Intelligent Classification Method for Grid-Monitoring Alarm Messages Based on Information Theory
Abstract
1. Introduction
- We build a multi-dimensional evaluation index system based on information theory and determine the information value of monitoring alarm messages from a statistical viewpoint. Thus, we overcome the barrier of set rules and reduce the workload of the supervisors.
- The analytic hierarchy process (AHP) is used to comprehensively evaluate alarm messages. It can realize the automatic classification and intelligent marking of large numbers of monitoring alarm messages. The disposal pattern can be transformed from the passive response to a single record to active perception hierarchically.
2. Quantitative Calculation of the Information Value of Alarm Messages Based on Information Theory
2.1. Pre-Processing of Alarm Messages
2.2. Alarm Messages and Information Theory
2.3. Definition of Alarm-Message Entropies
2.3.1. Absolute Alarm-Message Entropy
2.3.2. Average Absolute Alarm-Message Entropy
2.3.3. Term Frequency-Inverse Document Frequency (TF-IDF) Alarm-Message Entropy
2.3.4. Average TF-IDF Alarm-Message Entropy
2.3.5. Relative Alarm-Message Entropy
2.3.6. Average Relative Alarm-Message Entropy
2.3.7. Self-Information of the Alarm Message
3. Comprehensive Evaluation of Alarm Messages Based on the Analytic Hierarchy Process
3.1. Construction of the Judgment Matrix
3.2. Hierarchical Ranking and Consistency Check
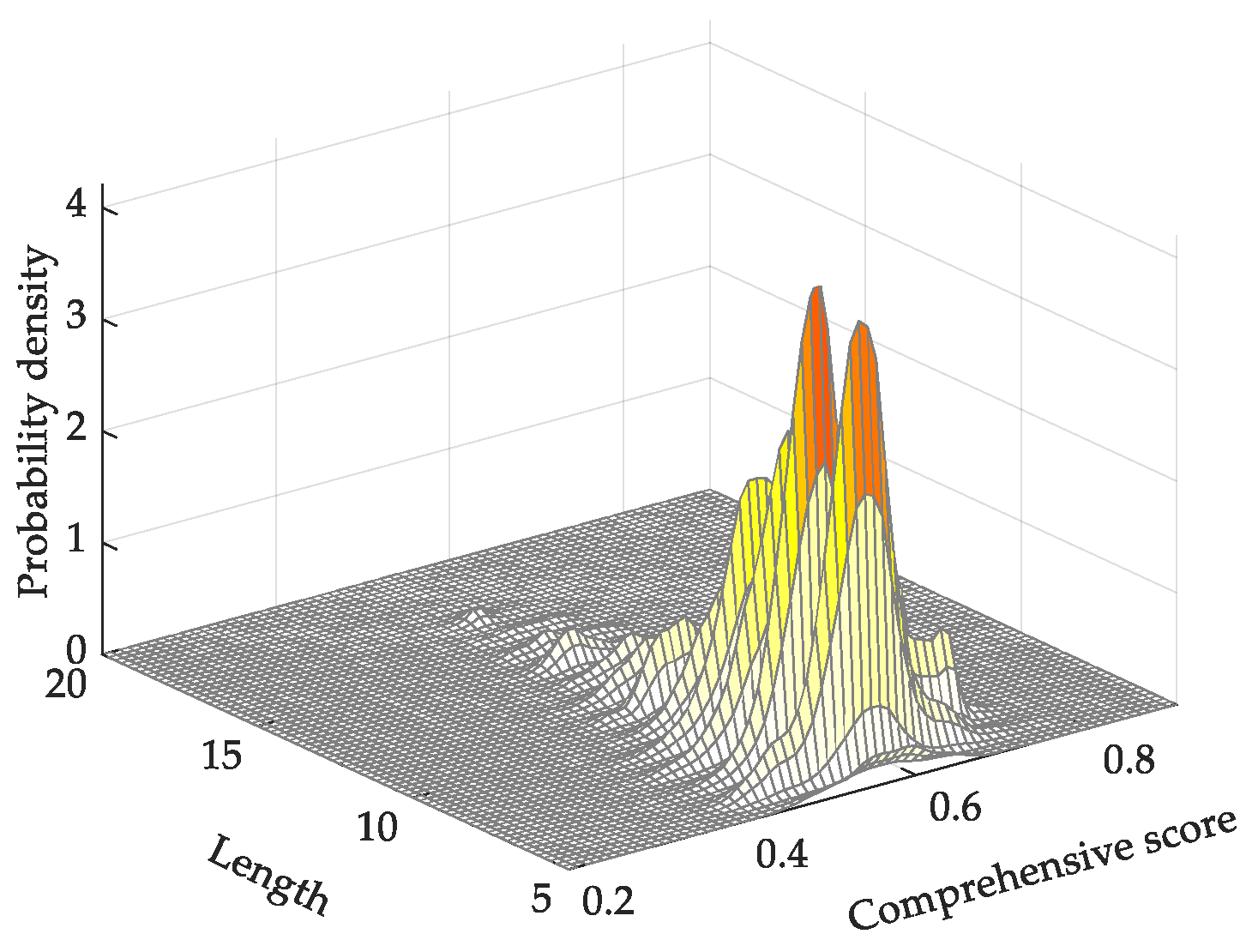
3.3. Comprehensive Evaluation
4. Results
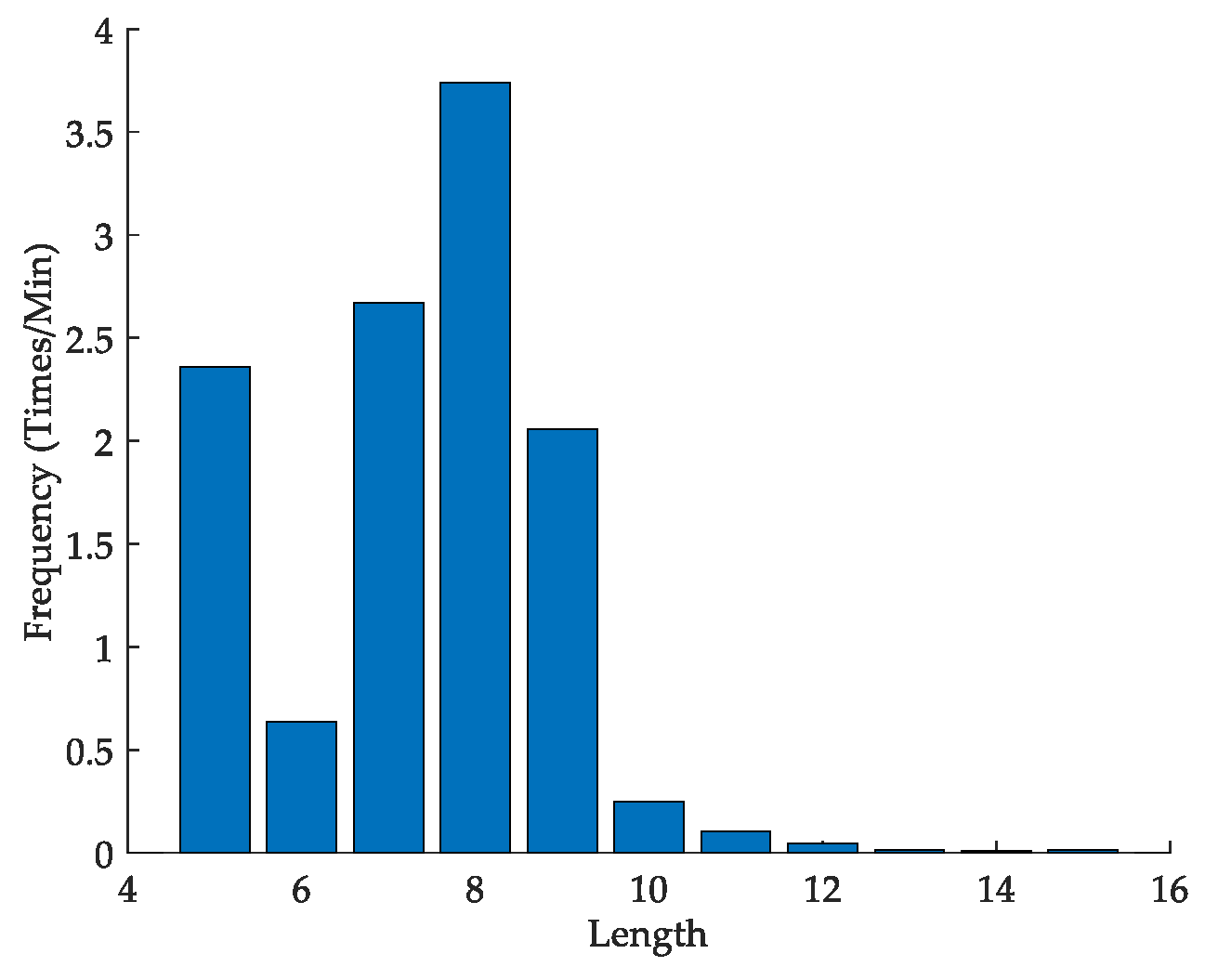
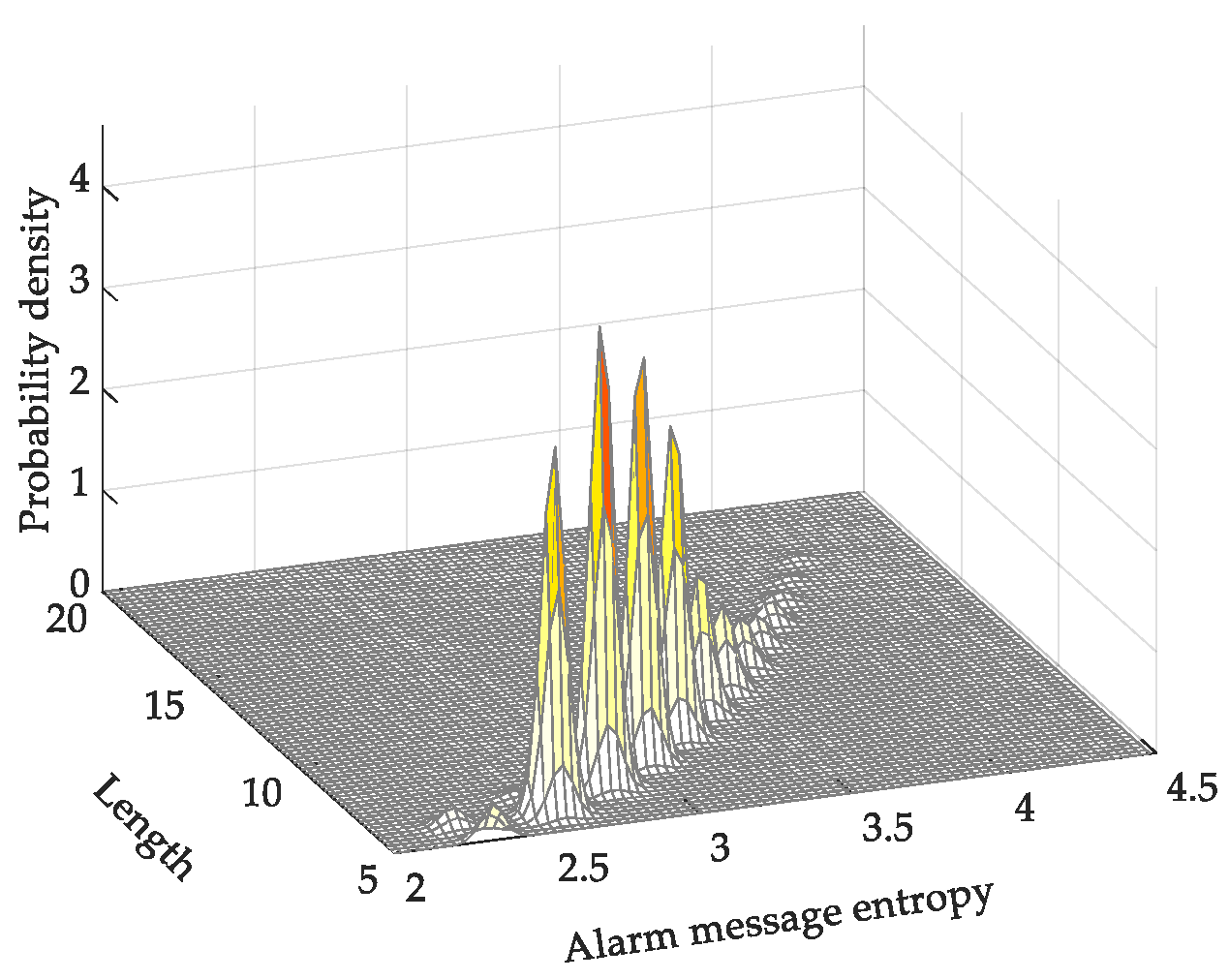
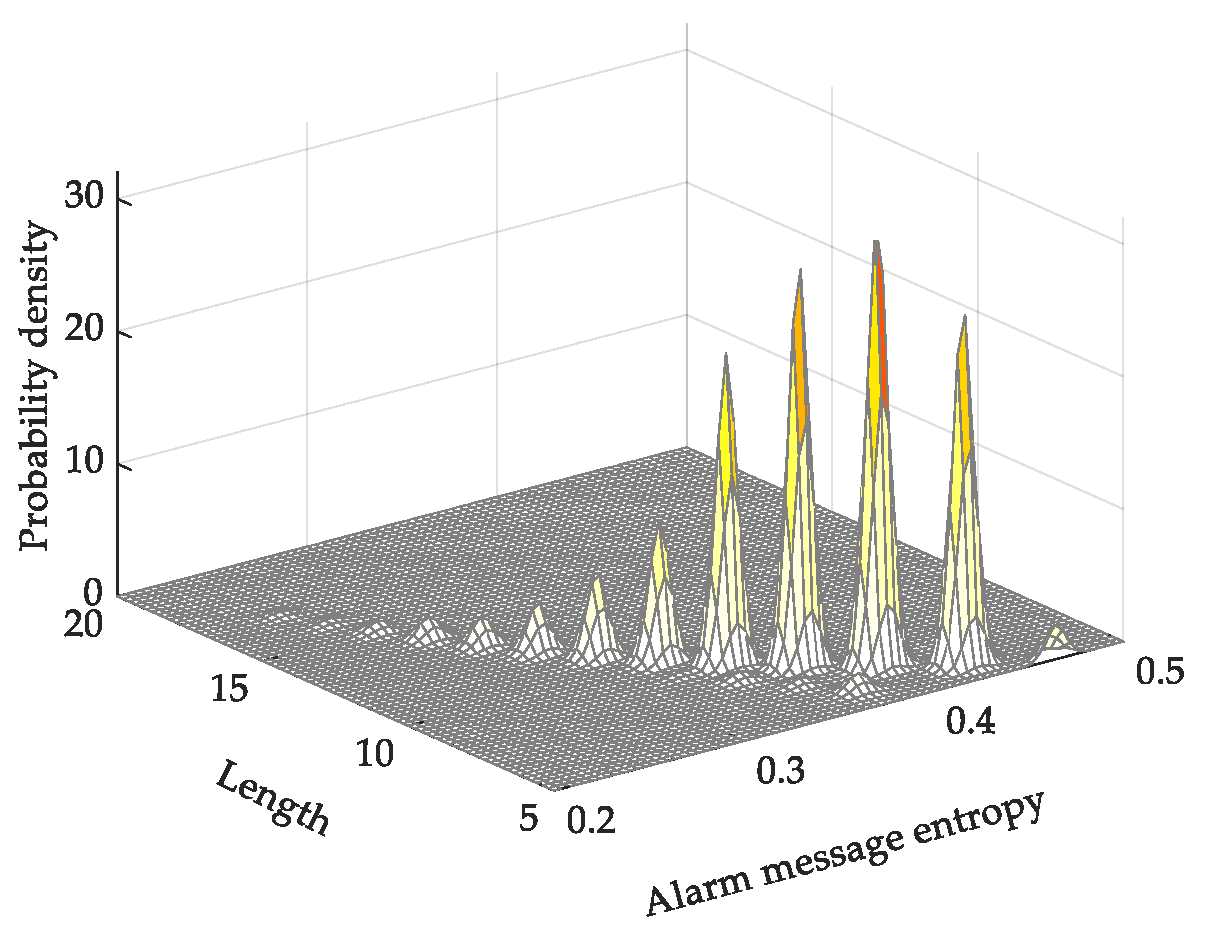
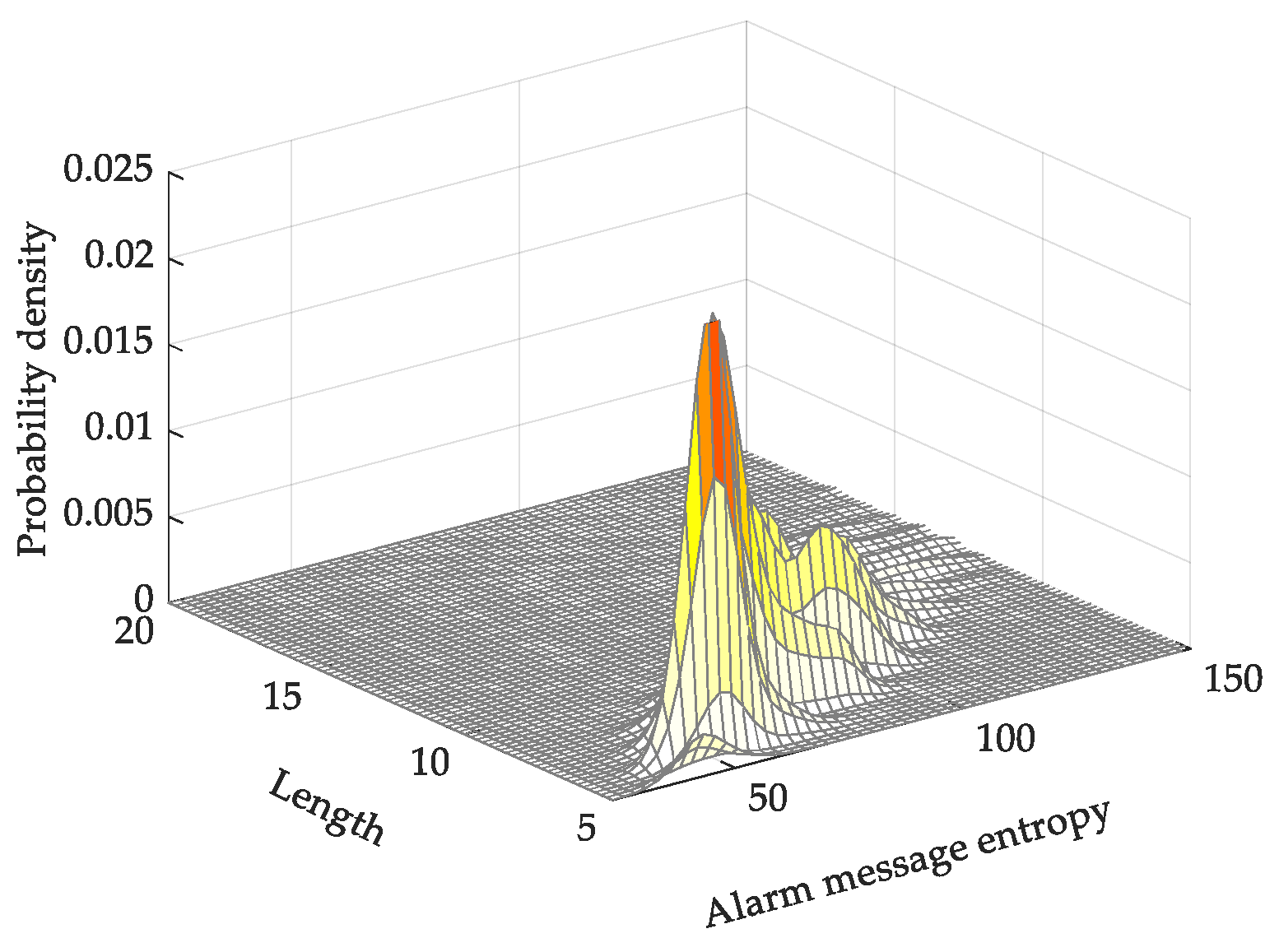
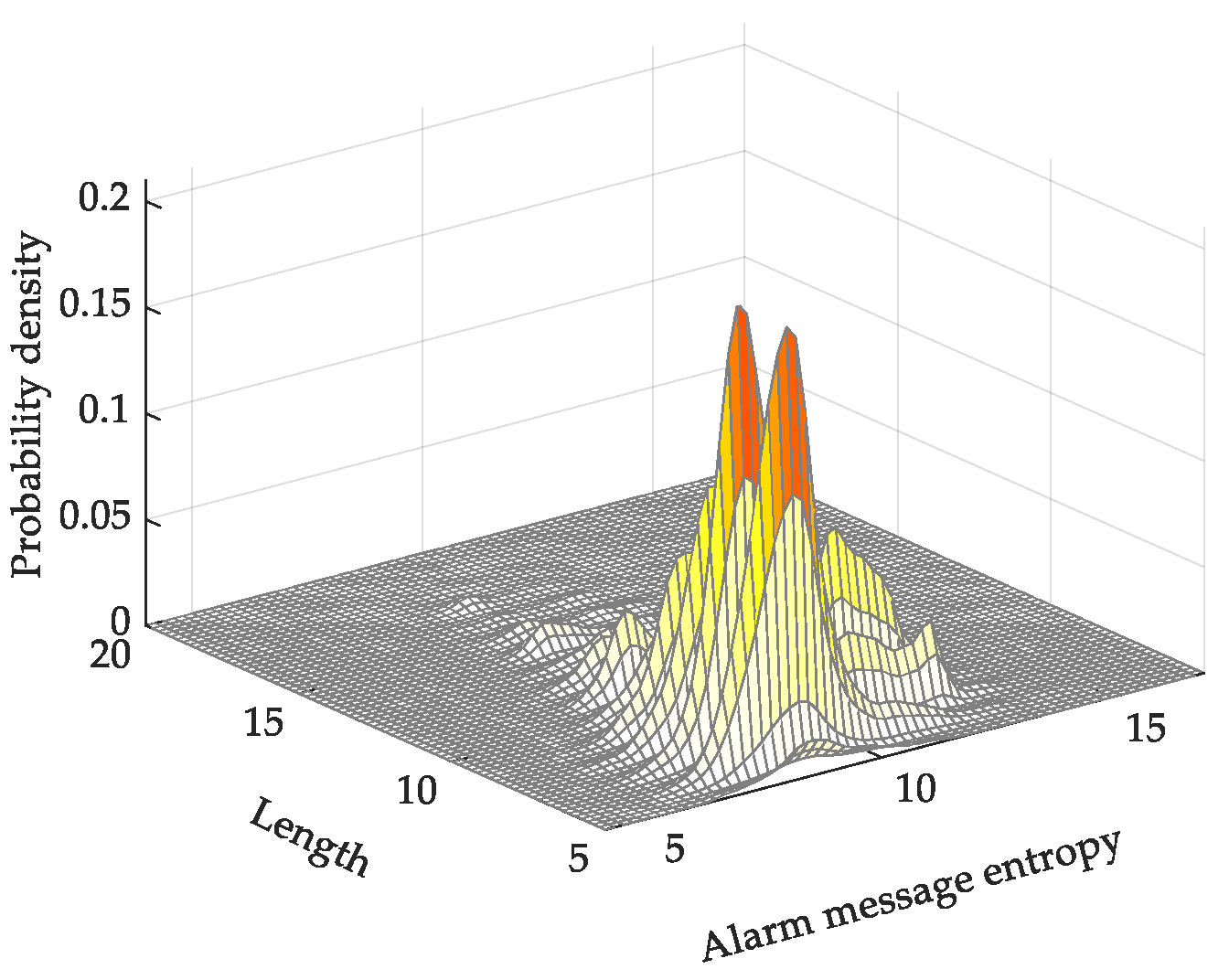
4.1. Analysis of Multiple Alarm-Message Entropies
- 1.
- Absolute alarm-message entropy
- 2.
- Average absolute alarm-message entropy
- 3.
- TF-IDF alarm-message entropy
- 4.
- Average TF-IDF Alarm-Message Entropy
- 5.
- Relative alarm-message entropy
- 6.
- Average relative alarm-message entropy
- 7.
- Self-information of monitoring alarm messages
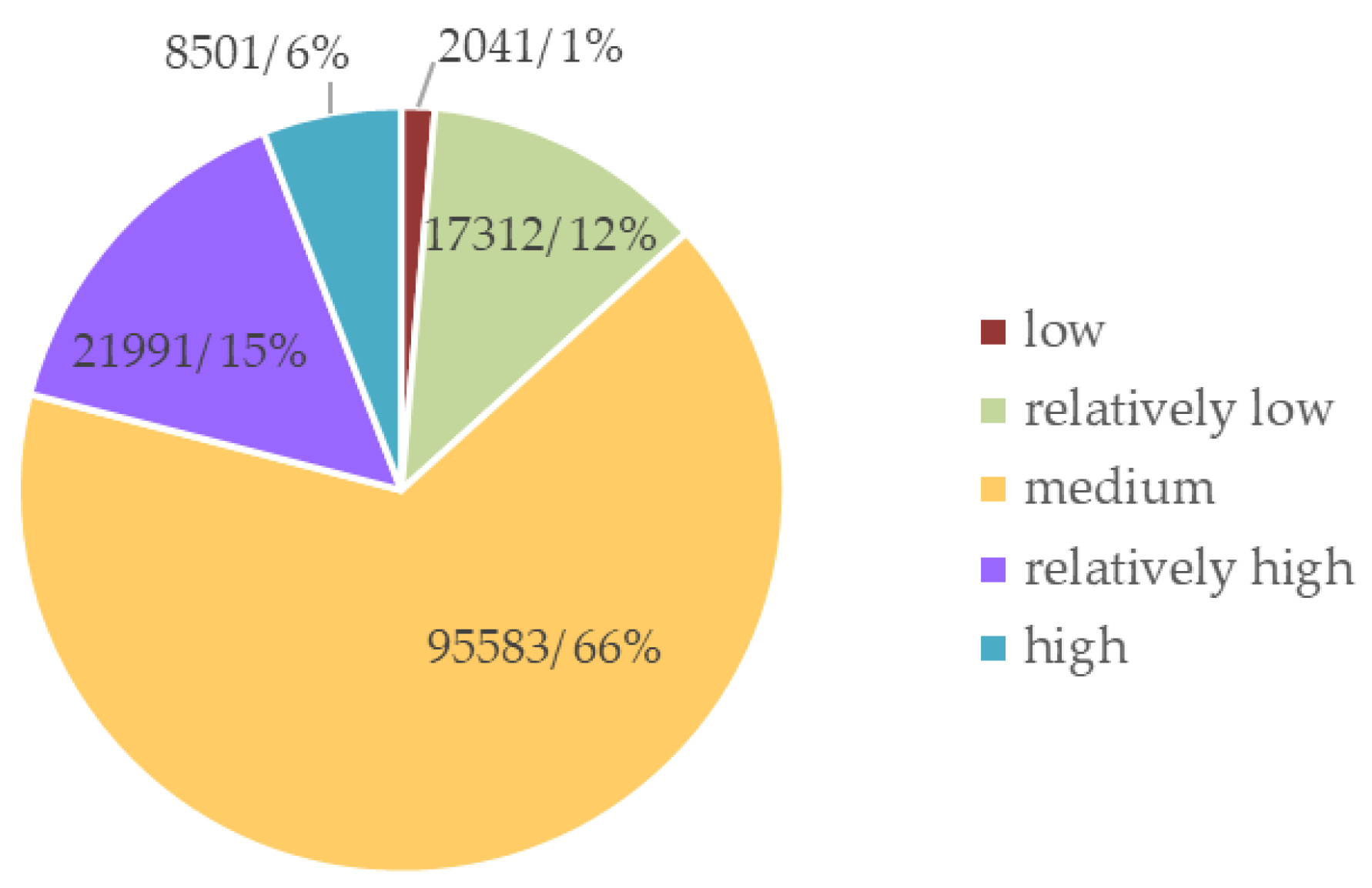
4.2. Analysis of Comprehensive Evaluation
5. Discussion
6. Conclusions
- The proposed method is based on information theory and can quantify the value of alarm messages at the sentence and word levels. It can achieve the automatic classification of alarm messages.
- Based on the analytic hierarchy process (AHP), this method combines the advantages of the measurement of various kinds of entropy, and can be used to carry out accurate and overall classification of alarm messages.
Author Contributions
Funding
Conflicts of Interest
References
- Yu, C.; Yi, W.; Yunlong, D.; Ning, X.; Tianxia, Z.; Limin, W. Application of Alarm Message Statistical Analysis Based on Protection and Fault Information System. In Proceedings of the 2018 IEEE International Conference of Safety Produce Informatization (IICSPI), Chongqing, China, 10–12 December 2018; pp. 719–722. [Google Scholar]
- Li, Z.X.; Yin, X.G.; Zhang, Z.; He, Z. Wide-Area Protection Fault Identification Algorithm Based on Multi-Information Fusion. IEEE Trans. Power Deliv. 2013, 28, 1348–1355. [Google Scholar]
- Zang, H.; Cheng, L.; Ding, T.; Cheung, K.W.; Liang, Z.; Wei, Z.; Sun, G. Hybrid Method for Short-Term Photovoltaic Power Forecasting Based on Deep Convolutional Neural Network. IET Gener. Transm. Distrib. Inst. Eng. Technol. 2018, 12, 4557–4567. [Google Scholar] [CrossRef]
- Bayati, M.; Abedi, M.; Gharehpetian, G.B.; Farahmandrad, M. Short-term interaction between electric vehicles and microgrid in decentralized vehicle-to-grid control methods. Prot. Control Mod. Power Syst. 2019, 4, 42–52. [Google Scholar] [CrossRef]
- Zang, H.; Cheng, L.; Ding, T.; Cheung, K.W.; Wang, M.; Wei, Z.; Sun, G. Estimation and Validation of Daily Global Solar Radiation by Day of the Year-Based Models for Different Climates in China. Renew. Energy 2019, 135, 984–1003. [Google Scholar] [CrossRef]
- Hu, Z.; He, T.; Zeng, Y.; Luo, X.; Wang, J.; Huang, S.; Liang, J.; Sun, Q.; Xu, H.; Lin, B. Fast image recognition of transmission tower based on big data. Prot. Control Mod. Power Syst. 2018, 3, 149–158. [Google Scholar] [CrossRef]
- Aida, A.M.; Haidar, S.; Teymoor, G. K-NN Based Fault Detection and Classification Methods for Power Transmission Systems. Prot. Control Mod. Power Syst. 2017, 2, 359–369. [Google Scholar]
- Wang, J.; Yang, F.; Chen, T.; Shah, S.L. An Overview of Industrial Alarm Systems: Main Causes for Alarm Overloading, Research Status, and Open Problems. IEEE Trans. Autom. Sci. Eng. 2016, 13, 1045–1061. [Google Scholar] [CrossRef]
- Lee, H.J.; Park, D.Y.; Ahn, B.S.; Park, Y.M.; Park, J.K.; Venkata, S.S. A fuzzy expert system for integrated fault diagnosis. IEEE Trans. Power Deliv. 2000, 15, 833–838. [Google Scholar]
- Silva, V.N.; Linden, R.; Ribeiro, G.F. A Framework for Expert Systems Development Integrated to a SCADA/EMS Environment. In Proceedings of the International Conference on Intelligent Systems Applications to Power Systems, Niigata, Japan, 5–8 November 2007; pp. 1–4. [Google Scholar]
- Zhao, W.; Bai, X.; Wang, W.; Ding, J. A Novel Alarm Processing and Fault Diagnosis Expert System Based on BNF Rules. In Proceedings of the 2005 IEEE/PES Transmission & Distribution Conference & Exposition: Asia and Pacific, Dalian, China, 18 August 2005; pp. 1–6. [Google Scholar]
- Souza, J.C.; Filho, M.B.; Freund, R.S. A Hybrid Intelligent System for Alarm Processing in Power Distribution Substations. Int. J. Hybrid Intell. Syst. 2010, 7, 125–136. [Google Scholar] [CrossRef]
- Fritzen, P.C.; Cardoso, G.; Zauk, J.M.; De Morais, A.P.; Bezerra, U.H.; Beck, J.A. Integrated Use of Artificial Neural Networks and Genetic Algorithms for Problems of Alarm Processing and Fault Diagnosis in Power Systems. In Proceedings of the ACIIDS’10 Second International Conference on Intelligent Information & Database Systems: Part I, Hue City, Vietnam, 24–26 March 2010; pp. 370–379. [Google Scholar]
- Zhang, Y.; Zhang, Y.; Wen, F.; Chung, C.Y.; Tseng, C.L.; Zhang, X.; Zeng, F.; Yuan, Y. A Fuzzy Petri Net Based Approach for Fault Diagnosis in Power Systems Considering Temporal Constraints. Int. J. Electr. Power Energy Syst. 2016, 78, 215–224. [Google Scholar] [CrossRef]
- Zhang, Z.; Gao, Z.; Li, S.; Zhao, Y. The Method of Distribution Network Fault Location Based on Improved Dempster-Shafer Theory of Evidence. In Proceedings of the IEEE PES Asia-Pacific Power and Energy Engineering Conference (APPEEC), Bangalore, India, 8–10 November 2017; pp. 1–3. [Google Scholar]
- Li, W.; Chen, W.; Guo, C.; Zhu, B.; Xu, L. Fault Diagnosis Method for Power Distribution Systems Based on Multi-Source Information. In Proceedings of the IECON 2017—43rd Annual Conference of the IEEE Industrial Electronics Society, Beijing, China, 29 October 2017; pp. 1–4. [Google Scholar]
- Yang, X.; Sun, S.M. Construction of Regional Grid Intelligent Alarm System. In Proceedings of the International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), Offenburg, Germany, 20–23 October 2015; pp. 144–147. [Google Scholar]
- Liao, Z.W.; Liu, S. Substation Alarm Information Processing Based on Ontology Theory. In Proceedings of the 2015 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 2377–2382. [Google Scholar]
- State Grid Corporation of China. Information Specification for Supervision and Control of Substation Devices; State Grid Corporation of China: Beijing China, 2015. [Google Scholar]
- Qin, Q.; Lai, X.; Zou, J. Direct Multistep Wind Speed Forecasting Using LSTM Neural Network Combining EEMD and Fuzzy Entropy. Appl. Sci. 2019, 9, 126. [Google Scholar] [CrossRef]
- Williams, T.; Crawford, C. Probabilistic Load Flow Modeling Comparing Maximum Entropy and Gram-Charlier Probability Density Function Reconstructions. IEEE Trans. Power Syst. 2013, 28, 272–280. [Google Scholar] [CrossRef]
- Gao, B.; Wu, C.; Wu, Y.; Tang, Y. Expected Utility and Entropy-Based Decision-Making Model for Large Consumers in the Smart Grid. Entropy 2015, 17, 6560–6575. [Google Scholar] [CrossRef]
- Zheng, Y.; Sun, C.; Li, J.; Yang, Q.; Chen, W. Entropy-Based Bagging for Fault Prediction of Transformers Using Oil-Dissolved Gas Data. Energies 2011, 4, 1138–1147. [Google Scholar] [CrossRef]
- da Silva, A.M.L.; da Costa Castro, J.F.; Billinton, R. Probabilistic Assessment of Spinning Reserve via Cross-Entropy Method Considering Renewable Sources and Transmission Restrictions. IEEE Trans. Power Syst. 2017, 33, 4574–4582. [Google Scholar] [CrossRef]
- Bekenstein, J.D. Black Holes and Entropy. Phys. Rev. D Part. Fields 1973, 7, 2333–2346. [Google Scholar] [CrossRef]
- Mahbub, M.S.; Souza, P.D.; Williams, R. Understanding Environmental Changes Using Statistical Mechanics. Ann. Data Sci. 2019, 1–13. [Google Scholar] [CrossRef]
- Shannon, C.E. A Mathematical Theory of Communication. Bell Labs Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Barnum, H.; Barrett, J.; Clark, L.O.; Leifer, M.; Spekkens, R.; Stepanik, N.; Wilce, A.; Wilke, R. Entropy and Information Causality in General Probabilistic Theories. New J. Phys. 2010, 3, 033024. [Google Scholar] [CrossRef]
- Wu, J. Beauty of Mathematics; Posts and Telecom Press: Beijing, China, 2012; pp. 59–60. [Google Scholar]
- Zhang, Y.; Chung, C.Y.; Wen, F.; Zhong, J. An Analytic Model for Fault Diagnosis in Power Systems Utilizing Redundancy and Temporal Information of Alarm Messages. IEEE Trans. Power Syst. 2016, 31, 4877–4886. [Google Scholar] [CrossRef]
- Hongbin, S.; Boming, Z.; Lei, T.; Feng, G.; Chendong, W. A Novel Optimal Decision-Making Principle Based on Minimization of Information Loss as Applied to Power System. Autom. Electr. Power Syst. 2002, 26, 9–13. [Google Scholar]
- Luo, W.J.; Ma, H.F.; He, Q.; Shi, Z.Q. Leveraging Entropy and Relevance for Document Summarization. J. Chin. Inf. Process. 2011, 25, 9–11. [Google Scholar]
- Zhu, Z.; Liang, J.; Li, D.; Yu, H.; Liu, G. Hot Topic Detection Based on a Refined TF-IDF Algorithm. IEEE Access 2019, 7, 26996–27007. [Google Scholar] [CrossRef]
- Gan, L.; Xu, D.; Hu, L.; Wang, L. Economic Feasibility Analysis for Renewable Energy Project Using an Integrated TFN–AHP–DEA Approach on the Basis of Consumer Utility. Energies 2017, 10, 2089. [Google Scholar] [CrossRef]
- Chen, F.; Guo, S.; Gao, Y.; Yang, W.; Yang, Y.; Zhao, Z.; Ehsan, A. Evaluation Model of Demand-Side Energy Resources in Urban Power Grid Based on Geographic Information. Appl. Sci. 2018, 8, 1491. [Google Scholar] [CrossRef]
- Du, D.; Pang, T.H.; Wu, Y. Modern Comprehensive Evaluation Method and Case Selection; Tsinghua University Press: Beijing, China, 2008; pp. 14–15. [Google Scholar]
- Lin, B.S.; Wang, C.M.; Yu, C.N. The Establishment of Human-Computer Interaction Based on Word2Vec. In Proceedings of the 2017 IEEE International Conference on Mechatronics and Automation, Takamatsu, Japan, 6–9 August 2017; pp. 1698–1703. [Google Scholar]





| Entropy | Definition | |
|---|---|---|
| From the Perspective of Words | From the Perspective of Sentences | |
| Absolute alarm-message entropy | √ | |
| TF-IDF alarm-message entropy 1 | √ | √ |
| Relative alarm-message entropy | √ | |
| Self-information of monitoring alarm message | √ | |
| Meaning | |
|---|---|
| 1 | is as important as |
| 3 | is slightly more important than |
| 5 | is obviously more important than |
| 7 | is much more important than |
| 9 | is of the utmost importance to the target compared with |
| 2, 4, 6, 8 | Middle values between the adjacent values |
| Reciprocal | Importance of to the target compared with : |
| Entropy | Characteristic | Feature |
|---|---|---|
| Absolute alarm-message entropy | Concentrated | Favors long messages |
| Average Absolute alarm-message entropy | Concentrated | Favors short messages; realistic |
| TF-IDF alarm-message entropy | Dispersed | Favors long messages with low word frequency; partially separates the alarm messages |
| Average TF-IDF alarm-message entropy | Dispersed | Favors short messages with low word frequency; separates the alarm messages well; realistic |
| Relative alarm-message entropy | Dispersed, concentrated in the mid-to-low entropy area | Favors long messages with low word frequency |
| Average relative alarm-message entropy | Dispersed | Favors messages with low word frequency |
| Self-information of monitoring alarm message | Concentrated in high-Entropy area | Favors messages with low sentence frequency |
| Index | |||||||
|---|---|---|---|---|---|---|---|
| Weight | 0.3504 | 0.2375 | 0.1590 | 0.1056 | 0.0696 | 0.0462 | 0.0318 |
| Grade | High | Relatively High | Medium | Relatively Low | Low |
|---|---|---|---|---|---|
| Probability (%) | 99.1 | 98.09 | 95.59 | 97.95 | 98.82 |
| Grade | Typical Alarm Message |
|---|---|
| High | Forbidden reclosure action caused by 2Y26PRC31A02DL low pressure in XX substation Power protection exit in 756 line of XX substation B-phase closing of 220 kV Xijin 4Y22 circuit breaker of XX substation |
| Relatively high | 1n GOOSE chain rupture of 102B smart terminal of XX substation AC air switch jump-off action of 172 of XX substation High-temperature alarm of the body winding of #2 main transformer in XX substation |
| Medium | Overloaded #2 main transformer protection blocked on-load voltage Regulation in XX substation 290 control circuit broken of XX substation Alarm of 710 Integrated Smart Terminal in XX substation |
| Relatively low | No energy stored in the spring 1R1of XX substation Unqualified bus voltage in 10 kV line in XX substation 1R2 circuit breaker opening of #2 capacitor of XX substation |
| Low | On-load voltage regulation on-off operation of #1 main transformer of XX substation Abnormal voltage of #2 AC bus of the transformer in XX substation 142 earthing of XX substation in XX City |
| Classification | Grade | ||||
|---|---|---|---|---|---|
| High | Relatively High | Medium | Relatively Low | Low | |
| Alarm (accident, abnormal, off-limit, displacement) | High risk | Medium risk | |||
| Notification (notification) | Medium risk | Low risk | |||
| Severity | Way of Alarm | Processing |
|---|---|---|
| High risk | Voice message, ring | Immediate processing (within 1 h) |
| Medium risk | Ring | Timely processing (within 1–4 h) |
| Low risk | Delay or no alarm | Processing in 4 h or more |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, G.; Ding, X.; Wei, Z.; Shen, P.; Zhao, Y.; Huang, Q.; Zhang, L.; Zang, H. Intelligent Classification Method for Grid-Monitoring Alarm Messages Based on Information Theory. Energies 2019, 12, 2814. https://doi.org/10.3390/en12142814
Sun G, Ding X, Wei Z, Shen P, Zhao Y, Huang Q, Zhang L, Zang H. Intelligent Classification Method for Grid-Monitoring Alarm Messages Based on Information Theory. Energies. 2019; 12(14):2814. https://doi.org/10.3390/en12142814
Chicago/Turabian StyleSun, Guoqiang, Xiaoliu Ding, Zhinong Wei, Peifeng Shen, Yang Zhao, Qiugen Huang, Liang Zhang, and Haixiang Zang. 2019. "Intelligent Classification Method for Grid-Monitoring Alarm Messages Based on Information Theory" Energies 12, no. 14: 2814. https://doi.org/10.3390/en12142814
APA StyleSun, G., Ding, X., Wei, Z., Shen, P., Zhao, Y., Huang, Q., Zhang, L., & Zang, H. (2019). Intelligent Classification Method for Grid-Monitoring Alarm Messages Based on Information Theory. Energies, 12(14), 2814. https://doi.org/10.3390/en12142814






