1. Introduction
In recent decades, with the vigorous progress of renewable energy, the randomness of renewable generation such as wind power and photovoltaics has made the smooth scheduling of power systems a hot topic [
1]. In order to enhance the flexible capacity and peaking capacity of the power system, voltage and frequency control of small generation units (GUs) in local power plants becomes necessary. Recently, the scheduling scheme based on network communication has been widely used in power systems [
2]. However, the utilization of heterogeneous electrical and electronic components with networks has made the data transmission fairly open to various cyber attacks. This can lead to serious security consequences. Unlike the attacks on traditional systems that limit the influence to the cyber level, the physical world of power systems can be impacted by malicious cyber attacks [
3], causing serious social and livelihood problems. Thus, these strong demands for power systems exist, despite malicious cyber attacks, designing analysis and synthesis approaches to ensure their reliability and security [
4,
5].
Typically, the various malicious attacks involve deception attacks and denial-of-service (DoS) attacks, where the latter attack leads to the information absence of the actuator and sensor by blocking the data transmission to their respective destinations. The DoS attack is very common in networked control systems, and lots of studies have been presented on networked power systems under DoS attacks. In [
6], an
load frequency control based on an event-triggered strategy is studied for multi-area power systems, and the resilient control approach is proposed to deal with the presence of DoS attacks. Security issues in remote state estimation with the existence of jamming attacks are investigated in [
7] using a game-theoretic approach. In [
8,
9], the optimal DoS attack strategies for maximizing the deterioration on the system performance from the view of the adversary are investigated.
Stability analysis is a popular research topic on security problems of control systems under DoS attacks. In [
10], the DoS attack model is characterized according to its frequency and duration, input-to-state stable (ISS) is demonstrated for the attacked closed-loop system, and transmission timing is scheduled based on this DoS attack model. Based on the analysis strategy proposed in [
10], to maximize the attack intensity index according to the frequency and duration of the attack model with which the stability of the system is not destroyed, a resilient control framework is proposed in [
11]. In [
12], the controller design and analysis is investigated with this DoS attack model for nonlinear dynamics. In [
13], based on the ISS control framework, the scenario of multiple transmission channels is considered for linear systems under DoS attacks. In [
14], an output-based synthetical control design strategy for a class of hybrid nonlinear dynamics under DoS attacks is provided in a dynamic event-triggered framework. In [
15], observer-based asynchronous control for switching power systems subject to DoS attacks is discussed. However, research on the resilient control of power systems under the condition of unreliable communication is still insufficient; particularly, the design of the output voltage and current control scheme of the GU via the network is still a challenging problem.
Traditionally, the control algorithms are executed in the time-scheduled strategy, in which the sampling and data communication are carried out periodically. Although the time-based periodic sampling might be preferable from the point of view of system analysis and design, it leads to the unnecessary waste of limited resources. Usually, network-based scheduling signals in power systems are not transmitted in real time but communicate when scheduling needs arise. In this way, the traditional time-triggered control method is no longer suitable. The event-triggered control scheme as a control strategy based on intermittent communication has been a wide concern for networked control systems [
16,
17,
18], and it can be used to construct a demand-based control scheme for GUs. In [
19], an event-triggered control (ETC) strategy with a periodic verification mechanism for linear systems is proposed, which is named periodic event-triggered control (PETC). By merging the time-scheduled strategy and ETC, the characteristic of PETC is to verify the triggering condition periodically—that is, whether to calculate and send new sampling data or new control data is determined at each periodic verification time. In [
20], consider the scenario where both the sensor-to-controller channel and the controller-to-actuator channel are communicated via a network, a PETC algorithm is designed according to the retrievable system state space model. The above studies are all about networked control systems without attacks. Practically, power system scheduling also has a fixed sampling period; however, it is still a challenge to construct a resilient control scheme for the GU under unreliable communication using the idea of PETC.
For grid-connected power plants, the purpose of scheduling is to maintain the balance and stability of voltage and frequency, which are specified by the main grid when there are demands. However, for the local power plants tasked with flexibility and peaking, voltage and frequency outputs for GU are definitively controlled according to the networked scheduling signals, and it is necessary to save network resources. By introducing the concept of neutral interactions, the dynamic model of GU in this paper is established by exploiting quasi-stationary line approximations of line dynamics [
21]. To improve the security of networked scheduling, the unreliable network communication channel is modeled as the communication interruption of the sensor channel due to the presence of a DoS attack. To construct the control framework, a smart sensor system is adopted in order to design the demand-driven mechanism (DDM)—that is, network communication is performed only when scheduling is required. Unfortunately, in the design of the control system, the load current of the unit connection is difficult to estimate. The conventional idea is to treat it as an unknown disturbance, but how to deal with the error term introduced by disturbance and noise is still a difficult point in the DDM design. To improve resilience against DoS attacks, a predictor is proposed in the controller system to compensate for the lack of data during communication intervals. Based on the ISS analysis framework, the stability when there are DoS attacks is proved and the maximum tolerable attack intensity index is quantified.
The prime innovations of this article are generalized below: First, the dynamic model of the GU for local power plant is established by exploiting quasi-stationary line approximations, and the unknown loads are treated as unmodeled disturbances, which can be restricted by the designed
observer. At the same time, the effects of disturbance and noise during the DDM design can be addressed by the quantified
performance index. Second, the advanced demand-driven resilient control method with a periodic verification strategy is presented to deal with the unreliable communication caused by DoS attacks, and the intermittent communication scenario meets the requirements of network scheduling for the GU by applying the prediction-based method. Third, based on the thought of robustness to the maximum disturbance accumulation error, the conservatism of the tolerable attack intensity in this result is decreased compared with [
10,
14].
The rest of this article is organized as follows: The GU model is described in
Section 2, and the observer and the predictor are designed. In
Section 3, the ISS of the demand-driven control approach is proved.
Section 4 gives the resilient control strategy under DoS attacks.
Section 5 provides simulation results. The conclusions of this paper are given in
Section 6.
2. System Formulation and Problem Description
First of all, the meanings of the symbols used in this paper are shown in the notation below. Then, the state space model of the GU is constructed, and the resilient control framework is designed based on it.
Notation: Let
and
be the sets of real and Euclidean spaces with dimension
n, respectively. Let
be the natural number set and
.
denotes the Euclidean norm for any vector
.
is the transpose of a given matrix
A,
is the spectral norm, and
is the logarithmic norm [
22] with
. For sets
and
, denote
by the relative complement of
in
.
denotes by the length of an interval
. For a measurable function
defined in
, the
norm of
is denoted by
.
2.1. Generation Unit Model
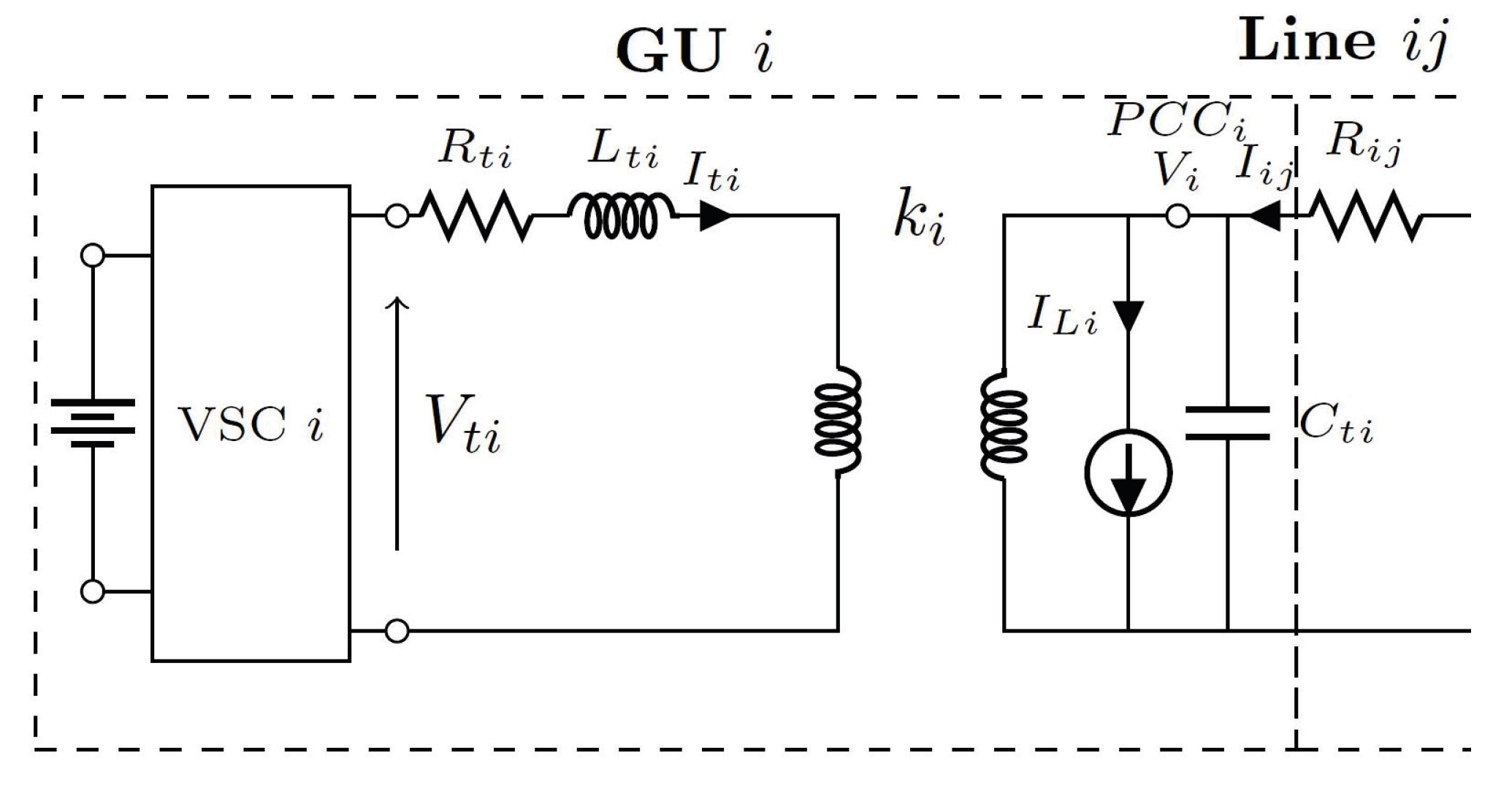
In this section, the dynamical model of the GU for a local power plant is presented. To simplify the analysis process, the realistic model of GU is assumed to consist of transformers, associated filters, and voltage source converters (VSCs) [
21]. As shown in
Figure 1, through a non-zero impedance three-phase line with
, the considered GU denoted by
i is connected with other units
j. The GU is made up of a VSC, a DC voltage source (representing a biomass or waste incineration unit), an inductance
, a series filter characterized by a resistance
, and a station step-up transformer
; further, at the point of common coupling (PCC) of the electrical network, the GUs are connected with each other through the transformer, where the transformer coefficients are represented by
and
, and
k is defined as the transformation ratio.
For the local loads that are connected to the PCC, consider the case where the GU proves the real and reactive powers. Suppose that the loads are time-varying and unknown, and the load current
is treated as the disturbance for the GU. At the PCC of each local area, the effect of high-frequency harmonics of the load voltage is attenuated by using the shunt capacitance
. In the abc-frame, based on the dynamical equations of this scheme and by applying Park’s transformation, the model rotating with speed
in the
-frame is obtained as follows:
where
is the output voltage at the PCC, and
and
are the output voltage and current of the GU, respectively. The states in (
1) and (
2) can be divided into two segments—that is, the
reference frame is divided as the real component
d- and the imaginary component
q-, respectively, and
is the line current. Modeling the load current
as the disturbance, (
1) and (
2) can be represented through the following continuous time linear dynamic form:
where
is the state vector,
is the control input,
is the unknown disturbance,
is the measurement output, and
is the measurement noise. Suppose that
and
are bounded, where
,
.
A,
B,
C, and
E are system matrices to be determined later. This model is regarded as the master model here, since the states of the line are controlled by the GU
i only for the control purpose.
To isolate the effects of other connected GUs on the grid, an approximate model is given to avoid the requirement of applying the line current in the GU’s dynamic equations. Let
; the quasi-stationary line approximations model is given as
Then, replace variable
in (
2) and divide the complex
quantities into the corresponding
d and
q components; the transformed model for GU
i is formulated as follows:
then, the dynamic model (
1) of the GU is constructed as the following state space model form:
where
,
,
,
, and
.
2.2. Control Framework
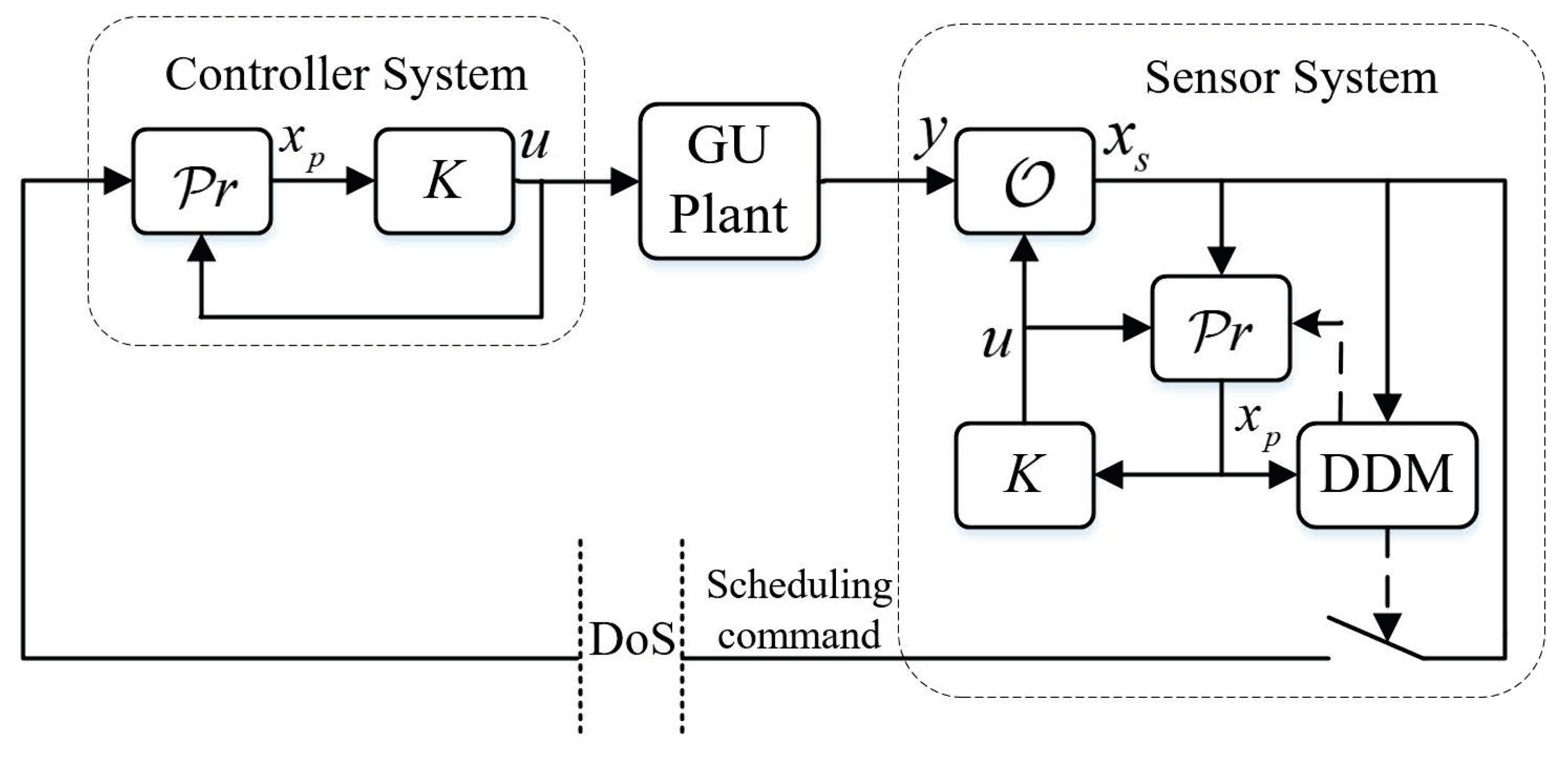
In order to meet the scheduling and control practice based on the network communication while guaranteeing the desirable scheduling performance of the GU, the control construction is designed as in
Figure 2. A sensor system is designed to transmit the measurement information to the remote controller system based on the communication network. At the same time, the network communication is unreliable, which is caused by DoS attacks.
The smart sensor system with a demand-driven method and periodic verification strategy is designed to schedule the scheduling commands. The sensor system consists of an observer
that deals with disturbance and noise, and the time when information is needed to be sent to the controller system is decided by a designed DDM. Furthermore, the controller system contains a predictor
that can compensate the GU’s state data loss during the transmission interval using the latest received data. To suppress the impact of disturbance and noise, the
observer is designed as follows:
where
denotes by the state estimation of the sensor system and
L is the designed gain matrix. Denote
by the observation error; then, the error dynamic can be formulated as
where
,
,
. Based on continuous-time systems’ bounded real lemma [
23], the gain matrix
L is able to be calculated based on the LMI in (
7) and
is obtained.
where
is a symmetric positive definite matrix and
is a small positive scalar, which represents the
performance index. The predictor is given as
Whether the observer data
are sent is determined by the demand of scheduling control, which is represented by the difference between the observed states of the GU and the predicted value of the remote controller. Then, the DDM is designed as follows:
where
,
,
and
are suitable positive demand parameters to be selected later, and
is obtained by solving LMI (
7). Besides, when the DDM (
9) is met, an acknowledgment (ACK) signal is required to affirm that the transmission attempt was successful, and this assumption is consistent with the TCP-type communication protocol.
Define
as the sequence performing data transmission of control update, and denote
by the data transmission interval between two consecutive attempts, which
where
and
are upper and lower bounds of the intervals between two consecutive attempts, respectively.
Remark 1. The length of interval is decided by the DDM (9), but it is necessary to set the lower and upper bound. Due to the characteristic of periodic verification strategy, the lower bound can be selected as the DDM verification period. Inspired by the pre-specified upper bound of inter-event times in [
17]
, the upper bound is needed to force the sensor to send data to the remote controller if the transmission is not executed for long periods of time. The sensor system transmits the latest estimation value
to the controller system by network communication to renew the state prediction
at
—that is,
, and it is the initial value for the state prediction when
. Then,
is calculated by (
8) and the control value is able to be designed by the switching controller formulated as
where
K is the state feedback gain matrix. In order to improve the rate of convergence, region poles assignment lemma [
23] is used to solve
K with
stability margin. Let
; then,
K can be obtained by solving the following LMI:
where
is a given coefficient and
is a symmetric positive definite matrix.
As in
Figure 2, a replica of the predictor
is run in the sensor system so that it can synchronize
that the controller system has and can judge whether (
9) is satisfied. When the DDM (
9) is not satisfied,
is not sent and the error between
and
is accumulated until (
9) is satisfied; then,
is transmitted to the predictor
, and an ACK signal is sent and returned to the sensor from the controller system by the network to ascertain that the transmission attempt was triumphant.
3. Demand-Driven Control Strategy
This section gives the design process of the demand-driven control strategy—that is, the selection method of driven parameters under the premise of ensuring the control objective. First of all, the control objective is described as the definition provided below:
Definition 1 ([
24]).
Given the GU system (3) with control input (11), for each and , if there is a -function and a -function such thatholds for all with , the system is considered to be ISS. Besides, the system (3) is globally asymptotically stable if (13) is satisfied for . Then, the design process of the demand-driven parameters is given. For
, to measure the difference between the truth state
and the state prediction
, which represents the demand of network communication, denote the prediction error by
Then, the formula for the closed-loop GU system is given as
Design the Lyapunov function as
, where
P is the unique solution of the following Lyapunov equation:
where
Q is any given positive definite symmetric matrix. Then, we have
for any
, where
and
are equal to the smallest and largest eigenvalues of
P, respectively.
is the smallest eigenvalue of
Q;
and
. Notice that
is always true when
; then, it yields
where the inequality comes from the triangle inequality and the fact that
. Then,
yields
where
. Then,
can be obtained by substituting (
20) into (
18) and indicates that when
holds,
where
,
, and
.
The use of the prediction method makes the controller system able to simulate the true state value; then, the discrepancy accumulated in the transmission interval is degraded by the information compensation. From (
14), it yields for any
that the dynamic of the prediction error can be formulated as
then, we have the upper bound of the error as
where
and
.
Because the DDM (
9) is periodically validated in the case of a continuous system process, it is necessary to investigate the transmission attempt sequence
to eliminate continuous transmissions within each validation period. Denote the estimation–prediction error by
; then, the dynamic of this error is
where
. Since
for any
, it yields
where
as in (
9); further, it yields that if
with
then for any
, the DDM (
9) cannot be satisfied if
.
Remark 2. Notice that the threshold part of the mechanism is divided into two items. One influences the stability of the system and is determined by the parameter . If the selected parameter is large, the demand error will be too large compared to the updated data , and the updated data may not stabilize the system. The other parameter is , which determines the influence of the disturbance and noise to the DDM. The selection of directly determines the minimum transmission interval , and can be chosen based on the quantitative relationship (25). 5. Simulation Examples
In this section, the GU model constructed in
Section 2.1 is applied to validate the resilient control performance of the designed methods. The parameters of the GU system are shown as follows:
,
,
,
,
,
,
,
. The system matrices of the GU model can be calculated as follows:
In the simulation, the unknown disturbance
is assumed as stochastic signals with a uniform distribution in
and noise
is
, where
a is a stochastic number with a uniform distribution bounded in
. The initial conditions are
. The control objective is to track the reference signal
. Selecting
, the gain matrices of observer and controller can be calculated by solving the LMIs (
7) and (
12) as follows:
The relative parameters can be obtained such that
,
,
,
,
, and
. Thus
has to be chosen such that
. Setting
, and
and
s, the demand-driven parameter
is chosen as
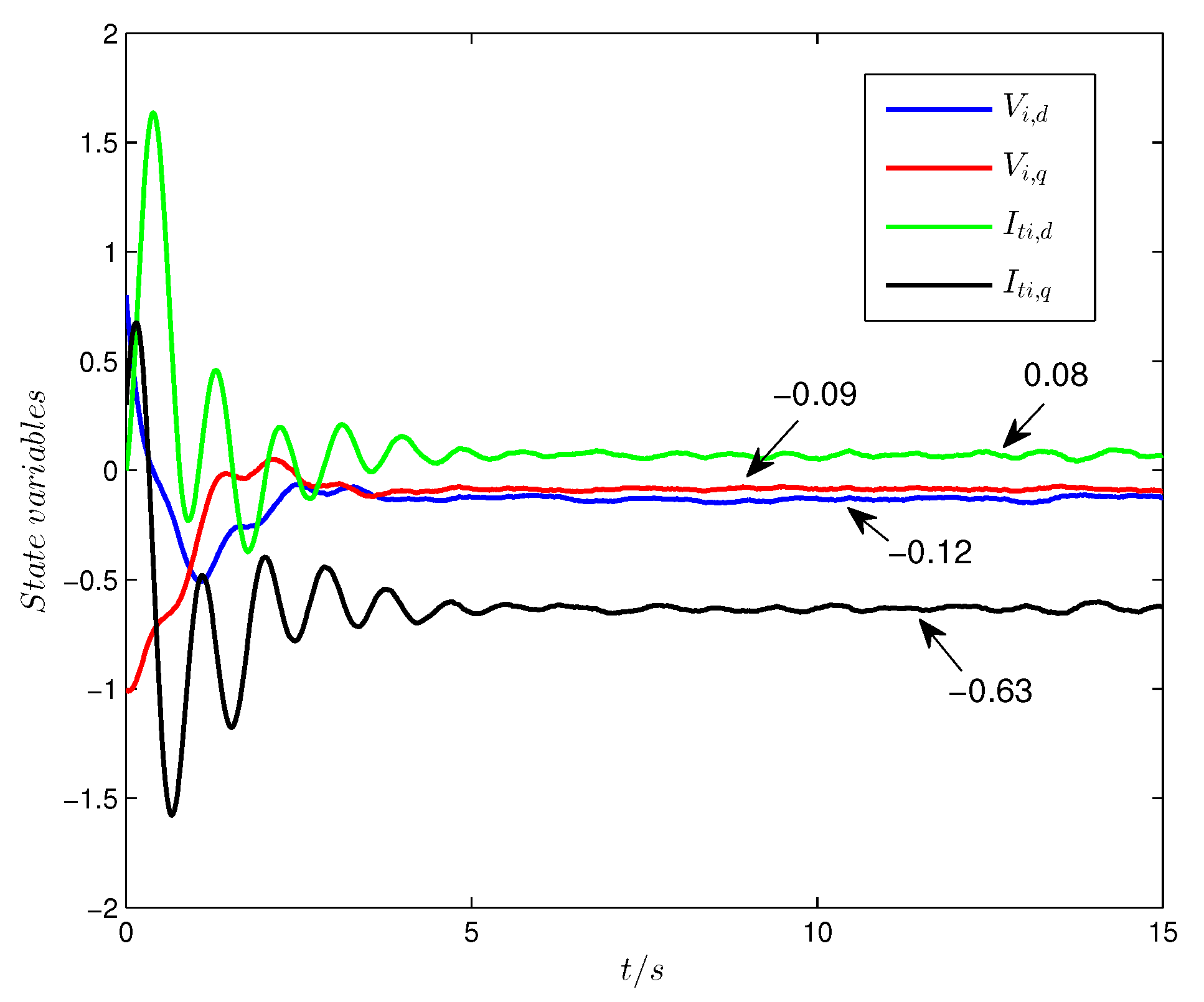
. When there are no DoS attacks, the state responses of the controlled system, the evolution of the transmission times, and the demand-driven conditions
and
are exhibited in
Figure 3 and
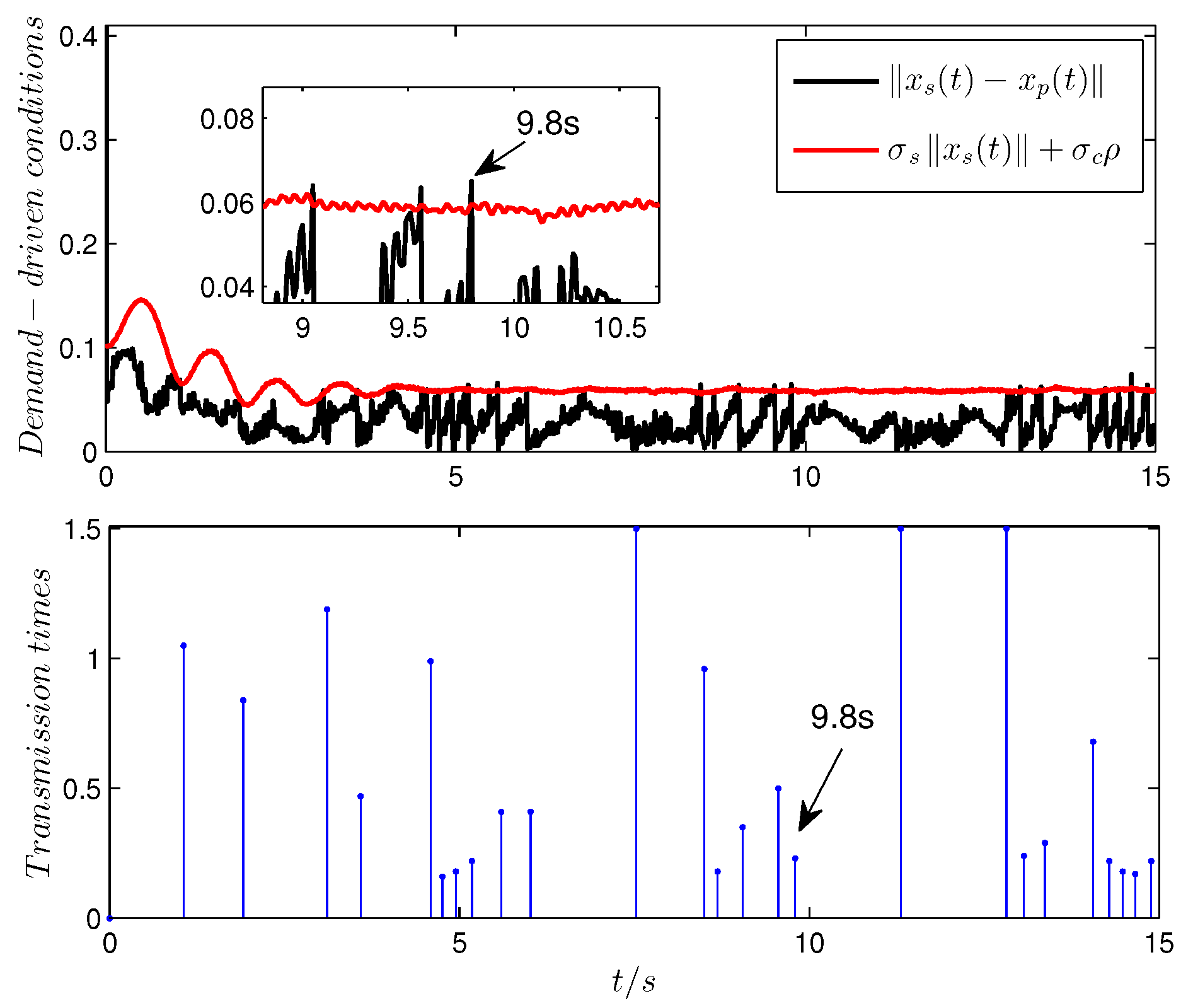
Figure 4, respectively. From the above figures, it is obvious that the demand-driven control algorithm is able to ensure that the state responses of the GU system track the reference values while the number of network transmissions is decreased significantly. From
Figure 4, when the demand (black) exceeds the transmission condition (red), the data are transmitted over the network (such as at 9.8 s). The black line quantifies the information difference between the controller side and the sensor side, which represent the control requirements in real application scenarios. The red line quantifies the acceptable demand threshold. If the information difference does not exceed the threshold, it indicates that the impact of the difference on system performance during actual application is tolerable, and no data transmission is required.
When DoS attacks occur, the transmission protocol is provided in (
31), and the transmission attempt period is
s. In the simulation time domain of 15 s, the DoS attack is executed randomly and satisfies
and
s. According to the duration and frequency of the attack, we have
and
; then,
. Then, the state responses of the closed-loop GU system, the evolution of the transmission times, and the demand-driven condition
and
are exhibited in
Figure 5,
Figure 6 and
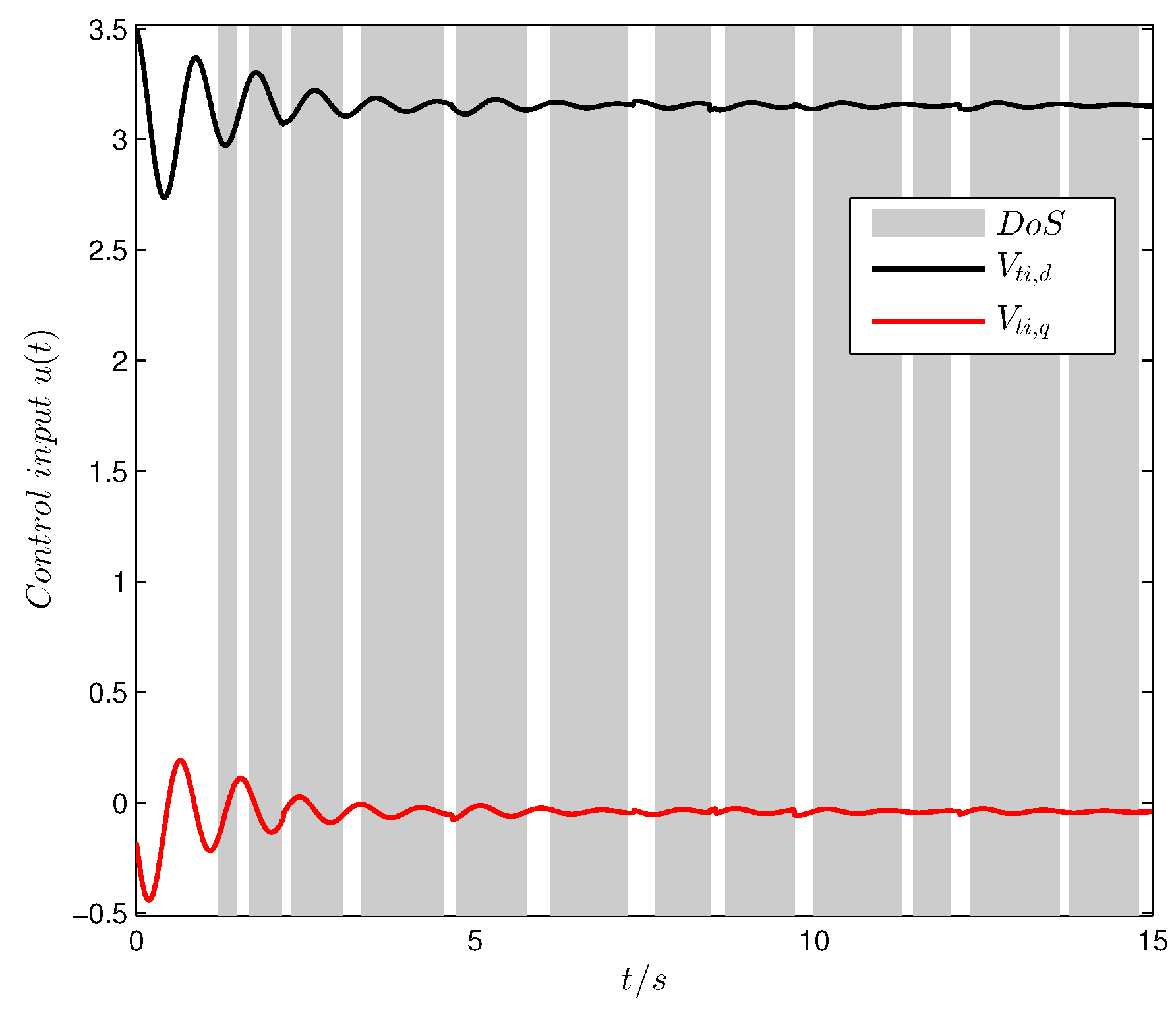
Figure 7, respectively. Finally, the control input of the GU model is given in
Figure 8.
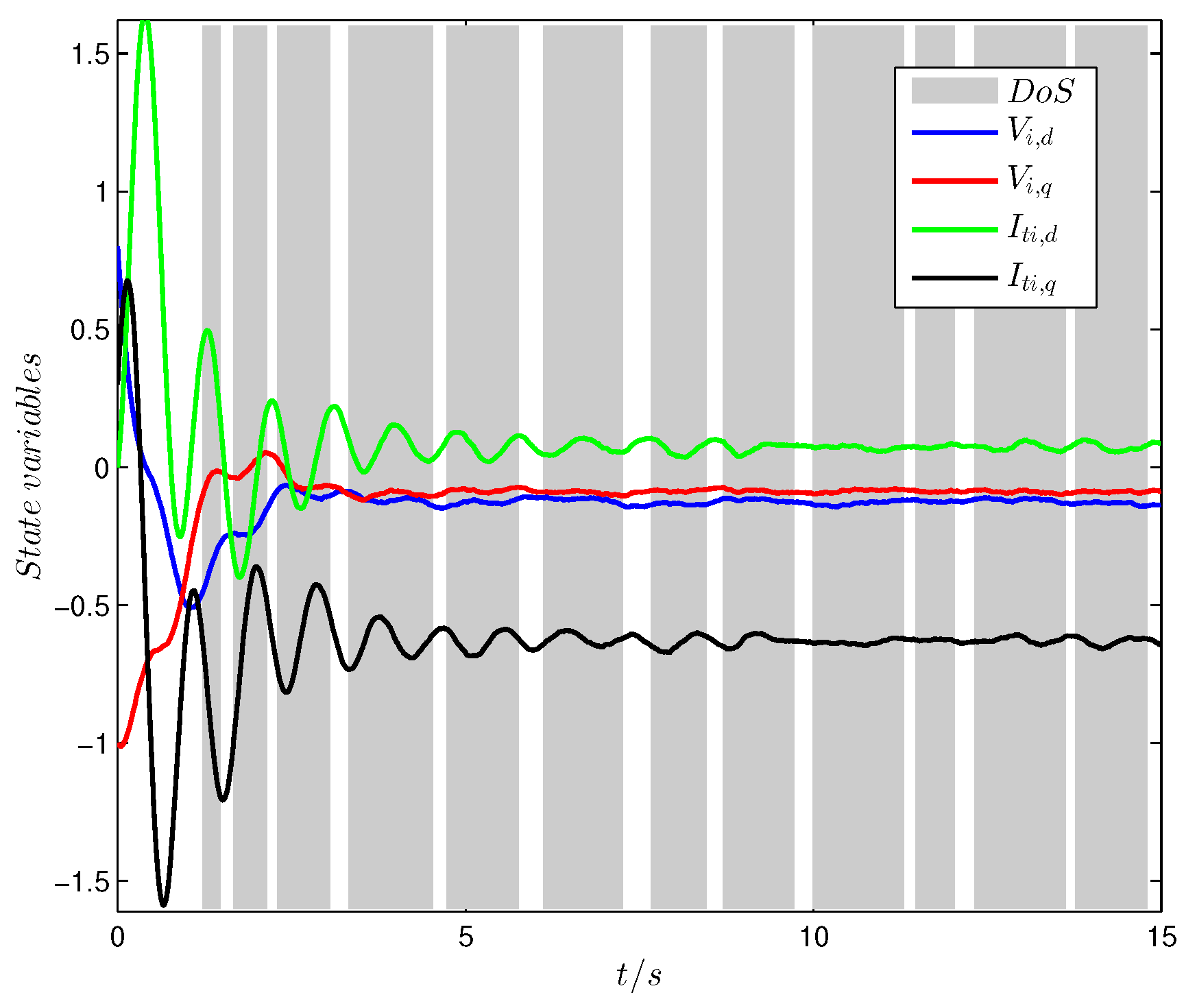
From
Figure 5, it can be observed that the states of the GU model can also track the reference values under DoS attacks. However, compared with
Figure 3 and
Figure 5, it is shown that the time it takes for the wave of states under DoS attacks to end is significantly longer than that without DoS attacks, which indicates the influence of the DoS attacks to the networked control strategy. As can be observed from
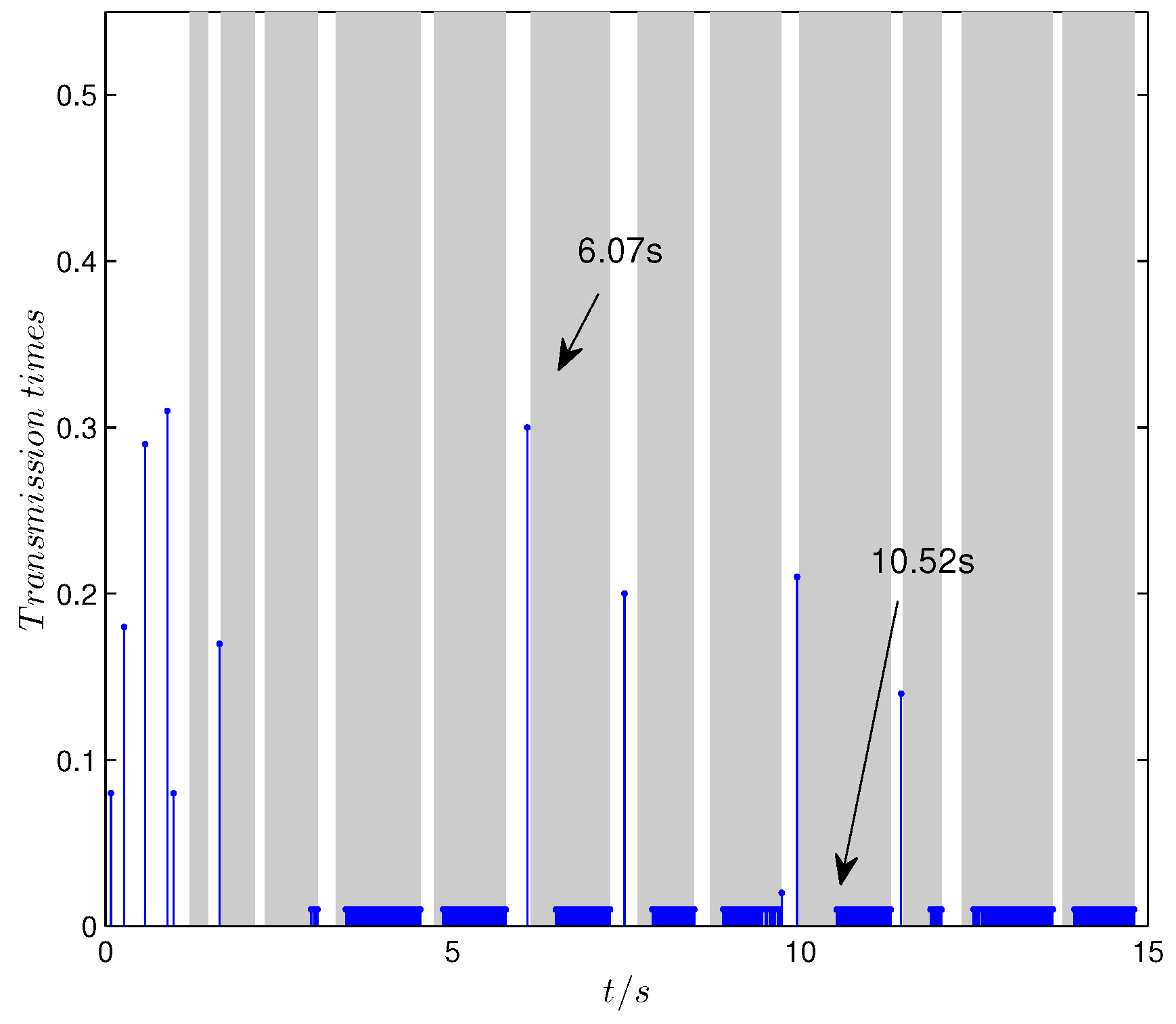
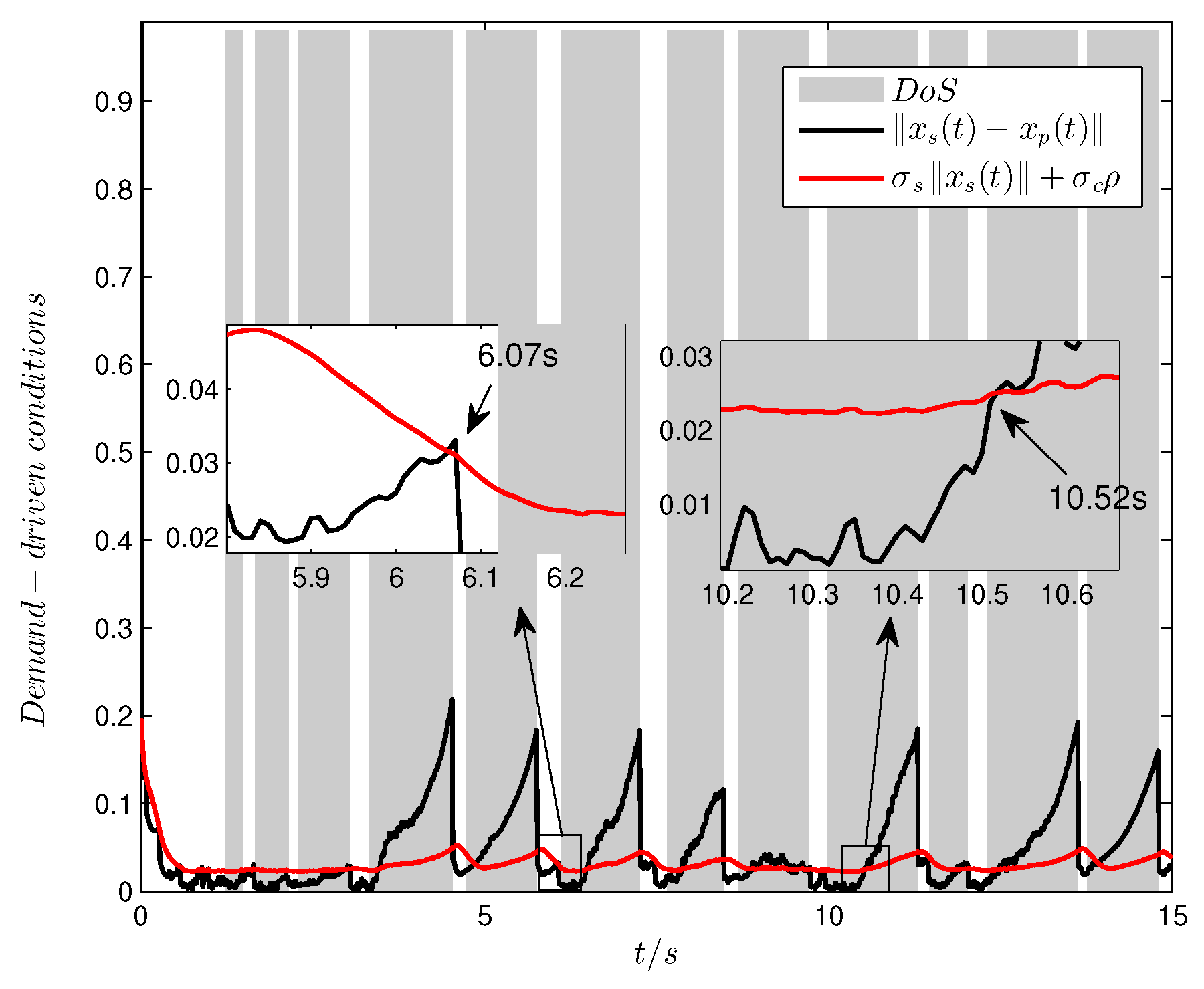
Figure 6 and
Figure 7, the demand-driven algorithm still works, and the transmission attempts succeed during the no-attack intervals when the demand exceeds the transmission condition (such as at 6.07 s) while the transmission mode switches to periodic attempts during the attack intervals (such as 10.52 s). As can be seen from the above figures, the demand-driven control scheme also has a certain potential resilience in practical applications. For instance, from
Figure 7, it can be seen that the DoS attacks before the demand (black) exceeds the threshold (red) are invalid. In these intervals, there is no transmission attempt, which can be observed in
Figure 6 before 10.52 s.
6. Conclusions
This paper focuses on the secure control problem for the GU of a local power plant under unreliable communication, and the demand-driven control strategy has been investigated. The unreliable communication in consideration is caused by DoS attacks, and the resilient control algorithm is designed to handle the problem of performance degradation in this scenario. An observer-based prediction method is provided, and the DDM is designed based on the error between the state estimation and prediction. In this way, the communication resources are saved while the ideal scheduling control performance is obtained. Based on the ISS analysis, the sufficient conditions on the DoS attack model are provided to ensure the stability of the GU system. Finally, simulation results were presented to demonstrate the effectiveness of the designed methods.
The technical novelties are summed up as follows: First, the observer-based prediction method is able to remove the influence of unknown load currents to the system and compensate the loss of state data in the interval between any two continuous transmissions of scheduling signals. Second, the advanced demand-driven strategy with periodic verification is presented to schedule the intermittent communication. Third, by using the thought of robustness to the maximum disturbance-induced error, the conservatism of the tolerable attack intensity is decreased.