Control Conditions for Equal Power Sharing in Multi-Area Power Systems for Resilience Against False Data Injection Attacks
Abstract
1. Introduction
- A resilient control strategy is proposed that detects potential cyber-attacks in a timely manner and isolates compromised areas (nodes) in a decentralized approach without disrupting normal MAPS operations. The resilience of this approach has been verified across numerous operational scenarios, such as load fluctuations and power sharing in the presence of FDI attacks.
- Time-varying FDI attacks on communication between different areas of MAPS are formulated and demonstrate their impact on MAPS operations. In the event of FDI attacks, the proposed control strategy effectively detects and isolates threats and swiftly restores optimal operational conditions, such as equal power sharing.
- A robust adaptive sliding mode observer is deployed to accurately assess the state of power in a CPS, such as a MAPS. Unlike traditional sliding mode observers, the proposed observer handles state errors robustly and automatically adjusts parameters to identify FDI attacks and load changes.
2. Preliminaries of Graphs
3. System Modeling
4. Attack Detection
4.1. ANN Observer
4.2. ANN Updated Law
4.3. Luenberger Observer (LO)
5. Equal Power-Sharing Condition Based on Consensus
5.1. Consensus Conditions with Communication Delay Caused by FDI Attack
5.2. Continuous Consensus Based on Sliding Mode Control
6. Design of Proposed Resilient Controller
Equal Power Sharing of Multi-Area Power System with Attack Observer
7. Simulations
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wen, S.; Yu, X.; Zeng, Z.; Wang, J. Event-triggering load frequency control for multiarea power systems with communication delays. IEEE Trans. Ind. Electron. 2015, 63, 1308–1317. [Google Scholar] [CrossRef]
- Wang, Z.; Liu, Y.; Yang, Z.; Yang, W. Load frequency control of multi-region interconnected power systems with wind power and electric vehicles based on sliding mode control. Energies 2021, 14, 2288. [Google Scholar] [CrossRef]
- Xu, K.; Niu, Y. Decentralized event-triggered sliding mode scheme for frequency regulation of multi-area power systems under deception attacks. Trans. Inst. Meas. Control 2023, 01423312231156237. [Google Scholar] [CrossRef]
- Yue, D.; Hu, S.; Cheng, Z.; Yue, D.; Hu, S.; Cheng, Z. Secure Distributed Optimal Frequency Regulation of Power Grid with Time-Varying Voltages Under False Data Injection Attacks. In Secure Control of Networked Control Systems and Its Applications; Springer: Singapore, 2021; pp. 251–270. [Google Scholar]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2016, 32, 3317–3318. [Google Scholar] [CrossRef]
- Zhao, P.; Gu, C.; Ding, Y.; Liu, H.; Bian, Y.; Li, S. Cyber-resilience enhancement and protection for uneconomic power dispatch under cyber-attacks. IEEE Trans. Power Deliv. 2020, 36, 2253–2263. [Google Scholar] [CrossRef]
- Ahmed, Z.; Saeed, M.A.; Jenabzadeh, A.; Xu, X.; Zhang, W. Frequency domain resilient consensus of multi-agent systems under IMP-based and non IMP-based attacks. Automatica 2022, 146, 110582. [Google Scholar] [CrossRef]
- Ahmed, Z.; Ali, N.; Zhang, W. H2 Resilient Consensus Control of Multiagent Systems Under Deception Attack. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 2530–2534. [Google Scholar] [CrossRef]
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C. False data injection cyber-attacks detection for multiple DC microgrid clusters. Appl. Energy 2022, 310, 118425. [Google Scholar] [CrossRef]
- Zhou, Q.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A. A cyber-attack resilient distributed control strategy in islanded microgrids. IEEE Trans. Smart Grid 2020, 11, 3690–3701. [Google Scholar] [CrossRef]
- He, H.; Yan, J. Cyber-physical attacks and defences in the smart grid: A survey. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 13–27. [Google Scholar] [CrossRef]
- Ranjbar, M.H.; Kheradmandi, M.; Pirayesh, A. Assigning operating reserves in power systems under imminent intelligent attack threat. IEEE Trans. Power Syst. 2019, 34, 2768–2777. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Attack detection and identification in cyber-physical systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef]
- Paridari, K.; O’Mahony, N.; Mady, A.E.D.; Chabukswar, R.; Boubekeur, M.; Sandberg, H. A framework for attack-resilient industrial control systems: Attack detection and controller reconfiguration. Proc. IEEE 2017, 106, 113–128. [Google Scholar] [CrossRef]
- Zhang, X.G.; Yang, G.H.; Ren, X.X. Network steganography based security framework for cyber-physical systems. Inf. Sci. 2022, 609, 963–983. [Google Scholar] [CrossRef]
- Rawat, D.B.; Bajracharya, C. Detection of false data injection attacks in smart grid communication systems. IEEE Signal Process. Lett. 2015, 22, 1652–1656. [Google Scholar] [CrossRef]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Ao, W.; Song, Y.; Wen, C. Adaptive cyber-physical system attack detection and reconstruction with application to power systems. IET Control Theory Appl. 2016, 10, 1458–1468. [Google Scholar] [CrossRef]
- Yan, Y.; Yu, S.; Yu, X. Euler’s discretization effect on a sliding-mode control system with supertwisting algorithm. IEEE Trans. Autom. Control 2020, 66, 2817–2824. [Google Scholar] [CrossRef]
- Zhou, Q.; Shahidehpour, M.; Yan, M.; Wu, X.; Alabdulwahab, A.; Abusorrah, A. Distributed secondary control for islanded microgrids with mobile emergency resources. IEEE Trans. Power Syst. 2019, 35, 1389–1399. [Google Scholar] [CrossRef]
- Zhou, Q.; Tian, Z.; Shahidehpour, M.; Liu, X.; Alabdulwahab, A.; Abusorrah, A. Optimal consensus-based distributed control strategy for coordinated operation of networked microgrids. IEEE Trans. Power Syst. 2019, 35, 2452–2462. [Google Scholar] [CrossRef]
- Beg, O.A.; Johnson, T.T.; Davoudi, A. Detection of false-data injection attacks in cyber-physical DC microgrids. IEEE Trans. Ind. Inform. 2017, 13, 2693–2703. [Google Scholar] [CrossRef]
- Jin, D.; Li, Z.; Hannon, C.; Chen, C.; Wang, J.; Shahidehpour, M.; Lee, C.W. Toward a cyber resilient and secure microgrid using software-defined networking. IEEE Trans. Smart Grid 2017, 8, 2494–2504. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, P.; Zhang, L.; Wang, B. Active synchronous detection of deception attacks in microgrid control systems. IEEE Trans. Smart Grid 2016, 8, 373–375. [Google Scholar] [CrossRef]
- Duan, J.; Chow, M.Y. A resilient consensus-based distributed energy management algorithm against data integrity attacks. IEEE Trans. Smart Grid 2018, 10, 4729–4740. [Google Scholar] [CrossRef]
- Wang, H.; Yan, Z.; Xu, X.; He, K. Probabilistic power flow analysis of microgrid with renewable energy. Int. J. Electr. Power Energy Syst. 2020, 114, 105393. [Google Scholar] [CrossRef]
- Lu, L.Y.; Liu, H.J.; Zhu, H.; Chu, C.C. Intrusion detection in distributed frequency control of isolated microgrids. IEEE Trans. Smart Grid 2019, 10, 6502–6515. [Google Scholar] [CrossRef]
- Che, L.; Liu, X.; Li, Z.; Wen, Y. False data injection attacks induced sequential outages in power systems. IEEE Trans. Power Syst. 2018, 34, 1513–1523. [Google Scholar] [CrossRef]
- Abhinav, S.; Schizas, I.D.; Lewis, F.L.; Davoudi, A. Distributed noise-resilient networked synchrony of active distribution systems. IEEE Trans. Smart Grid 2016, 9, 836–846. [Google Scholar] [CrossRef]
- Brentan, B.M.; Campbell, E.; Lima, G.; Manzi, D.; Ayala-Cabrera, D.; Herrera, M.; Montalvo, I.; Izquierdo, J.; Luvizotto, E., Jr. On-line cyber attack detection in water networks through state forecasting and control by pattern recognition. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 583–592. [Google Scholar]
- Sabzehgar, R.; Amirhosseini, D.Z.; Rasouli, M. Solar power forecast for a residential smart microgrid based on numerical weather predictions using artificial intelligence methods. J. Build. Eng. 2020, 32, 101629. [Google Scholar] [CrossRef]
- Canaan, B.; Colicchio, B.; Abdeslam, D.O. Detecting Cyber-Physical-Attacks in AC microgrids using artificial neural networks. In Proceedings of the 2021 IEEE 30th International Symposium on Industrial Electronics (ISIE), Kyoto, Japan, 20–23 June 2021; pp. 1–6. [Google Scholar]
- Abudin, M.J.; Thokchom, S.; Naayagi, R.; Panda, G. Detecting False Data Injection Attacks Using Machine Learning-Based Approaches for Smart Grid Networks. Appl. Sci. 2024, 14, 4764. [Google Scholar] [CrossRef]





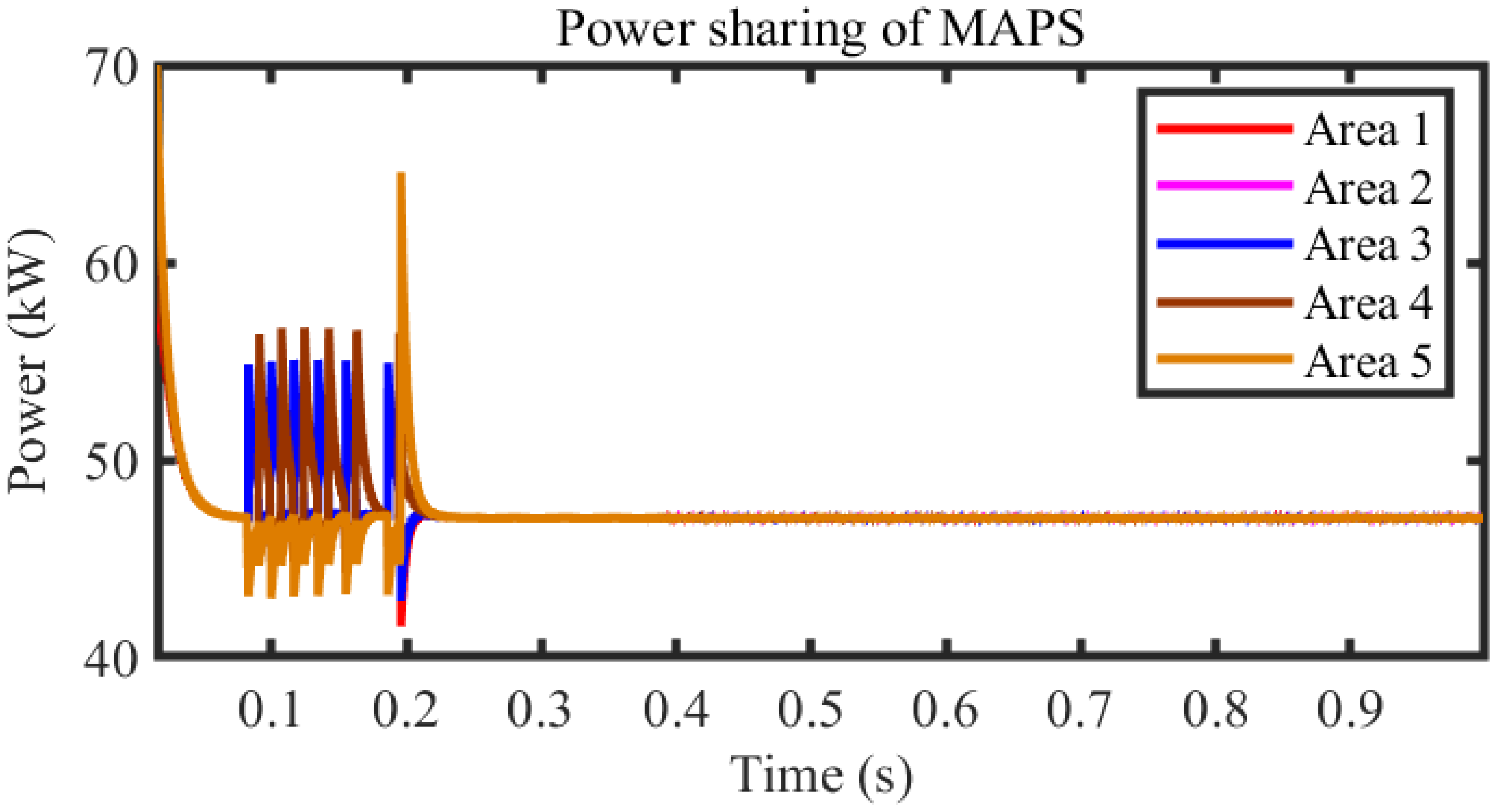
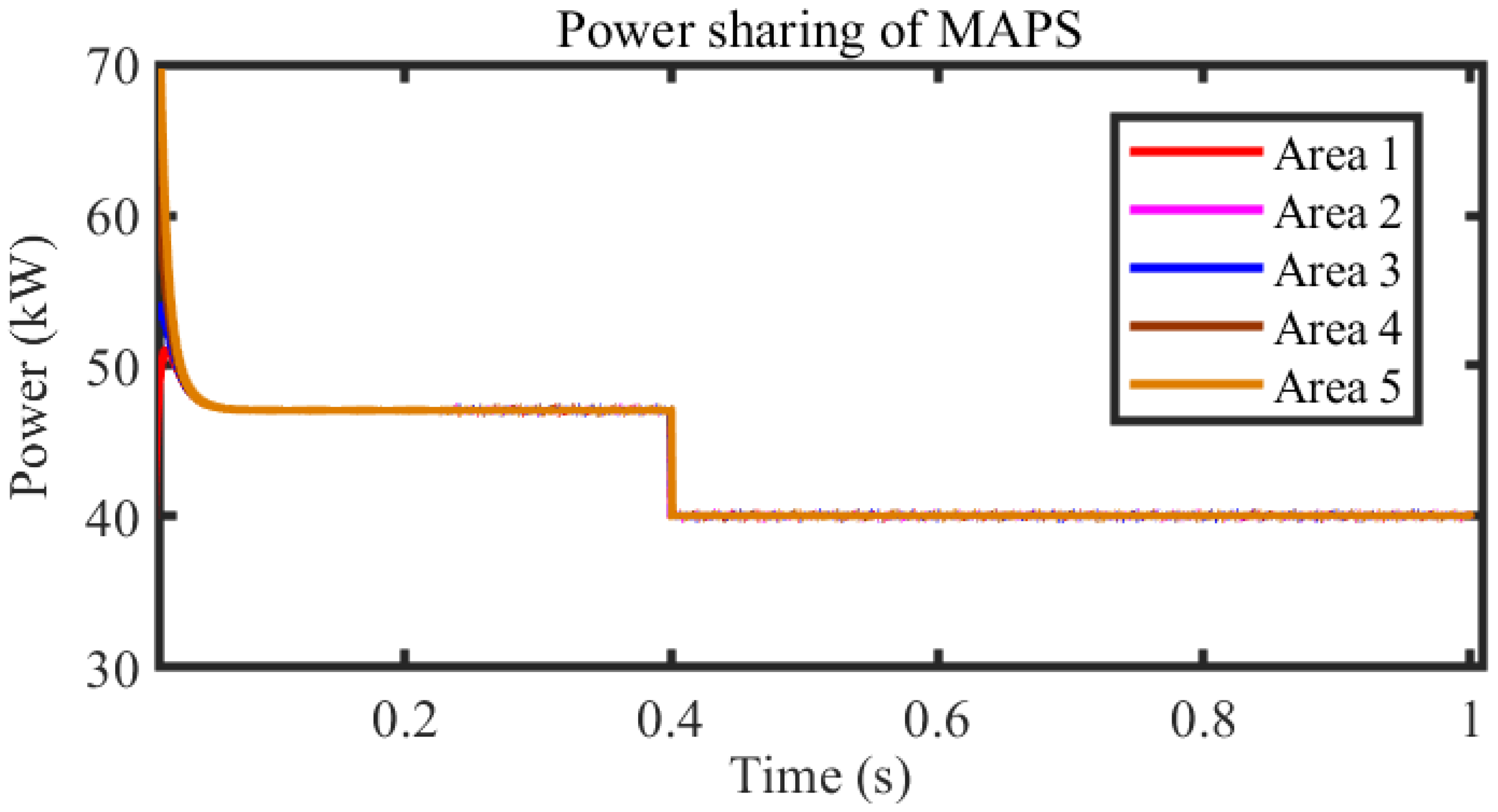
| Cases | Status | Stability Time (s) |
|---|---|---|
| Case 1 | Normal | 0.015 |
| Case 2 | Unstable | Unstable |
| Case 3 | Stale with root area under attacks | 0.15 |
| Case 4 | Stale with non-root area under attacks | 0.2 |
| Case 5 | Stable with load change | 0.4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmed, Z.; Nasir, M.; Alsekait, D.M.; Shah, M.Z.H.; AbdElminaam, D.S.; Ahmad, F. Control Conditions for Equal Power Sharing in Multi-Area Power Systems for Resilience Against False Data Injection Attacks. Energies 2024, 17, 5757. https://doi.org/10.3390/en17225757
Ahmed Z, Nasir M, Alsekait DM, Shah MZH, AbdElminaam DS, Ahmad F. Control Conditions for Equal Power Sharing in Multi-Area Power Systems for Resilience Against False Data Injection Attacks. Energies. 2024; 17(22):5757. https://doi.org/10.3390/en17225757
Chicago/Turabian StyleAhmed, Zahoor, Muhammad Nasir, Deema Mohammed Alsekait, Muhammad Zohaib Hassan Shah, Diaa Salama AbdElminaam, and Furqan Ahmad. 2024. "Control Conditions for Equal Power Sharing in Multi-Area Power Systems for Resilience Against False Data Injection Attacks" Energies 17, no. 22: 5757. https://doi.org/10.3390/en17225757
APA StyleAhmed, Z., Nasir, M., Alsekait, D. M., Shah, M. Z. H., AbdElminaam, D. S., & Ahmad, F. (2024). Control Conditions for Equal Power Sharing in Multi-Area Power Systems for Resilience Against False Data Injection Attacks. Energies, 17(22), 5757. https://doi.org/10.3390/en17225757








