MACsec Layer 2 Security in HSR Rings in Substation Automation Systems
Abstract
:1. Introduction
2. Background Information
2.1. IEC 61850 Security Considerations
- Attacks on IEC 61850
- –
- –
- Password Cracking Attacks: the purpose of this attack is for the attacker to gain unauthorized access to a system or device.
- –
- Packet Sniffing Attacks: when the packet sniffing attack is launched within the IEC 61850 substation network, the attacker will gain the ability to steal transmitted data and perform certain attacks such as the man-in-the middle attack.
- Attacks on GOOSE and Sample Values (SV)
- –
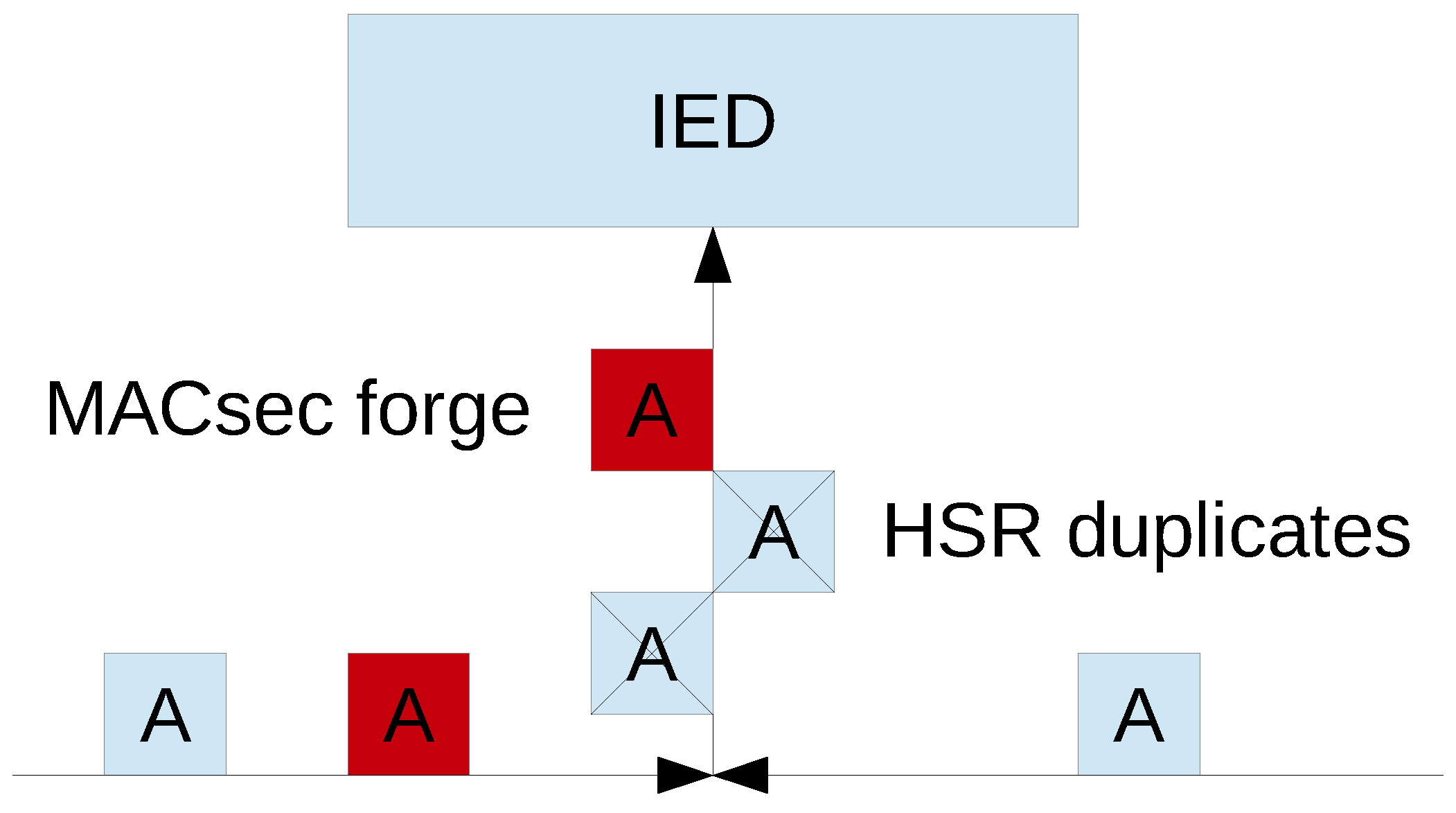
- GOOSE and SV Modification Attack: In [20], an attack is proposed. In this attack, the GOOSE control message packet is captured and then modified with a message that will allow the attacker to gain control and operate circuit breakers in a substation. For an SV packet, an attacker could generate a fabricated analog value, and this value is sent to a control center in a substation that leads to undesirable operations. This attack will enable the attacker to gain control of IEDs and cause unplanned power outage or even damage the substation field devices.
- –
- GOOSE and SV DoS Attacks: a DoS attack will cause an IED to stop responding to legitimate requests made by other IEDs. This will prevent the IED from performing its intended function and may lead to many other consequences such as power failure and equipment damage. A DoS attack can be conducted in several ways. The simplest way is to just send a large number of GOOSE or SV messages to an IED so that it becomes overwhelmed and no longer able to respond to legitimate requests.
- –
- GOOSE and SV Replay Attack: in a reply attack, the GOOSE messages used to send this tripping signal is captured and kept by the attacker. The attacker would then send the exact same message to cause the circuit breaker to trip when it is not supposed to. This will cause an unintentional power outage. For SV message replay attack, the attacker can capture an SV packet containing a certain power and voltage values, and then replay this same SV packet to other IEDs in the substation multiple times. SV packets with the same power and voltage values circulating inside the substation can lead to undesirable operation.
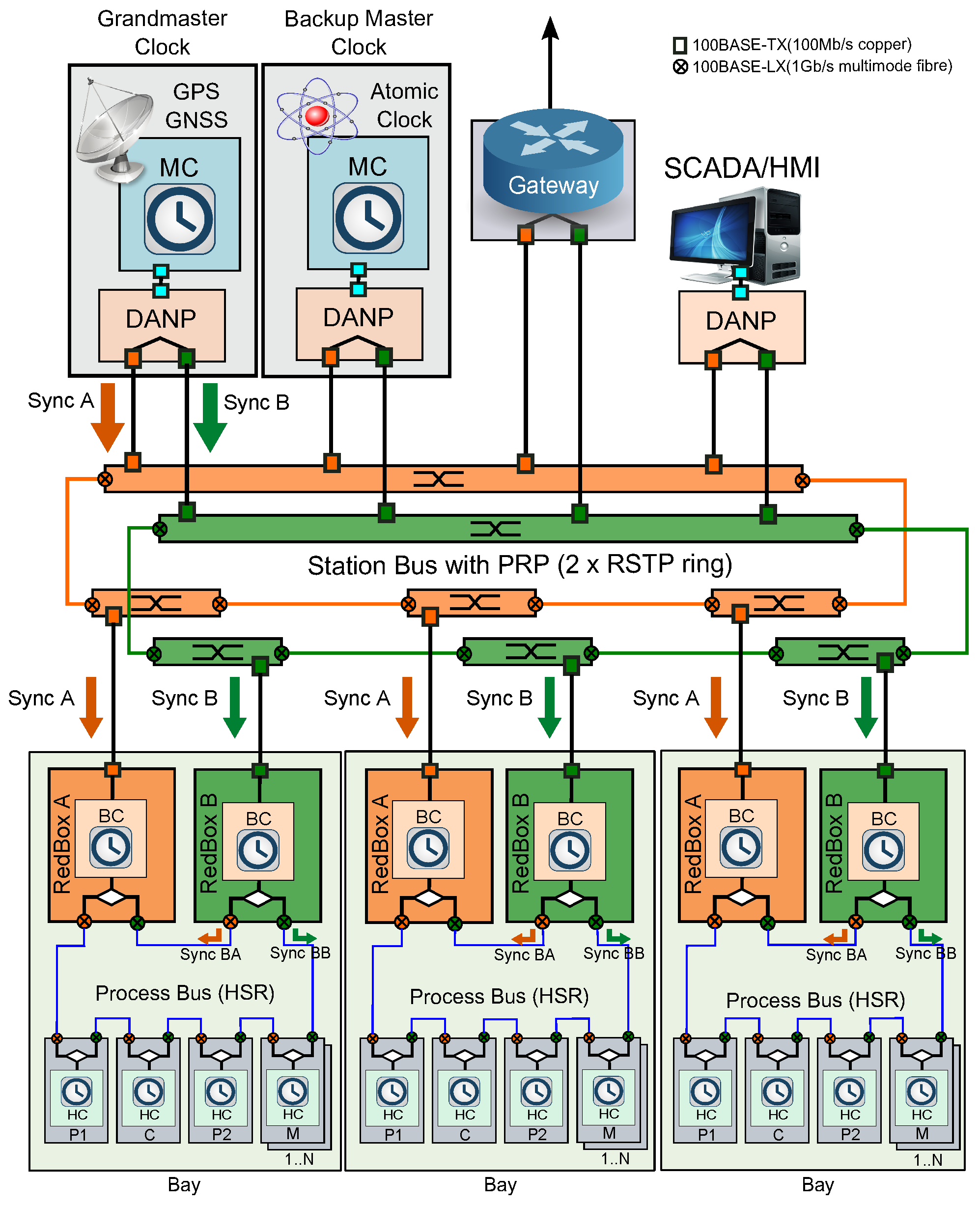
2.2. High-Availability Seamless Redundancy
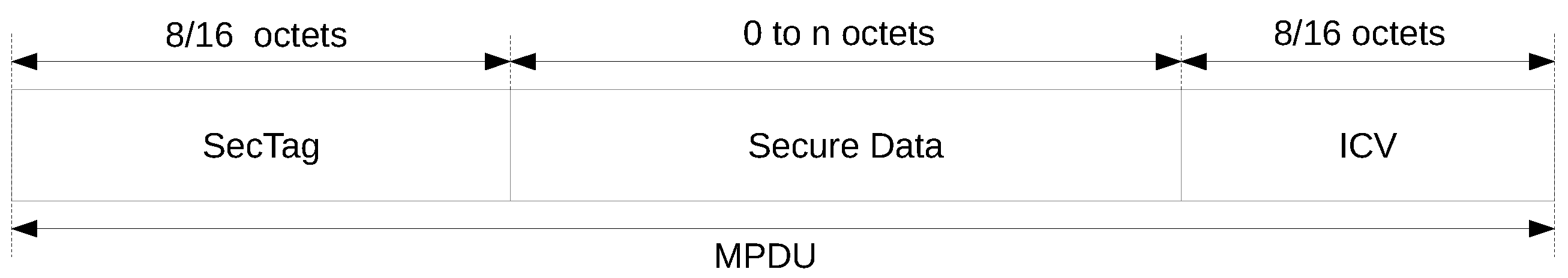
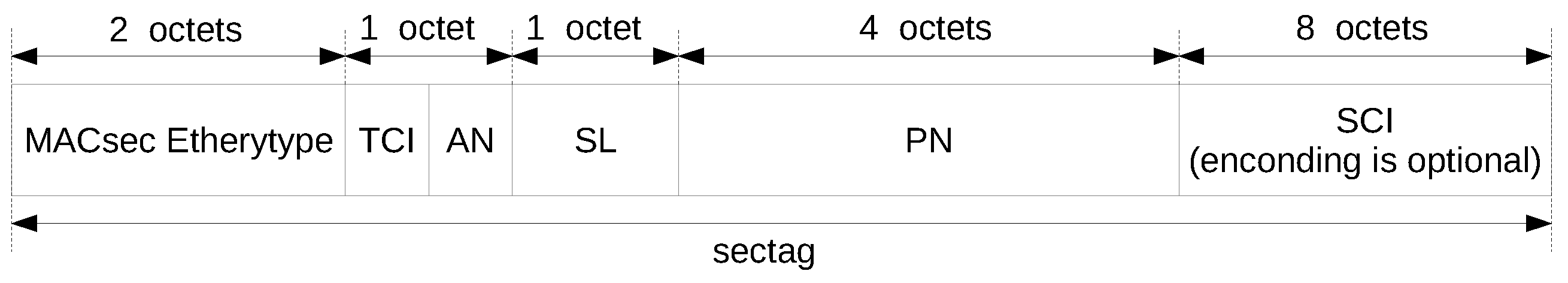
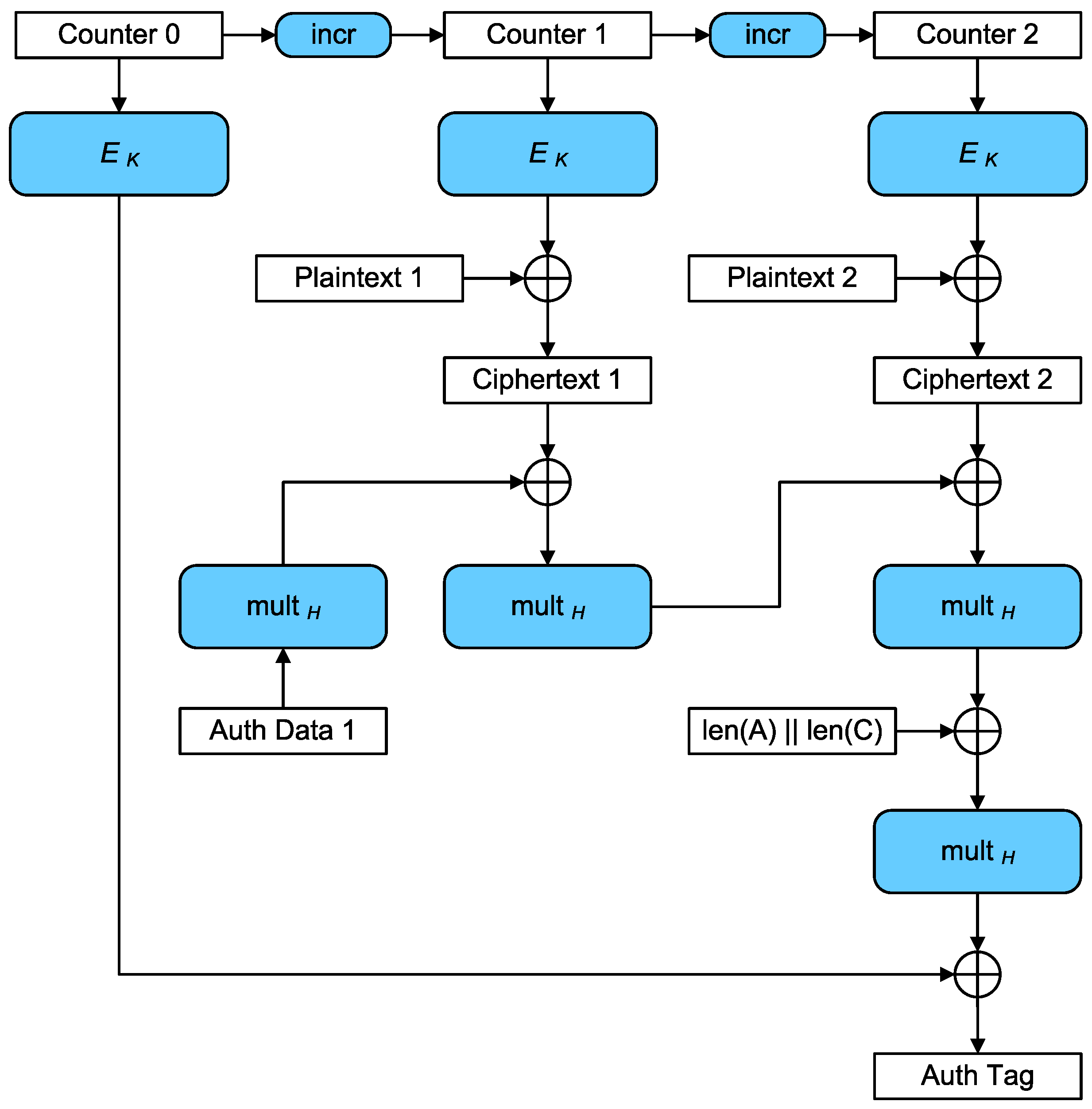
2.3. MACsec
- MACsec frame format;
- Secure Connectivity Associations that represent groups of stations connected via unidirectional Secure Channels;
- Two ciphers that provide encryption and authentication at the same time: GCM-AES128 and GCM-AES-256 [26].
- TCI: Tag Control Information. This field facilitates version numbering, determine whether confidentiality or integrity alone are in use, option inclusion, etc.
- AN: Association Number. It identifies up to four different secure associations within the context of a secure channel.
- SL: Short Length. This integer encodes the number of octets in the secure data field if that number is less than 48.
- PN: Packet Number. This field provides a unique initialization vector for all data transmitted using the same secure association, and, at the same time, it supports replay protection.
- SCI: Optionally encoded Secure Channel Identifier. This facilitates the identifications of the secure channel when there are three or more peers.
3. Communication Protection Alternatives
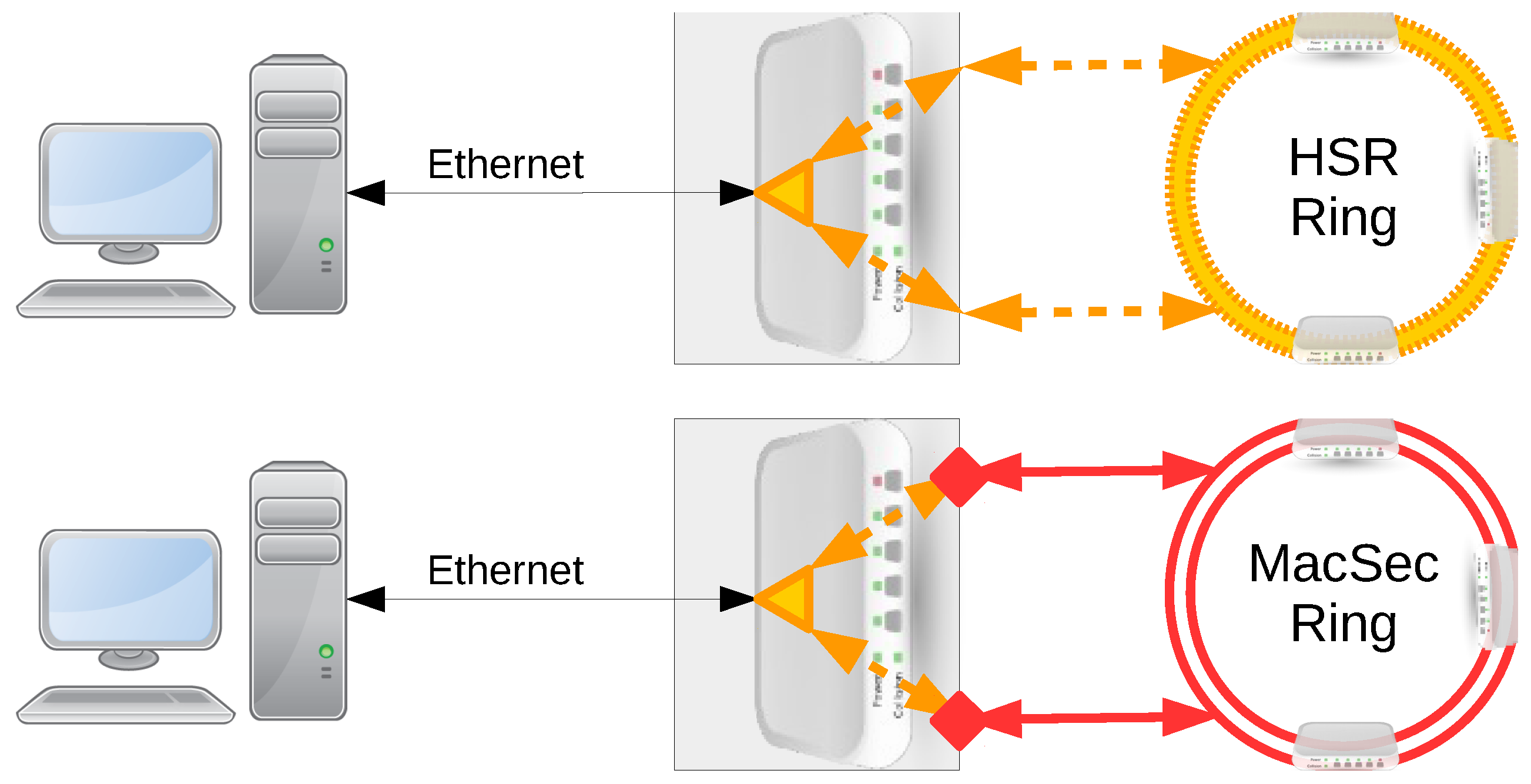
3.1. HSR in MACsec
3.2. MACsec in HSR
3.3. MACsec into Protected HSR
4. Impact of Protection Schemes in Communications
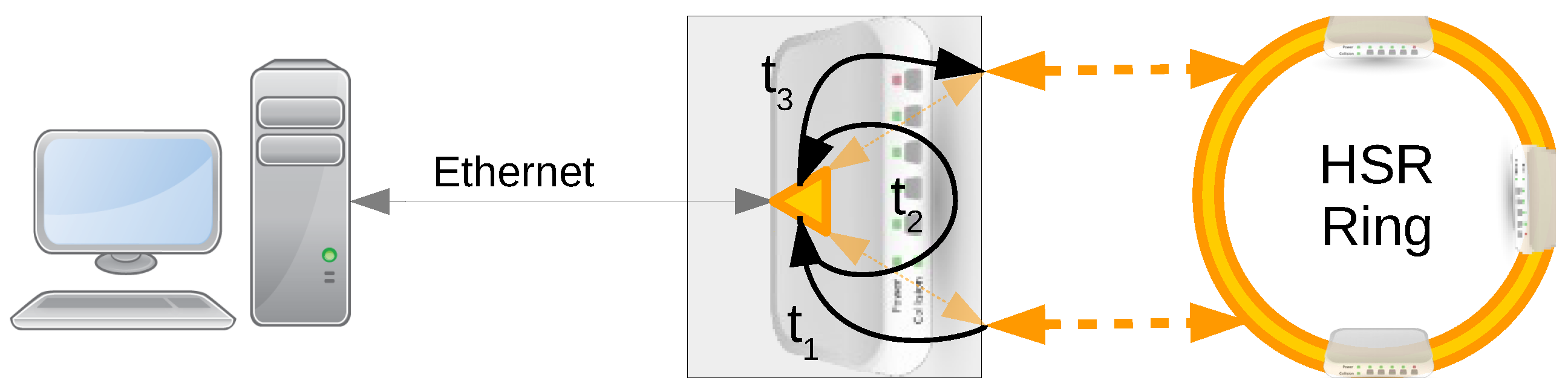
4.1. Latency
- depends on the operation mode used, for standard HSR without MACsec:
- –
- Store-and-Forward (SF): the whole frame is received before switching. This depends on the size of the frame: from 70 octets up to 1528 octets plus preamble and start of frame (P&SoF). It results in a time range from 6.24 to 122.88 .
- –
- Cut-Through (CT): switching starts after receiving P&SoF, addresses and HSR Tag to minimize the delay added in the nodes. The theoretical value is 2.08 for the regular HSR frame.
- is the time taken to decide whether to forward/receive/discard a frame, and it depends fundamentally on the time needed to check whether the frame has arrived before or not.
- is the time a frame has to wait to be sent because another frame is being sent. We have tested three different scenarios:
- –
- : no waiting time. In other words, no frame is being sent. This is the best case scenario. In the case of synchronized traffic, this would be the normal situation.
- –
- 12.8 : in an IEC 61850 process bus network, most traffic is of sample value type. These frames do not have a constant length, but 160 octets (8 octets P&SoF + 12 octets interframe gap + 140 SV frame) is quite common, and this frame would allow to send a single value.
- –
- 123.84 : the worst case scenario appears when the longest frame (1528 octets + 8 octets P&SoF + 12 octets interframe gap) is being transmitted and a new frame arrives from a different port.
- MACsec inside HSR or MACsec into protected HSR: the standard HSR times apply since HSR tag is in the same position and is not encrypted: 2.08 26 octets: 8 octets P&SoF + 6 destination MAC address + 6 source MAC address + 6 HSR tag.
- HSR inside MACsec: the HSR tag is buried inside the MACsec payload, depending on whether the payload is encrypted or only signed for authentication:
- –
- Signed: 3.36 42 octets: 8 octets P&SoF + 6 destination MAC address + 6 source MAC address + 16 MACsec header + 6 HSR tag.
- –
- Encrypted: 4.16 52 octets: 8 octets P&SoF + 6 destination MAC address + 6 source MAC address + 16 MACsec header + 16 MACsec decryption block, assuming a heavily pipelined decryption algorithm that results in negligible decryption time.
4.2. Throughput
5. Hardware Implementation
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- International Electrotechnical Commission. IEC 61850: Power Utility Automation; International Electrotechnical Commission: Geneva, Switzerland, 2016. [Google Scholar]
- Skeie, T.; Johannessen, S.; Brunner, C. Ethernet in substation automation. IEEE Control Syst. 2002, 22, 43–51. [Google Scholar] [CrossRef]
- Cleveland, F. IEC TC57 Security Standards for the Power System’s Information Infrastructure—Beyond Simple Encryption. In Proceedings of the 2005/2006 IEEE PES Transmission and Distribution Conference and Exhibition, Dallas, TX, USA, 21–24 May 2006; pp. 1079–1087.
- Ray, P.; Harnoor, R.; Hentea, M. Smart power grid security: A unified risk management approach. In Proceedings of the 2010 IEEE International Carnahan Conference on Security Technology (ICCST), San Jose, CA, USA, 5–8 October 2010; pp. 276–285.
- Wang, Y.; Ruan, D.; Gu, D.; Gao, J.; Liu, D.; Xu, J.; Chen, F.; Dai, F.; Yang, J. Analysis of Smart Grid security standards. In Proceedings of the 2011 IEEE International Conference on Computer Science and Automation Engineering (CSAE), Shanghai, China, 10–12 June 2011; Volume 4, pp. 697–701.
- Kanabar, M.; Voloh, I.; McGinn, D. Reviewing Smart Grid Standards for Protection, Control, and Monitoring Applications. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies Conference, Washington, DC, USA, 16–20 January 2012; pp. 1–8.
- Chen, T.; Abu-Nimeh, S. Lessons from Stuxnet. Computer 2011, 44, 91–93. [Google Scholar] [CrossRef]
- Langner, R. Stuxnet: Dissecting a Cyberwarfare Weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- International Electrotechnical Commission. IEC 62351 Power Systems Management and Associated Information Exchange—Data and Communications Security; International Electrotechnical Commission: Geneva, Switzerland, 2007. [Google Scholar]
- Krawczyk, H.; Bellare, M.; Canetti, R. HMAC: Keyed-Hashing for Message Authentication (RFC 2104). Frebruary 1997. Available online: https://www.ietf.org/rfc/rfc2104.txt (accessed on 24 January 2017).
- Jonsson, J.; Kaliski, B. Public-Key Cryptography Standards (PKCS) 1: RSA Cryptography Specifications. RFC 3447. February 2003. Available online: https://tools.ietf.org/html/rfc3447 (accessed on 24 January 2017).
- Eastlake, D.E., 3rd; Jones, P.E. Secure Hash Algorithm 1 (SHA1), RFC 3174. September 2001. Available online: https://tools.ietf.org/html/rfc3174 (accessed on 24 January 2017).
- Moreira, N.; Astarloa, A.; Kretzschmar, U. SHA-3 Based Message Authentication Codes to Secure IEEE 1588 Synchronization Systems. In Proceedings of the IEEE Conference on Industrial Electronics Society (IECON), Vienna, Austria, 10–13 November 2013; pp. 2323–2328.
- Treytl, A.; Gaderer, G.; Loschmidt, P.; Kerö, N. Investigations on Security Aspects in Clock Synchronized Industrial Ethernet. In Proceedings of the Precise Time and Time Interval Systems and Applications Meeting, Reston, VA, USA, 7–9 December 2006; pp. 232–240.
- Fuloria, S.; Anderson, R.; McGrath, K.; Hansen, K.; Alvarez, F. The Protection of Substation Communications. In Proceedings of the SCADA Security Scientific Symposium, Miami, FL, USA, 10–12 January 2010.
- IEEE 802.1AE-2006 Media Access Control (MAC) Security; IEEE Standards Department: Piscataway, NJ, USA, 2006.
- Rashid, M.T.A.; Yussof, S.; Yusoff, Y.; Ismail, R. A review of security attacks on IEC 61850 substation automation system network. In Proceedings of the 6th International Conference on Information Technology and Multimedia, Putrajaya, Malaysia, 18–20 November 2014; pp. 5–10.
- Premaratne, U.K.; Samarabandu, J.; Sidhu, T.S.; Beresh, R.; Tan, J.C. An Intrusion Detection System for IEC61850 Automated Substations. IEEE Trans. Power Deliv. 2010, 25, 2376–2383. [Google Scholar] [CrossRef]
- Premaratne, U.; Samarabandu, J.; Sidhu, T.; Beresh, R.; Tan, J.C. Security Analysis and Auditing of IEC 61850-Based Automated Substations. IEEE Trans. Power Deliv. 2010, 25, 2346–2355. [Google Scholar] [CrossRef]
- Hong, J.; Liu, C.C.; Govindarasu, M. Integrated Anomaly Detection for Cyber Security of the Substations. IEEE Trans. Smart Grid 2014, 5, 1643–1653. [Google Scholar] [CrossRef]
- Schlegel, R.; Obermeier, S.; Schneider, J. Assessing the Security of IEC 62351. In Proceedings of the 3rd International Symposium for ICS & SCADA Cyber Security Research 2015 (ICS-CSR 2015), Ingolstadt, Germany, 17–18 September 2015.
- Hohlbaum, F.; Braendle, M.; Alvarez, F. Cyber Security Practical Considerations for Implementing IEC 62351; Technical Report; ABB: Zürich, Switzerland, 2010. [Google Scholar]
- International Electrotechnical Commission. IEC 61850-90-4 Ed.01: Communication Networks and Systems for Power Utility Automation; International Electrotechnical Commission: Geneva, Switzerland, 2013. [Google Scholar]
- International Electrotechnical Commission. IEC 62439-3 Ed.02: Industrial Communications Networks—High Availability Automation Networks; International Electrotechnical Commission: Geneva, Switzerland.
- Felser, M. Real-Time Ethernet—Industry Prospective. Proc. IEEE 2005, 93, 1118–1129. [Google Scholar] [CrossRef]
- McGrew, D.; Viega, J. The Galois/Counter Mode of Operation (GCM), 2004. Available online: http://csrc.nist.gov/groups/ST/toolkit/BCM/documents/proposedmodes/gcm/gcm-spec.pdf (accessed on 24 January 2017).
- Identity-Based Networking Services: MAC Security; White Paper; Cisco: San Jose, CA, USA, 2011.
- McGrew, D.A.; Viega, J. The Security and Performance of the Galois/Counter Mode (GCM) of Operation. In INDOCRYPT, Volume 3348 of LNCS; Springer: Berlin, Germany, 2004; pp. 343–355. [Google Scholar]
- IEEE Standard for Local and Metropolitan Area Networks—Port-Based Network Access Control; IEEE Std 802.1X-2010 (Revision of IEEE Std 802.1X-2004); IEEE Standards Association: Piscataway, NJ, USA, 2010; pp. 1–205.
- Vitesse. Quad Port Dual Media QSGMII/SGMII GbE PHY with Intellisec and VeriTime. Available online: http://www.microsemi.com/products/ethernet-solutions/ethernet-phys/gigabit-ethernet-phys/vsc8584-quad-port-dual-media-qsgmii-sgmii-gbe-phy-with-intellisec-and-veritime (accessed on 24 January 2017).
- Abdolkhalig, A.; Zivanovic, R. Simulation and testing of the over-current protection system based on IEC 61850 Process-Buses and dynamic estimator. Sustain. Energy Grids Netw. 2015, 2, 41–50. [Google Scholar] [CrossRef]
- International Electrotechnical Commission. IEC 61850-5 Ed. 2: Communication Networks and Systems for Power Utility Automation—Part 5: Communication Requirements for Functions and Device7 Models; International Electrotechnical Commission: Geneva, Switzerland, 2013. [Google Scholar]
- IEEE 1588-2008—Precision Clock Synchronization Protocol for Networked Measurement and Control Systems; IEEE Standards Association: Piscataway, NJ, USA.
- Intel. Intel 82576EB Gigabit Ethernet Controller. Available online: http://ark.intel.com/products/series/32261/Intel-82576-Gigabit-Ethernet-Controller (accessed on 24 January 2017).
- Broadcom. Octal-Port 10/100/1000BASE-T 40 nm Transceiver. Available online: https://www.broadcom.com/products/ethernet-connectivity/copper-phy/gigabit-phy/bcm54380 (accessed on 24 January 2017).
- Inc, C. AES-GCM Authenticated Encrypt/Decrypt Core. Available online: https://www.design-reuse.com/sip/?q=gcm+aes+authenticated+encrypt+decrypt+core (accessed on 24 January 2017).
- Heliontech. AES-GCM Core. Available online: http://www.latticesemi.com/en/Products/DesignSoftwareAndIP/IntellectualProperty/IPCore/HelionTechCores/AESGCMCore.aspx (accessed on 24 January 2017).
- Scalable AES-GCM/GMAC/CTR IP Core, BA415. Available online: http://www.barco-silex.com/products/security/high-speed-aes/ (accessed on 24 January 2017).
- Algotronix. Multiple SecY IEEE 802.1ae MACSEC IP Core for 1Gbit Ethernet. Available online: https://www.xilinx.com/products/intellectual-property/1-4pilr2.html (accessed on 24 January 2017).







| Device | 1024 RSA Performance |
|---|---|
| SafeXcel-1741 | 119 op/sec sign, 1176 op/sec verify |
| SafeXcel-1841 | 1220 op/sec sign, 3790 op/sec verify |
| BCM5860 | 4600 op/sec |
| BCM5861 | 7000 op/sec |
| BCM5862 | 15,224 op/sec |
| MACsec in HSR | 289 (2885) | 41 (404) | 5 (48) |
| Signed HSR in MACsec | 179 (1786) | 38 (372) | 5 (48) |
| Encrypted HSR in MACsec | 145 (1443) | 36 (354) | 5 (47) |
| IEC 61850 | HSR | HSR + MACsec | |
|---|---|---|---|
| FEth | 9 | 9 | 7 |
| GEth | 97 | 94 | 78 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lázaro, J.; Astarloa, A.; Araujo, J.A.; Moreira, N.; Bidarte, U. MACsec Layer 2 Security in HSR Rings in Substation Automation Systems. Energies 2017, 10, 162. https://doi.org/10.3390/en10020162
Lázaro J, Astarloa A, Araujo JA, Moreira N, Bidarte U. MACsec Layer 2 Security in HSR Rings in Substation Automation Systems. Energies. 2017; 10(2):162. https://doi.org/10.3390/en10020162
Chicago/Turabian StyleLázaro, Jesús, Armando Astarloa, José Angel Araujo, Naiara Moreira, and Unai Bidarte. 2017. "MACsec Layer 2 Security in HSR Rings in Substation Automation Systems" Energies 10, no. 2: 162. https://doi.org/10.3390/en10020162
APA StyleLázaro, J., Astarloa, A., Araujo, J. A., Moreira, N., & Bidarte, U. (2017). MACsec Layer 2 Security in HSR Rings in Substation Automation Systems. Energies, 10(2), 162. https://doi.org/10.3390/en10020162





