CSV: Content Service Offloading System with Vehicular Caching
Abstract
1. Introduction
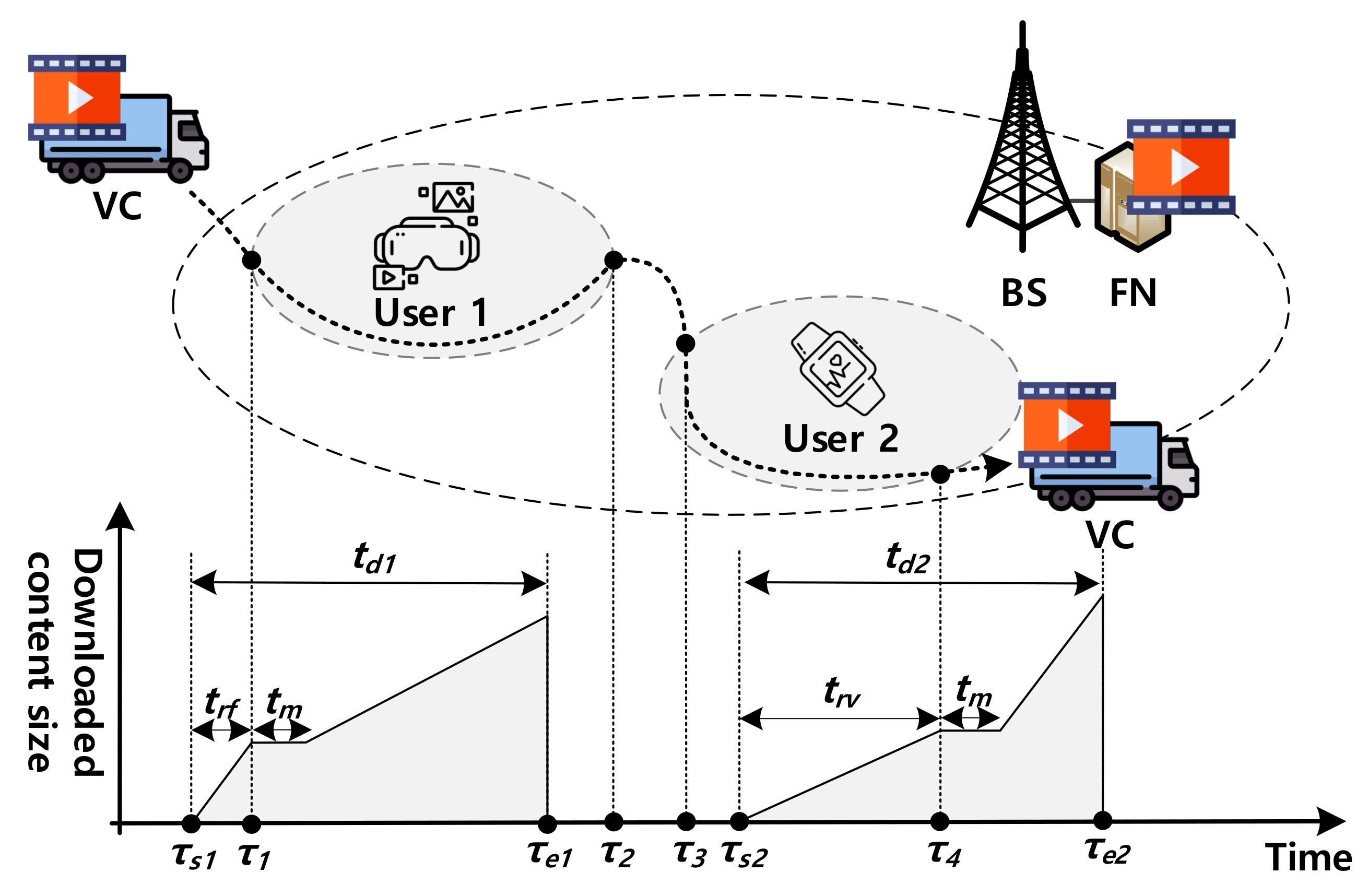
2. System Description
3. Performance Analysis
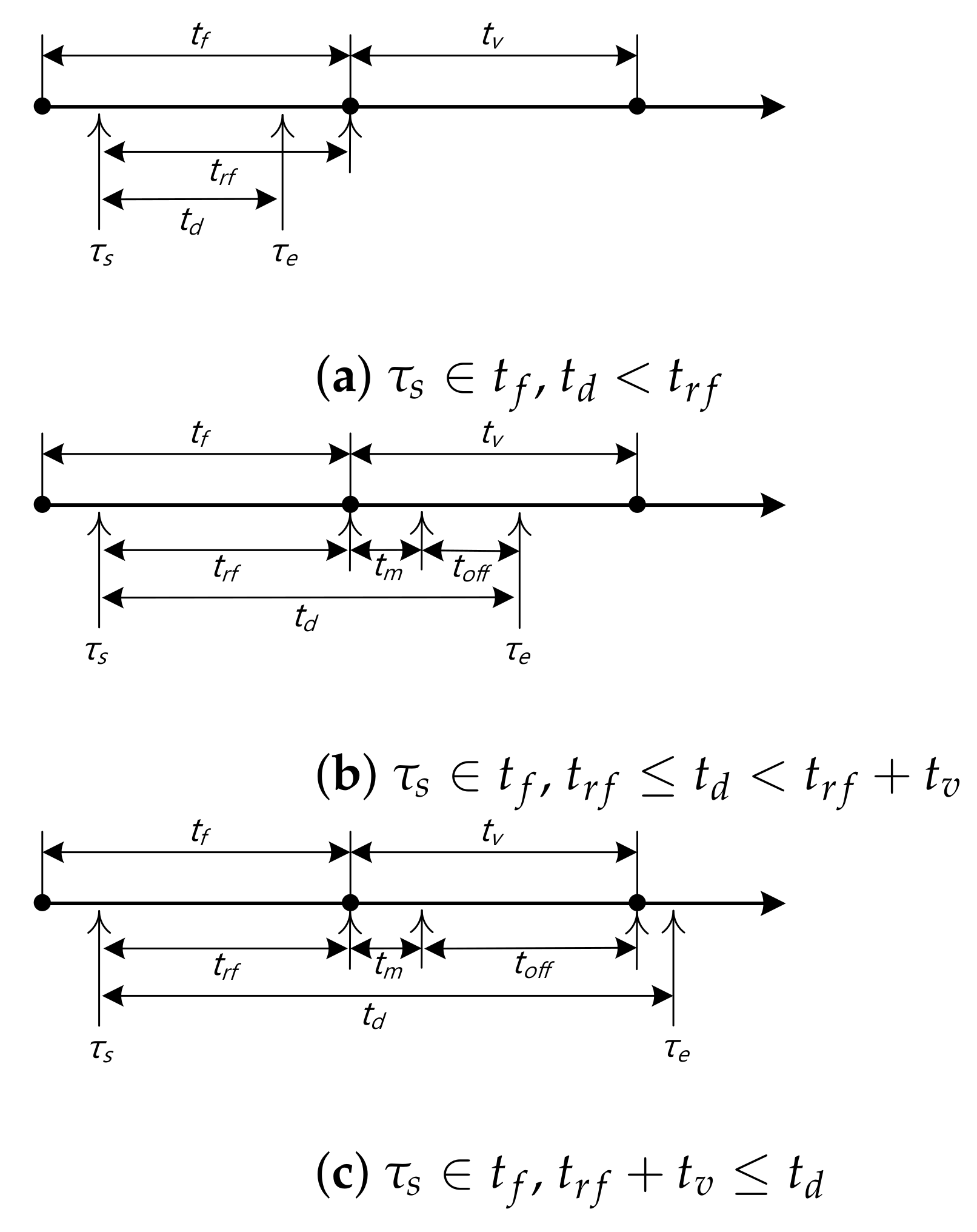
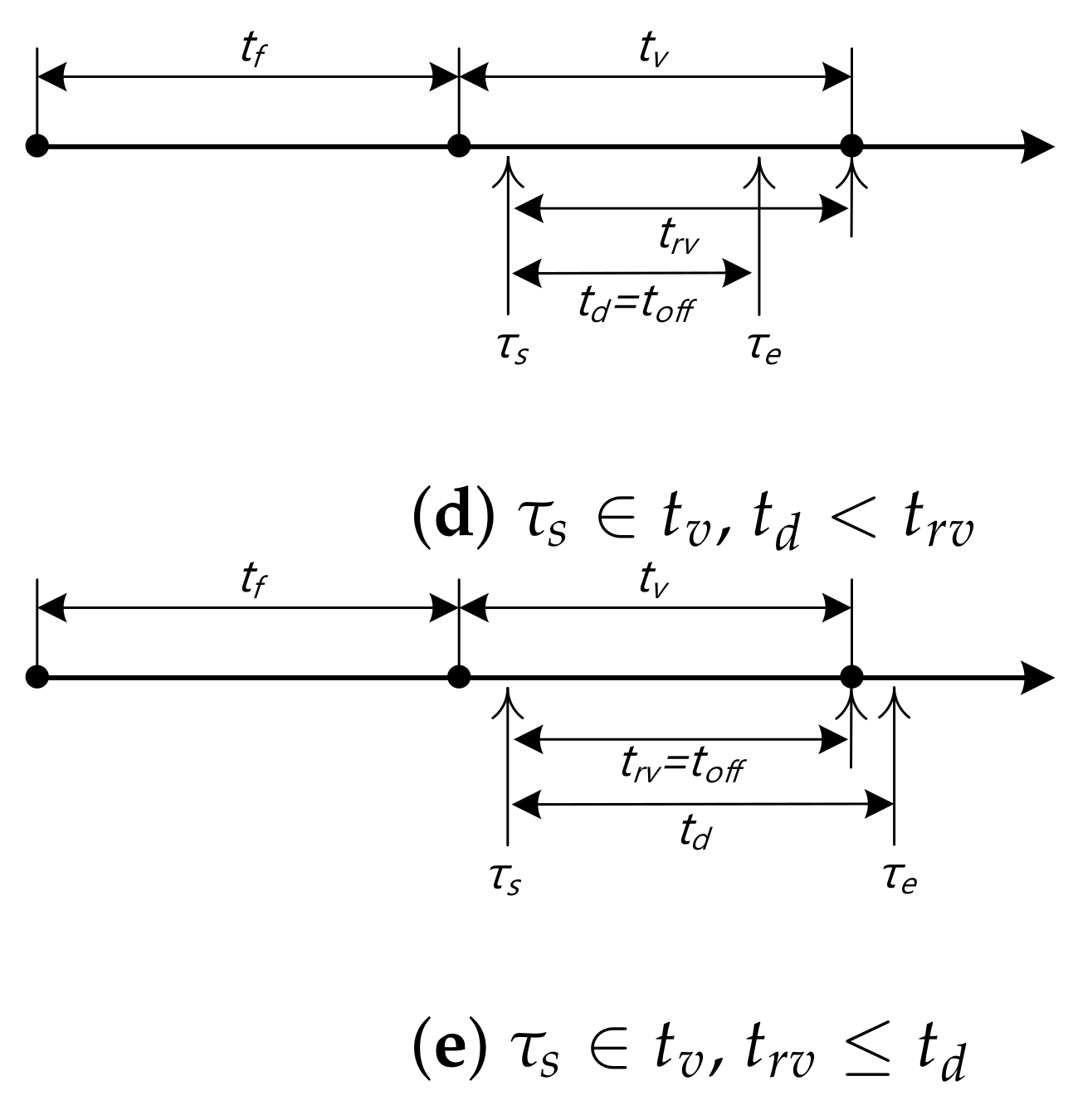
3.1. Effective VC Offloading Time
3.1.1.
3.1.2.
3.1.3.
3.1.4.
3.1.5.
3.2. VC Offloading Efficiency
3.3. VC Offloading Failure
3.3.1.
3.3.2.
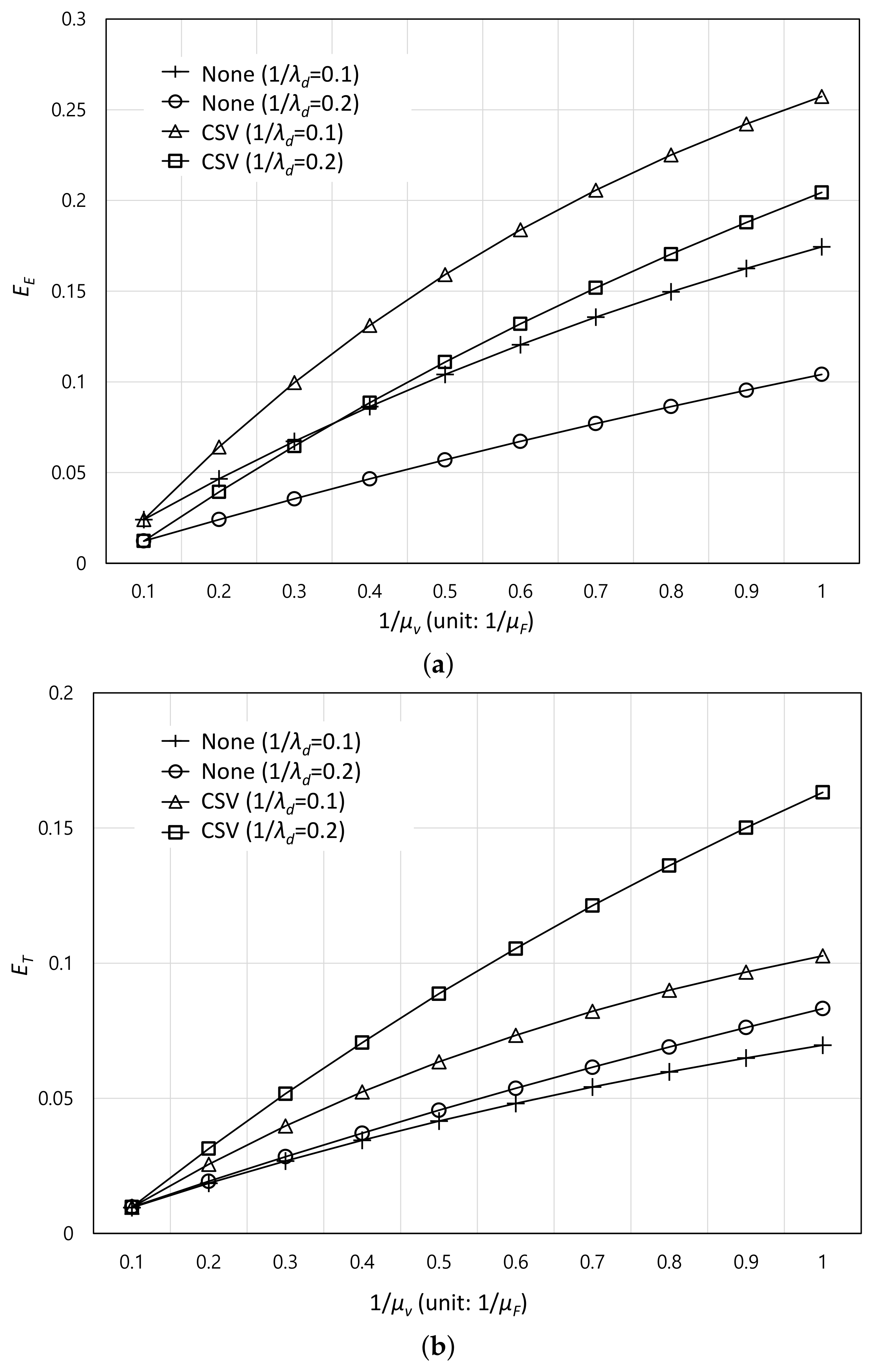
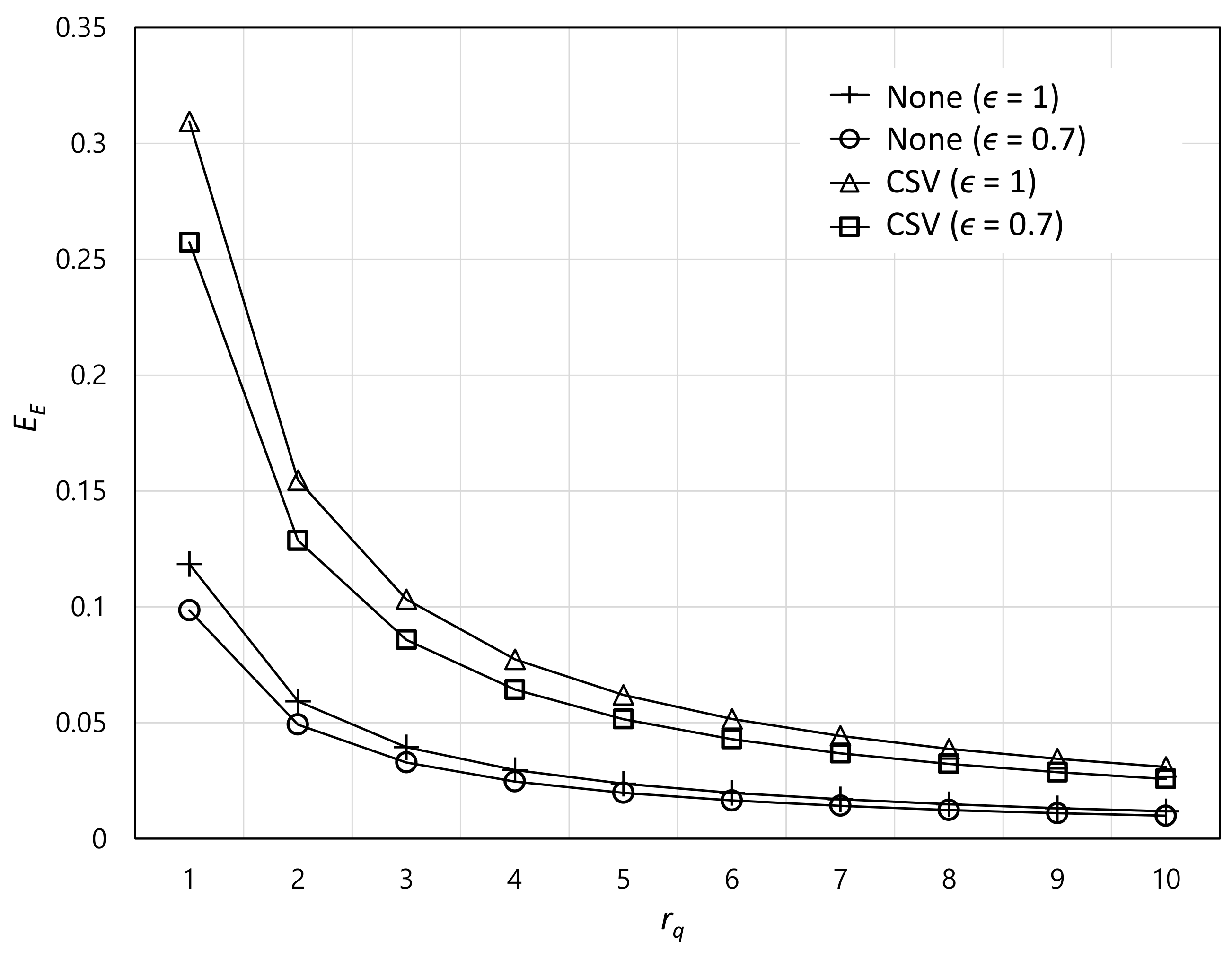
4. Simulation Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Liu, Y.; Peng, M.; Shou, G.; Chen, Y.; Chen, S. Toward edge intelligence: Multiaccess edge computing for 5G and internet of things. IEEE Internet Things J. 2020, 7, 672–6747. [Google Scholar] [CrossRef]
- Fan, Q.; Ansari, N. Towards workload balancing in fog computing empowered IoT. IEEE Trans. Netw. Sci. Eng. 2020, 7, 253–262. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Wang, L. Offloading in internet of vehicles: A fog-enabled real-time traffic management system. IEEE Trans. Ind. Inform. 2018, 14, 4568–4578. [Google Scholar] [CrossRef]
- Ruan, Y.; Joe-Wong, C. On the Economic Value of Mobile Caching. In Proceedings of the IEEE INFOCOM, Toronto, ON, Canada, 6–9 July 2020. [Google Scholar]
- Su, Z.; Hui, Y.; Xu, Q.; Yang, T.; Liu, J.; Jia, Y. An edge caching scheme to distribute content in vehicular networks. IEEE Trans. Veh. Technol. 2018, 67, 5346–5356. [Google Scholar] [CrossRef]
- Wu, H.; Zhang, J.; Cai, Z.; Liu, F.; Li, Y.; Liu, A. Toward energy-aware caching for intelligent connected vehicles. IEEE Internet Things J. 2020, 7, 8157–8166. [Google Scholar] [CrossRef]
- Huang, X.; Xu, K.; Chen, Q.; Zhang, J. Delay-aware caching in internet of vehicles networks. IEEE Internet Things J. 2021, 8, 10911–10921. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, C.; Luan, T.H.; Fu, Y.; Shi, W.; Zhu, L. A mobility-aware vehicular caching scheme in content centric networks: Model and optimization. IEEE Trans. Veh. Technol. 2019, 68, 3100–3112. [Google Scholar] [CrossRef]
- Yao, L.; Wang, Y.; Wang, X.; Guowei, W.U. Cooperative caching in vehicular content centric network based on social attributes and mobility. IEEE Trans. Mob. Comput. 2021, 20, 391–402. [Google Scholar] [CrossRef]
- Taleb, T.; Ksentini, A. Follow me cloud: Interworking federated Clouds and distributed mobile networks. IEEE Netw. 2013, 27, 12–19. [Google Scholar] [CrossRef]
- Bao, W.; Yuan, D.; Yang, Z.; Wang, S.; Li, W.; Zhou, B.B.; Zomaya, A.Y. Follow me fog: Toward seamless handover timing schemes in a fog computing environment. IEEE Commun. Mag. 2017, 55, 72–78. [Google Scholar] [CrossRef]
- Addad, R.A.; Dutra, D.L.C.; Bagaa, M.; Taleb, T.; Flinck, H. Fast service migration in 5G trends and scenarios. IEEE Netw. 2020, 34, 92–98. [Google Scholar] [CrossRef]
- Kyung, Y.; Kim, E.; Song, T. Opportunistic offloading scheme for content delivery service using electro-mobility networks. IET Intell. Transp. Syst. 2022, 1–8. [Google Scholar] [CrossRef]
- TS 23.285; Architecture Enhancements for V2X Services. 3GPP: Sophia Antipolis, France, 2022.
- TS 23.286; Application Layer Support for Vehicle-to-Everything (V2X) Services. 3GPP: Sophia Antipolis, France, 2022.
- Ko, H.; Kyung, Y. DYSON: Delayed offloading scheme with opportunistic fog nodes. IEEE Trans. Veh. Technol. 2022, 71, 10203–10208. [Google Scholar] [CrossRef]
- Shah, S.A.A.; Ahmed, E.; Imran, M.; Zeadally, S. 5G for Vehicular Communications. IEEE Commun. Mag. 2019, 56, 111–117. [Google Scholar] [CrossRef]
- Michalopoulou, M.; Kolios, P.; Panayiotou, C.; Ellinas, G. An Event-Triggering Approach for Bus Tracking Based on Multimodel Mobility Prediction. In Proceedings of the IEEE Intelligent Transportation System Conference, Auckland, New Zealand, 27–30 October 2019. [Google Scholar]
- Wichtlhuber, M.; Reinecke, R.; Hausheer, D. An SDN-based CDN/ISP collaboration architecture for managing high-volume flows. IEEE Trans. Netw. Serv. Manag. 2015, 12, 48–60. [Google Scholar] [CrossRef]
- Lee, J.H.; Lee, G.; Pack, S. Pseudonyms in IPv6 ITS communications: Use of pseudonyms, performance degradation, and optimal pseudonym change. Int. J. Distrib. Sens. Netw. 2015, 2015, 189389. [Google Scholar] [CrossRef]
- Ko, H.; Lee, J.; Pack, S. Performance optimization of delayed WiFi offloading in heterogeneous networks. IEEE Trans. Veh. Technol. 2017, 66, 9436–9447. [Google Scholar] [CrossRef]
- Lim, H.T.; Kim, Y.; Pack, S.; Kang, C.H. Call admission control with heterogeneous mobile stations in cellular/WLAN interworking systems. EURASIP J. Wirel. Comm. Netw. 2011, 91. [Google Scholar] [CrossRef]
- Suh, D.; Ko, H.; Pack, S. Efficiency analysis of WiFi offloading techniques. IEEE Trans. Veh. Technol. 2016, 65, 3813–3817. [Google Scholar] [CrossRef]
- Ross, S.M. Stochastic Processes; John Wiley: New York, NY, USA, 1996. [Google Scholar]
- Wu, H.; Chen, J.; Xu, W.; Cheng, N.; Shi, W.; Wang, L.; Shen, X. Delay-minimized edge caching in heterogeneous vehicular networks: A matching-based approach. IEEE Trans. Wirel. Commun. 2020, 19, 6409–6424. [Google Scholar] [CrossRef]
- Gao, J.; Zhang, S.; Zhao, L.; Shen, X. The design of dynamic probabilistic caching with time-varying content popularity. IEEE Trans. Mob. Comput. 2021, 20, 1672–1684. [Google Scholar] [CrossRef]

| Parameter | Default Value |
|---|---|
| 10 | |
| 10 | |
| 10 Mbps | |
| 5 Mbps | |
| Q | 50 |
| 0.01 | |
| 1 | |
| 10 GB | |
| Content size | [500 MB, 1000 MB] |
| 0.7 |
| 0.1 | |||||
| 0.2 | |||||
| tm | 0.01 | 0.02 | 0.03 | 0.04 | 0.05 | |
|---|---|---|---|---|---|---|
| 1/μv | ||||||
| 0.5/μf | 0.159 | 0.141 | 0.127 | 0.114 | 0.104 | |
| 1/μf | 0.257 | 0.240 | 0.225 | 0.213 | 0.202 | |
| tm | 0.01 | 0.02 | 0.03 | 0.04 | 0.05 | |
|---|---|---|---|---|---|---|
| 1/μv | ||||||
| 0.5/μf | 0.33% | 1.64% | 2.93% | 4.21% | 5.46% | |
| 1/μf | 0.05% | 0.64% | 1.45% | 2.25% | 3.05% | |
| Q | 10 | 30 | 50 | 70 | 90 | |
|---|---|---|---|---|---|---|
| CSV | 0.244 | 0.179 | 0.159 | 0.148 | 0.141 | |
| None | 0.160 | 0.117 | 0.104 | 0.097 | 0.092 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kyung, Y.; Song, T. CSV: Content Service Offloading System with Vehicular Caching. Sensors 2022, 22, 7967. https://doi.org/10.3390/s22207967
Kyung Y, Song T. CSV: Content Service Offloading System with Vehicular Caching. Sensors. 2022; 22(20):7967. https://doi.org/10.3390/s22207967
Chicago/Turabian StyleKyung, Yeunwoong, and Taewon Song. 2022. "CSV: Content Service Offloading System with Vehicular Caching" Sensors 22, no. 20: 7967. https://doi.org/10.3390/s22207967
APA StyleKyung, Y., & Song, T. (2022). CSV: Content Service Offloading System with Vehicular Caching. Sensors, 22(20), 7967. https://doi.org/10.3390/s22207967







