Abstract
The strong coupling between the power grid and communication systems may contribute to failure propagation, which may easily lead to cascading failures or blackouts. In this paper, in order to quantitatively analyse the impact of interdependency on power system vulnerability, we put forward a “degree–electrical degree” independent model of cyber-physical power systems (CPPS), a new type of assortative link, through identifying the important nodes in a power grid based on the proposed index–electrical degree, and coupling them with the nodes in a communication system with a high degree, based on one-to-one correspondence. Using the double-star communication system and the IEEE 118-bus power grid to form an artificial interdependent network, we evaluated and compare the holistic vulnerability of CPPS under random attack and malicious attack, separately based on three kinds of interdependent models: “degree–betweenness”, “degree–electrical degree” and “random link”. The simulation results demonstrated that different link patterns, coupling degrees and attack types all can influence the vulnerability of CPPS. The CPPS with a “degree–electrical degree” interdependent model proposed in this paper presented a higher robustness in the face of random attack, and moreover performed better than the degree–betweenness interdependent model in the face of malicious attack.
1. Introduction
With the advent of intelligent power grids, the interaction between communication systems and power grids has increased rapidly, forming complex interconnected networks called cyber-physical power systems (CPPS). Communication systems and power grids work cooperatively to supply service for human beings; they belong to different infrastructures but are representatively interdependent [1,2]. The interdependency between the two heterogeneous networks means that the power grid relies on a communication network for transmitting data and control information; meanwhile, it supplies electricity to the normal running of the communication network [3].
Under some circumstances, composite networks give rise to a security risk far more than single systems, where the strong coupling easily facilitates the propagation of an initial tiny failure, potentially resulting in catastrophic cascading events. For example, such cases were seen in the dramatic large-scale blackout of Italy on 28 September 2003, and the blackout of the Ukrainian power grid in 2016, due to external interference of hackers through the data network. It seems as though CPPS are more vulnerable holistically because of the embedding interactions [4]. While this conclusion may be incomplete and awry for all cases, the impact of interdependency is still not explicitly known and requires further studies.
The communication system and the power grid are completely heterogeneous in nature. The power grid belongs to a time-varying and continuous system, while the communication system is a discrete system. There are obvious differences between them in terms of components, transmission content and working mechanisms [5]. Research on the interaction between the cyber layer and physical layer contributes to reveal the propagation law of cascading fault in CPPS.
Traditional fault analyses are mostly focused on the power system internally. Furthermore, the majority of existing approaches treat the communication network and power grid as two individuals, ignoring the coupling relationship between cyber and physical layers, where they are separated completely and modelled independently.
The seminal contribution is that Buldyrev et al. [6] have developed a framework for understanding the robustness of interactive networks, and have applied this to analyzing cascading failures in a real power network and an internet network. Reference [7] points out that the percolation transition of a randomly coupled network of network (NON)-system is second order. In Reference [8], the authors proposed the concept of inter-similarity between networks and found that the robustness of coupled networks to random attacks could be significantly enhanced by increasing the similarity. Reference [9] proved that the double-star communication networks perform better than the mesh communication networks to prevent cascading failures in CPPS. Jia Guo et al. demonstrated that degree–betweenness interface type is the best in all closeness centrality interface strategies [10]. Reference [11] proposed a Markov-chain framework to capture the interdependence between infrastructure networks and evaluate the impacts of interdependence on recovery capability and system reliability. The authors in [12] put forward a framework to investigate the vulnerability of multi-layer networks and took the Shanghai urban rail transit network as an example to verify it. Recovery interventions are considered for mitigating cascading failures in a real network scenario of CPPS in [13]. In [14], the impacts of flow directions and line limits were analyzed and new electrical betweenness measures are proposed for power grid vulnerability assessment.
On the foundation of the above research, this paper provides a novel interdependent model with the “degree-electrical degree” assortative link pattern. Then, we compared the three types (“degree-electrical degree link”, “degree-betwenness link” or “random link”) of interdependent models and analyzed the corresponding integral vulnerability of the cyber-physical power system under random or malicious attacks.
The remainder of this paper is organized as follows. Fundamental concepts of the complex network and interdependent network are outlined in Section 2. In Section 3, we describe the interdependent model of CPPS based on the degree–electrical degree link pattern. The propagation process of cascading failures in interdependent networks is introduced in Section 4. In Section 5, we introduce the CPPS vulnerability assessment index. Section 6 shows the case study and simulation results. Finally, the related conclusions are discussed in Section 7.
2. Fundamental Concepts of Complex Network and Interdependent Network
2.1. Fundamental Concepts of Complex Network Theory
A network can be abstracted into a graph by leaving out the intrinsic properties of the components, where is a set of nodes and is a set of edges connecting ordered pairs of distinct nodes . Aside from this, an important notion must be mentioned, this being the adjacency matrix :
where which explicitly represents whether there is a link connecting the node pair or not.
2.1.1. Random Network
The generation method of random network was proposed by Erdős and Rényi in 1959 [15]. The random edges are rewired with a probability to connect two chosen nodes. The vital parameter is the connectivity or average degree, which measures the amount of neighbours that one node has in a synthetic random graph.
2.1.2. Average Path Length
The distance between two nodes in a network is quantified by the sum of edges that the shortest path passes through. Moreover, the maximum geodesic distance between any two nodes is called the diameter of the network, denoted as D, that is
The average path length , also known as characteristic path length, is referred to as the average distance between any two nodes in the network. The full expression of the average path length is
where is the amount of nodes.
2.1.3. Clustering Coefficient
The clustering coefficient , which is introduced to measure the connectivity between two nodes, is defined as proposed by Watts and Strogatz [16]:
where , which is a local clustering coefficient to show the likelihood of interconnection for two neighbours of the node [15]. By definition, we could know that and .
2.1.4. Degree and Degree Distribution
The degree of a node is defined as the sum of other nodes connected with that node. For a directed network, in-degree and out-degree respectively represent the numbers of incoming and outgoing links. Intuitively, the greater the degree is, the more significant the node appears to be. We can use the function to describe the distribution of nodes’ degree and make a plot of the cumulative distribution function, which expresses the probability where the degree of a stochastically selected node happens to be .
Regular graphs follow a simple degree distribution—delta distribution—since all the nodes shared the same degree. By contrast, random graphs are typically characterized by power-law distribution (namely scale-free distribution). Furthermore, completely random networks approximately show Poisson distribution.
2.1.5. Betweenness
The betweenness is equal to the number of shortest paths through a node or an edge. It is used to identify the critical components of a graph or network. The betweenness of node is formatted as
where is equivalent to the number of shortest paths between nodes and passing through node , and is the amount of shortest paths between nodes i and j.
2.1.6. Small-World Effect
The network, which has both short characteristic path length and high clustering coefficient, is labelled as a small-world network by Watts and Strogatz [16]. The small-world effect (six degrees of separation) is generic for many large and sparse real networks, and is reflected in social networks in that two of an individual’s friends, unfamiliar with each other, may have mutual acquaintances.
2.1.7. Scale-Free Network
Barthelemy and Amaral conjectured that networks with power-law degree distributions are referred to as scale-free networks, where a fraction of nodes have high connectivity while the majority of nodes have a small node degree [17].
2.2. Introduction of Interdependent Networks
Interdependent networks, namely super-networks, network of networks, or multiple networks, are composed of multiple single-layer networks with different structures or properties [18]. As shown in Figure 1, by taking networks A and B as an example, the dotted lines connecting interdependent nodes between different layers are called connecting edges, and three loopless connection types are shown in Figure 2. Generally, the connection between dependent edges falls into three types: (i) assortative links, (ii) disassortative links and (iii) random links [19]. Assortative links refers to connecting nodes with similar topological characteristics, such as node degree or betweenness, in two networks. Thus, the nodes in network A with higher degrees map the nodes in network B with higher degrees, and vice versa. Disassortative links mean that nodes in network A with higher degrees correspond to the nodes in network B with lower degrees, and vice versa. Random link refers to when the nodes in network A and B are connected randomly.
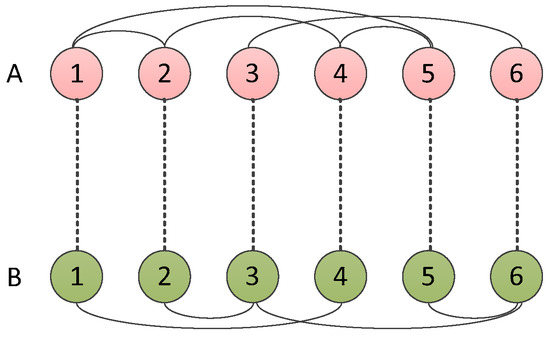
Figure 1.
Interdependency diagram.
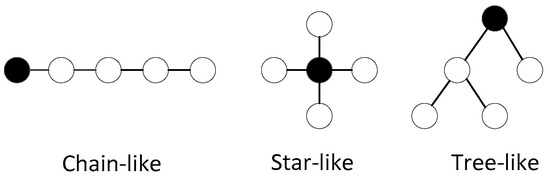
Figure 2.
Three types of interdependency.
The CPPS are large-scale composite systems in which the communication network and power grid are continuously interacting through interdependent nodes. Information collecting and monitoring equipment detect and upload the operation data in real-time, including measurement data (e.g., voltage and current of branches or nodes) and the operating state of devices (e.g., information of switches, breakers and transformer taps). The dispatch centre collects measurement information at nodes, monitors the power flow on the transmission line, manages the changes of network topology and then issues control commands [20]. The typical CPPS architecture is shown in Figure 3. Interactive nodes have diverse corresponding relation, for instance, one-to-one, one-to-more, more-to-one and more-to-more. In order to simplify the calculation, we assume that it is a one-to-one correspondence between power nodes and communication nodes.
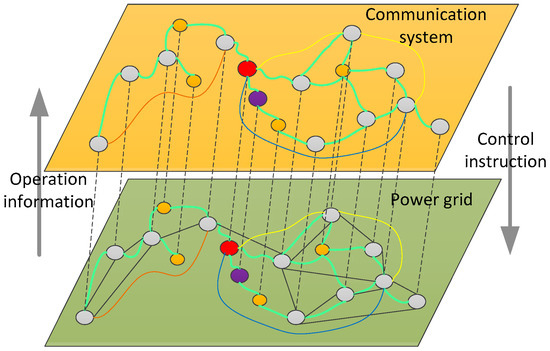
Figure 3.
The interdependency between the communication system and power grid.
3. Interdependent Model of Cyber Physical Power System
The topologies of the communication system and power grid were abstracted and expressed as undirected graphs and , respectively. Each layer represented a network with a specific structure and function. , where is the set of nodes in a network, and represents the set of internal edges in each layer.
3.1. The Model of Communication Networks
The cyber layer is a communication network based on Ethernet, where communication facilities, data channels and related algorithms were all represented as normal nodes. Because of transmission characteristics, some special communication nodes were not connected to power nodes, which only connect the inside communication nodes. For the sake of simplicity, we left out this condition in the paper. The connection relation between the communication nodes were expressed by the adjacency matrix, as follows:
where indicates the two nodes and were connected, otherwise .
There are two typical structures of the communication network: the double-star network and mesh network. Double-star networks belong to scale-free networks, while mesh networks show small-world properties. The power system is also a small-world network and sensitive to random attacks. It has been demonstrated in the literature [4] that the composite system obtained by coupling two layers of small-world network has a worse robustness under any attacks. Therefore, we only adopted the double-star communication network.
To generate a communication network, the initial node was specified, and on the base of it we added a new node and edges in one time step, and connected it to existing nodes according to the probability , where is the degree of the node and is the sum of degree value of all the existing nodes. As the communication network belonged to a scale-free network, we employed the degree value to identify crucial nodes. Then, the control centre (Power Dispatching Centre) [8] always corresponded to the node with highest degree.
3.2. The Model of Power Grids
The relation between load nodes in the power grid can be expressed using the adjacency matrix, as follows:
The power grid is a typical small-world network [9]. Thus, to find out vital nodes, the single index, the degree–betweenness, is questionable. The importance of power nodes depends on (1) node property (2) the location of nodes in the entire topology. Each node does not exist independently but closely relates to its neighbours. Therefore, we introduced the importance evaluation matrix for power nodes:
where is the total number of network nodes, represents the corresponding elements in the adjacent matrix, represents the average degree, is the degree of node and is the distribution parameter of the contribution degree, which denotes that node distributes its importance to adjacent node , and self-contribution is 100%.
Referring to the concept of network efficiency in complex network theory, we defined the connectivity efficiency to describe the difficulty of node for connecting other node .
If two nodes are not directly connected, , then . It shows that the smaller the line impedance value is, the more closely the two nodes are connected.
Therefore, we get the importance evaluation index of the electrical node, called the electrical degree.
This index fuses the topological property and the electrical characteristics of nodes, which was used to evaluate the importance of each node in the power grid.
3.3. Interactive Mechanism and Model between Power Grids and Communications Network
The interdependency between the communication system and power grid is shown as the dotted lines in Figure 2 and represented as . The communication layer had N nodes and the power layer had M nodes . Then, the overall CPPS can be described as follows:
where, if communication nodes and power nodes exchange energy or information reciprocally, , which means that there is a connecting edge; otherwise, .
In this paper, we advanced an interdependent network model based on assortative coupling, that is, the key nodes in the communication network corresponded to the important nodes in the power grid, called degree–electrical degree coupling. Firstly, in the communication network, all nodes were arranged in descending order of node degree , namely . If two nodes had the same degree, we further compared their betweenness and similarly array in descending order. The higher the degree of nodes, the more crucial the nodes were in the topology. As long as those important nodes survived under attacks, the system could retain normal operation. Secondly, in the power gird, the electrical degree of nodes was calculated, which was adopted to arrange the results from large to small, . Thirdly, we connected the first M cyber nodes and physical nodes one by one correspondingly to generate the symmetric interdependent network model studied in this paper.
Aside from this, for comparison, we obtained the degree–betweenness interdependent model in the same way. The cyber nodes were sorted by node degree in descending order, and the physical nodes were sorted by betweenness in descending order. Then, some cyber nodes with higher degrees were connected to those physical nodes with higher betweenness. Thus, similarly, we achieved the random interdependent model by coupling the cyber and physical nodes randomly.
4. The Propagation Process of Cascading Failures
In this paper, we supposed that the communication network and power grid had the same law of cascading failures. Once a communication node fails, the coupling power node loses control and quits operation. Afterwards, its coupling communication nodes lose power supply, and even communication interruptions occur. If a power node fails, its adjacent nodes malfunction because of overload. Moreover, the coupling communication nodes are removed from the system because of lacking electricity or incorrect metrical data. At this point, we seek the maximal connected subgraph of the present network structure. If a node does not belong to the maximal connected subgraph, it cannot maintain its function anymore and will also be expired.
We assumed that the node 5 fails because of a random failure or deliberate attack, and the specific fault propagation process of cascading failure is described in Figure 4 [21].
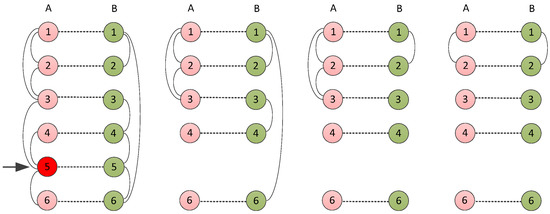
Figure 4.
The specific process of cascading failure in a cyber physical power system.
- First stage: in the cyber layer A, node 5 is attacked and fails, and its interconnected edges and interdependent edges are deleted.
- Second stage: in the physical layer B, the node dependent on cyber node 5 fails, and then the directly connected edges are removed.
- Third stage: we seek the maximal connected subgraph of the cyber network A and remove invalid nodes, and meanwhile delete the coupling nodes and relevant edges in the physical layer B.
- Fourth stage: the same as the third stage—the invalid nodes and connected edges in the cyber layer A are removed, and this cycle repeats until there are only the maximal connected subgraph left in network A and B. Then CPPS reaches the final stable state.
5. CPPS Vulnerability Assessment
For interdependent network, the ability to maintain structural and functional integrity under attack is significant. In order to quantitatively analyse the vulnerability of CPPS, we introduced two indices: survival rate of nodes and survival rate of actual load.
5.1. Survival Rate of Node
In this paper, we employed the survival rate of nodes to evaluate the completeness of topological structure after an attack.
5.2. Survival Rate of Actual Load
The following constraints must be satisfied during operation.
Taking the aforementioned constraints into consideration, we can calculate the power flow of the current system composed of surviving nodes after cascading failures to guarantee operation security. If generators or lines overloaded, a series of control measures must be taken, such as load shedding and generator trip. After that, the remaining nodes are the final saved power loads, and then we can calculate the actual load survival rate.
The two indexes proposed above are not only suitable for one-to-one link patterns, but are also applicable to one-to-more and more-to-more coupling types in interdependent networks.
6. Case Study and Simulation Results
In this paper, we tested our model on the IEEE 118-bus power system and double-star communication network with the same number of nodes, that is , depicted in Figure 5 and Figure 6, respectively. Generally, the power grid has a tree structure, while the communication network shows a ring structure. Table 1 fully reflects the difference between them in terms of structures and properties. A series of topological characteristics of the two networks [23], such as degree–betweenness, average degree and cluster coefficient, are listed below. We put forward a new interdependent model with degree–electrical degree assortative link and compared it with the degree–betweenness interdependent model and random link interdependent model. Deliberate attacks, based on node degree and random failures, were adopted to test the vulnerability of the artificial CPPS. The simulation flowchart is shown in Figure 7.
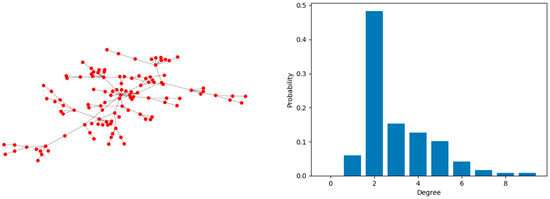
Figure 5.
The power grid and its degree distribution.
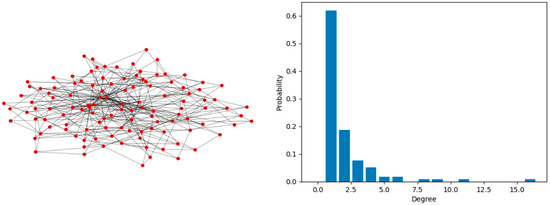
Figure 6.
The communication system and its degree distribution.

Table 1.
The statistical characteristics of the cyber physical power system.
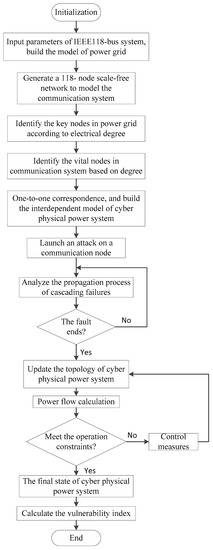
Figure 7.
Simulation flowchart.
In Table 1, is the number of nodes, is the number of edges, is the average node degree, denotes the clustering coefficient, L presents the average path length, and D is the network diameter.
6.1. Vulnerability of CPPS under Random Attack
Respectively, we took the three-type coupling modes to build the corresponding interdependent models: the random coupling interdependent model, the degree–betweenness interdependent model and the electrical degree–betweenness interdependent model. Firstly, we studied the vulnerability of CPPS under random attacks with different number of interdependent nodes (30, 60, 90, 118).
When analysing the interaction between the two networks, we took the intermediate connection type and coupling strength into consideration. Figure 8 illustrates how the different coupling strengths and connection types evidently effect the vulnerability of CPPS.
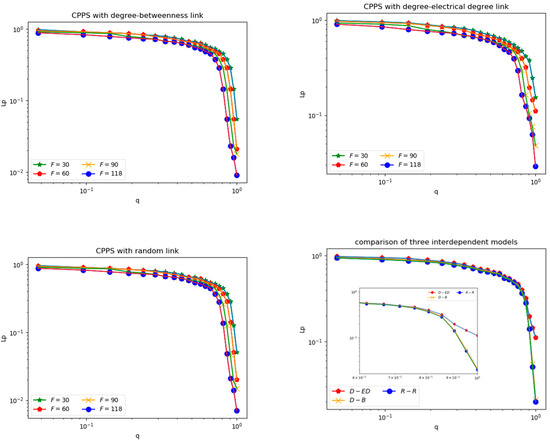
Figure 8.
The vulnerability of cyber-physical power systems (CPPS) under random attacks.
After launching a random attack against the communication system, we calculated and compared the actual load survival rate of the cyber physical power system with the “degree–betweenness”, “degree–electrical degree” and “random link” coupling modes.
From Figure 8 we know that, under a random attack, the three interdependent models showed similar performance. However, when a large scale attack was launched, the degree-electrical degree interdependent model could effectively reduce the probability of a blackout.
In addition, the figure shows that the resistibility of CPPS under random attack increased with the rise of coupling strength, regardless of what kind of interdependent model was used. Furthermore, the integral CPPS was the most robust with full dependence, i.e., F = 118, which is consistent with the conclusion in [24].
6.2. Vulnerability of CPPS under Malicious Attack
As above, comparisons were conducted between the “random link model”, “degree–betweenness link model” and “degree–electrical degree link model” under malicious attack. We calculated the vulnerability of the cyber physical power system under different interdependence strengths (30, 60, 90 and 118 strips of links). The simulation results are shown below, divided into four sets.
From Figure 9, we know that, compared with random attacks, the cyber physical power grid is more vulnerable to malicious attacks. In the case of malicious attacks, the cyber physical power system with a random link model is the most robust. The cyber nodes were connected with the power nodes randomly, thus the important nodes in the cyber layer and physical layer will not fail collectively after a malicious attack.
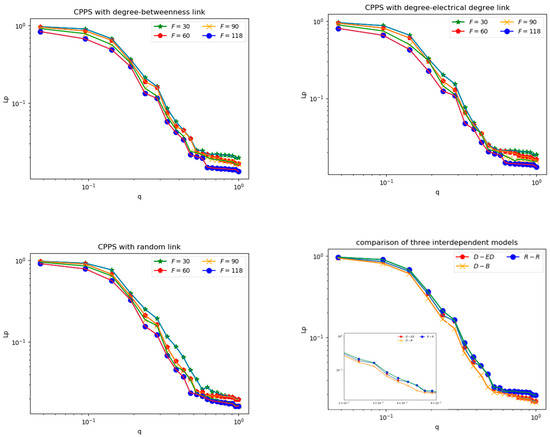
Figure 9.
The vulnerability of CPPS under malicious attack.
When the number of coupling edges was constant, the degree–electrical degree interdependent model was shown to be more robust than the degree–betweenness interdependent model, which will be useful in guiding the construction of a cyber physical power system.
Moreover, the figure shows that the vulnerability of CPPS under malicious attack increased with the rise of coupling strength. Furthermore, the integral system was the most vulnerable, with the mode of full dependence (i.e., F = 118).
7. Conclusions
Comprehensively getting hold of interaction mechanisms and dynamical characteristics of interdependent networks is the basis of cascading failure prevention in cyber physical power systems (CPPS). In this paper, a novel interdependent model of a cyber physical power system based on the degree–electrical degree coupling mode was put forward. As a case study, we took the double-star communication system, a scale-free network, and the IEEE 118-bus power grid, to generate an artificial CPPS. Then, the impacts of different interdependent models, coupling strength and attack types on CPPS vulnerability were analysed.
Through this research, we discovered that, on the premise of one-to-one correspondence, the cyber physical power system was shown to be more vulnerable under a malicious attack than under a random attack. Under a large scale random attack, the degree–electrical degree interdependent model effectively reduced the probability of large-scale blackout. In the case of malicious attack, the cyber physical power system with the random link pattern manifested as the most robust, and the degree–electrical degree interdependent model performed better than the degree–betweenness interdependent model. In addition, whatever the interdependent model, the robustness of the cyber physical power system decreased with the increase of coupling strength between the two layers. These simulation results reflect that the interaction or coupling between the communication system and power grid makes the power gird more vulnerable to some extent.
Moreover, in our opinion, in the future research of modelling and vulnerability analysis of cyber physical power systems, the following factors should be taken into consideration so as to improve the interdependent model: (1) In practice, the communication nodes and power nodes are not completely one-to-one coupled, and instead may be one-to-more or more-to-more connected. (2) Many vital communication nodes are configured with uninterruptible power supply (UPS) so that a short-time failure of the power gird will not affect the normal operation of the communication network, and thus the corresponding communication nodes may not fail immediately after some power nodes quit. (3) We should premeditate the intervention of multi-scenario requirements and various control measures to prevent cascading failures.
Author Contributions
Formal analysis, X.G. and H.Z.; Methodology, H.Z.; Resources, M.P.; Validation, Y.L.; Visualization, H.Z.; The initial version of the manuscript, H.Z. and J.M.G.; Review and editing, J.M.G.; The final version of the manuscript, H.Z.
Funding
This research was funded by the National Natural Science Foundation of China, grant numbers 61472128 and 61973107.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Otuoze, A.O.; Mustafa, M.W.; Larik, R.M. Smart grids security challenges: Classification by sources of threats. J. Electr. Syst. Inf. Technol. 2018, 5, 468–483. [Google Scholar] [CrossRef]
- Liu, W.; Gong, Q.; Han, H.; Wang, Z.; Wang, L. Reliability Modeling and Evaluation of Active Cyber Physical Distribution System. IEEE Trans. Power Syst. 2018, 33, 7096–7108. [Google Scholar] [CrossRef]
- Kröger, W.; Zio, E. Vulnerable Systems; Springer Science & Business Media: London, UK, 2011. [Google Scholar]
- Cai, Y.; Cao, Y.; Li, Y.; Huang, T.; Zhou, B. Cascading failure analysis considering interaction between power grids and communication networks. IEEE Trans. Smart Grid 2015, 7, 530–538. [Google Scholar] [CrossRef]
- Zhang, J.; Chu, Z.; Sankar, L.; Kosut, O. Can attackers with limited information exploit historical data to mount successful false data injection attacks on power systems? IEEE Trans. Power Syst. 2018, 33, 4775–4786. [Google Scholar] [CrossRef]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed]
- Parshani, R.; Buldyrev, S.V.; Havlin, S. Interdependent networks: Reducing the coupling strength leads to a change from a first to second order percolation transition. Phys. Rev. Lett. 2010, 105, 048701. [Google Scholar] [CrossRef] [PubMed]
- Chen, Z.; Wu, J.; Xia, Y.; Zhang, X. Robustness of interdependent power grids and communication networks: A complex network perspective. IEEE Trans. Circuits Syst. II Express Briefs 2017, 65, 115–119. [Google Scholar] [CrossRef]
- Cai, Y.; Li, Y.; Cao, Y.; Li, W.; Zeng, X. Modeling and impact analysis of interdependent characteristics on cascading failures in smart grids. Int. J. Electr. Power Energy Syst. 2017, 89, 106–114. [Google Scholar] [CrossRef]
- Guo, J.; Han, Y.; Guo, C.; Lou, F.; Wang, Y. Modeling and vulnerability analysis of cyber-physical power systems considering network topology and power flow properties. Energies 2017, 10, 87. [Google Scholar] [CrossRef]
- Rahnamay-Naeini, M.; Hayat, M.M. Cascading failures in interdependent infrastructures: An interdependent Markov-chain approach. IEEE Trans. Smart Grid 2016, 7, 1997–2006. [Google Scholar] [CrossRef]
- Zhang, J.; Song, B.; Zhang, Z.; Liu, H. An approach for modeling vulnerability of the network of networks. Phys. A Stat. Mech. Its Appl. 2014, 412, 127–136. [Google Scholar] [CrossRef]
- Tootaghaj, D.Z.; Bartolini, N.; Khamfroush, H.; He, T.; Chaudhuri, N.R.; La Porta, T. Mitigation and Recovery from Cascading Failures in Interdependent Networks under Uncertainty. IEEE Trans. Control Netw. Syst. 2018, 6, 501–514. [Google Scholar] [CrossRef]
- Wu, D.; Ma, F.; Javadi, M.; Thulasiraman, K.; Bompard, E.; Jiang, J.N. A study of the impacts of flow direction and electrical constraints on vulnerability assessment of power grid using electrical betweenness measures. Phys. A Stat. Mech. Its Appl. 2017, 466, 295–309. [Google Scholar] [CrossRef]
- Erdős, P.; Rényi, A. On the evolution of random graphs. Publ. Math. Inst. Hung. Acad. Sci. 1960, 5, 17–60. [Google Scholar]
- Watts, D.J.; Strogatz, S.H. Collective dynamics of ‘small-world’ networks. Nature 1998, 393, 440–442. [Google Scholar] [CrossRef]
- Barabási, A.L.; Albert, R. Emergence of scaling in random networks. Science 1999, 286, 509–512. [Google Scholar] [CrossRef] [PubMed]
- Gao, J.; Buldyrev, S.V.; Stanley, H.E.; Havlin, S. Networks formed from interdependent networks. Nat. Phys. 2012, 8, 40–48. [Google Scholar] [CrossRef]
- Rueda, D.F.; Calle, E. Using interdependency matrices to mitigate targeted attacks on interdependent networks: A case study involving a power grid and backbone telecommunications networks. Int. J. Crit. Infrastruct. Prot. 2017, 16, 3–12. [Google Scholar] [CrossRef]
- Wang, H.; Ruan, J.; Zhou, B.; Li, C.; Wu, Q.; Raza, M.Q.; Cao, G. Dynamic Data Injection Attack Detection of Cyber-Physical Power Systems with Uncertainties. IEEE Trans. Ind. Inform. 2019, 1. [Google Scholar] [CrossRef]
- Moussa, B.; Akaber, P.; Debbabi, M.; Assi, C. Critical links identification for selective outages in interdependent power-communication networks. IEEE Trans. Ind. Inform. 2017, 14, 472–483. [Google Scholar] [CrossRef]
- Ye, H.; Mou, Q.; Wang, X.; Liu, Y. Eigen-analysis of large delayed cyber-physical power system by time integration-based solution operator discretization methods. IEEE Trans. Power Syst. 2018, 33, 5968–5978. [Google Scholar] [CrossRef]
- Kong, P.Y. Optimal Configuration of Interdependence between Communication Network and Power Grid. IEEE Trans. Ind. Inform. 2019, 15, 4054–4065. [Google Scholar] [CrossRef]
- Wang, J.; Jiang, C.; Qian, J. Robustness of interdependent networks with different link patterns against cascading failures. Phys. A Stat. Mech. Its Appl. 2014, 393, 535–541. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).