1. Introduction
Solar energy is characterized as non-polluting, renewable, cheap and easy to obtain, thus considered to be an effective solution for energy shortage and environmental pollution caused by industrial and economic development [
1]. A photovoltaic (PV) system is a collection device of solar energy that converts solar energy into electrical energy, which has attracted great attention from scholars. In order to better design and apply fault diagnosis [
2] and maximum power-point-tracking control [
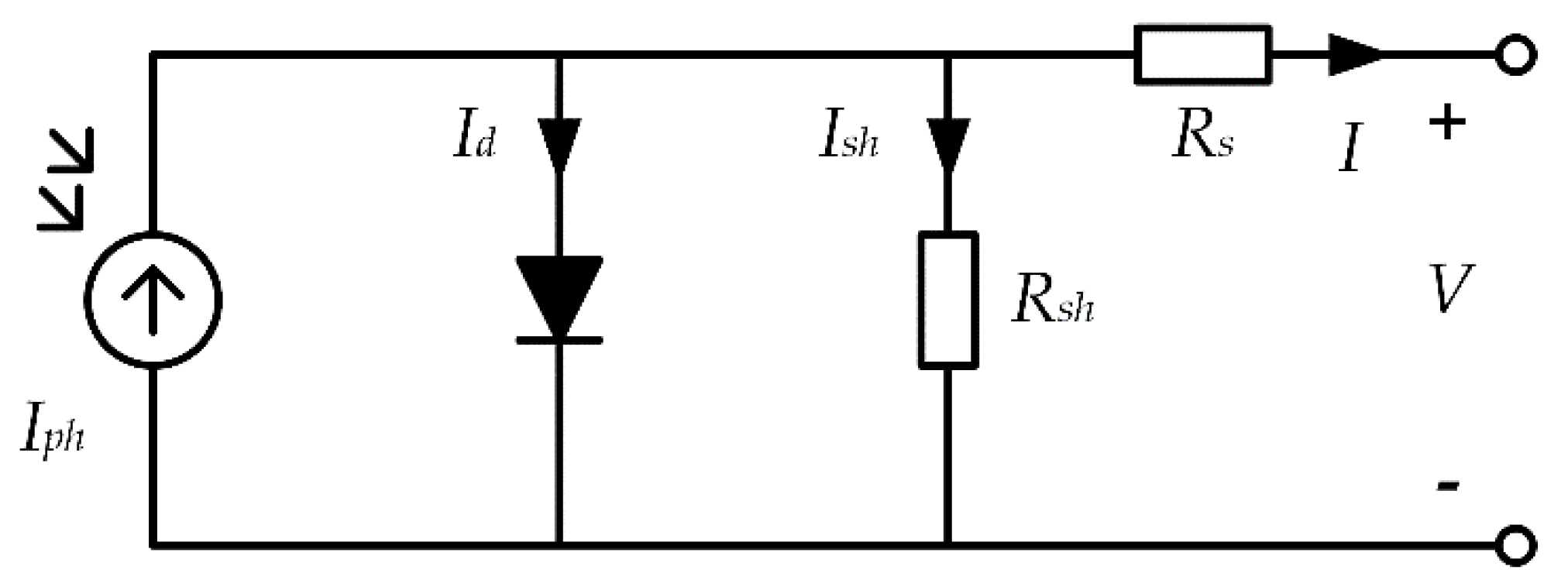
3] and other technologies of a PV system, it is very important to establish a mathematical model that can describe the current–voltage relationship in PV systems with high accuracy. In recent years, scholars at home and abroad have conducted a lot of research on the output characteristic models of PV system. The most commonly seen ones are the single-diode model (SDM) [
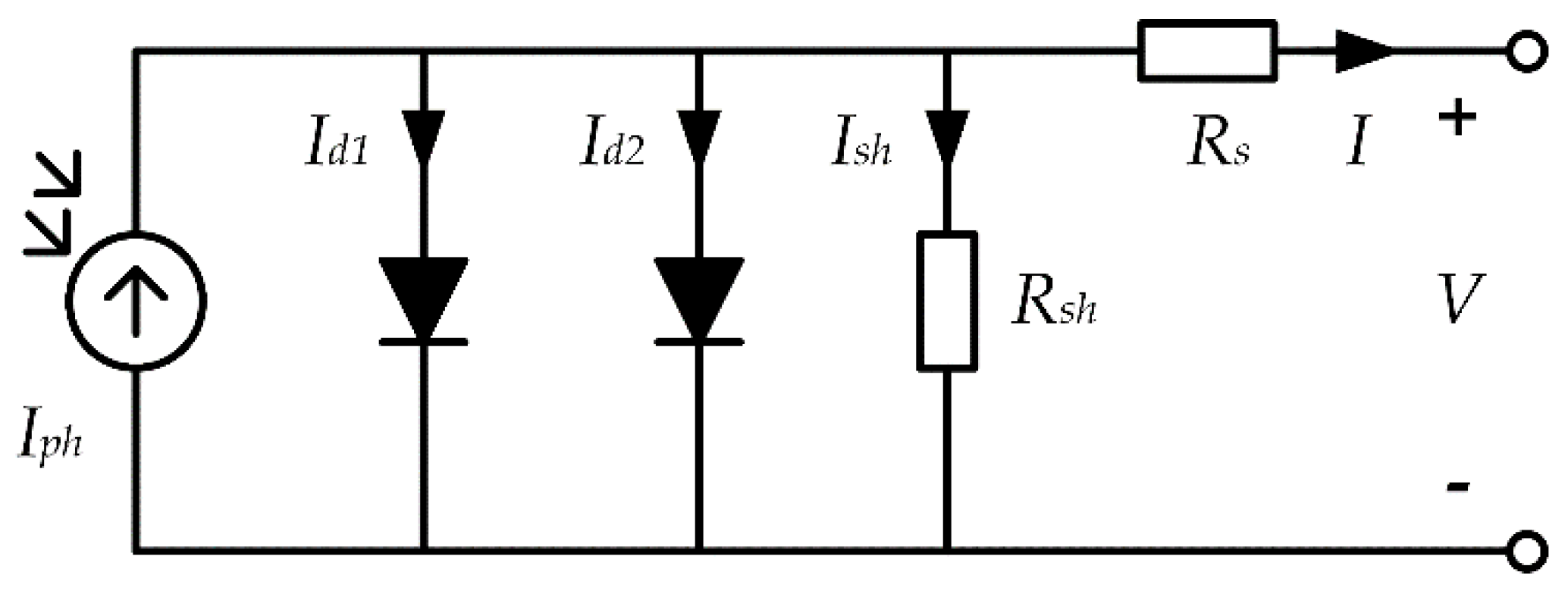
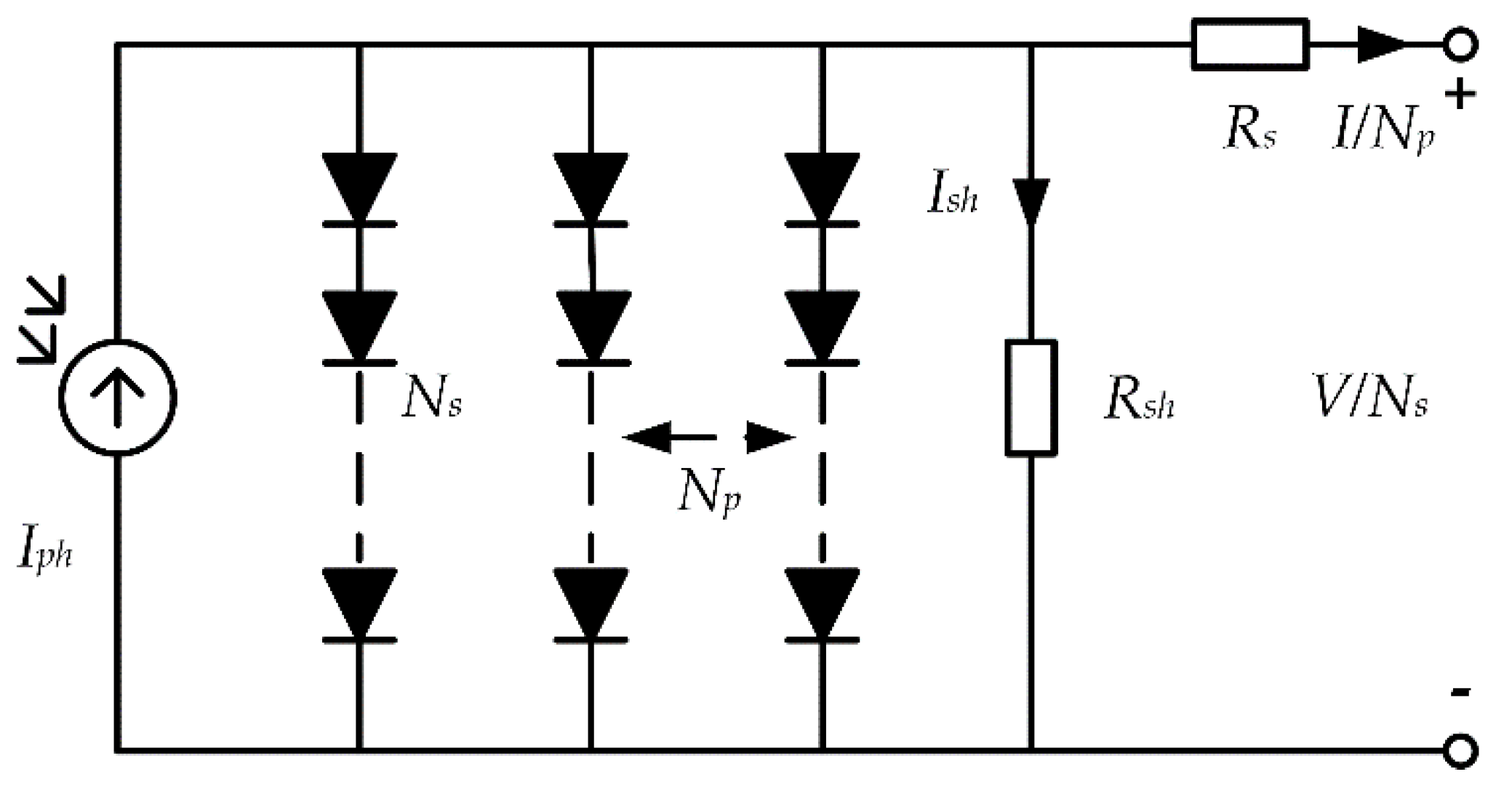
4], the double-diode model (DDM) and the PV module model [
5,
6]. The accuracy of a PV model mainly depends on its model parameters, whose availability usually decreases due to aging, faults and unstable operating conditions. Therefore, accurate, stable and efficient identification of these PV model parameters is crucial for the evaluation, optimization and control of PV models. Parameter identification for a PV system model can be regarded as a function optimization problem, but because its search space is nonlinear and multi-modal, it is easy to fall into local optimum in the solution, which puts forward higher requirements for the solution [
7].
The characteristics of swarm intelligence are clearly manifested in the behavior of organisms that adjust themselves according to the perceived information. Swarm intelligence is the information interaction between biological individuals, groups and environments that follow simple rules, and the characteristics of intelligence emerge as a whole. With the deepening of relevant research on Swarm Intelligence (SI), particle swarm optimization (PSO) [
8], artificial fish swarm algorithm (AFSA) [
9], ant colony algorithm [
10], bacterial colony algorithm [
11], artificial bee colony algorithm (ABC) [
12], wolf pack algorithm [
13] and their corresponding improved algorithms [
14,
15,
16] have been proposed successively. Simple, robust, adaptable and applicable to wide ranges, these algorithms are effective ways to solve all kinds of complex optimization problems and have also been widely used for model parameter identification of a PV system [
17,
18,
19,
20,
21,
22,
23,
24,
25]. Ref. [
22] proposes a particle swarm algorithm (Classified Perturbation Mutation based Particle Swarm Optimization, CPMPSO) to seek solution for perturbation variation classification of PV system model parameter identification. It uses the damping constraint processing strategy to avoid falling into local optimization. Ref. [
23] proposes a Logistic Chaotic Java to solve the parameter identification problem. The Logistic chaotic mapping strategy is introduced in the update stage of the algorithm to improve the population diversity. At the same time, the chaotic mutation strategy is introduced in the search stage to balance the search and exploration ability of the algorithm, but it also turns out to be easy to fall into local optimization in the later stage of the algorithm. Ref. [
24] introduces the multiple learning backtracking search algorithm (MLBSA) for parameter identification of different PV models. Xu Yan et al. [
25] propose a PV model parameter identification method based on a hybrid leapfrog algorithm. The update strategy of this method is directional and has strong local search ability, which can effectively solve the problem that the algorithm is easy to fall into local optimum. However, the solution steps of the algorithm are relatively complex, and the solution time is long. The intelligent optimization algorithm and its improved algorithm can globally optimize the parameters of a PV model on the basis of a small amount of experimental data, achieving satisfactory results with high precision and small errors, which can effectively meet the actual needs of some projects. However, due to the limitations of the algorithm’s own optimization mechanism, it is difficult for most algorithms to find the exact global optimal solution in practice. Therefore, it is still a challenge to design a highly competitive intelligent optimization algorithm to identify the parameters of a PV system model.
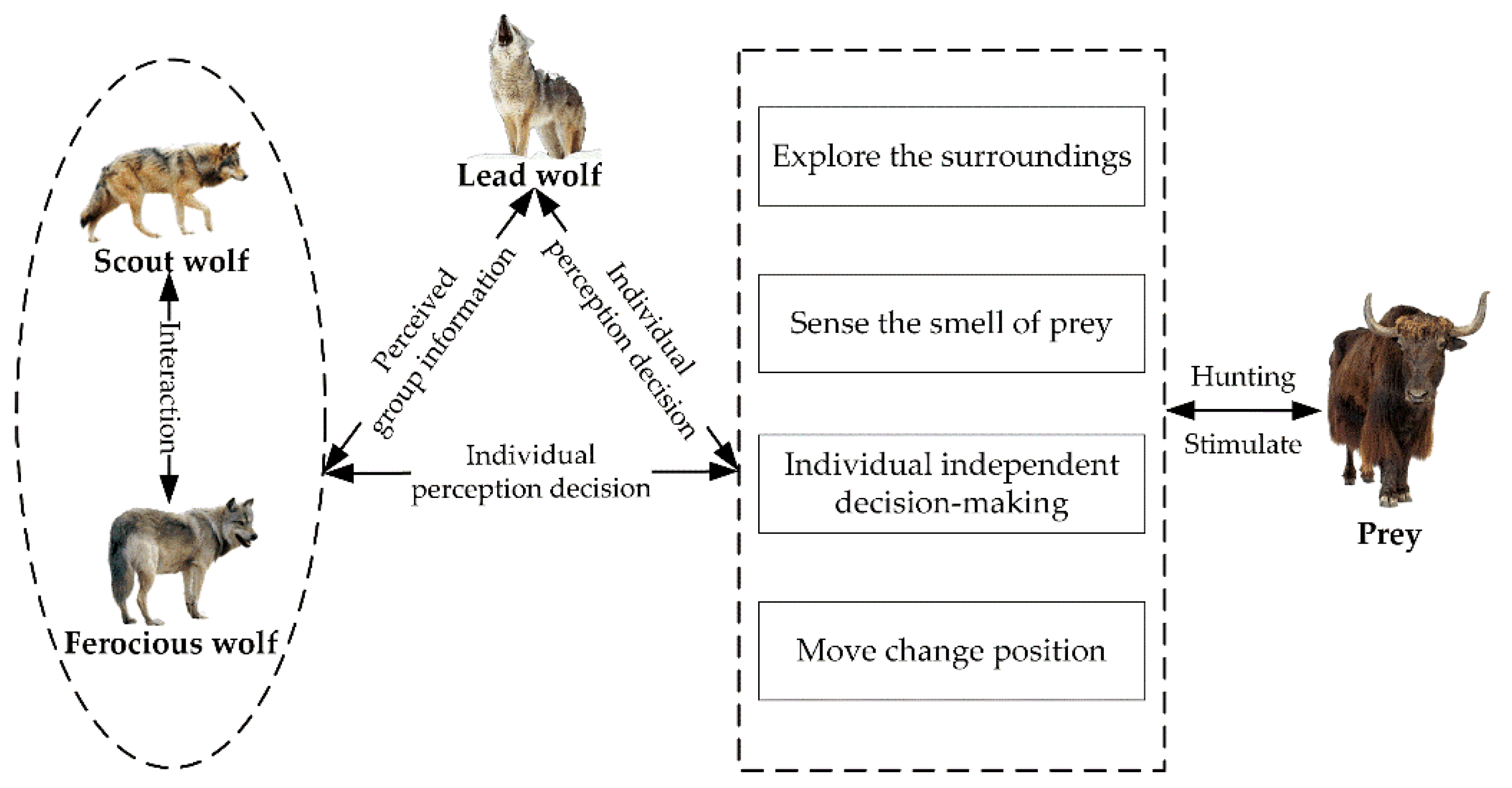
Wolf pack is a type of biological population with strong cognitive ability and rigorous social organization structure. Confronted with the “survival of the fittest” rule in a harsh environment, they have formed extremely sophisticated and efficient group intelligence behaviors such as cooperative hunting, enemy defense, reproduction, child rearing, etc. They have clear social class and labor division, and the group has demonstrated high intelligence features. Therefore, Yang et al. [
26] propose a wolf swarm search algorithm based on the hunting behavior of wolves, which provides a better idea for solving complex problems. In 2013, Wu Husheng et al. [
13] deeply analyzed the roles and behaviors of wolves in wolf pack hunting and designed a new wolf pack algorithm (WPA) based on the two rules of “winner as the king” and “survival of the strong” and the three behaviors of “walk, summon and siege”. The algorithm has good performance in global search and local exploration and shows great advantages in solving efficiency. It has been widely used in solving many practical problems such as 0–1 knapsack problem [
27], TSP problem [
28] and the path optimization problem [
29]. Moreover, many scholars have improved the WPA in practical application in terms of too many parameters, high consumption of computing resources, long computing time and being easy to fall into local optimization, etc., and put forward a large number of improved algorithms [
30,
31,
32,
33,
34]. Although a large number of improved algorithms have been proposed, the WPA is still rarely used for solving practical complex engineering problems, such as parameter identification of a PV model, and its efficiency and accuracy for solving complex optimization problems need to be further improved.
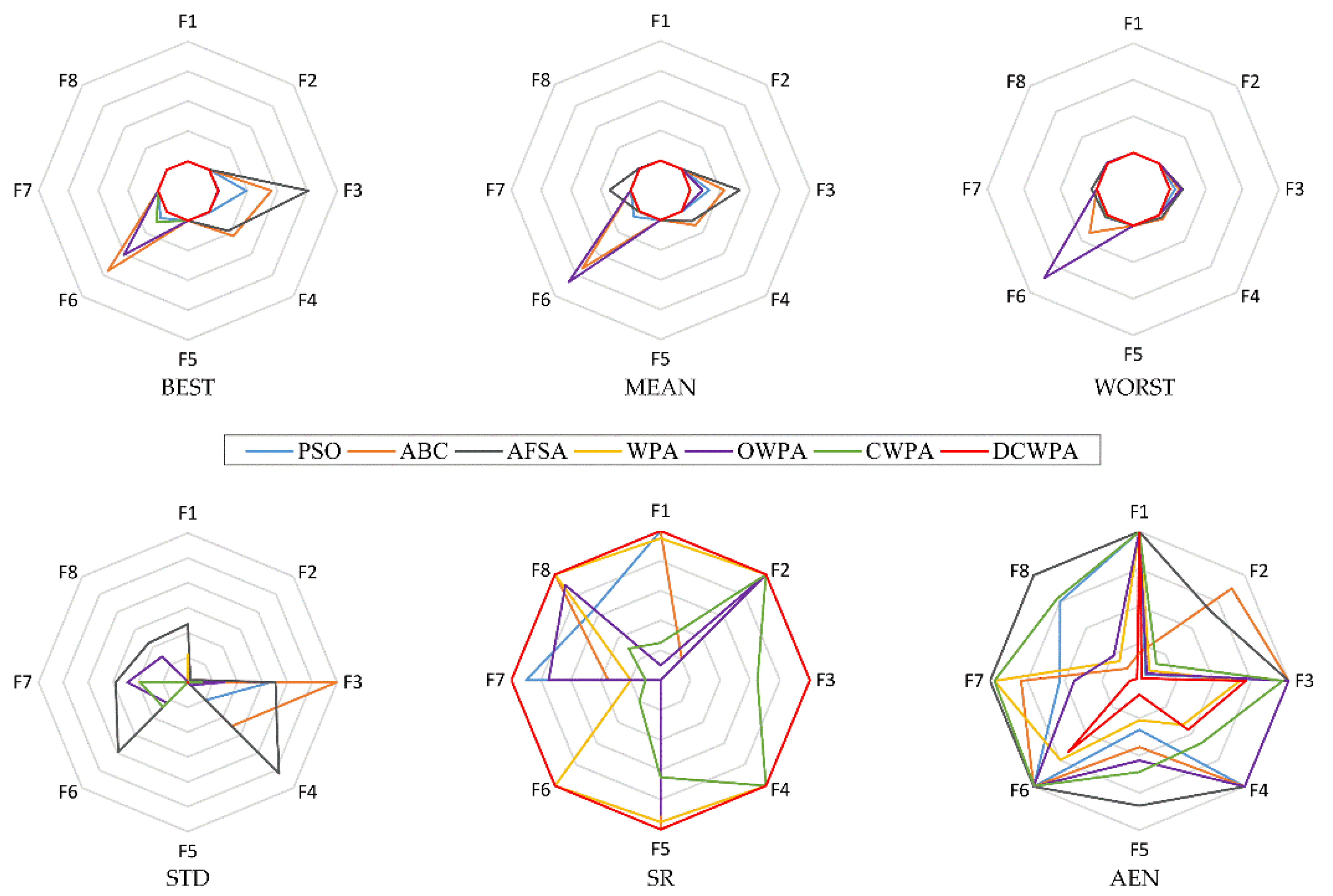
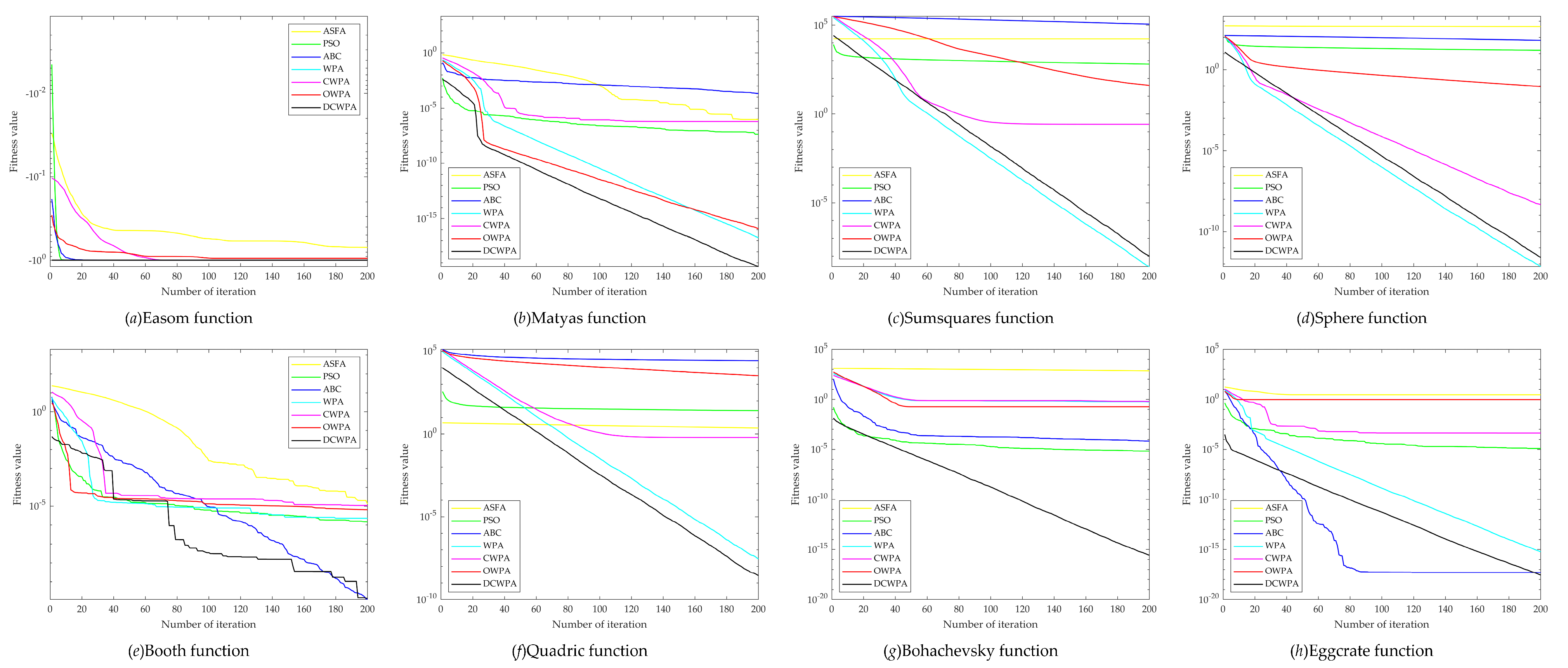
Aiming to avoid the low accuracy of the current intelligent optimization algorithm and the nonlinear and complexity of a PV module model, this paper proposes an improved Wolf Pack Algorithm (WPA) for parameter identification of a PV model based on the analysis of the basic Wolf pack algorithms. This algorithm uses the chaotic map sequence to initialize the population, thus to improve the diversity of the initial population. It adopts the walking direction mechanism based on the drunk walking model and the adaptive walking step size to increase the randomness of walking, enhance the individual’s ability to explore and develop and improve the ability of algorithm optimization. It also designs the judgment conditions for half siege in order to accelerate the convergence of the algorithm and improve the speed of the algorithm. In the iterative process, according to the change of the optimal solution, the Hamming Distance is used to judge the similarity of individuals in the population, and the individuals of the population are constantly updated to avoid the algorithm from stopping evolution prematurely due to falling into local optimization. This paper firstly analyzes the time complexity of the algorithm and then selects eight standard test functions (Benchmark) with different characteristics to verify the performance of the DCWPA algorithm for continuous optimization, and finally the improved algorithm is applied to the parameter identification problem of PV models. The experimental results show that the DCWPA has higher identification accuracy than other algorithms, and the results are more consistent with the measured data. Thus, the effectiveness and superiority of the improved algorithm in identifying solar cell parameters are verified, and the identification effect of the improved algorithm on solar cell parameters under different illumination is shown.
This paper is organized as follows.
Section 2 introduces the PV module parameter identification problem and its mathematical model.
Section 3 introduces the basic wolf pack algorithm and carefully analyzes its performance and its shortcomings.
Section 4 proposes a specific improvement strategy for the problems existing in the basic wolf pack algorithm, forming the DCWPA. In
Section 5, benchmark functions are used to verify the performance of the DCWPA for solving continuous optimization problems. In
Section 6, experiments are conducted to evaluate the effectiveness and superiority of the proposed algorithm for solving the parameter identification problem of PV models. In
Section 7, the conclusion is drawn for the future work.
3. Basic Wolf Pack Algorithm
3.1. Basic Principles
In nature, wolves have a strict social division mechanism and efficient cooperative hunting mode. Usually, there are three kinds of wolves in the wolf pack: the lead wolf, the scout wolf and the fierce wolf. The lead wolf makes overall planning, the scout wolf roams and searches, and the fierce wolf rounds up and attacks. The division of labor is clear, and each performs its own duties. After catching prey, it is distributed according to work and the survival of the fittest so that the population capacity continues to evolve [
13]. Therefore, three intelligent behaviors (wandering behavior, summoning behavior and siege behavior) and two basic mechanisms (the selection mechanism of winner as the lead wolf and the evolution mechanism of survival of the fittest) can be abstracted from the swarm intelligence model of wolves [
13]. On this basis, the WPA is proposed, and its basic principle model is shown in
Figure 4.
3.2. Basic Process
Consider the area where wolves hunt as a Euclidean space where the size of wolf pack is and the dimension of the space is . The position of wolf is , where is the position of wolf in the dimension space. The concentration of the prey smell perceived by wolf (that is, the fitness value of the objective function) is recorded as , then . Taking solving the maximum fitness value of the function as an example, the following two basic mechanisms and three intelligent behaviors in the wolf pack algorithm are explained.
- 1.
Selection mechanism of the lead wolf. In the process of wolf rounding up, the lead wolf is constantly changing according to the principle of “winner as the king”. In the initial wolf pack, the individual wolf with the largest objective function value is selected as the lead wolf. During the round-up process, if there is an individual wolf that is superior to the target function value corresponding to the position of the lead wolf, the individual wolf will immediately replace the original lead wolf. In the whole process, the position of the lead wolf is denoted as , and its corresponding objective function value is denoted as .
- 2.
Evolution mechanism of the wolf pack. The food distribution rules of the wolf pack reward on merit will inevitably lead to the starvation of some individual wolves with weak ability. Therefore, in the wolf pack algorithm, individual wolves with the worst objective function value are removed, and individual wolves are randomly produced to update the wolf pack, where and is the proportion factor of population renewal.
- 3.
Wandering behavior. The scout wolf advances one step in directions, respectively, calculates the fitness value of the positions after moving forward and then returns to the original position. After one step in the direction, the position of the scout wolf in the dimensional space is shown in Equation (5). In the directions, the scout wolf advances in the direction with the largest fitness value and greater than the current position fitness value . We continue to perform the above walking behavior and stop until the walking reaches the maximum number of steps or when occurs, which determines the updated lead wolf.
Here is the walking step and ; , because the search ability of each scout wolf is different, the value of is also different, which takes a random integer. Generally, the larger is, the more detailed the scout wolf search is, but the slower the algorithm calculation speed is.
- 4.
Summoning behavior. After the wandering behavior is over, the lead wolf calls all wolves to approach him. After receiving the call information of the lead wolf, fierce wolf quickly approaches the lead wolf with a large attack step according to Equation (6). If fierce wolf finds a position with a greater fitness value than the current position of the lead wolf on the way to the lead wolf, fierce wolf will replace the lead wolf and call; otherwise, the fierce wolf continues to perform the summoning behavior until the siege conditions are met: .
is the judgment distance turning into siege behavior, and
can be calculated by Equation (7).
and are the upper and lower bounds of the value of the variable in the dimensional space, respectively.
Suppose the distance between the fierce wolf
and the lead wolf in the
generation is
, as shown in Equation (8),
can be calculated by using the Manhattan distance.
In the above equation, represents the position of the fierce wolf in the dimensional space in generation , represents the position of the lead wolf in the dimensional space in generation , and represents the position of the fierce wolf in the dimensional space in generation .
- 5.
Siege behavior. Take the position of the lead wolf as the position of the prey, and all wolves siege the prey according to Equation (9). During the siege, if a new prey is found and its corresponding fitness value is greater than the current prey fitness value, update the prey location and siege the new prey until the prey is captured.
where
takes the random number within (0,1), and
represents the siege step length.
There are three steps in the WPA: walking step length
, running step length
and siege step length
. The relationship of the three steps is shown in Equation (10):
In the above formula, represents the step size factor. The larger is, the more detailed the search is.
3.3. Performance Analysis
In the WPA, the walk behavior makes the algorithm have better traversality, so the algorithm has strong global exploration ability. The lead wolf selection mechanism and calling behavior make the wolves gather quickly and accelerate the convergence speed of the algorithm. Moreover, during the siege, the wolves further refine the search near the current optimal solution, which improves the local exploration ability of the algorithm. In addition, the renewal mechanism of wolves not only maintains the population advantage, but also helps to jump out of the local optimum. Therefore, the WPA shows better optimization performance. However, the algorithm still shows some shortcomings in practical application, as follows:
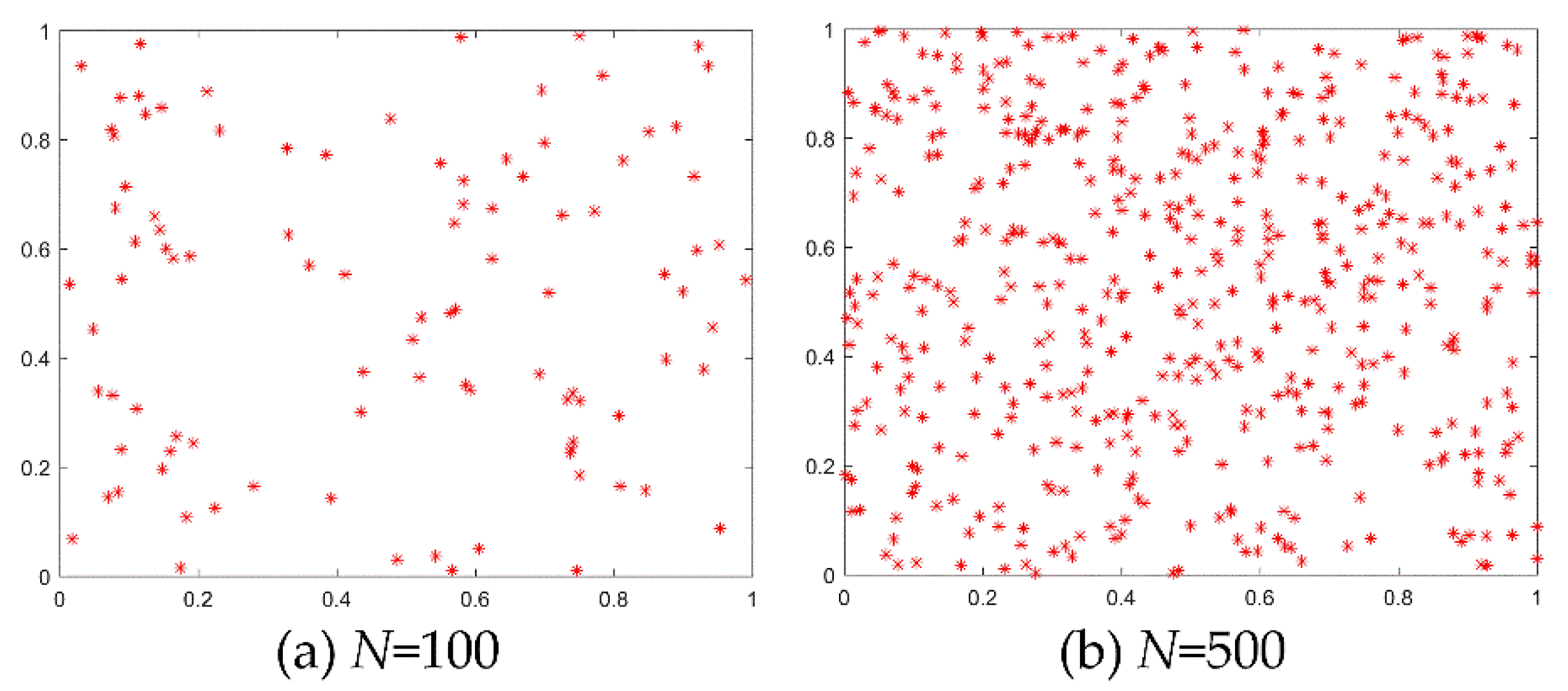
Disadvantage 1: The population initialization of the WPA generally adopts the way of pseudo-random number, so the population cannot cover the solution space evenly. If we invoke all the rand function in MATLAB software to initialize the two populations of size 100 and 500, respectively, as shown in
Figure 5, the individuals in the initial population overlap each other, and some areas are blank. As a result, the initial population is unable to cover the whole solution space evenly, affecting the optimization performance of the algorithm.
Disadvantage 2: In the wandering behavior, the scout wolf adopts the greedy strategy, as shown in
Figure 6. When the search direction
in Equation (5) is fixed, the wandering of each scout wolf is equivalent to selecting the direction to move in the fixed
directions. The direction is relatively fixed, and the randomness of direction change is significantly reduced. If the prey is between the parallel lines of the search direction, it is very difficult for the scout wolf to find the prey; that is, it is hard to find the global optimal solution. In addition, the walk step adopts a fixed value, which also reduces the randomness of the search.
Disadvantage 3: In the running behavior, it is necessary to continuously analyze and calculate the distance between all the fierce wolves and the lead wolf, and only when the distance between all the fierce wolves and the lead wolf is less than the critical distance , can the running behavior be ended and the prey be besieged. When solving high-dimensional complex optimization problems, the algorithm will inevitably consume a large amount of computing resources. At the same time, it may also make the algorithm unable to jump out of the rush behavior for a long time, resulting in a slow running speed and a large increase in time consumption.
Disadvantage 4: The WPA adopts the mechanism of continuous iterative change of population to optimize. In order to maintain the population superiority, only a few wolves are updated. At the later stage of iteration, the diversity of the population is bound to decrease, it is difficult to jump out of the local optimum, and the evolution will be stopped prematurely, so the solution accuracy of the algorithm is difficult to reach the best.
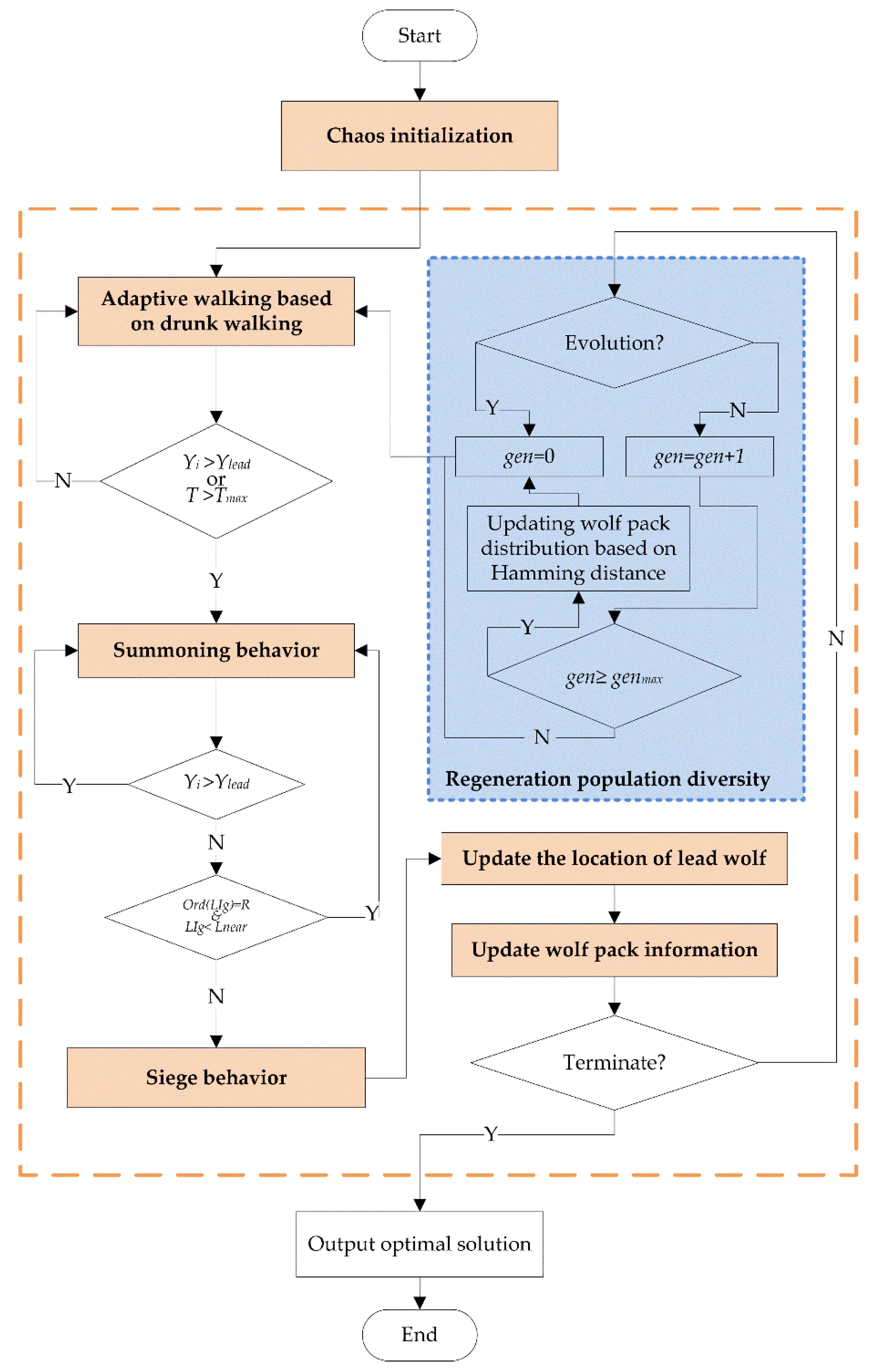
4. Improved Wolf Pack Algorithm
4.1. Improvement Strategy
Aiming at the four shortcomings of the WPA, this paper puts forward four improvement strategies. The first is to use a chaotic map to initialize the population, enhancing the diversity. The second is to choose the walking direction based on the drunk walking model and adopt the adaptive walking step size to increase the randomness of walking and improve the individual’s optimization ability. The third is to design the rush behavior. When half of the wolves meet the siege distance, the judgment conditions for siege behavior are carried out, so that the algorithm convergence is accelerated, and the algorithm solution speed is improved. Finally, in the iterative process, according to the change of the optimal solution, the Hamming Distance is used to judge the similarity of individuals in the population, and the individuals of the population are constantly updated to avoid the algorithm from stopping evolution prematurely due to falling into local optimization.
4.1.1. Population Initialization Based on Chaotic Maps
Chaotic states exist widely in nature and society and have the characteristics of randomness, ergodicity and regularity. Chaos motion can traverse all states without repetition within a certain range according to its own laws [
36]. Therefore, in order to efficiently generate an initialization population with uniform distribution in the solution space, a chaotic mapping method is proposed to initialize the location of wolves. Currently, there are many kinds of chaotic map sequences that can meet such conditions. As shown in
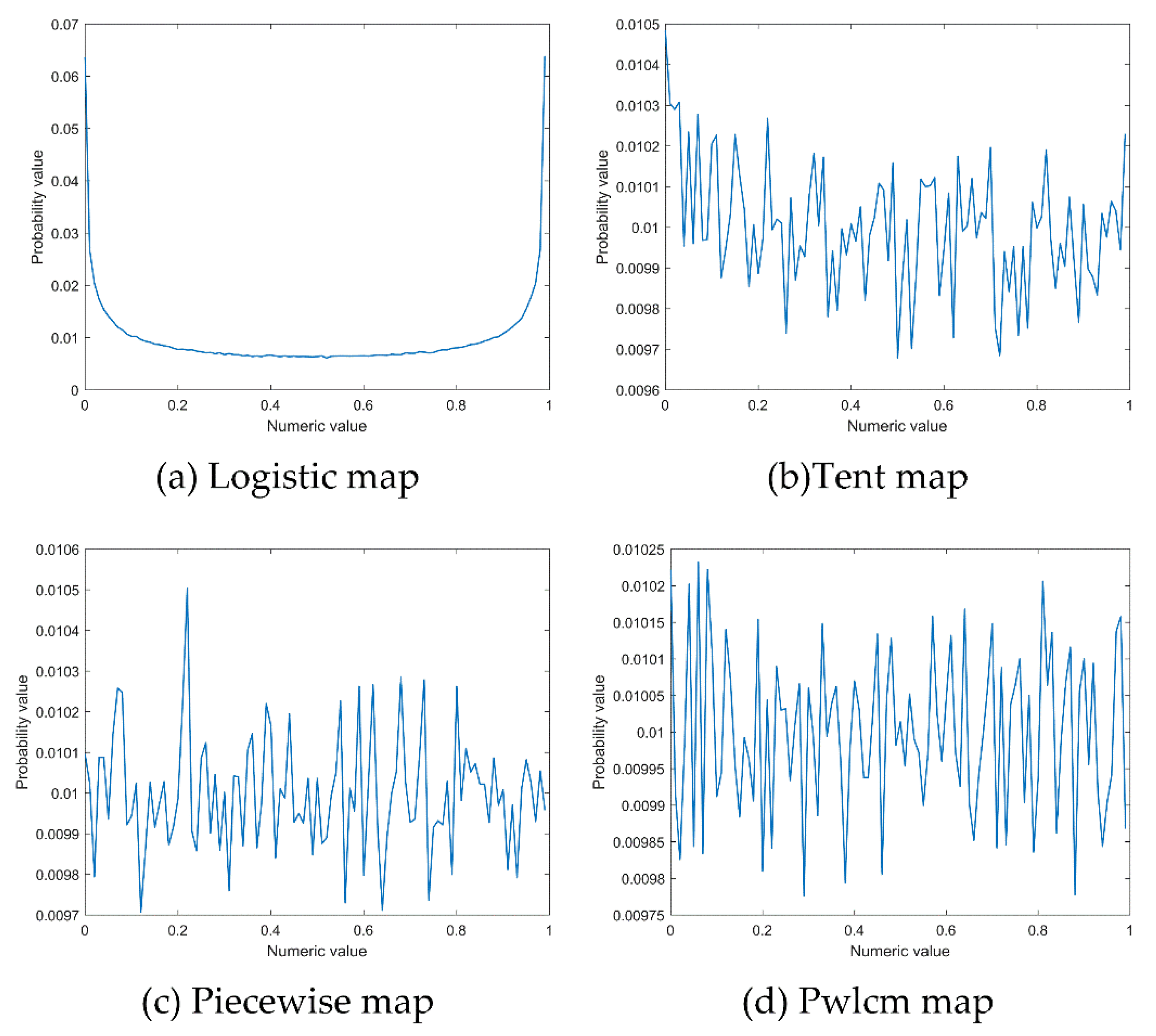
Table 2, Logistic map, Tent map, Piecewise map and Pwlcm map are four typical chaotic maps.
In order to intuitively display the characteristics of the four chaotic maps in
Table 2, their probability distribution characteristics in the (0,1) interval are compared. Among them, the probability distribution is obtained in the following way: 50,000 chaotic numerical points generated by 50,000 iterations of chaotic mapping are used to count the probability of these 50,000 points falling into 100 intervals after equal division of interval (0,1), and the probability distribution diagram as shown in
Figure 7 is drawn.
Analysis of
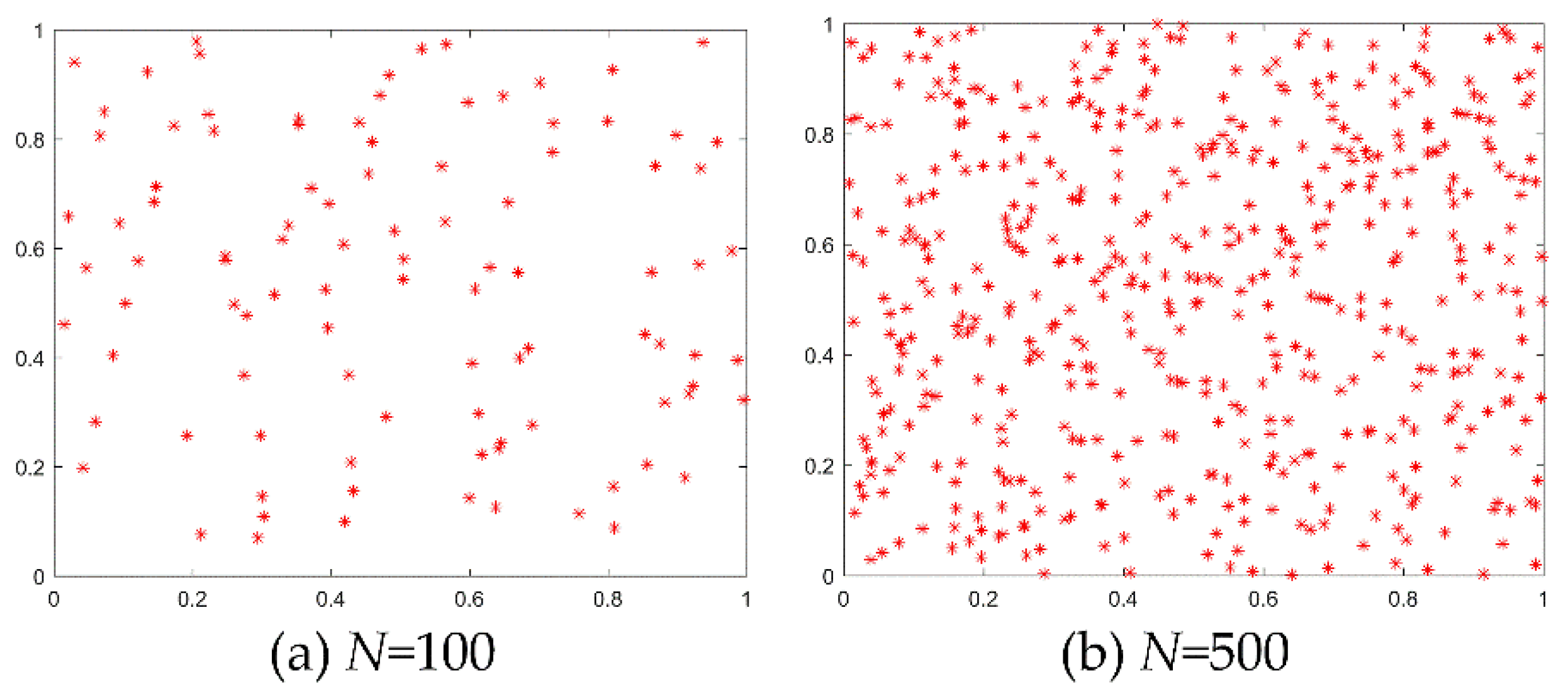
Figure 7 shows that the logistic map shows a distribution trend that is large in the middle and small at both ends. If the global optimal solution of the function problem is distributed in the middle, there will be a large number of invalid searches, which will be very unfavorable for the global optimization. The probability distribution in the interval of the Tent map, the Piecewise map and the Pwlcm map (0,1) is uniform. The population initialized with these three distributions is evenly distributed in the solution space, so it can avoid excessive search in some local areas (such as the logistic map, a large number of searches are concentrated at both ends of the interval) and reduce the adverse impact caused by the incompatibility between the distribution characteristics of chaotic sequence and the location of the global optimal solution of the optimization problem. As can be seen from the figure, the probability fluctuation range of the Tent map is (0.0105, 0.00967), the probability fluctuation range of the Piecewise map is (0.0105, 0.0097), and the probability fluctuation range of the Pwlcm map is (0.01023, 0.00977). Compared with the Tent map and the Piecewise map, the probability distribution of the Pwlcm map is more uniform, and the interval size of the Pwlcm map probability distribution is 0.00046, which is much smaller than the other two sequences. As shown in
Figure 8, if we use the Pwlcm map to initialize two two-dimensional populations with population numbers of 100 and 500 between (0, 1), it is obvious that compared with the randomly generated initial population in
Figure 5, the distribution of the initial population generated by the Pwlcm map is more uniform, which is conducive to the complete search of the whole region in the initial stage of the algorithm. Therefore, this paper selects the Pwlcm map to initialize the individual population of the WPA.
After the chaotic ergodic sequence
is obtained by the Pwlcm map search, the chaotic ergodic sequence
needs to be transformed to the original solution space according to the following Equation (11).
Among them, and represent the upper boundary and lower boundary of wolf activity, respectively.
4.1.2. Random Walk Based on Drunken Walk Model
Random walk [
37] was put forward by Pearson in 1905. It is a random and irregular form of movement, and the next step in the movement process is uncertain. The idea of random walk is that an element starts random motion from any point, and after a certain period of time, it will traverse the entire space. Random walk has been widely used in many fields because of its strong applicability. Gupta et al. [
38] designed an improved gray wolf optimization algorithm based on the idea of random walk, which shows good performance in solving continuous optimization problems and real-life optimization problems. Random walk can generally be divided into three types: Markov chain [
39], Levy flight [
40] and drunkard walk [
41]. The drunk walking model is shown in Equation (12). In this model, the direction of each step of the drunk is in any direction in the whole space, which has great uncertainty and randomness and can better traverse the whole space.
Therefore, in order to enhance the breakthrough ability of the scout wolf and avoid it falling into local areas, a walking behavior based on drunk walking is designed by combining drunk walking with greedy walking behavior, as shown in
Figure 9. Equation (12) is the mathematical expression of the random walk based on the drunken walk model. In the process of wandering, scout wolf
takes a greedy strategy according to Equation (12), advances one step in
directions, respectively, records the position and corresponding fitness value before and after each step and then returns to the original position. Among the
directions, the direction with the largest odor concentration and greater than the current odor concentration
is taken as the update direction of the scout wolf.
The step length
of a drunk can be fixed or changed. A small step length is helpful to carry out a fine search, while a large enough step length is helpful to expand the search range or jump out of the local optimum. At the same time, considering the spatial distance between the position of the scout wolf and the lead wolf, the walking length is designed as the adaptive step length shown in Equation (13). The adaptive step length can effectively increase the randomness of the wolf search to enhance the ability of wolf breakthrough and optimization.
is the position of wolf , and is the position of the lead wolf.
4.1.3. Half-Population Siege Strategy
The wolves except the lead wolf are regarded as fierce wolves, and fierce wolves quickly approach the lead wolf after receiving the summoning order. When the distance between more than half of the fierce wolves and the lead wolf is less than the determined distance , all the fierce wolves will adjust their positions to be within the siege range to execute the siege behavior.
In the
iteration, the maximum distance between the
fierce wolves closest to the lead wolf and the lead wolf is
. In order to obtain the distance
, the distance between the fierce wolf and the lead wolf is sorted, and
represents the order of
in the sequence after the distance between each fierce wolf and the lead wolf is arranged in ascending order. The sequence encoding vector
of all wolves is shown in Equation (14).
In each iteration, when the maximum distance
between the
fierce wolves closest to the lead wolf and the lead wolf is less than
(i.e., the siege conditions in Equation (15) are met), all fierce wolves adjust their positions and execute the siege behavior; Otherwise, they continue to perform the summoning behavior.
4.1.4. Evolutionary Mechanism Based on Hamming Distance
After several iterations of the WPA, most individual wolves are near the current optimal solution. As the similarity between individuals increases and the population diversity decreases, it is very easy to cause “stopping evolution prematurely”, leading to the stagnation of evolution. Therefore, this paper introduces the similarity judgment mechanism based on the Hamming Distance [
42] to dynamically update the population in order to maintain the continuous evolution of the population. When the number of stagnant changes of the optimal value exceeds the preset threshold, we will calculate the the Hamming Distance between each wolf and the lead wolf to judge the similarity between individuals, eliminate the individual wolves with high similarity with the lead wolf and generate new individuals with low similarity with the lead wolf to enhance the diversity of the population to improve the ability of the algorithm to jump out of the local extreme value in the iteration and maintain the vitality of continuous evolution.
The Hamming Distance is mainly used to describe the difference between two vectors with the same dimension. As shown in Equation (16), the Hamming Distance is the sum
of the number of positions with different values at all corresponding positions of vector
and vector
. It can accurately reflect the difference between two vectors, so as to objectively judge the similarity of vectors.
In the above equation, is the XOR operator, represents the dimension of the vector, and .
Suppose the similarity between individuals in the wolf pack is
, which represents the proportion of the sum of the number of dimensions with the same position in all the corresponding dimensional spaces of the two artificial wolves to the total dimension. Then, according to Equation (17), the similarity
of any two wolves in the wolf pack can be calculated. By contrast, if the calculated similarity
, is less than the preset threshold
, it indicates that the similarity between the two individuals is low. Otherwise, the similarity between the two individuals is high.
When the population evolution is found to be stagnant in the iterative optimization process, the similarity between all individual wolves and the current alpha wolf is calculated by the Hamming Distance. Individuals with low similarity will be retained, individuals with high similarity will be eliminated, and individuals with low similarity to the head wolf will be generated to update the wolf group. Then the wolves are distributed in the solution space, and the global optimization ability of the algorithm is increased. The specific process is as follows:
Step 1: Calculate the similarity between all individual wolves and the lead wolf. Individuals whose is greater than form wolf pack , and other individuals form wolf pack . Let the scale of be , then the scale of be .
Step 2: In order to maintain the dominance of the population, only outstanding individuals in the wolf pack are retained, , and the remaining individuals in are eliminated.
Step 3: In the optimization space, individuals whose similarity meets the requirements are randomly generated and supplemented to , .
Step 4: Combine and to form a new wolf pack, that is, the initial wolf pack of the next iteration.
It should be noted that wolves have good distribution in the solution space at the initial stage of evolution. In order to improve the convergence of the algorithm, save computing resources and reduce computing time, only when the population stagnant evolution algebra reaches the threshold can the population be updated by the population dynamic update method based on the Hamming Distance.
4.2. Basic Process of Improved WPA
The flow of the improved algorithm is shown in
Figure 10. The calculation steps of the algorithm are described below by taking the solution of the maximum value as an example:
Step 1: Initialization. According to the wolf pack generation method based on the Pwlcm map in Equation (11), artificial wolves are randomly generated in the Euclidean space of , with the position of artificial wolf as , the step length factor as , the maximum number of walks as , the distance judgment factor as , the maximum number of iterations as , the update scale factor as , the evolution stop threshold as and the similarity judgment threshold as .
Step 2: Wandering behavior. Select the lead wolf and treat all other wolves except the lead wolf as scout wolves. Let all scout wolves have random walk based on the exploration direction of the drunk walk model, then decide the best position in the next step and move forward by using the adaptive greedy mechanism, calculate the fitness value of the scout wolves’ positions and update the lead wolf in real time.
Step 3: Summoning behavior. All other wolves except the lead wolf are considered fierce wolves. After the lead wolf issues the summoning command, all scout wolves quickly move closer to the lead wolf according to Equation (6). If the fierce wolf finds a better fitness value than the position of the lead wolf during the attack, that is: , then the fierce wolf replaces the lead wolf and initiates a call; otherwise, continue to attack until the siege conditions of half the population are met, end the summoning behavior and turn to Step 4.
Step 4: Siege behavior. The position of the lead wolf is regarded as the position of the prey, and all wolves besiege the prey according to Equation (9).
Step 5: Wolf pack update. Compare the objective function value corresponding to the lead wolf after each iteration with the function value corresponding to the lead wolf in the previous generation. If , update the position of the lead wolf, and update the wolves with poor fitness value according to Equation (11).
Step 6: Determine whether to terminate. Judge whether the maximum number of iterations or the accuracy requirement is reached, and if so, output the optimal solution and its corresponding fitness value; otherwise, go to step 7.
Step 7: Determine whether to update the wolf pack. If there is no artificial wolf with a new optimal position in the current generation of the wolf pack, record the algebra that has stopped evolving, and determine whether the conditions for updating the population are met. If , go to step 8; otherwise, go to step 2.
Step 8: Population update. By updating the individuals with high similarity to the lead wolf in the population based on the Hamming Distance, a new wolf pack is obtained, which is used as the initial population for the next generation evolution, then , and go to step 2.
4.3. Time Complexity Analysis of the Algorithm
In order to illustrate the operation efficiency of the DCWPA, this paper uses the time complexity analysis method in [
43] to analyze the time complexity of the proposed algorithm.
In the WPA, the population size is
, and the length of individual wolf positions is
. The setting time of parameters such as basic motion step
, maximum walking period
of wolf detection, siege judgment distance
and update scale factor
is
, the time of generating the initial population is
, and the time of calculating the fitness function value is
, then the time complexity of algorithm initialization is:
If we assume the time consumption of the competition process of the lead wolf as
, the time consumption of the wandering process of the scout wolf as
, the time consumption of the fierce wolf performing the calling behavior and approaching the lead wolf as
, the time consumption of the fierce wolf moving towards the lead wolf in each dimension space as
, and the time consumption of judging whether to end the calling behavior as
, then the time complexity of the algorithm in this stage is:
From the above, the time complexity of each iteration in the WPA is:
We put the time complexity of the algorithm analyzed in combination with the basic process of the DCWPA. In the initialization phase of the algorithm, the time consumption of generating the initialization population by chaotic mapping is
, and the other initialization processes are the same as the WPA. Therefore, the time complexity of DCWPA initialization is:
The time consumption of calculating the adaptive walk step length of the scout wolf as
, the time consumption of judging whether the siege condition of half the population is reached as
, the time consumption of population diversity detection and population evolution update as
, and the rest of the process is the same as that of the WPA. Then the time complexity of this stage is:
In summary, the time complexity of each iteration process in the DCWPA is:
Therefore, compared with the WPA, the time complexity of the DCWPA does not change, and the operating efficiency of the algorithm does not decrease.
7. Conclusions
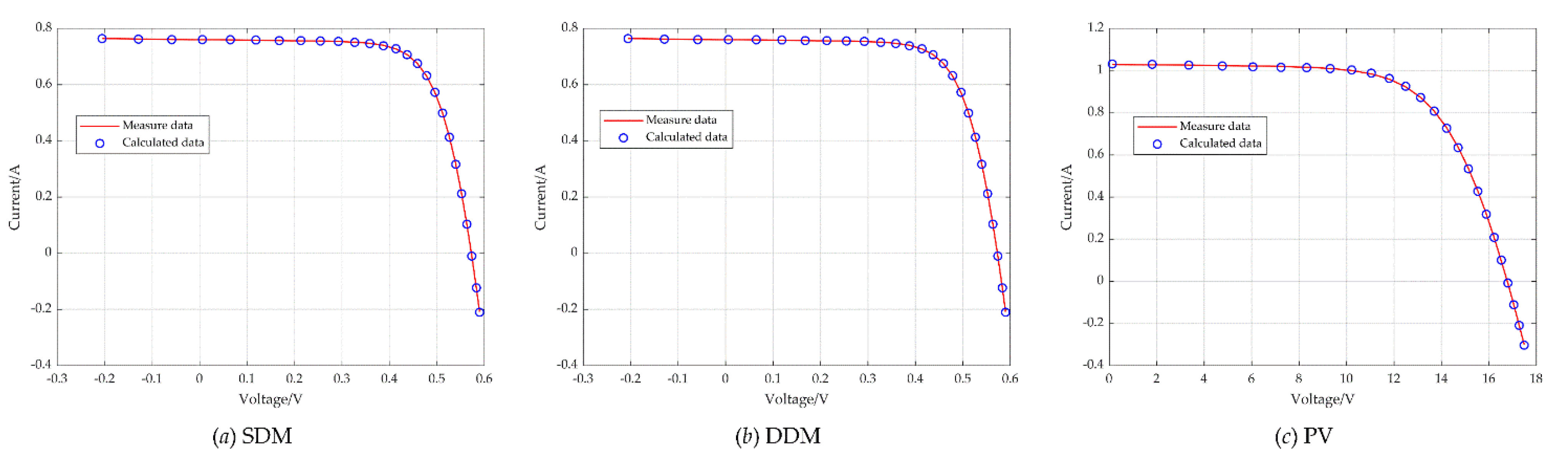
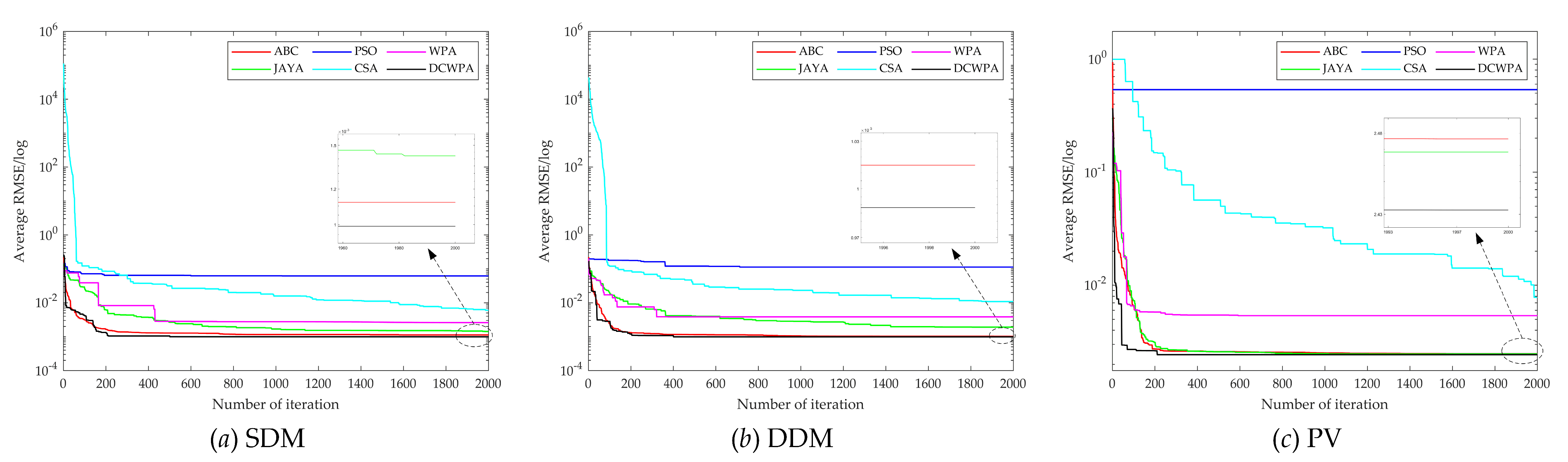
Aiming at the low accuracy problem of parameter identification by the current intelligent optimization algorithm in a PV model, this paper improves the basic wolf pack algorithm and puts forward a novel drunken adaptive walking chaotic wolf pack algorithm, which is named the DCWPA for short. The DCWPA uses the chaotic map sequence to initialize the population, thus to improve the diversity of the initial population. It adopts the walking direction mechanism based on the drunk walking model and the adaptive walking step size to increase the randomness of walking, enhance the individual’s ability to explore and develop and improve the ability of algorithm optimization. It also designs the judgment conditions for half siege in order to accelerate the convergence of the algorithm and improve the speed of the algorithm. In the iterative process, according to the change of the optimal solution, the Hamming Distance is used to judge the similarity of individuals in the population, and the individuals of the population are constantly updated to avoid the algorithm from stopping evolution prematurely due to falling into local optimization. This paper selects eight standard test functions (Benchmark) with different characteristics to verify the performance of the DCWPA algorithm for continuous optimization and uses it for parameter identification of a single-diode five-parameter model, a double-diode seven-parameter model and a photovoltaic module model. The results show that the DCWPA has stronger optimization ability in high-dimensional complex continuous reading space and can accurately and reliably identify the model parameters of photovoltaic modules. This research provides a new idea and method for solving the parameter identification problem of a PV module model.
Although the DCWPA shows better performance in PV module model parameter identification, there are still some works that need further improvement. First, whether the proposed method still has good performance for complex PV module models requires continued validation and research. In addition, in terms of the DCWPA algorithm, too many parameters and complex algorithm processes still need to be solved in the next step. Finally, the method should be further extended to other practical engineering problems.