Empowered to Detect: How Vigilance and Financial Literacy Shield Us from the Rising Tide of Financial Frauds
Abstract
1. Introduction
2. Literature Review
2.1. Financial Fraud and Scams
2.2. Hypotheses Development
3. Methodology
3.1. Instrument Measurements
3.2. Sample Selection and Data Gathering
4. Results and Discussion
4.1. Validity and Reliability of the Model
4.2. Composite Measurement Model
4.3. Structural Model Evaluation
4.4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Abinaya, R., E., B. N., & Naveen, P. (2020, July 23–24). Spam detection on social media platforms. 2020 7th International Conference on Smart Structures and Systems (ICSSS) (pp. 1–3), Chennai, India. [Google Scholar] [CrossRef]
- Aguirre-Urreta, M. I., & Rönkkö, M. (2018). Statistical inference with PLSc using bootstrap confidence intervals. MIS Quarterly, 42(3), 1001–A10. Available online: https://www.jstor.org/stable/26635063 (accessed on 22 October 2024). [CrossRef]
- Aigbavboa, C. O. (2013). An integrated beneficiary centred satisfaction model for publicly funded housing schemes in South Africa. University of Johannesburg (South Africa). [Google Scholar]
- Akter, S., D’Ambra, J., & Ray, P. (2011, August 4–8). An evaluation of PLS based complex models: The roles of power analysis, predictive relevance and GoF index. 17th Americas Conference on Information Systems 2011, AMCIS 2011 (Vol. 2, pp. 1313–1319), Detroit, MI, USA. [Google Scholar]
- Ali, F., Rasoolimanesh, S. M., Sarstedt, M., Ringle, C. M., & Ryu, K. (2018). An assessment of the use of partial least squares structural equation modeling (PLS-SEM) in hospitality research. International Journal of Contemporary Hospitality Management, 30(1), 514–538. [Google Scholar] [CrossRef]
- Anderson, K. B. (2019). Mass-market consumer fraud: In the united states: A 2017 update (pp. 429–454). Federal Trade Commission, Staff Repo. [Google Scholar]
- Anderson, R., Barton, C., Böhme, R., Clayton, R., Van Eeten, M. J. G., Levi, M., Moore, T., & Savage, S. (2013). Measuring the cost of cybercrime. In The economics of information security and privacy (pp. 265–300). Springer. [Google Scholar]
- Atkinson, A., & Messy, F.-A. (2012). Measuring financial literacy: Results of the OECD/international network on financial education (INFE) pilot study. Available online: https://www.oecd-ilibrary.org/measuring-financial-literacy_5k9csfs90fr4.pdf (accessed on 11 December 2024).
- Bagozzi, R. P., & Yi, Y. (2012). Specification, evaluation, and interpretation of structural equation models. Journal of the Academy of Marketing Science, 40(1), 8–34. [Google Scholar] [CrossRef]
- Bai, F., & Chen, X. (2013). Analysis on the new types and countermeasures of credit card fraud in mainland China. Journal of Financial Crime, 20(3), 267–271. [Google Scholar] [CrossRef]
- Barthel, A.-C., & Lei, S. (2021). Investment in financial literacy and financial advice-seeking: Substitutes or complements? The Quarterly Review of Economics and Finance, 81, 385–396. [Google Scholar] [CrossRef]
- Beach, S. R., Schulz, R., & Sneed, R. (2016). Associations between social support, social networks, and financial exploitation in older adults. Journal of Applied Gerontology, 37(8), 990–1011. [Google Scholar] [CrossRef] [PubMed]
- Beals, M., DeLiema, M., & Deevy, M. (2015). Framework for a taxonomy of fraud. Financial Fraud Research Center. [Google Scholar]
- Bijwaard, D. (2020). Consumer scams and fraud in Europe: Survey report 2020, European institute for gender equality. Lithuania. Available online: https://coilink.org/20.500.12592/96n468 (accessed on 28 September 2024).
- Black, W. K. (2006). Book review: Control fraud theory v. the protocols. Crime, Law and Social Change, 45(3), 241–258. [Google Scholar] [CrossRef]
- Blanton, K. (2012). The rise of financial fraud: Scams never change but disguises do. Center for Retirement Research Working Paper. [Google Scholar]
- Bokolo, B. G., & Liu, Q. (2024). Advanced algorithmic approaches for scam profile detection on instagram. Electronics, 13(8), 1571. [Google Scholar] [CrossRef]
- Boshmaf, Y., Muslukhov, I., Beznosov, K., & Ripeanu, M. (2011, December 5–9). The socialbot network: When bots socialize for fame and money. 27th Annual Computer Security Applications Conference (pp. 93–102), Orlando, FL, USA. [Google Scholar] [CrossRef]
- Brenner, L., Meyll, T., Stolper, O., & Walter, A. (2020). Consumer fraud victimization and financial well-being. Journal of Economic Psychology, 76, 102243. [Google Scholar] [CrossRef]
- Brody, R. G., Mulig, E., & Kimball, V. (2007). Phishing, pharming and identity theft. Academy of Accounting and Financial Studies Journal, 11(3), 43–56. [Google Scholar]
- Button, M., & Cross, C. (2017). Cyber frauds, scams and their victims. Routledge. [Google Scholar]
- Carswell, A. T., & Bachtel, D. C. (2009). Mortgage fraud: A risk factor analysis of affected communities. Crime, Law and Social Change, 52(4), 347–364. [Google Scholar] [CrossRef]
- Cheah, J.-H., Sarstedt, M., Ringle, C. M., Ramayah, T., & Ting, H. (2018). Convergent validity assessment of formatively measured constructs in PLS-SEM. International Journal of Contemporary Hospitality Management, 30(11), 3192–3210. [Google Scholar] [CrossRef]
- Chin, W. W. (1998). Commentary: Issues and opinion on structural equation modeling. MIS Quarterly, 22(1), vii–xvi. Available online: http://www.jstor.org/stable/249674 (accessed on 11 January 2025).
- Chryssikos, D., Passas, N., & Ram, C. D. (2008). The evolving challenge of identity-related crime: Addressing fraud and the criminal misuse and falsification of identity. International Scientific and Professional Advisory Council of the United Nations Crime Prevention and Criminal Justice Programme (ISPAC), Milan. [Google Scholar]
- Cole, T. (2023). How are financial institutions enabling online fraud? A developmental online financial fraud policy review. Journal of Financial Crime, 30(6), 1458–1473. [Google Scholar] [CrossRef]
- Cossa, A., Madaleno, M., & Mota, J. (2022). Financial literacy environment scan in Mozambique. Asia Pacific Management Review, 27(4), 229–244. [Google Scholar] [CrossRef]
- Czechowska, I. D., & Waliszewski, K. (2018). Mis-selling in finance as an effect of excessive concentration on sales. Przedsiębiorczość i Zarządzanie, 19(1), 1. [Google Scholar]
- Davies, D. R., & Parasuraman, R. (1977). Cortical evoked potentials and vigilance: A decision theory analysis BT—Vigilance: Theory, operational performance, and physiological correlates (R. R. Mackie, Ed.; pp. 285–306). Springer US. [Google Scholar] [CrossRef]
- Deevy, M., Lucich, S., & Beals, M. (2012). Scams, schemes & swindles. Financial Fraud Research Center. [Google Scholar]
- DeLiema, M., Deevy, M., Lusardi, A., & Mitchell, O. S. (2018). Exploring the risks and consequences of elder fraud victimization: Evidence from the health and retirement study. Pension Research Council Working Paper. The Wharton School, University of Pennsylvania. Available online: https://repository.upenn.edu/entities/publication/1e040594-cd3b-4193-93c5-e3af838c5688 (accessed on 10 August 2024).
- DeLiema, M., Deevy, M., Lusardi, A., & Mitchell, O. S. (2020). Financial fraud among older americans: Evidence and implications. The Journals of Gerontology: Series B, 75(4), 861–868. [Google Scholar] [CrossRef] [PubMed]
- DeLiema, M., Fletcher, E., Kieffer, C. N., Mottola, G. R., Pessanha, R., & Trumpwer, M. (2019, September). Exposed to scams: What separates victims from non-victims? FINRA investor education foundation, BBB institute for marketplace trust, and stanford center on longevity. Available online: https://www.finrafoundation.org/sites/finrafoundation/files/exposed-to-scams-what-separates-victims-from-non-victims_0_0.pdf (accessed on 1 September 2024).
- Drew, J. M., & Cross, C. (2013). Fraud and its PREY: Conceptualising social engineering tactics and its impact on financial literacy outcomes. Journal of Financial Services Marketing, 18(3), 188–198. [Google Scholar] [CrossRef]
- Dwivedi, Y. K., Kelly, G., Janssen, M., Rana, N. P., Slade, E. L., & Clement, M. (2018). Social media: The good, the bad, and the ugly. Information Systems Frontiers, 20(3), 419–423. [Google Scholar] [CrossRef]
- Engels, C., Kumar, K., & Philip, D. (2020). Financial literacy and fraud detection. The European Journal of Finance, 26(4–5), 420–442. [Google Scholar] [CrossRef]
- Ericson, R. V., & Doyle, A. (2006). The institutionalization of deceptive sales in life insurance: Five sources of moral risk. The British Journal of Criminology, 46(6), 993–1010. [Google Scholar] [CrossRef]
- Fan, J. X., & Yu, Z. (2022). Prevalence and risk factors of consumer financial fraud in China. Journal of Family and Economic Issues, 43(2), 384–396. [Google Scholar] [CrossRef]
- Fisher, J. (2014). Risk, recklessness and policing the financial markets. In Fighting financial crime in the global economic crisis (pp. 7–28). Routledge. [Google Scholar]
- Fletcher, N. (2007). Challenges for regulating financial fraud in cyberspace. Journal of Financial Crime, 14(2), 190–207. [Google Scholar] [CrossRef]
- Frankel, T. (2012). The ponzi scheme puzzle: A history and analysis of con artists and victims. Oxford University Press. [Google Scholar]
- Friedrichs, D. O. (2010). Trusted criminals: White collar crime in contemporary society. Cengage Learning. ISBN 0495600822, 9780495600824. [Google Scholar]
- Garg, V., & Niliadeh, S. (2013, May 23–24). Craigslist scams and community composition: Investigating online fraud victimization. Proceedings—IEEE CS Security and Privacy Workshops, SPW 2013 (pp. 123–126), San Francisco, CA, USA. [Google Scholar] [CrossRef]
- Geis, G. (2011). White-collar and corporate crime: A documentary and reference guide. Bloomsbury Publishing USA. [Google Scholar]
- Gordon, S., & Ford, R. (2006). On the definition and classification of cybercrime. Journal in Computer Virology, 2(1), 13–20. [Google Scholar] [CrossRef]
- Green, D. M., & Swets, J. A. (1966). Signal detection theory and psychophysics (Vol. 1). Wiley New York. [Google Scholar]
- Guiso, L., Sapienza, P., & Zingales, L. (2008). Trusting the stock market. The Journal of Finance, 63(6), 2557–2600. [Google Scholar] [CrossRef]
- Hair, J. F., Jr., Hult, G. T. M., Ringle, C. M., & Sarstedt, M. (2021a). A primer on partial least squares structural equation modeling (PLS-SEM). Sage Publications. [Google Scholar]
- Hair, J. F., Jr., Hult, G. T. M., Ringle, C. M., Sarstedt, M., Danks, N. P., & Ray, S. (2021b). Partial least squares structural equation modeling (PLS-SEM) using R: A workbook. Springer Nature. [Google Scholar]
- Hair, J. F., Jr., Sarstedt, M., Hopkins, L., & G. Kuppelwieser, V. (2014). Partial least squares structural equation modeling (PLS-SEM). European Business Review, 26(2), 106–121. [Google Scholar] [CrossRef]
- Hair, J. F., Risher, J. J., Sarstedt, M., & Ringle, C. M. (2019). When to use and how to report the results of PLS-SEM. European Business Review, 31(1), 2–24. [Google Scholar] [CrossRef]
- Hauk, N., Hüffmeier, J., & Krumm, S. (2018). Ready to be a silver surfer? A meta-analysis on the relationship between chronological age and technology acceptance. Computers in Human Behavior, 84, 304–319. [Google Scholar] [CrossRef]
- Hautus, M. J., Macmillan, N. A., & Creelman, C. D. (2021). Detection theory: A user’s guide. Routledge. [Google Scholar]
- Henseler, J., Dijkstra, T. K., Sarstedt, M., Ringle, C. M., Diamantopoulos, A., Straub, D. W., Ketchen, D. J., Hair, J. F., Hult, G. T. M., & Calantone, R. J. (2014). Common beliefs and reality about PLS: Comments on rönkkö and evermann (2013). Organizational Research Methods, 17(2), 182–209. [Google Scholar] [CrossRef]
- Henseler, J., Hubona, G., & Ray, P. A. (2016). Using PLS path modeling in new technology research: Updated guidelines. Industrial Management & Data Systems, 116(1), 2–20. [Google Scholar] [CrossRef]
- Henseler, J., Ringle, C. M., & Sarstedt, M. (2015). A new criterion for assessing discriminant validity in variance-based structural equation modeling. Journal of the Academy of Marketing Science, 43(1), 115–135. [Google Scholar] [CrossRef]
- Hicks, D. (2005). Phishing and pharming: Helping consumers avoid Internet fraud. Communities and Banking, Fall 2005, 28–31. Available online: https://econpapers.repec.org/RePEc:fip:fedbcb:y:2005:i:fall:p:28-31 (accessed on 9 August 2024).
- Holtfreter, K., Reisig, M. D., & Blomberg, T. G. (2005). Consumer fraud victimization in Florida: An empirical study. St. Thomas Law Review, 18, 761. [Google Scholar]
- Holtfreter, K., Reisig, M. D., Piquero, N. L., & Piquero, A. R. (2010). Low self-control and fraud: Offending, victimization, and their overlap. Criminal Justice and Behavior, 37(2), 188–203. [Google Scholar] [CrossRef]
- Hudson, A. (1998, September 13–19). The uses and abuses of derivatives. Symposium on Economic Crime for a Session titled “Internal Controls for End-Users and Sellers (pp. 1–13), Cambridge, UK. [Google Scholar]
- Huston, S. J. (2010). Measuring financial literacy. Journal of Consumer Affairs, 44(2), 296–316. [Google Scholar] [CrossRef]
- Iman, N., Nugroho, S. S., Junarsin, E., & Pelawi, R. Y. (2023). Is technology truly improving the customer experience? Analysing the intention to use open banking in Indonesia. International Journal of Bank Marketing, 47, 2651. [Google Scholar] [CrossRef]
- Instefjord, N., Jackson, P., Perraudin, W., Pagano, M., & Röell, A. (1998). Securities fraud. Economic Policy, 13(27), 587–623. Available online: http://www.jstor.org/stable/1344764 (accessed on 18 September 2024). [CrossRef]
- Jansen, J., & Leukfeldt, R. (2016). Phishing and malware attacks on online banking customers in the Netherlands: A qualitative analysis of factors leading to victimization. International Journal of Cyber Criminology, 10(1), 79–91. [Google Scholar] [CrossRef]
- Jewkes, Y., & Yar, M. (2013). Handbook of internet crime. Routledge. [Google Scholar]
- Jorgensen, B. L. (2007). Financial literacy of college students: Parental and peer influences. Available online: https://api.semanticscholar.org/CorpusID:150625957 (accessed on 18 September 2024).
- Judges, R. A., Gallant, S. N., Yang, L., & Lee, K. (2017). The role of cognition, personality, and trust in fraud victimization in older adults. Frontiers in Psychology, 8, 1–10. [Google Scholar] [CrossRef]
- Junarsin, E., Pelawi, R. Y., Kristanto, J., Marcelin, I., & Pelawi, J. B. (2023). Does fintech lending expansion disturb financial system stability? Evidence from Indonesia. Heliyon, 9(9), e18384. [Google Scholar] [CrossRef]
- Junger, M., Koning, L., Hartel, P., & Veldkamp, B. (2023). In their own words: Deception detection by victims and near victims of fraud. Frontiers in Psychology, 14, 1135369. [Google Scholar] [CrossRef]
- Kersting, L. M., Marley, R. N., & Mellon, M. J. (2015). The association between financial literacy and trust in financial markets among novice nonprofessional investors. Academy of Accounting and Financial Studies Journal, 19(3), 201. [Google Scholar]
- Krawiec, K. D. (2000). Accounting for greed: Unraveling the rogue trader mystery. Oregon Law Review, 79, 301. [Google Scholar] [CrossRef]
- Krawiec, K. D. (2009). The return of the rogue. Arizona Law Review, 51, 127. [Google Scholar]
- Kubacki, D. (2022). Sale of getback bonds as an example of misselling. Finanse i Prawo Finansowe, 2, 19–33. [Google Scholar] [CrossRef]
- Langenderfer, J., & Shimp, T. A. (2001). Consumer vulnerability to scams, swindles, and fraud: A new theory of visceral influences on persuasion. Psychology & Marketing, 18(7), 763–783. [Google Scholar] [CrossRef]
- Langevoort, D. C. (1997). Organized illusions: A behavioral theory of why corporations mislead stock market investors (and cause other social harms). University of Pennsylvania Law Review, 146, 101. [Google Scholar] [CrossRef]
- Lawson, P. (2009, April 16–24). Identity-related crime victim issues: A discussion paper. Commission on Crime Prevention and Criminal Justice, Vienna, Austria. [Google Scholar]
- Lee, J., & Soberon-Ferrer, H. (1997). Consumer vulnerability to fraud: Influencing factors. Journal of Consumer Affairs, 31(1), 70–89. [Google Scholar] [CrossRef]
- Levi, M. (2017). Organized fraud and organizing frauds: Unpacking research on networks and organization. In Transnational Financial Crime (pp. 309–340). Routledge. [Google Scholar]
- Loewenstein, G. F., Weber, E. U., Hsee, C. K., & Welch, N. (2001). Risk as feelings. Psychological Bulletin, 127(2), 267. [Google Scholar] [CrossRef] [PubMed]
- Lomnicka, E. (2008). Investor protection in securities markets. In The new oxford companion to law (Online Edition). Oxford University Press. [Google Scholar]
- Lu, X., Zhang, X., Guo, J., & Yue, P. (2024). Digital finance era: Will individual investors become better players? Journal of International Financial Markets, Institutions and Money, 91, 101935. [Google Scholar] [CrossRef]
- Lusardi, A., Mitchell, O. S., & Curto, V. (2010). Financial literacy among the young. Journal of Consumer Affairs, 44(2), 358–380. [Google Scholar] [CrossRef]
- Maniscalco, B., Charles, L., & Peters, M. A. K. (2024). Optimal metacognitive decision strategies in signal detection theory. Psychonomic Bulletin & Review, 32, 1041–1069. [Google Scholar] [CrossRef]
- McAlvanah, P., Anderson, K. B., Letzler, R., & Mountjoy, J. (2015). Fraudulent advertising susceptibility: An experimental approach. Available online: https://ssrn.com/abstract=2593898 (accessed on 18 September 2024).
- Mishra, M. K. (2019). Financial literacy and education for improving financial skills. Available online: https://ssrn.com/abstract=3488670 (accessed on 18 September 2024).
- Morgan, R. E. (2021). Financial fraud in the United States, 2017. US Department of Justice, Office of Justice Programs, Bureau of Justice.
- Naylor, R. T. (2007). The alchemy of fraud: Investment scams in the precious-metals mining business. Crime, Law and Social Change, 47(2), 89–120. [Google Scholar] [CrossRef]
- Nolasco, C. A. R. I., Vaughn, M. S., & del Carmen, R. V. (2013). Revisiting the choice model of Ponzi and Pyramid schemes: Analysis of case law. Crime, Law and Social Change, 60(4), 375–400. [Google Scholar] [CrossRef]
- Nunnally, J. C. (1994). The assessment of reliability. Psychometric Theory, 3, 248–292. [Google Scholar]
- OECD/INFE. (2018, March). OECD/INFE toolkit for measuring financial literacy and financial inclusion. OECD. [Google Scholar]
- Ozili, P. K. (2020). Advances and issues in fraud research: A commentary. Journal of Financial Crime, 27(1), 92–103. [Google Scholar] [CrossRef]
- Parasuraman, R. (1986). Vigilance, monitoring, and search. In Handbook of perception and human performance, Vol. 2: Cognitive processes and performance (pp. 1–39). John Wiley & Sons. [Google Scholar]
- Phan, D. H. B., Narayan, P. K., Rahman, R. E., & Hutabarat, A. R. (2020). Do financial technology firms influence bank performance? Pacific-Basin Finance Journal, 62, 101210. [Google Scholar] [CrossRef]
- Phillips-Wren, G., & Adya, M. (2020). Decision making under stress: The role of information overload, time pressure, complexity, and uncertainty. Journal of Decision Systems, 29(Suppl. 1), 213–225. [Google Scholar] [CrossRef]
- Pignatiello, G. A., & Hickman, R. L., Jr. (2018). Correlates of cognitive load in surrogate decision makers of the critically III. Western Journal of Nursing Research, 41(5), 650–666. [Google Scholar] [CrossRef] [PubMed]
- Podsakoff, P. M., MacKenzie, S. B., Lee, J.-Y., & Podsakoff, N. P. (2003). Common method biases in behavioral research: A critical review of the literature and recommended remedies. Journal of Applied Psychology, 88(5), 879–903. [Google Scholar] [CrossRef]
- Policastro, C., & Payne, B. K. (2015). Can you hear me now? Telemarketing fraud victimization and lifestyles. American Journal of Criminal Justice, 40(3), 620–638. [Google Scholar] [CrossRef]
- Raval, D. (2021). Who is victimized by fraud? Evidence from consumer protection cases. Journal of Consumer Policy, 44(1), 43–72. [Google Scholar] [CrossRef]
- Reisig, M. D., & Holtfreter, K. (2013). Shopping fraud victimization among the elderly. Journal of Financial Crime, 20(3), 324–337. [Google Scholar] [CrossRef]
- Reurink, A. (2018). Financial fraud: A literature review. Journal of Economic Surveys, 32(5), 1292–1325. [Google Scholar] [CrossRef]
- Reyns, B. W. (2018). Identity-related crimes. In R. Reichel, & R. Randa R (Eds.), Transnational crime and global security (pp. 161–179). Praeger Security International. [Google Scholar]
- Ringle, C. M., Wende, S., & Becker, J.-M. (2015). SmartPLS3. SmartPLS GmbH. [Google Scholar]
- Sahoo, S. R., & Gupta, B. B. (2020). Fake profile detection in multimedia big data on online social networks. International Journal of Information and Computer Security, 12(2–3), 303–331. [Google Scholar] [CrossRef]
- Sarstedt, M., Ringle, C. M., & Hair, J. F. (2017). Treating unobserved heterogeneity in PLS-SEM: A multi-method approach BT—Partial least squares path modeling: Basic concepts, methodological issues and applications (H. Latan, & R. Noonan, Eds.; pp. 197–217). Springer International Publishing. [Google Scholar] [CrossRef]
- Saunders, M., Lewis, P., & Thornhill, A. (2019). Research methods for business students (8th ed.). Pearson. [Google Scholar]
- See, J. E., Howe, S. R., Warm, J. S., & Dember, W. N. (1995). Meta-analysis of the sensitivity decrement in vigilance. Psychological Bulletin, 117(2), 230. [Google Scholar] [CrossRef]
- Sekaran, U., & Bougie, R. (2016). Research methods for business: A skill building approach. John Wiley & Sons. [Google Scholar]
- Shafahi, M., Kempers, L., & Afsarmanesh, H. (2016, December 5–8). Phishing through social bots on Twitter. 2016 IEEE International Conference on Big Data (Big Data) (pp. 3703–3712), Washington, DC, USA. [Google Scholar] [CrossRef]
- Shang, Y., Wu, Z., Du, X., Jiang, Y., Ma, B., & Chi, M. (2022). The psychology of the internet fraud victimization of older adults: A systematic review. Frontiers in Psychology, 13, 912242. [Google Scholar] [CrossRef]
- Shapiro, D. (2013). Generating alpha return: How ponzi schemes lure the unwary in an unregulated market. In How they got away with it: White collar criminals and the financial meltdown (pp. 130–147). Columbia University Press. Available online: http://www.jstor.org/stable/10.7312/will15690 (accessed on 22 October 2024).
- Shapiro, S. P. (1987). Wayward capitalists: Targets of the securities and exchange commission. Yale University Press. [Google Scholar]
- Shaw, T. H., Matthews, G., Warm, J. S., Finomore, V. S., Silverman, L., & Costa, P. T. (2010). Individual differences in vigilance: Personality, ability and states of stress. Journal of Research in Personality, 44(3), 297–308. [Google Scholar] [CrossRef]
- Shmueli, G., Sarstedt, M., Hair, J. F., Cheah, J.-H., Ting, H., Vaithilingam, S., & Ringle, C. M. (2019). Predictive model assessment in PLS-SEM: Guidelines for using PLSpredict. European Journal of Marketing, 53(11), 2322–2347. [Google Scholar] [CrossRef]
- Shover, N., Coffey, G. S., & Sanders, C. R. (2004). Dialing for dollars: Opportunities, justifications, and telemarketing fraud. Qualitative Sociology, 27(1), 59–75. [Google Scholar] [CrossRef]
- Simborg, D. W. (2008). Healthcare fraud: Whose problem is it anyway? Journal of the American Medical Informatics Association: JAMIA, 15(3), 278–280. [Google Scholar] [CrossRef] [PubMed]
- Skinner, H. E., & Giesbrecht, B. (2025). Beyond detection rate: Understanding the vigilance decrement using signal detection theory. Frontiers in Cognition, 3. Available online: https://www.frontiersin.org/journals/cognition/articles/10.3389/fcogn.2024.1505046 (accessed on 18 January 2025).
- Stanovich, K. E., Sá, W. C., & West, R. F. (2004). Individual differences in thinking, reasoning, and decision making. In The nature of reasoning (pp. 375–409). Cambridge University Press. [Google Scholar] [CrossRef]
- Streukens, S., & Leroi-Werelds, S. (2016). Bootstrapping and PLS-SEM: A step-by-step guide to get more out of your bootstrap results. European Management Journal, 34(6), 618–632. [Google Scholar] [CrossRef]
- Tenenhaus, M., Vinzi, V. E., Chatelin, Y.-M., & Lauro, C. (2005). PLS path modeling. Computational Statistics & Data Analysis, 48(1), 159–205. [Google Scholar] [CrossRef]
- Tiwari, V. (2017, May 5–6). Analysis and detection of fake profile over social network. 2017 International Conference on Computing, Communication and Automation (ICCCA) (pp. 175–179), Greater Noida, India. [Google Scholar] [CrossRef]
- Tseng, P.-L., & Guo, W.-C. (2022). Fintech, credit market competition, and bank asset quality. Journal of Financial Services Research, 61(3), 285–318. [Google Scholar] [CrossRef]
- Udayakumar, R., Joshi, A., Boomiga, S. S., & Sugumar, R. (2023). Deep fraud net: A deep learning approach for cyber security and financial fraud detection and classification. Journal of Internet Services and Information Security, 13(4), 138–157. [Google Scholar] [CrossRef]
- Van Wyk, J., & Mason, K. A. (2001). Investigating vulnerability and reporting behavior for consumer fraud victimization. Journal of Contemporary Criminal Justice, 17(4), 328–345. [Google Scholar] [CrossRef]
- Velikonja, U. (2012). The cost of securities fraud. William & Mary Law Review, 54, 1887. [Google Scholar]
- Venkataraman, R., & Venkatesan, T. (2018). Analysis of factors determining financial literacy using structural equation modelling. Journal of Management, 9(2), 19–29. [Google Scholar] [CrossRef]
- Waqas, M., Rafiq, S., & Wu, J. (2023). Online shopping: A systematic review of customers’ perceived benefits and challenges during COVID-19 pandemic. Global Knowledge, Memory and Communication. ahead-of-print. [Google Scholar] [CrossRef]
- Warm, J. S., Matthews, G., & Finomore, V. S., Jr. (2018). Vigilance, workload, and stress. In Performance under stress (pp. 131–158). CRC Press. [Google Scholar]
- Wexler, M. N. (2010). Financial edgework and the persistence of rogue traders. Business and Society Review, 115(1), 1–25. [Google Scholar] [CrossRef]
- Wolfe, D. T., & Hermanson, D. R. (2004). The fraud diamond: Considering the four elements of fraud: Certified public accountant. The CPA Journal, 74(12), 38–42. [Google Scholar]
- Xing, T., Sun, F., Wang, K., Zhao, J., Wu, M., & Wu, J. (2020). Vulnerability to fraud among Chinese older adults: Do personality traits and loneliness matter? Journal of Elder Abuse & Neglect, 32(1), 46–59. [Google Scholar] [CrossRef]
- Zeller, T., Jr. (2005, June 21). Black market in stolen credit card data thrives on internet. The New York Times. [Google Scholar]
- Zeng, N., Liu, Y., Gong, P., Hertogh, M., & König, M. (2021). Do right PLS and do PLS right: A critical review of the application of PLS-SEM in construction management research. Frontiers of Engineering Management, 8(3), 356–369. [Google Scholar] [CrossRef]
- Zhang, X., Zhu, S., & Liang, W. (2012, December 10–13). Detecting spam and promoting campaigns in the twitter social network. 2012 IEEE 12th International Conference on Data Mining (pp. 1194–1199), Brussels, Belgium. [Google Scholar] [CrossRef]
- Zhuo, S., Wu, W., Zhou, Y., Cao, R., & Bian, J. (2024). Research on comprehensive blockchain regulation and anti-fraud system BT—Blockchain and trustworthy systems (J. Chen, B. Wen, & T. Chen, Eds.; pp. 133–146). Springer Nature. [Google Scholar]
| Main Construct | Reflective | Instruments |
|---|---|---|
| Fraud Victimization | FV1 | How often did you invest your money because someone had promised high or guaranteed returns? |
| FV2 | How often did you pay to receive a gift, grant, inheritance, or lottery winning that you never received? | |
| FV3 | How often did you give or lend money to someone pretending to be your relative, friend, or acquaintance? | |
| FV4 | When responding to an e-mail or website, how often did you provide your username, password, or debit or credit card information to a stranger/outsider? | |
| Fraud Exposure | FE1 | How often did you receive notification of a lottery win or competition win, but were later informed that you had to pay a certain amount of money or purchase a product to claim your prize? |
| FE2 | How often have you been contacted by someone pretending to come from a legitimate organization, and asked to provide (or confirm) your personal information? | |
| FE3 | How often did you access a website, was told you had a computer or internet problem, and then asked about personal information to resolve it? | |
| FE4 | How often have you been promised that you would receive goods, services, discounts, or important investment profit if you transferred or invested money? | |
| Vigilance | VL1 | You are suspicious of letters or e-mails that contain spelling and grammatical errors. |
| VL2 | You avoid clicking links in e-mails or text messages unless you know the senders. | |
| VL3 | You are suspicious when people you do not know contact you directly, via telephone, e-mail, social media, etc. | |
| VL4 | You always check a vendor’s credibility. | |
| Financial Literacy | FL1 | Net worth is ……
|
| FL2 | Which account usually pays the HIGHEST interest?
| |
| FL3 | What are the MOST important factors that lenders use when deciding as to whether to approve loans?
| |
| FL4 | If a consumer fails to pay personal debt, the creditor is allowed to do all of the following EXCEPT?
| |
| FL5 | What does a credit bureau do?
| |
| FL6 | If a credit card account has a balance carried over from the previous month, when will interest charges usually begin on a new credit purchase?
| |
| FL7 | Which of the following investment combinations is the most risky?
| |
| FL8 | Many people put aside money to take care of unexpected expenses. If you have money to put aside for emergencies, in which of the following forms will it be of LEAST benefit if you need it right away?
| |
| FL9 | The main reason to purchase insurance is to
| |
| FL10 | Rob and Molly are of the same age. At age 25, Rob began saving $2000 a year for 10 years and then stopped at age 35. At age 35, Molly realized that she needed money for retirement and started saving $2000 per year for 30 years and then stopped at age 65. Now they are both 65 years old. Who has the most money in his or her retirement account (assuming both investments had the same interest rate)?
|
| Demographic | Characteristics | Frequency | Percentage |
|---|---|---|---|
| Gender | Male | 253 | 38 |
| Female | 418 | 62 | |
| Age | 17–25 | 302 | 45 |
| 26–35 | 141 | 21 | |
| 36–45 | 101 | 15 | |
| 46–55 | 54 | 8 | |
| 56–65 | 73 | 11 | |
| Level of education | Associate degree | 74 | 11 |
| Bachelor’s degree | 456 | 68 | |
| Master’s degree | 101 | 15 | |
| Doctoral degree | 40 | 6 | |
| Internet usage (weekly) | Below 10 h | 60 | 9 |
| 11–15 h | 362 | 54 | |
| 16–25 h | 228 | 34 | |
| Above 25 h | 21 | 3 |
| Construct | Item | Outer Loading | Cronbach’s Alpha | ρA | Composite Reliability | AVE | VIF |
|---|---|---|---|---|---|---|---|
| Fraud Victimization | FV1 | 0.881 | 0.877 | 0.955 | 0.913 | 0.726 | 3.140 |
| FV2 | 0.858 | 2.131 | |||||
| FV3 | 0.745 | 1.749 | |||||
| FV4 | 0.914 | 2.718 | |||||
| Fraud Exposure | FE1 | 0.701 | 0.780 | 0.787 | 0.854 | 0.595 | 1.248 |
| FE2 | 0.755 | 2.109 | |||||
| FE3 | 0.834 | 2.169 | |||||
| FE4 | 0.792 | 2.607 | |||||
| Vigilance | VL1 | 0.835 | 0.850 | 0.928 | 0.895 | 0.682 | 2.698 |
| VL2 | 0.828 | 2.785 | |||||
| VL3 | 0.821 | 1.720 | |||||
| VL4 | 0.818 | 1.607 |
| VIF | Outer Weight | t-Stats | p-Value | |
|---|---|---|---|---|
| FL1 | 1.597 | 0.214 | 46.482 | 0.000 *** |
| FL2 | 1.463 | 0.213 | 45.015 | 0.000 *** |
| FL3 | 1.316 | 0.218 | 49.908 | 0.000 *** |
| FL4 | 1.094 | 0.130 | 23.092 | 0.000 *** |
| FL5 | 1.576 | 0.161 | 38.255 | 0.000 *** |
| FL6 | 1.356 | 0.108 | 20.336 | 0.000 *** |
| FL7 | 1.796 | 0.213 | 51.976 | 0.000 *** |
| FL8 | 1.264 | 0.214 | 46.132 | 0.000 *** |
| FL9 | 1.383 | 0.218 | 49.202 | 0.000 *** |
| FL10 | 1.173 | 0.213 | 44.666 | 0.000 *** |
| FE | FV | FE*VL | VL | |
|---|---|---|---|---|
| Fraud Exposure (FE) | ||||
| FE*VL | 0.194 | |||
| Fraud Victimization (FV) | 0.256 | 0.154 | ||
| Vigilance (VL) | 0.133 | 0.159 | 0.253 |
| PLS | LM | PLS-LM | Remark | ||
|---|---|---|---|---|---|
| RMSE | Q2 Predict | RMSE | RMSE | ||
| FV4 | 0.635 | 0.116 | 0.546 | 0.089 | Moderate |
| FV3 | 0.855 | 0.298 | 0.974 | −0.119 | |
| FV2 | 0.954 | 0.128 | 0.858 | 0.094 | |
| FV1 | 1.267 | 0.360 | 1.539 | −0.272 | |
| VL4 | 0.606 | 0.279 | 0.646 | −0.036 | Low |
| VL3 | 0.963 | 0.067 | 0.897 | 0.036 | |
| VL2 | 0.885 | 0.016 | 0.805 | 0.036 | |
| VL1 | 0.835 | 0.031 | 0.788 | 0.036 | |
| Variable | Factor 1 (Fraud Victimization) | Factor 2 (Vigilance) | Factor 3 (Fraud Exposure) | Uniqueness | Eigenvalue |
|---|---|---|---|---|---|
| FV1 | 0.679 | 0.050 | 0.461 | 0.293 | 3.275 |
| FV2 | 0.693 | 0.082 | 0.265 | 0.318 | |
| FV3 | 0.797 | 0.094 | 0.397 | 0.167 | |
| FV4 | 0.684 | 0.122 | 0.471 | 0.236 | |
| FE1 | 0.426 | 0.433 | −0.369 | 0.346 | 1.802 |
| FE2 | 0.420 | 0.477 | −0.474 | 0.313 | |
| FE3 | 0.353 | 0.424 | −0.519 | 0.342 | |
| FE4 | 0.459 | 0.391 | −0.508 | 0.264 | |
| VL1 | −0.368 | 0.699 | 0.303 | 0.232 | 2.552 |
| VL2 | −0.329 | 0.746 | 0.240 | 0.229 | |
| VL3 | −0.391 | 0.646 | 0.251 | 0.313 | |
| VL4 | −0.374 | 0.555 | 0.201 | 0.381 |
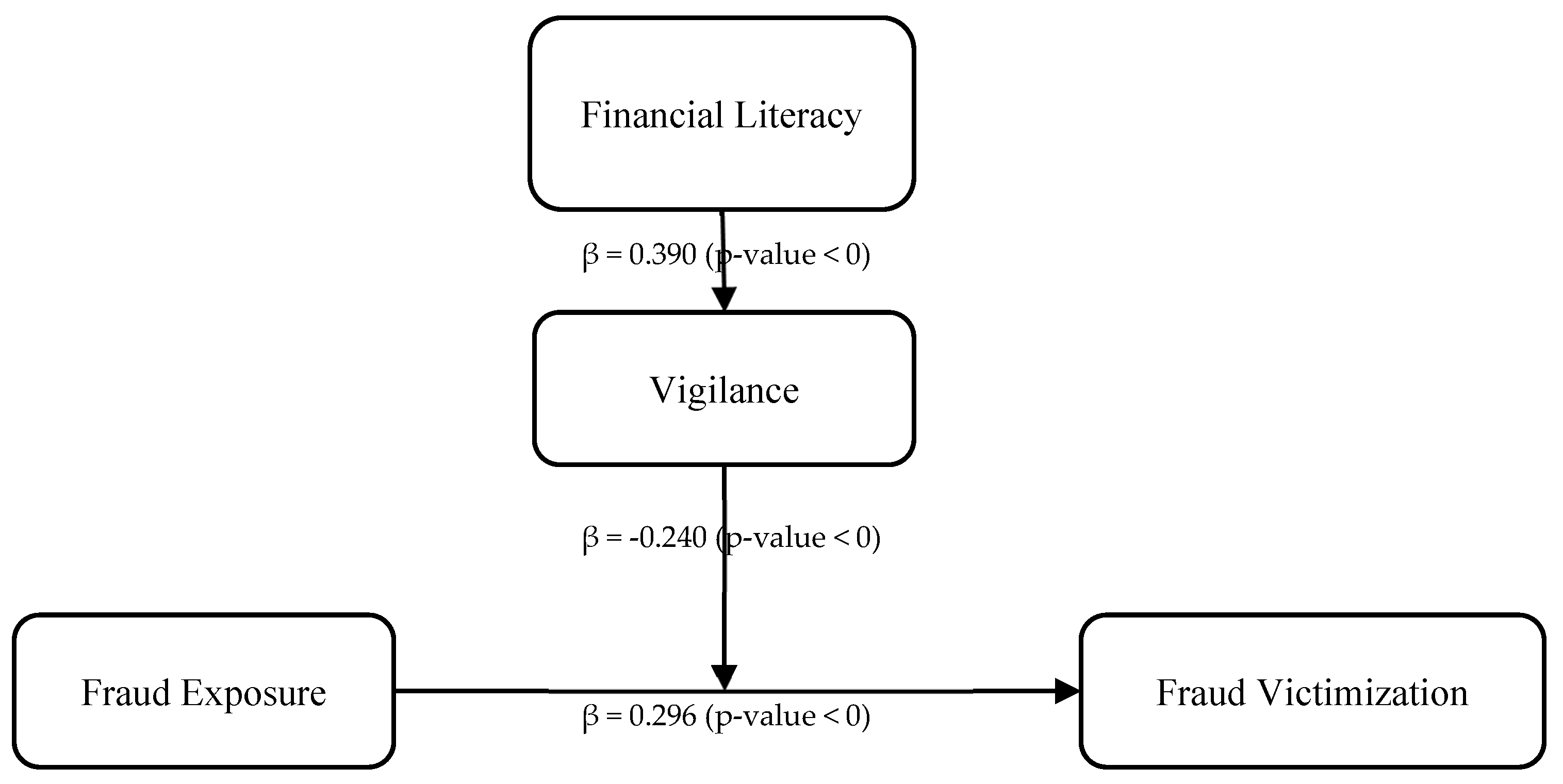
| Path | Coefficient | Standard Error | t-Stats | p-Value | Decision | |
|---|---|---|---|---|---|---|
| Hypothesis 1 | FE → FV | 0.296 | 0.031 | 9.457 | 0.000 *** | Supported |
| VL→FV | −0.320 | 0.027 | 11.657 | 0.000 *** | ||
| Hypothesis 2 | FE*VL → FV | −0.240 | 0.035 | 6.811 | 0.000 *** | Supported |
| Hypothesis 3 | FL → FV | 0.390 | 0.037 | 10.454 | 0.000 *** | Supported |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pelawi, R.Y.; Tandelilin, E.; Lantara, I.W.N.; Junarsin, E. Empowered to Detect: How Vigilance and Financial Literacy Shield Us from the Rising Tide of Financial Frauds. J. Risk Financial Manag. 2025, 18, 425. https://doi.org/10.3390/jrfm18080425
Pelawi RY, Tandelilin E, Lantara IWN, Junarsin E. Empowered to Detect: How Vigilance and Financial Literacy Shield Us from the Rising Tide of Financial Frauds. Journal of Risk and Financial Management. 2025; 18(8):425. https://doi.org/10.3390/jrfm18080425
Chicago/Turabian StylePelawi, Rizky Yusviento, Eduardus Tandelilin, I Wayan Nuka Lantara, and Eddy Junarsin. 2025. "Empowered to Detect: How Vigilance and Financial Literacy Shield Us from the Rising Tide of Financial Frauds" Journal of Risk and Financial Management 18, no. 8: 425. https://doi.org/10.3390/jrfm18080425
APA StylePelawi, R. Y., Tandelilin, E., Lantara, I. W. N., & Junarsin, E. (2025). Empowered to Detect: How Vigilance and Financial Literacy Shield Us from the Rising Tide of Financial Frauds. Journal of Risk and Financial Management, 18(8), 425. https://doi.org/10.3390/jrfm18080425






