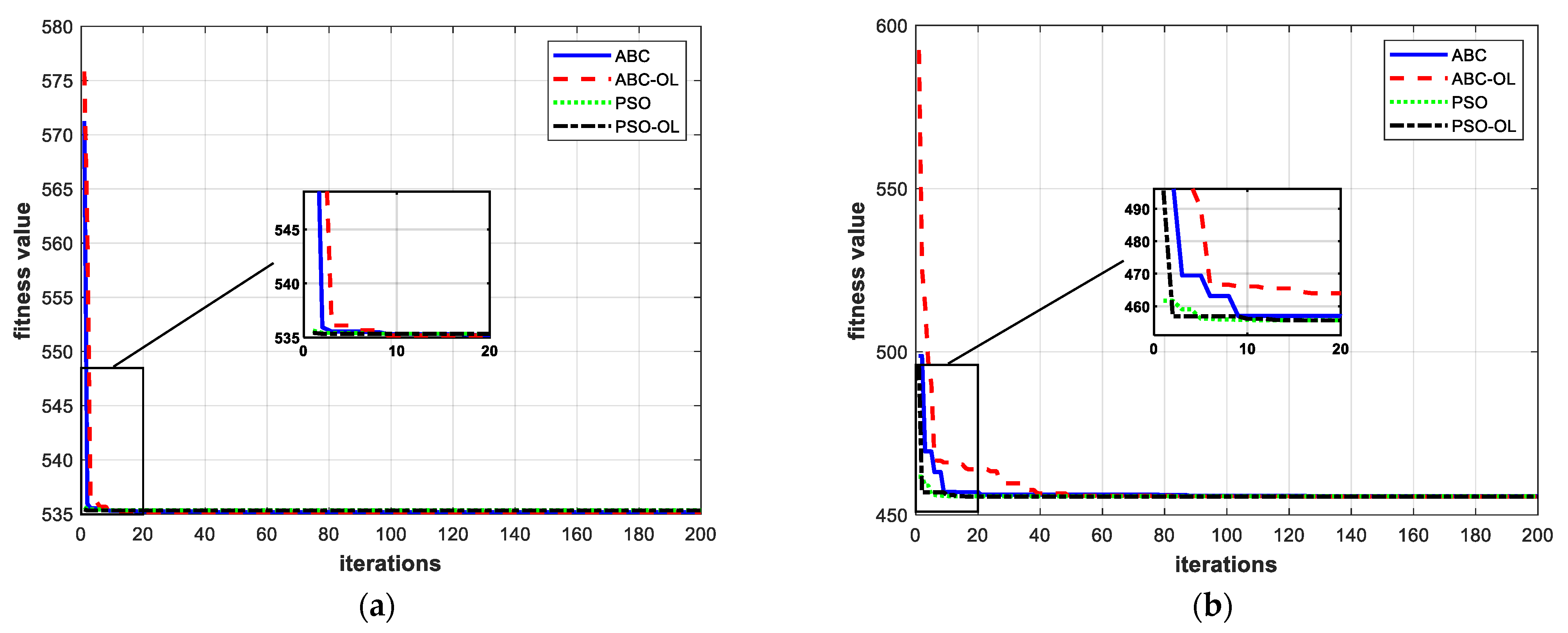
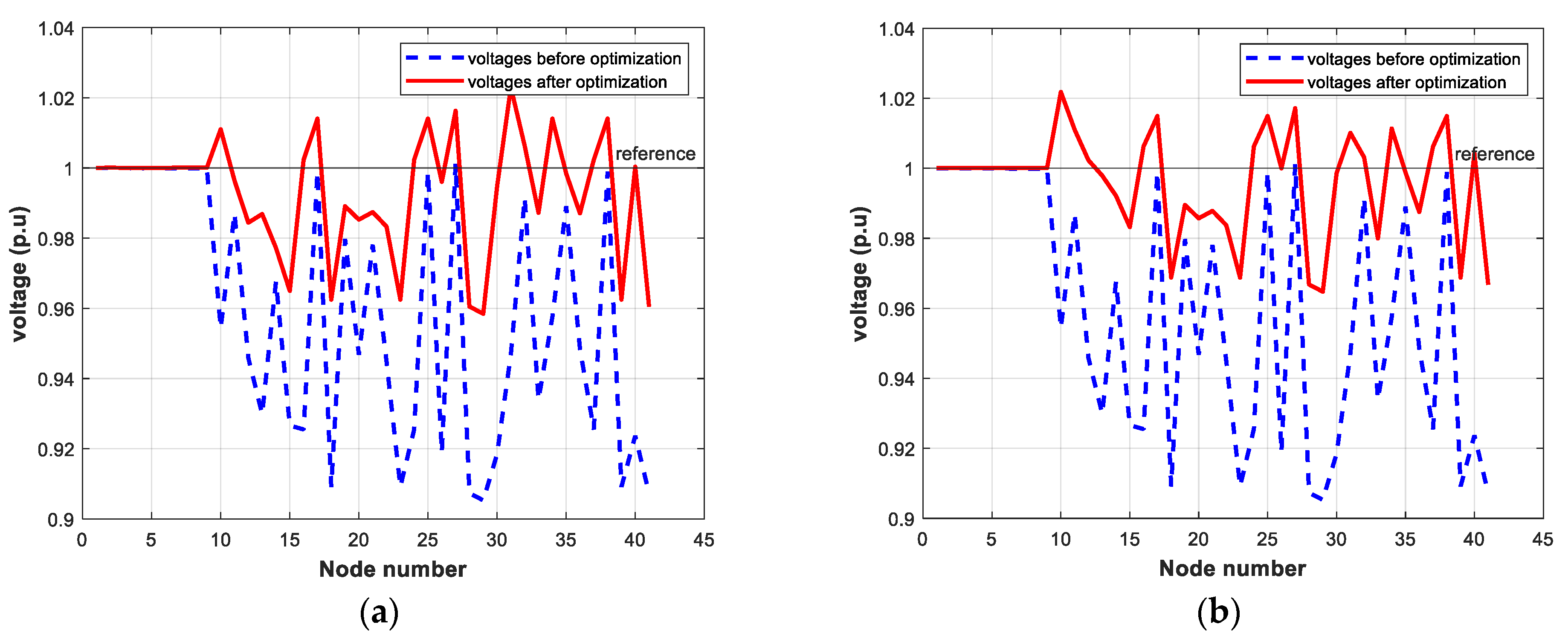
Conventionally, a vector is represented by bold regulator letters such as v and a matrix is represented by italic capital letters, e.g., M. A scaler is written as a regular italic letter such as s. Multiplication is written as “” or “”, or else it is omitted. Unless we specify otherwise, these conventions are adopted throughout this paper.
In this section, we first introduce an efficient iterative load flow (LF) method (i.e., the fixed-point method) used in the distribution network, followed by the optimal power flow (OPF) formulation, to represent the optimal PV allocation problem. The LF method is applied to enforce equality constraints in the OPF, which is highly non-linear. The problem consists of two objectives with certain constraints under PV-peak-hour operation (12:00 p.m.).
2.1. Distribution Power Flow (DPF)
The power flow program was first developed in the 1950s for transmission systems, and yet it did not become popular until the 1990s [
22]. Distributed power flow analysis is the computational procedure used to determine the steady-state operation of the power system; in other words, to calculate the state variables of bus voltage magnitude and angle at each node.
Traditionally, the power flow in the distribution network is one-way from substation to loads, and yet, with high DER penetration into distribution networks, nowadays, the power flow direction can be bilateral, as demonstrated in
Figure 1. IEEE1547-2018 is the standard that was released in 2018 to facilitate high DER penetration [
3]. Advanced applications such as (1) voltage quality analysis (sizes and locations of capacitor banks, locations and ratings of voltage regulators, line upgrades), (2) DER integration (given the location of a new DER, determine the impact on operations), and (3) outage restoration analysis (if an outage occurs, determine how to operate switches to restore the load) are built upon DPF.
There are several popular power flow algorithms in the literature, and in this study, we implemented a simple yet efficient iterative method, the fixed-point method, which can handle heavily unbalanced and large DER-penetrated distribution circuits. Before introducing the fixed-point method, we list some disadvantages of two popular algorithms. (1) The backward/forward sweep method. Here, the first drawback is that this method can have trouble dealing with systems that have high penetration of distributed generation sources because, in this situation, the power flow might not be unidirectional, which violates an assumption of the method. The second drawback is that while it is relatively efficient for smaller systems, the computational time can grow rapidly for large-scale, multi-phase, and unbalanced distribution systems. (2) The Newton Raphson method. In this case, the first drawback is that the Jacobian matrix used in this method needs to be updated and inverted at each iteration, which is computationally intensive, particularly for large-scale power systems. The second drawback is that the Newton Raphson method is most suited to transmission systems (generally mesh networks) and can have trouble with the unique characteristics of distribution systems, which are typically radial and have more unbalanced loads.
Therefore, this work adopted the fixed-point method operated in OpenDSS [
7]. The mathematical process is presented here, followed by a summary of its advantages.
Here,
is the compensation or injection current vector from the power conversion elements (load, generator, Vsource, Isource, storage, etc.) in the circuit, which may be non-linear, non-constant, and node-voltage dependent;
v is the node voltage vector; and
is a network admittance matrix composed of all elements’ primitive matrices
, as shown in
Figure 2.
is the matrix representation for each current-carrying circuit element (lines, loads, regulators, capacitors, etc.). For example, to represent the relationship of a current with vector
i and voltage vector
v between two buses of two conductors, as shown in
Figure 3,
is calculated and can be treated as a black box.
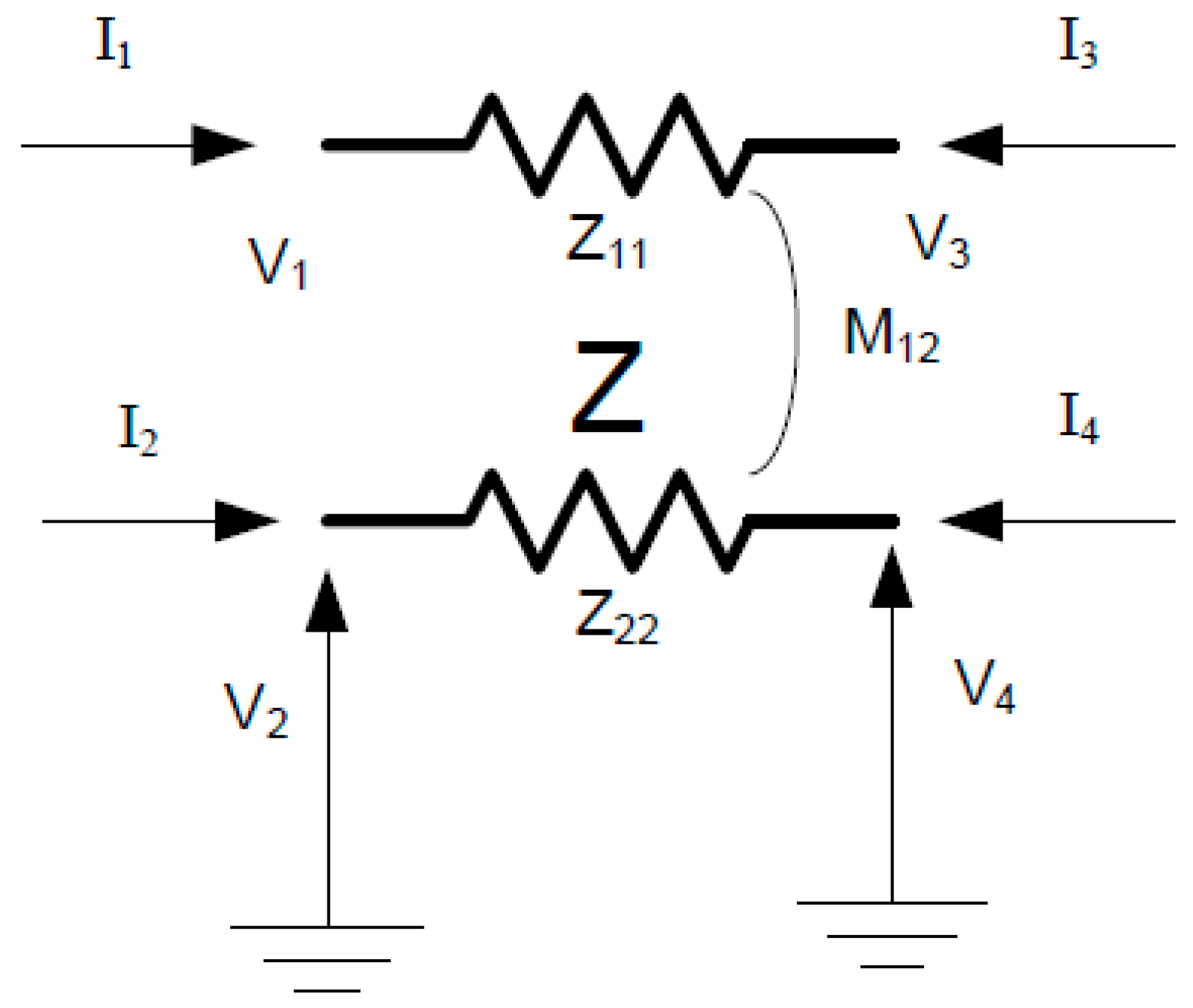
Here,
v1,
v2,
v3, and
v4 are voltages on terminals 1, 2, 3, and 4, respectively;
Z is the self-impedance; and
m is the mutual impedance induced by the magnetic field of two lines.
Z is a 2 × 2 matrix describing the impedance characteristics of the coupled impedances. The element has four terminals, as shown in
Figure 3, and a system of equations is written in nodal admittance form relating the currents entering each terminal to the voltage of each terminal with respect to a common zero-voltage reference, usually remote earth. The matrix relating the voltages and currents in this form is the
matrix as defined in (3) and (4). Note that the
Z matrix appears four times in the
matrix. Lines, reactors, capacitor banks, and transformers of nearly any complexity can be modeled simply by extending the principles of this example to the actual number of phases and windings [
7].
As mentioned previously, the network
admittance matrix is composed of the
of each circuit element, then an iterative method is used to solve
v. The process is straightforward. We first use an initial guess of
(1.0 p.u.) to calculate
and then calculate the voltage iteratively until the algorithm converges (the difference in current and previous
v is within a predefined threshold).
Figure 4 presents a flow chart of the iterative PF method.
Here,
n is the number of iterations. Note that most entries in
I are zero, but for DERs and non-linear voltage-dependent loads (such as constant power and constant current loads), the corresponding entries in
I are non-zero. The advantages of this DLF are as follows: (1)
remains constant if there is no network topology change. In other words, the matrix inversion only needs to be performed once during the iteration, which saves a lot of computational time. (2) The DLF can take very unbalanced three-phase networks and converge those successfully. (3) It is also suitable for parallel source (mesh topology) networks, as opposed to the radial network topology, which is required by the commonly used backward/forward sweep method [
23]. (4) It provides the option to run a long-time-series continuous load flow efficiently thanks to the fast solving feature.
2.2. Optimal PV Allocation
Figure 1 gives an overview of high PV system penetration into an unbalanced distribution network. This indicates that there are MW-scale, commercial, and residential types of PV systems and the power flow becomes bidirectional after large PV penetration. Bidirectional power flow certainly increases the complexity for system operators, but what is more concerning is the voltage issue introduced by PV. During the heavy loading period, PV penetration normally helps improve the voltage profile because voltage under a heavy load is near to or even lower than the low voltage limits. Thanks to PV penetration, the voltage will be boosted to the acceptable range. Yet, during light loading and high PV penetration times, such as noon, voltages are likely to be boosted above the high limit, which causes damage to the system.
Therefore, the PV allocation problem requires finding the optimal locations and sizing of PV systems to achieve objectives such as maximizing PV power injection or minimizing voltage deviation from 1.0 p.u. for all node voltages and when subjected to certain equality and inequality constraints. The mathematical form is expressed as follows:
where
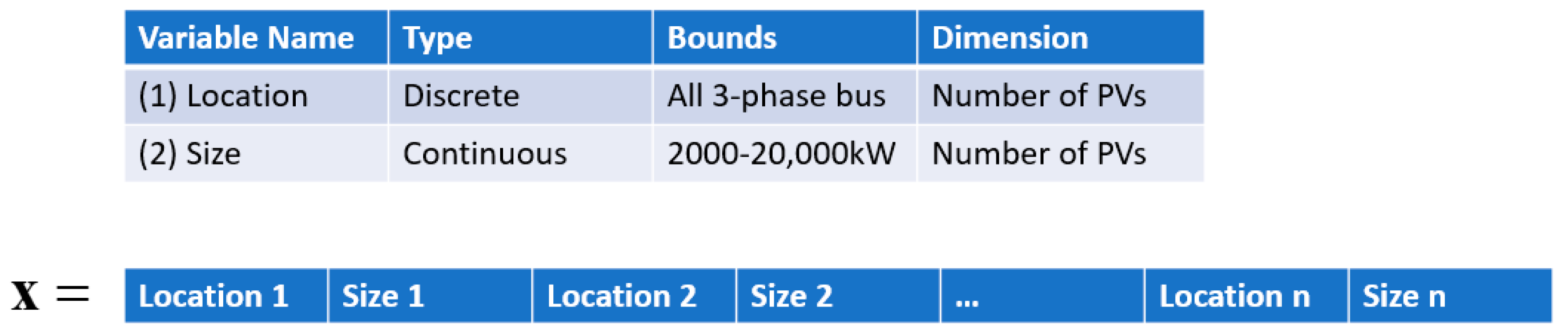
u is the control variable including PV locations and sizes;
x is the state variable/dependent variable including voltages and angles at each bus;
y is the known network parameters, such as network resistance, impendence, device rating, etc.;
g(٠) is the inequality constraints, which include line flow limit, voltage limit, and PV active power injection limit; and
h(٠) represents the equality constraints, which constitute the power balance equation at each node, represented as follows:
where
Pi and
Qi are the real and reactive power at each node
I. Note that unlike a transmission network, each bus in a distribution network will have to include multiple nodes in the model to reflect the possible unbalanced power flow. In other words, the size of equations increases significantly.
Vi,
Vj,
δi, and
δj, are the voltage magnitude and angle at nodes
I and
j;
Yij and
θij are the Y-bus admittance matrix elements between nodes
i and
j. Equation (9) comprises two highly non-linear equations.
For the objective function
f(٠), two objectives,
f1 and
f2, were considered in this study.
f1 was to minimize the voltage violation while maximizing the power injection (minimizing negative power injection) at a specific hour, whereas
f2 was to minimize the voltage violation and voltage deviation from 1.0 p.u. at specific hour, as shown below:
where
vi and
pPVi are the bus voltage and the real power injection at PV bus
i, respectively;
npv is the number of PV systems;
n is the total number of buses; and the voltage deviation is multiplied by a constant number
α of 1000. This will give the fitness value of the cost function of
f2 as a large number for clear selection and presentation.
As mentioned previously,
g(٠) are the inequality constraints, listed as follows:
where (12) is the constraint for the
ith generator; (13) represents the
ith transformer tapping limit; (14) is the voltage limit at the
ith node; (15) is the complex power flow limit at the
ith line; and (16) represents the PV system capacity limits, which are 2000–20,000 kVA in this study. (16) is the control variable constraint, which is enforced within the control variable feasible domain. The rest of the equations are related to dependent variables, and only violations from (14) are penalized with objective functions, if they exist, because (12), (13), and (15) are enforced when performing the power flow calculation in (5). The objective function then becomes (17):
where
fobj is the final objective function including the penalization term,
f is the objective functions defined from (10) and (11), and
pen is a large positive number as the penalty coefficient.