IEC 62443 Standard for Hydro Power Plants
Abstract
:1. Introduction
1.1. Motivation
1.2. Literature Review
1.3. Contribution
2. Conceptualization
2.1. Safety vs. Security
2.2. Risk Analysis
2.3. HAZOP vs. Cyber-HAZOP
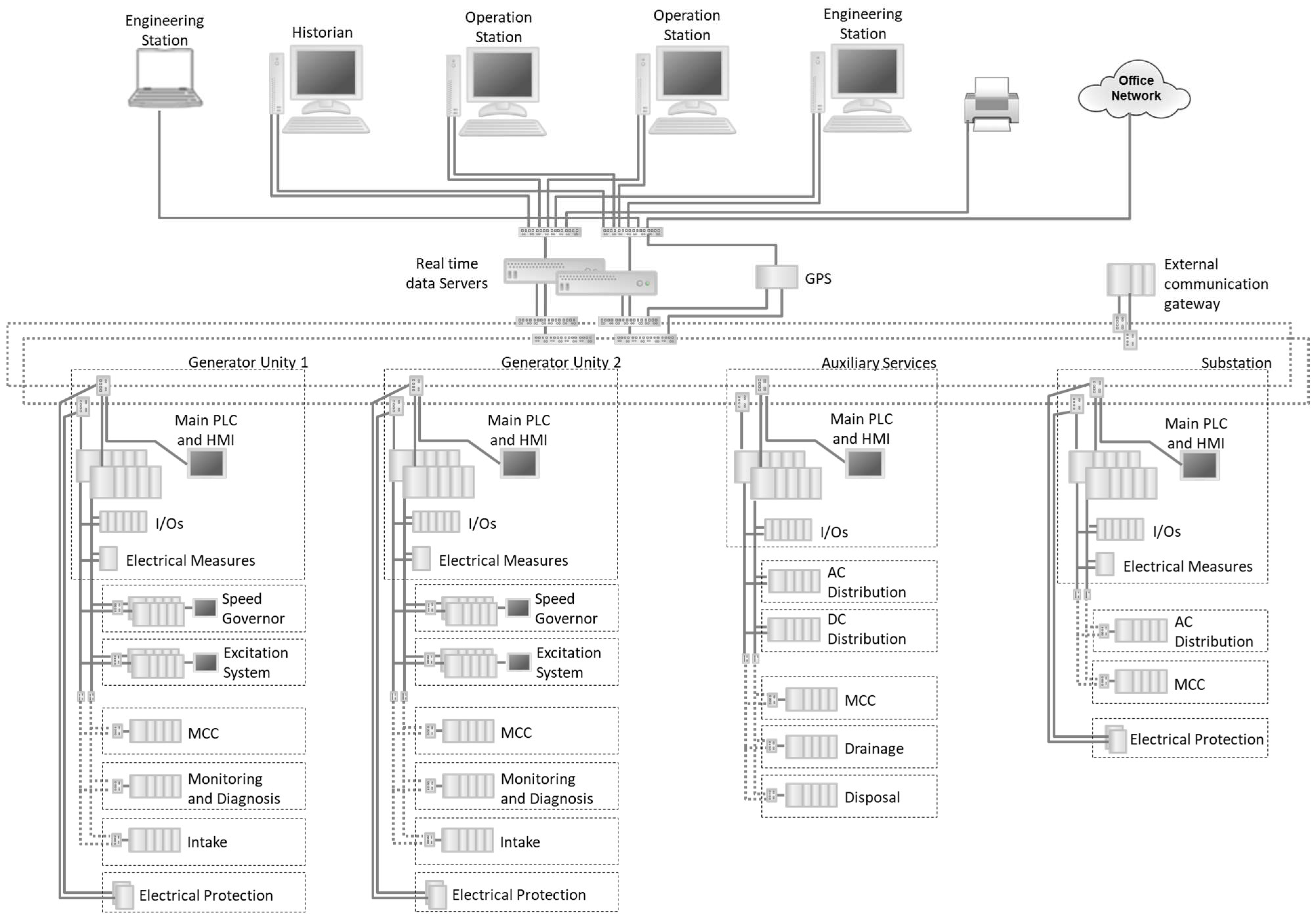
2.4. Hydro Power Plants Systems and Its Vulnerabilities
3. CSMS Application Guide for HPP’s According to IEC 62443
3.1. Initiate CSMS Program
- What is the expected result taking into consideration that a CSMS does not generate ROI (return of investment)?
- Are there financial resources in short term to enable the application of resulting countermeasures?
- Are there financial resources available in short, medium, and long term for the maintenance of the CSMS?
- Are there specialists available for each HPP system that can participate in the detailed risk assessment?
- Is it possible to initiate the CSMS only by reallocation of personnel activities or is it necessary to contract new personnel?
- Will the program be applied only by internal efforts, or will there be third-part suppliers?
- Will the CSMS be developed for a single HPP or for a group of them? Will reference automation architecture be developed?
- What is the timeline expectation? Is it feasible?
3.2. High Level Risk Assessment
- Which HPP’s systems can cause personnel injury in case of inadequate operation?
- Which HPP’s systems can cause environmental damage in case of inadequate operation?
- Which HPP’s systems can cause equipment damage in case of inadequate operation?
- What is the impact on company’s reputation due to a well succeeded cyberattack?
- What is the financial and social impact if one or more generator unities stop working due to a successful cyber attack?
- What is the actual and pretended risk tolerance?
- How is the IT × OT integration? Which team acts in case of incidents?
- What does the governments agents require regarding cyber security in critical infrastructures?
3.3. Detailed Risk Assessment
- Is there an incident database to guide systems prioritization?
- Is there a safety risk analysis that can be adapted to a security risk analysis?
- How many defence layers will be applied for priority systems?
- What is the impact of the countermeasures on the systems?
3.4. Establish Policies, Procedures and Awareness
- What kind of trainings will be created: theoretical, practical or both?
- Which personnel should be involved: IT, OT, or both? From which specialty?
- Will an external company be hired for specific trainings?
- Will there be mandatory trainings? What will be the frequency?
- How will be the means of divulgation of the new policies and procedures inside the HPP?
- How will the integration between IT and OT departments be approached in the policies, procedures, and awareness program?
- What will be the frequency of policies and procedures revision?
- Will there be mandatory policies and procedures?
3.5. Select and Implement Countermeasures
- Will it be given emphasis for internal or externa attacks for the HPP under consideration (intentional or unintentional)?
- Can the selected countermeasures be implemented in a single step or is it necessary to divide the implementation in more steps due to financial restrictions?
- Recent cyber attack cases in similar plants occurred due to what kind of lack of security?
- What are the existing safeguards for the worst-case consequences? Is it possible to improve by applying more defence layers?
3.6. Maintain the CSMS
4. Study Case for a Typical HPP
4.1. Methodology and Contextualization
4.2. Initiate CSMS Program
- Electrical maintenance and operation;
- Mechanical maintenance and operation;
- Electrical engineering;
- Mechanical engineering;
- Automation engineering;
- Information technology;
4.3. High Level Risk Assessment
4.4. Detailed Risk Assessment
- Plant personnel would not attack or pass information to outside attackers intentionally because besides it is easier to detect, and, in the case of a dangerous incident, they would be exposed to possible injuries, so it is assumed that the leak of internal information is due to social engineering, reinforcing the need of trainings and awareness.
- Differently from process data that contains industrial secrets, it is assumed that data from a HPP is not the focus, reducing the need of defence layers related to data itself. Before applying solutions such as deep packet inspection (DPI), other defence layers would be priority.
- Taking the previous premises into consideration, it is presumed that the focus of a cyber attack on a HPP is to take control of the substation and/or generator unities to turn the system down, in other words, it is assumed that it would be an attack more similar to Blackenergy than to Stuxnet.
4.5. Establish Policies, Procedures and Awareness
4.5.1. Awareness Trainings
4.5.2. Policies and Procedures
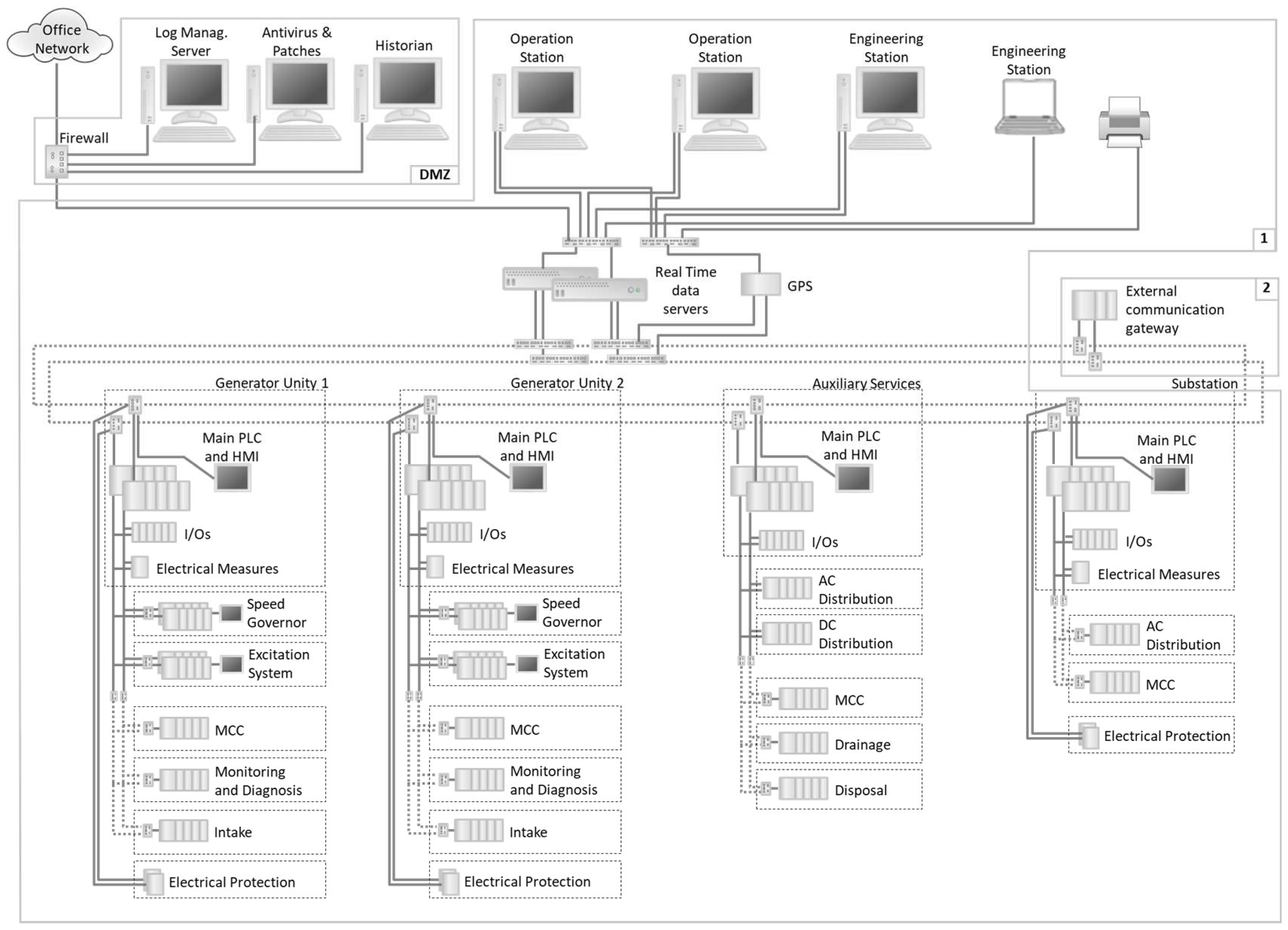
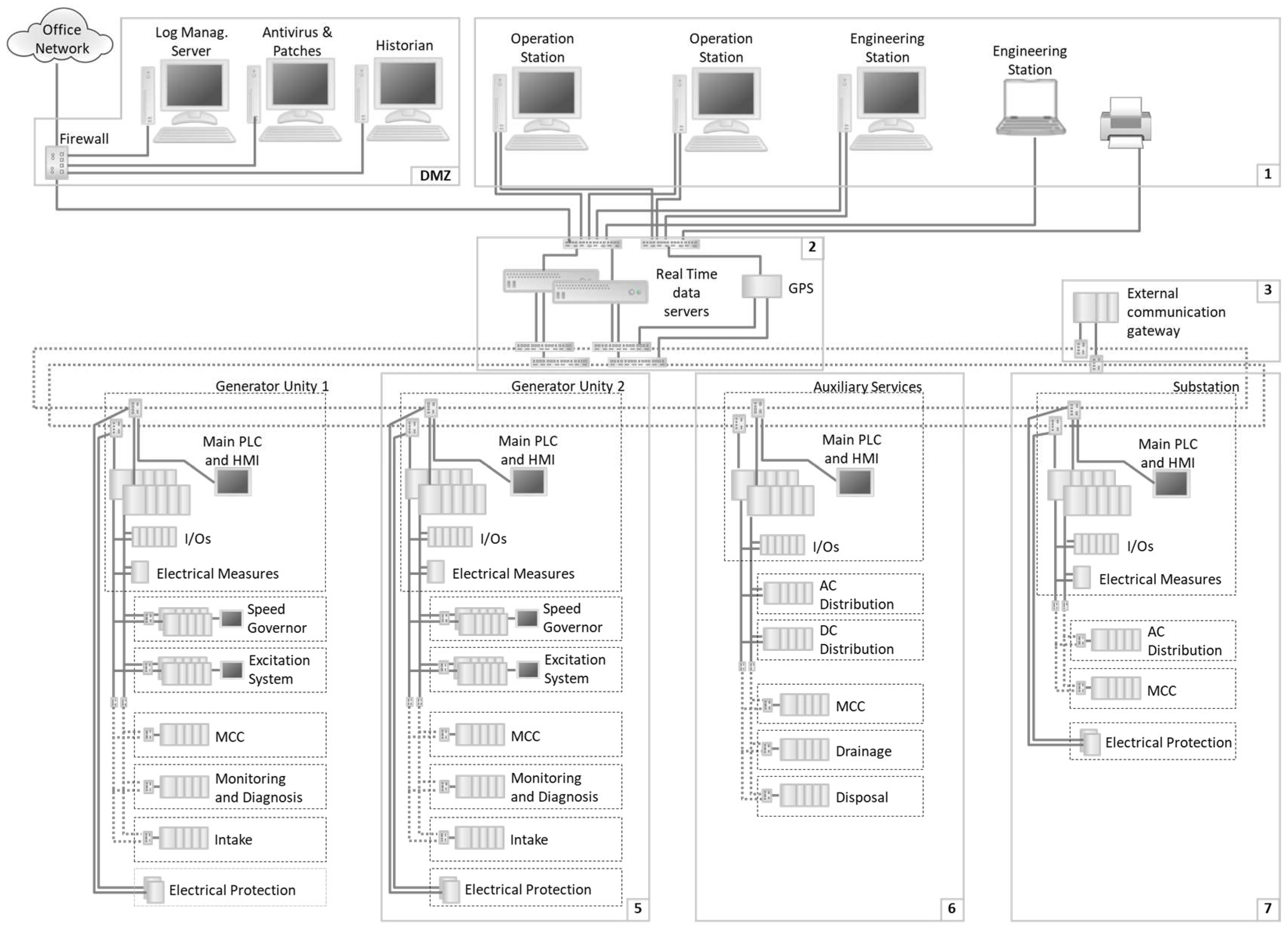
4.6. Select and Implement Countermeasures
- Division into security cells protected through firewall to control activities that occur within and between then.
- Inclusion of a server with security functionalities: antivirus and Windows patches.
- Inclusion of a centralized log management system.
- Configuration of a DMZ (demilitarized zone) to limit data flow from process to office network containing the historian server, antivirus, Windows patch update server, and log management server.
- Supervisory system;
- Communication link with operation centre or regulation agent;
- Communication between process data and office network;
- Network equipment;
- Electrical protection system;
- Controllers.
5. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Gopstein, A.; Nguyen, C.; O’Fallon, C.; Hastings, N.; Wollman, D.A. NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release 4.0, Special Publication (NIST SP); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021. Available online: chrome-extension://efaidnbmnnnibpcajpcglclefindmkaj/https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.1900-206.pdf (accessed on 27 December 2022).
- Jahil, A.A.A.; Giarratano, D. Improvement of Cyber-Security Measures in National Grid SA Substation Process Control; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2017. [Google Scholar]
- Faquir, D.; Chouliaras, N.; Sofia, V.; Olga, K.; Maglaras, L. Cyber Security in Smart Grid: Challenges and Solutions; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2019; pp. 546–551. [Google Scholar]
- Alsuwian, T.; Shahid Butt, A.; Amin, A.A. Smart Grid Cyber Security Enhancement: Challenges and Solution—A Review. Sustainability 2022, 14, 14226. [Google Scholar] [CrossRef]
- Backes, M.; Keefe, K.; Valdes, A. A Microgrid Ontology for the Analysis of Cyber-Physical Security; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2017. [Google Scholar]
- Ang, C.K.G.; Utomo, N.P. Cyber Security in the Energy World; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2017; pp. 1–5. [Google Scholar]
- Buyuk, O.O.; Camurcu, A.Y. A Novel Actual Time Cyber Security Approach to Smart Grids; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2018. [Google Scholar]
- Chobanov, V.; Doychev, I. Cyber Security impact on energy systems. In Proceedings of the 2022 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 9–11 June 2022; pp. 1–5. [Google Scholar]
- Liu, Y.; Qin, H.; Chen, Z.; Shi, C.; Zhang, R.; Chen, W. Research on Cyber Security Defense Technology of Power Generation Acquisition Terminal in New Energy Plant; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2019; pp. 25–30. [Google Scholar]
- Chen, Y.C.; Mooney, V.; Grijalva, S. Grid Cyber-Security Strategy in An Attacker-Defender Model; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020. [Google Scholar]
- Chen, Y.; Li, J.; Lu, Q.; Lin, H.; Xia, Y.; Li, F. Cyber security for multi-station integrated smart energy stations: Architecture and solutions. Energies 2021, 14, 4287. [Google Scholar] [CrossRef]
- IEC 62443-2-1; Industrial Communication Networks–Network and System Security—Part 2-1: Establishing an Industrial Automation and Control System Security Program. IEC: Geneva, Switzerland, 2010.
- IEC 62443-1-1; Industrial Communication Networks–Network and System Security—Part 1-1: Terminology, Concepts and Models. IEC: Geneva, Switzerland, 2009.
- Nolan, D.P. Safety and Security Review for the Process Industries–Application of HAZOP, PHA, What-If and SVA Reviews; Elsevier: Amsterdam, The Netherlands, 2014. [Google Scholar]
- Marszal, E. Security process hazard analysis review. ISA InTech Mag. 2016. Available online: https://www.isa.org/intech-home/2016/march-april/features/security-process-hazard-analysis-review (accessed on 24 November 2022).
- Knapp, E.D.; Langill, J.T. Industrial Network Security–Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems; Syngress: Rockland, MA, USA, 2015. [Google Scholar]
- Heluany, J.B. Application of Cyber Security Standards in HPPs. Master’s Thesis, University of São Paulo, São Paulo, Brazil, 2018. [Google Scholar]


| Paper title | Use Case Domain | NIST Domain | Cyber Security Approach |
|---|---|---|---|
| A microgrid ontology for the analysis of cyber-physical security | Microgrid | Generation; Distribution; | Attack vs. Defence |
| A novel actual time cyber security approach to smart grids | Substation | Distribution | Network security |
| Cyber security for multi-station integrated smart energy stations: Architecture and solutions | Smart Energy Stations (SESs) | Generation; Distribution; | Security management system |
| Cyber Security impact on energy systems | Virtual Power Plant (VPP) | Generation; | Risk vs. Mitigation; People management; |
| Cyber Security in the smart grid: challenges and solutions | Smart Grid | All | Risk vs. Mitigation |
| Cyber security in the energy world | Smart Grid | All | Network security |
| Grid cyber security strategy in an attacker–defender model | Power grid infrastructure | Distribution; | Attack vs. Défense |
| Improvement of cyber-security measures in national grid SA substation process control | Substation | Distribution; | Risk vs. Mitigation |
| Research on cyber security defence technology of power generation acquisition terminal in new energy plant | Power generation acquisition terminal | Generation; | Attack vs. defence |
| Smart grid cyber security enhancement: Challenges and solutions: a review | Smart Grid | All | Risk vs. Mitigation |
| Activity | Supplier |
|---|---|
| Engineering, tests, and commissioning of field network, process network, and supervisory system | Suppliers of automation and control systems |
| Communication between process data and office network | Suppliers of automation and control systems or information technology with customer participation, possibly involving IT and OT teams to support the activity |
| Communication link for remote access | Suppliers of automation and control systems or information technology with customer participation, possibly involving IT and OT teams to support the activity |
| Communication link with regulation agent | Automation and control systems suppliers generally subcontract telecommunications companies for this scope. Customer participation can involve IT and OT teams to support the activity. |
| Category | Potential Vulnerabilities |
|---|---|
| Supervisory System | Poor physical security; lack of system hardening; inadequate security awareness; poor password policies; poor account management; social engineering susceptibility; lack of patch management; lack of authentication; zero-day vulnerabilities; ineffective anti-virus/application whitelisting; insufficient access control; use of vulnerable ICS protocols; untested third-party applications; insecure embedded applications; |
| Communication link with operation centre or regulation agent | Poor physical security; lack of system hardening; inadequate port security; lack of authentication; unnecessary firewall rules; lack of patch/firmware management; poor configuration management; configuration errors; |
| Communication between process data and office network | Poor physical security; lack of system hardening; inadequate port security; lack of authentication; unnecessary firewall rules; poor configuration management; lack of patch/firmware management; configuration errors; uncontrolled file sharing; |
| Network equipment | Poor physical security; configuration errors; poor configuration management; inadequate port security; lack of firmware management; unnecessary firewall rules; lack of intrusion detection capabilities; use of vulnerable ICS protocols; |
| Electrical protection system | Poor physical security; lack of firmware management; configuration errors; poor configuration management; lack of authentication; use of vulnerable ICS protocols; |
| Controllers | Poor physical security; lack of system hardening; lack of firmware management; untested application integration; configuration errors; poor configuration management; lack of authentication; use of vulnerable ICS protocols; |
| Topic | Decision |
|---|---|
| Business plan | Enough investment for a dedicated team and for the implementation of a CSMS in this pilot plant. |
| CSMS scope | Complete automation architecture with selection of priority countermeasures according to the established risk tolerance and detailed risk analysis to be performed. |
| Stakeholders | Head office of the electrical company, regional unities, services, and product providers. |
| Organization support | Full support of all organization, given that cyber security has become a priority in the company’s strategy. |
| Subsystem | Guideword | Param. | Deviation | Possible Causes | Conseq. | P | S | R | Existing Safeguards |
|---|---|---|---|---|---|---|---|---|---|
| Excitation system | No/Low | Isolation | Low or inexistent isolation | Dust on the generator brushes. Damage in the internal equipment of the excitation system that are connected to the power electronics circuits. | Unity stops | 0.1 | 5.0 | 0.5 | SCADA alarm. Protection relay 64R |
| Excitation system | No | Control ystem | Control system out of work | CLP damage. Cabling failure. Failure on the 125Vcc powering system | Unity stops | 0.1 | 3.0 | 0.3 | Control system redundancy |
| Topic | Content |
|---|---|
| Risks, threats and vulnerabilities | Conceptual definitions and approach of risks associated to the HPP’s cyber assets. |
| Risk analysis | Conceptual definitions of the risk analysis utilized in the HPP (cyberHAZOP) to prepare the team for continuous documentation revision. |
| Standards | General view of the main international standards used as base for the HPP’s policies: NERC CIP, IEC 62443 and NIST 800-82. |
| Social Engineering | Focus on behaviour issues exemplifying well succeeded social engineering attacks to promote awareness and improve the level of responsibility when dealing with internal data |
| Topic | Content |
|---|---|
| Use of removable media | Policy describing allowed and forbidden attitudes and its respective procedures. If the utilization of removable media is absolutely necessary, before being connected to the system, it must be verified and sanitized |
| Backup | All applicable systems must have an associated document with the backup procedure, which must be conducted every three months or when some change is applied |
| Restore | The restore procedure must be tested every 12 months for all applicable systems. Examples: PLCs multi-project, servers’ images, historian data, operation station images, devices configuration (e.g., firewall and protection relays), among others |
| Incidents | Incident report policy containing a procedure to be followed in case of compromised systems |
| Change | Change management policy with examples and templates to keep the documentation always in the last revision. |
| Inventory | Inventory policy containing a template document. The inventory procedure must be revised each 12 months or in case of change for both physical and cyber assets. |
| Patches | Patch management policy and related procedures focusing relevant systems to keep the plant safe. Only security patches should be applied for whatever system: Windows platforms, firmware, or automation software. The CSMS responsible must verify available patches every week and filter the applicable ones to include in the updates planning |
| Access control | Access control policy for both physical and cyber assets according to minimum privilege philosophy. Access levels must be documented with responsible names and the document must be revised every six months or in case of change |
| Logs | Policy describing which logs should be monitored for each system |
| Controllers | ||||
|---|---|---|---|---|
| Item | Description | Yes | No | Comments |
| 1 | Physical security: allocation of controllers inside cabinets with access control | |||
| 2 | Hardening: disable non-utilized functionalities | |||
| 3 | Hardening: disable logical and physical (USB and others) nonutilized ports. | |||
| 4 | Firmware: guarantee that the device is running with the last homologated firmware version | |||
| 5 | Configuration: keep the controllers configuration tool with physical access control and restrict users able to change configurations | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Heluany, J.B.; Galvão, R. IEC 62443 Standard for Hydro Power Plants. Energies 2023, 16, 1452. https://doi.org/10.3390/en16031452
Heluany JB, Galvão R. IEC 62443 Standard for Hydro Power Plants. Energies. 2023; 16(3):1452. https://doi.org/10.3390/en16031452
Chicago/Turabian StyleHeluany, Jessica B., and Ricardo Galvão. 2023. "IEC 62443 Standard for Hydro Power Plants" Energies 16, no. 3: 1452. https://doi.org/10.3390/en16031452
APA StyleHeluany, J. B., & Galvão, R. (2023). IEC 62443 Standard for Hydro Power Plants. Energies, 16(3), 1452. https://doi.org/10.3390/en16031452






