that this is exactly the set of vertices inserted into the queue. We first show by induction over the ith inserted vertex. The first vertex is in as . Now, consider a . It was either added in Line 18 or Line 24. In the first case, there was a vertex such that for some . By the induction hypothesis we have and by the definition of the colosseum we have and, thus, . In the second case, there were vertices with . By the induction hypothesis, we have again . Let be the connected components of and . Since the colosseum is universal consistent with respect to Q by Lemma 3, we have . By the definition of the colosseum, we have and, thus, .
To see , consider for a contradiction the vertices of in reversed topological order (recall that the colosseum is acyclic) and let C be the first vertex in this order with and . If , we have by phase I and are complete, so assume otherwise. Since , we have either or . In the first case, there is a block with . Block , thus, precedes C in the reversed topological order and, by the choice of C, we have . Therefore, at some point, is extracted from the queue and, in Line 18, C would be added to K, a contradiction.
In the second case, there are vertices with . By the choice of C, we have again . Since H is universal consistent with respect to Q, we have for every that is contained in . In particular, the vertices , , ⋯, are contained in , and these elements are added to K whenever the are processed (for simplicity, assume here that ℓ is a power of 2). Once these elements are processed, Line 24 will also add their union, that is, vertices of the form . In this way, the process will add vertices that correspond to increasing subgraphs of G to K, resulting ultimately in adding into K, which is the contradiction we have been looking for.
Once is known, it is easy to compute the subgraph , that is, to compute the edges of the subgraph induced by . Phase III essentially iterates over all vertices and adds edges according to the definition of the colosseum.
For the runtime, observe that the queue will contain exactly the set and, for every element extracted, we search through the current , which leads to the quadratic timebound of . Furthermore, we have to compute the neighborhood of every extracted element, and we have to test whether two such configurations intersect—both can easily be achieved in time . Finally, in phase III, we have to compute connected components of the elements in , but since this is possible in linear time per element, it is clearly possible in time for the whole graph. □
4.5. Distance Queries in Edge-Alternating Graphs
We have just discussed how to compute the pit for a given graph and . The computation of graph measures such as treewidth now boils down to simple distance queries to this pit. To obtain an intuition of “distance” in edge-alternating graphs, think about such a graph as in our game and consider some vertex v. There is always one active player that may decide to take one existential edge (a fly-move in our game) or the player may decide to ask the opponent to make a move and, thus, has to handle all universal edges (a reveal-move in our game). From the point of view of the active player, the distance is thus the minimum over the minimum of the distances of the existential edges and the maximum of the universal edges.
Definition 2 (Edge-Alternating Distance)
. Let be an edge-alternating graph with and , let further be a constant, and and be weight functions. The distance from v to Q is inductively defined as for and otherwise: Lemma 4. Given an acyclic edge-alternating graph , two weight functions and , a source vertex , a subset of the sinks Q, and a constant . The value can be computed in time and a corresponding edge-alternating path can be output in the same time.
Proof of Lemma 4. Since
H is acyclic, we can compute a topological order of
using the algorithm from [
80]. We iterate over the vertices
v in reversed order and compute the distance as follows. If
v is a sink, we set:
If v is not a sink, we have already computed for all and, hence, can compute by the formula of the definition. Since this algorithm has to consider every edge once, the whole algorithm runs in time . A path from s to Q of length can be found by backtracking the labels starting at s. □
Being able to answer distance queries in the pit yields an easy way of computing graph measures that have game theoretic characterizations [
61,
62,
76]. For instance, if we wish to compute a tree decomposition (there is no bound on the number of branches nor on the depth), we seek a winning strategy that may use an unbounded number of reveals and fly-moves—hence, we just can look for
any path from the start configuration to
Q. If we, instead, look for a path decomposition, we seek a tree decomposition without branches—hence, we need a winning strategy that does not use reveals and we can find one by introducing heavy weights on the universal edges. The following theorem collects graph measures that can be computed with similar arguments. We provide a sketch that illustrates how the weights have to be chosen within the main text; the interested reader finds the full (unfortunately somewhat technical) proof in
Appendix A.
Theorem 2. Given a graph G and an integer k, we can decide in time whether G has { treewidth, pathwidth, treedepth, q-branched treewidth, dependency treewidth } at most k.
Proof. All five problems have game theoretic characterizations in terms of the same search game with the same configuration set [
61,
62,
76]. More precisely, they condense to various distance questions within the colosseum by assigning appropriate weights to the edges.
treewidth: To solve treewidth, it is sufficient to find any edge-alternating path from the vertex to a vertex in Q. We can find a path by choosing and as , and by setting .
pathwidth: In the pathwidth game, the searchers are not allowed to perform any reveal [
76]. Hence, universal edges cannot be used and we set
to
. By setting
to
and
, we again only need to find some path from
to
Q with weight less than
∞.
treedepth: In the game for treedepth, the searchers are not allowed to remove a placed searcher again [
61]. Hence, the searchers can only use
k existential edges. Choosing
as
,
as
, and
is sufficient. We have to search a path of weight at most
k.
-branched treewidth: For
q-branched treewidth, we wish to use at most
q reveals [
62]. By choosing
as
,
as
, and
, we have to search for a path of weight at most
q.
dependency treewidth: This parameter is, in essence, defined via graph searching game that is equal to the game we study with some fly- and reveal-moves forbidden. Forbidding a move can be achieved by setting the weight of the corresponding edge to ∞ and by searching for an edge-alternating path of weight less than ∞. □
4.6. Extending the Algorithm to Directed Treewidth
D-width has a game theoretic characterization based on the following version of the game: The searchers and the fugitive now play on a digraph
G, the searchers have unlimited reveals (
), and the fugitive is restricted to move inside strongly connected components (i. e., she can only reach vertices from which there is path back to her current position). Let D-search
be the minimal number of searchers required to catch the fugitive in a
monotone way. In contrast to the games we have considered previously, the number of required searchers may be reduced if we allow non-monotone strategies [
81]. However, this is not relevant for the D-width, as we have:
Fact 2 ([81]). D-search (G).
Similar to the undirected games, we can construct a colosseum H, where each vertex corresponds to a configuration of the game. We put an existential edge from to when we can transform to by placing a searcher in and by removing all covered searchers (i. e., all searchers that stand on vertices v with ). A universal edge is put from C to all its strongly connected components .
Observation 1. Apart from G now being directed, not much changes for the colosseum. In particular, it is easy to see that it is still an acyclic edge-alternating graph. Thus, we can compute the pit in it using Theorem 1.
Corollary 1. Given a digraph and an integer k, we can test whether or not we have in time .
Proof. Compute the pit for the directed graph using Theorem 1; weight the edges with
and
as
, and set
(as for undirected treewidth in Theorem
Section 4.5). Find a shortest edge-alternating path from
V to the sinks of the pit using Lemma 4. □
5. Color Coding Sieves
The bottleneck in practical implementations of the presented algorithm is the enumeration of compatible blocks that can be glued (Line 22 and 23 in
Figure 5). The same problem was observed in the positive-instance driven algorithms for treewidth [
52] and treedepth [
48]. Both used so called
block sieves to tackle this problem.
These sieves are data structures based on set tries [
82] allowing for an efficient enumeration over blocks that are
possible candidates. More precisely, if
K is the set of already computed blocks and the algorithm from
Figure 5 reaches Line 22 with a block
C, a block sieve shall efficiently enumerate a set
such that all
for which the algorithm reaches Line 24 are contained in
while
is maximized. Trivially, one could store
K as list and just test for every element whether it is compatible (this is exactly what
Figure 5 does). A block sieve improves this naive idea by storing the sets in a tree that represents intersections. Hence, while enumerating the output, one can prune some parts of the tree (of
K) and, thus, has to consider only a subset of
. Tamaki presented this idea for the first time [
52] and a more involved version was used by Trimble [
48]. However, both implementations came with the drawback that they do
not provide any guarantee on how well they sieve. We provide a randomized data structure for which we can provide tight bounds for the probability that certain unnecessary blocks are pruned. Furthermore, we show how to derandomize this data structure using the well-known color coding technique and obtain an implementation of the block sieve data structure that correctly prunes
all of these blocks.
Another disadvantage of set tries is the overhead introduced by managing a tree structure of sets compared to, say, storing the blocks in a simple list or array. During the development of our treedepth solver
PID for PACE 2020, we actually observed that block sieves can negatively impact the performance of positive-instance driven solvers on instances of medium size [
49].
In this section, we develop a randomized data structure that gives us the performance advantage of block sieves, reduces the overhead introduced by the set tries, and provides provable guarantees on the sieve quality. Color coding sieves apply different filter strategies successively to divide the set of all blocks into smaller and smaller sets. These sets often become small enough to be stored in simple lists. Only if these lists become too large, we divide them into multiple lists via a random choice. If such a separation happens frequently, the data structure converges into a classical set trie.
We assume a total order < on V, that is, . Furthermore, we denote the smallest vertex in a set by . Observe that < implies a partial order ⋖ on subgraphs where if, and only if, . The color coding sieve will be used to store the set , which, as before, consists of blocks C. The first operation supported by our data structure is the insertion operation that inserts a block C to the set represented by the data structure and is denoted by insert(C).
The second operation is used to speed up Line 22 in Listing 5. For a fixed block
C, we have to enumerate all blocks
that (i) do
not intersect
C (procedure intersect(
C,
) in
Figure 6) and that (ii) satisfy
(procedure offer(
C,
t) in
Figure 6). Recall that two blocks intersect if
,
or
.
Definition 3. A block is compatible with respect to a block C if all of the following holds:
;
;
, , and .
The set of all blocks that are compatible to C is denoted by .
In light of this definition, query operation query(C) should return a super set of . To support efficient implementation of such queries, a color coding sieve stores a set of blocks in three levels. Each level filters the blocks by making use of one of the three items of Definition 3.
The level-1 sieve partitions the blocks into sets for to make use of the partial ordering ⋖. We choose this partition because there are in general many more blocks with than with .
Each set
is stored as a
level-2 sieve of depth γ. These sieves are the eponym for the data structure and partition
by making use of
colorings
. Each coloring assigns two colors, say blue and orange, to the vertices of
G. Let
and
be the set of orange and blue vertices according to
, respectively. The set
is partitioned into sets
, where
. A block
C belongs to
if, and only if, the number of orange neighbors w. r. t.
is exactly
, that is,
The idea is that whenever we query a block
C with
blue neighbors, we only have to search for compatible blocks in those sets
with
.
Finally, the sets are stored as level-3 sieves, which are lazily built random set tries. Initially, we store the set as a list. If the size of the list grows too large, i. e., for a threshold , we pick a random vertex and divide into and . These sets are then recursively managed by new level-3 sieves. Observe that a level-3 sieve degenerates into a set trie with random order after n splits. However, because of the other sieve levels, we hope for far fewer recursive steps in the level-3 sieves.
5.1. Insert a Block to the Color Coding Sieve
Inserting a block C is straight forward: Every sieve adds it to the corresponding sieves of the next level. In detail, the level-1 sieve would add C to the sieve with . The level-2 sieve, on the other hand, counts, for , the number of orange neighbors of C and adds the block to . Finally, this level-3 sieve follows a path from the root in the trie to a leaf by checking for vertices on that path whether they are in C. Then C is added to the list stored at the leaf, which eventually is split if it grows too large.
5.2. Query the Color Coding Sieve
To answer query(C), we need to iterate through the sieves. For the level-1 sieve, let q be such that . As we only need to find blocks with , we can focus our search on the sets with . In order to sieve out elements on level 2, let C have blue neighbors (w. r. t. ). We only need to consider sets with for all .
Finally, for level-3 sieves, if is a list, we simply output that list. If is split into and for a vertex , we have to investigate these sets recursively. If , we only have to recur in , as we seek blocks that are disjoint from C. Otherwise, we have to search in both sets.
The data structure is illustrated in
Figure 7 together with the steps corresponding to an insert and a query. The following lemma states that the color coding sieve is, in fact, a block sieve: the output of query(
C) contains all blocks that are compatible to
C.
Lemma 5. After a sequence of insertions has inserted a set K of blocks to a color coding sieve that corresponds to a graph and , we have for all possible blocks C.
Proof. All three levels of the color coding sieve manage a partition of the set of blocks they contain and, thus, of K. We argue that any is output on query(C). The proof is by contradiction, so assume is pruned by one of the sieves.
If is pruned on level 1, it must have been in a set with and for . Thus, and, hence, is not compatible with respect to C by property 1 of being compatible.
Now, assume was pruned by the level-2 sieve. Then was stored in a set that was not explored. Hence, there must be an index and a number with such that contains at least orange and blue vertices with respect to . This is a witness for and, thus, a contradiction to property 2 of being compatible.
Finally, if was pruned by the level-3 sieve, then clearly the sieve contains multiple layers (otherwise the whole list is output). The only way the sieve prunes is that it had split its list with a vertex and . Since was pruned, we have and, hence, —a contradiction to property 3 of being compatible. □
5.3. Optimizing Level-2 Sieves
We have not yet specified the colorings used in level 2. In the following, we first consider randomized colorings and then make use of color coding for derandomization. Using the guarantees provided by this technique, we obtain a provable running time bound for the level-2 sieve. We are interested in the probability that a block with is part of the output if we use random colorings.
Lemma 6. Let and fix some blocks C and with . If is chosen randomly, the probability that is output by query(C) is at most Proof of Lemma 6 Let and let be a randomly sampled coloring. Note that is output by query(C) if, and only if, , where we define as the number of blue neighbors and equivalently as the number of orange neighbors.
A coloring is called
good if
as it allows to discard
. A vertex
is
good if either
and
or
and
. Hence, a coloring is good if at least
vertices are good. Note that all vertices in
are good (as each vertex is colored). In the following, we thus assume that
, which is the worst case. As each coloring occurs with probability
, the probability to hit a good coloring is then exactly
Hence, the probability of hitting a non-good coloring (and outputting
) is at most
This term is maximized for
, as the denominator grows faster than the nominator. Hence, the probability to output
is at most
□
If we choose all colorings randomly and independent, we obtain:
Corollary 2. Fix some blocks C and with . If are chosen randomly and independent, the probability that is output by query(C) is at most We can now increase until the term is below a tolerable threshold. If we add sufficiently many colorings, we may obtain the same result with deterministic colors that are produced by hash functions (that is, the level-2 sieve can be derandomized).
Definition 4. For two natural numbers n and k, an -universal coloring family is a set Λ of functions such that for every subset of size and for every mapping , there is at least one function with for all .
It is well-known that such families can be constructed via hash functions.
Theorem 3 (Theorem 13.41 in [
83])
. For all natural numbers n and k, an -universal coloring family Λ of size can be found in time . Let be -universal coloring family and assume that we operate the level-2 sieve with colorings such that each of the colorings is produced by one of the hash functions in . Now assume we perform query(C) and fixate any block with . By the properties of -universal coloring families, there is at least one coloring in that colors the vertices in in such a way that contains at least ℓ orange vertices, contains at least r blue vertices, and . Hence, the level-2 sieve prunes and, therefore, prunes all blocks that are incompatible to C by property 2 of being compatible. We collect this finding in form of the following theorem:
Theorem 4. There is a computable function such that for any graph G on n vertices and any , the level-2 sieve can be implemented deterministically with colors. When a block C is queried, this sieve prunes all stored blocks with .
5.4. Pruning Queries in Level-3 Sieves
If the level-3 sieve degenerates into a set trie, we can use the structure of the trie to prune queries. Consider a node p of the trie and observe that the path from p to the root defines two sets and of required and forbidden vertices, respectively. Each block stored in the subtrie rooted at p fulfills and . Hence, if , we do not have to explore p or its children. Define a pin to be a vertex with and , and let be the set of pins at p. Note that all blocks stored in the subtrie rooted at p are adjacent to v and, thus, we can prune the search if as all blocks then intersect with C. Pins become neighbors of glued blocks and, hence, we can also prune if .
6. Experimental Evaluation of Color Coding Sieves
In this section, we experimentally evaluate the performance gain of a positive-instance driven algorithm when equipping it with a color coding sieve. We exemplarily do so by adding the color coding sieve (with
and randomly generated coloring) to our treedepth solver
PID that is built on the algorithms developed within this paper [
49]. A comparison of
PID with other state-of-the-art treedepth solvers was recently performed in the light of PACE 2020 and can be found in [
45].
We perform the experiments on a computer equipped with 64 GB of RAM and an AMD Ryzen Threadripper 3970X with 32 cores of 3.7 Ghz each and with 144 MB of combined cache. The system runs on Ubuntu 18.04.5 LTS, 64bit. We let the solver run on two benchmark sets: the well-known DIMACS graph coloring instances (see [
34,
84] for an overview of these instances in light of treewidth), and the instances that were used in the exact track of the treedepth challenge PACE 2020 [
45]. Both solvers (without and with color coding sieves) were run for 10 min on each instance. The results of the experiment are illustrated as scatter plots in
Figure 8 (the left one corresponds with the DIMACS instances, the right one to the PACE 2020 instances).
As one can observe, the color coding sieve generally improves the performance of the solver. Just on a few outlier instances, the solver cannot utilize this data structure, which is probably due to many non-compatible blocks that have a small neighborhood and, thus, are not pruned by the level-2 sieve. We can also observe that the obtained speedup is larger on the PACE 2020 instances than on the DIMACS instances. The PACE instances were generally harder to solve for PID and contained more blocks. Hence, the solver can utilize the color coding sieve better on this benchmark set.
6.1. Color Coding Sieves on Hyperbolic Random Graphs
In this section, we investigate the potential performance boost obtained by using coloring coding sieves on
hyperbolic random graphs. We use the same experimental setup as in the last section and, again, equip our treedepth solver
PID [
49] with the color coding sieve data structure. In contrast to the last section, we will now:
For this experiment, we use
hyperbolic random graphs, which are known to replicate many structural properties of real-world networks [
85,
86]. Loosely speaking, these graphs are generated by sampling points randomly in a disk (these are the vertices) and by connecting points by an edge if their
hyperbolic distance is smaller than some predefined threshold.
We generated a set of 210 hyperbolic random graphs using the
Hyperbolic Graph Generator [
87]. The generator expects six parameters that we set as shown in
Table 1. The solver
PID was used with the four configurations explained in
Table 2, whereby the level-2 sieves always use uniformly sampled random colorings.
All configuration of the solver were run on all instances for at most 30 min. The results of the experiment are illustrated in a cumulative distribution function plot in
Figure 9. Various interesting findings are contained in the plot: First, we can observe that the core solver without any sieve layer (-wo) cannot fully utilize the provided 30 min time window. All instances solved by this configuration are solved within 20 min and, indeed, afterwards the amount of blocks becomes too large to be enumerated naively.
Second, we see the small (and expected) disadvantage of solvers with color coding sieves (-trie and -color-1) compared to the core algorithm (-wo) on “easy” instances (that can be solved in a minute or less). Of course, using involved data structures comes with an overhead and, if there are simply not enough blocks, we may not overcome this disadvantage with the improvements provided by the data structure. However, we can also observe that the performance of the solver with lazily built tries (-trie) and with the full color coding sieve (-color-1) quickly outperforms the core solver on the remaining instances. For the same reason as mentioned above, the lazily built set trie alone is better than the whole sieve on “medium hard” instance (solvable in about five minutes). Then, on even harder instances with more blocks, the additional layers can be utilized and the full color coding sieve provides the overall best performance.
Third, we can observe that, on this test set, choosing (-color-2) has no positive effect compared to using (-color-1). Adding more colorings increases the overhead of the data structure and, thus, a negative effect is expected if a layer cannot be fully utilized. Here, we conclude that on instances that are currently tractable for the solver, there are not enough blocks such that a second random partition sufficiently improves the enumeration of compatible blocks. However, we can also observe that the trend is positive, i. e., the overhead of a second coloring is reduced more and more on harder instances. We thus conjecture that, if the solver can be tuned to solve larger instances, the positive effect of colorings, theoretically provided by Corollary 2, will also have a positive impact in practical implementations.
6.2. Sieve-Quality of the Individual Layers
So far, we measured the performance boost obtained by adding a color coding sieve to PID with respect to the overall time the solver needs to solve an instance. In this section, we rather focus on the quality of the individual layers of the sieve. That is, we do not measure the time used to solve an instance but measure the amount of blocks that a sieve filtered.
In more detail, we measure the
total number of blocks generated by
PID (that is, the total number of blocks inserted into the sieve) and the number of
compatible blocks that were filtered from the output of the sieve (over the complete run of the solver). We compare this number with the
number of loaded blocks, which is the number of blocks returned by the sieve. Of course, all compatible blocks are loaded, but (if the sieve works poorly) many other blocks may be loaded, too. We measure the
performance of the sieve as the fraction of falsely loaded blocks over all non-compatible blocks. See
Table 3 for the exact terminology.
Observe that, in the light of Corollary 2 and Theorem 3, the performance of a color coding sieve converges to 1 if
, the number of colorings, converges to infinity. See
Figure 10 for an illustrative example.
For the following experiments, we only use
a single layer of the color coding sieve and make all measurements with respect to a complete run of the solver for a given instance (i. e., summed over various values of the target width
k). Since we aim to obtain a good estimation of the actual performance of the various sieves via experimental means, we consider rather difficult instances in this section. First, in
Table 4, we consider
-grid graphs, which are well-known to be difficult for various graph decomposition algorithms. Secondly, we hand-crafted a set of instances that are particularly difficult for the positive-instance driven approach. Let a
-spider be the graph obtained by the following procedure: start with a star with
n leaves, then replace every edge by a path with
d vertices, and finally replace every vertex by a clique on
c vertices that is fully-connected to the vertices of adjacent cliques. (Intuitively, a star is a worst-case instance for the positive-instance driven approach, as initially only the leaves are positive subproblems and, by trying to glue them together, the solver has to explore all
subsets of the leaves. By stretching and thickening the edges, we enforce that this behaviour stays the same and circumvent heuristics internally used by the solver.) The corresponding experiment is summarized in
Table 5. Finally, we performed the experiment on a set of instances from the PACE 2020 benchmark set [
45] (see
Section 6). The results are presented in
Table 6.
From the experimental data shown in
Table 4,
Table 5 and
Table 6, we conclude three observations: First, the level-1 sieve alone does not much. This was expected, as this sieve has semantically the least function. It is intended as fast preprocessing for the other sieves. Secondly, the level-2 and level-3 sieve (a single random partition and a normal set trie) are relatively equivalent. While the former is better on spider graphs, the latter is better on instances from the PACE benchmark set. Our final observation is that both sieves greatly improve their performance if the extensions are added (more colorings for the level-2 sieve or the improvements discussed after Theorem 3 for the trie, respectively). Comparing the level-2 sieve with
to the improved trie leads again to a mixed picture in which both of the sieves are better than the other on some of the instances. We conclude that taking a random partitioning is a valuable alternative to a set trie.
The level-2 sieve has two advantages over the set trie: (i) it is comparatively easy to implement and comes with low constants and (ii) we can easily improve its performance by adding more colorings. On the downside, adding more colorings slows this sieve down. Hence, if we need a large , a set trie becomes the better choice.