Customer Privacy Concerns as a Barrier to Sharing Data about Energy Use in Smart Local Energy Systems: A Rapid Realist Review
Abstract
1. Introduction
2. Materials and Methods
2.1. Methodology
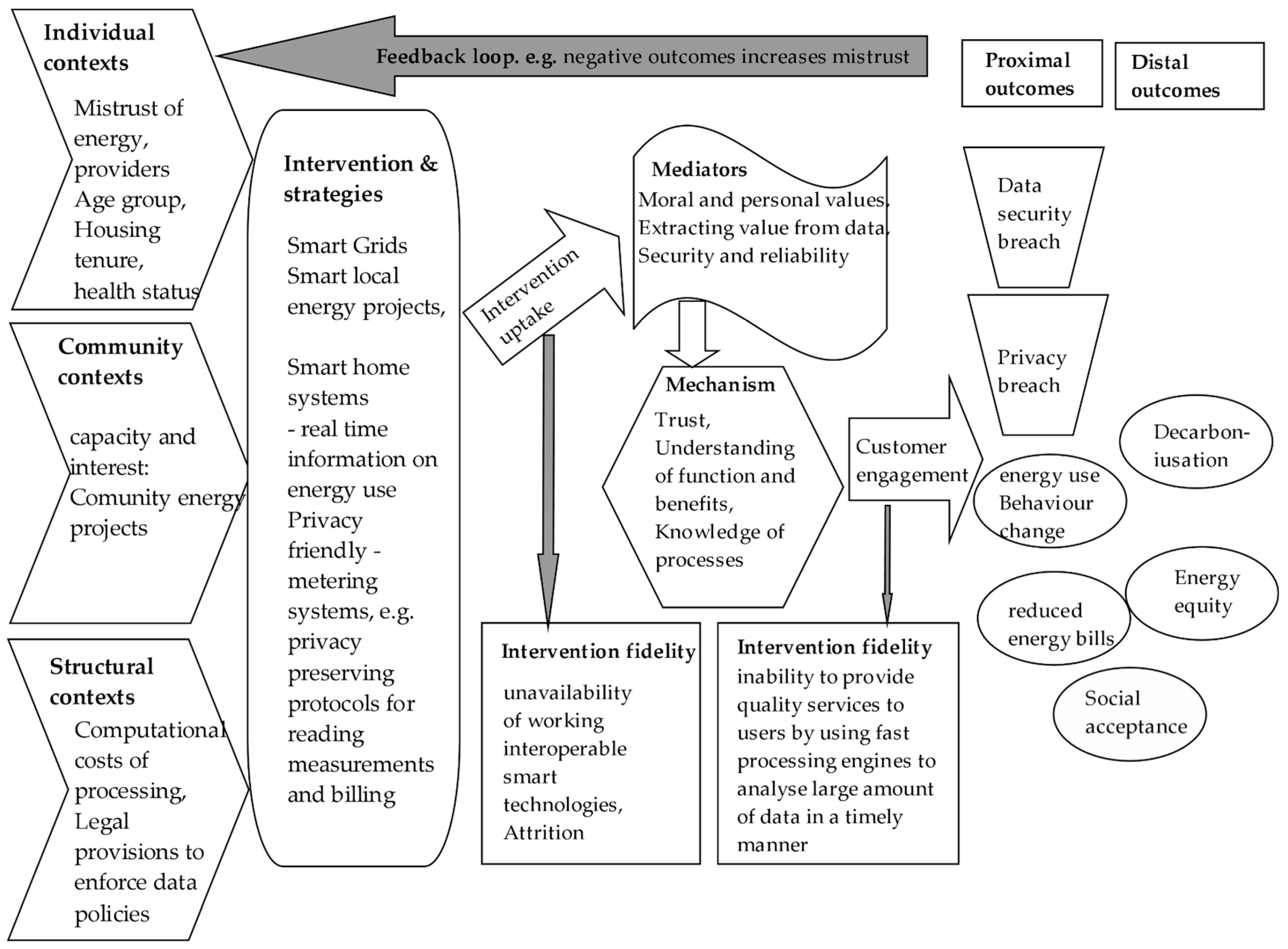
Initial Programme Theory
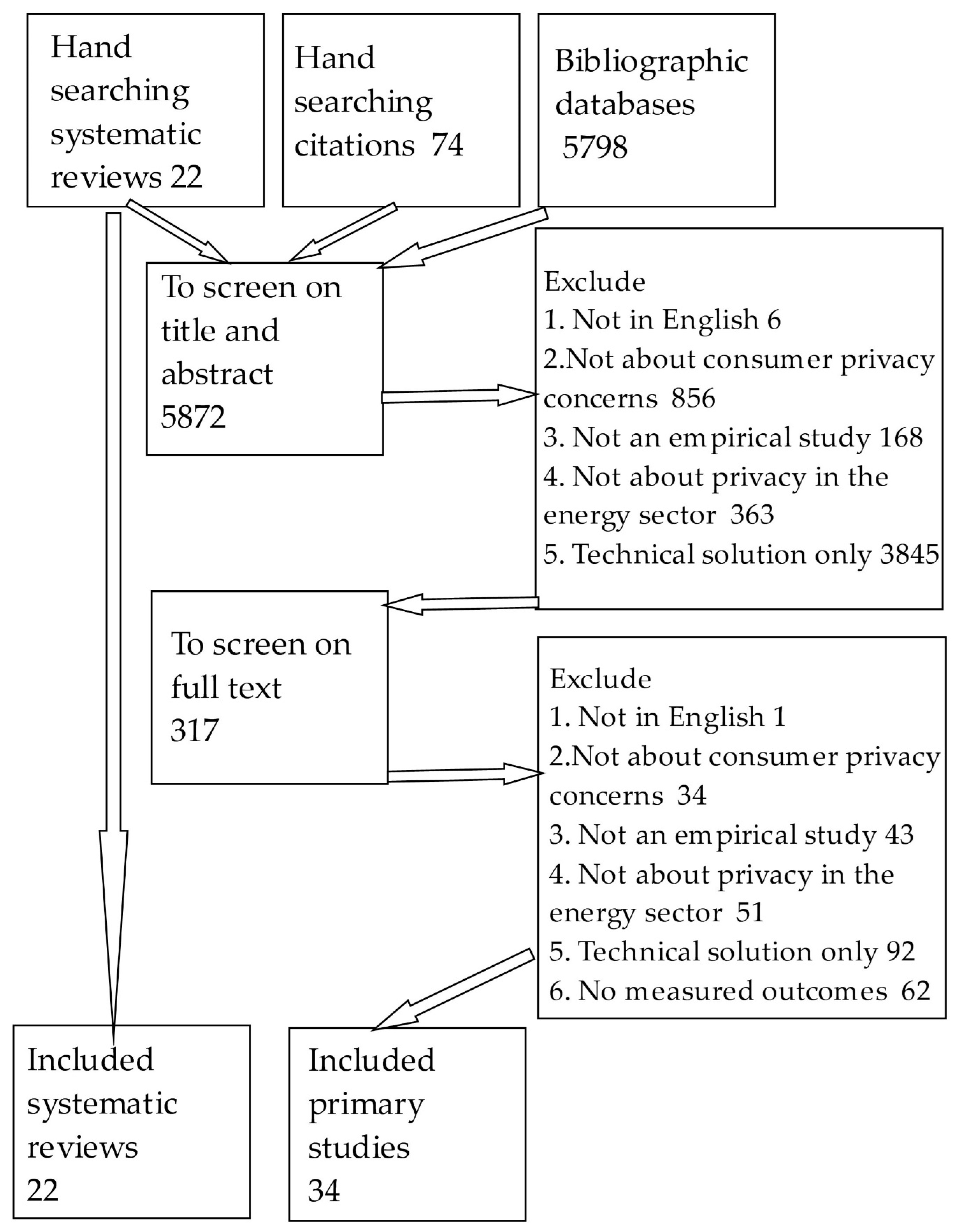
2.2. Search Strategy
2.3. Screening Studies: Applying Inclusion and Exclusion Criteria
2.4. Inclusion Criteria
- Study is published in English. The review does not currently have resource to provide translations of studies published in other languages. Studies not published in English were not excluded at the search stage but were included in the count of published studies.
- Study must include consideration of privacy concern and, in particular, the role this plays in choices around to what extent customers participate. The study will not be included if it presents only a technical privacy solution (e.g., encryption) with no interaction with consumer privacy concerns.
- The study must include numerical outcomes or views and experiences.
- Study must present clear methods for their research.
- Studies with a focus on energy will be prioritized for inclusion, with studies in other areas included on the basis of theoretical and practical relevance.
2.5. Characterising Included Studies
- Date of publication;
- Study methods;
- Geographical location;
- Study aims;
- Intervention aims;
- Programme theory of change;
- Type of privacy concern;
- Privacy domain;
- Participant characteristics;
- Characteristics of the person(s)/organization(s) delivering the intervention;
- Intervention type;
- Intervention components/content;
- Outcome measures;
- Intervention contexts;
- Implementation factors;
- Type of publication;
- Funder of research;
- Quality of execution of study;
- Relevance of study to this review.
2.6. Identifying and Describing Studies: Quality Assurance Process
- Internal validity: how reliable the study is in its execution.
- Construct validity: the extent to which the concrete measures in the study match up to the intervention theory of change [23].
- Conclusion validity (rigor): the reliability and trustworthiness in reaching its findings and conclusions [24].
- Relevance/generalizability: to what extent the findings are replicable and generalizable to the SLES context, as well as the relevance of the study to this rapid review.
3. Results
3.1. Description of the Included Studies
3.2. Methods of Synthesis
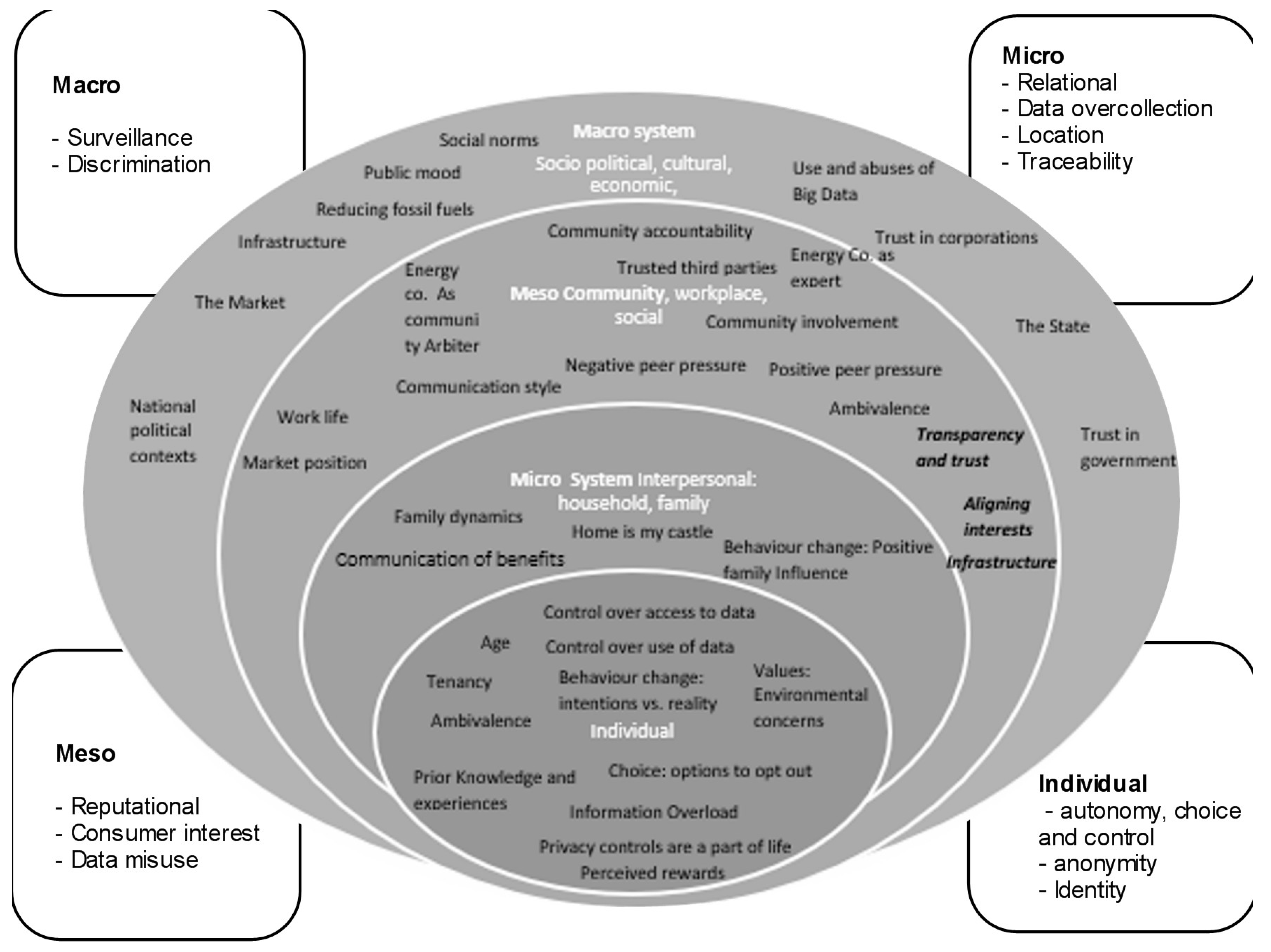
3.3. Privacy Concerns and Barriers to Data Sharing in Different Domains
“For now, I don’t see any way of misusing my data that could turn out to be my downfall. […] It would be nice, however, to see what data is transferred or stored. If I can control this, it’s on me to decide what may be transferred or used.” ([40] single-person household).
“…because you don’t know the situation of the people in the house… So just to…choose to switch off someone’s electricity...... I know that we could make do and we’d be fine. .... But there are other houses maybe they couldn’t or maybe there’s something about them that we don’t know…” (Frances, [44]).
3.4. Privacy, Barriers and Facilitators in the Micro, Interpersonal Contexts
“The fact that the electric company can tell when I’ve turned on the dishwasher or a light bulb or the TV—that’s pretty fascinating to me. I don’t know how they do that, but do I want them to know that? well it’s not a bad thing. It’s still a private thing…” [28].
“So… he monitors it all on his thing (computer) and it drives her insane! So, she thinks its dreadful, she feels violated all the time, cos his workmates will be walking past his desk. One even called her one day saying ‘Wow Kay, your power is going through the roof!’” [49].
- Diversity. SLES providers should recognize their diverse user base and have a diverse development team.
- Privacy and choice. SLES providers should empower all of their users (not just the named “bill payer”), to easily make active and informed decisions about their privacy settings.
- Security and data. SLES providers should build secure technology, and only collect necessary data, which will limit the risk that the data can be intercepted and/or be used maliciously.
- Combatting gaslighting. Data collection and control over data should disrupt attempts at manipulating someone into doubting their memories and judgement with pertinent, timely notifications, and auditing, i.e., there should be limits to deletion of records of activity.
- Technical ability. SLES providers should ensure that the use of the technology is intuitive and can be understood by all who could be affected by it, regardless of their technical confidence.
“…They could even ‘see’ when you are going to bed [by seeing when you] switch off the lights.” [41].
3.5. Type of Privacy Concern, Barriers, and Facilitators in the Mesosystem of Community, Social Groups, and Work
“Sometimes it feels a bit futile if you don’t think anyone else is doing it. So, I think if you know that other people are doing it, it makes you feel you’re having a bigger impact” [44].
“You can also see it as an invasion of your privacy. Someone is going to meddle in. You might experience some sort of social pressure on the way you do your housekeeping.” [47].
“We have those sensors in the rooms; then I see it as natural that they look if it runs alright. Or are they just letting everything run without even keeping an eye on what is going on? There must be a reason for why we have sensors in various rooms.” [35].
“…If you have the ambition to become energy-neutral, then you need to have an element of exchange. And if you exchange, you need an institution to organize that.” [12].
3.6. Types of Privacy Concerns and Barriers and Facilitators in the Macro Socio–Political, Economic, and Cultural Context
“I have nothing to hide. It is just that connections will be made between different databases. That will result in a profile. For many that profile will be just fine, but for a small minority this profile will mark them as terrorists!” [12]
3.7. Demographic Factors That Impact Data Sharing
“If the potential adopter [of energy efficiency measures] is not the party that pays the energy bill, then good information in the hands of the potential adopter may not be sufficient for optimal diffusion” [84].
3.8. Theories of Change in Studies
3.9. Theories of Privacy Ethics: Between Social Norms and Individual Decision Making
3.10. Theories of Individual Behaviour
- Relative advantage;
- Compatibility;
- Complexity;
- Trialability;
- Observability.
4. Guiding Principles for Interventions to Address Privacy Concerns
- Recognize the mutual benefits of data sharing for smart local energy systems and work with customers as partners.
- Involve people in the design of data sharing technologies from the start.
- Give people a say on the third parties that they are happy to share data with.
- Empower people to set the boundaries around the flow of information about themselves.
- Ensure that the purpose and value of the data collected are transparent and fair.
- Ensure that everyone affected by sharing of data are involved in giving their informed consent.
- Recognize that technologies for revealing and monitoring behaviours in the home can be used in unexpected and unwanted ways.
- Ensure there are channels of feedback and ongoing communication to continuously improve service delivery.
4.1. Guiding Principle 1—Recognize the Mutual Benefits of Data Sharing for Smart Local Energy Systems and Work with Customers as Partners
4.2. Guiding Principle 2—Involve People in the Design of Data Sharing Technologies from the Start
4.3. Guiding Principle 3—Give People a Say on the Third Parties That They Are Happy to Share Data With
4.4. Guiding Principle 4—Empower People to Set the Boundaries around the Flow of Information about Themselves
4.5. Guiding Principle 5—Ensure That the Purpose and Value of the Data Collected Are Transparent and Fair
4.6. Guiding Principle 6—Ensure That Everyone Who Is Affected by Sharing of Data Are Involved in Giving Their Informed Consent
4.7. Guiding Principle 7—Recognise That Technologies for Revealing and Monitoring Behaviours in the Home Can Be Used in Unexpected and Unwanted Ways
4.8. Guiding Principle 8—Ensure There Are Channels of Feedback and Ongoing Communication to Continuously Improve Service Delivery
5. Conclusions
- (1)
- Personal characteristics associated with discrimination (e.g., age, disability);
- (2)
- Features of relationships (coercive, abusive relationships);
- (3)
- Time-dependent relationships (e.g., temporary, insecure accommodation).
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- UKRI. Prospering from the Energy Revolution Challenge. 2018. Available online: https://www.ukri.org/our-work/our-main-funds/industrial-strategy-challenge-fund/clean-growth/prospering-from-the-energy-revolution-challenge/ (accessed on 17 February 2021).
- Wilson, C.; Jones, N.; Devine-Wright, H.; Devine-Wright, P.; Gupta, R.; Rae, C.; Tingay, M. Common Types of Local Energy System Projects in the UK; EnergyRev: London, UK; University of Strathclyde Publishing: Glasgow, Scotland, 2020; ISBN 9781909522657. [Google Scholar]
- Strbac, G.; Pudjianto, D.; Aunedi, M.; Papadaskalopoulos, D.; Djapic, P.; Ye, Y.; Moreira, R.; Karimi, H.; Fan, Y. Cost-Effective Decarbonization in a Decentralized Market: The Benefits of Using Flexible Technologies and Resources. IEEE Power Energy Mag. 2019, 17, 25–36. [Google Scholar] [CrossRef]
- Lund, H.; Østergaarda, P.A.; Connolly, D.; Mathiesen, B.V. Smart energy and smart energy systems. Energy 2017, 137, 556–565. [Google Scholar] [CrossRef]
- Ford, R.; Maidment, C.; Vigurs, C.; Fell, M.J.; Morris, M. Smart local energy systems (SLES): A framework for exploring transition, context, and impacts. Technol. Forecast. Soc. Chang. 2021, 166, 120612. [Google Scholar] [CrossRef]
- Kremers, E.; Gonzalez de Durana, J.; Barambones, O. Multi-agent modelling for the simulation of a simple smart microgrid. Energy Convers. Manag. 2013, 75, 643–650. [Google Scholar] [CrossRef]
- Nambi, S.N.A.U.; Pournaras, E.; Venkatesha, P.R. Temporal Self-Regulation of Energy Demand. IEEE Trans. Ind. Inform. 2016, 12, 1196–1205. [Google Scholar] [CrossRef]
- Vázquez-Canteli, J.R.; Nagy, Z. Reinforcement learning for demand response: A review of algorithms and modeling techniques. Appl. Energy 2019, 235, 1072–1089. [Google Scholar] [CrossRef]
- Hargreaves, T.; Nye, M.; Burgess, J. Making energy visible: A qualitative field study of how householders interact with feedback from smart energy monitors. Energy Policy 2010, 38, 6111–6119. [Google Scholar] [CrossRef]
- Harrison, C.; Eckman, B.; Hamilton, R.; Hartswick, P.; Kalagnanam, J.; Paraszczak Williams, P. Foundations for Smarter Cities. IBM J. Res. Dev. 2010, 54, 1–16. [Google Scholar] [CrossRef]
- Information Commissioner’s Office. What is personal data? 2020. Available online: https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/key-definitions/what-is-personal-data (accessed on 20 November 2020).
- Naus, J.; van Vliet, B.J.M.; Hendriksen, A. Households as change agents in a Dutch smart energy transition: On power, privacy and participation. Energy Res. Soc. Sci. 2015, 9, 125–136. [Google Scholar] [CrossRef]
- Marikyan, D.; Papagiannidis, S.; Alamanos, E. A systematic review of the smart home literature: A user perspective. Technol. Forecast. Soc. Chang. 2019, 138, 139–154. [Google Scholar] [CrossRef]
- Kraemer, M.J.; Flechais, I. Researching Privacy in Smart Homes: A Roadmap of Future Directions and Research Methods. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT-2018, London, UK, 28–29 March 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Pal, D.; Triyason, T.; Funilkul, S. Smart Homes and Quality of Life for the Elderly: A Systematic Review. In Proceedings of the 2017 IEEE International Symposium on Multimedia (ISM), Taichung, Taiwan, 11–13 December 2017; pp. 413–419. [Google Scholar] [CrossRef]
- Aleisa, N.; Renaud, K. Privacy of the Internet of Things: A Systematic Literature Review. In Proceedings of the 50th Hawaii International Conference on System Sciences, Waikoloa Village, HI, USA, 4–7 January 2017. [Google Scholar] [CrossRef]
- Watzlaf VJ, M.; Zhou, L.; Dealmeida, D.R.; Hartman, L.M. A systematic review of research studies examining telehealth privacy and security practices used by healthcare providers. Int. J. Telerehabilitation 2017, 9, 39–50. [Google Scholar] [CrossRef] [PubMed]
- Abrilahij, A.; Boll, T. A Qualitative Metasynthesis of Reasons for the Use or Nonuse of Assistive Technologies in the Aging Population. Geropsych-J. Gerontopsychol. Geriatr. Psychiatry 2019, 32, 79–92. [Google Scholar] [CrossRef]
- Pawson, R.; Greenhalgh, T.; Harvey, G.; Walshe, K. Realist review: A new method of systematic review designed for complex policy interventions. J. Health Serv. Res. Policy 2005, 10 (Suppl. 1), 21–34. [Google Scholar] [CrossRef]
- Saul, J.E.; Willis, C.D.; Bitz, J.; Best, A. A time-responsive tool for informing policy making: Rapid realist review. Implement. Sci. IS 2013, 8, 103. [Google Scholar] [CrossRef]
- Vigurs, C.; Maidment, C.; Fell, M.; Shipworth, D. A Review of Reviews of Smart Local Energy System Research; EnergyRev consortium: London, UK, 2021. [Google Scholar]
- Thomas, J.; Brunton, J.; Graziosi, S. EPPI-Reviewer 4: Software for Research Synthesis. EPPI-Centre Software; Social Science Research Unit: London, UK, 2010. [Google Scholar] [CrossRef]
- Reis, H.; Judd, C. (Eds.) Handbook of Research Methods in Social and Personality Psychology, 2nd ed.; Cambridge University Press: Cambridge, UK, 2014. [Google Scholar] [CrossRef]
- Cook, T.D.; Campbell, D.T. Quasi-Experimentation: Design & Analysis Issues for Field Settings; Houghton Mifflin: Boston, MA, USA, 1979; ISBN 10 0395307902. [Google Scholar]
- Bailey, J.; Axsen, J. Anticipating PEV buyers’ acceptance of utility controlled charging. Transp. Res. Part A-Policy Pract. 2015, 82, 29–46. [Google Scholar] [CrossRef]
- Begier, B. Effective cooperation with energy consumers: An example of an ethical approach to introduce an innovative solution. J. Inf. Commun. Ethics Soc. 2014, 12, 107–121. [Google Scholar] [CrossRef]
- BEIS. Smart Metering Implementation Programme: Review of the Data Access and Privacy Framework. 2018, p. 40. Available online: https://www.gov.uk/government/publications/smart-metering-implementation-programme-review-of-the-data-access-and-privacy-framework (accessed on 22 February 2021).
- Choe, E.K.; ConsIvo, S.; Jung, J.; Harrison, B.; Patel, S.N.; Kientz, J.A. Investigating Receptiveness to Sensing and Inference in the Home Using Sensor Proxies. In Ubicomp’12: Proceedings of the 2012 ACM International Conference on Ubiquitous Computing; Association for Computing Machinery: New York, NY, USA, 2012; pp. 61–70. Available online: https://WOS:000494987600007 (accessed on 22 February 2021).
- Citizens Advice Bureau. Clear and in Control: Energy Consumers’ Views on Data Sharing and Smart Devices. 2019. Available online: https://www.citizensadvice.org.uk/Global/CitizensAdvice/Energy/Clear%20and%20in%20control%20-%20Energy%20consumers’%20views%20on%20data%20sharing%20and%20smart%20devices.pdf (accessed on 17 February 2021).
- Da Silva, P.G.; Karnouskos, S.; Ilic, D. A Survey Towards Understanding Residential Prosumers in Smart Grid Neighbourhoods. In Proceedings of the 2012 3rd IEEE PES Innovative Smart Grid Technologies Europe (ISGT Europe), Berlin, Germany, 14–17 October 2012; pp. 1–8. [Google Scholar] [CrossRef]
- Delmas, M.A.; Lessem, N. Saving power to conserve your reputation? The effectiveness of private versus public information. J. Environ. Econ. Manag. 2014, 67, 353. [Google Scholar] [CrossRef]
- Fell, M.J.; Shipworth DHuebner, G.M.; Elwell, C.A. Knowing Me, Knowing You: The role of trust, locus of control and privacy concern in acceptance of domestic electricity demand-side response. In Proceedings of the ECEEE 2015 Summer Study on Energy Efficiency Presqu’île de Giens, Toulon/Hyères, France, 1–6 June 2015; pp. 2153–2163. Available online: https://www.eceee.org/library/conference_proceedings/eceee_Summer_Studies/2015/9-dynamics-of-consumption/knowing-me-knowing-you-the-role-of-trust-locus-of-control-and-privacy-concern-in-acceptance-of-domestic-electricity-demand-side-response/ (accessed on 22 February 2021).
- Giordano, V.; Gangale, F.; Fulli, G.; Jiméne, M.S. Smart grid projects in Europe: Lessons learned and current developments. 2011. Available online: https://op.europa.eu:443/en/publication-detail/-/publication/8fa38f9a-f163-496d-bd98-3ae1dfa96861/language-en/format-PDF (accessed on 22 February 2021).
- Guerreiro, S.; Batel Susana Lima, M.L.; Moreira, S. Making energy visible: Sociopsychological aspects associated with the use of smart meters. Energy Effic. 2015, 8, 1149–1167. [Google Scholar] [CrossRef]
- Hansen, M.; Hauge, B. Scripting, control, and privacy in domestic smart grid technologies: Insights from a Danish pilot study. Energy Res. Soc. Sci. 2017, 25, 112–123. [Google Scholar] [CrossRef]
- Hess, D.J. Smart meters and public acceptance: Comparative analysis and governance implications. Health Risk Soc. 2014, 16, 243–258. [Google Scholar] [CrossRef]
- Hmielowski, J.D.; Boyd, A.D.; Harvey, G.; Joo, J. The social dimensions of smart meters in the United States: Demographics, privacy, and technology readiness. Energy Res. Soc. Sci. 2019, 55, 189–197. [Google Scholar] [CrossRef]
- Hoenkamp, R.A.; Huitema, G.B. Good Standards for Smart Meters. In Proceedings of the 2012 9th International Conference on the European Energy Market, Florence, Italy, 10–12 May 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Horne, C.; Darras, B.; Bean, E.; Srivastava, A.; Frickel, S. Privacy, technology, and norms: The case of Smart Meters. Soc. Sci. Res. 2015, 51, 64–76. [Google Scholar] [CrossRef]
- Huang, C.; Sankar, L. Incentive Mechanisms for Privacy-Sensitive Electricity Consumers with Alternative Energy Sources. In Proceedings of the 2016 Annual Conference on Information Science and Systems (CISS), Princeton, NJ, USA, 16–18 March 2016; pp. 175–180. [Google Scholar] [CrossRef]
- Jakobi, T.; Ogonowski, C.; Castelli, N.; Stevens, G.; Wulf, V. The Catch(es) with Smart Home—Experiences of a Living Lab Field Study. In Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems, Denver, CO, USA, 6–11 May 2017; pp. 1620–1633. [Google Scholar] [CrossRef]
- Jakobi, T.; Patil, S.; Randall, D.; Stevens, G.; Wulf, V. It Is About What They Could Do with the Data: A User Perspective on Privacy in Smart Metering. ACM Trans. Comput.-Hum. Interact. 2019, 26, 2. [Google Scholar] [CrossRef]
- Kapade, N. Credit based system for fair data sharing in smart Grid. In Proceedings of the 2017 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 5–7 January 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Melville, E.; Christie, I.; Burningham, K.; Way, C.; Hampshire, P. The electric commons: A qualitative study of community accountability. Energy Policy 2017, 106, 12. [Google Scholar] [CrossRef]
- Moere, A.V.; Tomitsch, M.; Hoinkis, M.; Trefz, E.; Johansen, S.; Jones, A. Comparative Feedback in the Street: Exposing Residential Energy Consumption on House Facades. In Human-Computer Interaction—Interact 2011 Lecture Notes in Computer Science; Campos, P., Graham, N., Jorge, J., Nunes, N., Palanque, P., Winckler, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6946. [Google Scholar] [CrossRef]
- Ofgem. Ofgem Consumer First Panel, Year 9, Wave 3, Half-Hourly Settlement. 2018. Available online: https://www.ofgem.gov.uk/publications-and-updates/ofgem-consumer-first-panel-year-9-wave-3-half-hourly-settlement (accessed on 22 February 2021).
- Pournaras, E.; Nikolic, J.; Velasquez, P.; Trovati, M.; Bessis, N.; Helbing, D. Self-regulatory information sharing in participatory social sensing. EPJ Data Sci. 2016, 5, 14. [Google Scholar] [CrossRef]
- Sexton, A.; Shepherd, E.; Duke-Williams, O.; Eveleigh, A. The role and nature of consent in government administrative data. Big Data Soc. 2018, 5, 1–17. [Google Scholar] [CrossRef]
- Snow, S.; Radke, K.; Vyas, D.; Brereton, M. Privacy in the New Era of Visible and Sharable Energy-Use Information. In Proceedings of the OzCHI ‘14 26th Australian Computer-Human Interaction Conference on Designing Futures: The Future of Design, Sydney, Australia, 2–5 December 2014; pp. 342–351. [Google Scholar] [CrossRef]
- Horne, C.; Przepiorka, W. Technology use and norm change in online privacy: Experimental evidence from vignette studies. Inf. Commun. Soc. 2019, 3–18. [Google Scholar] [CrossRef]
- Toft, M.B.; Thøgersen, J. Exploring private consumers’ willingness to adopt Smart Grid technology. Int. J. Consum. Stud. 2015, 39, 648–660. [Google Scholar] [CrossRef]
- Valor, C.; Escudero, C.; Labajo, V.; Cossent, R. Effective design of domestic energy efficiency displays: A proposed architecture based on empirical evidence. Renew. Sustain. Energy Rev. 2019, 114, 109301. [Google Scholar] [CrossRef]
- Van Aubel, P.; Poll, E. Smart metering in the Netherlands: What, how, and why. Int. J. Electr. Power Energy Syst. 2019, 109, 719–725. [Google Scholar] [CrossRef]
- Vermont Transco LLC. Customer Participation in the Smart Grid—Lessons Learned. 2014. Available online: https://www.energy.gov/sites/prod/files/2014/10/f18/SG-CustParticipation-Sept2014.pdf (accessed on 22 February 2021).
- Walter, J.; Abendroth, B. Losing a Private Sphere? A Glance on the User Perspective on Privacy in Connected Cars. In Advanced Microsystems for Automotive Applications 2017. Lecture Notes in Mobility; Zachäus, C., Müller, B., Meyer, G., Eds.; Springer: Cham, Switzerland, 2017. [Google Scholar] [CrossRef]
- Winter, J.S. Citizen Perspectives on the Customization/Privacy Paradox Related to Smart Meter Implementation. Int. J. Technoethics 2015, 6, 45–59. [Google Scholar] [CrossRef]
- Yao, Y.X.; Basdeo, J.R.; Kaushik, S.; Wang, Y. Defending My Castle: A Co-Design Study of Privacy Mechanisms for Smart Homes. In Proceedings of the CHI ‘19: 2019 CHI Conference on Human Factors in Computing Systems, Glasgow, Scotland, 4–9 May 2019. [Google Scholar] [CrossRef]
- Maidment, C.; Vigurs, C.; Fell, M.; Shipworth, D. A Systematic Map of Smart Local Energy Research; EnergyRev consortium: London, UK, 2021; Forthcoming. [Google Scholar]
- Bronfenbrenner, U. The Ecology of Human Development; Harvard University Press: Cambridge, MA, USA, 1979; ISBN 10 0674224574. [Google Scholar]
- Thiesse, F. RFID, privacy, and the perception of risk: A strategic framework. J. Strateg. Inf. Syst. 2007, 16, 214–232. [Google Scholar] [CrossRef]
- Lesic, V.; Glasgo, B.; Krishnamurti, T.; Bruin, W.B.; Davis, M.; Azevedo, I.L. Comparing consumer perceptions of appliances’ electricity use to appliances’ actual direct-metered consumption. Environ. Res. Commun. 2019, 1, 111002. [Google Scholar] [CrossRef]
- Barr, S. Environmental action in the home: Investigating the value-action gap. Geography 2006, 91, 43–54. Available online: www.jstor.org/stable/40574132 (accessed on 17 February 2021). [CrossRef]
- Chan, K. Environmental attitudes and behaviors of secondary schools’ students in Hong Kong. Environmentalist 1996, 16, 279–306. [Google Scholar] [CrossRef]
- Bogo, J. Sustainability 101: Using the community as a classroom, colleges are rewriting the standards for environmental education. Environ. Mag. 1999, 10, 36–40. Available online: https://www.thefreelibrary.com/Sustainability+101.-a057800744 (accessed on 17 February 2021).
- Anable, J.; Lane, B.; Kelay, T. An Evidence Base Review Of public Attitudes to Climate Change and Transport Behavior: Final Report; Contract PPRO 004/006/006; Department of Transport: London, UK, 2006. Available online: http://www.dft.gov.uk/pgr/sustainable/reviewtransportbehaviourclimatechange/pdf/iewofpublicattitudestocl5730.pdf (accessed on 22 February 2021).
- Lai, I.K.W.; Liu, Y.; Sun, X.; Zhang, H.; Xu, W. Factors influencing the behavioural intention towards full electric vehicles: An empirical study in Macau. Sustainability 2015, 7, 12564–12585. [Google Scholar] [CrossRef]
- Flynn, R.; Bellaby, P.; Ricci, M. The ‘Value-Action Gap’ in Public Attitudes towards Sustainable Energy: The Case of Hydrogen Energy. Sociol. Rev. 2009, 57, 159–180. [Google Scholar] [CrossRef]
- Sanchez-Sabate, R.; Sabaté, J. Consumer Attitudes Towards Environmental Concerns of Meat Consumption: A Systematic Review. Int. J. Environ. Res. Public Health 2019, 16, 1220. [Google Scholar] [CrossRef]
- Blankenberg, A.-K.; Alhusen, H. On the Determinants of Pro-Environmental Behavior: A Literature Review and Guide for the Empirical Economist, Center for European, Governance and Economic Development Research Discussion Papers 350; University of Göttingen, Department of Economics: Göttingen, Germany, 2019. [Google Scholar] [CrossRef]
- Nuttall, L.; Evans, J.; Franklin, M.; James, S.B. Coercive Control Resistant Design the Key to Safer Technology; IBM: Armonk, NY, USA, 2019; Available online: https://www.ibm.com/blogs/policy/wp-content/uploads/2020/05/CoerciveControlResistantDesign.pdf (accessed on 17 February 2021).
- Office for National Statistics. Coronavirus and Homeworking in the UK Labour Market: 2019. Available online: https://www.ons.gov.uk/employmentandlabourmarket/peopleinwork/employmentandemployeetypes/articles/coronavirusandhomeworkingintheuklabourmarket/2019 (accessed on 23 November 2020).
- Legros, S.B. Mapping the Social-Norms Literature: An Overview of Reviews. Perspect. Psychol. Sci. 2019, 15, 62–80. [Google Scholar] [CrossRef] [PubMed]
- Cialdini, R.B.; Trost, M.R. Social influence: Social norms, conformity and compliance. In the Handbook of Social Psychology; Gilbert, D.T., Fiske, S.T., Lindzey, G., Eds.; McGraw-Hill: New York, NY, USA, 1998; pp. 151–192. ISBN 978-0-470-13747-5. [Google Scholar]
- Le Zion, R.; Tene, O.; Polonetsky, I.J. A Theory of Creepy: Technology, Privacy, and Shifting Social Norms. Yale J. Law Technol. 2014, 16, 59. Available online: https://digitalcommons.law.yale.edu/yjolt/vol16/iss1/2 (accessed on 22 February 2021).
- Renn, O.; Burns, W.J.; Kasperson, J.X.; Kasperson, R.E.; Slovic, P. The Social Amplification of Risk: Theoretical Foundations and Empirical Applications. J. Soc. Issues 1992, 48, 137–160. [Google Scholar] [CrossRef]
- Chew, C.; Eysenbach, G. Pandemics in the Age of Twitter: Content Analysis of Tweets during the 2009 H1N1 Outbreak. PLoS ONE 2010, 5, e14118. [Google Scholar] [CrossRef] [PubMed]
- Easton, D. A Systems Analysis of Political Life; John Wiley: New York, NY, USA, 1965. [Google Scholar] [CrossRef]
- Zhou, K.; Fu, C.; Yang, S. Big data driven smart energy management: From big data to big insights. Renew. Sustain. Energy Rev. 2016, 56, 215–225. [Google Scholar] [CrossRef]
- Coe, C.; Gibson, A.; Spencer, N.; Stuttaford, M. Sure Start: Voices of the “hard to reach”. Child: Care Health Dev. 2008, 34, 447–453. [Google Scholar] [CrossRef] [PubMed]
- Madden, M.; Rainie, L. American Attitudes towards Privacy, Security and Surveillance; Pew Research Center: Washington, DC, USA, 2015; Available online: https://www.pewresearch.org/internet/2015/05/20/americans-attitudes-about-privacy-security-and-surveillance/ (accessed on 16 February 2021).
- National Energy Action. Warm Homes Fund: Programme Evaluation. Abridged Interim Report; National Energy Action: Newcastle upon Tyne, UK, 2020; Available online: https://www.nea.org.uk/wp-content/uploads/2020/01/Warm-Homes-Fund-Programme-Evaluation-Abridged-FINAL-13.07.20.pdf (accessed on 17 February 2021).
- Johnson, C.Y.; Bowker, J.M.; Cordell, H.K. Ethnic variation in environmental belief and behavior: An examination of the new ecological paradigm in a social psychological context. Environ. Behav. 2004, 36, 157–186. [Google Scholar] [CrossRef]
- Klobas, J.E.; McGill, T.; Wang, X.Q. How perceived security risk affects intention to use smart home devices: A reasoned action explanation. Comput. Secur. 2019, 87, 13. [Google Scholar] [CrossRef]
- GJaffe, A.; Stavins, R. Energy-Efficiency Investments and Public Policy. Energy J. 1994, 15, 43–65. Available online: http://www.jstor.org/stable/41322875 (accessed on 23 November 2020).
- Mccarthy, L.; Ambrose, A.; Pinder, J. Energy (in)Efficiency: Exploring What Tenants Expect and Endure in the Private Rented Sector in England. Making the Case for More Research into the Tenant’s Perspective. An Evidence Review; Sheffield Hallam University: Sheffield, UK, 2016; Available online: http://shura.shu.ac.uk/15615/ (accessed on 17 February 2021).
- National Statistics. The Family Resources Survey, 2018/19; Department for Work and Pensions: London, UK, 2020. [Google Scholar]
- Office for National Statistics. The UK Private Rented Sector. Housing, Communities and Local Government. 2019. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/874507/family-resources-survey-2018-19.pdf (accessed on 17 February 2021).
- Burns, J.; Hood, M. Transparency and Trust: A Guide to Data Protection and Privacy for Landlords and Tenants. 2017. Available online: https://www.housemark.co.uk/media/1766/dataprotection_report_v7.pdf (accessed on 17 February 2021).
- McCabe, A.; Pojani, D.; Broese van Groenou, A. The application of renewable energy to social housing: A systematic review. Energy Policy 2018, 114, 549–557. [Google Scholar] [CrossRef]
- Bahaj, A.S.; James, P.A.B. Urban energy generation: The added value of photovoltaics in social housing. Renew. Sustain. Energy Rev. 2007, 11, 2121–2136. [Google Scholar] [CrossRef]
- Moore, N.; Haines, V.; Lilley, D. Improving the installation of renewable heating technology in UK social housing properties through user centred design. Indoor Built Environ. J. Int. Soc. Built Environ. 2015, 24, 970–985. [Google Scholar] [CrossRef] [PubMed]
- Pickvance, C.G. Choice or coercion: Dilemmas of sustainable social housing. A study of two developments in Kent. Local Environ. 2009, 14, 207–214. [Google Scholar] [CrossRef]
- Wheal, R.; Fulford, D.; Wheldon, A.; Oldach, R. Photovoltaics (PV) in social housing. Int. J. Ambient Energy 2004, 25, 12–18. [Google Scholar] [CrossRef]
- Elvers, H.; Jandrig, B.; Grummich, K.; Tannert, C. Mobile phones and health: Media coverage study of German newspapers on possible adverse health effects of mobile phone use. Health Risk Soc. 2009, 11, 165–179. [Google Scholar] [CrossRef]
- Cousin, M.; Siegrist, M. The public’s knowledge of mobile communication and its influence on base station siting preferences. Health Risk Soc. 2010, 12, 231–250. [Google Scholar] [CrossRef]
- Claassen, L.; Smid, T.; Woudenberg, F.; Timmermans, D.R.M. Media coverage on electromagnetic fields and health: Content analysis of Dutch newspaper articles and websites. Health Risk Soc. 2012, 14, 681–696. [Google Scholar] [CrossRef]
- Nissenbaum, H. Privacy as contextual integrity. Wash. Law Rev. 2004, 79, 119–157. [Google Scholar]
- Clayton, S.; Opotow, S. Justice and Identity: Changing Perspectives on What Is Fair. Personal. Soc. Psychol. Rev. 2003, 7, 298–310. [Google Scholar] [CrossRef] [PubMed]
- Zalta, E.N. (Ed.) The Stanford Encyclopedia of Philosophy; The Metaphysics Research Lab: Stanford, CA, USA, 2004; Available online: https://plato.stanford.edu/archives/win2012/entries/davidson/ (accessed on 17 February 2021).
- Rawls, J. Justice as Fairness: A Restatement; Harvard University Press: Cambridge, MA, USA, 2001; ISBN 9780674005112. [Google Scholar]
- Taylor, L. The ethics of big data as a public good: Which public? Whose good? Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 2016, 374, 20160126. [Google Scholar] [CrossRef] [PubMed]
- Davis, F. Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology. MIS Q. 1989, 13, 319–340. [Google Scholar] [CrossRef]
- Pavlou, P. Consumer Intentions to Adopt Electronic Commerce—Incorporating Trust and Risk in the Technology Acceptance Model. DIGIT 2001 Proceedings. 2001. Available online: https://aisel.aisnet.org/digit2001/2 (accessed on 17 February 2021).
- Kranz, J.; Gallenkamp, J.; Picot, A. Power control to the people? Private consumers’ acceptance of smart meters. In Proceedings of the 18th European Conference on Information Systems (ECIS), Pretoria, South Africa, 7–9 June 2010; Available online: https://aisel.aisnet.org/ecis2010/96/ (accessed on 17 February 2021).
- Stragier, J. Introducing smart grids in residential contexts: Consumers’ perception of smart household appliances. In Proceedings of the 2010 IEEE Conference on Innovative Technologies for an Efficient and Reliable Electricity Supply (CITRES), Waltham, MA, USA, 27–29 September 2010; Available online: https://biblio.ugent.be/publication/1065521 (accessed on 21 February 2021). [CrossRef]
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Rotter, J.B. Generalized expectancies for internal versus external control of reinforcement. Psychol. Monogr. Gen. Appl. 1966, 80, 1. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, 5th ed.; Free Press: New York, NY, USA, 2003; ISBN 10 0743222091. [Google Scholar]
- Garling, A.; Thogersen, J. Marketing of electric vehicles. Bus. Strategy Environ. 2001, 10, 53–65. [Google Scholar] [CrossRef]
- Arts, J.W.C.; Frambach, R.T.; Bijmolt, T.H.A. Generalizations on consumer innovation adoption: A meta-analysis on the drivers of intention and behavior. Int. J. Res. Mark. 2011, 28, 134–144. [Google Scholar] [CrossRef]
- O’Neill, J.; Tabish, H.; Welch, V.; Petticrew, M.; Pottie, K.; Clarke, M.; Evans, T.; Pardo, J.; Waters, E.; White, H.; et al. Applying an equity lens to interventions: Using PROGRESS ensures consideration of socially stratifying factors to illuminate inequities in health. J. Clin. Epidemiol. 2014, 67, 56–64. [Google Scholar] [CrossRef] [PubMed]
- Oliver, S.; Kavanagh, J.; Caird, J.; Lorenc, T.; Oliver, K.; Harden, A. Health Promotion, Inequalities and Young People’s Health. A Systematic Review of Research. 2008. Available online: http://eppi.ioe.ac.uk/cms/LinkClick.aspx?fileticket=lsYdLJP8gBI%3d&tabid=2412&mid=4471&language=en-US (accessed on 17 February 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vigurs, C.; Maidment, C.; Fell, M.; Shipworth, D. Customer Privacy Concerns as a Barrier to Sharing Data about Energy Use in Smart Local Energy Systems: A Rapid Realist Review. Energies 2021, 14, 1285. https://doi.org/10.3390/en14051285
Vigurs C, Maidment C, Fell M, Shipworth D. Customer Privacy Concerns as a Barrier to Sharing Data about Energy Use in Smart Local Energy Systems: A Rapid Realist Review. Energies. 2021; 14(5):1285. https://doi.org/10.3390/en14051285
Chicago/Turabian StyleVigurs, Carol, Chris Maidment, Michael Fell, and David Shipworth. 2021. "Customer Privacy Concerns as a Barrier to Sharing Data about Energy Use in Smart Local Energy Systems: A Rapid Realist Review" Energies 14, no. 5: 1285. https://doi.org/10.3390/en14051285
APA StyleVigurs, C., Maidment, C., Fell, M., & Shipworth, D. (2021). Customer Privacy Concerns as a Barrier to Sharing Data about Energy Use in Smart Local Energy Systems: A Rapid Realist Review. Energies, 14(5), 1285. https://doi.org/10.3390/en14051285






