Abstract
In recent years, the safety of oil and gas pipelines has become a primary concern for the pipeline industry. This paper presents a comprehensive study of the vulnerability concepts that may be used to measure the safety status of pipeline systems. The origins of the vulnerability concepts are identified, the development and evolution of the vulnerability concepts are described, and the main connotations of the four levels of vulnerability concepts applied in different fields at this stage are summarized. Qualitative and quantitative methods of vulnerability assessment are comprehensively investigated, and the advantages and disadvantages, scope of application and key issues faced are compared and summarized. The research and analysis show that the vulnerability assessment of oil and gas pipelines is at a preliminary stage, and there is an urgent demand to establish a unified vulnerability concept and assessment system for oil and gas pipeline systems. The current qualitative or semi-quantitative assessment of pipeline vulnerability research lacks reasonable and scientific standards and bases for the classification of indicators and the determination of indicator scores, and it needs to focus on the establishment and improvement of quantitative assessment models.
1. Introduction
With the rapid development of oil and gas pipelines and the increasing dependence of the national economy on these pipelines, the requirements for reliability in the operation and security of oil and gas pipelines have increased. The issue of how to identify factors that may cause interruptions to customer supply and the probability of causing interruptions is becoming more and more prominent. In order to improve system reliability, pipeline companies need to eliminate accident factors from the current traditional identification of risk assessment and integrity evaluation studies in preventive management. Currently, in order to study and solve the reliability of pipeline systems, especially the accident prevention problem of girth welds of high-grade steel pipes, this paper systematically compares the research results on vulnerability in order to establish a vulnerability identification and evaluation method for pipeline systems in greater depth through the study of the basic concepts and methods of vulnerability, and to answer engineering challenges such as whether a defect exists for a long time and the risk is high, and whether it would develop into an accident.
In the early 20th century, the term vulnerability first appeared in the medical research literature and simply denoted the vulnerability of the body’s organs to weakening or loss of function due to their inability to become immune to specific diseases or viruses [1,2,3]. After the Second World War, the concept of “vulnerability” was first introduced into military science when the U.S. Social Science Research Council’s Atomic Energy Commission published a study on nuclear weapons [4], and in 1951, scholar Qu [5] conducted a discursive analysis of the vulnerability of the U.S. war economy, which was also the first time the term “vulnerability” was used in Chinese scholarship. In 1968, Marat [6] introduced the concept of vulnerability for the first time in a systematic study of the physical environmental pollution of groundwater systems. At the beginning of the development of vulnerability research, the definition of “vulnerability” was more similar to the concept of “risk”, indicating the possibility that the object of study would be exposed to disturbing conditions or the possibility of sustaining damage [7,8]. As vulnerability research expanded, the object of study became more complex and vulnerability assessments were applied to ecosystems, economic issues, climate change, engineering and many other fields of study.
Vulnerability is defined by the World Meteorological Organization (WMO) and the Intergovernmental Panel on Climate Change (IPCC) of the United Nations Environment Programme (UNEP) in their 2001 report on climate change [9] as the degree to which a system is vulnerable to climate change or has insufficient capacity to cope with the adverse effects of climate change. The IPCC considers vulnerability as a function of the combination of climate change characteristics such as the rate and magnitude of climate change within a system and the sensitivity and adaptive capacity of the system. Meanwhile, the IPCC defines “sensitivity” and “adaptation”, with sensitivity referring to the degree to which a system can withstand various climate-related impacts, both favourable and unfavourable; adaptation refers to the dynamic process of system operation or the ability of a system to adapt itself to climate change, to reduce the potential losses or mitigate the consequences of climate change, and to adapt in relation to the socio-economic infrastructure, the impact of human activities and interventions [9]. Based on this, this paper presents comprehensive research on the vulnerability concept of pipeline system safety status, identifies the origin of the vulnerability concept, explains the development and evolution process of the vulnerability concept, and summarizes the main connotations of the four levels of the vulnerability concept applied in different fields at the present stage. The qualitative and quantitative methods of vulnerability evaluation are comprehensively investigated, the advantages and disadvantages of each method, the scope of application and the key problems faced are compared and summarized, and relevant recommendations for vulnerability analysis of oil and gas pipelines are put forward.
2. The Development and Connotation of the Vulnerability Concept
2.1. The Concept of Vulnerability
Although the concept of “vulnerability” is understood differently by experts and scholars from different academic fields and research directions, in general terms, the concept of vulnerability can be summarized at four levels.
- Cutter [8] defined vulnerability as the probability that an individual or group is exposed to hazards and associated negative impacts, and Zapata et al. [10] defined vulnerability as the probability that damage to life, property and the environment will occur as a result of a combination of the vulnerability of the object of study and external disturbances. It can be seen that such scholars consider vulnerability as the probability of the object of study being exposed to adverse conditions such as disturbances and disasters or the possibility of damage occurring, which is similar to the concept of “risk” and focuses on the mechanisms and probability of adverse effects such as disturbances and disasters;
- The definition of vulnerability given by Timmerman [11] is the degree to which a system produces an adverse response when a disaster event occurs, and Tunner et al. [12] considered vulnerability to be primarily the degree to which the object of study (system level, subsystem level, system component level) may suffer damage when exposed to a disaster or disturbance. This type of understanding can be summarized as the extent to which vulnerability is the degree to which the object of study produces losses under conditions of adverse effects such as disturbances and disasters, and this understanding focuses on the results of exposure of the object of study to adverse disturbances;
- Dow [13] defined vulnerability as the ability of the object of study (individual or group) to cope with disaster events, while Vogel [14] summarized vulnerability as the ability of the object of research (individual or group) to anticipate, deal with, resist and recover from adverse conditions. This classification considers vulnerability as the ability of the research object to withstand or resist adverse effects such as disturbances and disasters, highlighting the human drivers that encompass social institutions, economic systems, power structures, etc., that are spawned by vulnerability [13];
- With the development and improvement of vulnerability-related research, more scholars understand vulnerability as a combination of many related concepts such as “sensitivity”, “risk”, “resilience”, and “adaptive capacity” [15]. Airlie [16] defined vulnerability as the degree to which a system component suffers damage due to exposure to perturbing conditions and the system’s ability to handle, adjust and adapt to the perturbing conditions. Adger [17] considered vulnerability as a state in which a system is vulnerable to damage due to exposure to disturbing conditions and lack of adaptive capacity. These understandings consider not only the system’s own influence on vulnerability, i.e., its adaptive capacity, but also the mechanisms by which the system interacts with disturbances outside the system and the environment.
From a review of vulnerability research at home and abroad, it is clear that a number of scholars from different research fields have initially reached a consensus on the concept of “vulnerability” as follows.
- Vulnerability is an inherent unstable property of a system, facility or internal component that exists prior to exposure to disturbance, disaster and other adverse effects; the statement that disturbance and disaster cause the system to become vulnerable is false. Taking the vulnerability of oil and gas pipeline systems as an example, the girth weld is an important part of the oil and gas pipeline system; in the absence of other disturbance factors such as non-design loads, the girth weld becomes the weak link and vulnerable point of the pipeline system due to its double discontinuity of geometry and material [18];
- The research object of vulnerability has multi-level characteristics. Nowadays, the concept of vulnerability has been extended and applied to all levels from large countries and regions to small communities and households, and the research object involves people and biomes, regions and territories, markets and economies, politics and wars, etc. [15];
- Vulnerability is determined by a combination of natural, social, economic and other elements that constitute the system. Vulnerability is a system, facility or internal component that is susceptible to some damage or loss under the influence of external environmental changes or disturbances;
- The vulnerability research object is subject to disturbances of multi-scale characteristics, the system is often exposed to multiple combinations of internal and external disturbances, and there is usually a complex interaction between the different scales of disturbances [15]. Taking oil and gas pipeline vulnerability as an example, internal pressure fluctuations of the system and external disturbances such as geological hazards, heavy vehicle crushing, and human damage can affect the safe and smooth operation of the pipeline;
- Vulnerability research is often based on analyses of specifically set disturbance conditions, and systems are not vulnerable to any one type of disturbance, and often exhibit different vulnerabilities under different disturbance conditions. Therefore, vulnerability is usually closely related to the particular disturbance imposed on the system;
- The definition and identification of the concept of “vulnerability” includes common terms such as “exposure”, “sensitivity” and “adaptive capacity“ [19,20,21]; the “exposure” of the research subject to external disturbances, the “sensitivity” of the research subject to external disturbances and the “adaptive capacity” of the research subject have become important components (Figure 1) of the concept of vulnerability [9,22,23,24].
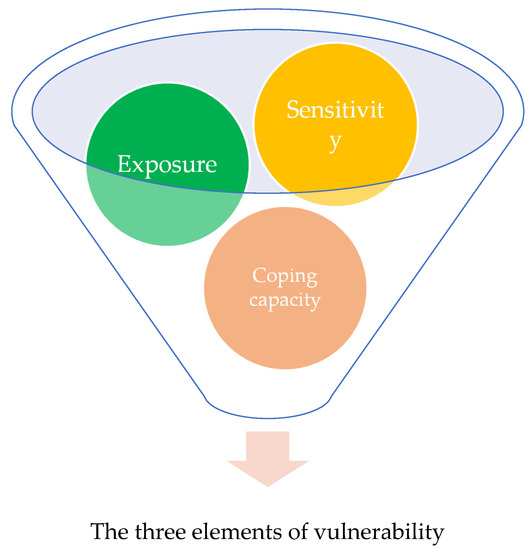 Figure 1. Diagram of the three elements of vulnerability.
Figure 1. Diagram of the three elements of vulnerability.
It is worth pointing out that, in response to the different stages of vulnerability research in various fields, or the different elements considered in constructing vulnerability models, some scholars have proposed the concept of vulnerability in a narrow sense and vulnerability in a broad sense. Shi [25,26] classified disaster vulnerability into narrow vulnerability, which only included human socio-economic sensitivity to disaster-causing factors, and broad vulnerability, which included disaster-causing conditions, disaster-bearing body systems and regional time periods. Wu et al. [27,28] conducted a systematic study of groundwater pollution vulnerability from two perspectives: natural static, uncontrollable narrow vulnerability under simple hydrogeological conditions and composite, dynamic adjustable and controllable broad vulnerability when superimposed on anthropogenic natural factors.
2.2. Identification of Similar Concepts
2.2.1. Vulnerability and Risk
At the beginning of the development of vulnerability research, the definition of “vulnerability” was more similar to the concept of “risk”, which indicates the probability that the object of study will be exposed to disturbing conditions or sustaining damage [7,8].
Risk is usually expressed as the product of the probability of failure and the consequence of failure. What this approach often fails to address is that “high-risk pipelines have been free of high-risk factors for a long time”, seriously affecting the acceptance of risk by some members of the public, engineers, senior management, etc. For example, in the case of ring weld failures in oil and gas pipelines, geological hazards, poor performance of the base material and defects in the ring weld can lead to unacceptable ring weld failures, whereas the possibility of geological hazards, poor material performance and defects is not highly likely to be the cause of a critical failure state, so vulnerability is equivalent to moving the problem forward and better controlling the occurrence of failure. At the same time, the adaptive capacity considered in vulnerability reflects the system’s ability to cope with and recover from exposure. For example, in the case of small diameter, low steel grade pipelines the ability to adapt to geological hazards by deforming the pipeline on a large scale, reducing the local invariance of the pipeline and making it impervious to damage is coping capacity; resilience refers to the ability to maintain and repair the pipeline. These are not considered by the concept of risk.
2.2.2. Vulnerability and Reliability
Reliability refers to the ability of a product or system to perform a specified function under specified conditions and within a specified period of time, emphasising the state of the system that provides normal use before a failure occurs (until it does), or when it does not occur. In oil and gas pipeline systems, the reliability of the pipeline calculated based on the reliability method is very high and the value is often extremely close to 1. The calculated maximum allowable probability of failure of the pipeline is generally much less than 0.1. However, in engineering practice, oil and gas pipeline failures occur frequently, causing unacceptable casualties, economic losses and environmental pollution, i.e., high system reliability but unacceptable consequences of accidental events. In such cases, risk-based evaluation methods can be used to measure such events, but when the probability of failure is very small and the consequences of failure are very large, i.e., the “0-∞” problem in mathematics, the risk of such events cannot be clearly derived.
Vulnerability is not reliability. Vulnerability is a quantitative assessment of the state of the system from the point of view of the likelihood of an accident occurring, focusing on the vulnerabilities that exist in the system itself. Feng [28] proposed to use vulnerability, counter-vulnerability and integrity to reflect the physical state of the pipeline system and management system, etc., to quantitatively describe the tendency of pipeline accidents to occur.
2.2.3. Vulnerability and Fragility
Vulnerability refers to the chance of damage to an affected body and the ease with which damage can occur [29]. The main object of fragility assessment is the affected body, and fragility assessment can be seen as an application of vulnerability studies to structures such as bridges and roads. It is most widely applied in the fragility of bridges [30,31], roads [32,33,34] and other structures in earthquakes.
Vulnerability is generally considered to encompass not only the probability of damage to the structure under disturbance in fragility (i.e., vulnerability), but also the ability to adapt to disturbance conditions through potential state parameters that can be changed and adjusted [35].
2.2.4. Vulnerability and Resilience
The term resilience first originates from the Latin word “resilio”, which means “to return to the original state” [36]. In the existing literature, the concept of resilience is rather abstract and there is no consensus among scholars on the definition of resilience [37]. As toughness is applied in different disciplines, the concept is being extended. Three types of more typical definitions of toughness are given below.
- Scholars Ye et al. [37] summarized the concept of resilience in different fields to conclude that resilience encompasses three important core capabilities, namely: the defensive capacity, adjustment recovery capacity and reorganisation evolutionary capacity, demonstrated when the system is disturbed by the impact of endogenous or exogenous uncertainties under certain spatial and temporal contexts, where the concept of resilience not only reflects the sensitivity and coping capacity included in vulnerability, but also reflects a certain degree of anti-vulnerability;
- Scholars Shuang et al. [38] argue that the key capabilities of resilience are absorptive capacity, resilience and adaptive capacity, a view that is reflected in the concept of resilience in areas such as urban hazards [39], supply chains [40], and water supply network systems [41];
- Scholars such as Zhang [42] argue that in the field of infrastructure such as power grids, resilience usually includes three aspects corresponding to the aspects of reliability, vulnerability and resilience, respectively: the ability of the system to continue to function normally; the ability of the system to withstand internal and external unexpected accidental shocks; and the ability of the system to quickly recover to its established function through active adjustment after its function is degraded by shocks.
This suggests that vulnerability and resilience are interrelated and that both reflect the response of the object of study to change. Resilience is concerned with the return of the system to its original state, whereas vulnerability is concerned with the state of the system in response to a disturbance (when the system may not return to its original state).
3. Research on Vulnerability Assessment Methods
Existing vulnerability assessment methods can be divided into two main categories: qualitative and quantitative assessment methods. Qualitative assessment methods are more frequently applied in the initial stage of vulnerability research, and this method has the feature of easy operation, but the accuracy of assessment results is lower [36]. Common quantitative vulnerability assessment methods include comprehensive indicator method, layer superposition method, vulnerability function model assessment method, fuzzy object element assessment method and hazard analysis method [43].
3.1. Qualitative Assessment Methods
Qualitative vulnerability assessment is a qualitative approach to the study of system vulnerability based on historical statistical analysis and actual research data, usually through a variety of means such as induction and deduction, and a non-quantitative characterisation and outlook of the subject from the perspective of evolution, analysis of the current situation and prediction of the direction of development.
Qualitative vulnerability assessment is often carried out by means of inductive and comparative analysis. Vulnerability assessment based on the inductive approach is usually driven by past empirical data and field research materials to explore the growth pattern and development characteristics of the vulnerability of the research object, so as to predict and analyze the future development trend of vulnerability [35]. Vulnerability assessment based on the comparative method is based on comparing two types of interrelated data, and extrapolating the patterns and trends of one type of data from the evolution of the other [44].
3.2. Quantitative Assessment Methods
3.2.1. Comprehensive Indicator Method
The comprehensive indicator method [45] is used to analyze the structure and function of the research area, to construct a system of assessment indicators based on the apparent characteristics of vulnerability, the causes of vulnerability, the environmental context and other aspects, to assign weights to the assessment indicators and to finally summarize the vulnerability indicator by means of mathematical statistical analysis, which is used to present the relative size of the vulnerability of the research object and to classify the vulnerability level.
Zhang et al. [46] constructed an innovative “pressure-support-state-response” indicator system (Figure 2) to evaluate the vulnerability of wetland ecosystems in the Yellow River region. Dang et al. [47] constructed a coastal zone ecosystem vulnerability assessment system with three levels and 23 indicators from the perspectives of exposure, sensitivity and adaptive capacity.
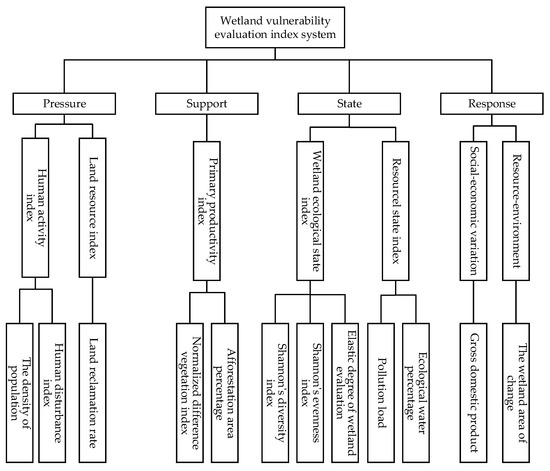
Figure 2.
Wetland vulnerability assessment indicator system [46].
Some scholars have conducted research on assessment indicator systems, and several types of assessment indicator systems have gradually been developed: the “cause and outcome performance” model [48,49,50], the “stress-state-response” model [46,51,52,53], the “multi-system” [54] and the “exposure-sensitivity-adaptation” model [55], etc. Mathematical and statistical methods such as weighted summation (averaging) [56], principal component analysis [57,58,59,60,61], analytical hierarchy process [62,63,64,65,66,67,68] and fuzzy comprehensive assessment [69,70,71] are widely used in the comprehensive vulnerability indicator synthesis process.
The comprehensive indicator method has been widely used in the vulnerability assessment of a variety of systems by virtue of its simplicity and clarity, convenience and flexibility, and ease of operation. However, in the process of establishing the indicator system, the method is unable to consider the changing state of the research object over time scales; in the process of determining the indicator weights, there is a strong subjectivity, which is likely to ignore the intrinsic correlation mechanism between indicators; at the same time, the vulnerability assessment results obtained based on the integrated indicator method are often difficult to verify [72].
3.2.2. Layer Superimposition Method
The layer superimposition method [73] allows for both qualitative and quantitative analysis [35], by superimposing layers representing different vulnerability elements or layers representing different forms of disturbance, and thus visually capturing the spatial distribution of vulnerability in terms of form and state of difference.
O’Brien et al. [74] constructed a climate change vulnerability map and a globalization vulnerability map for the Indian region by superimposing the adaptive capacity map, climate sensitivity map and trade sensitivity map, and finally constructed a dual exposure vulnerability map of climate change and globalization for India by superimposing the climate change vulnerability and globalization vulnerability maps (Figure 3), so as to evaluate and analyze the vulnerability of different regions to climate change in the context of globalization. Marc et al. [75] constructed a “livelihood” vulnerability map of ecosystem service indicators by superimposing a stratified potential impact layer with an adaptive capacity layer to predict ecosystem service provision in the European region.
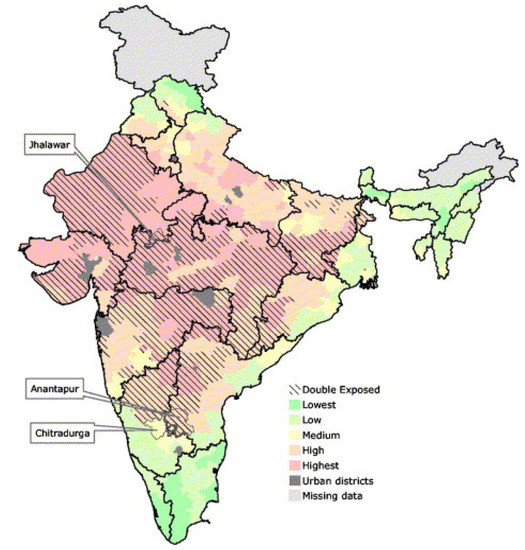
Figure 3.
Distribution of vulnerability to the dual exposure to climate change and globalization in India [74].
The method of superimposing different vulnerability elements is more suitable for regional and territorial vulnerability assessment studies, which can better characterize the spatial differences in vulnerability of the study object under the influence of regional hazards or regional disturbances, and also better reflect the spatial differences in sensitivity, risk and coping capacity; however, in the case of co-existence of multiple hazards or disturbances, the coping capacity indicators are only selected to characterize the common indicators that can cope with different hazards or disturbances, which will lead to the degree of vulnerability of the study region to a specific disaster or disturbance not being captured.
The layer superimposition method for different forms of disturbance, as its name suggests, is suitable for vulnerability assessment studies under conditions of coexistence of multiple disturbances; however, this method does not capture the variability in the overall level of impact of the study system for different hazards or disturbances.
3.2.3. Fuzzy Object Element Assessment Method
The first prerequisite for the fuzzy element assessment method is the need to select a reference system, which usually has the lowest or highest vulnerability, and subsequently determine the relative vulnerability of the study area by deriving the degree of similarity between the study area and the reference system.
When the fuzzy object assessment method is used, the object model is usually represented by the ordered three-element group R = (N,C,V), where N denotes the name of the assessment thing, C denotes the characteristic value, and the fuzzy quantity value about the characteristic value C is V. Zhang et al. [76] used hierarchical analysis, comprehensive fuzzy theory, and the method of a topologizable set of material elements to construct a fuzzy material element model for ecological vulnerability assessment of Minqin Oasis in Gansu, containing four aspects of land resource system, ecosystem, water resource system, and artificial intervention system, with a total of 16 indicators. Ma et al. [77] used the fuzzy object element method to establish a water resources vulnerability assessment indicator system and judging criteria from three perspectives: benefit level, water resources quantity and ecological environment, and carried out a quantitative analysis of the dynamic development trend of water resources vulnerability in Urumqi, Xinjiang. In the fuzzy element analysis-based security assessment model for PV-containing distribution networks constructed by Fan et al. [78], N denotes the security assessment of PV-containing distribution networks, C is each assessment indicator and V is the assessment indicator quantity value.
The fuzzy element assessment method makes full use of the original variable data and does not need to consider the relationship between variables. However, the assessment results of this method depend on the selection criteria of the reference system. Due to the strong subjectivity of the selection of the reference system and the lack of reasonable basis and scientific method, the results of the fuzzy meta-assessment can only reflect the relative degree of geographical vulnerability of each study area, and cannot show the important factors that lead to spatial differences in vulnerability [15].
3.2.4. Hazard Analysis Method
The hazard analysis method [79] characterizes the vulnerability of a research object by calculating the current state vector values and the natural state vector values of each variable of the research object as the Euclidean distance between the two. The greater the Euclidean distance, the more vulnerable the system is and the more possible it is that the system will undergo a complete change in structure and performance [79]. This method reflects the degree of deviation from the natural state of the object of assessment. Given that the definition of the natural state does not take into account the existence of human activities, and that the range of values of each variable remains basically stable under the natural state condition, the assessment results are less dependent on the selection of the reference natural state. However, the hazard analysis method assumes that the vulnerability of the study object is minimal in the natural state, an assumption that overlooks the impact of human activities on the improvement and promotion of the ecological environment; the method reflects the degree of deviation from the natural state of the assessment object but does not clarify whether the structure and function of the study object have changed fundamentally [15].
3.2.5. Vulnerability Function Model Assessment Method
The vulnerability function model assessment method is a method for evaluating the vulnerability of a research object by constructing a vulnerability function model based on the quantitative analysis and assessment of the components of vulnerability and the identification of the mechanisms of interaction between the components.
Shi’s innovative model for disaster vulnerability assessment proposes a broad vulnerability assessment model and a narrow vulnerability assessment model [25,26], defining the broad vulnerability as the vulnerability assessment of a disaster system, which is a coupling function of the vulnerability of the nurturing environment, the vulnerability of the carrier system (socio-economic system), and the vulnerability of the region or time period (Equation (1)); the narrow vulnerability is defined as the sensitivity of the human socio-economic system to disaster-causing factors, which is a coupling function of economic vulnerability, social and human vulnerability, and political vulnerability.
where VSE is regional spatial and temporal vulnerability, VE is vulnerability of the incubating environment, VST is vulnerability of the disaster-bearing body, VF is economic vulnerability, VSH is social and human vulnerability, VP is political vulnerability, E is the environmental system, F is economic, S is social, H is human, P is political, φ is latitude, λ is longitude, h is altitude, t is time, Δφ is unit latitude, Δλ is unit longitude, Δh is altitude, and Δt is time period.
Vulnerability function model assessment methods can more accurately characterise the interaction mechanisms between the constituent elements of vulnerability, but the development of this assessment method has been slowed by the lack of uniformity in the concept of vulnerability, the incompleteness of the assessment system and the inconsistent understanding of the interrelationships between the constituent elements.
4. Pipeline System Vulnerability-Related Studies
4.1. Exploring the Connotations of Vulnerability
Pipelines and the people, equipment and facilities, and the environment along the pipeline route, as well as society and the national energy strategy and security are all affected by pipeline accidents. The numerous risk factors are interrelated and interact with each other, and the pipeline system and the environment around the pipeline come together to form a coupled, complex, integrated pipeline–environment system. Therefore, the research object of oil and gas pipeline vulnerability is often not only the pipeline itself, but also the environmental conditions along the pipeline, equipment and facilities, as well as measures and institutions with a certain level of response and coping recovery capacity for pipeline incidents.
At the current stage, pipeline vulnerability research is still at the stage of mapping development, and some scholars have carried out an exploration of the meaning and definition of pipeline vulnerability. The vulnerability of oil and gas pipelines is evaluated in terms of the hazards and vulnerabilities of the pipeline itself and the potential for accidents to occur, the main body along the pipeline that would be exposed to disasters after a pipeline damage event, and the response capability to prevent and control pipeline accidents. Therefore, the vulnerability of oil and gas pipelines is usually divided into disaster-causing factors vulnerability, hazard-bearing body vulnerability and coping capacity vulnerability.
The vulnerability of disaster-causing factors refers to the sensitivity of the integrated pipeline–environmental system to damage or leakage caused by external disturbances, disasters and other adverse effects; the vulnerability of the hazard-bearing body refers to the potential scope of impact and severity of consequences of damage or leakage of the integrated pipeline–environmental system; and the coping capacity vulnerability refers to the ability of the oil and gas pipeline system itself and external emergency measures to respond to accidental disasters. The higher the incident sensitivity and severity of consequences and the poorer the coping capacity, the higher the pipeline system vulnerability [80].
In the book “Anti-Fragile” [81], Nassim innovated a way to quantitatively characterise pipeline system accidents using the three elements of vulnerability, anti-fragility and toughness; Feng [28], based on the actual situation of pipeline integrity management and assessment in China, improved the proposal to quantitatively characterize pipeline accidents based on vulnerability, anti-vulnerability and integrity state. The vulnerability of a pipeline system is the tendency for an accident to occur as a result of changes in the internal or external conditions of the pipeline, and this tendency leads to an increased probability of an accident occurring on the pipeline. Positive anti-vulnerability is when the pipeline system’s integrity management and emergency response systems are enhanced following a change in internal or external conditions, or even following an accident; negative anti-vulnerability is a state of adaptation, neglect or paralysis to an accident or risk. Both vulnerability and anti-vulnerability are states of the pipeline system, and the combined indicators of both characterize the probability of an incident occurring on the pipeline system. The integrity of a pipeline system is the physical state of the pipeline being intact and outstanding in its ability to cope with changes in conditions [28].
Pipeline vulnerability research focuses on oil and gas pipelines under specific disturbances, such as typhoon hazards, landslide hazards, and risk of crossing water. Bahareh et al. [82] based their analytical algorithm for the vulnerability of above-ground facilities and above-ground transport networks on the quantitative response of failure rates under different pipeline material properties and geometry conditions, and visualise the vulnerability and failure impact range through data integration. Liu et al. [83] carried out a vulnerability analysis of the gas pipeline network based on the geographical distribution between the urban road system and the gas pipeline system, identifying vulnerable areas of the urban safety operational infrastructure system. Ni et al. [84] developed a numerical analytical model of pipe strain underground settlement, including parameters such as soil properties, pipe dimensions and pipe performance, and constructed and evaluated pipe vulnerability curves by means of lasso regression machine learning techniques. Ni et al. [85] constructed a pipeline vulnerability curve based on a numerical simulation model of pipeline failure under permanent fault displacement, also by means of a lasso regression technique, and systematically analyzed the effect of uncertainties in parameters such as burial depth, pipe properties and pipe geometry on the vulnerability of the pipeline.
4.2. Vulnerability Assessment Methodology Study
In 2004, the American Petroleum Institute introduced vulnerability to risk assessment for the first time [86], and since the 1910s, Chinese researchers have gradually extended the study of vulnerability to oil and gas pipelines [87], exploring the connotations of vulnerability, the construction of indicator systems, and the determination of indicator weights for oil and gas pipelines. The comprehensive indicator method is widely used because of its clear principles and ease of implementation.
Chen et al. [88] considered that oil and gas pipeline vulnerability is an inherent property of a system that is susceptible to degradation or loss of function and damage due to its own adverse factors or lack of coping capacity, and carried out the construction and analysis of a vulnerability indicator system from two aspects: the pipeline itself and the disaster-bearing body. Hou et al. [89] established a drainage pipeline structural vulnerability assessment model by determining four main indicators based on the pipe degradation model: pipe diameter, burial depth, age and material, and determining the indicator weights through the network analysis method. Zhao et al. [90] constructed a “detect–deter–delay–respond–recover” vulnerability assessment model from the perspective of accident development history, used the entropy value method to specify the indicator weights, and finally built a vulnerability-based risk assessment process for oil and gas pipelines. Wang Jia [87] carried out an analysis and assessment of the inherent vulnerability of oil and gas pipelines at different key locations through the fuzzy comprehensive assessment method. Wang et al. [91] constructed a vulnerability assessment system for urban natural gas pipelines and town gas PE pipeline systems. Based on the results of finite element numerical simulation, Fu [86] and Shu [92] established a safety assessment indicator system for the overhanging section of gas transmission pipelines through water and a safety assessment indicator system for buried gas transmission pipelines across faults, respectively, based on the vulnerability of the causal factors, the vulnerability of the disaster-bearing body and the vulnerability of the coping capability. Wang et al. [93] integrated risk theory with vulnerability analysis methods and constructed a “risk-vulnerability” analysis method to identify key components of pipeline networks in three directions: pipeline operation status, pipeline transmission performance and pipeline network characteristics.
Some scholars combined multiple comprehensive indicator assessment methods in their pipeline vulnerability research. Huang et al. [94] constructed a long-distance pipeline vulnerability assessment indicator system containing 28 indicators considering the disaster-causing perspective, the emergency rescue perspective and the consequence perspective, determined the indicator weights based on a hierarchical analysis nine-level scale method, and proposed a fuzzy comprehensive assessment model for long-distance pipeline vulnerability. Zhao [95], Dou [96], Cui [97] and other scholars determined the vulnerability assessment indicator weights based on the analytical hierarchy process method and used the fuzzy comprehensive assessment method to construct vulnerability assessment models for urban buried natural gas pipelines, oil pipelines and city gas pipeline networks, respectively.
4.3. Vulnerability Assessment Indicator Selection
Summarizing the existing research on the vulnerability of pipeline systems based on the comprehensive indicator method, it can be found that in the process of determining the vulnerability assessment indicators for pipelines, most scholars determined the vulnerability assessment indicators from three levels: the causative factors, the disaster-bearing bodies and the coping capacity [97], and gave specific assessment indicators under the three levels in a targeted manner by considering specific perturbations in a particular environment.
There are many factors affecting the vulnerability of pipeline systems, and the correlation between them is complicated, which makes it impossible to explore a clear relationship between vulnerability and all the influencing factors. At the same time, due to the reality that assessment models have a large number of indicators, complex weights and tedious analytical and computational processes, as well as the inability of assessment algorithms to take into account the dynamic development of time scales and the lack of self-adaptive capabilities, some scholars have attempted to make up for these shortcomings with the help of artificial neural networks. Zhao et al. [98] established a vulnerability indicator system and classification criteria for urban gas pipeline networks in terms of physical, structural and social functions, and trained a BP neural network algorithm to obtain “sensitivity degree” and “own coping capacity” predictions. The vulnerability function model was finally constructed. Wang [99] optimized the indicator weights with the help of BP neural networks, taking into account the fuzzy uncertainty of the factors affecting the possibility of pipeline failure and the consequences of pipeline failure. Chen et al. [87] constructed an optimized vulnerability assessment model based on support vector machine regression after establishing a vulnerability assessment indicator system for long-distance oil and gas pipelines. Li et al. [100] constructed a vulnerability assessment indicator system for oil pipelines in CO2-driven reservoirs from three aspects: disaster-causing factors, disaster-bearing bodies and disaster response, and established a vulnerability assessment model using a support vector machine regression method and carried out engineering example applications.
5. Summary of the Current Status of Vulnerability Assessment Research
Vulnerability research is an important theory and methodology for studying the extent of damage and a system’s ability to cope with external disturbances, and is a new research paradigm for multiple research fields. A study of vulnerability research was carried out to analyze and compare the concept of vulnerability. The concept of the term vulnerability is not yet uniform in different research fields, and four distinct levels can be distinguished regarding the concept of vulnerability.
- Vulnerability is the probability that the object of study will be exposed to adverse effects, such as disturbances and disasters, or that damage will occur;
- Vulnerability is the extent to which the object of research will be damaged by adverse effects such as disturbances and disasters;
- Vulnerability is the ability of the object of research to withstand adverse effects such as disturbances and disasters;
- Vulnerability is a combination of related concepts such as “risk”, “sensitivity” and “coping capacity”.
Vulnerability assessment methods were investigated, five quantitative vulnerability assessment methods were systematically introduced, and the strengths and weaknesses of the various assessment methods, their scope of application and the key issues to be addressed were compared and analyzed, as shown in Table 1.

Table 1.
Summary of common methods for quantitative vulnerability assessment.
The following recommendations for vulnerability research and the selection of vulnerability assessment methods are summarized below: (1) Vulnerability studies should start with an easy-to-use assessment method such as the composite indicator method, and then, after obtaining a more specific and comprehensive understanding and knowledge of the vulnerability of the subject of the study, carry out in-depth analytical studies using quantitative assessment methods that can take into account more complex conditions and are more closely related to the real situation. (2) In solving complex system problems, different vulnerability assessment methods have their own strengths and weaknesses. When conducting vulnerability studies, assessment methods should be selected according to the specific conditions of the research object, research objectives, information and data collection, etc.; multiple assessment methods can also be complemented and integrated to form a more comprehensive and optimized vulnerability assessment method. (3) Vulnerability assessment, in addition to giving a scientific and reasonable degree of vulnerability of the research object, also needs to convert the quantitative assessment results obtained into control measures to reduce the vulnerability of the research object, providing effective information and recommendations for life, engineering and development practices. (4) In the face of multi-structured, multi-level and dynamically developing complex research objects, important aspects affecting the vulnerability of complex systems should be identified and vulnerability assessment should be carried out in a targeted manner.
6. Conclusions
Based on research and analysis of domestic and international studies on the vulnerability of oil and gas pipelines, the following is clear:
- There is still no unified and accepted theoretical system of oil and gas pipeline vulnerability, and scholars do not have a unified definition of the concept of vulnerability; on the whole, oil and gas pipeline vulnerability studies generally consider three aspects: disaster-causing factors, disaster-bearing bodies and coping capacity;
- Some of the scholars focus more on the improvement and optimization of the parameters related to the quantitative assessment model, while others focus more on the criteria and basis for determining the scores of indicators and the scientific and reasonable classification of grades;
- The comprehensive indicator assessment method is the most widely used in the vulnerability assessment of oil and gas pipelines, and the existing research results adopt a single assessment method, a similar assessment indicator system and lack innovation;
- The commonly used methods for determining indicator weights are subjective weights based on the hierarchical analysis method and objective weights based on the entropy method. Some scholars have proposed some innovative methods for determining indicator weights, but most of them are at the experimental stage, and the process and results of vulnerability assessment lack verification.
Author Contributions
Conceptualization, Q.F. and H.Z. (Hong Zhang); methodology, X.L., B.Y. and X.Z.; writing—original draft preparation, Y.Y. and H.Z. (Han Zhang); writing—review and editing, J.C.; supervision, H.Z. (Hong Zhang) and X.L.; project administration, Q.F. and H.Z. (Hong Zhang); funding acquisition, H.Z. (Hong Zhang) and X.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research has been co-financed by National Key R&D Program of China (Grant No. 2022YFC3070100), Natural Science Foundation of China (Grant No. 52004314), Young Elite Scientists Sponsorship Program by Beijing Association for Science and Technology (Grant No. BYESS2023145), the Science and Technology Research Project of PipeChina (Grant No. WZXGL202105).
Data Availability Statement
Data is contained within the article. The data presented in this study are available in the references.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Anonymous. The Vulnerability of the Apices of the Lungs. Hospital 1901, 30, 190. [Google Scholar]
- Traquair, H.M. The special vulnerability of the macular fibres and “sparing of the macula”. Br. J. Ophthalmol. 1925, 9, 53–57. [Google Scholar] [CrossRef]
- Meyer, A. The Selective Regional Vulnerability of the Brain and its Relation to Psychiatric Problems. Proc. R. Soc. Med. 1936, 29, 1175–1181. [Google Scholar] [CrossRef] [PubMed]
- Coale, A. Reducing vulnerability to atomic attack; protective methods that may reduce the potential consequences of an attack by atomic bombs. Bull. At. Sci. 1947, 3, 71–98. [Google Scholar] [CrossRef] [PubMed]
- Qu, Z.P. The fragility of America’s war economy. World Intellect. 1951, 23, 20. [Google Scholar]
- Margat, J. Vulnérabilité des Nappes d’eau Souterraine à Lapollution: Base de la Cartographie; Doc. BRGM, 68 SGL 198HYD; Département d’Hydrogéologie: Orlean, France, 1968. [Google Scholar]
- Cutter, S.L. Living with Risk: The Geography of Technological Hazards; Edward Arnold: London, UK, 1993. [Google Scholar]
- Kates, R.W. The interaction of climate and society. Clim. Impact Assess. 1985, 3, 3–36. [Google Scholar]
- IPCC. Climate Change 2001: Impacts, Adaptation, and Vulnerability; Cambridge University Press: Cambridge, UK, 2001. [Google Scholar]
- Zapata, R.; Caballeros, R. Un Tema del Desarrollo: La Reduccion de la Vulnerabilidad frente a los Desastres; CEPAL, Naciones Unidas: Ciudad de México, Mexico, 2000. [Google Scholar]
- Timmerman, P. Vulnerability, Resilience and the Collapse of Society: A Review of Models and Possible Climatic Applications; Institute for Environmental Studies, University of Toronto: Toronto, ON, Canada, 1981. [Google Scholar]
- Tunner, I.B.L.; Kasperson, R.E.; Matson, P.A.; McCarthy, J.J.; Corell, R.W.; Christensen, L.; Eckley, N.; Kasperson, J.X.; Luers, A.; Martello, M.L.; et al. A framework for vulnerability analysis in sustainability science. Proc. Natl. Acad. Sci. USA 2003, 100, 8074–8079. [Google Scholar]
- Dow, K. Exploring differences in our common futures: The meaning of vulnerability to global environmental change. Geoforum 1992, 23, 417–436. [Google Scholar] [CrossRef]
- Vogel, C. Vulnerability and global environmental change. In Proceedings of the Human Dimensions of Global Change Meeting, Rio de Janeiro, Brazil, 6–8 October 2001; World Commission of Environment and Development: Geneva, Switzerland, 2001. [Google Scholar]
- Li, H.; Zhang, P.Y.; Cheng, Y.Q. Concepts and assessment methods of vnlnerability. Prog. Geogr. 2008, 27, 18–25. [Google Scholar]
- Research and Assessment Systems for Sustainability Program. Vulnerability and Resilience for Coupled Human-Environment Systems: Report of the Research and Assessment Systems for Sustainability Program 2001 Summer Study; Airlie House: Warrenton, VA, USA, 2001. [Google Scholar]
- Adger, W.N. Vulnerability. Glob. Environ. Chang. 2006, 16, 268–281. [Google Scholar] [CrossRef]
- Zhang, H.; Wu, K.; Liu, X.B.; Yang, Y.; Sui, Y.L.; Zhang, Z.Y. Numerical simulation method for strain capacity of girth welding joint on X80 pipeline with 1422 mm diameter. Oil Gas Storage Transp. 2020, 39, 0162–0168. [Google Scholar]
- Smit, B.; Wandel, J. Adaptation, adaptive capacity and vulnerability. Glob. Environ. Change 2006, 16, 282–292. [Google Scholar] [CrossRef]
- Gallopin, G.C. Linkages between vulnerability, resilience, and adaptive capacity. Glob. Environ. Change 2006, 16, 293–303. [Google Scholar] [CrossRef]
- Downing, T.E.; Patwardhan, A. Vulnerability Assessment for Climate Adaptation; APF TeclInical Paper 3; United Nations Development Programe: New York City, NY, USA, 2003. [Google Scholar]
- Birkmann, J. Risk and vulnerability indicators at different scales: Applicability, usefulness and policy implications. Environ. Hazards 2007, 7, 20–31. [Google Scholar] [CrossRef]
- Liu, X.Q.; Wang, Y.L.; Peng, J. Progress in vulnerability analysis of coupled human-environment system. Adv. Earth Sci. 2009, 24, 917–927. [Google Scholar]
- Shi, P.J. Theory on disaster science and disaster dynamics. J. Nat. Disasters 2002, 11, 1–9. [Google Scholar]
- Shi, P.J. Theory and practice on disaster system research in a fourth time. J. Nat. Disasters 2006, 14, 1–7. [Google Scholar]
- Wu, S.J.; Sun, G.N.; Xue, L. Analysis on groundwater vulnerability: A case study in Xi’an City. China J. Arid. Land Resour. Environ. 2006, 21, 31–36. [Google Scholar]
- Wu, X.T. Analysis of Vulnerability of Groundwater Pollution and Space-Time Change in Xi’an City from 1985 to 2003. Ph.D. Thesis, Shaanxi Normal University, Xi’an, China, 2007; pp. 8–9. [Google Scholar]
- Feng, Q.S. Theoretical study on characteristics and quantification of oil and gas pipeline accidents. Oil Gas Storage Transp. 2017, 36, 369–374. [Google Scholar]
- Li, T.F. Disaster Geology; Peking University Press: Beijing, China, 2002. [Google Scholar]
- Zhang, S.F. Seismic Vulnerability Analysis for Bridge Structures with High Piers. Ph.D. Thesis, Southwest Jiaotong University, Chengdu, China, 2014. [Google Scholar]
- Yu, Q.X. Seismic Fragility Study of Bridge Based on Historical Damage Data. Ph.D. Thesis, Institute of Engineering Mechanics, China Earthquake Administration, Harbin, China, 2014. [Google Scholar]
- Chen, L.P. Seismic Vulnerability Analysis for Highway Bridges in Wenchuan Region. Ph.D. Thesis, Southwest Jiaotong University, Chengdu, China, 2012. [Google Scholar]
- Tian, S.J.; Kong, J.M.; Chen, Z.F. Vulnerability assessment of slope hazard based on function of highway. J. Earth Sci. Environ. 2013, 35, 119–126. [Google Scholar]
- Qi, H.L.; Tian, W.P.; Li, J.C. Vulnerability assessment of hazard-affected body of highway collapse disaster. J. Nat. Disasters 2013, 22, 160–166. [Google Scholar] [CrossRef]
- Yang, F.; Ma, C.; Fang, H.J. Research progress on vulnerability: From theoretical research to comprehensive practice. Acta Ecol. Sin. 2019, 39, 441–453. [Google Scholar]
- Zhao, R.D.; Fang, C.L.; Liu, H.M. Progress and prospect of urban resilience research. Prog. Geogr. 2020, 39, 1717–1731. [Google Scholar] [CrossRef]
- Ye, X.L.; He, Y.; Sun, R.H. Vulnerability and anti-vulnerability: Research progress and review of tourism resilience. Tour. J. 2023, 1–24. [Google Scholar] [CrossRef]
- Shuang, Q.; Liu, H.J.; Porse, E. Review of the Quantitative Resilience Methods in Water Distribution Networks. Water 2019, 11, 1189. [Google Scholar] [CrossRef]
- Wen, J.H.; Yan, J.P.; Wang, H.M.; Wang, J.; Dong, Q.; Gao, M.T.; Cheng, X.T.; Lv, Y.M. Integrated catastrophic disaster risk management of modern cities from the perspective of resilience. Urban Issues 2019, 76–82. [Google Scholar] [CrossRef]
- Shi, J.X.; Lu, D.N. Research on improving the resilience and safety level of industrial chain supply chain. Res. Financ. Issues 2023, 1–11. [Google Scholar] [CrossRef]
- Liu, H.J. Research on the Resilience of Urban Water Distribution Networks Based on Energy and Topology. Ph.D. Thesis, Beijing Jiaotong University, Beijing, China, 2021. [Google Scholar] [CrossRef]
- Zhang, J.J.; Su, H.; Gao, P. Resilience based supply assurance of natural gas pipeline networks and its research prospects. Acta Pet. Sin. 2020, 41, 1665–1678. [Google Scholar]
- Zhao, X.W. Study on Vulnerability Assessment of Urban Buried Natural Gas Pipeline. Ph.D. Thesis, Capital University of Economics and Business, Beijing, China, 2010. [Google Scholar]
- Cai, H.S.; Liu, S.M.; Li, F.Y.; Lin, L. Comparative analysis of static and dynamic evaluation of ecological frangibility. Acta Agric. Univ. Jiangxiensis 2009, 31, 149–155, 165. [Google Scholar]
- Wang, Z.J.; Su, Y. Analysis of Eco-environmental vulnerability characteristics of Hanzhong City, near the water source midway along the route of the south-to-north water transfer project, China. Acta Ecol. Sin. 2018, 38, 432–442. [Google Scholar]
- Zhang, X.Q.; Wang, L.K.; Fu, X.S.; Li, H.; Xu, C. Ecological vulnerability assessment based on PSSR in Yellow River Delta. J. Clean. Prod. 2017, 167, 1106–1111. [Google Scholar] [CrossRef]
- Dang, E.S.; Hu, W.J.; Chen, G.L.; Ma, Z.; Chen, B. Ecological vulnerability assessment of coastal zone in Dongshan county based on VSD model. Mar. Environ. Sci. 2017, 36, 296–302. [Google Scholar]
- Deng, W.; Yuan, X.Z.; Sun, R.; Zhang, Y.W. Eco-vulnerability Assessment Based on Remote Sensing in the Argo-pastoral Ecotone of North China. Environ. Sci. Technol. 2016, 39, 174–181. [Google Scholar]
- Zhang, L.S.; Li, P.; Zhang, J.Q. Analysis of ecological vulnerability and its major influencing factors in Gansu province. Chin. J. Agric. Resour. Reg. Plan. 2013, 34, 55–59. [Google Scholar]
- Zhou, S.X.; Tian, Y.P.; Liu, L.F. Analysis of Driving Forces of Agricultural Eco-environmental Vulnerability in the Hilly Area in Southern China: A Case Study in Hengyang Basin. Prog. Geogr. 2011, 30, 938–944. [Google Scholar]
- Ma, J.; Li, C.X.; Wei, H.; Ma, P.; Yang, Y.J.; Ren, Q.S.; Zhang, W. Dynamic evaluation of ecological vulnerability in the Three Gorges Reservoir Region in Chongqing Municipality, China. Acta Ecol. Sin. 2015, 35, 7117–7129. [Google Scholar]
- Zhang, F.; Liu, X.P.; Zhang, J.Q.; Wu, R.; Ma, Q.; Chen, Y. Ecological vulnerability assessment based on multi-sources data and SD model in Yinma River Basin, China. Ecol. Model. 2017, 349, 41–50. [Google Scholar] [CrossRef]
- Yu, Z.Y.; Li, B.; Zhang, X.S. Social ecological system and vulnerability driving mechanism analysis. Acta Ecol. Sin. 2014, 34, 1870–1879. [Google Scholar]
- Chen, M.Q.; Cai, H.S.; Zhao, X.M. On Spatial Differential Features of Fragile Eco-environment in Poyang Lake Area under GIS. Acta Agric. Univ. Jiangxiensis 2003, 25, 523–527. [Google Scholar]
- Li, T.Y. Spatial Vulnerability Based on the Framework of the Exposure-Sensitivity-Adaptive Capacity: A Case Study of Lanzhou. Econ. Geogr. 2017, 37, 86–95. [Google Scholar]
- Moss, R.H.; Malone, E.L.; Brenkert, A.L. Vulnerability to Climate Change: A Quantitative Approach; Prepared for the U.S. Department of Energy Under Contract DE-AC06-76RLO 1830; National Technical Information Service: Springfield, VA, USA, 2001. [Google Scholar]
- Cutter, S.L.; Boruff, B.J.; Shirley, W.L. Social Vulnerability to Environmental Hazards. Soc. Sci. Q. 2003, 84, 242–261. [Google Scholar] [CrossRef]
- Huang, F.; Liu, X.N.; Zhang, Y.Z. GIS-Based Eco-environmental Vulnerability Evaluation in West Jilin Province. Sci. Geogr. Sin. 2003, 23, 95–100. [Google Scholar]
- Feng, L.H.; Huang, Y.J. Comprehensive evaluation of fragility of ecological environment. Trop. Geogr. 2003, 23, 102–114. [Google Scholar]
- Wang, H.Y.; Liang, C. Research on the application of activity-based costing in cost control of iron and steel enterprises. J. Liaoning Univ. Petrochem. Technol. 2015, 35, 76–80. [Google Scholar]
- Xiong, W.; Wu, Y.M. Causality and impulse response on the relationship of China’s economic growth and environment fragility. Resour. Sci. 2006, 28, 17–23. [Google Scholar]
- Thirumalaivasan, D.; Karmegam, M.; Venugopal, K. AHP-DRASTIC: Software for specific aquifer vulnerability assessment using DRASTIC model and GIS. Environ. Model. Softw. 2003, 18, 645–656. [Google Scholar] [CrossRef]
- He, X.C.; Shao, D.G.; Chen, N.H. Research on partitioning of groundwater environmental vulnerability. Eng. J. Wuhan Univ. 2005, 38, 73–78. [Google Scholar]
- Zhang, L.; Li, C.J.; Su, X. Determination of Pipeline Risk Factor Weight by Fuzzy Analytic Hierarchy Process. Pet. Mach. 2006, 34, 43–45+3. [Google Scholar]
- Zhou, J.; Peng, J.H.; Sun, J.H. Study of the optimization of an injection and production scheme of gas storage in depleted gas reservoirs based on a fuzzy comprehensive evaluation method. Pet. Sci. Bull. 2021, 6, 494–504. [Google Scholar]
- Zhao, Y.X.; He, L.; Liu, S.D.; Liu, W.Q.; He, Y.; Zhang, J.P. Evaluation method of agro-ecosystem vulnerability. Chin. J. Ecol. 2007, 26, 754–758. [Google Scholar]
- Ni, S.H.; Gu, Y.; Wang, H.R. Study on frangibility zoning of agricultural drought in China. Adv. Water Sci. 2005, 16, 705–709. [Google Scholar]
- Wan, H.X.; Sun, Z.D.; Wang, R. Study on the evaluation of ecological frangibility of the wetlands in the Bosten Lake Region. Arid. Land Geogr. 2006, 29, 248–254. [Google Scholar]
- Dixon, B. Groundwater vulnerability mapping: A GIS and fuzzy rule based integrated too. Appl. Geogr. 2005, 25, 327–347. [Google Scholar] [CrossRef]
- Martino, F.D.; Sessa, S.; Loia, V. A fuzzy-based tool for modelization and analysis of the vulnerability of aquifers: A case study. Int. J. Approx. Reason. 2005, 38, 99–111. [Google Scholar] [CrossRef]
- Fan, Y.X.; Gao, P.H.; Wang, H.J. Theoretical model for fuzzy evaluation of vulnerability of regional hazard bearing body. J. Catastrophology 2003, 18, 20–23. [Google Scholar]
- Wang, H. Vulnerability Assessment and Protection Strategy of Urban Gas Pipeline. Ph.D. Thesis, Xi’an University of Architecture and Technology, Xi’an, China, 2018. [Google Scholar]
- Xue, Z.P.; Deng, H.; Yang, X.W.; Liu, C.L. Yield mapping analysis methods in precision agriculture based on decision-making tree modeling and map-overlapping. Trans. CSAE 2006, 22, 140–144. [Google Scholar]
- O’brien, K.; Leichenkob, R.; Kelkar, U.; Venema, H.; Aandahl, G.; Tompkins, H.; Javed, A.; Bhadwal, S.; Barg, S.; Nygaard, L.; et al. Mapping vulnerability to multiple stressors: Climate change and globalization in India. Glob. Environ. Chang. 2004, 14, 303–313. [Google Scholar] [CrossRef]
- Metzger, M.J.; Leemans, R.; Schröter, D. A multidisciplinary multi-scale framework for assessing vulnerabilities to global change. Int. J. Appl. Earth Obs. Geoinf. 2005, 7, 253–267. [Google Scholar] [CrossRef]
- Zhang, X.; Cai, H.J.; Wang, H.Q. The ecological environment vulnerability assessment with fuzzy matter-element model in Minqin oasis. Agric. Res. Arid. Areas 2009, 27, 195–199. [Google Scholar]
- Ma, D.M.; Chen, D.C. Application of fuzzy mater element model based on Euclid approach degree on vulnerability assessment of water resources. South–North Water Transf. Water Sci. Technol. 2015, 13, 1003–1007. [Google Scholar]
- Fan, R.N.; Bi, R.; Han, P.P.; Ju, F. Security evaluation of distribution network with PV base on fuzzy matter-element method. Electr. Energy Manag. Technol. 2016, 11, 28–33. [Google Scholar]
- Smith, E.R.; Tran, L.T.; O’neill, R.V. Regional Vulnerability Assessment for the Mid-Atlantic Region: Evaluation of Integration Methods and Assessments Results; EPA Regional Vulnerability Assessment Program, EPA/600/R-03/082; U.S. Environmental Protection Agency: Washington, DC, USA, 2003. [Google Scholar]
- He, J.Q. Discussion on vulnerability assessment of urban natural gas pipeline. Mod. Prop. Manag. 2011, 10, 116–117. [Google Scholar]
- Taleb, N.N. Anti-Fragility; China CITIC Press: Beijing. China, 2014; pp. 38–39. [Google Scholar]
- Inanloo, B.; Tansel, B.; Shams, K.; Jin, X.; Gan, A. A decision aid GIS-based risk assessment and vulnerability analysisapproach for transportation and pipeline networks. Saf. Sci. 2016, 84, 57–66. [Google Scholar] [CrossRef]
- Liu, K.; Wang, M.; Zhu, W.H.; Wu, J.; Yan, X. Vulnerability analysis of an urban gas pipeline networkconsidering pipeline-road dependency. Int. J. Crit. Infrastruct. Prot. 2018, 23, 79–88. [Google Scholar] [CrossRef]
- Ni, P.P.; Mangalathu, S. Fragility analysis of gray iron pipelines subjected to tunneling induced ground settlement. Tunn. Undergr. Space Technol. 2018, 76, 133–144. [Google Scholar] [CrossRef]
- Ni, P.P.; Mangalathu, S.; Liu, K.W. Enhanced fragility analysis of buried pipelines through Lasso regression. Acta Geotech. 2020, 15, 471–487. [Google Scholar] [CrossRef]
- Fu, R. Study on Safety Assessment and Protective Measures of Overhanging Section of Gas Pipeline across Water Area. Ph.D. Thesis, Southwest Petroleum University, Chengdu, China, 2016. [Google Scholar]
- Wang, J.L. Vulnerability Analysis of Long-Distance Oil and Gas Pipelines. Ph.D. Thesis, Beijing University of Chemical Technology, Beijing, China, 2020. [Google Scholar]
- Chen, S.; Zhao, D.F.; Jiang, X.; An, C.; Hu, S. Research on vulnerability evaluation indicator of oil and gas pipeline based on ISM. In Proceedings of the Hazardous Chemicals Pipeline Safety Management and Technology—The Second CCPS China Process Safety Conference, Qingdao, China, 27 August 2014; pp. 277–283. [Google Scholar]
- Hou, Q.; Gao, L.W.; Tao, G.Q.; Lv, M.; Zhang, C. Structure vulnerability research for regional drainage pipes. J. Qingdao Technol. Univ. 2015, 36, 59–64+94. [Google Scholar]
- Zhao, D.F.; Chen, S.; Zhao, Z.Q. Study on oil-gas pipeline risk assessment method based on vulnerability and its application. China Saf. Sci. J. 2014, 24, 57–62. [Google Scholar]
- Wang, X.H.; Qu, A.; Xu, Y.L.; Yang, H.R.; Meng, T. Vulnerability Assessment Technique for City PE Gas Pipeline System. Geol. Sci. Technol. Inf. 2016, 35, 37–40. [Google Scholar] [CrossRef]
- Shu, C. Study on Safety Evaluation Technology of Gas Pipeline Buried in Geological Crossing Fault. Ph.D. Thesis, Southwest Petroleum University, Chengdu, China, 2018. [Google Scholar]
- Wang, W.C.; Zhang, Y.; Li, Y.X.; Liu, C.; Han, S. Vulnerability analysis of natural gas pipeline networks based on risk theory. Oil Gas Storage Transp. 2022, 41, 42–47. [Google Scholar]
- Huang, X.Z.; Xie, X.P. Analysis and evaluation of vulnerabilities of gas transmission pipeline. Gas Heat 2018, 28, 5–10. [Google Scholar]
- Zhao, X.W.; Chai, J.S. Study on indicators of vulnerability assessment for city buried gas pipeline system. J. Saf. Sci. Technol. 2011, 7, 92–96. [Google Scholar]
- Dou, J.H. Oil pipeline vulnerability evaluation based on fuzzy comprehensive evaluation method. Oil-Gas Field Surf. Eng. 2016, 35, 20–23. [Google Scholar]
- Cui, Y.H.; Cui, Y.D.; Li, H.X.; Zhou, N.; Shi, P.; Tang, W.W.; Xie, H. Vulnerability analysis and evaluation for urban gas pipeline network system. J. Chongqing Univ. Sci. Technol. (Nat. Sci. Ed.) 2012, 14, 87–89+96. [Google Scholar]
- Zhao, L.; Yi, J.; Wang, W.H. Evaluation methods and their application to meet the challenge of the urban gas network vulnerability. J. Saf. Environ. 2015, 15, 68–72. [Google Scholar]
- Wang, X.M. Risk Evaluation of Municipal Buried Gas Pipeline. Ph.D. Thesis, Nanjing University of Technology, Nanjing, China, 2006. [Google Scholar]
- Li, F.; Yi, J.; Wang, W.H.; Zuo, D.R. Study on vulnerability evaluation of oil pipeline for CO2 flooding reservoir based on SVM. J. Saf. Sci. Technol. 2015, 11, 157–163. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).