Energy Signal-Aided Secure Beamforming and Self-Energy Recycling in Full-Duplex Wireless-Powered Relay Networks
Abstract
:1. Introduction
- (1)
- A novel two-phase ES-aided secure transmission scheme is established by using the FD pattern to realize contemporaneous information as well as energy delivery. We study secure joint beamforming and ES and TS coefficient design for the SRM problem in FD-WPR systems;
- (2)
- An antenna multiplexing method using the configured antenna to receive information to enhance the intensity of the information signal is proposed;
- (3)
- To deal with the aforementioned difficult problem, one-dimensional (1D) search and semi-definite relaxation (SDR) techniques are used to resolve the question. Then, an alternative method to transform the original problem into two sub-problems is proposed. By solving these subproblems iteratively, the closed solution of the beamforming, the covariance of the ES, and the optimal time allocation are obtained. Moreover, the tightness of SDR is established with the aid of the Karysh–Kuhn–Tucker (KKT) conditions.
2. Related Work
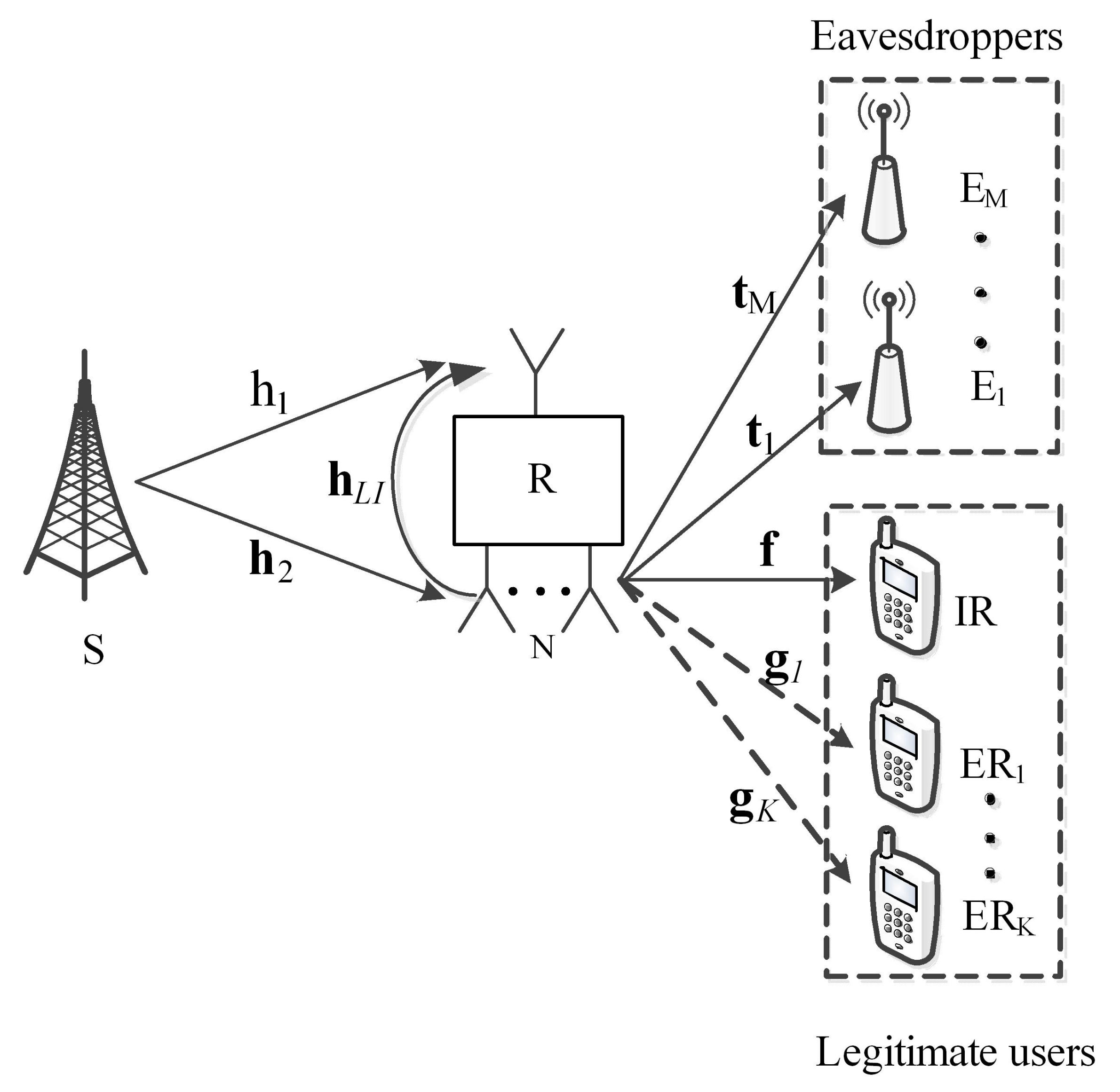
3. System Pattern and Question Formulation
4. Secrecy Rate Optimization
4.1. Beamforming Vector and Energy Signal Design
4.2. Description of the Solving Algorithm
| Algorithm 1. Algorithm proposed for solving problem (19). |
 |
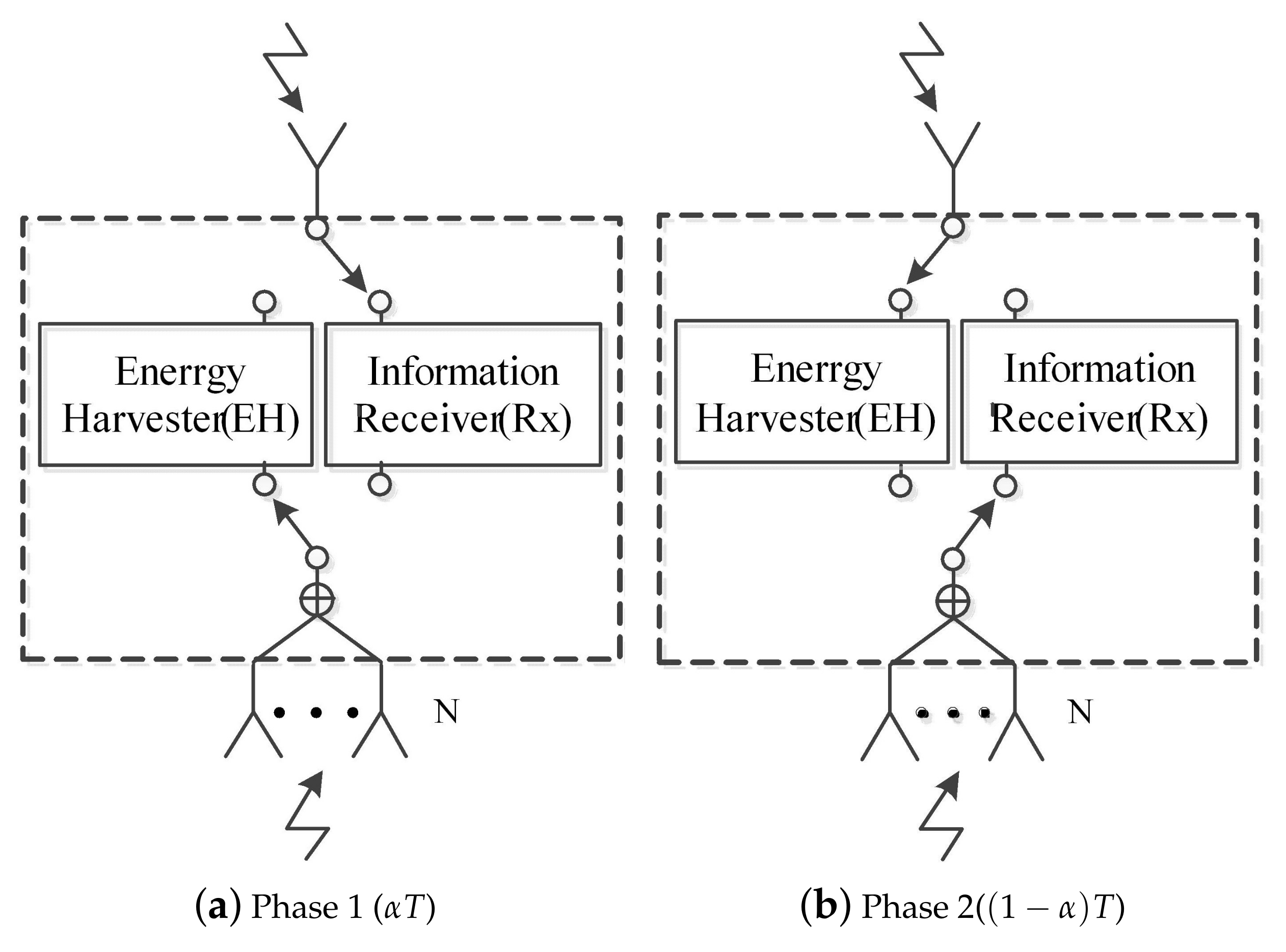
4.3. Time Allocation Ratio Design
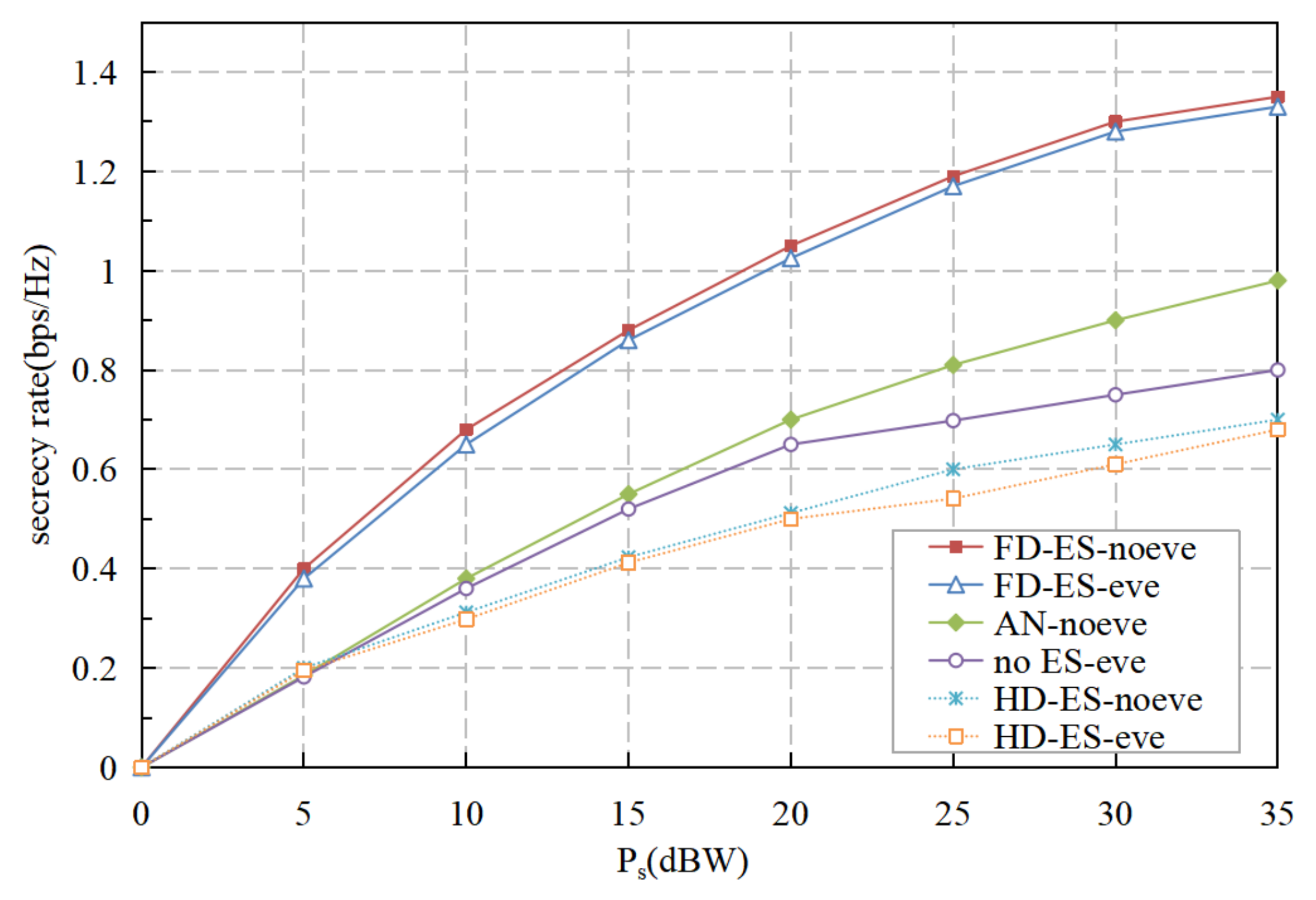
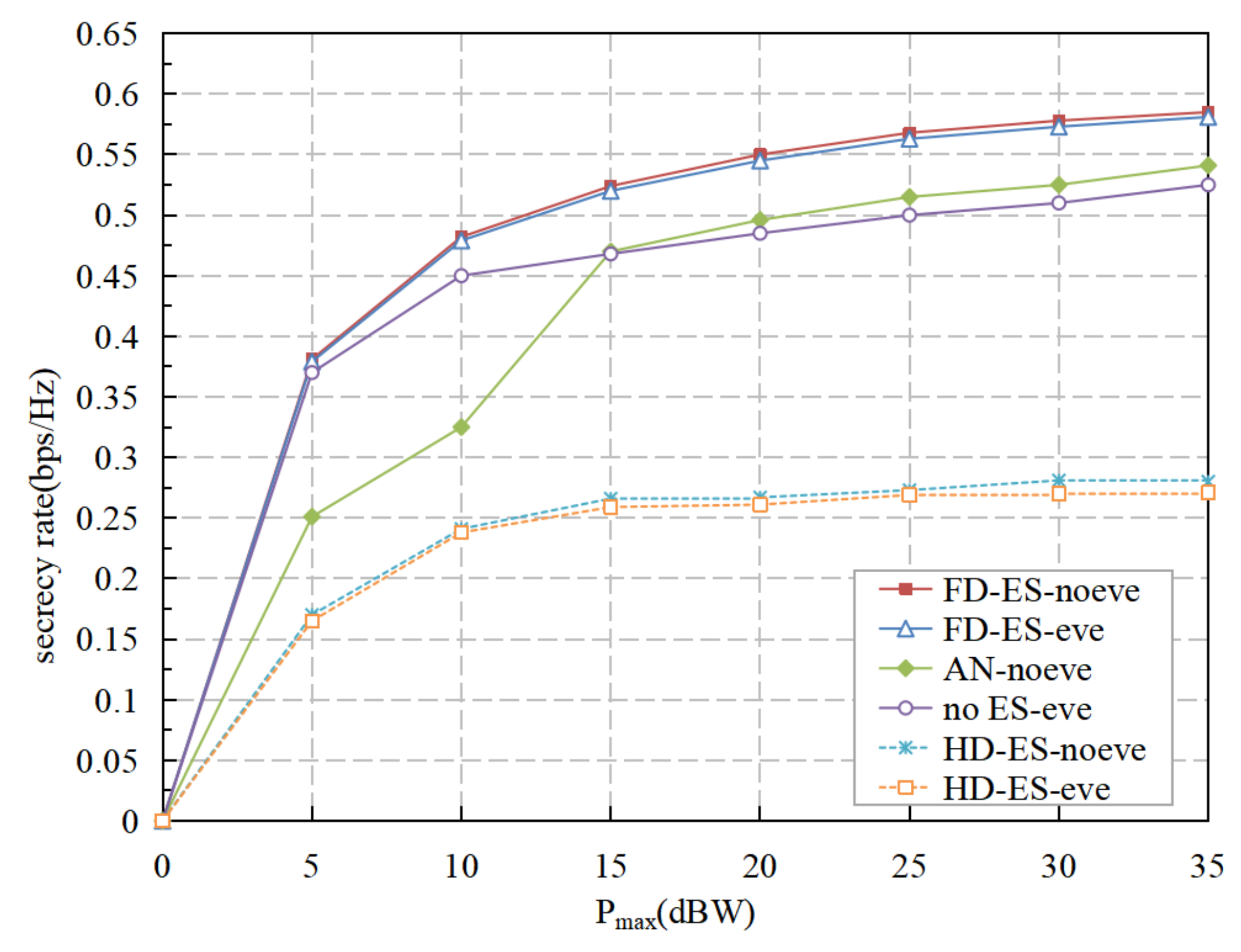
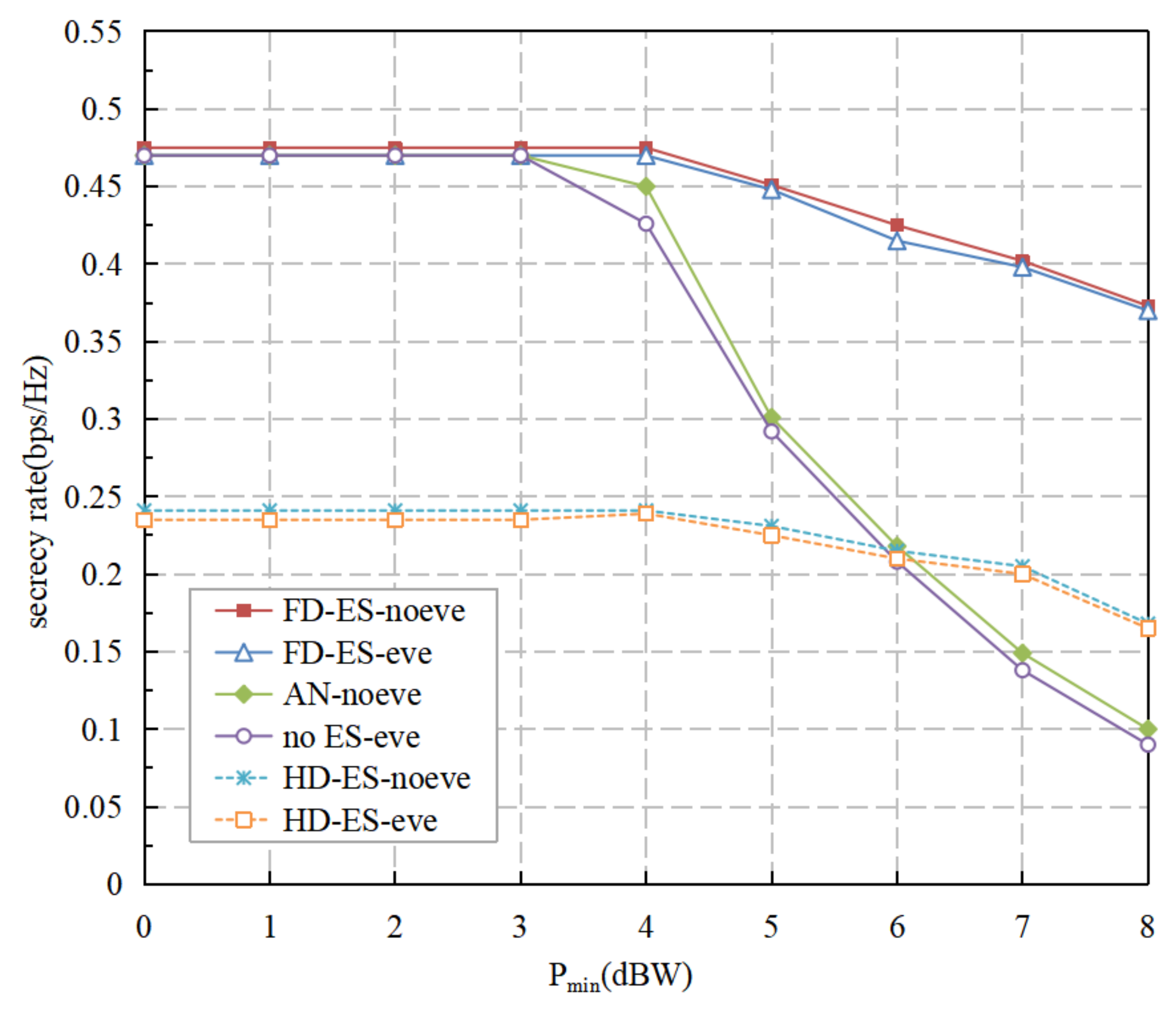
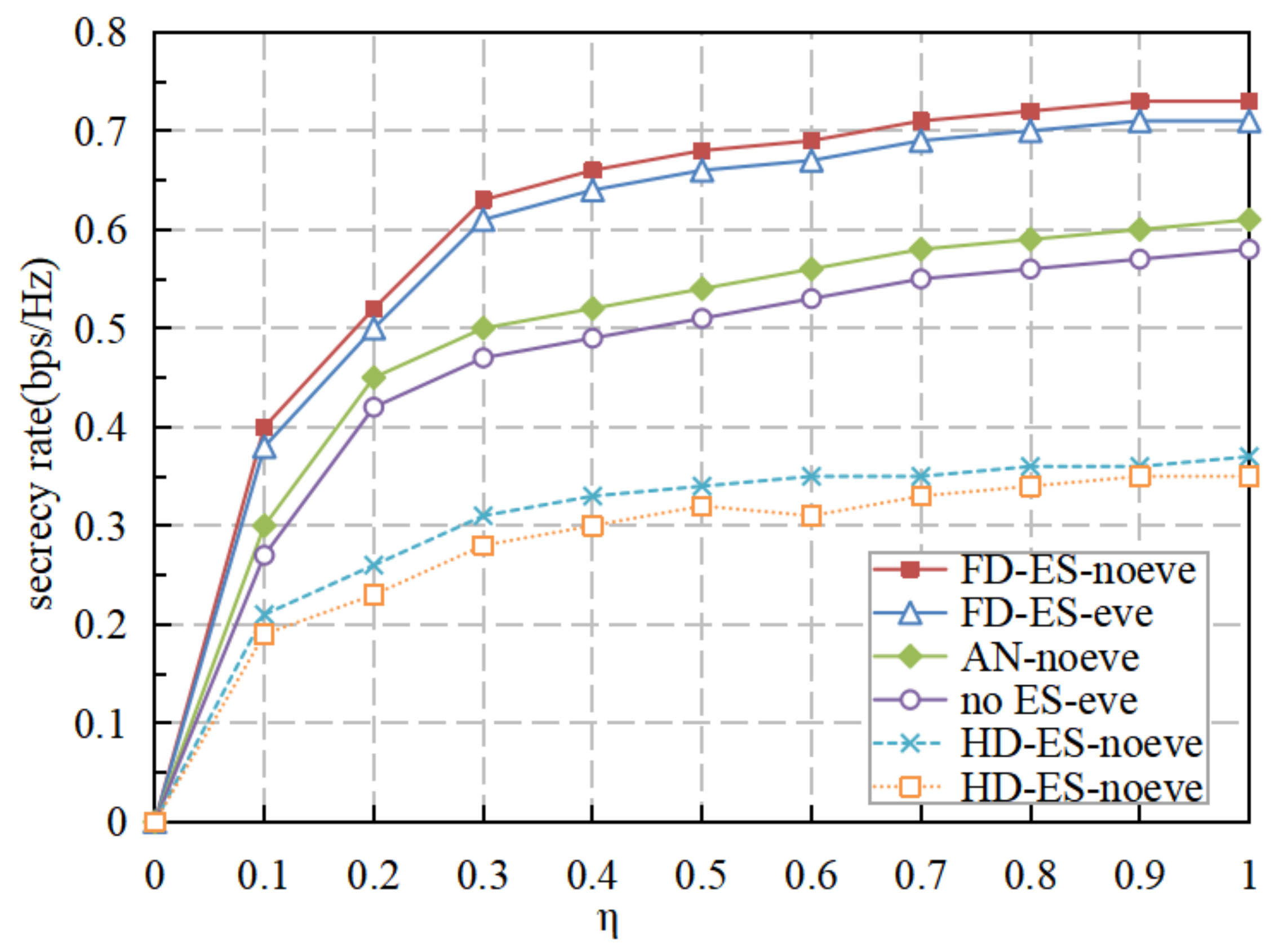
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix A.1. Proof of Proposition 2
Appendix A.2. Notation Description
| No. | Notation | Description |
| 1 | conjugate transpose of matrices A | |
| 2 | trace of matrices A | |
| 3 | rank of matrices A | |
| 4 | stacking the columns of a matrices {A} into a phasor a | |
| 5 | , and | absolute value, Euclidean norm and Frobenius norm respectively |
| 6 | ⊗ | Hadamard product |
| 7 | {A} is a positive semi-definite matrices | |
| 8 | identity matrix | |
| 9 | the oblique matrices with  vector on main oblique vector on main oblique | |
| 10 | the minimum eigenvalue of the matrices involved | |
| 11 | a random variable abiding a complicated circular Gaussian distribution with average as well as covariance |
References
- Zhang, R.; Ho, C.K. MIMO Broadcasting for Simultaneous Wireless Information and Power Transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef] [Green Version]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Robust Beamforming for Secure Communication in Systems With Wireless Information and Power Transfer. IEEE Trans. Wirel. Commun. 2014, 13, 4599–4615. [Google Scholar] [CrossRef] [Green Version]
- Zhu, Z.; Zhang, Y.; Wang, Z.; Zhang, Y.; Gao, X.; Chu, Z. Robust beamforming for multiuser MISO interference channel with energy harvesting constraint. In Proceedings of the International Conference on Communications & Networking in China, Shanghai, China, 15–17 August 2015. [Google Scholar]
- Shi, Q.; Xu, W.; Wu, J.; Song, E.; Wang, Y. Secure Beamforming for MIMO Broadcasting With Wireless Information and Power Transfer. IEEE Trans. Wirel. Commun. 2015, 14, 2841–2853. [Google Scholar] [CrossRef] [Green Version]
- Feng, Y.; Yang, Z.; Zhu, W.; Li, Q.; Lv, B. Robust Cooperative Secure Beamforming for Simultaneous Wireless Information and Power Transfer in Amplify-and-Forward Relay Networks. IEEE Trans. Veh. Technol. 2016, 66, 2354–2366. [Google Scholar] [CrossRef]
- Wen, Z.; Liu, X.; Beaulieu, N.C.; Wang, R.; Wang, S. Joint Source and Relay Beamforming Design for Full-Duplex MIMO AF Relay SWIPT Systems. IEEE Commun. Lett. 2016, 20, 320–323. [Google Scholar] [CrossRef]
- Wan, Y.; Li, Q.; Zhang, Q.; Qin, J. Optimal and Suboptimal Full-Duplex Secure Beamforming Designs for MISO Two-Way Communications. IEEE Wirel. Commun. Lett. 2015, 4, 493–496. [Google Scholar] [CrossRef]
- Li, Q.; Zhang, Q.; Qin, J. Secure Relay Beamforming for SWIPT in Amplify-and-Forward Two-Way Relay Networks. IEEE Trans. Veh. Technol. 2016, 65, 9006–9019. [Google Scholar] [CrossRef]
- Sabharwal, A.; Schniter, P.; Guo, D.; Bliss, D.W.; Rangarajan, S.; Wichman, R. In-Band Full-Duplex Wireless: Challenges and Opportunities. IEEE J. Sel. Areas Commun. 2014, 32, 1637–1652. [Google Scholar] [CrossRef] [Green Version]
- Zheng, G. Joint Beamforming Optimization and Power Control for Full-Duplex MIMO Two-way Relay Channel. IEEE Trans. Signal Process. 2014, 63, 555–566. [Google Scholar] [CrossRef] [Green Version]
- Zeng, Y.; Zhang, R. Full-Duplex Wireless-Powered Relay With Self-Energy Recycling. IEEE Wirel. Commun. Lett. 2015, 4, 201–204. [Google Scholar] [CrossRef] [Green Version]
- Kim, H.; Kang, J.; Jeong, S.; Lee, K.E.; Kang, J. Secure beamforming and self-energy recycling with full-duplex wireless-powered relay. In Proceedings of the 2016 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016. [Google Scholar] [CrossRef]
- Li, T.; Chen, P.; Wang, Z.; Xiao, N. Secure Beamforming for Simultaneous Wireless Information and Power Transfer in Wireless-Powered Full-Duplex Relay Networks. In Proceedings of the 2019 14th International Conference on Computer Science & Education (ICCSE), Toronto, ON, Canada, 19–21 August 2019. [Google Scholar]
- Chen, P.; Li, T.; Fang, X. Secure Beamforming and Artificial Noise Design in Full-Duplex Wireless-Powered Relay Networks. In Proceedings of the 2019 IEEE 11th International Conference on Communication Software and Networks (ICCSN), Chongqing, China, 12–15 June 2019. [Google Scholar]
- Wu, W.; Wang, B.; Deng, Z.; Zhang, H. Secure Beamforming for Full-Duplex Wireless Powered Communication Systems With Self-Energy Recycling. IEEE Wirel. Commun. Lett. 2017, 6, 146–149. [Google Scholar] [CrossRef]
- Hu, S.; Ding, Z.; Ni, Q. Beamforming optimisation in energy harvesting cooperative full-duplex networks with self-energy recycling protocol. IET Commun. 2016, 10, 848–853. [Google Scholar] [CrossRef] [Green Version]
- Su, Y.; Jiang, L.; He, C. Decode-and-forward relaying with full-duplex wireless information and power transfer. IET Commun. 2017, 11, 2110–2115. [Google Scholar] [CrossRef]
- Chu, Z.; Zhou, F.; Xiao, P.; Zhu, Z.; Mi, D.; Al-Dhahir, N.; Tafazolli, R. Resource Allocation for Secure Wireless Powered Integrated Multicast and Unicast Services with Full Duplex Self-Energy Recycling. IEEE Trans. Wirel. Commun. 2018, 18, 620–636. [Google Scholar] [CrossRef] [Green Version]
- Li, J.; Ding, X.; Li, X.; Zhao, K.; Shi, W. Research on the Energy Allocation Scheme Based on SWIPT Relaying System. Mob. Netw. Appl. 2018, 23, 1449–1458. [Google Scholar] [CrossRef]
- Wu, J.; Kong, W.; Gao, P.; Jin, N.; Zhang, J.; Tao, J.; Snášel, V. Design Consideration of Bidirectional Wireless Power Transfer and Full-Duplex Communication System via a Shared Inductive Channel. Energies 2021, 14, 4918. [Google Scholar] [CrossRef]
- Mou, W.; Cai, Y.; Yang, W.; Yang, W.; Xu, X.; Hu, J. Exploiting full Duplex techniques for secure communication in SWIPT system. In Proceedings of the 2015 International Conference on Wireless Communications & Signal Processing (WCSP), Nanjing, China, 15–17 October 2015. [Google Scholar]
- Deng, Z.; Gao, Y.; Li, W.; Cai, C. Robust secure beamforming for SWIPT systems with full-duplex receivers and energy-harvesting eavesdroppers. In Proceedings of the 2017 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Taipei, Taiwan, 12–14 June 2017. [Google Scholar]
- Liu, M.; Liu, Y. Power Allocation for Secure SWIPT Systems with Wireless-Powered Cooperative Jamming. IEEE Commun. Lett. 2017, 21, 1353–1356. [Google Scholar] [CrossRef] [Green Version]
- Niu, H.H.; Zhang, B.N.; Guo, D. Joint cooperative beamforming and artificial noise design for secure AF relay networks with energy-harvesting eavesdroppers. Front. Inf. Technol. Electron. Eng. 2017, 18, 850–862. [Google Scholar] [CrossRef]
- Yu, H.; Wan, S.; Cai, W.; Xu, L.; Zhou, X.; Wang, J.; Wu, Y.; Shu, F.; Wang, J.; Wang, J. GPI-based Secrecy Rate Maximization Beamforming Scheme for Wireless Transmission with AN-aided Directional Modulation. IEEE Access 2017, 6, 12044–12051. [Google Scholar] [CrossRef]
- Dang, S.; Chen, G.; Coon, J.P. Outage Performance Analysis of Full-Duplex Relay-Assisted Device-to-Device Systems in Uplink Cellular Networks. IEEE Trans. Veh. Technol. 2016, 99, 4506–4510. [Google Scholar] [CrossRef] [Green Version]
- Hehao, N.; Zhang, B.; Guo, D.; Huang, Y. Joint Robust Design for Secure AF relay Networks with SWIPT. IEEE Access 2017, 5, 9369–9377. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Chen, H. Robust Artificial Noise-Aided Secure Beamforming in Wireless-Powered Non-Regenerative Relay Networks. IEEE Access 2016, 4, 7921–7929. [Google Scholar] [CrossRef]
- Qiao, J.; Zhang, H.; Zhou, X.; Yuan, D. Joint beamforming and time switching design for secrecy rate maximization in wireless-powered FD relay systems. IEEE Trans. Veh. Technol. 2017, 67, 567–579. [Google Scholar] [CrossRef]
- Bi, Y.; Chen, H. Accumulate and Jam: Towards Secure Communication via A Wireless-Powered Full-Duplex Jammer. IEEE J. Sel. Top. Signal Process. 2016, 10, 1538–1550. [Google Scholar] [CrossRef]
- Qiao, J.; Zhang, H.; Zhao, F.; Yuan, D. Secure Transmission and Self-Energy Recycling with Partial Eavesdropper CSI. IEEE J. Sel. Areas Commun. 2018, 36, 1531–1543. [Google Scholar] [CrossRef] [Green Version]
- Luo, Z.; Ma, W.; So, A.M.; Ye, Y.; Zhang, S. Semidefinite Relaxation of Quadratic Optimization Problems. IEEE Signal Process. Mag. 2010, 27, 20–34. [Google Scholar] [CrossRef]
- Michael Grant and Stephen Boyd. CVX: Matlab Software for Disciplined Convex Programming, Version 2.0 Beta. Available online: http://cvxr.com/cvx (accessed on 20 September 2013).
- Nguyen, T.N.; Tran, P.T.; Voznak, M. Wireless energy harvesting meets receiver diversity: A successful approach for two-way half-duplex relay networks over block Rayleigh fading channel. Comput. Netw. 2020, 172, 107176. [Google Scholar] [CrossRef]
- Srirutchataboon, G.; Kochi, J.; Sugiura, S. Performance Analysis of Hybrid Buffer-Aided Cooperative Protocol Based on Half-Duplex and Virtual Full-Duplex Relay Selections. IEEE Open J. Commun. Soc. 2021, 2, 1862–1873. [Google Scholar] [CrossRef]
- Zhu, G.; Lin, X.; Zhu, K.; Zhang, W.; Yu, J.X. TreeSpan: Efficiently computing similarity all-matching. In Proceedings of the 2012 ACM SIGMOD International Conference on Management of Data, New York, NY, USA, 20–24 May 2012; pp. 529–540. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ou, L.; Chen, P.; Luo, X.; Dang, S.; Sun, Y. Energy Signal-Aided Secure Beamforming and Self-Energy Recycling in Full-Duplex Wireless-Powered Relay Networks. Energies 2021, 14, 6497. https://doi.org/10.3390/en14206497
Ou L, Chen P, Luo X, Dang S, Sun Y. Energy Signal-Aided Secure Beamforming and Self-Energy Recycling in Full-Duplex Wireless-Powered Relay Networks. Energies. 2021; 14(20):6497. https://doi.org/10.3390/en14206497
Chicago/Turabian StyleOu, Lizhen, Peipei Chen, Xueshan Luo, Shuping Dang, and Yuchen Sun. 2021. "Energy Signal-Aided Secure Beamforming and Self-Energy Recycling in Full-Duplex Wireless-Powered Relay Networks" Energies 14, no. 20: 6497. https://doi.org/10.3390/en14206497
APA StyleOu, L., Chen, P., Luo, X., Dang, S., & Sun, Y. (2021). Energy Signal-Aided Secure Beamforming and Self-Energy Recycling in Full-Duplex Wireless-Powered Relay Networks. Energies, 14(20), 6497. https://doi.org/10.3390/en14206497




