Abstract
Connectivity in large-scale data center networks is a critical indicator to evaluate network state. A feasible and performance-guaranteed algorithm enables us to find disjoint paths between network vertices to ensure effective data transfer and to maintain the normal operation of network in case of faulty nodes. As an important data center network, BCube Connected Crossbars (BCCC) has many excellent properties that have been widely studied. In this paper, we first propose a vertex disjoint path algorithm with the time complexity of in BCCC, where n denotes a switch connected to n servers and k denotes dimension. Then, we prove that the restricted connectivity of . Finally, we present an fault-free algorithm in BCCC, where is the restricted connectivity. This algorithm can obtain a fault-free path between any two distinct fault-free vertices under the condition that each vertex has at least one fault-free neighbor in the BCCC and a set of faulty vertices F with .
1. Introduction
The data center network (DCN) is a critical infrastructure of cloud computing, which can provide important cloud services such as GFS [1], Bigtable [2], and Dryad [3]. A data center network is a bridge connecting large-scale servers in the data center for distributed computing. As a widely used server-centric DCN, BCCC [4] can provide good network performance using inexpensive off-the-shelf switches and commodity servers with only two network interface card (NIC) ports. BCCC has many desirable properties such as high scalability, a near-equal-length parallel path, and a small diameter. The Hamilton properties and routing algorithm of BCCC have been studied [5,6,7,8].
Server failures are normal, since there are a large number of servers in the actual network. When the network fails, how to restore normal communication should be considered first. Furthermore, whether there is a fault-free path between any two different fault-free vertices and how to construct a fault-free path using an algorithm should be also taken into account. In other words, this is a problem of fault-tolerant routing, which is also the major problem we will study in this paper.
When designing or selecting a network topology for a data center, the most fundamental consideration is the fault tolerance of the network. Fault tolerance refers to the ability to continue working in the case of a network failure. Fault tolerance is the maximum number of failed devices that the network will allow to operate normally. In this paper, fault tolerance is directly determined by the connectivity of the network. The larger the connectivity scale, the better fault-tolerant performance of the data center network. In order to overcome the shortcoming of traditional connectivity, Harary [9] introduced the concept of the restricted faulty nodes on the resulting graph. Following this trend, Esfahanian [10] proposed the concept of restricted connectivity. The restricted connectivity is the connectivity under the condition that each fault-free node has at least one fault-free neighbor.
There have been many studies on the restricted connectivity of networks. Li et al. [11] establish a universally h-restricted connectivity for a class of hypercube-based compound networks, such as hierarchical cubic network and its generalization complete cubic network. Cheng [12] studies the h-restricted connectivity of an n-dimensional balanced hypercube . Li et al. [13] investigate the h-restricted connectivity of the generalized hypercube. Liu et al. [14] prove the k-restricted edge connectivity of the data center network DCell and Lin et al. [15] establish the 3-restricted connectivity of an n-dimensional split-star network. Wang [16] shows the r-restricted connectivity of hyper Petersen graphs. Ma et al. [17] prove the restricted edge connectivity of Kronecker product graphs.
Finding disjoint paths between two vertex sets in a massively parallel system establishes secure communication paths that do not interfere with each other. Constructing multiple disjoint paths for two vertices increases the probability of constructing a fault-free path. In addition to being used to avoid congestion, speed up transmission rates, and provide alternative propagation paths, disjoint paths can also enhance the robustness of vertex failures and the ability to load balance. Wu et al. [18] propose an algorithm to give the disjoint path between any two distinct vertices in dragonfly networks. Kern [19] gives exact algorithms for disjoint paths and disjoint connected subgraphs on graphs with n vertices and m edges in H-free graphs. Hadid et al. [20] propose a self-stabilizing One-to-Many node disjoint path routing algorithm in star networks.
Fault-tolerant techniques are one of the pillar technologies of the network. At the routing algorithm level, routing fault tolerance is achieved by selecting different routing paths to bypass faulty links and nodes. Therefore, a fault-tolerant routing algorithm with good effects can be achieved by improving the traditional routing algorithm. Fault-tolerant routing algorithms for different networks have been studied. Pushparaj et al. [21] propose an algorithm for routing the packets in the case of a link fault in Mesh-of-Tree (MoT) topology. The algorithm ensures that the packets will reach their destination via the shortest possible path. Nehnouh et al. [22] introduce a new fault-tolerant routing algorithm, to tolerate permanent and transient faults in network-on-chips. Zhang et al. [23] propose a novel fault-tolerant routing algorithm for 3-ary n-cube networks based on the disjoint path with structure faults. Thuan et al. [24] propose a stochastic link-fault-tolerant routing algorithm in a folded hypercube by introducing a type of limited global information called routing probabilities. Ipek et al. [25] propose a highly adaptive fault-tolerant routing algorithm for two-dimensional network-on-chips.
In this paper, we study the vertex disjoint path construction algorithm and fault-tolerant routing algorithm under restricted connectivity in the BCCC. The major contributions are as follows:
- (1)
- We first propose a vertex disjoint path construction algorithm in BCCC. Time complexity is o(). With this algorithm, n vertex disjoint paths can be constructed for any two vertices in the BCCC.
- (2)
- We prove that under the condition that each vertex has at least one fault-free neighbor in BCCC, its restricted connectivity is and , when and , respectively, where is the connectivity.
- (3)
- We give an fault-free algorithm, where denotes the restricted connectivity of BCCC. This algorithm can obtain a fault-free path between any two distinct fault-free vertices under the condition that each vertex has at least one fault-free neighbor.
The rest of this paper is organized as follows: Section 2 provides the preliminaries. Section 3 proposes a vertex disjoint path construction algorithm. Section 4 discusses the restricted connectivity of BCCC. Section 5 gives a fault-free algorithm to obtain a fault-free path and an analysis of the time complexity of the algorithm. Section 6 provides the discussion and conclusions.
2. Preliminaries
2.1. Graph-Theoretic Terms
Given a simple graph G, we use and to denote the vertex set and the edge set, respectively. An edge with end vertices u and v is denoted by . For each vertex , if , we say that u is a neighbor of v or u is adjacent to v. The set of all the neighbors of u is called the neighbor set of u in G, denoted by . The total number of vertices of graph G is denoted by N.
Pathway P is a sequence consisting of with a length of n, and there is for any . For any two different paths, and , the starting and ending points are the same, named x and y, respectively. If , then and will be vertex disjoint paths. Furthermore, if all vertices in P are fault-free, then P will be a fault-free path. If is a path between u and x, and is a path between x and v in G, then let (,) be a path between u and v in G. The reverse of P is , denoted by .
Let and F be a set of faulty vertices. For any vertex x in G, if , then x is faulty; otherwise, x is fault-free. The connectivity of graph G is defined as . This is the minimum number of vertices needed to make the graph disconnected or trivial. If we specify that every vertex has at least one fault-free neighbor, we call the connectivity in this case the limited connectivity, which is defined as .
2.2. Structure and Properties of BCCC
The BCCC structure connects servers by using recursively defined squares. In , n denotes the n-port server and k denotes the dimension. First, we let n servers connect to an n-port switch as an element, denoted by BCCC(n,0). BCCC(n,k) is composed of n BCCC(n,k−1)s connecting elements. Two types of switch are used in BCCC, which are the type A switch and type B switch. A type A switch has n ports for forming an element and a type B switch has ports for connecting different elements. Any server x in BCCC(n,k) can be represented by and . Any switch s can be represented by and . Overall, to build BCCC(n,k), we need dual-port servers, type A switches, and type B switches. An example of is shown in Figure 1.
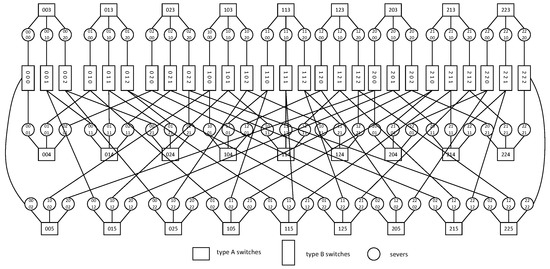
Figure 1.
Structure of .
We can see that a pair of servers and are neighbors, meaning that they are connected by the same switch, if and only if , or , such that , and , , , such that .
According to the numbering rules of the server, connects different layers. , . Therefore, BCCC can be divided into n subgraphs. We divide BCCC into n subgraphs according to the second digit number of the server from right to left. Servers with the same second digit number are located in the same subgraph. These subgraphs are named , , …, . The second digit number is 0 and the subgraph is . We named the server connected to other subgraphs , and named those not connected to other subgraphs . An example of is shown in Figure 2.
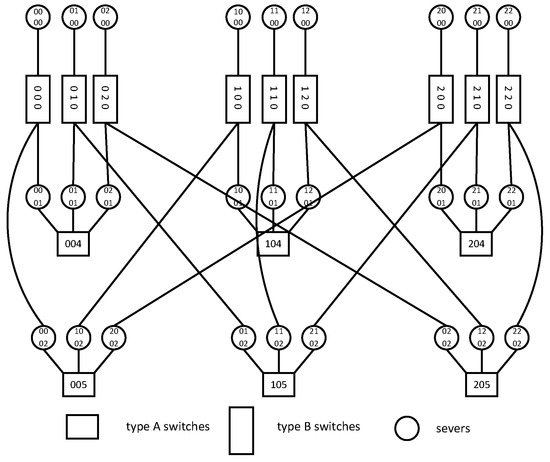
Figure 2.
Structure of .
Lemma 1.
BCCC (n,k) has the following properties [4]:
- (1)
- is (n+k−1)-regular graph. .
- (2)
- The connectivity of is
- (3)
- There are vertex disjoint paths connecting different in .
3. Vertex Disjoint Path Construction Algorithm
In this section, we propose a vertex disjoint path construction algorithm for BCCC. The algorithm constructs n vertex disjoint paths between any two nodes u and v in the BCCC.
3.1. Algorithm Description and Implementation
There are two vertex disjoint path algorithms, including BuildPathSet and Convert. BuildPathSet is the master algorithm. The Convert algorithm can change one bit of the u node number to the corresponding bit of the v node. The flow of the vertex disjoint path algorithm is as follows (refer to Algorithm 1). First, a series of v nodes located at the vertices of the same type A switch are selected. Then, a vertex located on the same type B switch as v is determined. The mode of the first path is as follows. First, we reach node x. The value of the bit of x is 0. In addition, x is on the same type A switch as the source node. The path is selected from node x to node . The second path pattern is as follows. First, some data arrive at the y node. The value of the bit of y is 1. In addition, node y and the source node reside on the same type A switch. The path is from node y to node . The other paths follow the same rules. The Convert algorithm is invoked times during the process from the source node to the target node. One digit is changed from the highest digit of the number to the lowest digit each time.
| Algorithm 1 Vertex Disjoint Path Algorithm of BCCC. |
| Input: Two different vertices u = and v = in . Let the neighbor node of the same type A switch with v be , and select any a neighbor node in the same type B switch as . |
| Output:n vertex disjoint paths from u to v. |
| 1: function BuildPathSet() |
| 2: ; |
| 3: for do |
| 4: , ; |
| 5: add u to ; |
| 6: if i then |
| 7: u = , = i, i ; |
| 8: add u to ; |
| 9: for j = k + 1; j > 0; j do |
| 10: if then |
| 11: break; |
| 12: if then |
| 13: u, = CONVERT(u, v, , , ); |
| 14: if then |
| 15: u = ; |
| 16: add u to ; |
| 17: if then |
| 18: add v, z to ; |
| 19: print(); |
| 20: function CONVERT(u, v, , , ) |
| 21: , x ; |
| 22: , y ; |
| 23: if == then |
| 24: ; |
| 25: else |
| 26: ; |
| 27: ; |
| 28: add w to ; |
| 29: ; |
| 30: u = ; |
| 31: add u to ; |
| 32: return(u, ); |
3.2. Analysis of Vertex Disjoint Path Construction Algorithm
First, the time complexity of the Convert algorithm is analyzed. The node number of u is changed from one bit to v. This node is added to the path set and the time complexity is . The second ’for’ loop in the BuildPathSet algorithm runs a total of k times from high to low with concomitant time complexity. The first ’for’ loop causes the algorithm to form a total of n paths with adjoint time complexity. In summary, the time complexity of the BuildPathSet algorithm is .
3.3. Application Examples
Example 1.
Given the network (see Figure 1), three vertex disjoint paths are constructed by the algorithm. The source node is selected as 0000 and the target node as 2011. It can be obtained that the nodes located in the same switch with the target node are 2111, 2211, and 2010. The first path is from 0000 to 2111. The Convert algorithm is used to gradually change from the highest bit to the lowest bit. Therefore, . This eventually reaches 2011 through the type A switch.
The second path first selects node 0010, which is located in the same type A switch as node 0000, and reaches 2211 from 0010, using the Convert algorithm. Therefore, . Because the 2011 node is encountered on the path to the 2211 node and 2011 is the target node, the path is obtained by jumping out directly according to lines 10 and 17 of the algorithm.
The third path selects node 0020, which is located in the same type A switch as node 0000. The Convert algorithm is used to reach 2010 from 0020. Therefore, . Finally, three vertex disjoint paths from 0000 to 2011 are obtained.
4. Restricted Connectivity of BCCC
In this section, we prove the restricted connectivity of BCCC. We refer to the entire graph of as G.
Theorem 1.
The restricted connectivity of is
, if ,
, if , when and .
Proof.
Let u and v be two vertices of the same type A switch (). Therefore, .
If , according to the definition,
Let , so is divided into two disconnected subgraphs: one is and the other is . Furthermore, u has a fault-free neighbor v. Therefore, each vertex of subgraph has at least one fault-free neighbor. Let , for , when u and v are located in the same type A switch, each node in has only one neighbor that is a faulty node. According to Lemma 1 (2), . Therefore, is constantly greater than 2 when and . It can be ensured that each node in has at least one fault-free neighbor.
In summary, is disconnected and each vertex in both subgraphs contains at least one fault-free neighbor. Hence, . Therefore, the theorem holds.
Let x and y be two vertices of the same type B switch () (). Therefore, .
If , according to the definition,
Proving that the two vertices are in the same type B switch is the same as proving the two vertices are in the same type A switch. Let , so is disconnected and each vertex in both subgraphs contains at least one fault-free neighbor. Above all, . Therefore, the theorem holds. □
Theorem 2.
The restricted connectivity of is
, if ,
, if , when and .
Proof.
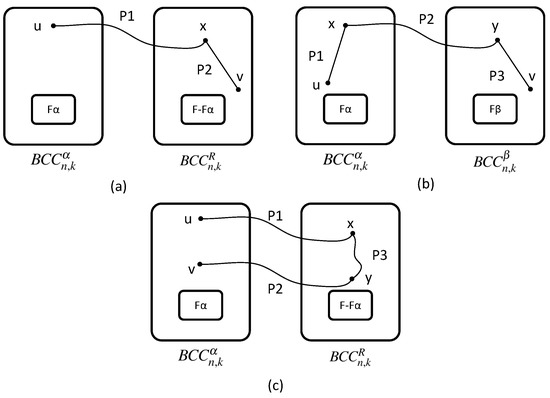
Let F be the set of faulty vertices in G. Proving this theorem is equivalent to proving, for any two vertices u and v in , there exists a fault-free path from u to v. Furthermore, any vertex in has at least one fault-free neighbor.
If u and v are adjacent, the theorem holds. Hence, we discuss the case that u and v are not adjacent. According to the structure of BCCC, BCCC can be divided into n subgraphs. Let for be the subgraph of G. Furthermore, , for . Let and . Let , be a subgraph other than in G and . If , u is named as . Otherwise, u is named as .
Lemma 2.
If F is a set of vertices in , and for any subgraph i in , is connected if .
Proof.
According to the construction rules of BCCC, U is set as the point adjacent to in to reach the conclusion that the point set of U is located in the same type A switch of subgraph and has no neighbors. Therefore, the point in the set of U points is the one with the fewest neighbors in . These vertices have k vertex disjoint paths in the subgraph. This achieves . Moreover, for any vertex x in to connect to , one of x’s neighbors in the same type A switch is not in the subgraph. Therefore, .
Because and , are connected, and the Lemma holds. □
According to the position of u and v vertices in BCCC, we have the following cases.
- Case 1. .
- Subcase 1.1. .
Without losing generality, suppose . Apparently, . According to Lemma 2, is connected. Next, we discuss the following cases.
- Subcase 1.1.1. u is .
- Subcase 1.1.1.1. .
Selecting a vertex x, , there is a path from to x in . Because is connected, there exists a fault-free path from x to v in .
- Subcase 1.1.1.2. .
Because the neighbors of are all fault vertices in subgraph , there must be a fault-free neighbor in subgraph . Now, we consider how many fault-free paths from to exist in . Furthermore, .
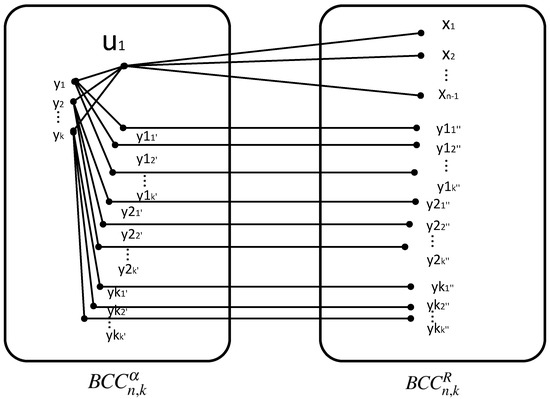
Let be all neighbors of in .
Let be all neighbors of in ; be the same type A switch neighbors of ; be all neighbors of in and . Thus, there are paths from to as follows (refer to Figure 3). The specific paths are listed below:

Figure 3.
paths from to .
Because , , . Whether or , . Therefore, there is at least one fault-free path from to . Assume that t is the last vertex in the path . If , then is a path from to v in . Otherwise, since is connected, there is a fault-free path from t to v in . Then, the path is a fault-free path from to v in .
- Subcase 1.1.2. u is .
It can be obtained that is a vertex in and its neighbors are all in this subgraph. According to the definition of restricted connectivity, there is a fault-free neighbor in . Now, we consider how many fault-free paths there are from to in .
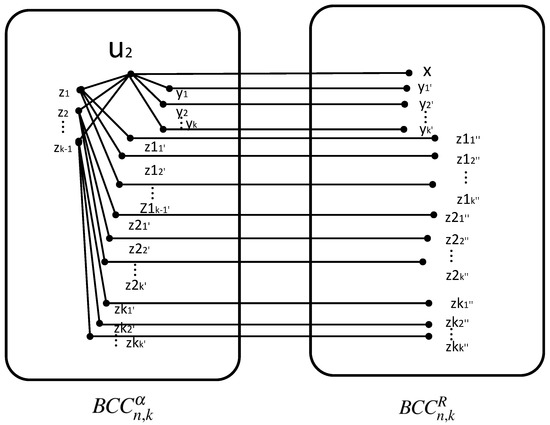
Let x be the neighbor of and .
Let be the same type A switch neighbors of ; be all neighbors of in , and .
Let be neighbors of in the same type B switch, except x; be the same type A switch neighbors of ; be all neighbors of in and . Above all, there are paths from to as follows (refer to Figure 4). The specific paths are listed below:

Figure 4.
paths from to .
Since , we have when and . Furthermore, when , whether or , . Therefore, there is at least one fault-free path P in the above paths from to . Assume that w is the last vertex in the path . If , then is a path from u to v in . Otherwise, since is connected, there is path between w and v in . Then, the path is a path from to v in .
- Subcase 1.2. .
Because and are all connected, let be a set of vertices connected to other subgraphs in . Let be a set of vertices connected to other subgraphs in . It can be obtained that . Whether or . Therefore, there must exist a fault-free vertex and in the same type A switch. If , then it is directly connected to . If , since is connected, there exists a fault-free path from u to x in . Since x and y are located in the same switch, there is a fault-free path from x to y. If , it is directly connected to . If , since is connected, there exists a fault-free path from y to v in . Then, the path is a path from u to v in (refer to Figure 5b).

Figure 5.
Figure (a) is subcase 1.1.1.1; Figure (b) is subcase 1.2; Figure (c) is subcase 2.
- Subcase 2. .
If , is connected. There exists a fault-free path from u to v in . Thus, we only need to consider that . According to subcase 1.1, if is not connected, is connected. According to subcase 1.1.1 and subcase 1.1.2, whether or , there must exist a fault-free path from u(v) to . Thus, there exists a fault-free path from u to a vertex x in and a fault-free path from v to a vertex y in . If , the path is a path from u to v. If , since is connected, there exists a fault-free path from x to y. Then, the path is a path from u to v in (refer to Figure 5c).
In summary, if there exists a fault-free path between any two vertices u and v in BCCC, the theorem holds. □
Theorem 3.
The restricted connectivity of is
, if ,
, if , when and .
Proof.
According to Theorems 1 and 2, the theorem holds. □
5. Fault-Free Routing Algorithm of under the Restricted Connectivity
In this section, we first give a fault-free routing Algorithm . Furthermore, we analyze the time complexity of this algorithm.
5.1. Algorithm Description and Implementation
Algorithm (refer to Algorithm 2) can give a fault-free path between any two fault-free vertices u and v in , where F is the set of faulty vertices in G, , and any vertex in has at least one neighbor.
| Algorithm 2 Fault-free routing algorithm of . |
| Input: Given the graph G to represent , a set of fault vertices , two different vertices u and v. The subgraph in which u is located, subgraph in which v is located. |
| Output: A fault-free path from vertex u to v in . |
| 1: function BCCFTP(u,v,,,F,) |
| 2: if then |
| 3: Return BCTP(u,v,,F); |
| 4: else if () then |
| 5: Return(u,v); |
| 6: (), , ; |
| 7: , |
| 8: if then |
| 9: if then |
| 10: PATHSEQ(u, F, , ); |
| 11: let s be the last vertex of ; |
| 12: if then |
| 13: return ; |
| 14: return(, BCTP(s,v,, ); |
| 15: else if then |
| 16: PATHSEQ(v, F, , ); |
| 17: let s be the last vertex of ; |
| 18: if then |
| 19: return ; |
| 20: return(BCTP(u, s, , F), ); |
| 21: else && |
| 22: PATHSEQ(u, F, , ); |
| 23: let s be the last vertex of ; |
| 24: if then |
| 25: return ; |
| 26: +=BCTP(s, v, , ); |
| 27: return ; |
| 28: else if then |
| 29: return(BCTP(u, v, , ). |
| 30: else |
| 31: PATHSEQ(u, F, , ); |
| 32: let s be the last vertex of ; |
| 33: PATHSEQ(v, F, , ); |
| 34: let t be the last vertex of ; |
| 35: if w be the first common vertex of and then |
| 36: return ((, u, w),(, w, v)); |
| 37: +=BCTP(s, t, , F); |
| 38: return + ; |
| 39: |
| 40: function PATHSEQ(u, F, , ) |
| 41: if then |
| 42: if then |
| 43: select one fault-free vertex x from ; |
| 44: return(u, x); |
| 45: else |
| 46: for all do |
| 47: if then |
| 48: for all do |
| 49: if then |
| 50: for all do |
| 51: if then |
| 52: select one fault-free vertex from ; |
| 53: return(u, , , , ) |
| 54: else |
| 55: Select a vertex connected to other subgraphs, select a vertex in the same type A switch, and a vertex in the same type B switch from ; |
| 56: if then |
| 57: select one fault-free vertex from ; |
| 58: return(u, , ); |
| 59: if then |
| 60: for all do |
| 61: if then |
| 62: for all do |
| 63: select one fault-free vertex from ; |
| 64: return(u, , , ); |
| 65: for all do |
| 66: if then |
| 67: for all do |
| 68: if then |
| 69: for all do |
| 70: select one fault-free vertex from ; |
| 71: return(u, , , , ); |
| 72: |
| 73: function BCTP(u, v, , F) |
| 74: Select a fault free path from in ; |
5.2. Analysis of Fault-Free Unicast Algorithm
First, the time complexity of and functions is analyzed. u in exists in the function. This depends on whether u is connected to other subgraphs, including and . The path from to the subgraph is , . The time complexity of in different situations is as follows. First, the path is , because finds a vertex x in , and returns a path . The time complexity is in this case. Second, the path is . Each vertex in the set is and the time complexity is after traversing . Each vertex in the set is and the time complexity is less than after traversing . Each vertex in the set is and the time complexity is less than after we go through . Each vertex in the set is and the time complexity is . After traversing , paths ) are obtained. The time complexity is less than O in this case.
The path from to subgraph includes , , and . First, the path is . Each vertex in the set is x and the time complexity is after the function traverses . Next, vertex is found from . The time complexity in this case is O. Second, the path is . The function traverses . The node is set on the same type A switch as u to and the time complexity to . Then, traversing sets the point connected with other subgraphs as , and the time complexity is less than . Finally, is traversed and node selected. In this case, the time complexity is less than . Third, the path of is the same as the path of . In summary, the time complexity of the function is combined with and .
Next, we analyze . is divided into two cases, including and .
In the case of , if , Algorithm will first obtain a fault-free path from u to a vertex s in by . The time complexity of this part is . Next, Algorithm will return if ; then, the time to obtain the path from u to v in is . Otherwise, Algorithm will return (,); then, the time to run is O and the time to obtain a path (, by connecting path and is O. Thus, the time to obtain the path from u to v in is O = O. Furthermore, for subcases , , and , the time to obtain the path from u to v in is O, which is similar to that discussed in the case of .
In the case of , if , Algorithm will firstly obtain a fault-free path from u to v in by PATHSEQ . The time complexity of this part is O. Then, Algorithm BCCFTP will first obtain a fault-free path from u to a vertex s and path from v to a vertex t in in the time of O. If and have a common vertex w, Algorithm will return (Path, Path. Since the time to obtain Path is O, the time complexity is O = O. If and have no common vertex, the function will run to construct a fault-free path from s to t. The time complexity of this part is O. Therefore, the time to obtain the path from u to v in G is O = O.
In summary, the time complexity of Algorithm is O.
6. Discussion and Conclusions
As the infrastructure of cloud computing, data center networking has become a hot topic in recent years. As an important DCN model, BCCC can support millions of servers with excellent communication characteristics and provide good fault tolerance. In this paper, a point disjoint path algorithm with time complexity is proposed. The algorithm can give n vertex disjoint paths between any two vertices. Multiple disjoint paths can enhance routing performance and improve network reliability. Then, we prove the condition that each vertex has at least one fault-free neighbor, and that the restricted connectivity of BCCC is and , when and , respectively. Restricted connectivity can be obtained at almost twice the traditional connectivity. The larger the connectivity scale, the better the fault-tolerant performance of the data center network. Finally, we give the trouble-free algorithm with limited connectivity. This algorithm can obtain the fault-free path between any two different fault-free vertices. The premise is that each vertex has at least one fault-free neighbor in the BCCC.
Our algorithm is proposed based on the condition that each fault-free vertex has one fault-free neighbor. In the majority of cases, each vertex has more than one fault-free neighbor in large interconnected networks. In the future, the h-restricted connectivity of BCCC will be studied, which is a guarantee for accommodating more failed servers when the network is large enough. Fault-free algorithms based on h-restricted connectivity can ensure that the network allows more fault nodes. In addition, many other network connectivity limitations in DCN have not been studied, such as Ficonn [26], HCN and BCN [27]. This, together with the design of related routing algorithms, may be worth further investigation. In the meantime, most networks only consider server failures. In fact, both switches and links could fail. There are currently few studies on switch and link failures. Therefore, the fault tolerance of switches and links in the network can be analyzed, and corresponding fault-tolerant routing algorithms can be designed to ensure the connectivity of the network.
Author Contributions
Conceptualization, J.L. and X.D.; methodology, J.L. and H.L.; software, J.L. and Z.H.; validation, J.L. and X.D.; formal analysis, J.L. and Z.H.; investigation, J.L. and X.D.; data curation, J.L. and H.L.; writing—original draft preparation, J.L. and X.D.; writing—review and editing, J.L., X.D., H.L. and Z.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Special Project for Key R&D and the Promotion of Science, Technology Department of Henan Province (202102210327, 222102210272, 222102210052, 222102210007, 222102210062 and 212102210094), the Key Technology Research and Development Project of Henan Province under Grant (222102210055), the Postgraduate Education Reform and Quality Improvement Project of Henan Province under Grant (YJS2022JD26), the Major Science and Technology Projects of Henan Province, the Major Public Welfare Projects of Henan Province (201300210400) and Kaifeng Science and Technology Development Plan (2201010).
Data Availability Statement
Not applicable, the study does not report any data.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ghemawat, S.; Gobioff, H.; Leung, S.T. The Google file system. In Proceedings of the Nineteenth ACM Symposium on Operating Systems Principles, Bolton Landing, NY, USA, 19–22 October 2003; pp. 29–43. [Google Scholar]
- Chang, F.; Dean, J.; Ghemawat, S.; Hsieh, W.C.; Wallach, D.A.; Burrows, M.; Chandra, T.; Fikes, A.; Gruber, R.E. Bigtable: A distributed storage system for structured data. ACM Trans. Comput. Syst. (TOCS) 2008, 26, 1–26. [Google Scholar] [CrossRef]
- Isard, M.; Budiu, M.; Yu, Y.; Birrell, A.; Fetterly, D. Dryad: Distributed data-parallel programs from sequential building blocks. In Proceedings of the 2nd ACM SIGOPS/EuroSys European Conference on Computer Systems 2007, Lisboa, Portugal, 21–23 March 2007; pp. 59–72. [Google Scholar]
- Li, Z.; Guo, Z.; Yang, Y. BCCC: An expandable network for data centers. In Proceedings of the Tenth ACM/IEEE Symposium on Architectures for Networking and Communications Systems, Marina del Rey, CA, USA, 20–21 October 2014; pp. 77–88. [Google Scholar]
- Castillo, A.C. BCube Connected Crossbar and GBC3 Network Architecture: An Overview. In Proceedings of the 2022 31st Conference of Open Innovations Association (FRUCT), Helsinki, Finland, 27–29 April 2022; pp. 37–44. [Google Scholar]
- Li, X.Y.; Lin, W.; Liu, X.; Lin, C.K.; Pai, K.J.; Chang, J.M. Completely independent spanning trees on BCCC data center networks with an application to fault-tolerant routing. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 1939–1952. [Google Scholar] [CrossRef]
- He, X.; Zhang, Q.; Han, Z. The Hamiltonian of Data Center Network BCCC. In Proceedings of the 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing,(HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Omaha, NE, USA, 3–5 May 2018; pp. 147–150. [Google Scholar]
- Han, Z.; Zhang, W. A summary of the BCCC data center network topology. In Proceedings of the 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Omaha, NE, USA, 3–5 May 2018; pp. 270–272. [Google Scholar]
- Harary, F. Conditional connectivity. Networks 1983, 13, 347–357. [Google Scholar] [CrossRef]
- Esfahanian, A.H. Generalized measures of fault tolerance with application to n-cube networks. IEEE Trans. Comput. 1989, 38, 1586–1591. [Google Scholar] [CrossRef]
- Li, X.; Zhou, S.; Ma, T.; Guo, X.; Ren, X. The h-Restricted Connectivity of a Class of Hypercube-Based Compound Networks. Comput. J. 2022, 65, 2528–2534. [Google Scholar] [CrossRef]
- Cheng, D. The h-restricted connectivity of balanced hypercubes. Discret. Appl. Math. 2021, 305, 133–141. [Google Scholar] [CrossRef]
- Li, X.; Zhou, S.; Guo, X.; Ma, T. The h-restricted connectivity of the generalized hypercubes. Theor. Comput. Sci. 2021, 850, 135–147. [Google Scholar] [CrossRef]
- Liu, X.; Meng, J. The k-restricted edge-connectivity of the data center network DCell. Appl. Math. Comput. 2021, 396, 125941. [Google Scholar] [CrossRef]
- Lin, L.; Huang, Y.; Wang, X.; Xu, L. Restricted connectivity and good-neighbor diagnosability of split-star networks. Theor. Comput. Sci. 2020, 824, 81–91. [Google Scholar] [CrossRef]
- Wang, S. The r-Restricted Connectivity of Hyper Petersen Graphs. IEEE Access 2019, 7, 109539–109543. [Google Scholar] [CrossRef]
- Ma, T.; Wang, J.; Zhang, M. The restricted edge-connectivity of Kronecker product graphs. Parallel Process. Lett. 2019, 29, 1950012. [Google Scholar] [CrossRef]
- Wu, S.; Fan, J.; Cheng, B.; Yu, J.; Wang, Y. Connectivity and constructive algorithms of disjoint paths in dragonfly networks. Theor. Comput. Sci. 2022, 922, 257–270. [Google Scholar] [CrossRef]
- Kern, W.; Martin, B.; Paulusma, D.; Smith, S.; van Leeuwen, E.J. Disjoint paths and connected subgraphs for H-free graphs. Theor. Comput. Sci. 2022, 898, 59–68. [Google Scholar] [CrossRef]
- Hadid, R.; Villain, V. A Self-stabilizing One-To-Many Node Disjoint Paths Routing Algorithm in Star Networks. In Proceedings of the IFIP International Conference on Distributed Applications and Interoperable Systems; Springer: Berlin/Heidelberg, Germany, 2020; pp. 186–203. [Google Scholar]
- Pushparaj, J.; Soumya, J.; Veda Bhanu, P. A link fault tolerant routing algorithm for mesh of tree based network-on-chips. In Proceedings of the 2019 IEEE International Symposium on Smart Electronic Systems (iSES) (Formerly iNiS), Rourkela, India, 16–18 December 2019; pp. 181–184. [Google Scholar]
- Nehnouh, C.; Senouci, M. A New Fault Tolerant Routing Algorithm for Networks on Chip. Int. J. Embed.-Real-Time Commun. Syst. (IJERTCS) 2019, 10, 68–85. [Google Scholar] [CrossRef]
- Zhang, Y.; Fan, W.; Han, Z.; Song, Y.; Wang, R. Fault-tolerant routing algorithm based on disjoint paths in 3-ary n-cube networks with structure faults. J. Supercomput. 2021, 77, 13090–13114. [Google Scholar] [CrossRef]
- Thuan, B.T.; Ngoc, L.B.; Kaneko, K. A stochastic link-fault-tolerant routing algorithm in folded hypercubes. J. Supercomput. 2018, 74, 5539–5557. [Google Scholar] [CrossRef]
- Ipek, A.; Tosun, S.; Ozdemir, S. HAFTA: Highly adaptive fault-tolerant routing algorithm for two-dimensional network-on-chips. Concurr. Comput. Pract. Exp. 2021, 33, e6378. [Google Scholar] [CrossRef]
- Li, D.; Guo, C.; Wu, H.; Tan, K.; Zhang, Y.; Lu, S. FiConn: Using backup port for server interconnection in data centers. In Proceedings of the IEEE INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 2276–2285. [Google Scholar]
- Guo, D.; Chen, T.; Li, D.; Li, M.; Liu, Y.; Chen, G. Expandable and cost-effective network structures for data centers using dual-port servers. IEEE Trans. Comput. 2012, 62, 1303–1317. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).