A New Hybrid Online and Offline Multi-Factor Cross-Domain Authentication Method for IoT Applications in the Automotive Industry
Abstract
:1. Introduction
2. Related Works
3. Functionality and Security Goals
- Mutual Authentication: To ensure the effectiveness of all participants, the vehicles and the servers need to authenticate each other.
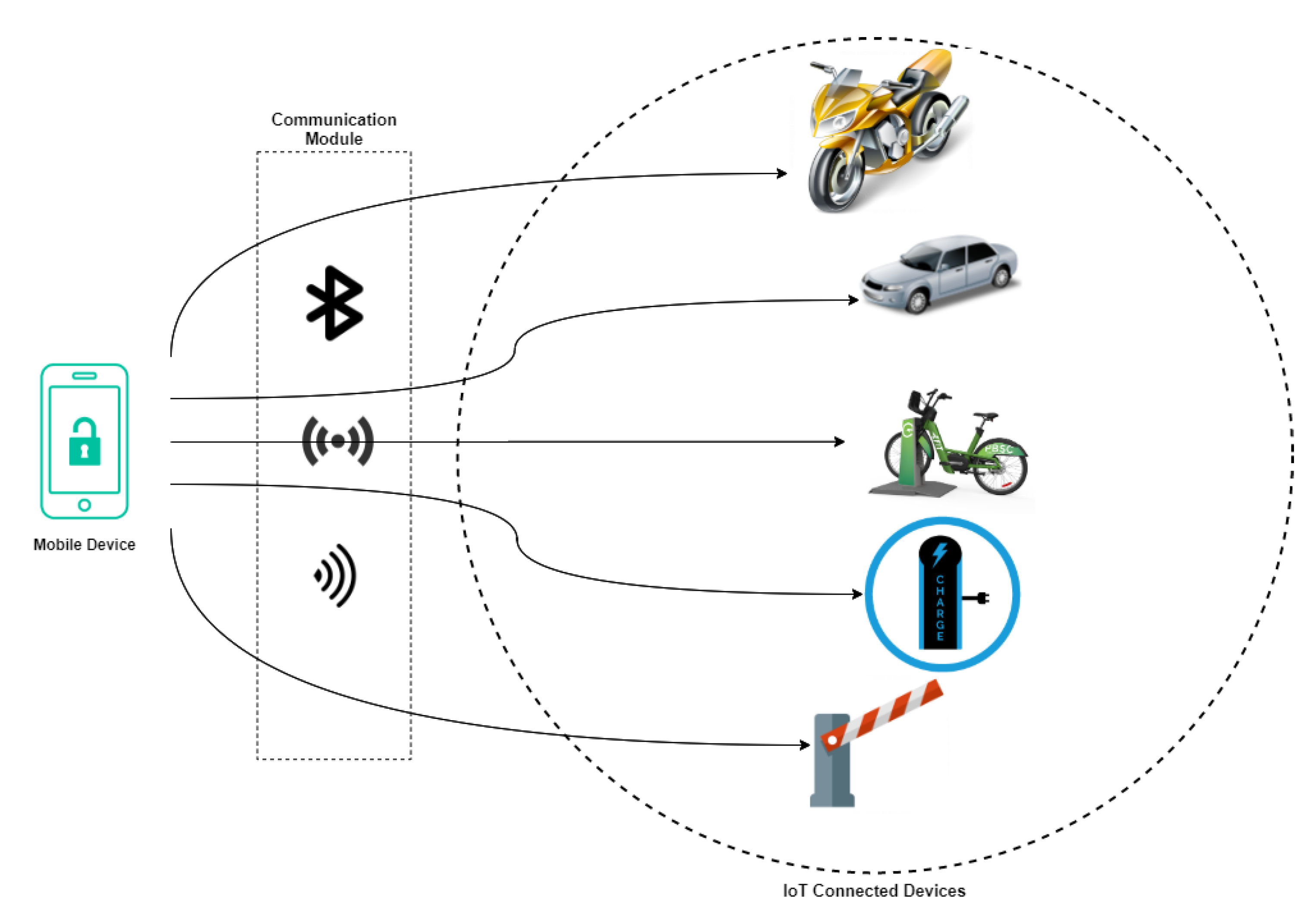
- Offline Authentication: The car or any IoT-connected devices solutions depend on connected vehicles, which restricts their functional areas to areas with a stable network link. To address this restriction, we require users to authenticate offline during car (un)locking, allowing car-sharing services to go to areas with less secure networks or no network access at all.
- Vehicle anonymity: When a user uploads his ID to the medical server, adversaries should not obtain the user’s identity during the registration process.
- Low Computing Cost: The IoT devices are resource constrained devices with low power, so the authentication schemes must be designed with low computational costs to suit the IoT devices’ requirements.
- Integrity: The vehicle may authenticate each message to ensure that it was not tampered with by an adversary.
- Confidentiality: Passive attacks such as eavesdropping or traffic monitoring should not be able to access vehicle data. As a result, only designated individuals have access to or use vehicle data.
- Forward Secrecy: The proposed protocol should provide backwards and forwards confidentiality to ensure the protection of messages exchanged in previous and future communications. Even if the adversary obtains the current session key, he cannot get the session keys created in prior and subsequent sessions.
- Resistance Against Attacks: In-vehicle and device communication, any newly developed authentication scheme must be resistant to masquerade attacks, alteration attacks, replay attacks, and man-in-the-middle attacks.
- −
- Replay attacks: In IoT-connected vehicles, replay attacks should be prevented by using timestamps and random numbers in the transmitted messages [48].
- −
- Man-in-middle attack: An adversary intercepts the messages sent between the vehicle and server and replaces them with messages.
- −
- Offline password guessing attack: In this attack, an attacker can employ some of the intercepted information, such as keys, or the self-generated parameters, to guess the user’s password [49]. These attacks can never be "prevented," but protocols can be made secure against such attacks.
- −
- Server spoofing attack: This attack can be solved entirely by providing mutual authentication between vehicle and server.
- −
- Privileged insider attack: When the server needs to retain the user’s password for later authentication, the keys are probably being stolen by the adversary because the server can find out the patient’s new password.
- −
- Denial of service (DoS) attack: Services are denied to the attackers by the automative users/vehicles and the servers [50].
- −
- Impersonation attack: A dishonest user can easily impersonate another legal user.
4. Cryptography Materials
4.1. Elliptic Curve Cryptography (ECC)
4.2. AES-ECC Algorithm
- Input data, i.e., username, password, and a biometric of the user using a smartphone.
- The data are hashed using the SHA-2 function to generate a hash value for data summary.
- It generates a digital signature using a private sender key and an ECC digital signature.
- Using the private key of the AES, the sender encrypts the digital signature and the data that need to be sent result in data ciphertext and signature ciphertext.
- The sender then encrypts the AES private key using the ECC encryption module to generate the key ciphertext. Then, it sends the ciphertext via the Internet.
- Upon receiving, the receiver uses his private key to decrypt the AES key; then, it decrypts the data ciphertext and signature ciphertext using the AES key.
- Based on the sender’s public key, the receiver verifies the signature to summarize the received data and the hash value using the SHA-2 function. If the value is the same, then the data are valid; otherwise, the session is ended.
5. Proposed Scheme
5.1. Setup Phase
5.2. User Registration Phase
- The user inputs the identity , passwords , and imprint biometrics . The mobile device picks a pseudonym identity . Then, it generates a random number as a private vehicle key and calculates the vehicle public key . Later, it generates a random number and computes . The the message is encrypted with AES public key alongside the user biometric and sends to AS.
- Upon receiving , the AS decrypts the message using the AES public key to obtain the user’s information.The AS then verifies the user’s identity and password with the one stored in its database; if it exists, it notifies the user Ui. Otherwise, it computes where d is the AS’s private key. Then, the mobile device MD generates nonce based on the timestamp and a check number (CN) , where CN is a six-digit number for user identification which is a value obtained by calculating the mod nanosecond. Then it encrypts the nonce with . Furthermore, it computes , and . The AS calculates and stores it in the database. Finally, it sends the parameters to the Ui.
- After receiving , it stores the parameters in the memory of the vehicle module.
5.3. Server Registration Phase
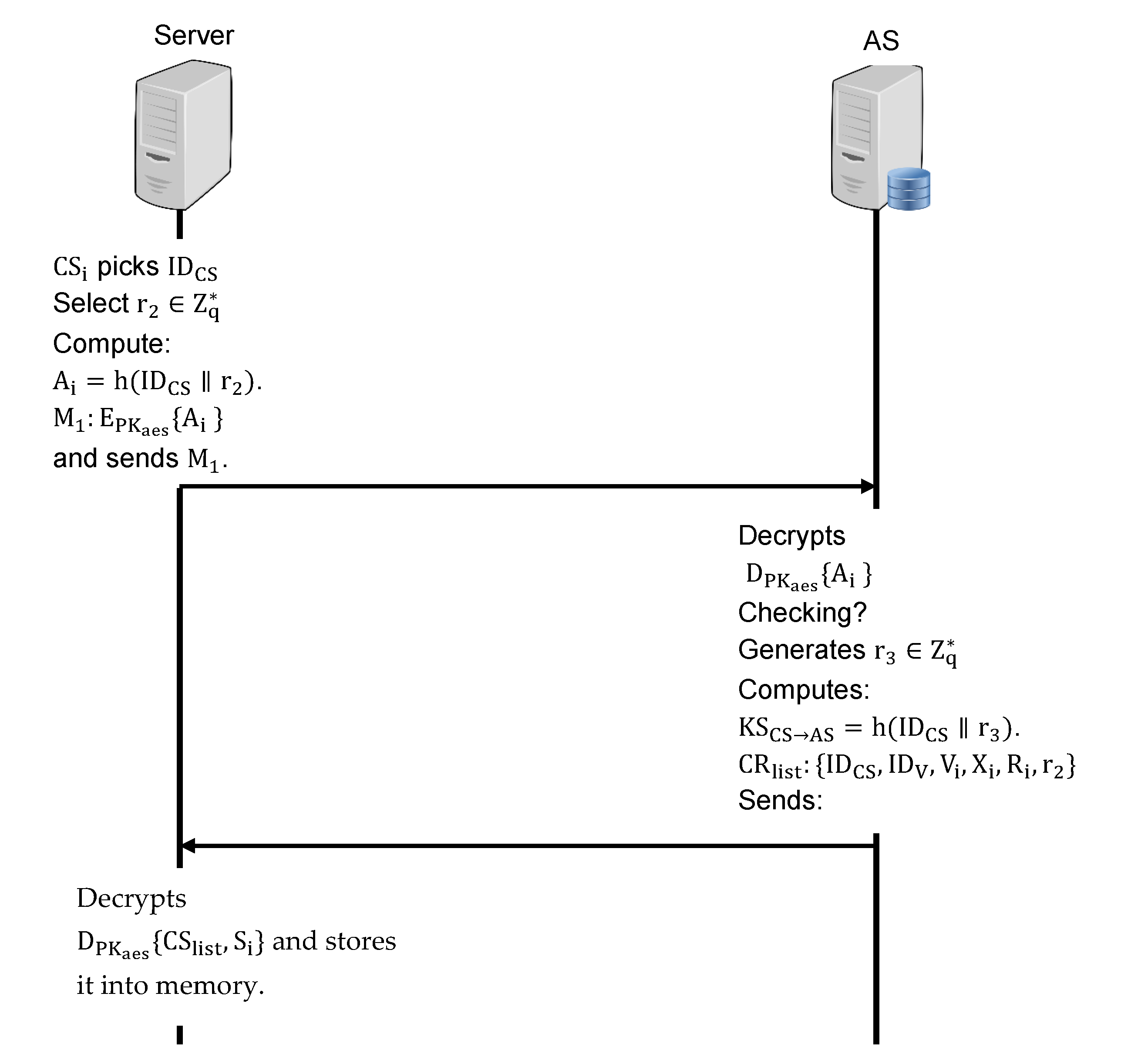
- The picks an identity and select a random number to compute . Then encrypt the message with AES’s public key and sends to the AS.
- The AS receives and decrypts using the public key to obtain the value , It checks whether the identity exists in the database or not; if so, the AS ask to reapply the registration. Otherwise, it generates a random number and computes a session key shared between the server and the AS . Furthermore, the AS will prepare a list that contains all the registered cards in the reader and a secret value to identify the server. Finally, the AS sends the to the server.
- Upon receiving, the decrypts the message using AES public key and obtain the . Then, it stores the values in its memory for future access.
5.4. Online Vehicle Booking
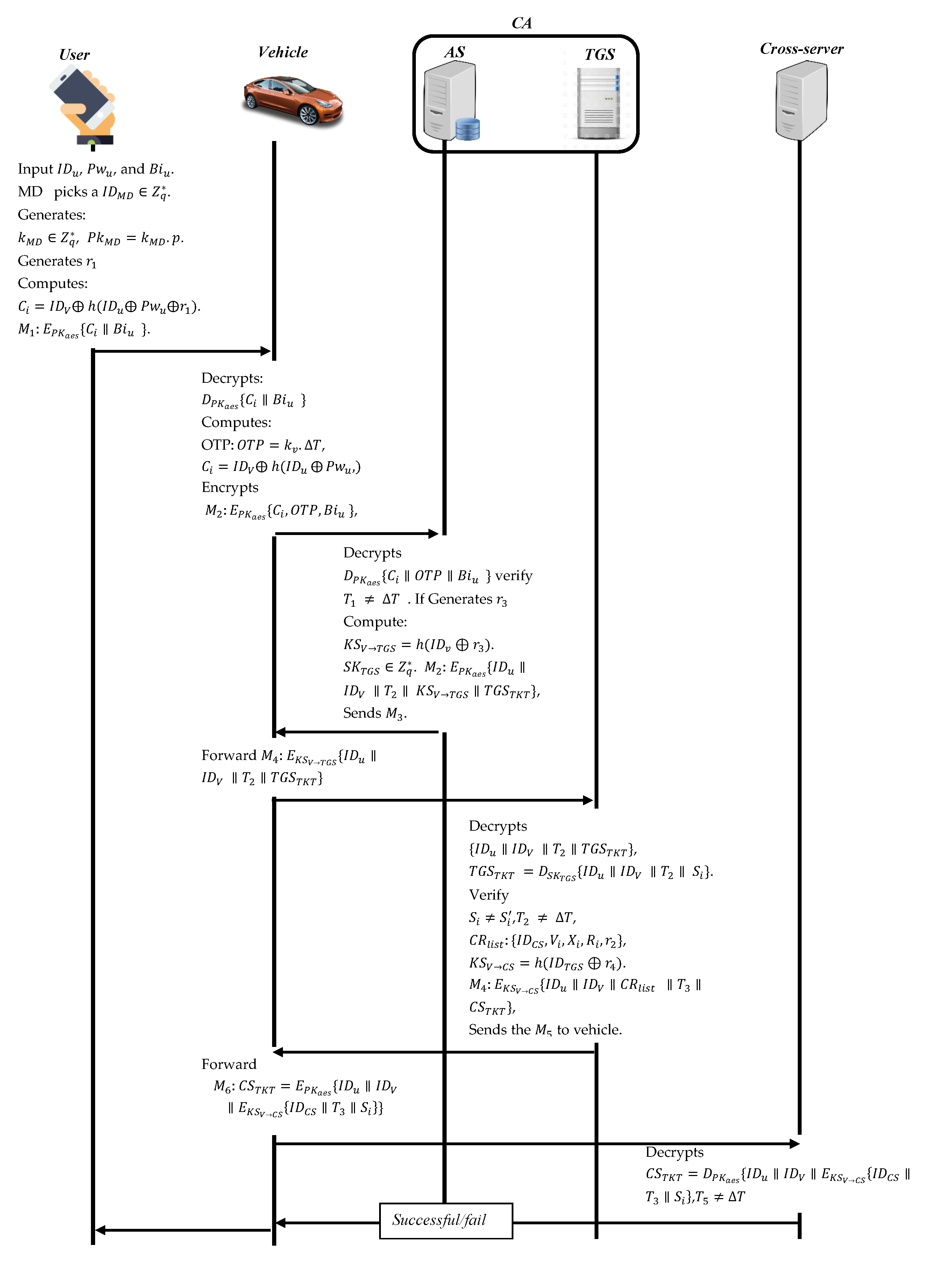
- The user inputs his identity , passwords , and imprint biometrics . The MD picks a pseudonym identity . Then, it generates a random number as MD private key and calculates the MD public key . Later, MD generates a random number and computes The message is encrypted with an AES public key alongside the user’s biometric and sends to the vehicle.
- Upon receiving , the vehicle decrypts the message using an AES public key to obtain the user’s information. The vehicle then verifies the user’s identity and password with the ones stored in its database. If they exist, notify the user’s Ui. Later, the vehicle computes 32 bits , where is the current time of the vehicle.The vehicle computes and encrypts ; then sends to the AS.
- When the AS receives it decrypts the message to obtain the values and verify the identity of the user and vehicle, and checks the freshness of the timestamp . If invalid, the session is ended. Furthermore, it verifies the received TOTP by matching with generated TOTP batch by the AS; if there is not a match, the session is ended; otherwise, it causes a random number and computes a shared key session to enable the vehicle to communicate with the ticket granting service (TGS) Then, the AS in trusted authority generates a secret key randomly for the TGS . It later computes the message , where the that can be decrypted by the TGS only. Finally, AS sends to the vehicle.
- The vehicle gets the and decrypts it using the AES public key to obtain . Then, it forwards the message to the TGS in the trusted authority.
- The TGS receives the message and decrypts it to obtain , and then decrypts the ticket .The TGS verifies the secret value ; if invalid, it ends the session; otherwise, it checks the freshness of the timestamp . If not new, it ends the session. Otherwise, it generates a random number and computes the key session shared between the vehicle and the cross-server Then, composes the message , where is . Finally, the TGS sends the to the vehicle.
- Upon receiving the , the vehicle decrypts the message to obtain the session key and the . Then, it decrypts the ticket . It forwards to the cross-server.
- The cross-server receives the and decrypts to obtain the values. Then, it checks the freshness of the timestamp . If not fresh, it ends the session; otherwise, the vehicle booking is successfully made.
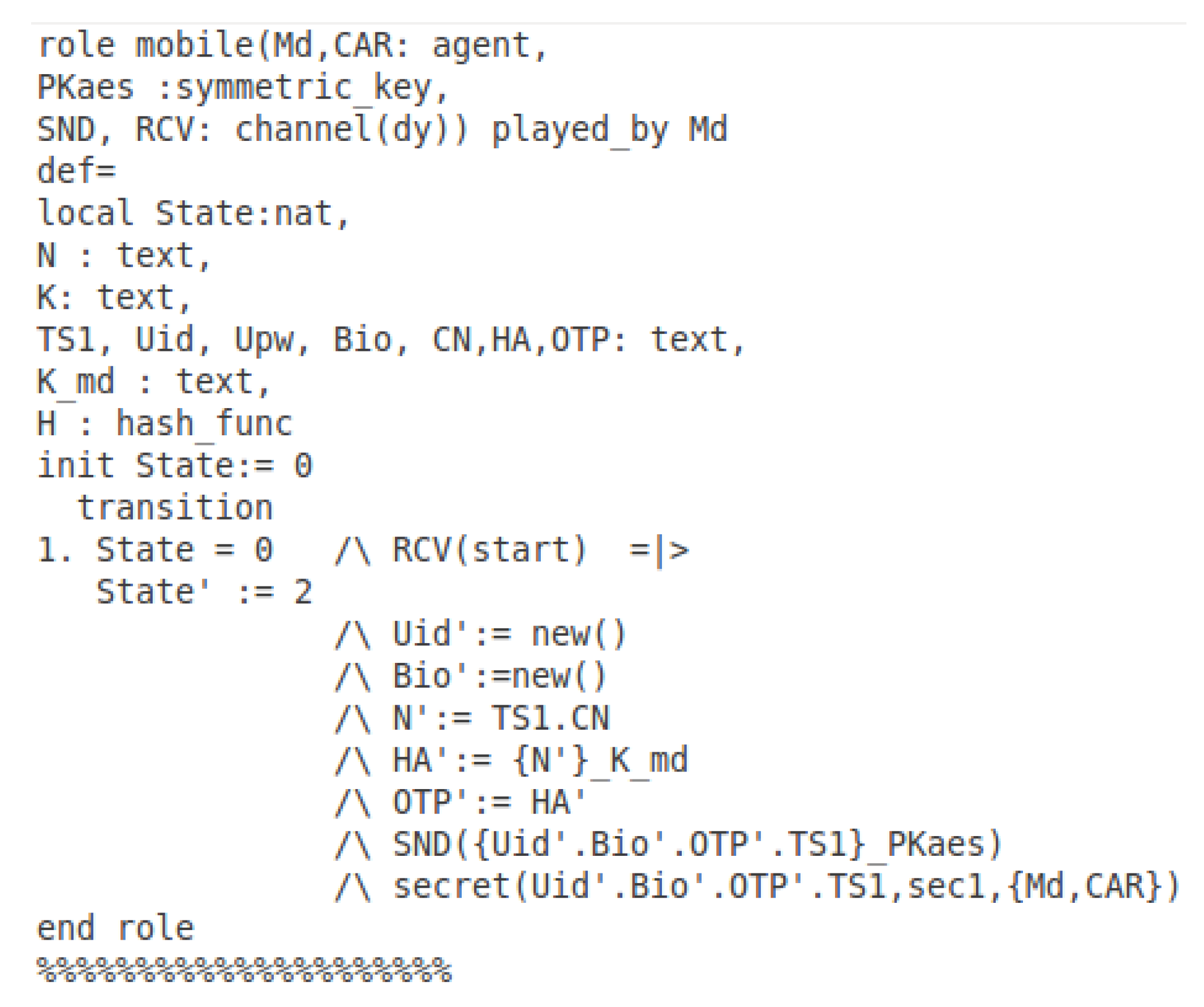
5.5. Offline Authentication
- The user inputs their information identity passwords , and imprint biometrics using the mobile device. The mobile device verifies the identity and biometrics with its database. Then, the mobile device MD generates nonce based on the timestamp and checks number where CN is a six-digit number for user identification which is a value obtained by calculating the mod in nanoseconds. Then encrypts the nonce with . Later, it generates the time one-time password TOTP . The mobile device encrypts the message with AES public key and sends to the vehicle.
- Upon receiving , the vehicle module decrypts it and obtains . The vehicle verifies the parameters by checking the timestamp , and verifies the identity and biometric. The TOTP is confirmed with the generated batch of TOTPs of the last period by the vehicle. If the provided TOTP does not match one of the batches and the number or the authentication attempts exceeds ten times, the authentication fails. A failed authentication notifies the user. Otherwise, successful offline authentication is established.
6. Security Analysis
6.1. Informal Security Analysis
- Mutual Authentication: The authentication scheme must provide mutual authentication between all the considered entities in the system. In the proposed scheme, the user can communicate with all entities by verifying the timestamp The freshness of the session key is checked by the AS and the TGS. Furthermore, the one-time password (OTP) is verified by the server with the generated batch to check the message’s validity and the OTP. Therefore, the proposed scheme provides a mutual authentication property.
- Froward secrecy: In the proposed scheme, the vehicle and the server compute the session key as hence, the adversary cannot obtain the values because the session key is encrypted with an AES public key and also the ECC key. Furthermore, a new random number is involved in calculating the key session, and the attacker cannot obtain the random value. The user’s information is further protected using the one-way hash function Thus, the adversary cannot obtain the user’s bits; therefore, the proposed scheme provides perfect forward secrecy.
- Anonymity: Anonymity is essential to protect the user’s information in the communication between the entities, since the transmission is done via a public channel. The user’s information is calculated and encrypted further with AES public key . The adversary will not be able to get the user identity, password, and biometric. Furthermore, this information is protected using a one-way hash function as well. Furthermore, the key session is generated freshly in every communication, and the adversary cannot track the communication between the entities. Assume the adversary could obtain the key session of the current transmission; he/she could not obtain the key session of the next communication. Therefore, the proposed scheme provides anonymity.
- Confidentiality: The proposed scheme ensures the confidentiality of the message by using a fresh random number The message is also encrypted using AES public key in every communication amongst the entities. In the offline authentication, the mobile device encrypts the value that used to calculate the OTP with device key . Furthermore, it encrypts the message with an AES key before transmission . Furthermore, the key session is generated independently in each communication. Therefore, the proposed scheme guarantees the confidentiality of the message.
- Integrity: The integrity of the messages transmitted during the authentication process is guaranteed in the proposed scheme, as the scheme verifies the message by comparing the received values with stored ones in the AS, TGS, and cross-server . The verification depends on the timestamp’s freshness and the secret values on the server side by calculating them to confirm the message’s authenticity. Therefore, the proposed scheme provides message integrity.
- Key freshness: In the proposed scheme, the shared key session is generated as independently. The key session is generated freshly in every communication session amongst the vehicle, AS, TGS, and cross-server. Hence, the adversary cannot obtain the key session since it calculates the identity and fresh random number. Assume the adversary obtained the current key session; he/she will not get the session key of the next communication. Therefore, the freshness of the key is provided by the proposed scheme.
- Offline Authentication: The proposed scheme provides an offline authentication between the mobile user device and the vehicle by providing the vehicle OTP=HA, and . The vehicle checks the timestamp , and verifies the identity and biometric. Furthermore, The TOTP is confirmed with the batch of TOTPs generated in the last period by the vehicle. If the provided OTP does not match one of the batches, the authentication fails; otherwise, successful offline authentication is established. Therefore, the proposed scheme provides offline authentication between the user and the vehicle.
- Cross-domain authentication: The vehicle can authenticate to any server registered with a central authority and in a different geographical location. The proposed scheme allows the user to authenticate with the server in the booking phase applied in online mode. The vehicle sends an authentication request to the central authority to get the ability to authenticate with a cross-server. Therefore, the proposed scheme provides cross-domain authentication.
- Replay attack: The freshness of the messages is guaranteed in each session, since the message is composed of a fresh timestamp The tickets and the messages , include a fresh timestamp. Upon receiving the message, the receiver checks the freshness of the timestamp by comparing it with the current time of the system The usually is very small to make it difficult for the adversary to replay the captured message within . The message is further encrypted with a temporary session key make it computationally infeasible for the adversary to modify the composing timestamp. Therefore, the proposed scheme is resilient to replay attacks.
- Impersonation attack: The adversary who wants to impersonate the user must calculate a valid in the online booking phase. The values are protected using a one-way hash function, and the adversary cannot decipher such values. Additionally, post-transmission is encrypted with the AES key for secure communication and to prevent attackers from capturing the user’s information. Therefore, the proposed scheme is resilient to impersonation attacks.
- Modification attack: In the proposed scheme, the message integrity is preserved using a one-way hash function to protect the user’s information. for example, the element guarantees prevention against modification attacks. Any alteration in the value O can easily be identified during the comparison and reconstruction of the message at another entity. Furthermore, the messages exchanged amongst entities are encrypted using AES public key, and the communication is retained. Assume the adversary captured the message ; it is computationally challenging for the adversary to make any changes as the information is encrypted with a temporary session key. Similarly, the exchanged messages are ciphered to prevent any modification. Therefore, the proposed scheme withstands the modification attack.
- Man-in the middle attack: In this attack, the adversary tries to modify the captured message in a way where the destination cannot differentiate the modified message from the original message. Assume the adversary applies an MiTM attack between the vehicle and the AS by capturing and modifying the message or the message between the vehicle and the TGS . The message’s construction is computationally hard for the adversary, as the message is double encrypted with both the fresh session key and an AES public key. Furthermore, the tickets, such as are encrypted, and each contains a ciphered timestamp and secret value that will be validated later by their respective destinations. Therefore, the proposed scheme is protected from a man-in-the-middle attack.
- Server spoofing attack: This attack tries to spoof a server by replaying an old authentication message . This attempt fails, since the user uses a new and different random number, and a fresh session key is used as well, which means the session key is used differently in each session. The session key of the current communication is different from those of the last and next sessions. Therefore, the proposed scheme is resilient to a server spoofing attack.
- Privileged insider attack: A privileged attack can allow access to a user’s information. Assume the adversary has the registration information of the user identity and ; he/she cannot guess the information as the information is protected using a one-way hash function and composed with a random number. Furthermore, the information is ciphered before transmission. Therefore, the proposed scheme withstands a privileged insider attack.
- Denial of service (DoS) attack: A DoS attack makes the server unavailable. In the proposed scheme, the timestamp is used to check the freshness of the message. In the booking phase, if the user and central authority exchanged the messages , the server checks the timestamp against the current timestamp ; if not fresh, the server rejects the message. Furthermore, the message also included a secret value . The server will check that for the validity of the message. As a result, the proposed scheme is secure against the DoS attacks.
- Offline guessing attack: With the assistance of the side-channel attacks such as SPA and DPA, the adversary cannot obtain because the user’s information is protected using the one-way hash function. Even if the adversary obtains , he/she cannot decipher the ticket in the offline environment and encrypted using the temporary session key. Therefore, the proposed scheme withstands the offline guessing attack.
6.2. Syverson and Van Oorschot (Svo) Logic
- The Separation rule Modus Ponens (MP) from and
- The necessity of rules Necessitation (Nec) from believing .
- Believes:Ax.1: P believes believes believesAx.2: P believes believes .
- Source Association:Ax.3: Sharedkey received said sees K.Ax.4: received said Y.
- Key agreement:Ax.5: SharedKey .
- Receiving:Ax.6: P received receives .AX.7: P received sees receives X.
- Seeing:Ax.8: P received sees X.Ax.9: P sees sees .Ax.10: P sees sees .
- Comprehending:Ax.11: P believes believes (P sees X).Ax.12: :(P received believes P sees X) ⊃ P believes P received .
- Saying:Ax.13: P said said sees .Ax14: P says says said .
- Jurisdiction:Ax.15: (P controls says ) .
- Freshness:Ax.16: .Ax.17: .
- Nonce-Verification:Ax.18: .
- Symmetric goodness of shared keys:Ax.19: .
- Having:Ax.20:P has sees K.
- Goal.1: Vehicle believes User says
- Goal.2: AS believes vehicle says .
- Goal.3: Vehicle believes AS says .TGS believes vehicle says .
- Goal.4: Vehicle believes TGS says .CS believes vehicle says .
- Goal.5: Vehicle Believes AS says . CS believes TGS says .
- Goal.6: Vehicle believes sharedkey . CS believes sharedkey
- Goal.7: Vehicle believes fresh . CS believes fresh
- Assumptions:
- AS.1: Vehicle Believes fresh
- CS believes fresh
- AS.2: Vehicle believes vehicle received
- AS believes AS received
- AS.3: TGS believes TGS received
- Vehicle believes vehicle received
- CS believes CS received
- AS.4: Vehicle believes vehicle received
- TGS believes TGS received
- CS believes CS received
- AS.5: Vehicle believes
- AS believes
- TGS believes
- CS believes
- AS.6: Vehicle believes SV
- AS believes SV
- TGS believes SV
- CS believes SV
- AS.7: Vehicle believes ((AS says
- TGS believes ((vehicle says
- CS believes ((vehicle says
- AS.8: Vehicle believes
- AS believes
- TGS believes
- CS believes
- AS.9: Vehicle believes (vehicle sees
- AS beliefs (AS sees
- TGS believes
- CS believes
- AS.10: ¬ (vehicle said
- ¬ (AS said
- ¬ (TGS said
- AS.11: Vehicle believes fresh
- CS believes fresh
- From AS.2, AS.5, AS.6, Ax.4, we can get:
- S1: Vehicle believes AS said
- TGS believes the vehicle said
- Vehicle believes TGS said
- CS believes vehicle said
- From S1, AS.1, AS.2, Ax.19, we get:
- S2: Vehicle believes User says
- AS believes vehicle says
- The Goal 1., and Goal 2. are proved.
- From S2, AS.5, Ax.1, and Necessitation, we can get:
- S3: Vehicle believes
- AS believes
- TGS believes
- CS believes
- From S3, AS.8, Ax.5, we can get:
- S4: Vehicle believes sharedkey
- CS believes sharedkey
- Where
- From AS.2, Ax.1, Ax.8, we can obtain:
- S5: Vehicle believes (vehicle sees
- AS believes
- TGS believes
- CS believes
- From S5, AS.9, Ax.5, we can obtain:
- S6: Vehicle believes vehicle sees sharedkey
- CS believes CS sees sharedkey
- Where
- From S4, S6, the definition of Sharedkey we can get:
- S7: Vehicle believes sharedkey
- AS believes sharedkey
- Thus, Goal.6 is proved.
- From AS.7, AS.2, S1, Ax.6, Ax.13, Ax.14, we can obtain:
- S8: Vehicle believes ((AS said
- TGS believes ((vehicle said
- CS believes ((vehicle said
- Thus, Goal 3, and Goal 4., are proved.
- From AS.1, AS.2, S4, Ax.16,Ax.17, we can get:
- S9: Vehicle believes fresh
- CS believes fresh
- Goal 7., proved.
- From AS.3, S4, Ax.3, we can obtain:
- S10: vehicle believes AS said fresh
- TGS believes AS said
- CS believes TGS said
- From S10, AS.11, and Ax.19, we can get:
- S11: vehicle believes AS says
- TGS believes AS says
- CS believes TGS says
- Thus, Goal 5. proved.
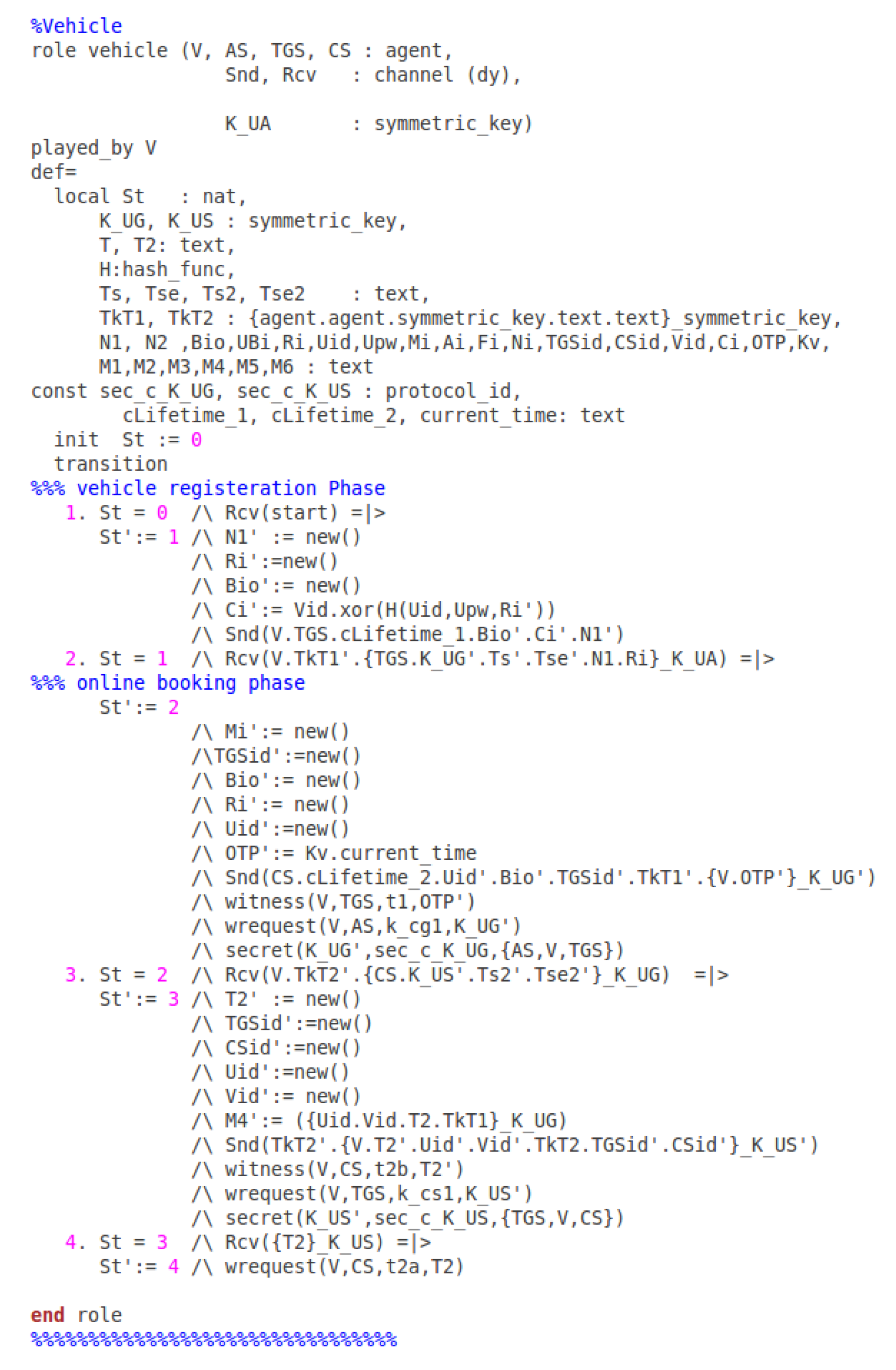
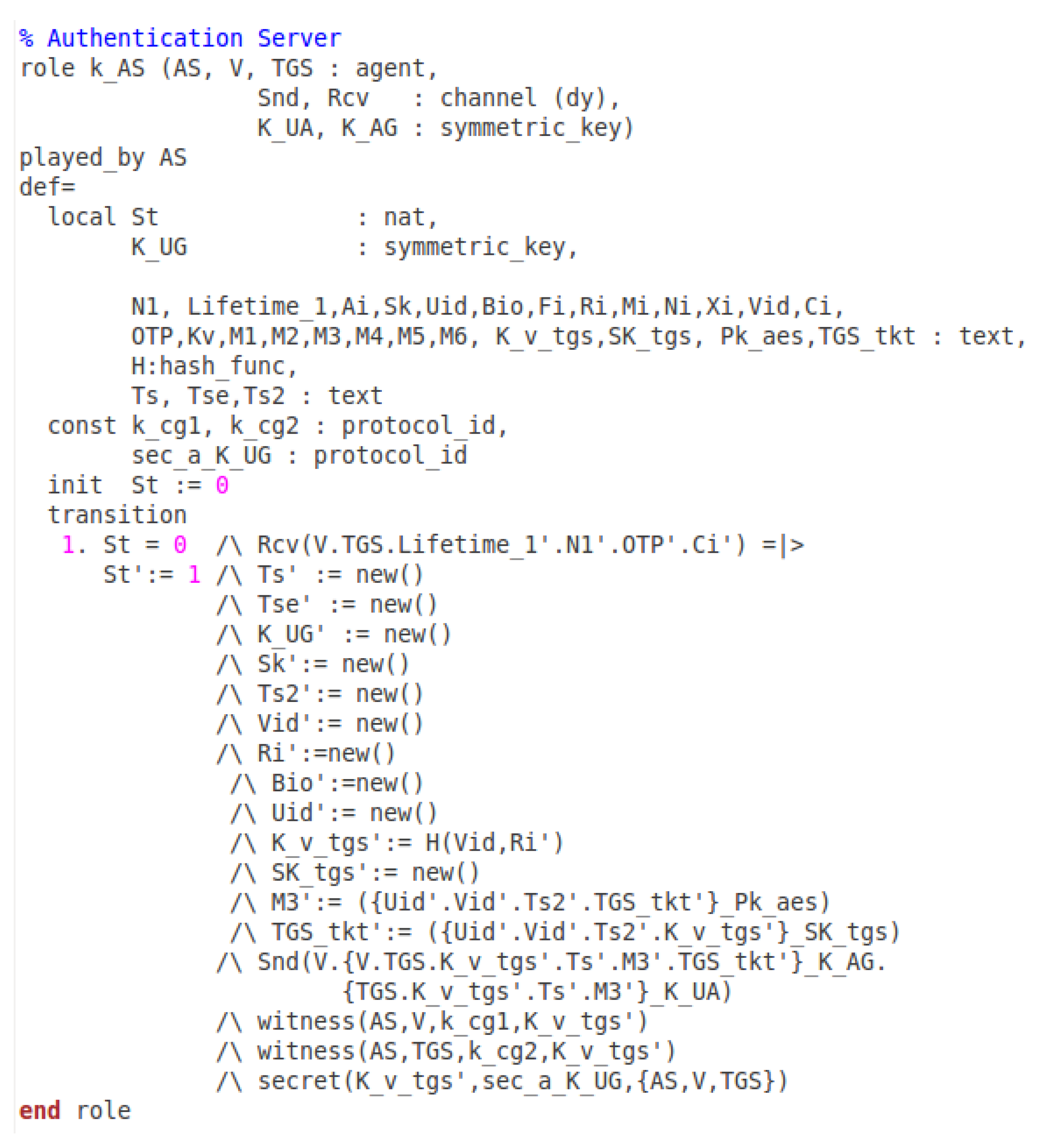
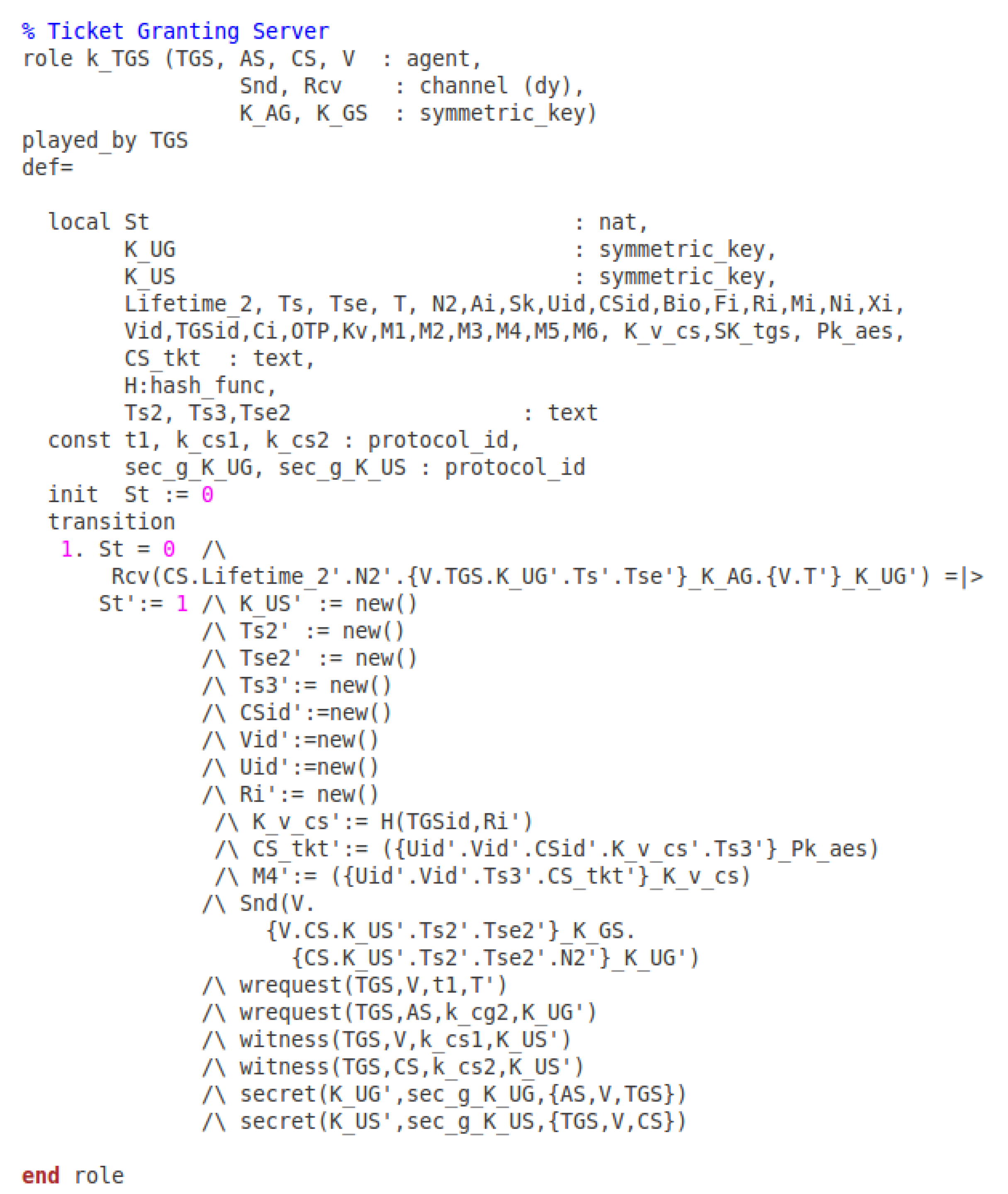
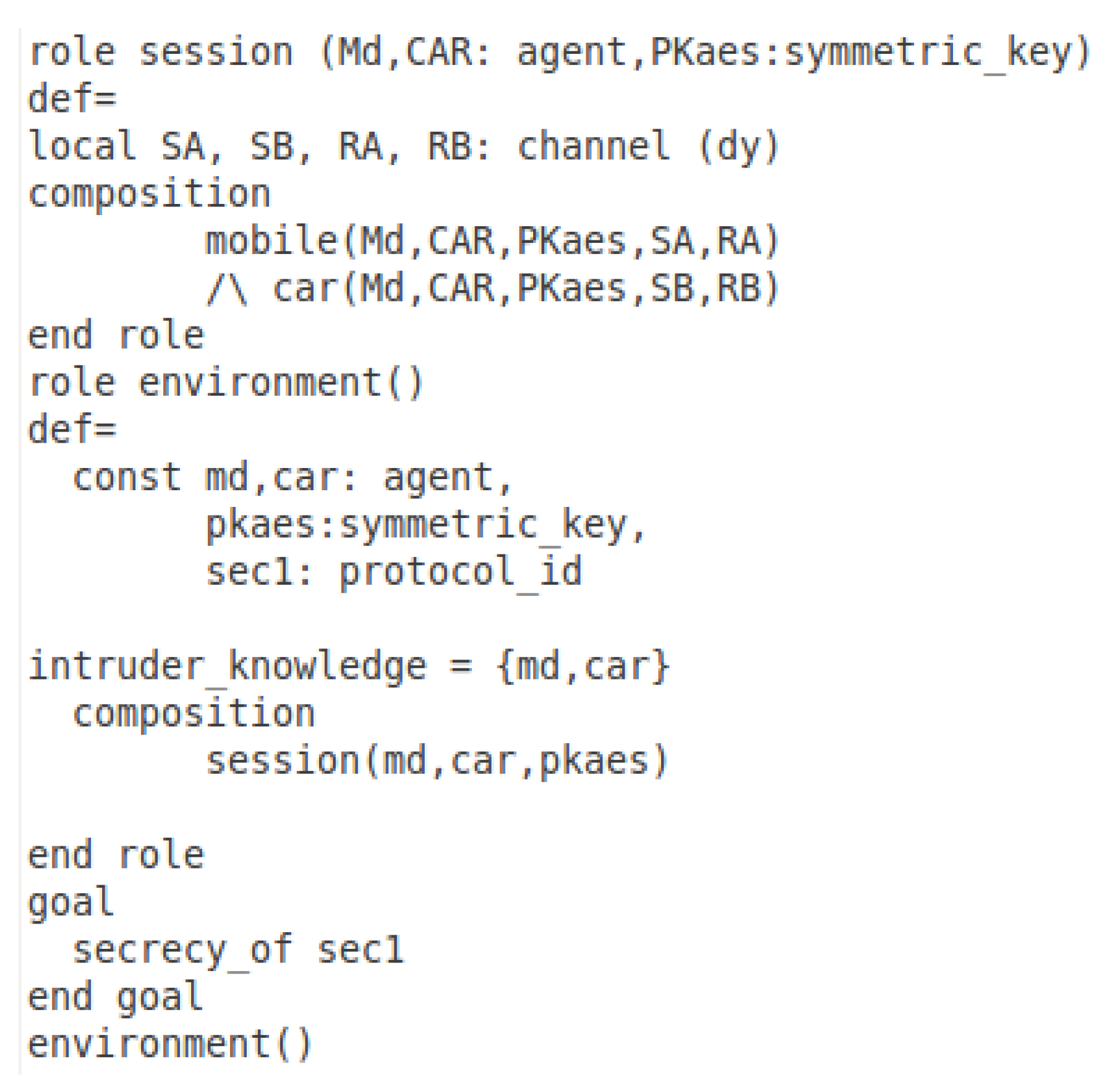
7. The Avispa Simulation
7.1. Specifying the Online Booking in Hlpsl
- secrecy_of sec_a_K_UG: It states that AS, V, and TGS know the value K_UG.
- secrecy_of sec_g_K_UG: It indicates that the AS, V, and TGS share the value K_UG.
- secrecy_of sec_g_K_US: It means that the TGS, V, and CS know the K_US.
- secrecy_of sec_s_K_US: It shows that the agents TGS, V, and CS know K_US.
- secrecy_of sec_c_K_UG: It indicates that the AS, V, and TGS share K_UG.
- secrecy_of sec_c_K_US: It states that the agents TGS, V, and CS share K_US.
- weak_authentication_on k_cg1: The K_UG shared between the vehicle and AS.
- weak_authentication_on k_cg2: The AS and TGS shared the key K_v_tgs.
- weak_authentication_on k_cs1: The vehicle and TGS have the value K_US.
- weak_authentication_on k_cs2: The TGS and the CS knows the value K_US.
- weak_authentication_on t2a: The timestamp T2 is only valid between the CS and vehicle.
- weak_authentication_on t2b: The timestamp T2 shared between the CS and vehicle.
- weak_authentication_on t1: The timestamp T1 is shared amongst the vehicle and TGS.
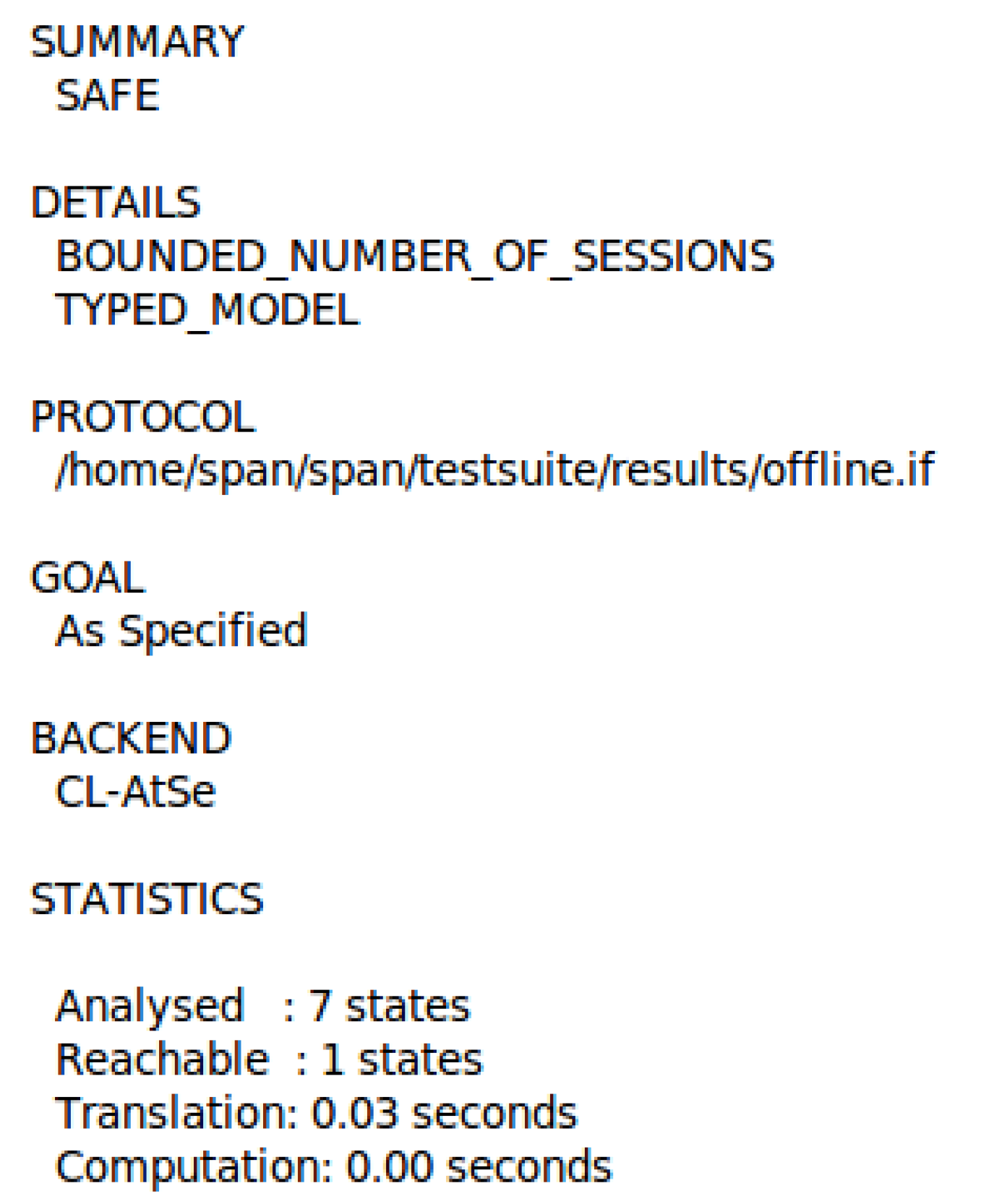
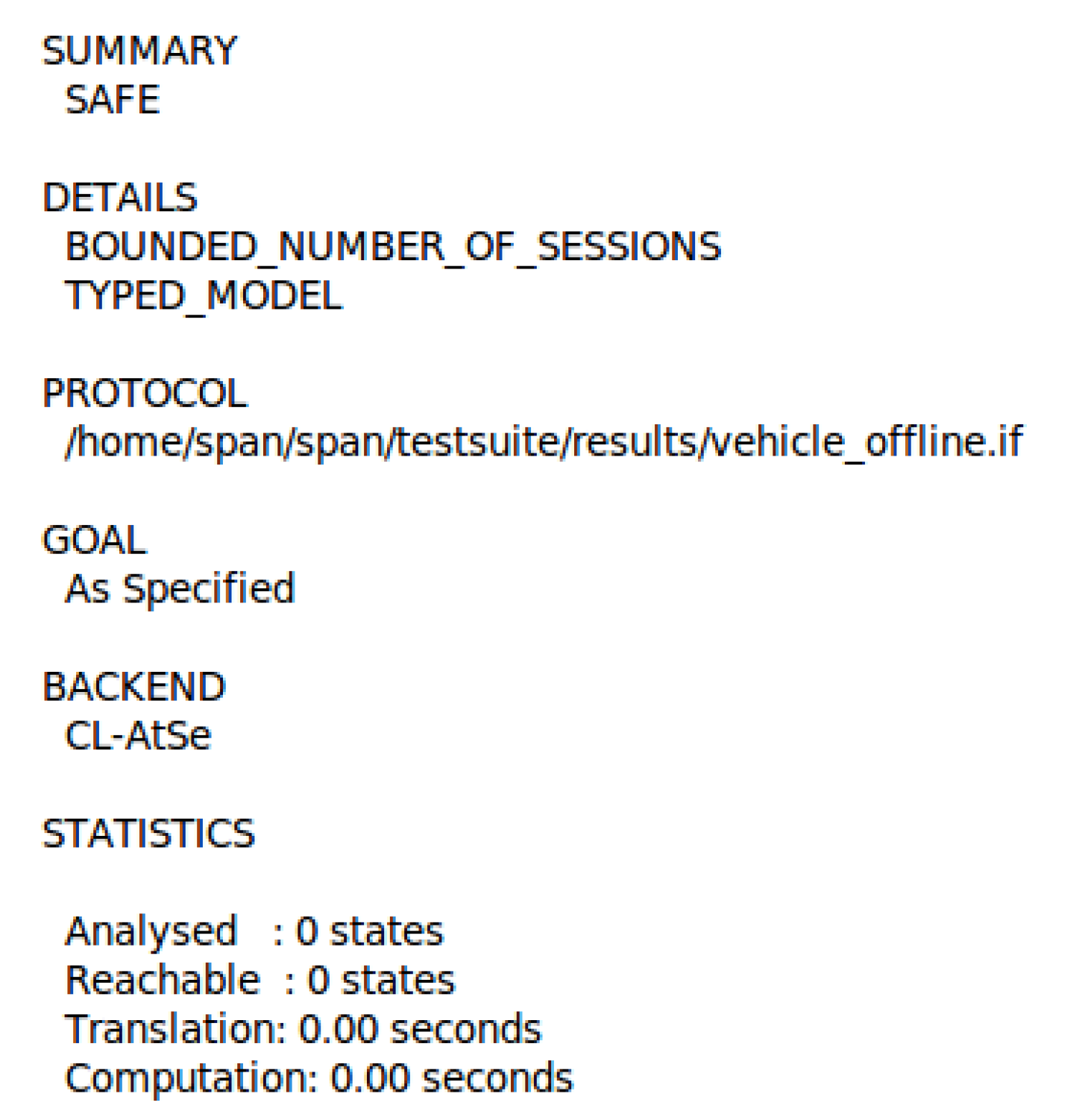
7.2. Booking Phase Simulation Results
- SUMMARY: This section specifies whether the protocol is "secure," "unsafe," or "inconclusive."
- DETAILS: This section describes the various conditions under which the protocol is considered secure, and the conditions used to detect an attack or the reasons why the result was inconclusive.
- PROTOCOL, GOAL, and BACK-END: This subdivision specifies the protocol name, the research goal, and the back-end users.
- COMMENTS and STATISTICS: This subdivision contains some remarks and figures, and traces of an attack.
7.3. Specifying the Offline Phase in HLPSL
7.4. Offline Phase Simulation Results
8. Performance Evaluation
8.1. Computational Cost
8.2. Communication Cost
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Abu Talib, M.; Abbas, S.; Nasir, Q.; Mowakeh, M.F. Systematic literature review on Internet-of-Vehicles communication security. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718815054. [Google Scholar] [CrossRef] [Green Version]
- Fu, X.; Yang, Y. Modeling and analyzing cascading failures for Internet of Things. Inf. Sci. 2021, 545, 753–770. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, W.; Chen, J.; Wang, W. Evolutionary V2X technologies toward the Internet of vehicles: Challenges and opportunities. Proc. IEEE 2020, 108, 308–323. [Google Scholar] [CrossRef]
- Mahmood, A.; Zhang, W.E.; Sheng, Q.Z. Software-defined heterogeneous vehicular networking: The architectural design and open challenges. Future Internet 2019, 11, 70. [Google Scholar] [CrossRef] [Green Version]
- Liu, L.; Lu, S.; Zhong, R.; Wu, B.; Yao, Y.; Zhang, Q.; Shi, W. Computing Systems for Autonomous Driving: State of the Art and Challenges. IEEE Internet Things J. 2020, 8, 6469–6486. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Castedo, L. Towards the Internet of smart trains: A review on industrial IoT-connected railways. Sensors 2017, 17, 1457. [Google Scholar] [CrossRef] [Green Version]
- Zantalis, F.; Koulouras, G.; Karabetsos, S.; Kandris, D. A review of machine learning and IoT in smart transportation. Future Internet 2019, 11, 94. [Google Scholar] [CrossRef] [Green Version]
- Khalid, H.; Hashim, S.J.; Syed Ahmad, S.M.; Hashim, F.; Chaudhary, M.A. Cross-SN: A Lightweight Authentication Scheme for a Multi-Server Platform Using IoT-Based Wireless Medical Sensor Network. Electronics 2021, 10, 790. [Google Scholar] [CrossRef]
- Bhuiyan, M.Z.A.; Kuo, S.Y.; Cao, J.; Wang, G. Guest Editorial: Trustworthiness in Industrial Internet of Things Systems and Applications. IEEE Trans. Ind. Inform. 2020, 16, 6079–6082. [Google Scholar] [CrossRef]
- Chen, C.M.; Xiang, B.; Liu, Y.; Wang, K.H. A secure authentication protocol for internet of vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G.; Severino, A. A review on IEEE 802.11 p for intelligent transportation systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Ahmad, F.; Kurugollu, F.; Adnane, A.; Hussain, R.; Hussain, F. MARINE: Man-in-the-middle attack resistant trust model in connected vehicles. IEEE Internet Things J. 2020, 7, 3310–3322. [Google Scholar] [CrossRef] [Green Version]
- Mahmood, A.; Butler, B.; Zhang, W.E.; Sheng, Q.Z.; Siddiqui, S.A. A hybrid trust management heuristic for VANETs. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 748–752. [Google Scholar]
- Anderson, J.M.; Nidhi, K.; Stanley, K.D.; Sorensen, P.; Samaras, C.; Oluwatola, O.A. Autonomous Vehicle Technology: A Guide for Policymakers; Rand Corporation, 776 Main Street: Santa Monica, CA, USA, 2014. [Google Scholar]
- Dibaei, M.; Zheng, X.; Jiang, K.; Maric, S.; Abbas, R.; Liu, S.; Zhang, Y.; Deng, Y.; Wen, S.; Zhang, J.; et al. An overview of attacks and defences on intelligent connected vehicles. arXiv 2019, arXiv:1907.07455. [Google Scholar]
- Merco, R.; Biron, Z.A.; Pisu, P. Replay attack detection in a platoon of connected vehicles with cooperative adaptive cruise control. In Proceedings of the 2018 Annual American Control Conference (ACC), Milwaukee, WI, USA, 27–29 June 2018; pp. 5582–5587. [Google Scholar]
- Barbero, A.I.; Rosnes, E.; Yang, G.; Ytrehus, O. Near-field passive RFID communication: Channel model and code design. IEEE Trans. Commun. 2014, 62, 1716–1727. [Google Scholar] [CrossRef] [Green Version]
- Kumar, V.; Ahmad, M.; Mishra, D.; Kumari, S.; Khan, M.K. RSEAP: RFID based secure and efficient authentication protocol for vehicular cloud computing. Veh. Commun. 2020, 22, 100213. [Google Scholar] [CrossRef]
- Gitlin, J.M. Driver Stranded after Connected Rental Car Cannot Call Home. ars TECHNICA. Available online: https://www.techdirt.com/articles (accessed on 18 February 2020).
- Sutrala, A.K.; Bagga, P.; Das, A.K.; Kumar, N.; Rodrigues, J.J.; Lorenz, P. On the design of conditional privacy preserving batch verification-based authentication scheme for Internet of vehicles deployment. IEEE Trans. Veh. Technol. 2020, 69, 5535–5548. [Google Scholar] [CrossRef]
- Safkhani, M.; Camara, C.; Peris-Lopez, P.; Bagheri, N. RSEAP2: An enhanced version of RSEAP, an RFID based authentication protocol for vehicular cloud computing. Veh. Commun. 2021, 28, 100311. [Google Scholar] [CrossRef]
- Wei, F.; Zeadally, S.; Vijayakumar, P.; Kumar, N.; He, D. An intelligent terminal based privacy-preserving multi-modal implicit authentication protocol for internet of connected vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 3939–3951. [Google Scholar] [CrossRef]
- Shah, G.; Saifuddin, M.; Fallah, Y.P.; Gupta, S.D. RVE-CV2X: A Scalable Emulation Framework for Real-Time Evaluation of CV2X-based Connected Vehicle Applications. In Proceedings of the 2020 IEEE Vehicular Networking Conference (VNC), New York, NY, USA, 16–18 December 2020; pp. 1–8. [Google Scholar]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.K.R. Unified biometric privacy preserving three-factor authentication and key agreement for cloud-assisted autonomous vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. An efficient identity-based conditional privacy-preserving authentication scheme for secure communication in a vehicular ad hoc network. Symmetry 2020, 12, 1687. [Google Scholar] [CrossRef]
- Alnasser, A.; Sun, H.; Jiang, J. Recommendation-based trust model for vehicle-to-everything (V2X). IEEE Internet Things J. 2019, 7, 440–450. [Google Scholar] [CrossRef] [Green Version]
- Addobea, A.A.; Hou, J.; Li, Q. MHCOOS: An Offline-Online Certificateless Signature Scheme for M-Health Devices. Secur. Commun. Netw. 2020, 2020. [Google Scholar] [CrossRef] [Green Version]
- Yu, P.; Tate, S.R. Online/offline signature schemes for devices with limited computing capabilities. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 8–11 April 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 301–317. [Google Scholar]
- Wu, T.S.; Chen, Y.S.; Lin, K.Y. Id-based online/offline signature from pairings. In Proceedings of the 2010 International Computer Symposium (ICS2010), Tainan, 16–18 December 2010; pp. 198–203. [Google Scholar]
- Shamir, A.; Tauman, Y. Improved online/offline signature schemes. Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 355–367. [Google Scholar]
- Khalid, H.; Hashim, S.J.; Ahmad, S.; Hashim, F.; Chaudary, M.A. Cybersecurity in Industry 4.0 context: Background, issues, and future directions. Chapter Nine Pillars Technol. Ind. 2020, 263–307. [Google Scholar] [CrossRef]
- Liu, D.; Zhang, S.; Zhong, H.; Shi, R.; Wang, Y. An efficient identity-based online/offline signature scheme without key escrow. Int. J. Netw. Secur. 2017, 19, 127–137. [Google Scholar]
- Dmitrienko, A.; Plappert, C. Secure free-floating car sharing for offline cars. In Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; pp. 349–360. [Google Scholar]
- Dmitrienko, A.; Sadeghi, A.R.; Tamrakar, S.; Wachsmann, C. SmartTokens: Delegable access control with NFC-enabled smartphones. In Proceedings of the International Conference on Trust and Trustworthy Computing, Vienna, Austria, 13–15 June 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 219–238. [Google Scholar]
- Symeonidis, I.; Aly, A.; Mustafa, M.A.; Mennink, B.; Dhooghe, S.; Preneel, B. Sepcar: A secure and privacy-enhancing protocol for car access provision. In European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2017; pp. 475–493. [Google Scholar]
- Haas, S.; Wallner, A.; Toegl, R.; Ulz, T.; Steger, C. A secured offline authentication approach for industrial mobile robots. In Proceedings of the 2017 13th IEEE Conference on Automation Science and Engineering (CASE), Xi’an, China, 20–23 August 2017; pp. 308–313. [Google Scholar]
- Li, F.; Xiong, P. Practical secure communication for integrating wireless sensor networks into the internet of things. IEEE Sens. J. 2013, 13, 3677–3684. [Google Scholar] [CrossRef]
- Fu, X.; Fortino, G.; Pace, P.; Aloi, G.; Li, W. Environment-fusion multipath routing protocol for wireless sensor networks. Inf. Fusion 2020, 53, 4–19. [Google Scholar] [CrossRef]
- Saeed, M.E.S.; Liu, Q.; Tian, G.; Gao, B.; Li, F. HOOSC: Heterogeneous online/offline signcryption for the Internet of Things. Wirel. Netw. 2018, 24, 3141–3160. [Google Scholar] [CrossRef]
- Vinoth, R.; Deborah, L.J.; Vijayakumar, P.; Kumar, N. Secure Multi-factor Authenticated Key Agreement Scheme for Industrial IoT. IEEE Internet Things J. 2020, 8, 3801–3811. [Google Scholar] [CrossRef]
- Zmezm, H.F.; Hashim, S.; Sali, A.; Alezabi, K.A. Pre-authentication design for seamless and secure handover in mobile WiMAX. Int. Rev. Comput. Softw. (IRECOS) 2015, 10, 764–772. [Google Scholar] [CrossRef]
- Han, D.; Lu, Y.; Du, X.; Gan, J. Offline Authentication Scheme Based on Blockchain Technology for Smart Lock. In Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering, Beijing, China, 28–30 November 2018; pp. 384–390. [Google Scholar]
- Fu, X.; Yang, Y. Analysis on invulnerability of wireless sensor networks based on cellular automata. Reliab. Eng. Syst. Saf. 2021, 212, 107616. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Hou, J.L.; Yeh, K.H. Novel authentication schemes for IoT based healthcare systems. Int. J. Distrib. Sens. Netw. 2015, 11, 183659. [Google Scholar] [CrossRef]
- Scripcariu, L.; Mătăsaru, P.D. On the substitution method of the AES algorithm. In Proceedings of the International Symposium on Signals, Circuits and Systems ISSCS2013, Iasi, Romania, 11–12 July 2013; pp. 1–4. [Google Scholar]
- Scripcariu, L.; Diaconu, F.; Mătăsaru, P.D.; Gafencu, L. AES vulnerabilities study. In Proceedings of the 2018 10th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Iasi, Romania, 28–30 June 2018; pp. 1–4. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication protocols for internet of things: A comprehensive survey. Secur. Commun. Netw. 2017, 2017. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef] [Green Version]
- Hancock, B. Security views. Comput. Secur. 2001, 20, 348363. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Santa Barbara, CA, USA, 18–22 August 1985; Springer: Berlin/Heidelberg, Germany, 1985; pp. 417–426. [Google Scholar]
- Khalid, H.; Hashim, S.J.; Ahmad, S.M.S.; Hashim, F.; Chaudhary, M.A. SELAMAT: A New Secure and Lightweight Multi-Factor Authentication Scheme for Cross-Platform Industrial IoT Systems. Sensors 2021, 21, 1428. [Google Scholar] [CrossRef]
- M’Raihi, D.; Machani, S.; Pei, M.; Rydell, J. Totp: Time-based one-time password algorithm. In Internet Request for Comments; Internet Engineering Task Force (IETF): Mountain View, CA, USA, 2011; p. 685E. [Google Scholar]
- Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Mantovani, J.; Mödersheim, S.; Vigneron, L. A high level protocol specification language for industrial security-sensitive protocols. In Workshop on Specification and Automated Processing of Security Requirements-SAPS’2004; Austrian Computer Society: Linz, Austria, 2004; 13p. [Google Scholar]












| Ref. | Issue | Method | Advantages | Disadvantages |
|---|---|---|---|---|
| [10] | Offline identity guessing attack, location spoofing attack, and replay attack, | CDH | prevents offline guessing attacks | Intruder has the capability to disrupt integrity, authenticity, confidentiality. |
| [28] | Devices with limited computing capabilities. | RSA algorithm | Improve the efficiency of both online and offline phases. | Not feasible for IoT devices with limited resources. |
| [29] | Attacks based on existential forgery on adaptively chosen messages | Bilinear pairing | Secure from forgery attacks. | High computation due to Bilinear pairing. |
| [30] | The trade-off between the size of the keys and the complexity. | Trapdoor hash function | Secure against adaptive chosen message attacks. | For different messages, several chameleon hashes values are used. |
| [32] | Overcomes the key escrow problem, | Bilinear Pairing and MTP function. | Resolve the key escrow problem. | High computation due to Bilinear pairing. |
| [33] | Online communication shortcomings. | Identity-based encryption | Allows the car to expand its services to areas without reliable network coverage. | Suffers from various passive attacks. |
| [34] | Leakage and unintended manipulation of security-critical data | Identity-based encryption | Provides a two-line defence against software attacks | Requires high computation and communication costs. |
| [35] | Allows users to share their cars conveniently without sacrificing their security and privacy. | AES | Ensure that messages sent between vehicles and VPKI servers are unlinkable. | The security of the protocol was not proven. |
| [36] | Robots suffer from higher safety risks than | One- Time Passwords (OTP). | Secured method for offline authentication on mobile robots | Vulnerable to replay attack, man-in-the-middle attack. |
| [45] | Limited computational resources of low-cost IoT based devices make the design of security components for such devices difficult. | Single sign-on (SSO) | Use the unitary token to access different services. | Vulnerable to impersonation and modification attacks. |
| [37] | Insecure communication between a sensor node and an Internet host. | Identity-based cryptography | Works against adaptive chosen-ciphertext attacks. | High complexity due to the Bilinear pairing. |
| [39] | Design a heterogenous scheme. | Certificateless signcryption | Overcome the key escrow | Not suitable for use in industrial IoT. |
| [42] | Secure end-to end security. | Blockchain | Secure transmission | High complexity, energy consumption, single point failure. |
| Notation | Description |
|---|---|
| p,q | Large prime numbers |
| TA | Trusted Authority |
| Vehicle | |
| AS | Authentication Server |
| TGS | Ticket Granting Service |
| CS | Cross-Server |
| Encryption/Decryption Pairs | |
| System master key | |
| SPK | System public key |
| AES public Key | |
| User’s Identity | |
| Mobile device identity | |
| User Password | |
| User Biometric | |
| Vehicle Identity | |
| User’s private key | |
| User Public key | |
| CN | Check number |
| OTP | One-time Password |
| Cross-server identity | |
| Random number | |
| One-Way hash function |
| SM-AKA [40] | HOOSC [39] | CP-VBP [20] | RSEAP [18] | Proposed Scheme | |
|---|---|---|---|---|---|
| Mutual Authentication | √ | √ | √ | √ | √ |
| Froward secrecy | √ | √ | ✕ | √ | √ |
| Anonymity | √ | ✕ | ✕ | √ | √ |
| Confidentiality | ✕ | ✕ | √ | √ | √ |
| Integrity | ✕ | ✕ | ✕ | √ | √ |
| Key freshness | ✕ | √ | √ | ✕ | √ |
| Offline Authentication | √ | √ | ✕ | ✕ | √ |
| Cross-domain authentication | ✕ | ✕ | ✕ | ✕ | √ |
| Replay attack | √ | √ | √ | √ | √ |
| Impersonation attack | √ | ✕ | √ | √ | √ |
| Modification attack | ✕ | √ | √ | √ | √ |
| Man-in the middle attack | √ | √ | √ | √ | √ |
| Server spoofing attack | ✕ | ✕ | ✕ | ✕ | √ |
| Privileged insider attack | √ | √ | ✕ | √ | √ |
| Denial of service (DoS) attack | √ | √ | ✕ | √ | √ |
| Offline guessing attack | ✕ | √ | √ | √ | √ |
| Notation | Description |
|---|---|
| is a theorem | |
| K is the public signature verification key for P | |
| K is the public key-agreement key for P | |
| K can verify if X is Y’s signature | |
| X is fresh | |
| The ciphertext encrypted by K | |
| The message signed by K |
| Scheme | Computation Cost (ms) | Communication Cost (bits) | ||
|---|---|---|---|---|
| Online Phase | Offline Phase | Total | ||
| HOOSC [39] | ms | ms | 42.36 ms | 2368 bits |
| SM-AKA [40] | ms | 22.052 ms | 2880 bits | |
| CP-VBA [20] | ms | ms | 22.700 ms | 1952 bits |
| RSEAP [18] | ms | 21.625 ms | 1740bits | |
| Proposed Scheme | ms | ms | 15.482 ms | 1016 bits |
| Description | Time (ms) |
|---|---|
| Identity-based signature | 23.866 |
| Identity-based signature verification | 5.872 |
| Asymmetric signature | 3.85 |
| Asymmetric signature verification | 0.1925 |
| Public-key-based encryption | 3.85 |
| Public key-based decryption | 3.85 |
| symmetrical encryption | 0.0046 |
| Symmetric decryption | 0.0046 |
| Scalar multiplication in | 0.442 |
| Scalar multiplication | 20.23 |
| ECS scalar multiplication | 1.970 |
| Point multiplication operation | 0.832 |
| Exponentiation Operations | 6.614 |
| Bilinear pairing | 12.523 |
| Map-to-point hash function | 4.406 |
| Fuzzy extractor | 0.0023 |
| 0.0023 | |
| 12.418 | |
| 0.974 | |
| 0.0046 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khalid, H.; Hashim, S.J.; Ahmad, S.M.S.; Hashim, F.; Chaudhary, M.A. A New Hybrid Online and Offline Multi-Factor Cross-Domain Authentication Method for IoT Applications in the Automotive Industry. Energies 2021, 14, 7437. https://doi.org/10.3390/en14217437
Khalid H, Hashim SJ, Ahmad SMS, Hashim F, Chaudhary MA. A New Hybrid Online and Offline Multi-Factor Cross-Domain Authentication Method for IoT Applications in the Automotive Industry. Energies. 2021; 14(21):7437. https://doi.org/10.3390/en14217437
Chicago/Turabian StyleKhalid, Haqi, Shaiful Jahari Hashim, Sharifah Mumtazah Syed Ahmad, Fazirulhisyam Hashim, and Muhammad Akmal Chaudhary. 2021. "A New Hybrid Online and Offline Multi-Factor Cross-Domain Authentication Method for IoT Applications in the Automotive Industry" Energies 14, no. 21: 7437. https://doi.org/10.3390/en14217437
APA StyleKhalid, H., Hashim, S. J., Ahmad, S. M. S., Hashim, F., & Chaudhary, M. A. (2021). A New Hybrid Online and Offline Multi-Factor Cross-Domain Authentication Method for IoT Applications in the Automotive Industry. Energies, 14(21), 7437. https://doi.org/10.3390/en14217437







