Cybersecurity Issues in Electrical Protection Relays: A Systematic Review
Abstract
1. Introduction
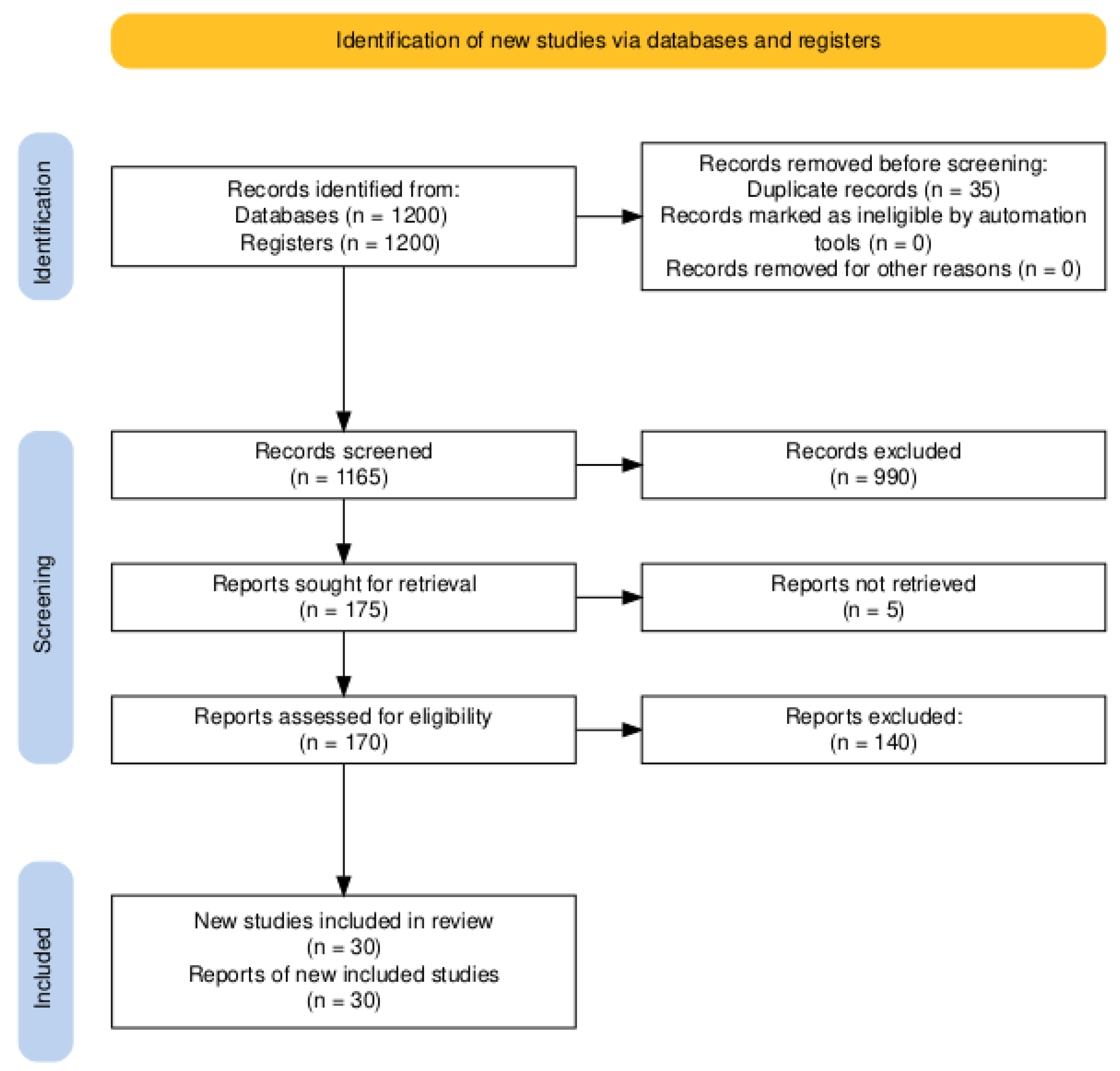
2. Methodology
- Publication Indexing: Only papers indexed in Scopus were considered to ensure quality and credibility.
- Publication Date: Articles published within the last 10 years (2014–2024) were included to focus on recent advancements and emerging trends.
- Relevance: The papers had to explicitly address topics related to digital electrical protection relays and their cybersecurity aspects.
3. Vulnerabilities in Electrical Protections
| Citation | Title | Year | Type |
|---|---|---|---|
| [10] | Evexchange: A relay attack on electric vehicle charging system | 2022 | Conference |
| [11] | Cyber attacks on protective relays in digital substations and impact analysis | 2020 | Conference |
| [13] | Cyber security issues for protective relays; c1 working group members of power system relaying committee | 2007 | Conference |
| [14] | Cyber attacks on remote relays in smart grid | 2017 | Conference |
| [15] | Cyber security—Securing the protection and control relay communication in substation | 2018 | Conference |
| [16] | Cybersecurity issues in communication-based electrical protections | 2022 | Conference |
| [17] | Impacts of Cyber Attack on Performance of Current-Based Relays in Transmission Lines | 2024 | Conference |
| [18] | Indirect Cyber-Physical Attack with Combined Circuit Breaker and Excitation System | 2023 | Conference |
| [19] | Modelling and analysing security threats targeting protective relayoperations in digital substations | 2023 | Conference |
| [20] | Performance of Distance Relay Against Cyber Attack in Transmission Lines | 2024 | Conference |
| [21] | Power system risk assessment in cyber attacks considering the role of protection systems | 2016 | Journal |
| [22] | Cybersecurity for Distance Relay Protection | 2020 | Technical Report |
3.1. Attacks on Electrical Protection Relays
- Relay Attacks: Relay attacks can be used to indirectly trip a relay by sending a trip request from a compromised primary relay to a backup relay and confirming the request with another compromised peer relay [14]. An attacker can also cause a cascading failure by tripping a set of relays [16]. Attackers can compromise a primary relay of a line and then directly trip the line. Attackers can manipulate the measured impedance of current transformers and/or voltage transformers, causing it to fall within the relay’s zone setting and triggering a trip command [20]. Attackers can modify relay settings such as threshold values, which can cause the relay to either fail to detect a fault or to trip unnecessarily due to a load increase [17]. Attackers can modify the zone setting values of relays, which may cause the relay to fail to detect a fault or to incorrectly interpret an increase in system load as a fault
- Cyber Attacks via Network Communication: Man-in-the-middle attacks can be used to exploit vulnerabilities in the IEC 61850 standard, injecting spoofed GOOSE data frames into the substation communication network. Cyber attacks can manipulate GOOSE data in digital substations [11]. Attackers can gain access to the substation network by targeting the corporate information technology of the control center, stealing credentials of corporate user accounts with remote accessibility rights [19]. Denial-of-Service attacks can disrupt the communication between relays, causing them to trigger actions such as opening circuit breakers. False Data Injection Attacks involve injecting fabricated measurements or data into the relay system to cause false tripping or misoperation. Attackers can send false trip confirmations to relays, manipulating trust mechanisms. Attackers can replay measurements from previous fault conditions to the relay system or modify or drop response packets sent to a target relay, which could result in the attacker’s compromised relays being seen as trusted
- Physical Attacks: Physical access to equipment, such as instrument transformers, allows the adjustment of tap settings, which results in incorrectly scaled measurements. Physical access to substations and relays provides the opportunity for attackers to practice on real equipment.
3.2. Potential Impacts on the Power System
- False Tripping: Cyber attacks can cause the false tripping of circuit breakers, leading to unnecessary disconnections of transmission lines or equipment. This can be achieved, for example, by manipulating current measurements and causing the measured impedance to fall within the relay’s zone. False tripping of multiple relays may result in cascading failures and widespread outages.
- Missed Tripping: Cyber attacks can cause relays to fail to trip during actual fault conditions, which can result in damage to equipment or cause the fault to spread.
- Cascading Failures and Blackouts: Coordinated attacks on multiple relays can lead to cascading failures and widespread blackouts. Cascading failures can be triggered when a set of relays is compromised. Attackers may target specific sets of lines that can trigger cascading failures.
- Equipment Damage: Cyber attacks can result in equipment damage due to the failure of the protection system to operate properly during abnormal conditions. Failure to open a circuit breaker during a fault can cause significant damage to substation equipment.
- System Instability and Inefficiency: The manipulation of control set points in relays can lead to instability in the power systems. Compromised relays and their communication can disrupt normal power system operations, leading to instability. Attacks can lead to increased oscillations and the probable tripping of generators
4. Countermeasures
5. Research Gaps and Future Directions
- Limited Threat Analysis Specific to Protection Relays: most cybersecurity studies focus on general industrial control systems without tailored threat modeling for electrical protection relays. This leads to gaps in understanding relay-specific vulnerabilities such as firmware manipulation, protocol exploitation, and timing attacks. At the same time, there is a lack of standardized testing frameworks. There is no universal or widely accepted framework for testing the cybersecurity of protection relays under realistic attack scenarios. Existing testing approaches often fail to simulate diverse adversarial tactics.
- Underexplored Attack Scenarios on Relay Coordination: Research rarely addresses how coordinated cyber attacks can disrupt relay coordination, leading to cascading failures or delayed fault clearing in interconnected power grids.
- Inadequate Real-Time Detection Mechanisms: Current Intrusion Detection Systems for protection relays struggle with real-time anomaly detection due to resource limitations and the need for ultra-fast fault clearing in power systems.
- Vulnerabilities in Legacy Systems and Insufficient Integration of Cybersecurity with Relay Functions: Cybersecurity measures are often treated as an add-on rather than being integrated into the design and functionality of protection relays. This compromises the reliability and speed required for grid protection. Many power systems still rely on legacy relays with limited or no built-in cybersecurity features. The risks posed by these outdated systems are understudied.
Future Research Directions
- Open-source resources: The availability of public datasets would significantly improve the development of solutions for cybersecurity in protection relays. Currently, the lack of openly accessible, high-quality datasets tailored to electrical protection systems is a major bottleneck in advancing research and development in this field [42,43]. Public datasets containing examples of normal operations and cyber attack scenarios (e.g., relay spoofing, denial-of-service attacks, GOOSE message manipulation) allow for more precise threat modeling tailored to protection relays. Public datasets that include both cyber (e.g., network traffic logs) and physical (e.g., relay trip times, power flows) data enable research on the interplay between cyber attacks and physical grid impacts.
- Resilient control algorithms: Resilient control strategies are an essential aspect of improving the cybersecurity of protection relays, especially in scenarios where intrusion detection systems are impractical due to time constraints or resource limitations. These methods focus on ensuring that the system continues to function effectively, even when facing cyber attacks or operational disruptions. For protection relays, this means maintaining their ability to detect and isolate faults while minimizing the impact of compromised components or malicious activities. One key principle of resilient control is ensuring that critical functions can operate in a “graceful degradation” mode. If a relay or its communication network is attacked, the system should remain operational in a reduced but stable state, avoiding total failure. For instance, if a relay’s communication is disrupted, it can revert to local, hardcoded protection mechanisms. Similarly, resilient control emphasizes fault tolerance by incorporating redundancy and algorithms that can detect and compensate for abnormal behavior caused by attacks. For example, relays can verify decisions against neighboring devices to identify potential inconsistencies or malicious actions. Another important feature is self-healing, which refers to automatic recovery mechanisms that mitigate the impact of cyber attacks. If spoofed or manipulated messages compromise relay communication, self-healing techniques can include resetting the communication channel or reauthenticating connections. Decentralized decision-making also plays a critical role. In cases where central control systems are affected, individual relays can make decisions autonomously based on local measurements, maintaining protection operations even without external instructions.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| GOOSE | Generic Object-Oriented Substation Event |
| SV | Sampled Values |
| V2G | Vehicle to grid |
| IED | Intelligent Electronic Device |
| PMU | Phasor Measurement Unit |
| WAMS | Wide Area Measurement System |
References
- Velini, A.; Minetti, M.; Bruno, S.; Bonfiglio, A.; Procopio, R.; La Scala, M. Renewable energy communities virtual islanding: A decentralized service to improve distribution grid security. Sustain. Energy Grids Netw. 2025, 42, 101700. [Google Scholar] [CrossRef]
- Minetti, M.; Fresia, M. A Review of Primary and Secondary Control for Islanded No-Inertia Microgrids. In Proceedings of the 2021 IEEE International Conference on Environment and Electrical Engineering and 2021 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe), Bari, Italy, 7–10 September 2021; pp. 1–7. [Google Scholar]
- Gaggero, G.; Piserà, D.; Girdinio, P.; Silvestro, F.; Marchese, M. From Microgrids to Virtual Power Plants: A Cybersecurity Perspective. In IoT Enabled-DC Microgrids; CRC Press: Boca Raton, FL, USA, 2024; pp. 103–120. [Google Scholar]
- Bonfiglio, A.; La Fata, A.; Minetti, M. A pattern recognition based tool for smart distribution networks reconfiguration. Electr. Power Syst. Res. 2025, 248, 111890. [Google Scholar] [CrossRef]
- Armellin, A.; Gaggero, G.B.; Cattelino, A.; Piana, L.; Raggi, S.; Marchese, M. Integrating OT data in SIEM platforms: An Energy Utility Perspective. In Proceedings of the 2023 International Conference on Electrical, Communication and Computer Engineering (ICECCE), Dubai, United Arab Emirates, 30–31 December 2023; pp. 1–7. [Google Scholar]
- Vaidya, B.; Makrakis, D.; Mouftah, H.T. Authentication and authorization mechanisms for substation automation in smart grid network. IEEE Netw. 2013, 27, 5–11. [Google Scholar] [CrossRef]
- Langer, L.; Skopik, F.; Smith, P.; Kammerstetter, M. From old to new: Assessing cybersecurity risks for an evolving smart grid. Comput. Secur. 2016, 62, 165–176. [Google Scholar] [CrossRef]
- Reda, H.T.; Ray, B.; Peidaee, P.; Anwar, A.; Mahmood, A.; Kalam, A.; Islam, N. Vulnerability and impact analysis of the IEC 61850 GOOSE protocol in the smart grid. Sensors 2021, 21, 1554. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]
- Conti, M.; Donadel, D.; Poovendran, R.; Turrin, F. Evexchange: A relay attack on electric vehicle charging system. In Proceedings of the European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2022; pp. 488–508. [Google Scholar]
- Rajkumar, V.S.; Tealane, M.; Ştefanov, A.; Palensky, P. Cyber attacks on protective relays in digital substations and impact analysis. In Proceedings of the 2020 8th IEEE Workshop on Modeling and Simulation of Cyber-Physical Energy Systems, Sydney, Australia, 21 April 2020; pp. 1–6. [Google Scholar]
- IEC 61850:2025; Series—Communication Networks and Systems for Power Utility Automation. International Electrotechnical Commission: Geneva, Switzerland, 2025.
- Ward, S.; O’Brien, J.; Beresh, B.; Benmouyal, G.; Holstein, D.; Tengdin, J.T.; Fodero, K.; Simon, M.; Carden, M.; Yalla, M.V.; et al. Cyber security issues for protective relays; c1 working group members of power system relaying committee. In Proceedings of the 2007 IEEE Power Engineering Society General Meeting, Tampa, FL, USA, 24–28 June 2007; pp. 1–8. [Google Scholar]
- Zhang, J.; Dong, Y. Cyber attacks on remote relays in smart grid. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; pp. 1–9. [Google Scholar]
- Sukumara, T.; Starck, J.; Vellore, J.; Kumar, E.; Harish, G. Cyber security—Securing the protection and control relay communication in substation. In Proceedings of the 2018 IEEE 71st Annual Conference for Protective Relay Engineers (CPRE), College Station, TX, USA, 26–29 March 2018; pp. 1–7. [Google Scholar]
- Gaggero, G.B.; Rossi, M.; Girdinio, P.; Marchese, M. Cybersecurity issues in communication-based electrical protections. In Proceedings of the 2022 IEEE International Conference on Electrical, Computer and Energy Technologies (ICECET), Prague, Czech Republic, 20–22 July 2022; pp. 1–6. [Google Scholar]
- Gupta, N.K.; Gangolu, S.; Kumar, H. Impacts of Cyber Attack on Performance of Current-Based Relays in Transmission Lines. In Proceedings of the 2024 IEEE International Conference on Computer, Electronics, Electrical Engineering & Their Applications (IC2E3), Srinagar Garhwal, India, 6–7 June 2024; pp. 1–6. [Google Scholar]
- Yadav, S.; Kishor, N.; Purwar, S.; Chakrabarti, S. Indirect Cyber-Physical Attack with Combined Circuit Breaker and Excitation System. In Proceedings of the IEEE EUROCON 2023—20th International Conference on Smart Technologies, Torino, Italy, 6–8 July 2023; pp. 204–209. [Google Scholar]
- Elrawy, M.F.; Hadjidemetriou, L.; Laoudias, C.; Michael, M.K. Modelling and analysing security threats targeting protective relay operations in digital substations. In Proceedings of the 2023 IEEE International Conference on Cyber Security and Resilience (CSR), Venice, Italy, 31 July–2 August 2023; pp. 523–529. [Google Scholar]
- Gupta, N.K.; Gangolu, S. Performance of Distance Relay Against Cyber Attack in Transmission Lines. In Proceedings of the 2024 IEEE 4th International Conference on Sustainable Energy and Future Electric Transportation (SEFET), Hyderabad, India, 31 July–3 August 2024; pp. 1–6. [Google Scholar]
- Liu, X.; Shahidehpour, M.; Li, Z.; Liu, X.; Cao, Y.; Li, Z. Power system risk assessment in cyber attacks considering the role of protection systems. IEEE Trans. Smart Grid 2016, 8, 572–580. [Google Scholar] [CrossRef]
- McDermott, T.E.; Doty, J.D.; O’Brien, J.G.; Eppinger, C.R.; Becejac, T. Cybersecurity for Distance Relay Protection; Technical Report; Pacific Northwest National Lab. (PNNL): Richland, WA, USA, 2020.
- Narang, J.K.; Bag, B. Deep learning-based integrated attack detection framework to protect distance relays against cyberattacks. Electr. Power Syst. Res. 2024, 231, 110346. [Google Scholar] [CrossRef]
- Gupta, K.; Mohanty, R.; Sahoo, S.; Panigrahi, B.K. Cyber intrusion detection for line current differential relays in DC distribution system. Sustain. Energy Grids Netw. 2023, 34, 101065. [Google Scholar] [CrossRef]
- Khaw, Y.M.; Jahromi, A.A.; Arani, M.F.; Sanner, S.; Kundur, D.; Kassouf, M. A deep learning-based cyberattack detection system for transmission protective relays. IEEE Trans. Smart Grid 2020, 12, 2554–2565. [Google Scholar] [CrossRef]
- Ameli, A.; Ayad, A.; El-Saadany, E.F.; Salama, M.M.; Youssef, A. A learning-based framework for detecting cyber-attacks against line current differential relays. IEEE Trans. Power Deliv. 2020, 36, 2274–2286. [Google Scholar] [CrossRef]
- Suman, A.A.; Sarangi, S. A Novel Approach for Cyber Attack Detection and Mitigation in Differential Relays Using WAMs Data. In Proceedings of the 2024 IEEE 4th International Conference on Sustainable Energy and Future Electric Transportation (SEFET), Hyderabad, India, 31 July–3 August 2024; pp. 1–6. [Google Scholar]
- Tripathi, A.M.; Yadav, R.; Pradhan, A.K. A Novel Approach for Enhancing Cyber Resiliency in Distance Relay using PCA and Random Forest. In Proceedings of the 2024 IEEE 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kamand, India, 24–28 June 2024; pp. 1–5. [Google Scholar]
- Ameli, A.; Hooshyar, A.; El-Saadany, E.F.; Youssef, A.M. An intrusion detection method for line current differential relays. IEEE Trans. Inf. Forensics Secur. 2019, 15, 329–344. [Google Scholar] [CrossRef]
- Ameli, A.; Saleh, K.A.; Kirakosyan, A.; El-Saadany, E.F.; Salama, M.M. An intrusion detection method for line current differential relays in medium-voltage DC microgrids. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3580–3594. [Google Scholar] [CrossRef]
- Sheng, S.; Chan, W.L.; Li, K.; Xianzhong, D.; Xiangjun, Z. Context information-based cyber security defense of protection system. IEEE Trans. Power Deliv. 2007, 22, 1477–1481. [Google Scholar] [CrossRef]
- Hong, J.; Nuqui, R.F.; Kondabathini, A.; Ishchenko, D.; Martin, A. Cyber attack resilient distance protection and circuit breaker control for digital substations. IEEE Trans. Ind. Inform. 2018, 15, 4332–4341. [Google Scholar] [CrossRef]
- Pola, S.; Jovanovic, M.; Azzouz, M.A.; Mirhassani, M. Cyber resiliency enhancement of overcurrent relays in distribution systems. IEEE Trans. Smart Grid 2023, 15, 4063–4076. [Google Scholar] [CrossRef]
- Jahromi, M.Z.; Jahromi, A.A.; Sanner, S.; Kundur, D.; Kassouf, M. Cybersecurity enhancement of transformer differential protection using machine learning. In Proceedings of the 2020 IEEE Power & Energy Society General Meeting (PESGM), Montreal, QC, Canada, 2–6 August 2020; pp. 1–5. [Google Scholar]
- Rrushi, J.L. Defending electrical substations against 0-day malware through decoy I/O in protective relays. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 486–493. [Google Scholar]
- Ameli, A.; Hooshyar, A.; El-Saadany, E.F. Development of a cyber-resilient line current differential relay. IEEE Trans. Ind. Inform. 2018, 15, 305–318. [Google Scholar] [CrossRef]
- Yousefi kia, M.; Saniei, M.; Seifossadat, S.G. A novel cyber-attack modelling and detection in overcurrent protection relays based on wavelet signature analysis. IET Gener. Transm. Distrib. 2023, 17, 1585–1600. [Google Scholar] [CrossRef]
- Rajaee, M.; Mazlumi, K. Multi-agent distributed deep learning algorithm to detect cyber-attacks in distance relays. IEEE Access 2023, 11, 10842–10849. [Google Scholar] [CrossRef]
- Khaw, Y.M.; Jahromi, A.A.; FM, A.M.; Kundur, D.; Sanner, S.; Kassouf, M. Preventing false tripping cyberattacks against distance relays: A deep learning approach. In Proceedings of the 2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Beijing, China, 21–23 October 2019; pp. 1–6. [Google Scholar]
- Kulikov, A.; Loskutov, A.; Bezdushniy, D. Relay protection and automation algorithms of electrical networks based on simulation and machine learning methods. Energies 2022, 15, 6525. [Google Scholar] [CrossRef]
- Gaggero, G.B.; Girdinio, P.; Marchese, M. Artificial Intelligence and Physics-Based Anomaly Detection in the Smart Grid: A Survey. IEEE Access 2025, 13, 23597–23606. [Google Scholar] [CrossRef]
- Gaggero, G.B.; Armellin, A.; Portomauro, G.; Marchese, M. Industrial control system-anomaly detection dataset (ICS-ADD) for cyber-physical security monitoring in smart industry environments. IEEE Access 2024, 12, 64140–64149. [Google Scholar] [CrossRef]
- Faramondi, L.; Flammini, F.; Guarino, S.; Setola, R. A hardware-in-the-loop water distribution testbed dataset for cyber-physical security testing. IEEE Access 2021, 9, 122385–122396. [Google Scholar] [CrossRef]
- IEC 62443-2-1:2024; Security for Industrial Automation and Control Systems: Part 2-1: Security Program Requirements for IACS Asset Owners. International Electrotechnical Commission: Geneva, Switzerland, 2024.
- IEEE Std 1686™-2022; Standard for Intelligent Electronic Devices Cyber Security Capabilities. Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2022.
| Citation | Title | Year | Type |
|---|---|---|---|
| [23] | Deep learning-based integrated attack detection framework to protect distance relays against cyberattacks | 2024 | Journal |
| [24] | Cyber intrusion detection for line current differential relays in DC distribution system | 2023 | Journal |
| [25] | A deep learning-based cyberattack detection system for transmission protective relays | 2020 | Journal |
| [26] | A learning-based framework for detecting cyber-attacks against line current differential relays | 2020 | Journal |
| [27] | A Novel Approach for Cyber Attack Detection and Mitigation in Differential Relays Using WAMs Data | 2024 | Conference |
| [28] | A Novel Approach for Enhancing Cyber Resiliency in Distance Relay using PCA and Random Forest | 2024 | Conference |
| [29] | An intrusion detection method for line current differential relays | 2019 | Journal |
| [30] | An intrusion detection method for line current differential relays in medium-voltage DC microgrids | 2020 | Journal |
| [31] | Context information-based cyber security defense of protection system | 2007 | Journal |
| [32] | Cyber attack resilient distance protection and circuit breaker control for digital substations | 2018 | Journal |
| [33] | Cyber resiliency enhancement of overcurrent relays in distribution systems | 2023 | Journal |
| [34] | Cybersecurity enhancement of transformer differential protection using machine learning | 2020 | Conference |
| [35] | Defending electrical substations against 0-day malware through decoy I/O in protective relays | 2017 | Conference |
| [36] | Development of a cyber-resilient line current differential relay | 2018 | Journal |
| [37] | A novel cyber-attack modelling and detection in overcurrent protection relays based on wavelet signature analysis | 2023 | Journal |
| [38] | Multi-agent distributed deep learning algorithm to detect cyber-attacks in distance relays | 2023 | Journal |
| [39] | Preventing false tripping cyberattacks against distance relays: A deep learning approach | 2019 | Conference |
| [40] | Relay protection and automation algorithms of electrical networks based on simulation and machine learning methods | 2022 | Journal |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gaggero, G.B.; Girdinio, P.; Marchese, M. Cybersecurity Issues in Electrical Protection Relays: A Systematic Review. Energies 2025, 18, 3796. https://doi.org/10.3390/en18143796
Gaggero GB, Girdinio P, Marchese M. Cybersecurity Issues in Electrical Protection Relays: A Systematic Review. Energies. 2025; 18(14):3796. https://doi.org/10.3390/en18143796
Chicago/Turabian StyleGaggero, Giovanni Battista, Paola Girdinio, and Mario Marchese. 2025. "Cybersecurity Issues in Electrical Protection Relays: A Systematic Review" Energies 18, no. 14: 3796. https://doi.org/10.3390/en18143796
APA StyleGaggero, G. B., Girdinio, P., & Marchese, M. (2025). Cybersecurity Issues in Electrical Protection Relays: A Systematic Review. Energies, 18(14), 3796. https://doi.org/10.3390/en18143796








