Gravity-Law Based Critical Bots Identification in Large-Scale Heterogeneous Bot Infection Network
Abstract
1. Introduction
- We elaborate a SEIR-based HBIN by utilizing the advantages of the SEIR model and a heterogeneous information network (HIN), where the SEIR model depicts the transition states of bots, and HIN provides the heterogeneous spatial-temporal dependencies among various botnet devices. Such a comprehensive HBIN is capable of representing significant propagation characteristics on a global bot infection network for further influential bots identification;
- We design a Gravity-law based Critical Bots Identification algorithm based on HBIN, which distinguishes the influences of bots into intrinsic influences and diffusion influences. Such a GCBI algorithm is capable of identifying the critical bots in both local and global potential structural heterogeneous temporal-spatial dimensions;
- We implement an IoT botnet monitor system and collect millions of bot samples with distinct labels. We evaluate the effectiveness of our proposed algorithm with extensive experiments on the large-scale real dataset.
2. Botnet Infection Model
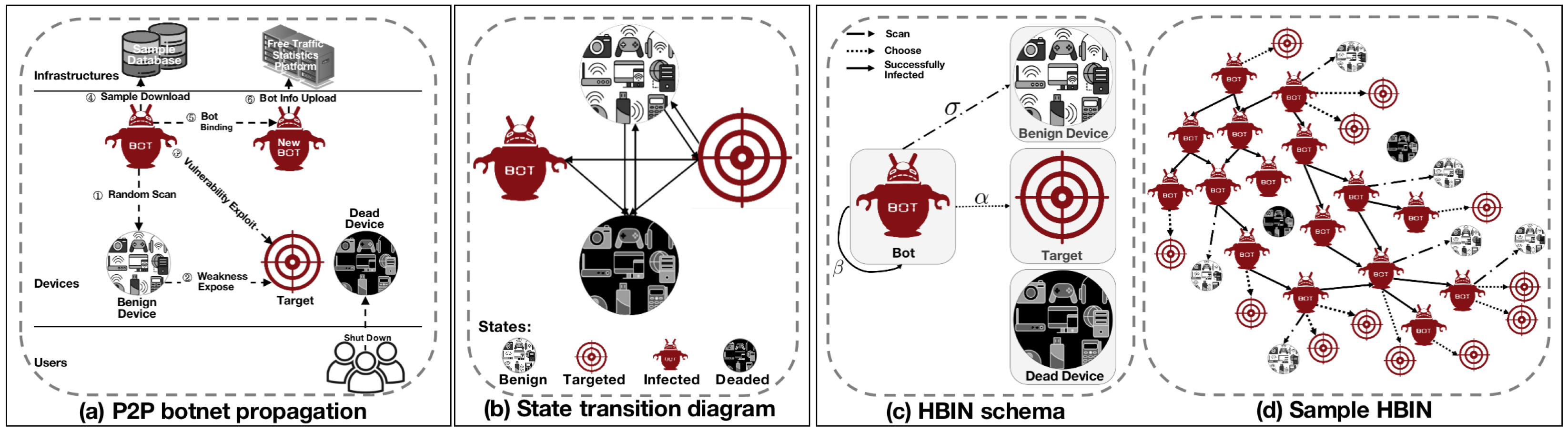
2.1. SEIR State Transition Diagram
2.2. HBIN Model
| Algorithm 1: Heterogeneous Bot Infection Network Generation Algorithm. |
 |
3. Critical Bots Identification
| Algorithm 2: Infection diffusion score calculation. |
 |
4. Implementation and Evaluations
4.1. Experiment Setup
- Nodes count (N);
- Node types count ();
- nodes number ();
- nodes number ();
- nodes number ();
- nodes number ();
- Edges count (E);
- Edge types count ();
- edge number ();
- edge number ();
- edge number ();
- The average of node out-degree ();
- Network diameter (): largest value of the shortest path distance between any two nodes;
- The average of shortest path length (): the average of shortest path length between any two nodes;
- The average of clustering coefficient (C): the average local clustering coefficient over all the nodes;
4.2. Baseline Methods and Metrics
4.3. Performance Comparison
5. System Deployment and Impacts
6. Related Work
7. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Trautman, L.J.; Hussein, M.T.; Ngamassi, L.; Molesky, M.J. Governance of the Internet of Things (loT). Jurimetrics J. 2020, 60, 315–351. [Google Scholar]
- Xu, Y.; Jiang, Y.; Yu, L.; Li, J. Brief Industry Paper: Catching IoT Malware in the Wild Using HoneyIoT. In Proceedings of the IEEE 27th Real-Time and Embedded Technology and Applications Symposium (RTAS), Nashville, TN, USA, 18–21 May 2021; pp. 433–436. [Google Scholar]
- Evesti, A.; Kanstrén, T.; Frantti, T. Cybersecurity situational awareness taxonomy. In Proceedings of the 2017 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (Cyber SA), London, UK, 19–20 June 2017; pp. 1–8. [Google Scholar]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Xie, J.; Tan, L. Fake-honeypot Detection Method for Semi-distributed Peer-to-Peer Botnet. Jisuanji Gongcheng/Comput. Eng. 2010, 36, 111–113. [Google Scholar]
- Schiller, C.; Binkley, J.R. Botnets: The killer Web Applications; Elsevier: Amsterdam, The Netherlands, 2011. [Google Scholar]
- Lu, Z.; Wang, W.; Wang, C. On the evolution and impact of mobile botnets in wireless networks. IEEE Trans. Mob. Comput. 2015, 15, 2304–2316. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Systems and Networks Research Lab. Available online: https://sysnet.lums.edu.pk/ (accessed on 2 May 2016).
- Al-Sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M. Internet of Things (IoT) communication protocols. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Amman, Jordan, 17–18 May 2017; pp. 685–690. [Google Scholar]
- Pastor-Satorras, R.; Vespignani, A. Epidemic spreading in scale-free networks. Phys. Rev. Lett. 2001, 86, 3200. [Google Scholar] [CrossRef] [PubMed]
- Chen, D.; Lü, L.; Shang, M.S.; Zhang, Y.C.; Zhou, T. Identifying influential nodes in complex networks. Phys. A Stat. Mech. Its Appl. 2012, 391, 1777–1787. [Google Scholar] [CrossRef]
- Bae, J.; Kim, S. Identifying and ranking influential spreaders in complex networks by neighborhood coreness. Phys. A Stat. Mech. Its Appl. 2014, 395, 549–559. [Google Scholar] [CrossRef]
- Kitsak, M.; Gallos, L.K.; Havlin, S.; Liljeros, F.; Muchnik, L.; Stanley, H.E.; Makse, H.A. Identification of influential spreaders in complex networks. Nat. Phys. 2010, 6, 888–893. [Google Scholar] [CrossRef]
- Zeng, A.; Zhang, C.J. Ranking spreaders by decomposing complex networks. Phys. Lett. A 2013, 377, 1031–1035. [Google Scholar] [CrossRef]
- Sabidussi, G. The centrality index of a graph. Psychometrika 1966, 31, 581–603. [Google Scholar] [CrossRef]
- Wang, W.; Tang, M.; Stanley, H.E.; Braunstein, L.A. Unification of theoretical approaches for epidemic spreading on complex networks. Rep. Prog. Phys. 2017, 80, 036603. [Google Scholar] [CrossRef] [PubMed]
- Page, L.; Brin, S.; Motwani, R.; Winograd, T. The PageRank Citation Ranking: Bringing Order to the Web; Technical Report; Stanford InfoLab: Stanford, CA, USA, 1999. [Google Scholar]
- Chen, D.B.; Gao, H.; Lü, L.; Zhou, T. Identifying influential nodes in large-scale directed networks: The role of clustering. PLoS ONE 2013, 8, e77455. [Google Scholar] [CrossRef] [PubMed]
- Ma, L.l.; Ma, C.; Zhang, H.F.; Wang, B.H. Identifying influential spreaders in complex networks based on gravity formula. Phys. A Stat. Mech. Its Appl. 2016, 451, 205–212. [Google Scholar] [CrossRef]
- Xie, Y.; Wang, X.; Jiang, D.; Xu, R. High-performance community detection in social networks using a deep transitive autoencoder. Inf. Sci. 2019, 493, 75–90. [Google Scholar] [CrossRef]
- Knight, W.R. A computer method for calculating Kendall’s tau with ungrouped data. J. Am. Stat. Assoc. 1966, 61, 436–439. [Google Scholar] [CrossRef]
- Shang, Q.; Deng, Y.; Cheong, K.H. Identifying influential nodes in complex networks: Effective distance gravity model. Inf. Sci. 2021, 577, 162–179. [Google Scholar] [CrossRef]
- Team Cymru. Available online: http://www.team-cymru.org/ (accessed on 23 January 2022).
- Abou Daya, A.; Salahuddin, M.A.; Limam, N.; Boutaba, R. A graph-based machine learning approach for bot detection. In Proceedings of the 2019 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Arlington, VA, USA, 8–12 April 2019; pp. 144–152. [Google Scholar]
- Alieyan, K.; ALmomani, A.; Manasrah, A.; Kadhum, M.M. A survey of botnet detection based on DNS. Neural Comput. Appl. 2017, 28, 1541–1558. [Google Scholar] [CrossRef]
- Pektaş, A.; Acarman, T. Botnet detection based on network flow summary and deep learning. Int. J. Netw. Manag. 2018, 28, e2039. [Google Scholar] [CrossRef]
- Pektaş, A.; Acarman, T. Effective feature selection for botnet detection based on network flow analysis. In Proceedings of the International Conference Automatics and Informatics, Madrid, Spain, 26–28 July 2017; pp. 1–4. [Google Scholar]
- Stevanovic, M.; Pedersen, J.M. On the use of machine learning for identifying botnet network traffic. J. Cyber Secur. Mobil. 2016, 4, 32. [Google Scholar] [CrossRef]
- Dua, S.; Du, X. Data Mining and Machine Learning in Cybersecurity; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Chowdhury, S.; Khanzadeh, M.; Akula, R.; Zhang, F.; Zhang, S.; Medal, H.; Marufuzzaman, M.; Bian, L. Botnet detection using graph-based feature clustering. J. Big Data 2017, 4, 1–23. [Google Scholar] [CrossRef]
- Kong, X.; Li, N.; Zhang, C.; Shen, G.; Ning, Z.; Qiu, T. Multi-Feature Representation based COVID-19 Risk Stage Evaluation with Transfer Learning. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1359–1375. [Google Scholar] [CrossRef]
- Xia, F.; Wang, L.; Tang, T.; Chen, X.; Kong, X.; Oatley, G.; King, I. CenGCN: Centralized Convolutional Networks with Vertex Imbalance for Scale-Free Graphs. IEEE Trans. Knowl. Data Eng. 2022. [Google Scholar] [CrossRef]
- Kephart, J.O.; White, S.R. Directed-graph epidemiological models of computer viruses. In Computation: The Micro and the Macro View; World Scientific: Singapore, 1992; pp. 71–102. [Google Scholar]
- Abaid, Z.; Sarkar, D.; Kaafar, M.A.; Jha, S. The early bird gets the botnet: A markov chain based early warning system for botnet attacks. In Proceedings of the 2016 IEEE 41st Conference on Local Computer Networks (LCN), Dubai, United Arab Emirates, 7–10 November 2016; pp. 61–68. [Google Scholar]
- Hasan, M.K.; Ismail, A.F.; Islam, S.; Hashim, W.; Ahmed, M.M.; Memon, I. A novel HGBBDSA-CTI approach for subcarrier allocation in heterogeneous network. Telecommun. Syst. 2019, 70, 245–262. [Google Scholar] [CrossRef]
- Liu, F.; Wang, Z.; Deng, Y. GMM: A generalized mechanics model for identifying the importance of nodes in complex networks. Knowl.-Based Syst. 2020, 193, 105464. [Google Scholar] [CrossRef]
- Hu, P.; Mei, T. Ranking influential nodes in complex networks with structural holes. Phys. A Stat. Mech. Its Appl. 2018, 490, 624–631. [Google Scholar] [CrossRef]
- Wang, Z.; Du, C.; Fan, J.; Xing, Y. Ranking influential nodes in social networks based on node position and neighborhood. Neurocomputing 2017, 260, 466–477. [Google Scholar] [CrossRef]
- Zareie, A.; Sheikhahmadi, A.; Fatemi, A. Influential nodes ranking in complex networks: An entropy-based approach. Chaos Solitons Fractals 2017, 104, 485–494. [Google Scholar] [CrossRef]
- Wang, M.; Li, W.; Guo, Y.; Peng, X.; Li, Y. Identifying influential spreaders in complex networks based on improved k-shell method. Phys. A Stat. Mech. Its Appl. 2020, 554, 124229. [Google Scholar] [CrossRef]
- Da Silva, L.N.; Malacarne, A.; e Silva, J.W.S.; Kirst, F.V.; De-Bortoli, R. The Scientific Collaboration Networks in University Management in Brazil. Creat. Educ. 2018, 9, 1469. [Google Scholar] [CrossRef][Green Version]
- Shetty, J.; Adibi, J. Discovering important nodes through graph entropy the case of enron email database. In Proceedings of the 3rd International Workshop on Link Discovery, Chicago, IL, USA, 21–24 August 2005; pp. 74–81. [Google Scholar]
- HBIN. Available online: https://github.com/w0xing/HBIN_data (accessed on 23 January 2022).



| Transition | Conditions |
|---|---|
| Become the target of a bot | |
| Device is closed, or vulnerabilities are repaired | |
| Vulnerabilities exploiting failed | |
| Vulnerabilities exploiting is successful | |
| Device is closed, or vulnerabilities are patched | |
| Device is closed, or vulnerabilities are patched | |
| Device is opened, or new vulnerability are emerged |
| Dataset | N | E | ND | C | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| HBIN | 18,611 | 4 | 12,810 | 5689 | 100 | 12 | 14,473 | 3 | 500 | 13,737 | 236 | 1.072 | 14 | 3.082 | 0.00003 |
| SI | GCBI | DC | Coreness | k-Shell | m-Shell | CC | BC | PR | CR | GM | EFFG | Greedy | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Top-5 ranking of crucial bots in HBIN selected by our proposed method, other state-of-the-art methods and SI benchmark model | |||||||||||||
| 1 | 231 | 231 | 95 | 95 | 3025 | 201 | 95 | 95 | 87 | 231 | 87 | 231 | 9665 |
| 2 | 226 | 226 | 87 | 87 | 1551 | 212 | 87 | 87 | 2271 | 226 | 212 | 226 | 951 |
| 3 | 229 | 229 | 2271 | 2271 | 229 | 9665 | 10,380 | 1980 | 95 | 229 | 49 | 229 | 3320 |
| 4 | 212 | 212 | 523 | 65 | 226 | 11,159 | 11,626 | 1698 | 11,626 | 201 | 5635 | 200 | 7 |
| 5 | 70 | 228 | 65 | 523 | 228 | 1753 | 96 | 1695 | 5989 | 200 | 8969 | 212 | 7377 |
| The total number of the same bots between SI benchmark method and other methods for the ranked top-5 bots | |||||||||||||
| Sum | 5 | 4 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 3 | 0 | 3 | 0 |
| Kendall’s values and the monotonicity values of our proposed method along with other state-of-the-art methods | |||||||||||||
| 1 | 0.556 | 0.156 | 0.244 | 0.067 | 0.111 | −0.067 | 0.032 | −0.111 | 0.2 | −0.022 | 0.333 | 0.114 | |
| M | 1 | 0.928 | 1 | 0.054 | 0.277 | 0.99 | 0.195 | 1 | 1 | 0.898 | 1 | 0.419 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, Q.; Wang, L.; Cui, L.; Yang, L.; Luo, B. Gravity-Law Based Critical Bots Identification in Large-Scale Heterogeneous Bot Infection Network. Electronics 2022, 11, 1771. https://doi.org/10.3390/electronics11111771
He Q, Wang L, Cui L, Yang L, Luo B. Gravity-Law Based Critical Bots Identification in Large-Scale Heterogeneous Bot Infection Network. Electronics. 2022; 11(11):1771. https://doi.org/10.3390/electronics11111771
Chicago/Turabian StyleHe, Qinglin, Lihong Wang, Lin Cui, Libin Yang, and Bing Luo. 2022. "Gravity-Law Based Critical Bots Identification in Large-Scale Heterogeneous Bot Infection Network" Electronics 11, no. 11: 1771. https://doi.org/10.3390/electronics11111771
APA StyleHe, Q., Wang, L., Cui, L., Yang, L., & Luo, B. (2022). Gravity-Law Based Critical Bots Identification in Large-Scale Heterogeneous Bot Infection Network. Electronics, 11(11), 1771. https://doi.org/10.3390/electronics11111771







